Introduction
This document describes conditions that need to be met in order to trigger Automated Actions.
Background Information
Automated Actions get triggered upon a compromise (means an un-compromised machine becomes a compromised machine). If an already-compromised machine triggers a new detection, this detection is added to the compromise, but since this is not a new compromise, it does not trigger an automated action.
One exception to this is the severity level. Automated actions get triggered based on criteria which is severity, nevertheless, compromises do not have severity by itself (onlyindividual detections do). If an Automated Action is configured to a severity level of high and a detection triggers as medium level, it does not trigger the action. If a subsequent event is added to the compromise that is high, the action triggers as this new detection is in the compromise that already exists.
What is a compromised machine?
A compromised machine is an endpoint that has an active compromise associated with it. A compromised machine can, by design, only have one compromise active at one time.
Applicability
Windows, Mac
Automated Actions Available
-
Take a forensic snapshot upon Compromise: Takes a Forensic Snapshot of a computer when a compromise occurs. A compromise event is basically an event sent by a connector that notifies of something potentially malicious that happens.
Conditions to trigger this automated action: Events that are the selected severity or higher, trigger the automated action.

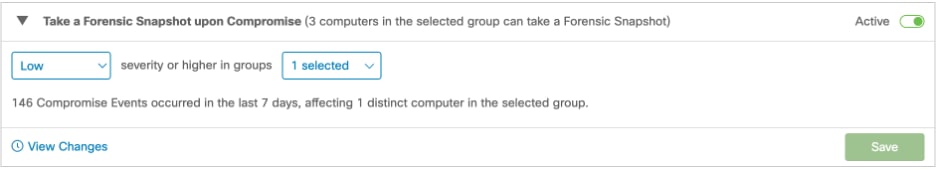
This is an example of a compromised machine:
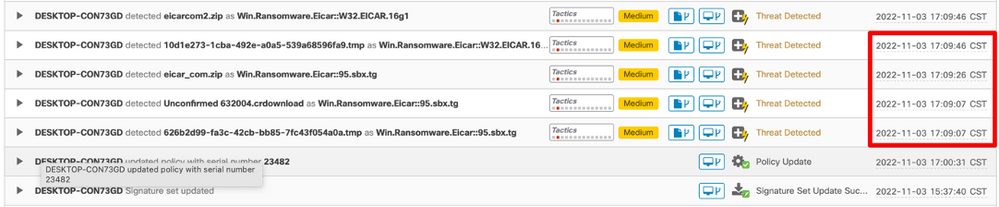
This is the Log of the automated action (from Audit Log tab)
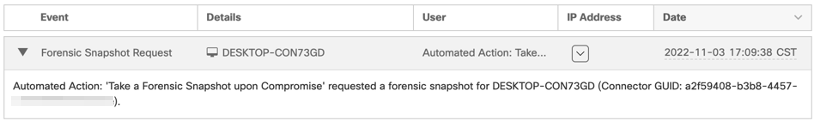
-
Isolate a computer upon compromise: Isolates computers when a compromise occurs.
Conditions to trigger this automated action: Events that are the selected severity or higher, trigger the automated action. The Rate Limit protects you against false positive detections. The Rate Limit feature looks at the total number of isolations in a 24 hour rolling window. If the number of isolations is greater than the limit, no further isolations are triggered. Computers are isolated again once the number of compromise events falls to fewer than the limit in the 24 hour rolling window or you stop isolation on computers that were automatically isolated.

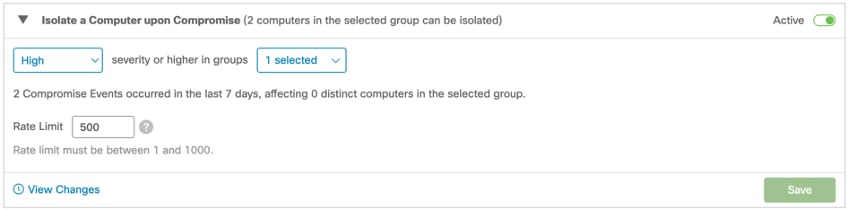
This is an example of a compromised machine:
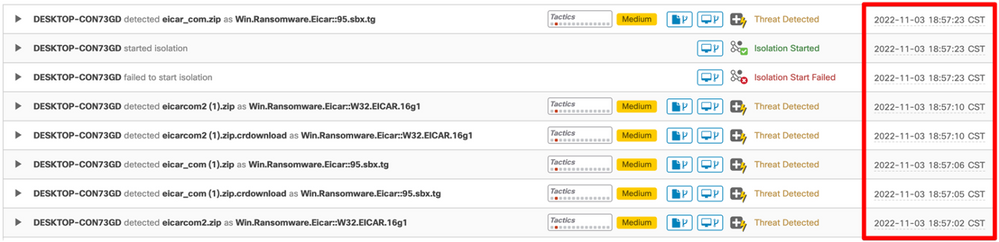
This is the Log of the automated action (from Audit Log tab):
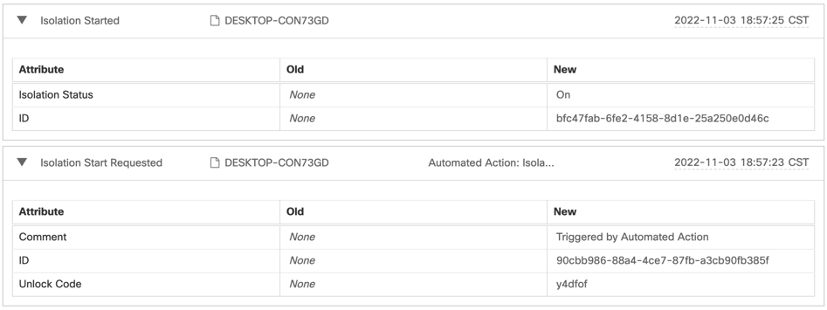
-
Submit to Secure Malware Analytics upon Detection: Submit a file to Secure Malware Analytics for File Analysis when a detection occurs.
Conditions to trigger this automated action: Events that are the selected severity or higher, trigger the automated action.

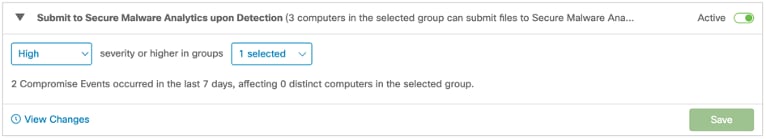
Example of a compromised machine:
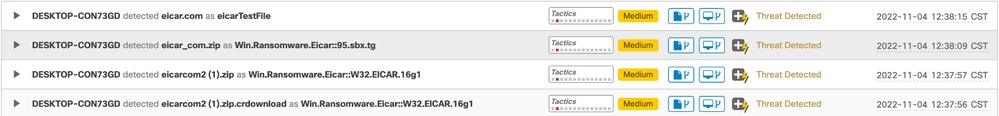
In this case, the file was submitted to Secure Malware analytics previously, so the file analysis was already done. Example as follows:
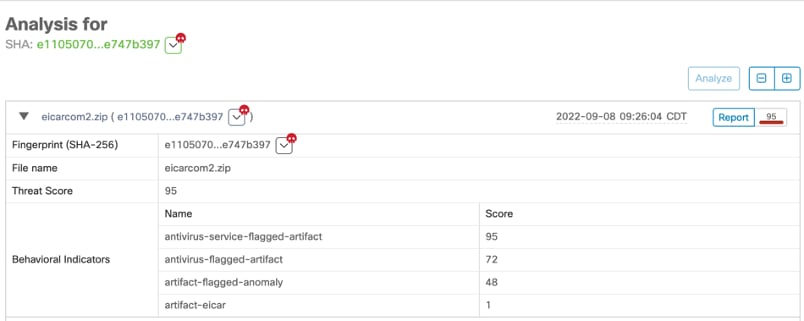

Note: This automated action is unaffiliated with compromises, and runs per-detection.
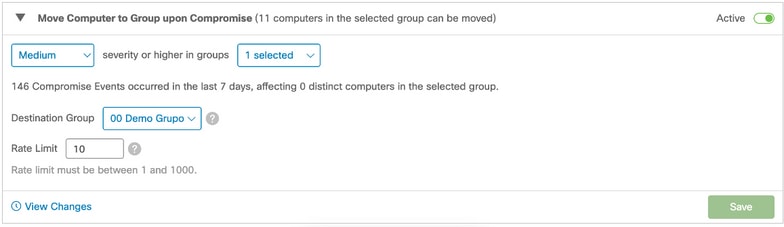
- Move Computer to group upon Compromise: Move computers from their current groups to another group when the action is triggered. This allows you to move compromised computers to a group with a policy that has more aggressive scanning and engine settings to remediate the compromise.
Conditions to trigger this automated action: Events that are the selected severity or higher, trigger the automated action.

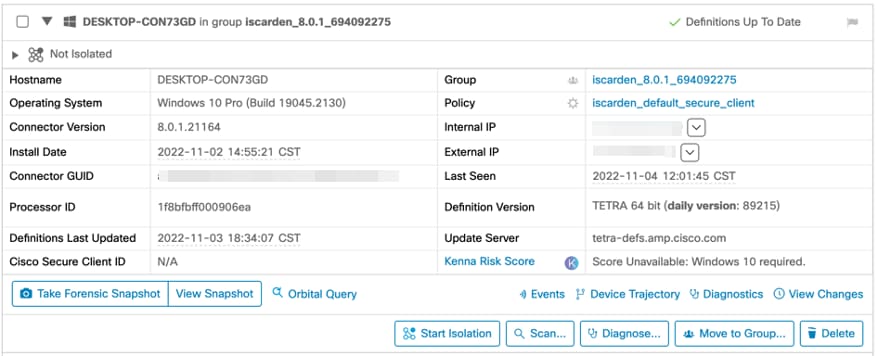
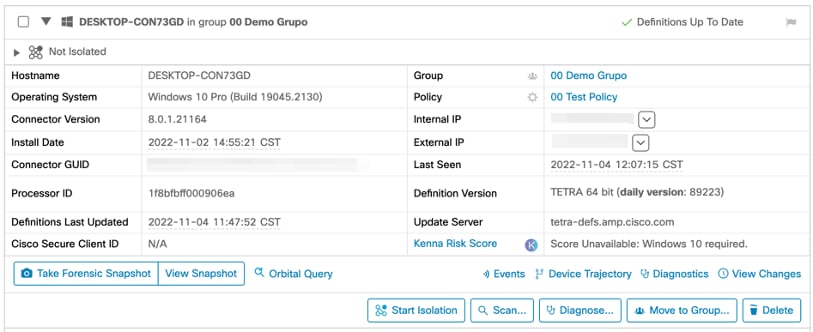
This is the computer in the original group:
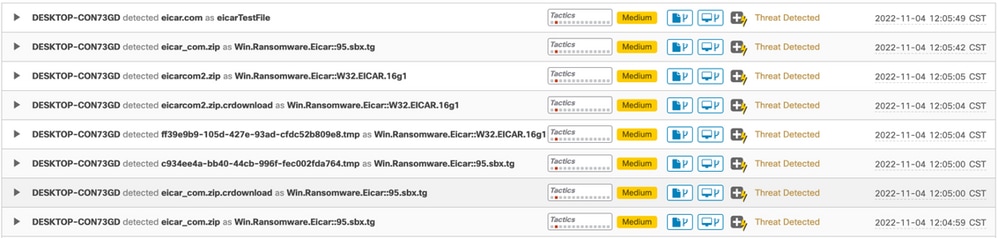
These are the events of compromise:
This is the Log of the automated action (from Audit Log tab):
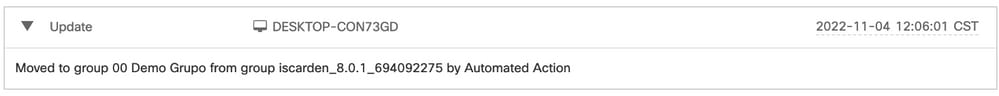
The computer was moved to specified group in the Automated Action setting:
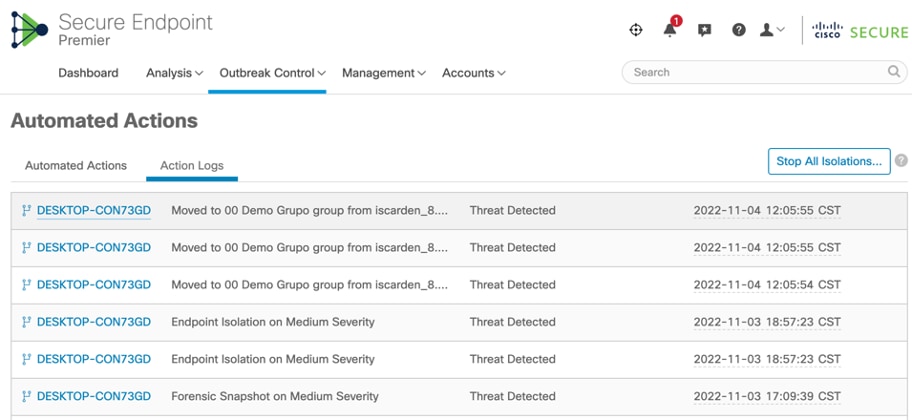
Action Logs
This is the full list of the Automated Action Logs from Automated Actions tab:
Related Information
Secure Endpoint User Guide





















 Feedback
Feedback