Introduction
This document describes how you can find which rule in your access control policy is expanding to how many access list elements.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Knowledge of Firepower technology
- Knowledge on configuring Access control policies on FMC
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Secure Firewall Management Center (FMC)
- Cisco Firepower Threat Defence (FTD)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
An Access control rule is created with the use of one or multiple combinations of these parameters:
- IP Address (Source and Destination)
- Ports (Source and Destination)
- URL (System provided Categories and Custom URLs)
- Application Detectors
- VLANs
- Zones
Based on the combination of parameters used in the access rule, the rule expansion changes on the sensor. This document highlights various combinations of rules on the FMC and their respective associated expansions on the sensors.
How To Calculate Access List Element Count (ACE) Using FMC CLI
Consider the configuration of an access rule from the FMC, as shown in the image:
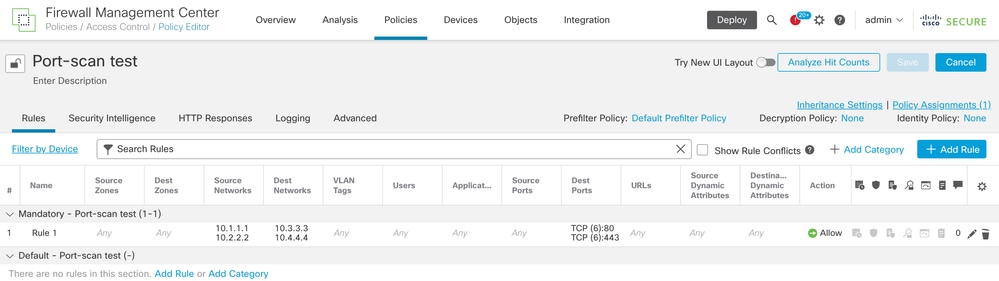 Rule Configuration in Access Control Policy
Rule Configuration in Access Control Policy
If you see this rule in FTD CLI, you notice that this rule got expanded into 8 Rules.
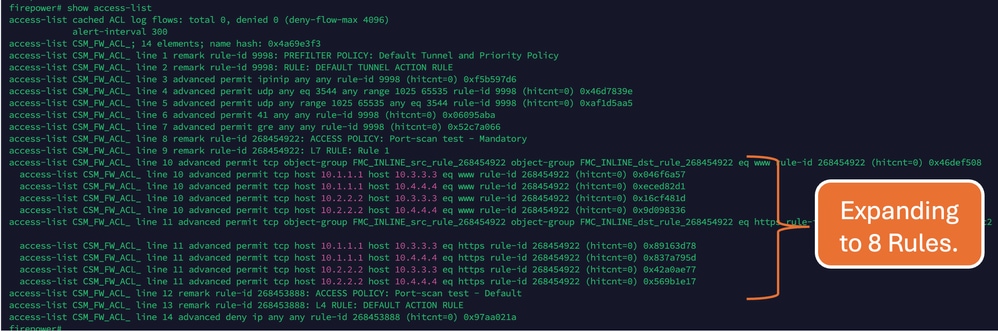
You can check which rule is expanding into how many access list elements using the perl command in FMC CLI:
perl /var/opt/CSCOpx/bin/access_rule_expansion_count.pl
root@firepower:/Volume/home/admin# perl /var/opt/CSCOpx/bin/access_rule_expansion_count.pl
Secure Firewall Management Center for VMware - v7.4.1 - (build 172)
Access Control Rule Expansion Computer
Enter FTD UUID or Name:
> 10.70.73.44
--------------------------------------------------------------------------------------------------------------------------
Secure Firewall Management Center for VMware - v7.4.1 - (build 172)
Access Control Rule Expansion Computer
Device:
UUID: 93cc359c-39be-11d4-9ae1-f2186cbddb11
Name: 10.70.73.44
Access Control Policy:
UUID: 005056B9-F342-0ed3-0000-292057792375
Name: Port-scan test
Description:
Intrusion Policies:
-------------------------------------------------------------------------------------------------
| UUID | NAME |
-------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------
Date: 2024-Jul-17 at 06:51:55 UTC
NOTE: Computation is done on per rule basis. Count from shadow rules will not be applicable on device.
Run "Rule Conflict Detection" tool on AC Policy for specified device to detect and optimise such rules.
--------------------------------------------------------------------------------------------------------------------------
| UUID | NAME | COUNT |
--------------------------------------------------------------------------------------------------------------------------
| 005056B9-F342-0ed3-0000-000268454919 | Rule 1 | 8 |
--------------------------------------------------------------------------------------------------------------------------
| TOTAL: 8
--------------------------------------------------------------------------------------------------------------------------
| Access Rule Elements Count on FTD: 14
--------------------------------------------------------------------------------------------------------------------------
>>> My JVM PID : 19417

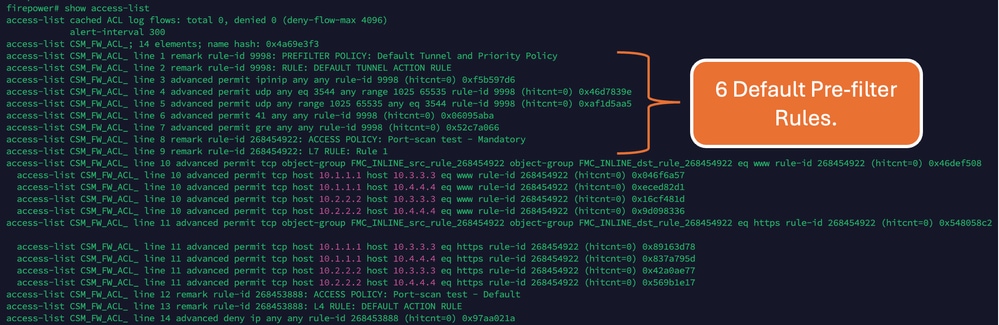
Note: Access Rule Elements Count on FTD: 14. This includes the default set of FTD rules (Pre-filter) and Default Access control rule as well.
The default Pre-filter rules can be seen in FTD CLI:
Impact of High ACE
- High CPU can be seen.
- High Memory can be seen.
- Device slowness can be observed.
- Deployments failure/ Longer deployment time.
Deciding When To Enable Object Group Search (OGS)
- Count of ACE is exceeding the device ACE limit.
- The CPU of the device is not already high as enabling OGS puts more stress on the device CPU.
- Enable it during non Production hours.

Caution: Please enable asp rule-engine transactional-commit access-group from FTD CLI clish mode before enabling the OGS. This is configured to avoid traffic drops during and just after the deployment process while enabling OGS.
Enabling Object Group Search
Currently OGS is not enabled:

- Log in to FMC CLI. Navigate to Devices > Device Management > Select the FTD device > Device. Enable the Object Group Search from Advanced Settings:
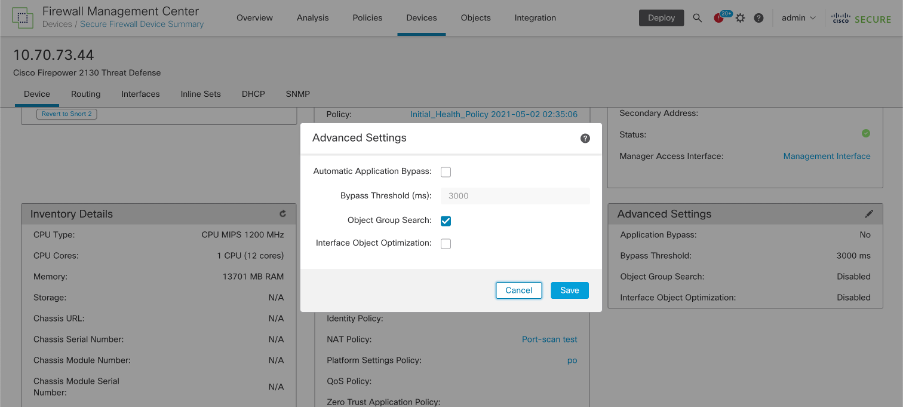
2. Click Save and deploy.
Verify
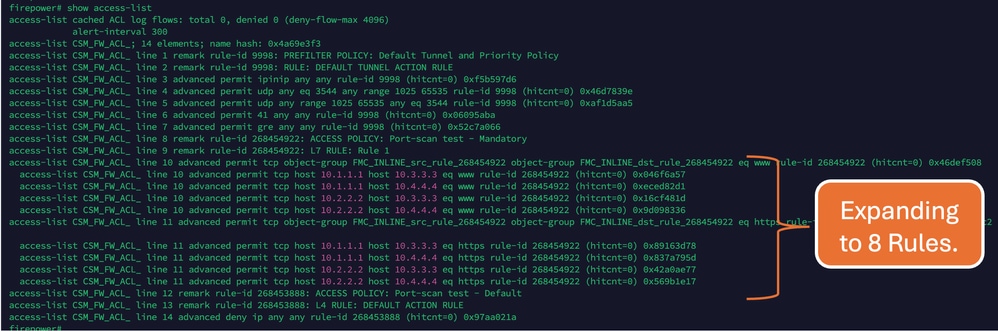
Before OGS is enabled:
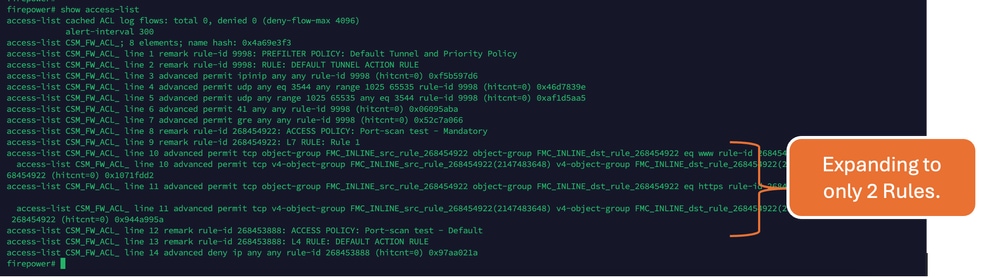
After OGS is enabled:
Related Information
For more detailed information on how rules are expanded in FTD, refer to the document Understand the Rule Expansion on FirePOWER Devices.
For more information on the FTD Architecture and Troubleshooting, refer to Dissecting (FTD) Firepower Threat Defense.











 Feedback
Feedback