Troubleshoot ASDM License, Upgrade and Compatibility Problems
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes the troubleshooting process for ASDM license, upgrade and compatibility problems.
Background
The document is part of the Adaptive Security Appliance Device Manager (ASDM) troubleshoot series along with these documents:
- Troubleshoot ASDM Launch Problems
- Troubleshoot ASDM Configuration, Authentication and Other Problems
- Troubleshoot ASDM TLS Security, Certificate and Vulnerability Problems
ASDM Upgrade Problems
Problem 1. How to upgrade ASA/ASDM upgrade from the source version X to the target version Y?
The user needs assistance with an ASA/ASDM upgrade from the source version X to the target version Y.
Troubleshoot – Recommended Actions
1. Ensure that the ASA, ASDM, operating system and Java versions are compatible with the target version. Refer to the Cisco Secure Firewall ASA Release Notes, Cisco Secure Firewall ASDM Release Notes, Cisco Secure Firewall ASA Compatibility.
The ASA, ASDM, operating system and Java versions must be compatible, and the target versions must be supported on specific hardware. https://www.cisco.com/c/en/us/td/docs/security/firepower/fxos/compatibility/fxos-compatibility.html
2. For ASA running on Firepower 4100/9300, ensure that the Firepower eXtensible Operating system (FXOS) and the ASA software versions are compatible. Refer to the Cisco Firepower 4100/9300 FXOS Compatibility.
3. Ensure to familiarize with the changes in the target version by checking the Cisco Secure Firewall ASA Release Notes, Cisco Secure Firewall ASDM Release Notes. In the case of Firepower 4100/9300, also familiarize with the changes in FXOS by checking the FXOS Release Notes.
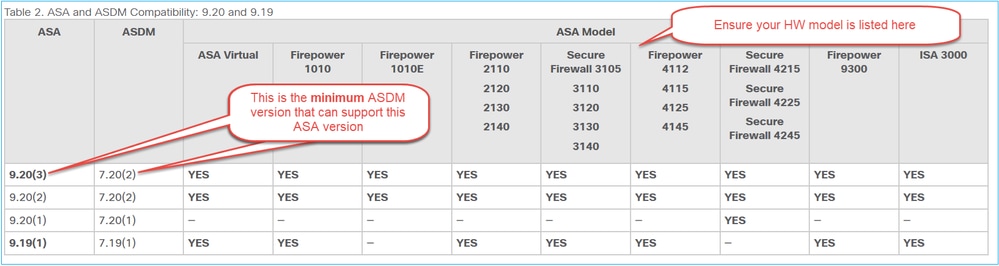
4. Ensure to check the upgrade path in the release notes. In this example, the Table 2 in the release notes for the version 7.22 contains the upgrade path from previous versions to the target version:
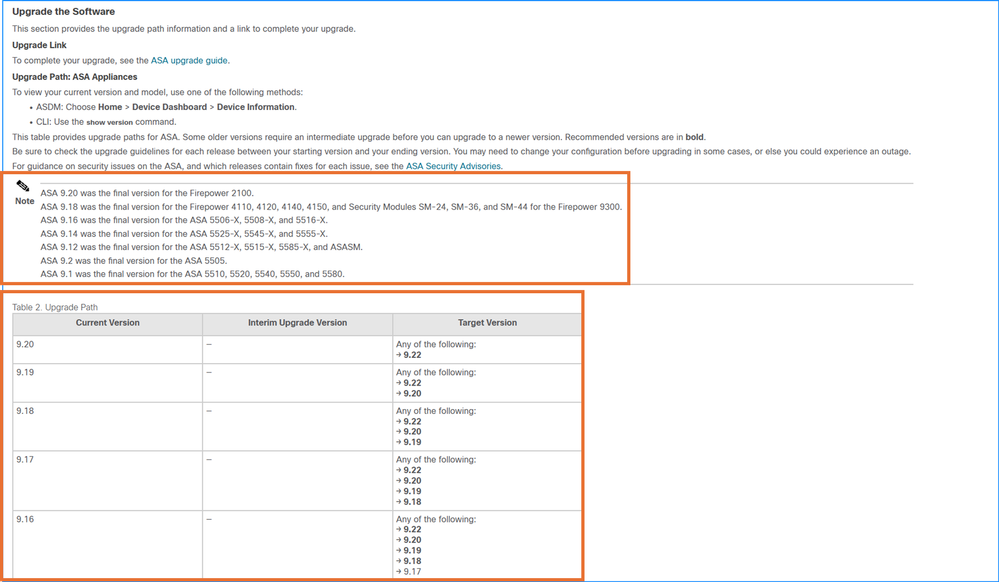
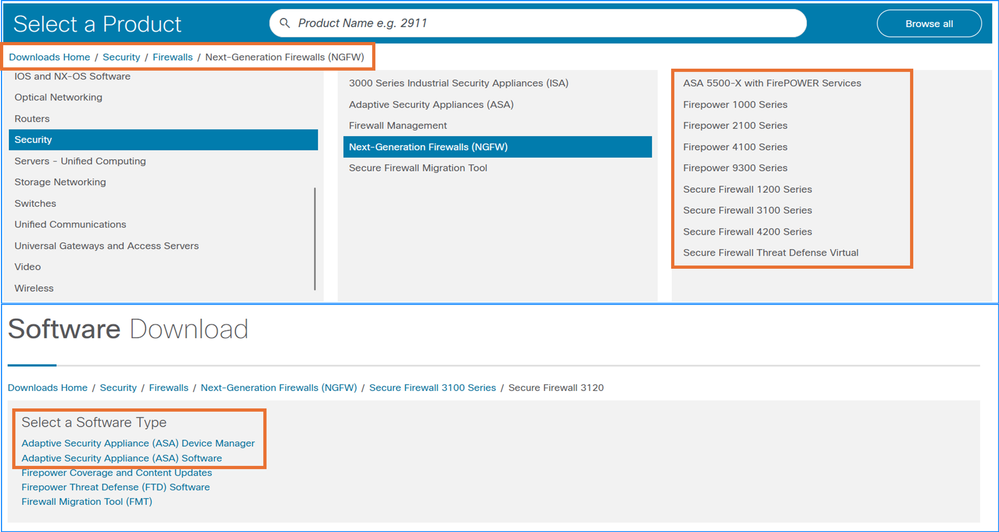
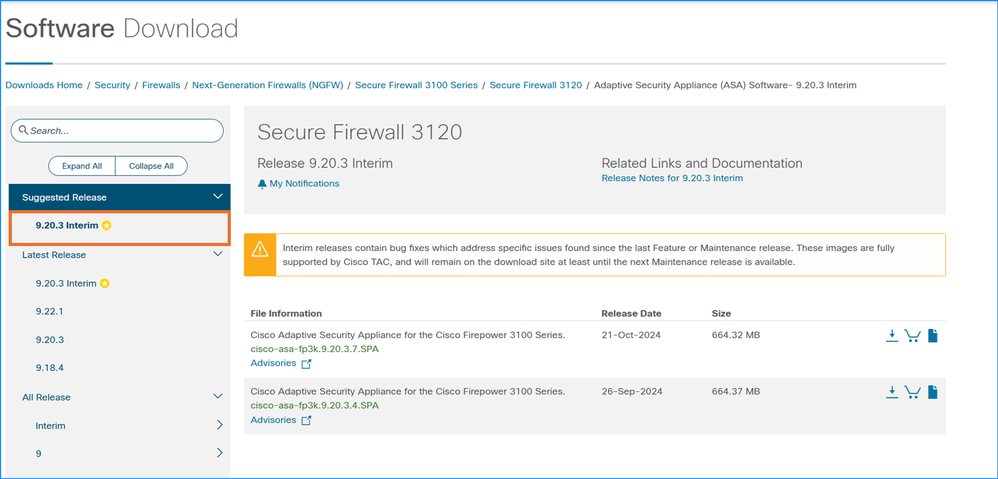
5. Once the compatibility requirements are satisfied, download the target ASA/ASDM and FXOS versions (Firepower 4100/9300 only) from the Software Download page. Ensure to select the specific hardware models as show in this example. The suggested releases are marked with a golden star:
6. Ensure to go through the Chapter: Planning Your Upgrade and the Chapter: Upgrade the ASA in the Cisco Secure Firewall ASA Upgrade Guide.
References
- Cisco Secure Firewall ASA Release Notes
- Cisco Secure Firewall ASDM Release Notes
- Cisco Secure Firewall ASA Compatibility
- Cisco Firepower 4100/9300 FXOS Compatibility
- Cisco Secure Firewall ASA Upgrade Guide
Problem 2. What are the recommended versions for ASA/ASDM?
The user asks about the recommended versions for ASA/ASDM.
Troubleshoot – Recommended Actions
The Cisco TAC does not provide recommendations about the software versions. Users can download the Cisco Suggested release based on software quality, stability and longevity. The suggested releases are marked with a golden star like shown below:
Problem 3. ASA/ASDM update check failure in ASDM via Tools > Check for ASA/ASDM Updates
The check for ASA/ASDM updates in ASDM via Tools > Check for ASA/ASDM Updates fails. Specifically, these symptoms are observed:
1. The Enter Network Password window re-appears after clicking the Login button even if the correct credentials are provided.
2. In the Java console logs the “Meta data request failed” error is shown:
2024-06-16 13:00:03,471 [ERROR] Error::Failed : Request processing
88887 [Thread-30] ERROR com.cisco.dmcommon.util.DMCommonEnv - Error::Failed : Request processing
2024-06-16 13:00:03,472 [ERROR] Error::Access token request processing failed
88888 [Thread-30] ERROR com.cisco.dmcommon.util.DMCommonEnv - Error::Access token request processing failed
2024-06-16 13:00:04,214 [ERROR] getMetaDataResponse :: Server returned HTTP response code: 403 for URL: https://api.cisco.com/software/v3.0/metadata/udi/PID%3A+ASA5525+VID%3A+V01+SN%3A+FOX1316G5R5/mdf_id/282867084/software_type_id/282885451/current_release/X
89630 [Thread-30] ERROR com.cisco.dmcommon.util.DMCommonEnv - getMetaDataResponse :: Server returned HTTP response code: 403 for URL: https://api.cisco.com/software/v3.0/metadata/udi/PID%3A+ASA5525+VID%3A+V01+SN%3A+FOX1316G5R5/mdf_id/282867084/software_type_id/282885451/current_release/X
2024-06-16 13:00:04,214 [ERROR] error::Meta data request failed.
89630 [Thread-30] ERROR com.cisco.dmcommon.util.DMCommonEnv - error::Meta data request failed.
Troubleshoot – Recommended Actions
Refer to the software Cisco bug ID CSCvf91260 “ASDM: Upgrade from CCO not working due to un-ignorable fields. "Meta data request failed”. The workaround is to download images directly from the download page and upload to the firewall.
Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
Problem 4. Which versions contain fixed for specific vulnerabilities?
The user asks about the fixed versions of specific vulnerabilities.
Troubleshoot – Recommended Actions
- Ensure to check the security advisory for the affected products.
- In the security advisory, provide the existing hardware and software version to the software checker and click Check:
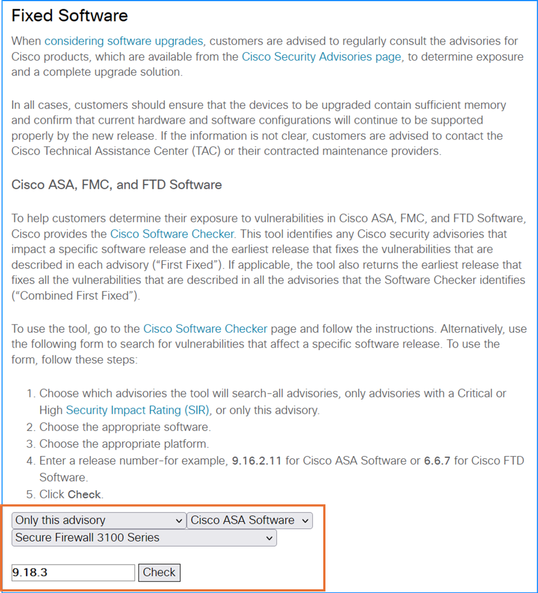
3. If the fixed version is available, note the versions in the FIRST FIXED OR NOT AFFECTED column:
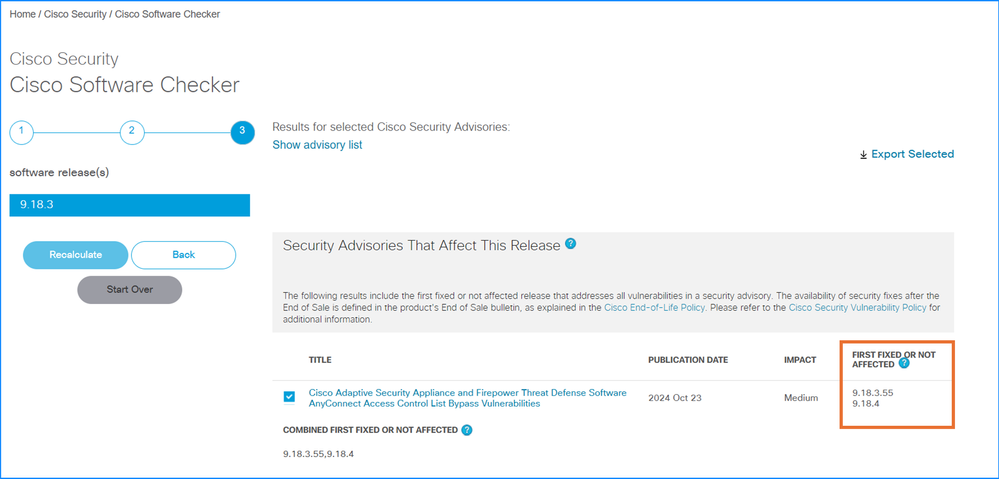
4. Go through the steps from the “Problem 1. How to upgrade ASA/ASDM upgrade from the source version X to the target version Y?” section to upgrade the software.
Problem 5. “% ERROR: ASDM package is not digitally signed. Rejecting configuration.” error message
The “% ERROR: ASDM package is not digitally signed. Rejecting configuration.” error message when a new ASDM image is set using the asdm image <image path> command.
Troubleshoot – Recommended Actions
1. The ASA validates whether the ASDM image is a Cisco digitally signed image. If you try to run an older ASDM image with an ASA version with this fix, ASDM is blocked and the message “%ERROR: Signature not valid for file disk0:/<filename>” is displayed at the ASA CLI. ASDM release 7.18(1.152) and later are backwards compatible with all ASA versions, even those without this fix. Refer to the Important Notes section in Release Notes for Cisco ASDM, 7.17(x).
2. For ASA running on the Secure Firewall 3100, check the software Cisco bug ID CSCwc12322 “Digitally signed ASDM image verification error on FPR3100 platforms”.
Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
References
Problem 6. Unable to check for ASA/ASDM Updates in multiple context mode
The Tools > Check for ASA/ASDM Updates option is greyed out in multiple context mode:
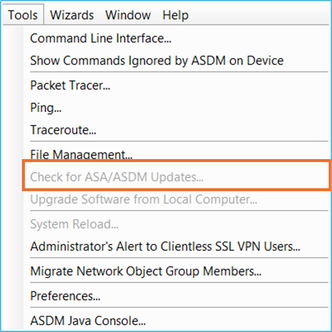
Troubleshoot – Recommended Actions
Usually, this option is greyed out because in the Device List tab the current select context is the admin context:
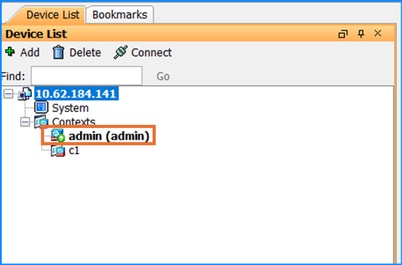
In this case, ensure to switch to the system context by double clicking on the System icon:
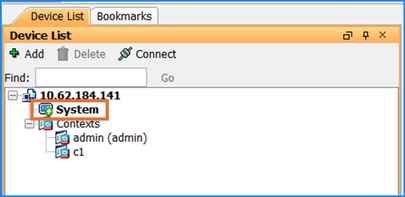
Problem 7. “Cisco's General Terms form have not been accepted or rejected to continue to download.” error message
The "Cisco's General Terms form have not been accepted or rejected to continue to download." error message is shown when the user tries to update the ASA/ASDM images via the Tools > Check for ASA/ASDM Updates menu.
Troubleshoot – Recommended Actions
This error message is shown if the end-user license agreement (EULA) is not accepted by the user. To continue, ensure to accept the EULA.
References
Problem 8. Unable to download software for specific hardware
The Software Download page does not show some ASA/ASDM software versions for specific hardware.
Troubleshoot – Recommended Actions
The availability of software for specific hardware mainly depends on the compatibility and the End-of-Life (EoL) milestones. In the case of incompatibility, EoL products or release deferrals, the software versions are usually not available for download.
Ensure to go through these steps to verify the compatibility and supported versions:
- Check the compatibility between software and hardware versions. Refer to the Cisco Secure Firewall ASA Compatibility.
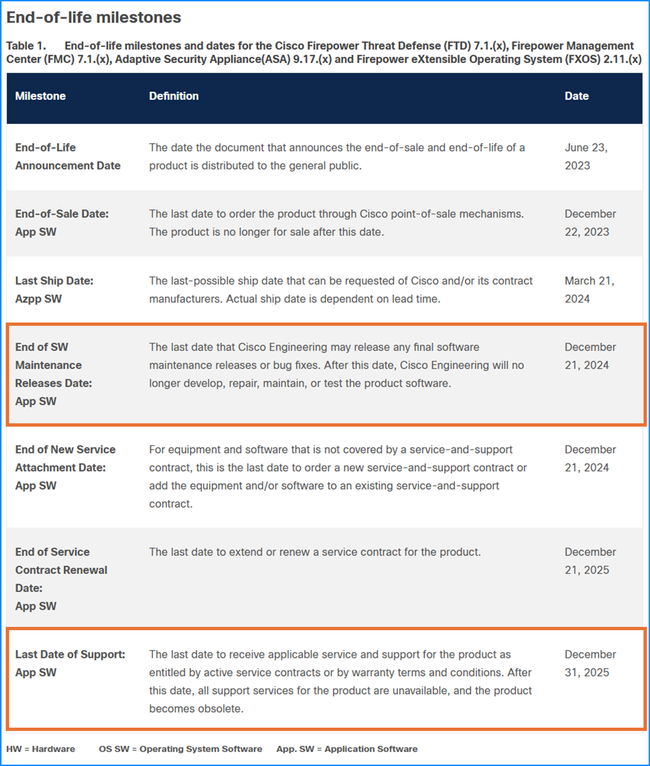
- Check the End of SW Maintenance Releases Date and the Last Date of Support in the End-of-Life and End-of-Sale Notices
- End of SW Maintenance Releases Date - The last date that Cisco Engineering can release any final software maintenance releases or bug fixes. After this date, Cisco Engineering no longer develops, repairs, maintains, or tests the product software.
- Last Date of Support - The last date to receive applicable service and support for the product as entitled by active service contracts or by warranty terms and conditions. After this date, all support services for the product are unavailable, and the product becomes obsolete.
3. Check Cisco Secure Firewall ASA Release Notes and Cisco Secure Firewall ASDM Release Notes for deferral or removal of release.
References
- Cisco Secure Firewall ASA Compatibility
- End-of-Life and End-of-Sale Notices
- Cisco Secure Firewall ASA Release Notes
- Cisco Secure Firewall ASDM Release Notes
Problem 9. “Error occurred in performing File Transfer HTTP Response code -1” error message
The “Error occurred in performing File Transfer HTTP Response code -1” error message is shown when the user uploads a file to the firewall using the ASDM Tools > File Management option.
Troubleshoot – Recommended Actions
Refer to the software Cisco bug ID CSCvf85831 “ASDM error "Error occurred in performing File Transfer HTTP Response code -1" during image upload”.
ASDM Compatibility Problems
This section covers the most common ASDM compatibility-related problems.
In general, ASDM must be compatible with these components:
- ASA
- Java
- Operating System (OS)
- Browser
- SFR module (if it is used)
Thus, before installing or upgrading ASDM, it is highly recommended to always check first this table:
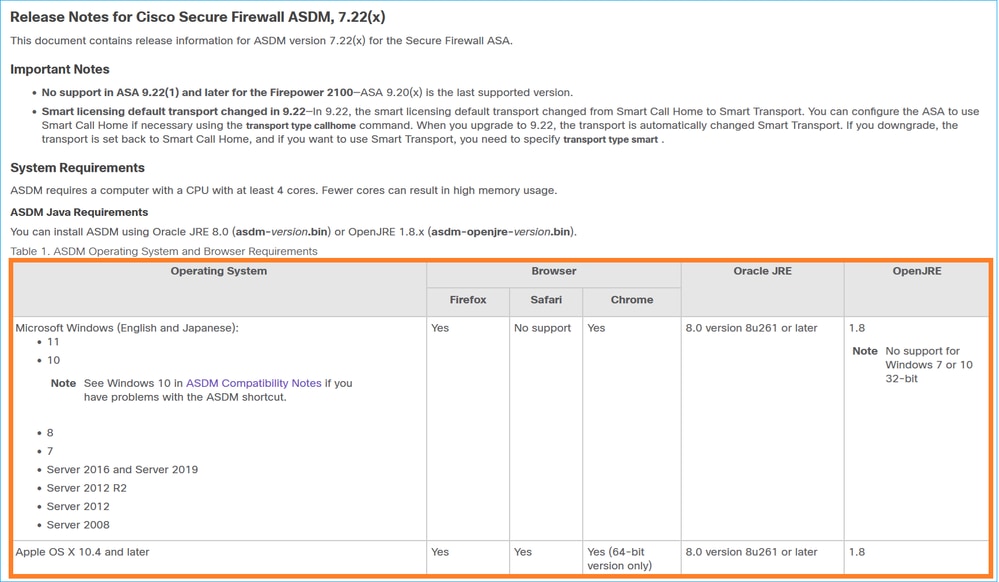
And then the ASA and ASDM Compatibility Per Model table, for example:
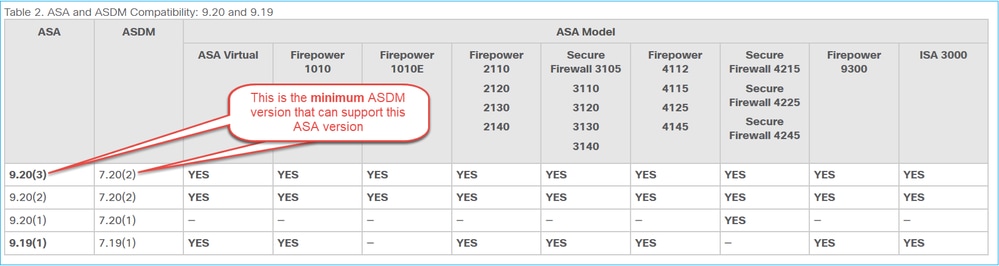
Notes:
New ASA versions require the coordinating ASDM version or a later version; you cannot use an old version of ASDM with a new version of ASA.
Example 1
You cannot use ASDM 7.17 with ASA 9.18. For ASA interims, you can continue to use the current ASDM version, unless otherwise stated. For example, you can use ASA 9.22(1.2) with ASDM 7.22(1).
Example 2
You have ASAS 9.8(4)32. You can use ASDM 7.19(1) to manage it since ASDM is backward compatible unless otherwise mentioned in the ASDM release notes.
References
- https://www.cisco.com/c/en/us/td/docs/security/asdm/7_22/release/notes/rn722.html#id_25469
- https://www.cisco.com/c/en/us/td/docs/security/asa/compatibility/asamatrx.html#id_65776
Problem 1. Incompatible Java version
Troubleshoot – Recommended Steps
Check the Java console logs:
Then check the Java and ASA compatibility guides:
- https://www.cisco.com/c/en/us/td/docs/security/asdm/7_22/release/notes/rn722.html#id_25469
- https://www.cisco.com/c/en/us/td/docs/security/asa/compatibility/asamatrx.html#id_65776
Problem 2. Incompatible ASA and ASDM version
If you run into incompatible ASA and ASDM versions you can lose access to ASDM UI.
Troubleshoot – Recommended Steps
You need to install the ASDM version from the CLI of the device, copy the image into the flash of the ASA via TFTP, and set the ASDM image using the command "asdm image" as explained in the guide below:
Example
asa# copy tftp flash
Address or name of remote host []? 10.62.146.125
Source filename []? asdm-7221.bin
Destination filename [asdm-7221.bin]?
Verifying file disk0:/asdm-7221.bin...
Writing file disk0:/asdm-7221.bin...
INFO: No digital signature found
126659176 bytes copied in 70.590 secs (1809416 bytes/sec)
asa# config terminal
asa(config)# asdm image disk0:/asdm-7151-150.bin
asa(config)# copy run start
Source filename [running-config]?
Cryptochecksum: afae0454 bf24b2ac 1126e026 b1a26a2c
4303 bytes copied in 0.210 secs
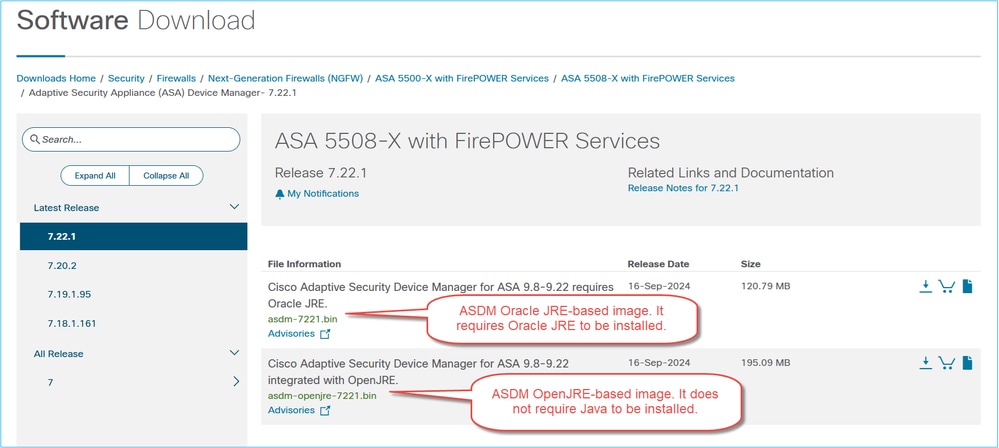
Problem 3. ASDM and OpenJDK Support
Cisco ASDM image does not support OpenJDK officially. Thus, there are 2 available options:
- Oracle JRE: Contains the Java Web Start runtime to launch ASDM on the host PC. To use this method you need the 64-bit Oracle JRE to be installed on the local PC. You can download this at the official website of Java.
- OpenJRE: The open JRE image is the same as the Oracle one, but the difference is that you don’t need to install the 64-bit Oracle JRE on the local PC since the image itself has the Java Web Start feature to launch the ASDM. This is the reason why the size of the OpenJRE image is greater than the Oracle JRE. Note that it is expected to see the OpenJRE using a bit older Java release, as they are compiled with the latest stable version available at the beginning of the ASDM openJRE development cycle.
Oracle JRE vs OpenJRE
|
Oracle JRE |
OpenJRE |
|
|
Requires Java to be installed on the end host |
Yes |
No (it has its own Java integrated) |
|
Proprietary |
Yes |
No (open source) |
|
Image size |
Medium |
Bigger since it also has Java integrated |
|
Image name |
asdm-xxxx.bin |
asdm-openjre-xxxx.bin |
Tip: If you decide to change the ASDM launcher version, first uninstall the existing ASDM launcher and then install the new by connecting to the ASA via HTTPS.
References
- https://www.cisco.com/c/en/us/td/docs/security/asdm/7_22/release/notes/rn722.html#id_25472
- OpenJDK: Full development and runtime environment, open-source, GPL license.
- Oracle JRE: Runtime environment only, proprietary license, requires a commercial license for production use.
- OpenJRE: Runtime environment only, open-source, GPL license.
- https://www.oracle.com/java/technologies/javase/jre8-readme.html
Problem 4. ASDM and Java Azul Zulu Compatibility
Oracle JRE-based ASDM images do not support Java Azul Zulu. On the other hand, ASDM OpenJRE-based images come Azul Zulu integration. Check ‘Problem 3’ recommendations for the available options.
Problem 5. WARNING: Signature not found in file disk0:/asdm-xxx.bin
Example:
asa# copy tftp flash:
Address or name of remote host [192.0.2.5]?
Source filename []? asdm-7171.bin
Destination filename [asdm-7171.bin]?
Accessing ftp://192.0.2.5/asdm-7171.bin...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Verifying file disk0:/asdm-7171.bin...
%WARNING: Signature not found in file disk0:/asdm-7171.bin.
Troubleshoot – Recommended Steps
This is typically an ASA vs ASDM compatibility problem. Check the ASDM compatibility guide and ensure your ASDM is compatible with the ASA image. You can find the ASA and ASDM compatibility matrix at:
https://www.cisco.com/c/en/us/td/docs/security/asa/compatibility/asamatrx.html#id_65776
Problem 6. “% ERROR: ASDM package is not digitally signed. Rejecting configuration.”
This error message can be shown when a new ASDM image is set using the asdm image <image path> command.
Troubleshoot – Recommended Actions
- The ASA validates whether the ASDM image is a Cisco digitally signed image. If you try to run an older ASDM image with an ASA version with this fix, ASDM is blocked and the message “%ERROR: Signature not valid for file disk0:/<filename>” is displayed at the ASA CLI. ASDM release 7.18(1.152) and later are backwards compatible with all ASA versions, even those without this fix. Refer to the Important Notes section in Release Notes for Cisco ASDM, 7.17(x).
- Update the Java version on your host PC.
- For ASA running on the Secure Firewall 3100, check the software Cisco bug ID CSCwc12322 “Digitally signed ASDM image verification error on FPR3100 platforms”
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwc12322
Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
Problem 7. “%ERROR: Signature not valid for file disk0:/<filename>”
The error is shown during the file copy, for example:
asa# copy tftp://cisco:cisco@192.0.2.1/cisco-asa-fp2k.9.20.3.7.SPA
Address or name of remote host [192.0.2.1]?
Source filename [cisco-asa-fp2k.9.20.3.7.SPA]?
Destination filename [cisco-asa-fp2k.9.20.3.7.SPA]?
Accessing tftp://cisco:<password>@192.0.2.1/cisco-asa-fp2k.9.20.3.7.SPA...
!!!!!!!!!!!!!!!!!!!...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Verifying file disk0:/cisco-asa-fp2k.9.20.3.7.SPA...
%ERROR: Signature not valid for file disk0:/cisco-asa-fp2k.9.20.3.7.SPA.
Troubleshoot – Recommended Actions
ASA 9.14(4.14) and later requires ASDM 7.18(1.152) or later. The ASA now validates whether the ASDM image is a Cisco digitally signed image. If you try to run an older ASDM image than 7.18(1.152) with an ASA version with this fix, ASDM is blocked and the message “%ERROR: Signature not valid for file disk0:/<filename>” is displayed at the ASA CLI.
This change was introduced due to Cisco ASDM and ASA Software Client-side Arbitrary Code Execution Vulnerability (CVE ID CVE-2022-20829)
- https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwb05291
- https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwb05264
In case the device operates in Platform Mode go through the instructions from this document to upload the image: https://www.cisco.com/c/en/us/td/docs/security/asa/upgrade/asa-upgrade/asa-appliance-asav.html#topic_zp4_dzj_cjb
References
- ASDM release notes: https://www.cisco.com/c/en/us/td/docs/security/asdm/7_14/release/notes/rn714.html#reference_yw3_ngz_vhb
- ASA upgrade guide: https://www.cisco.com/c/en/us/td/docs/security/asa/upgrade/asa-upgrade/asa-appliance-asav.html#task_E9EE51964590499999B1D976F66E2771
Problem 8. Secure Firewall Posture (Hostscan) Compatibility
Hostscan version depends more on AnyConnect version than ASA version. You can find both the versions here: Software Download - Cisco Systems:
https://software.cisco.com/download/home/283000185
Problem 9. Latest supported version
Troubleshoot – Recommended Actions
If you want to know the latest supported ASDM version for your firewall there are mainly two documents to check:
- ASDM release notes: https://www.cisco.com/c/en/us/td/docs/security/asdm/7_14/release/notes/rn714.html#reference_yw3_ngz_vhb
Specifically, the ASA Model table
The second document is the SW download page:
https://software.cisco.com/download/home/286291275
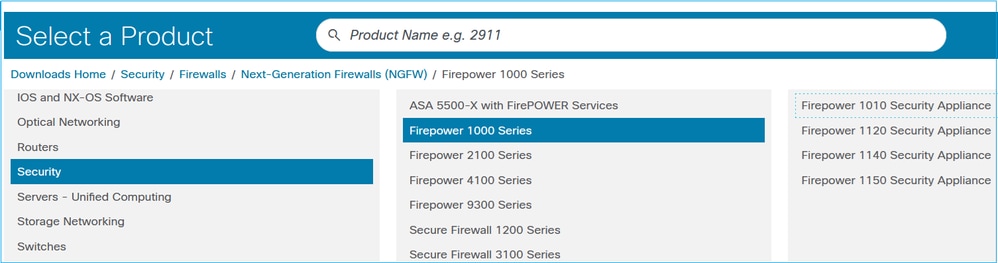
You can find the latest ASDM versions per SW train supported by your HW, for example:
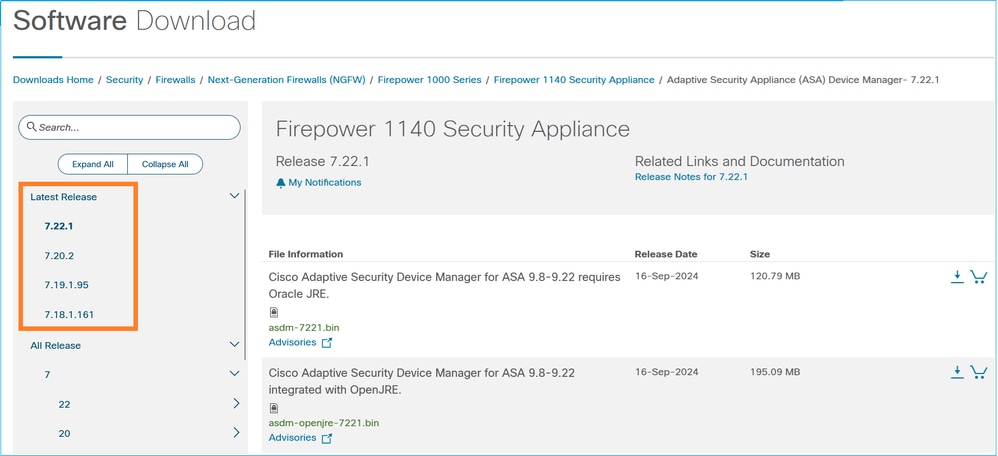
Problem 10. ASDM support on Linux
Troubleshoot – Recommended Actions
Linux is not officially supported.
Related enhancement:
Cisco bug ID CSCwk67345  ENH: Include Linux in the list of supported OSs
ENH: Include Linux in the list of supported OSs
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwk67345
Problem 11. ASDM end of support
Troubleshoot – Recommended Actions
Consult the ASA/ASDM End-of-Life and End-of-Sale Notices:
https://www.cisco.com/c/en/us/products/security/asa-firepower-services/eos-eol-notice-listing.html
ASDM License Problems
This section covers the most common ASDM license-related problems.
Smart Licensing model is used by:
- Firepower 4100/9300 chassis registration: License Management for the ASA
- ASAv, Firepower 1000, Firepower 2100, Firepower 9300, and Firepower 4100: Licenses: Smart Software Licensing (ASAv, ASA on Firepower)
All other models use Product Authorization Key (PAK) Licensing
References
- Cisco Secure Firewall ASA Series Feature Licenses - Model Guidelines
https://www.cisco.com/c/en/us/td/docs/security/asa/roadmap/licenseroadmap.html
Problem 1. 3DES/AES Smart License is Missing
ASDM requires Strong Encryption license (3DES/AES) on ASA unless you access it using the management interface. In order to enable ASDM access over a data interface you need to get the 3DES/AES license.
To request a 3DES/AES license from Cisco:
- Go to https://www.cisco.com/go/license
- Click Continue to Product License Registration.
- In the Licensing Portal, click Get Other Licenses next to the text field.
- Choose IPS, Crypto, Other... from the drop-down list.
- Type ASA in to the Search by Keyword field.
- Select Cisco ASA 3DES/AES License in the Product list, and click Next.
- Enter the serial number of the ASA, and go through the prompts to request a 3DES/AES license for the ASA.
Troubleshoot – Recommended Actions
To enable the license and register to the Cisco Smart Licensing portal, ensure that these items are in place:
- The ASA clock shows the correct time. The recommendation is to use an NTP server.
- Routing towards the Cisco Smart Licensing portal.
- HTTPS traffic is not blocked from the firewall to the licensing portal. A capture collection on the firewall can confirm this.
- If there is a need to use an HTTP proxy server include the necessary command, for example:
ciscoasa(config)# call-home
ciscoasa(cfg-call-home)# http-proxy 10.1.1.1 port 443
Problem 2. Oracle Java JRE Licensing Requirements
Troubleshoot – Recommended Actions
ASDM .bin image file comes in two flavors:
- Oracle JRE: Contains the Java Web Start runtime to launch ASDM on the host PC. To use this method you need the 64-bit Oracle JRE to be installed on the local PC. You can download this at the official website of Java.
- OpenJRE: The open JRE image is the same as the Oracle one, but the difference is that you don’t need to install the 64-bit Oracle JRE on the local PC since the image itself has the Java Web Start feature to launch the ASDM.
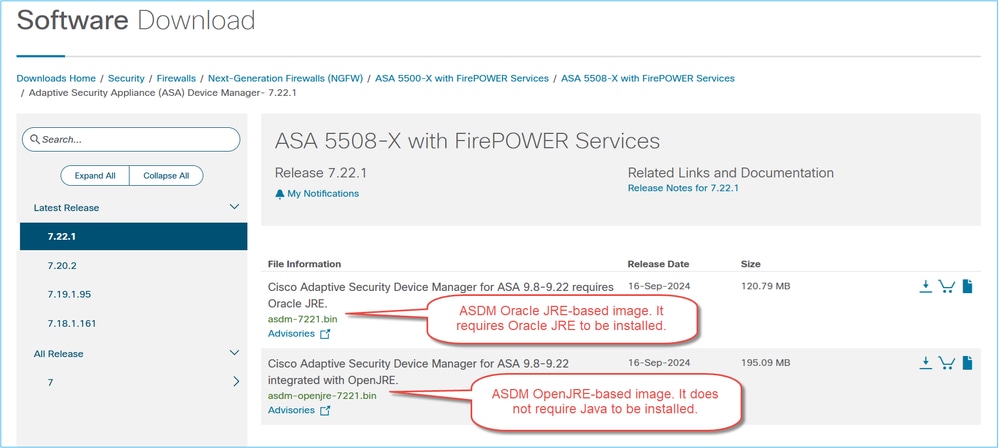
In case you decide to use the Oracle-based ASDM image, you need to have a Java license when you use it for non-Personal uses. Per Oracle Java SE Licensing FAQ:
Personal use is using Java on a desktop or laptop computer to do things such as to play games or run other personal applications. If you are using Java on a desktop or laptop computer as part of any business operations, that is not personal use. For example, you could use a Java productivity application to do your own homework or your personal taxes, but you could not use it to do your business accounting.
If you don’t want to apply any Java licenses you can use the OpenJRE-based ASDM image.
References
- https://www.oracle.com/java/technologies/javase/jdk-faqs.html
- ASDM Java Requirements for ASDM 7.22: https://www.cisco.com/c/en/us/td/docs/security/asdm/7_22/release/notes/rn722.html#id_25472
- ASDM Compatibility Notes for ASDM 7.22: https://www.cisco.com/c/en/us/td/docs/security/asdm/7_22/release/notes/rn722.html#id_25476
Note: Check the release notes for the ASDM version you use.
Problem 3. ASDM Warning about site-to-site VPN License in Multi-Context Mode
The ASDM displays this:
WARNING: There is no site-to-site VPN license allocated to this context. Please go to Security Context Management to allocate VPN license to this context.
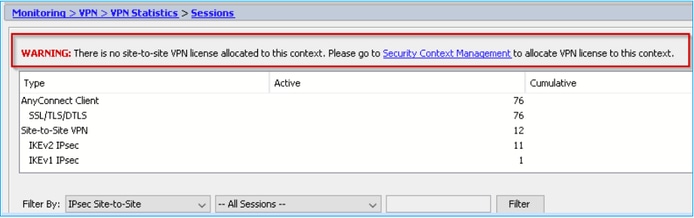
Troubleshoot – Recommended Actions
This is a cosmetic software defect tracked by:
Cisco bug ID CSCvj66962  ASDM 7.9(2) ASA 9.6(4)8 multi context L2L persistent error
ASDM 7.9(2) ASA 9.6(4)8 multi context L2L persistent error
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvj66962
You can subscribe to the defect, so you receive a notification on defect updates.
References
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
2.0 |
29-Nov-2024 |
Initial Release |
1.0 |
29-Nov-2024 |
Initial Release |
Contributed by Cisco Engineers
- Mikis ZafeiroudisCisco TAC Engineer
- Ilkin GasimovCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback