Introduction
This document describes issues caused by Microsoft Intune Attack surface reduction blocks using copied or impersonated system tools feature on systems managed by Microsoft Intune which in turn causes Secure Endpoint updates to fail.
Please refer to the feature documentation: https://learn.microsoft.com/en-us/defender-endpoint/attack-surface-reduction
Problem
We can experience issues with Secure Endpoint upgrades or installation which is represented by these errors and indicators.
There are various indicators that can be used to identify that this feature interfering with Secure Endpoint updates.
Indicator #1: During deployment, we going to notice this pop-up window at the end of the installation. Please note that the pop-up is fairly quick and there is no other recollection of any error once the installation is completed.
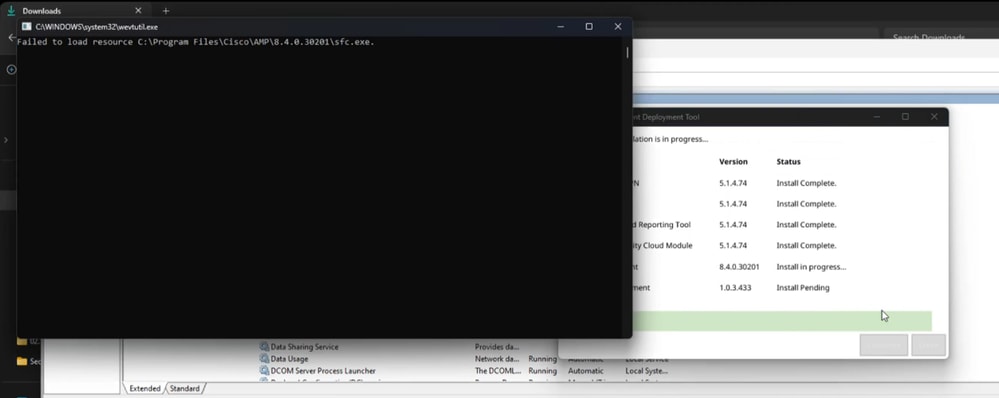
Indicator #2: After the installation, notice that Secure Endpoint is in disabled state in the UI.
Also, completely missing Secure Endpoint Service (sfc.exe) in the Task Manager -- > Services
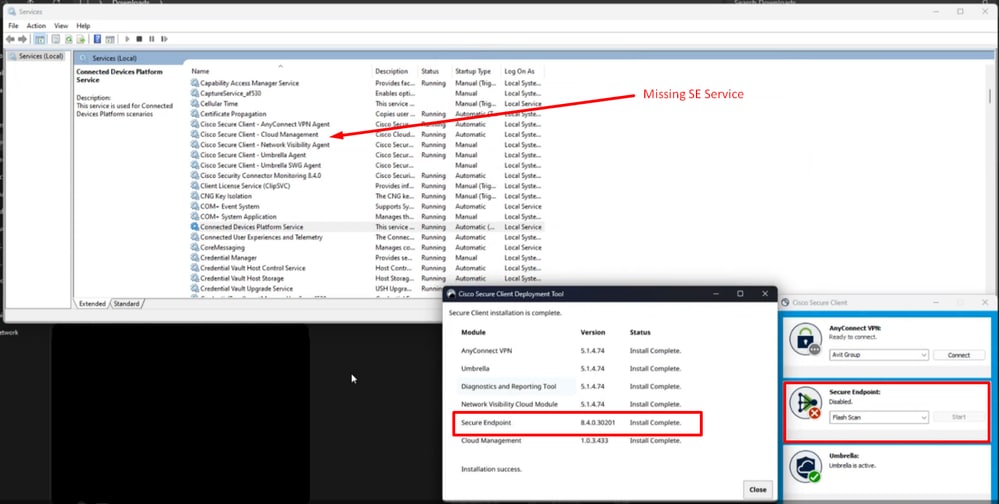
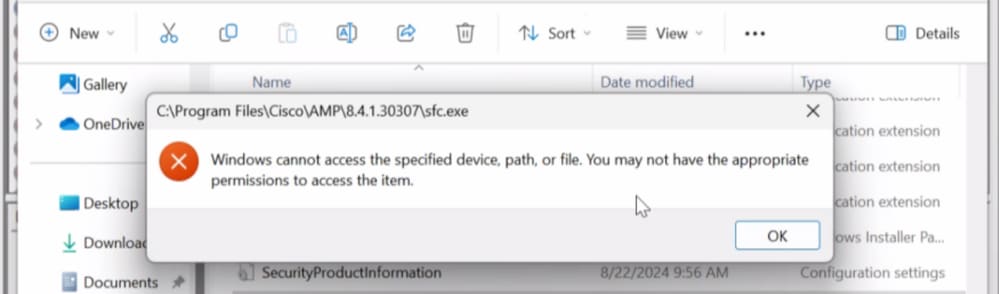
Indicator #3: If we navigate to the location of Cisco Secure Endpoint under C:\Program Files\Cisco\AMP\version and try to start the service manually, you get permission access denied even for the local admin account
Indicator #4: If we investigate immpro_install.log which is part of the diagnostic bundle we can observe a similar denial of access that look similar to this output.
Example #1:
(5090625, +0 ms) Aug 22 09:56:33 [17732]: ERROR: Util::GetFileSHA256: unable to generate file fp: C:\Program Files\Cisco\AMP\8.4.1.30307\sfc.exe, 0
(5090625, +0 ms) Aug 22 09:56:33 [17732]: ERROR: VerifyFile: Failed to grab hash of C:\Program Files\Cisco\AMP\8.4.1.30307\sfc.exe, aborting
(5090625, +0 ms) Aug 22 09:56:33 [17732]: ERROR: VerifyAllInstalledFiles: Failed to verify $AMP_INSTALL$\8.4.1.30307\sfc.exe
Example #2:
(1737859, +0 ms) Sept 11 14:04:05 [20180]: ERROR: imn_error: fp_gen_internal: failed to open file C:\Program Files\Cisco\AMP\8.4.1.30299\sfc.exe : 5 : Access is denied.
(1737859, +0 ms) Sept 11 14:04:05 [20180]: ERROR: Util::GetFileSHA256: unable to generate file fp: C:\Program Files\Cisco\AMP\8.4.1.30299\sfc.exe, 0
(1737859, +0 ms) Sept 11 14:04:05 [20180]: ERROR: VerifyFile: Failed to grab hash of C:\Program Files\Cisco\AMP\8.4.1.30299\sfc.exe, aborting
(1737859, +0 ms) Sept 11 14:04:05 [20180]: ERROR: VerifyAllInstalledFiles: Failed to verify $AMP_INSTALL$\8.4.1.30299\sfc.exe
Indicator #5: If we navigate under Windows Security and look in to the Protection History logs look for these type of log messages.
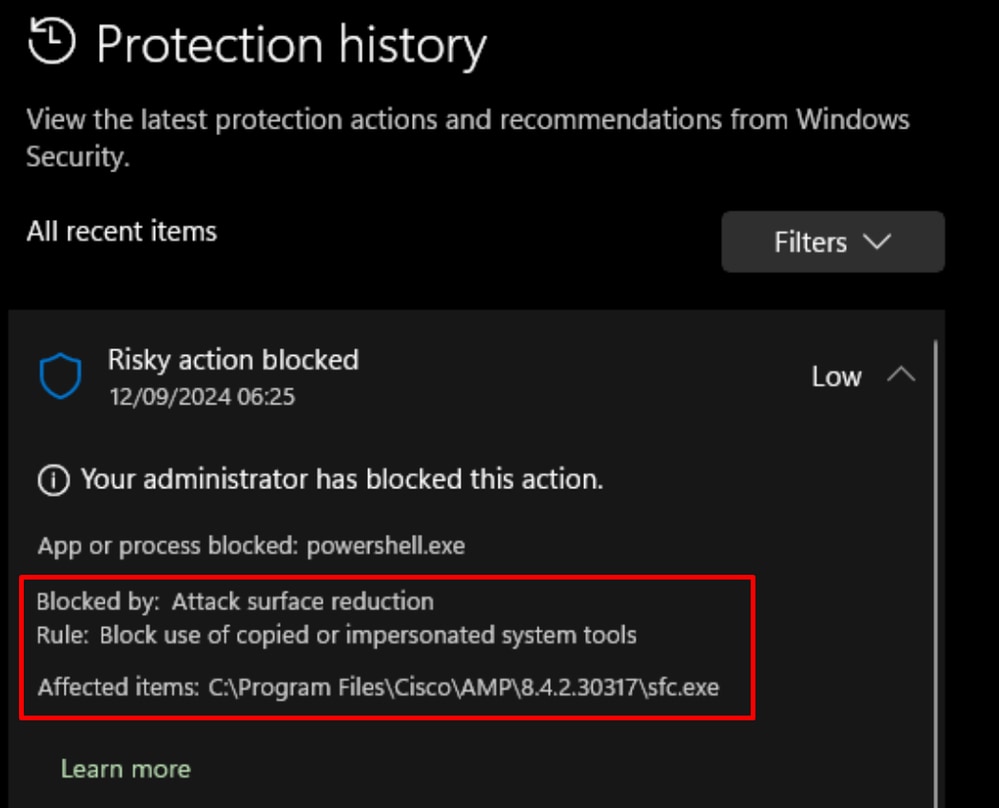
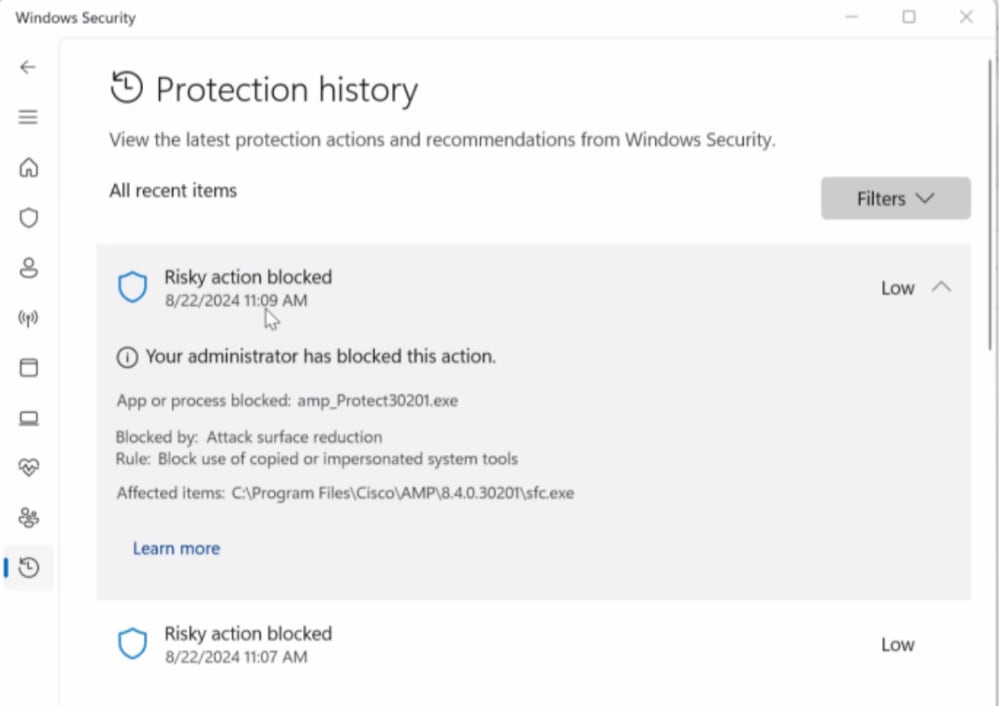
All these are indications that the Secure Endpoint is being blocked by 3rd party application. In this scenario, the issue was seen on Intune managed endpoints with either incorrectly configured or not configured Attack surface reduction - BLOCK use of copied or impersonated system feature.
Workaround
It is advised to consult configuration for this feature with the application developer or consult this feature further through this knowledge base.
For immediate remediation, we can either move our managed endpoint in intune to a less restrictive policy or temporary turn this feature explicitly off until proper steps are made.
This is the setting under Intune admin portal that was used as temporary measure to restore Secure Endpoint connectivity.
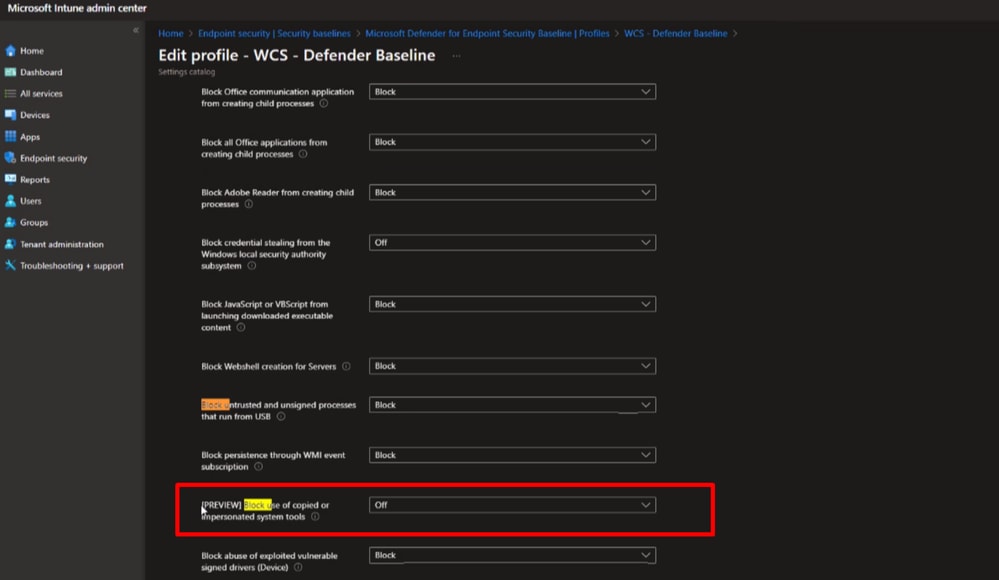

Caution: If you experience this issue, you must initiate full install due to missing sfc.exe








 Feedback
Feedback