Introduction
This document describes how to verify and troubleshoot EIGRP configuration on FTD devices using an FMC as manager.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Enhanced Interior Gateway Routing Protocol (EIGRP) concepts and functionality
- Cisco Secure Firewall Management Center (FMC)
- Cisco Secure Firewall Threat Defense (FTD)
Components Used
The information in this document is based on these software and hardware versions:
- FTDv for VMWare in version 7.2.8.
- FMC for VMWare in version 7.2.8.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
EIGRP Background
EIGRP can be configured on an FMC to use dynamic routing between FTD devices and other EIGRP capable devices.
The FMC only allows to configuration of one EIGRP Autonomous System (AS) in single mode.
The next parameters must match the EIGRP neighbors to form the EIGRP adjacency.
- An interface that belongs to the same IP subnet.
- EIGRP AS
- Hello and Hold intervals
- MTU
- Interface Authentication.
Basic Configuration
This section describes the needed parameters to configure EIGRP.
- Navigate to Devices > Device Management > Edit device
- Click the Routing tab.
- Click on EIGRP in the left menu bar.
- Mark the checkbox Enable EIGRP, to enable the protocol, and assign a value between 1-65535 to AS number.
- Note that the Auto Summary option is disabled by default
- Select one network/host, you can use an object previously created or add a new one by clicking on the add button (+)
- (Optional) Mark the checkbox Passive interface, to select the interfaces that do not redistribute the traffic.
- Click on Save, to store the changes.
Filter rules
The FTD allows the user to configure a distribution list to control the inbound and outbound routes.
- Navigate to Devices > Device Management > Edit device
- Click the Routing tab.
- Click on EIGRP.
- Click on Filtering Rules > Add.
- Select the corresponding information for the filtering fields.
- Filter direction
- Select Interface
- Select Access List
6. Move to steps, if there is a Standard Access List configured.
If the user needs to configure a Standard Access List, click on the plus button or create it from Objects > Object Management > Access List > Standard > Add Standard Access List.
7. Assign a name to the list
8. Click the plus ( + ) button
- Select an Action
- Add the network or host from the Available Network to the Selected Network.
9. Click on Add at the bottom to save the access list entry.
10. Click on Save, to save the standard access list.
11. Click on Ok.
12. Click on Save to validate the changes.
Redistribution
The FTD has the capability to redistribute the routes generated from BGP, RIP, and OSPF protocols, or from the static and connected routes into the EIGRP.
- Navigate to Devices > Device Management > Edit device
- Click the Routing tab.
- Click on EIGRP.
- Click on Redistribution.
- Enter the information in the redistribution fields.
- Protocol
- RIP
- OSPF
- BGP
- Connected
- Static
For OSPF is necessary to specify the Process ID, and for BGP the AS number on the filed Process ID*.
If the configuration requires redistribution of the information generated by the OSPF protocol, the user can select the OSPF type of Redistribution.
Optional Metrics refer to the EIGRP metrics and Route Map.
Interface
Hello and Hold timers
The Hello Packets are used for neighbor discovery and to detect the neighbor available. These packets are sent out in intervals, by default the value of this timer is 5 seconds.
Hold timer, determines the amount of time EIGRP deems a route is reachable and functional. By default, the hold time value is 3 times the hello interval.
Authentication
The FTD supports MD5 hash Algorithm to authenticate the EIGRP packets. By default, the authentication is disabled.
Mark the checkbox MD5 Authentication, to enable the MD5 hash algorithm.
Key
Unencrypted - plain text.
Encrypted
Troubleshooting and Validation commands
- show run router eigrp. Displays the EIGRP configuration
- show run interface [ interface]. Displays the EIGRP interface authentication and timers information.
- show eigrp events [{ start end} | type]. Displays the EIGRP event log.
- show eigrp interfaces [ if-name] [ detail]. Displays the interfaces participating in EIGRP routing.
- show eigrp neighbors [ detail | static] [ if-name]. Displays the EIGRP neighbor table.
- show eigrp topology [ ip-addr [ mask] | active | all-links | pending | summary | zero-successors]. Displays the EIGRP topology table.
- show eigrp traffic. Displays EIGRP traffic statistics.
Verification
Consider the next topology, this section uses the commands previously described to validate the EIGRP configuration applied to the FTD.
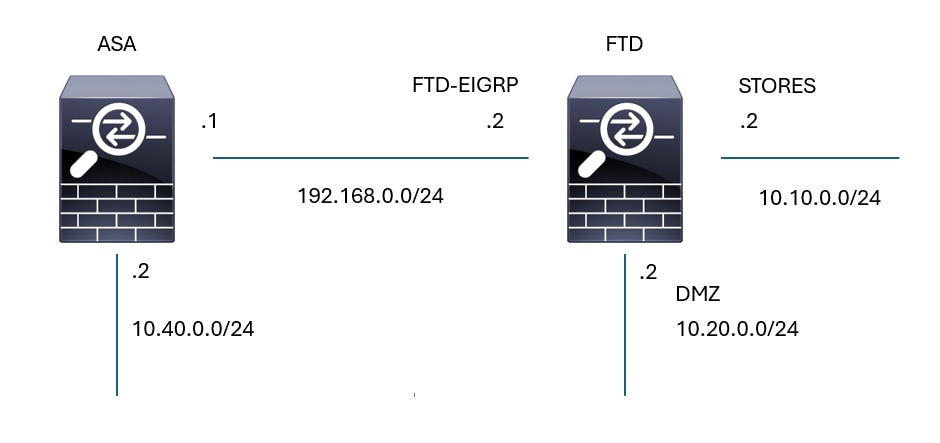 EIGRP Topology
EIGRP Topology
Basic Configuration
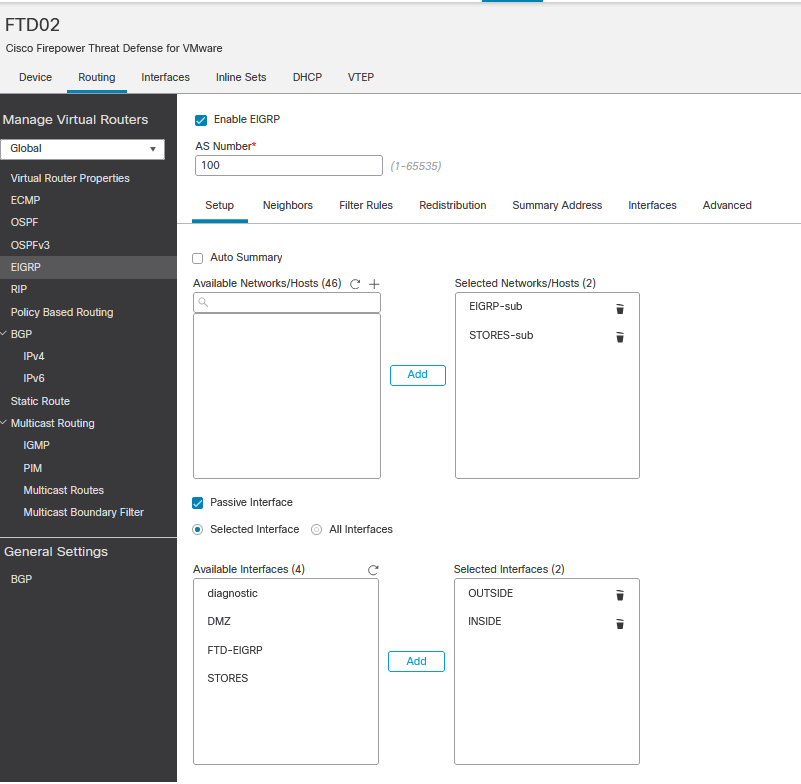 EIGRP Basic Configuration
EIGRP Basic Configuration
Redistribution
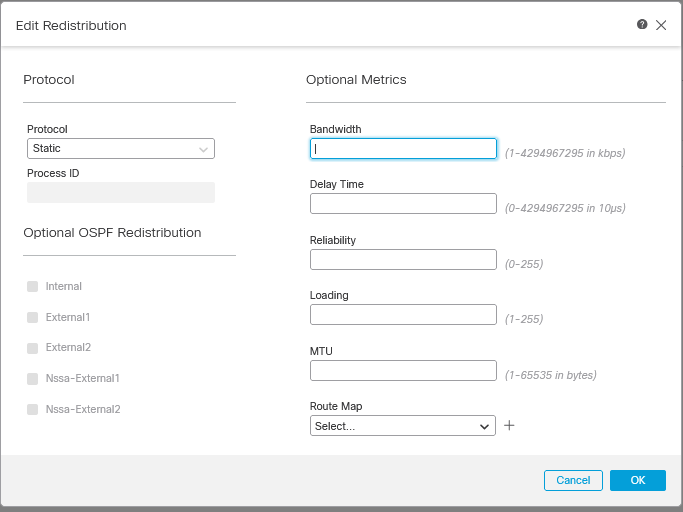 EIGRP Resdistribution Configuration
EIGRP Resdistribution Configuration
Interface configuration
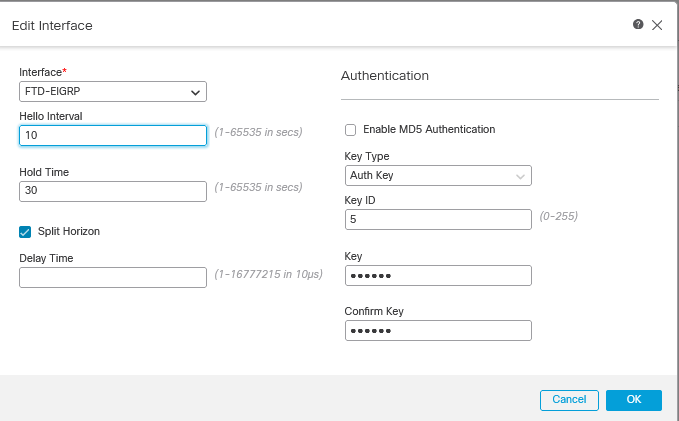 EIGRP Interface Configuration
EIGRP Interface Configuration
Validation using commands
firepower# show run router eigrp
router eigrp 100
no default-information in
no default-information out
no eigrp log-neighbor-warnings
no eigrp log-neighbor-changes
network 10.10.0.0 255.255.255.0
network 192.168.0.0 255.255.255.0
passive-interface OUTSIDE
passive-interface INSIDE
redistribute static
!
firepower# show run int g 0/2
!
interface GigabitEthernet0/2
nameif FTD-EIGRP
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 192.168.0.2 255.255.255.0
hello-interval eigrp 100 10
hold-time eigrp 100 30
firepower# show eigrp events
106 04:24:27.980 Conn rt change: 192.168.0.0 255.255.255.0 FTD-EIGRP
107 04:24:27.980 Lost route 1=forceactv: 192.168.0.0 255.255.255.0 0
108 04:24:27.980 Change queue emptied, entries: 1
109 04:24:27.980 Metric set: 192.168.0.0 255.255.255.0 512
110 04:24:27.980 Update reason, delay: new if 4294967295
111 04:24:27.980 Update sent, RD: 192.168.0.0 255.255.255.0 4294967295
112 04:24:27.980 Update reason, delay: metric chg 4294967295
113 04:24:27.980 Update sent, RD: 192.168.0.0 255.255.255.0 4294967295
114 04:24:27.980 Route installed: 192.168.0.0 255.255.255.0 0.0.0.0
115 04:24:27.980 Find FS: 192.168.0.0 255.255.255.0 4294967295
116 04:24:27.980 Rcv update met/succmet: 512 0
117 04:24:27.980 Rcv update dest/orig: 192.168.0.0 255.255.255.0 Connected
118 04:24:27.980 Metric set: 192.168.0.0 255.255.255.0 4294967295
119 04:24:27.980 Conn rt change: 192.168.0.0 255.255.255.0 FTD-EIGRP
firepower# show eigrp interfaces
EIGRP-IPv4 Interfaces for AS(100)
Xmit Queue Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable SRTT Un/Reliable Flow Timer Routes
FTD-EIGRP 1 0 / 0 48 0 / 1 193 0
firepower# show eigrp neighbors
EIGRP-IPv4 Neighbors for AS(100)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 192.168.0.1 FTD-EIGRP 27 09:15:22 48 1458 0 4
firepower# show eigrp topology
EIGRP-IPv4 Topology Table for AS(100)/ID(192.168.0.2)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 10.10.0.0 255.255.255.0, 1 successors, FD is 512
via Connected, STORES
P 10.40.0.0 255.255.255.0, 1 successors, FD is 768 ---------- Route learn from EIGRP neighbor
via 192.168.0.1 (768/512), FTD-EIGRP
P 192.168.0.0 255.255.255.0, 1 successors, FD is 512
via Connected, FTD-EIGRP
P 0.0.0.0 0.0.0.0, 1 successors, FD is 512
via Rstatic (512/0)
firepower# show eigrp traffic
EIGRP-IPv4 Traffic Statistics for AS(100)
Hellos sent/received: 16606/6989
Updates sent/received: 8/4
Queries sent/received: 2/0
Replies sent/received: 0/1
Acks sent/received: 3/5
SIA-Queries sent/received: 0/0
SIA-Replies sent/received: 0/0
Hello Process ID: 4007513056
PDM Process ID: 4007513984
Socket Queue:
Input Queue: 0/2000/2/0 (current/max/highest/drops)





 Feedback
Feedback