Troubleshoot ASDM Launch Problems
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes the troubleshooting process for Adaptive Security Appliance Device Manager (ASDM) launch problems.
Background
The document is part of the ASDM troubleshoot series along with these documents:
- Troubleshoot ASDM Configuration, Authentication and Other Problems
- Troubleshoot ASDM License, Upgrade and Compatibility Problems
- Troubleshoot ASDM TLS Security, Certificate and Vulnerability Problems
Troubleshoot ASDM Launch Problems
Problem 1. “Unable to launch device manager from” message is shown on ASDM
One or more of these symptoms are observed when attempting to connected to the firewall using ASDM:
- The error “Unable to launch device manager from” message is shown on ASDM:
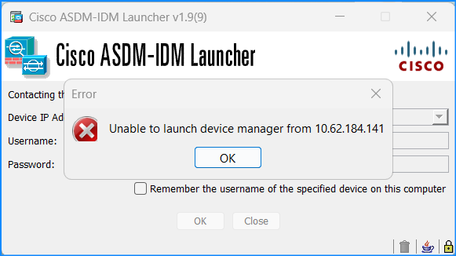
- The Java debug logs show one of the these exceptions:
java.net.ConnectException: Connection timed out: connect
at java.net.DualStackPlainSocketImpl.waitForConnect(Native Method)
java.net.ConnectException: Connection refused: connect
at java.net.DualStackPlainSocketImpl.waitForConnect(Native Method)
Trying for ASDM Version file; url = https://192.0.2.1/admin/
java.io.FileNotFoundException: https://192.0.2.1/admin/version.prop
java.net.SocketException: Connection reset
at java.net.SocketInputStream.read(Unknown Source)
at java.net.SocketInputStream.read(Unknown Source)
at sun.security.ssl.SSLSocketInputRecord.read(Unknown Source)
To verify this symptom, enable Java console logs:
Troubleshoot – Recommended Actions
- Ensure that the ASA, ASDM and operating system versions are compatible. Refer to the Cisco Secure Firewall ASA Release Notes, Cisco Secure Firewall ASDM Release Notes, Cisco Secure Firewall ASA Compatibility.
- On the ASDM-hosted operating system (OS), ensure that the OS firewall and other security software allow packets of ASDM connections in both (ingress and egress) directions.
- On the ASDM-hosted operating system (OS), ensure that the security software (for example, antivirus) and security policies, allow running the ASDM and Java software.
- Ensure HTTP server is enabled, and correct hosts/interfaces are configured:
# show run http
http server enable
http 192.0.2.0 255.255.255.0 management
The http server enable command can disappear from the running configuration due to Cisco bug ID CSCwc67687 "ASA HA failover triggers HTTP server restart failure and ASDM outage".

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
- Ensure the ASDM image is available on the local flash and configured:
# dir flash:
Directory of disk0:/
150 drwx 4096 05:55:01 Nov 14 2024 log
1074037795 -rw- 123665740 23:30:37 Oct 17 2024 asdm.bin
# show run asdm
asdm image disk0:/asdm.bin
no asdm history enable
- Ensure that the 3DES/AES licenses are available, if you are connecting to the ASA via the data interface:
# show ver | grep Encryption
Encryption hardware device : Cisco ASA Crypto on-board accelerator (revision 0x1)
Encryption-DES : Enabled
Encryption-3DES-AES : Enabled
- If WebVPN is enabled on the same interface, ensure different ports are configured for WebVPN and ASDM. Either change the WebVPN port or change the HTTPS server port.
In this example, both WebVPN and ASDM access are configured. The WebVPN service is running on the default HTTPS port 443, and the HTTPS port for ASDM is configured as 8443:
# show run webvpn
webvpn
enable outside <-- default HTTPS port 443
# show run http
http server enable 8443 <-- custom HTTPS port 8443
http 192.0.2.0 255.255.255.0 outside
- Ensure that connections from the host with ASDM and the firewall is allowed by intermediary devices in the network.
Potential problems:
- Incorrect routing
- Incorrect NAT/port forwarding
- Traffic is blocked in the transit path
From the firewall perspective, to confirm connectivity you can configure packet captures on specific interfaces:
# show run http
http server enable
http 192.0.2.0 255.255.255.0 management
# cap capm interface management match tcp any any eq https
# show capture capm
138 packets captured
1: 14:20:44.355526 192.0.2.35.50590 > 198.51.100.141.443: S 3649403547:3649403547(0) win 64240 <mss 1300,nop,wscale 8,nop,nop,sackOK>
2: 14:20:44.356152 198.51.100.141.443 > 192.0.2.35.50590: S 0:0(0) ack 3649403548 win 32768 <mss 1300>
3: 14:20:44.357388 192.0.2.35.50590 > 198.51.100.141.443: . ack 1 win 64240
4: 14:20:44.384715 192.0.2.35.50590 > 198.51.100.141.443: P 3649403548:3649403918(370) ack 1 win 32768
5: 14:20:44.384806 198.51.100.141.443 > 192.0.2.35.50590: . ack 3649403918 win 32398
6: 14:20:44.385829 198.51.100.141.443 > 192.0.2.35.50590: P 1:760(759) ack 3649403918 win 32768
- Ensure the ASDM current resource usage does not exceed the limit:
# show resource usage resource ASDM
Resource Current Peak Limit Denied Context
ASDM 1 1 5 0 admin
Use the show conn all protocol tcp port <port> command to check the list of active ASDM connections. Ensure to provide the correct port that the HTTP server servers on (show run http).
# show conn all protocol tcp port 443
2 in use, 8 most used
TCP management 192.0.2.35:50620 NP Identity Ifc 198.51.100.141:443, idle 0:00:08, bytes 119188, flags UOB
Alternatively, the show asp table socket command can used for the verification of active ASDM connections. Ensure to check only the connections with the port that the HTTP server is running on (show run http).
# show asp table socket
Protocol Socket State Local Address Foreign Address
SSL 0027eb28 LISTEN 198.51.100.141:443 0.0.0.0:*
SSL 00305798 ESTAB 198.51.100.141:443 192.0.2.35:50620
The clear conn all protocol tcp port <port> command can be used to clear connections.
- If the management-access <interface> command is configured and ASDM connects to the <interface> IP via a Virtual Private Network connection (VPN), remove and re-add the management-access <interface>. This is the workaround for the Cisco bug ID CSCvu60373
 “ASA - Management-access does not work over Tunnel Interface”.
“ASA - Management-access does not work over Tunnel Interface”.
- Check the Cisco bug ID CSCwd04210
 “ASA: ASDM sessions stuck in CLOSE_WAIT causing lack of MGMT”. Due to this defect, the ASDM session can terminate with the "Lost connection to firewall" message and further connection to the firewall be unsuccessful. The workaround is to reload the firewall.
“ASA: ASDM sessions stuck in CLOSE_WAIT causing lack of MGMT”. Due to this defect, the ASDM session can terminate with the "Lost connection to firewall" message and further connection to the firewall be unsuccessful. The workaround is to reload the firewall. - Check the Cisco bug ID CSCwh32118
 “ASDM management-sessions quota reached due to HTTP sessions stuck in CLOSE_WAIT”. Due to this defect, the ASDM management-sessions quota reaches due to HTTP sessions stuck in the CLOSE_WAIT state. The workaround steps:
“ASDM management-sessions quota reached due to HTTP sessions stuck in CLOSE_WAIT”. Due to this defect, the ASDM management-sessions quota reaches due to HTTP sessions stuck in the CLOSE_WAIT state. The workaround steps:
- Check the current and limit resource usage for ASDM:
# show resource usage resource ASDM
Resource Current Peak Limit Denied Context
ASDM 1 1 5 0 admin
- If the current value is the same as the limit, check the state of the HTTPS sessions:
# debug menu npshim -w
Handle State Intf
...
720108b6 CLOSE_WAIT
57835276 CLOSE_WAIT
58068272 CLOSE_WAIT
6ae93b92 CLOSE_WAIT
- If there are multiple entries in the CLOSE_WAIT state, use debug menu pdm 3 command to clear all these sessions.
- Check the symptoms of block depletion in the output of the show blocks command, specifically the lowest values in the LOW and CNT columns:
- 256- and 1550-byte block sizes have been exhausted and recovered:
# show blocks
SIZE MAX LOW CNT
0 5700 5608 5700
4 900 899 899
80 5000 4575 5000
256 13568 0 13563
1550 50000 0 49974
- 256- and 1550-byte block sizes have been exhausted and not recovered:
# show blocks
SIZE MAX LOW CNT
0 5700 5608 5700
4 900 899 899
80 5000 4575 5000
256 13568 0 0
1550 50000 0 0
Refer to the Cisco bug ID CSCvv71435 “ASA 256 and/or 1550 block depletion causes DMA Memory unreleased allocation”.
The workaround options:
- Rate limit syslog messages being created at a high rate. Most common messages IDs that would create a high rate of messages are the messages for connection creation and teardown, such as:
%ASA-6-302013: Built {inbound|outbound} TCP connection_id for interface:real-address/real-port (mapped-address/mapped-port) [(idfw_user)] to interface:real-address/real-port (mapped-address/mapped-port) [(idfw_user)] [(user)]
%ASA-6-302014: Teardown TCP connection id for interface :real-address /real-port [(idfw_user )] to interface :real-address /real-port [(idfw_user )] duration hh:mm:ss bytes bytes [reason [from teardown-initiator]] [(user )]In this case, a possible rate limit configuration would look like:
logging rate-limit 1 10000 message 302013
logging rate-limit 1 10000 message 302014
Other potential messages are: 302015 / 302016 / 302017 / 302018 / 302020 / 302036 / 302303 / 302304 / 302305 / 302306. Reference: logging rate-limit command reference.
- Disable the log messages being created at a high rate:
no logging message 302013
no logging message 302014
- Reactive option is to reload the device to release the allocated DMA memory. Consider using one of the preventive measures to avoid this issue recurrence.
- Check if logs like these lines are shown in the ASA console. In this case, ASDM or SSH connections fail to establish:
ERROR: FAIL to ALLOC the stack page 0xffffffffffffffff[size 36864] to 0x00007fa3b0c29000 errno (mmap:umap) 12:0Message #10 :
First MMAP Req/Updated 36864/45056 Front 0x00007fa3b0c28000 rtn 0x00007fa3b0c29000 back 0x00007fa3b0c32000
Message #11 : process_create: out of stack memory for name accept/ssh_2 size 32768 prio 3
Message #12 : _listen_ssh: failed to create thread for interface 2 port 22
Refer to the Cisco bug ID CSCwc23844 “ASAv high CPU and stack memory allocation errors despite over 30% free memory”. The temporary workaround is to reboot the firewall.

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
References
- Cisco Secure Firewall ASA Release Notes
- Cisco Secure Firewall ASDM Release Notes
- Cisco Secure Firewall ASA Compatibility
- logging rate-limit command reference
Problem 2. ASDM user interface is inaccessible via the Java Web Launch-Starting
To verify the symptoms, enable Java console logs:
The Java console logs show messages like these lines:
NLPException[category: Download Error : Exception: java.io.FileNotFoundException: https://192.0.2.1/admin/public/asdm.jnlp : LaunchDesc: null
at com.sun.javaws.Main.launchApp(Unknown Source)
at com.sun.javaws.Main.continueInSecureThread(Unknown Source)
at com.sun.javaws.Main.access$000(Unknown Source)
at com.sun.javaws.Main$1.run(Unknown Source)
at java.lang.Thread.run(Unknown Source)
Caused by: java.io.FileNotFoundException: https://10.75.32.2/admin/public/asdm.jnlp
at sun.net.www.protocol.http.HttpURLConnection.getInputStream0(Unknown Source)
at sun.net.www.protocol.http.HttpURLConnection.access$200(Unknown Source)
at sun.net.www.protocol.http.HttpURLConnection$9.run(Unknown Source)
at sun.net.www.protocol.http.HttpURLConnection$9.run(Unknown Source)
at java.security.AccessController.doPrivileged(Native Method)
at java.security.AccessController.doPrivilegedWithCombiner(Unknown Source)
at sun.net.www.protocol.http.HttpURLConnection.getInputStream(Unknown Source)
Troubleshoot – Recommended Actions
ASDM 7.18 ending support for Java Web Launch-Starting with ASDM 7.18, ASDM no longer supports Java Web Start due to Oracle's end of support for JRE 8 and Java Network Launching Protocol (JNLP). You must install the ASDM Launcher to launch ASDM. Refer to the Release Notes for Cisco Secure Firewall ASDM, 7.18(x).
References
Problem 3. ASDM gets stuck in ‘Please wait while ASDM is loading the current configuration from your device’
The error shown on ASDM UI is:
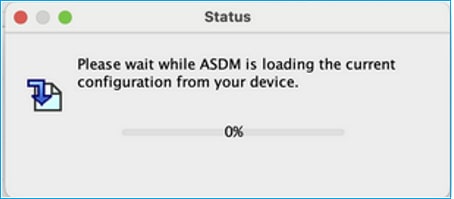
Troubleshoot – Recommended Actions
This is a known defect tracked by Cisco bug ID CSCvv14818  Misleading popup: Please wait while ASDM is loading the current configuration from your device.
Misleading popup: Please wait while ASDM is loading the current configuration from your device.

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
Problem 4. ASDM launch error: JAR resources in JNLP file are not signed by the same certificate
The error shown on ASDM UI is: ‘Unable to launch the application.’
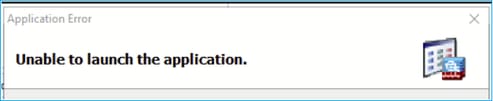
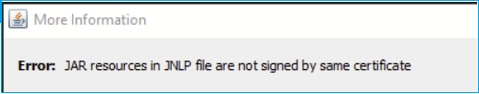
The ASDM Java logs show: ‘JAR resources in JNLP file are not signed by same certificate’
Troubleshoot – Recommended Actions
This is a known defect tracked by Cisco bug ID CSCwc13294  ASA: Cannot connect to ASA using ASDM with Java Web Launch
ASA: Cannot connect to ASA using ASDM with Java Web Launch

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.

Note: The ASDM Java Web Launch support ended in 7.18 release code. Starting with ASDM 7.18, ASDM no longer supports Java Web Start due to Oracle’s end of support for JRE 8 and Java Network Launching Protocol (JNLP). You must install the ASDM Launcher to launch ASDM.
Reference
https://www.cisco.com/c/en/us/td/docs/security/asdm/7_17/release/notes/rn717.html
Problem 5. ASDM hangs at 77% loading the device configuration
The ASDM gets stuck at 77% while parsing running configuration.
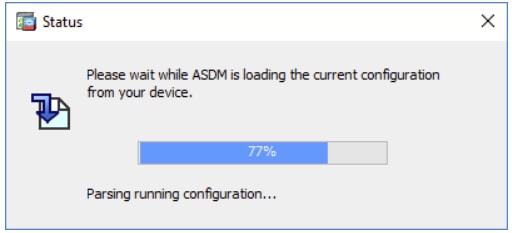
Troubleshoot – Recommended Actions
This is a known defect tracked by Cisco bug ID CSCvh02586  ASDM hangs at 77% loading the device configuration
ASDM hangs at 77% loading the device configuration

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
Problem 6. Unable to access ASDM on the standby firewall
Troubleshoot – Recommended Actions
Ensure that both firewalls have:
The same ASA software images, for example:
asa# show run boot
boot system disk0:/cisco-asa-fp1k.9.22.1.1.SPA
The same ASDM software images, for example:
asa# show asdm image
Device Manager image file, disk0:/asdm-7221.bin
Problem 7. ASDM hangs at ‘Software update completed.’
The ASDM UI gets stuck at ‘Software update completed.’ phase
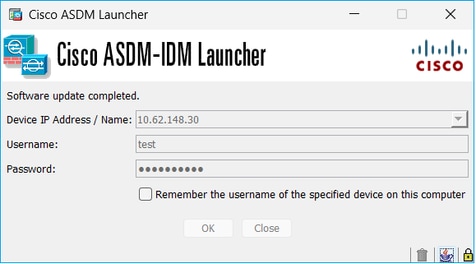
In the ASDM Java logs you see:
java.lang.NullPointerException
at vk.cz(vk.java:780)
at vk.b(vk.java:609)
at vk.<init>(vk.java:409)
at com.cisco.pdm.PDMApplet.start(PDMApplet.java:170)
at com.cisco.nm.dice.loader.Loader$1.run(Loader.java:416)
Exception in Starting Main window
Exception in thread "SGZ Loader: launchSgzApplet" java.lang.NullPointerException
at com.cisco.pdm.PDMApplet.start(PDMApplet.java:177)
at com.cisco.nm.dice.loader.Loader$1.run(Loader.java:416)
Note that the vk,cz, and so on. can be whatever characters, for example:
java.lang.NullPointerException
at t6.cr(t6.java:742)
at t6.b(t6.java:573)
at t6.<init>(t6.java:386)
at com.cisco.pdm.PDMApplet.start(PDMApplet.java:168)
at com.cisco.nm.dice.loader.Loader$1.run(Unknown Source)
Exception in Starting Main window
Exception in thread "SGZ Loader: launchSgzApplet" java.lang.NullPointerException
at com.cisco.pdm.PDMApplet.start(PDMApplet.java:175)
at com.cisco.nm.dice.loader.Loader$1.run(Unknown Source)
Troubleshoot – Recommended Actions
Ensure that your ASDM user has privilege level 15:
asa# show run username
username test password ***** pbkdf2 privilege 3 <- this cannot work
While this works:
asa# show run username
username test password ***** pbkdf2 privilege 15
Problem 8. ASDM on ASA multiple context hangs at 57% while parsing running configuration
The ASDM UI gets stuck at 57%. The UI shows: Please wait while ASDM is loading the current configuration from your device.
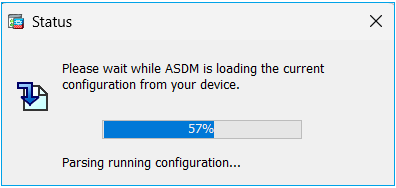
Troubleshoot – Recommended Actions
This is typically seen when all of these conditions are being met:
- ASA is in multiple context mode
- There is an aaa-server group that contains more than 4 servers.
Solution
Reduce the number of aaa-server in the group, for example:
Before:
aaa-server ACS protocol tacacs+
aaa-server ACS (management) host 192.0.2.1
key *****
aaa-server ACS (management) host 192.0.2.2
key *****
aaa-server ACS (management) host 192.0.2.3
key *****
aaa-server ACS (management) host 192.0.2.4
key *****
aaa-server ACS (management) host 192.0.2.5
key *****
aaa-server ACS (management) host 192.0.2.6
key *****
Change:
asa(config)# no aaa-server ACS (management) host 192.0.2.5
asa(config)# no aaa-server ACS (management) host 192.0.2.6
After:
aaa-server ACS protocol tacacs+
aaa-server ACS (management) host 192.0.2.1
key *****
aaa-server ACS (management) host 192.0.2.2
key *****
aaa-server ACS (management) host 192.0.2.3
key *****
aaa-server ACS (management) host 192.0.2.4
key *****
Reference
Problem 9. Unable to access ASDM on vASA
Many messages like these are shown:
Problem Details: ERROR: FAIL to ALLOC the stack page 0xffffffffffffffff[size 36864] to 0x00007ff62429c000 errno (mmap:umap) 12:0 First MMAP Req/Updated 36864/45056 Front 0x00007ff62429b000 rtn 0x00007ff62429c000 back 0x00007ff6242a5000
Other symptoms:
- High CPU utilization in the 'show cpu' output despite 'show cpu core' showing a low amount of utilization
- Stack memory allocation errors in the console
- Inability to SSH to the device
- SNMP polling fails
This is a known defect tracked by Cisco bug ID CSCwc23844  ASAv high CPU and stack memory allocation errors despite over 30% free memory
ASAv high CPU and stack memory allocation errors despite over 30% free memory

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
Troubleshoot ASDM-Related Problems on Windows OS
Problem 1. ASDM does not load the firewall configuration when using ASA + SFR
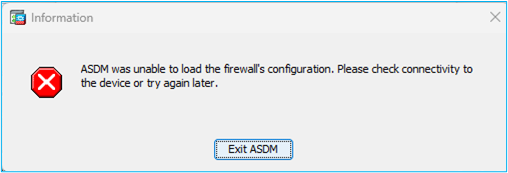
The error shown on ASDM UI is:
‘ASDM was unable to load the firewall’s configuration. Please check connectivity to the device or try again later.’
Troubleshoot – Recommended Actions
Check the ASDM release notes. They mention which OS is supported:
The related section:
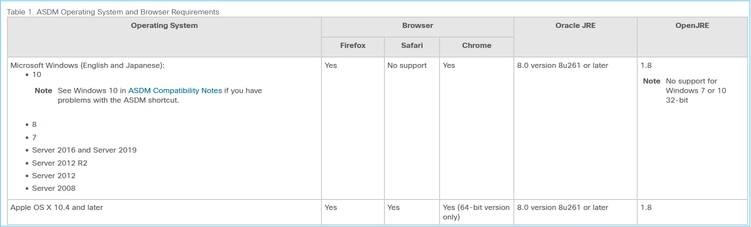
The screenshot is from the ASDM 7.18 release notes:
https://www.cisco.com/c/en/us/td/docs/security/asdm/7_18/release/notes/rn718.html
As it can be seen, Windows 11 and 2022 are not in the list.
Also, as from ASDM 7.16, on Windows Server 2016 and Server 2019, ASDM management of the FirePOWER module is not supported. You can alternatively use the FMC to manage the FirePOWER module when using ASDM for ASA management.
Troubleshooting Tip: Check the Java console logs on ASDM:
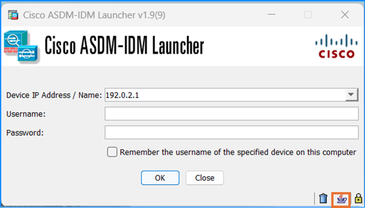
In case of an unsupported OS you see something like:
Caused by: java.lang.ExceptionInInitializerError: Exception com.teamdev.jxbrowser.chromium.internal.EnvironmentException: Unsupported operating system. Supported OS: Windows XP (SP2), 7, 8, 10, Vista, 2003 (SP1), 2008, 2012, Mac OS X & Linux. Current OS: Windows 11 [in thread "AWT-EventQueue-0"]
at com.teamdev.jxbrowser.chromium.internal.Environment.checkEnvironment(Unknown Source)
…
Solutions
Thus, in order to be able to manage the ASA using ASDM the options you have are:
Option 1: Manage the ASA and FirePOWER module from another, older host (for example, Windows 2010, Windows Server 2012, and so on.)
Option 2: Manage the FirePOWER module using FMC and keep managing the ASA using ASDM.
|
SFR module managed by FMC (DC) |
SFR module managed by ASDM |
asa# show module sfr details |
asa# show module sfr details |
Option 3: Shutdown the Firepower module:
ASA5508# sw-module module sfr shutdown
Shutdown module sfr? [confirm]
Shutdown issued for module sfr.

Note: The module shutdown is not a permanent solution. If you reboot the firewall, the SFR module comes UP again.
Option 4: In case you don’t plan to use the Firepower module any more, you can uninstall it:
ASA5508# sw-module module sfr uninstall
Option 5: Work with Cisco TAC to apply the workaround from the Cisco bug ID CSCwj51536  to manually replace the jxbrowser.jar files. Note though that this workaround still might not resolve the problem. In that case, you need to consider the previous options.
to manually replace the jxbrowser.jar files. Note though that this workaround still might not resolve the problem. In that case, you need to consider the previous options.
Problem 2. ASDM gets stuck while Downloading FirePOWER packages
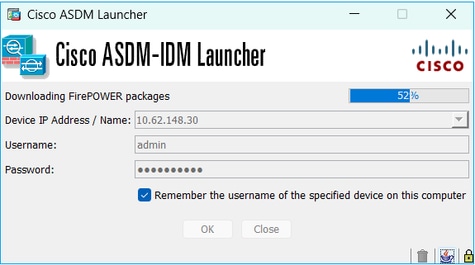
Troubleshoot – Recommended Actions
According to the Firepower compatibility guides, ASDM is not supported for FirePOWER module management with ASA 9.8(4.45)+, 9.12(4.50)+, 9.14(4.14)+, and 9.16(3.19)+; you have to use FMC to manage the module with these releases. These ASA releases require ASDM 7.18(1.152) or later, but ASDM support for the ASA FirePOWER module ended with 7.16.
Solution
Thus, in order to be able to manage the ASA using ASDM the options you have are:
Option 1: Manage the ASA and FirePOWER module from another, older host (for example, Windows 2010, Windows Server 2012, and so on.)
Option 2: Manage the FirePOWER module using FMC and keep managing the ASA using ASDM.
Option 3: Shutdown the Firepower module:
ASA5508# sw-module module sfr shutdown
Shutdown module sfr? [confirm]
Shutdown issued for module sfr.
Option 4: In case you don’t plan to use the Firepower module any more, you can uninstall it:
ASA5508# sw-module module sfr uninstall
Reference
Problem 3. "This app can't run on your PC" error message shown on Windows hosts
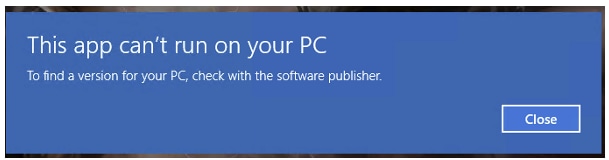
Troubleshoot – Recommended Actions
When you install the ASDM Launcher, Windows can replace the ASDM shortcut target with the Windows Scripting Host path, which causes this error. To fix the shortcut target:
- Choose Start > Cisco ASDM-IDM Launcher, and right-click the Cisco ASDM-IDM Launcher application.
- Choose More > Open file location. Windows opens the directory with the shortcut icon.
- Right click the shortcut icon, and choose Properties.
- Change the Target to: C:\Windows\System32\wscript.exe invisible.vbs run.bat (leave the invisible.vbs run.bat on the end as these scripts are used to open up ASDM).
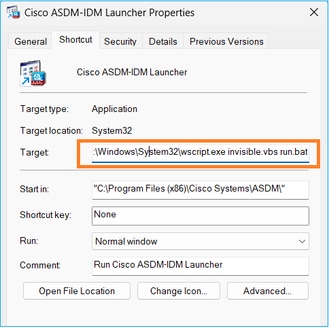
5. Click OK.
Reference
https://www.cisco.com/c/en/us/td/docs/security/asdm/7_22/release/notes/rn722.html
Problem 4. Windows cannot find ‘javaw.exe’. Make sure you typed the name correctly, and then try again.
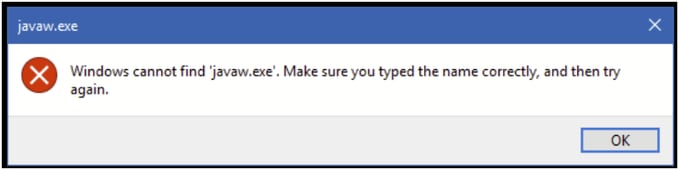
Troubleshoot – Recommended Actions
- Typically, this error is related to Java missing on the computer. Ensure you have a compatible Java version installed on your Windows host: https://www.java.com/en/download/help/windows_manual_download.html
https://www.cisco.com/c/en/us/td/docs/security/asdm/7_22/release/notes/rn722.html#id_25472
- Ensure you have the exact path of the Java program in the Windows Environment Variable path.
- In case the problem occurred after a Java upgrade, consider rolling back the Java version.
- Ensure that your ASDM Desktop icon point to the proper installation path. If not, delete it and create a new shortcut.
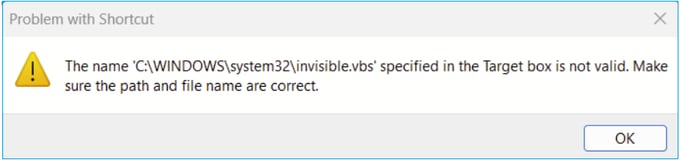
Problem 5. Problem with Shortcut ‘C:\Windows\system32\invisible.vbs’ in the Target box is not valid
Error shown: The name ‘C:\Windows\system32\invisible.vbs’ specified in the Target box is not valid. Make sure the path and file name are correct.
In some cases, the error is: Can not find script file ‘C:\Windows\system32\invisible.vgs’.
Troubleshoot – Recommended Actions
- Ensure you have administrator permissions when you install ASDM on the Windows host. In some cases, Active Directory settings for Windows users can restrict access to program file locations needed to successfully launch ASDM on Windows. Access is needed to these directories:
- Desktop folder
- C:\Windows\System32C:\Users\<username>\.asdm
- C:\Program Files (x86)\Cisco Systems
If your Active Directory is restricting directory access, you need to request access from your Active Directory administrator.
- Try installing a different version of Java on the Windows host.
References
https://www.cisco.com/c/en/us/td/docs/security/asdm/7_18/release/notes/rn718.html#id_25476
Problem 6. Windows Script Host Can not find script file “C:\WINDOWS\system32\invisible.vbs”
When trying to start the ASDM launcher, these error appears: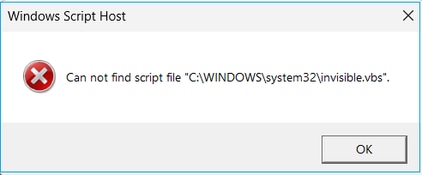
Troubleshoot – Recommended Actions
Follow these steps:
- Reboot the Windows host and delete/uninstall all instances of the ASDM launcher.
- Reinstall a newer, but still compatible version of the ASDM launcher. If there is no newer version install the same ASDM launcher you had before.
- Ensure the correct Java version has been installed.
Alternatively, you can try to use the OpenJRE-based ASDM installer since it does not need Oracle Java to be installed on the local PC.
Troubleshoot – Recommended Actions
Follow these steps:
- Reboot the Windows host and delete/uninstall all instances of the ASDM launcher.
- Reinstall a newer, but still compatible version of the ASDM launcher. If there is no newer version install the same ASDM launcher you had before.
- Ensure the correct Java version has been installed.
Alternatively, you can try to use the OpenJRE-based ASDM installer since it does not need Oracle Java to be installed on the local PC.
Problem 7. ASDM does not work on Windows Server 2022
Troubleshoot – Recommended Actions
At the time of this writing, Windows Server 2022 is not supported. Check the latest ASDM release notes from https://www.cisco.com/c/en/us/support/security/adaptive-security-appliance-asa-software/products-release-notes-list.html and if Windows Servver 2022 is not listed consider using a different OS from the supported list.
Problem 8. ASDM UI font size is too small
Troubleshoot – Recommended Actions
Try these steps:
- Find javaw.exe you installed (C:\ProgramData\Oracle\Java\javapath) or when having ASDM running open Task Manager and locate the service running:
- Right click -> Properties
- Go to Compatibility tab
- Click on ‘Change high DPI settings’
- Enable the ‘Use this setting to fix scaling problems for this program instead of the one in Settings’ checkbox
- Enable the ‘Override high DPI scaling behavior’ checkbox and select ‘System (Enhanced)’:
Before:
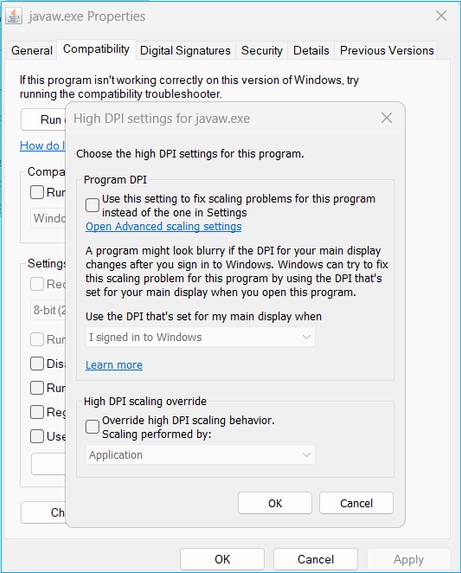
After:
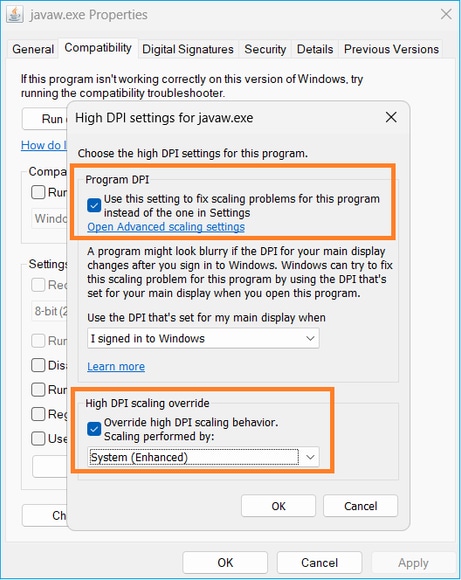
Problem 9. Java errors
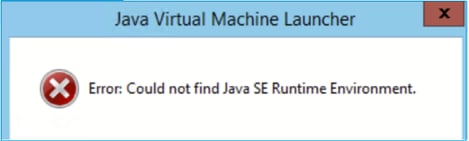
The ASDM UI can show one or more of these Java errors: Error: could not find java.dll
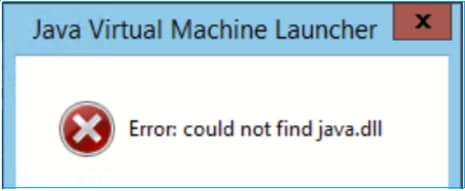
And/or:
Error: Could not find Java SE Runtime Environment.
And/or:
Error: Registry key ‘Software\JavaSoft\Java Runtime Environment’\CurrentVersion’ has value ‘x.x’, but ‘x.x’ is required.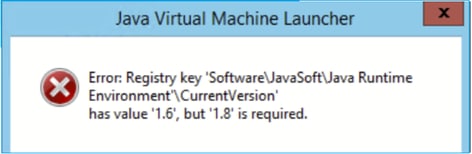
Troubleshoot – Recommended Actions
- Check if other versions of Java are installed.
- If other versions are installed, uninstall all versions of Java. Make sure to also uninstall Java 8.
Tip: You can review this key in the registry: HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Runtime Environment to determine the installed versions.
You can also confirm that all versions are completely uninstalled through this key.
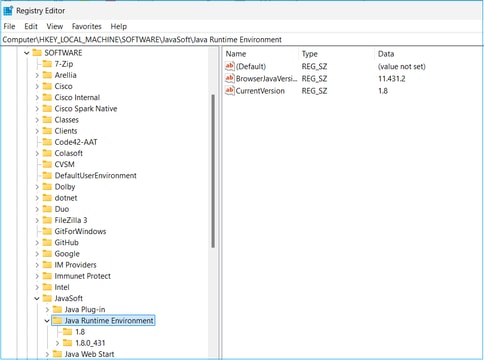
Warning: Be careful when working with Windows registry!
- Reinstall a compatible Java version.
Problem 10. ASDM version 7.19.1.94 openJRE version file in the backend still showing OracleJRE version
Normal Behavior with openJRE
Normally, when you install and openJRE-based ASDM image, the Java version reflects it:
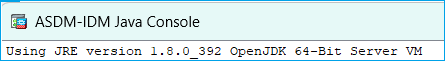
And there is a ‘jre’ folder created under this path: C:\Program Files (x86)\Cisco Systems\ASDM\jre
There, you can find a release file that contains information about Azul Zulu:
IMPLEMENTOR="Azul Systems, Inc."
IMPLEMENTOR_VERSION="Zulu8.74.0.17-CA-win64"
JAVA_VERSION="1.8.0_392"
OS_NAME="Windows"
OS_VERSION="5.2"
OS_ARCH="amd64"
SOURCE=".:git:51a769a8708c"
Incorrect Behavior with openJRE
Now, the problem is that in some ASDM versions (for example, 7.19.1.94) the UI shows:
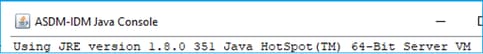
And the C:\Program Files (x86)\Cisco Systems\ASDM\jre\release file shows something like:
JAVA_VERSION="1.8.0_351"
OS_NAME="Windows"
OS_VERSION="5.2"
OS_ARCH="amd64"
SOURCE=".:git:c72692150ec4+"
BUILD_TYPE="commercial"
Troubleshoot – Recommended Steps
This is a known Cisco bug ID CSCwf74697  ASDM version 7.19.1.94 openJRE version file in the backend still showing OracleJRE version
ASDM version 7.19.1.94 openJRE version file in the backend still showing OracleJRE version

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
Workaround:
Use >= 7.18.1.161 or >= 7.19.1.95 OpenJRE version bin.
Problem 11. ASDM java errors "[ERROR] CLI-PASSTHROUGH-DEBUG Inside doInitialProcessing"
Symptoms (both must be true):
- ASDM operates with no problems.
- ASDM Java logs show
0 [SGZ Loader: launchSgzApplet] ERROR com.cisco.pdm.headless.startup - CLI-PASSTHROUGH-DEBUG Inside doInitialProcessing:
[ERROR] CLI-PASSTHROUGH-DEBUG Inside doInitialProcessing messenger: cqq@1a3c930 46 [SGZ Loader: launchSgzApplet] ERROR com.cisco.pdm.headless.startup –
CLI-PASSTHROUGH-DEBUG Inside doInitialProcessing messenger: cqq@1a3c930 CLI-PASSTHROUGH-DEBUG Inside doInitialProcessing messenger: cqq@1a3c930 Env.isAsdmInHeadlessMode()-------------->false IO Exception occurs while reading the dap file. java.io.FileNotFoundException: https://192.0.2.1 /admin/flash/dap.xml
No CSD version
Troubleshoot – Recommended Actions
This is a known cosmetic defect tracked by Cisco bug ID CSCwe28411  ASDM java errors "[ERROR] CLI-PASSTHROUGH-DEBUG Inside doInitialProcessing"
ASDM java errors "[ERROR] CLI-PASSTHROUGH-DEBUG Inside doInitialProcessing"

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information
Troubleshoot ASDM Connectivity Problems
Problem 1. ASDM launch fails due to reaching maximum number of sessions
The “The maximum number of management session for protocol http or user already exist. Please try again later” error message is shown on the ASDM:
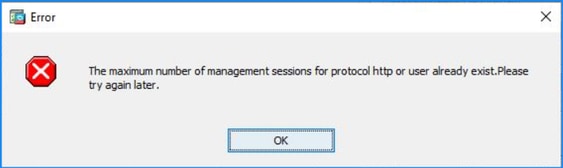
A similar error can be shown when switching between the contexts on ASDM.
Troubleshoot – Recommended Actions
Refer to the Cisco bug ID CSCwd04210: ASA: ASDM sessions stuck in CLOSE_WAIT causing lack of MGMT”. Due to this defect, the ASDM session can terminate with the "Lost connection to firewall" message and further connection to the firewall be unsuccessful.

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
Problem 2. Increase load/connection time in ASDM
The ASDM initial connection/load time increases in versions running the fix for the Cisco bug ID CSCvw79912 “Cisco Adaptive Security Device Manager Remote Code Execution Vulnerability”.
Troubleshoot – Recommended Actions
Refer to the Cisco bug ID CSCwd58653 “ASDM initial connection/load time increased”.

Note: This defect has been fixed in recent ASDM software releases. Check the defect details for more information.
Troubleshoot ASDM Memory-Related Problems
Problem 1. Unresponsive and/or sluggish ASDM user interface during configuration load
One or more of these symptoms are observed when running ASDM:
- ASDM UI becomes unresponsive and/or sluggish while loading the configuration.
- The “ASDM was unable to load the firewall’s configuration. Please check connectivity to the device and try again later” error message is shown:
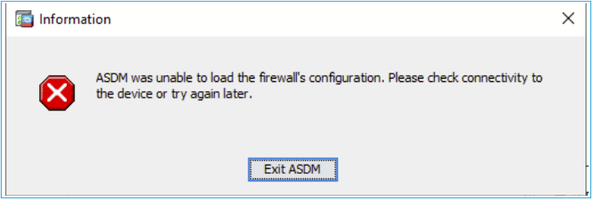
- The “Retrieval of Data (validating running configuration)” message is shown for an extended amount of time, for example, several hours.
- In the Java console logs these lines are shown:
Exception in thread "AWT-EventQueue-0" java.lang.OutOfMemoryError: Java heap space
Exception in thread "LoadConfigThread" java.lang.OutOfMemoryError: GC overhead limit exceeded
or
Exception in thread "AWT-EventQueue-0" java.lang.OutOfMemoryError: Java heap space
java.lang.reflect.InvocationTargetException
at java.awt.EventQueue.invokeAndWait(Unknown Source)
at java.awt.EventQueue.invokeAndWait(Unknown Source)
at javax.swing.SwingUtilities.invokeAndWait(Unknown Source)
at c1.f(c1.java:483)
at c1.setVisible(c1.java:455)
at ve.setVisible(ve.java:165)
at vd.d(vd.java:873)
at com.cisco.pdm.PDMApplet.populateLoginHistory(PDMApplet.java:268)
at com.cisco.pdm.PDMApplet.start(PDMApplet.java:233)
at com.cisco.nm.dice.loader.Loader$1.run(Loader.java:416)
Caused by: java.lang.OutOfMemoryError: Java heap space
To verify this symptom, enable Java console logs:
Troubleshoot – Recommended Actions
- Ensure that the ASA, ASDM and operating system versions are compatible. Refer to the Cisco Secure Firewall ASA Release Notes, Cisco Secure Firewall ASDM Release Notes, Cisco Secure Firewall ASA Compatibility.
- Increase the ASDM Configuration Memory on operating systems:
Windows
- Go to the ASDM installation directory, for example C:\Program Files (x86)\Cisco Systems\ASDM.
- Edit the run.bat file with any text editor.
- In the line that starts with “start javaw.exe”, change the argument prefixed with “-Xmx” to specify your desired heap size. For example, change it to -Xmx768M for 768 MB or -Xmx1G for 1 GB.
- Save the run.bat file.
Mac OS
- Right-click the Cisco ASDM-IDM icon and choose Show Package Contents.
- In the Contents folder, double-click the Info.plist file. If you have Developer tools installed, it opens in the Property List Editor. Otherwise, it opens in TextEdit.
- Under Java > VMOptions, change the string prefixed with “-Xmx” to specify your desired heap size. For example, change it to -Xmx768M for 768 MB or -Xmx1G for 1 GB.
- If this file is locked, you see an error such as this message:
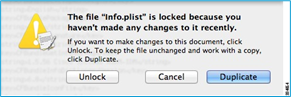
- Click Unlock and save the file. If you do not see the Unlock dialog box, exit the editor, right-click the Cisco ASDM-IDM icon, choose Copy Cisco ASDM-IDM, and paste it to a location where you have write permissions, such as the Desktop. Then change the heap size from this copy.
References
- Cisco Secure Firewall ASA Release Notes
- Cisco Secure Firewall ASDM Release Notes
- Cisco Secure Firewall ASA Compatibility
Problem 2. ASDM is unable to contact the firewall
The error “ASDM is temporarily unable to contact the firewall.” or “Unable to launch device manager” is shown when launching ASDM: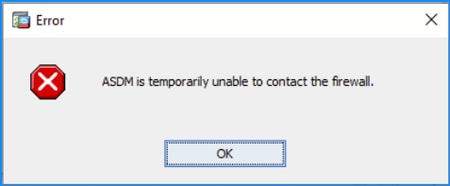
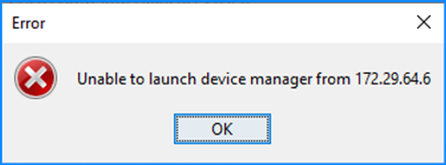
- Some of the packets of the ASDM HTTPS Connection are dropped with the (ctm-error) CTM returned error drop reason in the Accelerated Security Path (ASP):
# capture asp type asp-drop all buffer 33554432 match ip host 192.0.2.1 host 192.0.2.1 eq https
# show capture
capture asp type asp-drop all buffer 33554432 [Capturing - 587 bytes]
match ip host 192.0.2.1 host 192.0.2.2 eq https
# show cap asp
1 packet captured
1: 10:41:04.850648 192.0.2.1.56667 > 192.0.2.2.443: P 758423982:758424499(517) ack 2534033991 win 64440 Drop-reason: (ctm-error) CTM returned error
- The number of failed blocks is for 256 and 1550-size blocks is non-zero and the FAILED counter increases:
# show block
SIZE MAX LOW CNT FAILED
0 2950 2865 2950 0
4 400 398 399 0
80 2500 2369 2500 0
256 6302 0 6274 50693
1550 22147 0 22111 769896
2048 8848 8844 8848 0
2560 2964 2962 2964 0
4096 100 99 100 0
8192 100 99 100 0
9344 100 99 100 0
16384 154 153 154 0
65664 16 16 16 0
- The amount of the Free memory in the MEMPOOL_DMA memory pool is significantly low, typically around a couple of bytes or kilobytes:
# show memory detail | begin MEMPOOL_DMA
MEMPOOL_DMA POOL STATS:
Non-mmapped bytes allocated = 230686720
Number of free chunks = 175
Number of mmapped regions = 0
Mmapped bytes allocated = 0
Max memory footprint = 230686720
Keepcost = 336
Max contiguous free mem = 21136
Allocated memory in use = 230548640
Free memory = 138080
Troubleshoot – Recommended Actions
- Check the Cisco bug ID CSCvv71435 “ASA 256 and/or 1550 block depletion causes DMA Memory unreleased allocation”. The defect symptoms are observed at elevated rate of syslogs messages like 302013 or 302014.
Follow the steps from the Workaround section.
- Check the Cisco bug ID CSCwd58653 “ASDM initial connection/load time increased”. The ASDM initial connection/load time increased after ASDM upgrade to fix version of Cisco bug ID CSCvw79912 “Cisco Adaptive Security Device Manager Remote Code Execution Vulnerability”.

Note: Cisco bug ID CSCwd58653  and Cisco bug ID CSCvw79912
and Cisco bug ID CSCvw79912  have been fixed in recent ASDM software releases. Check the defect details for more information.
have been fixed in recent ASDM software releases. Check the defect details for more information.
References
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
3.0 |
29-Nov-2024 |
Initial Release |
1.0 |
28-Nov-2024 |
Initial Release |
Contributed by Cisco Engineers
- Ilkin GasimovCisco TAC Engineer
- Mikis ZafeiroudisCisco TAC Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback