Introduction
This document describes how to configure AnyConnect with Radius Authentication on Cisco Security Manager (CSM).
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- CSM 4.23
- AnyConnect configuration
- SSL protocol
Components Used
The information in this document is based on these software and hardware versions:
- CSM 4.23
- ASA 5515
- AnyConnect 4.10.6090
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configuration
Network Diagram
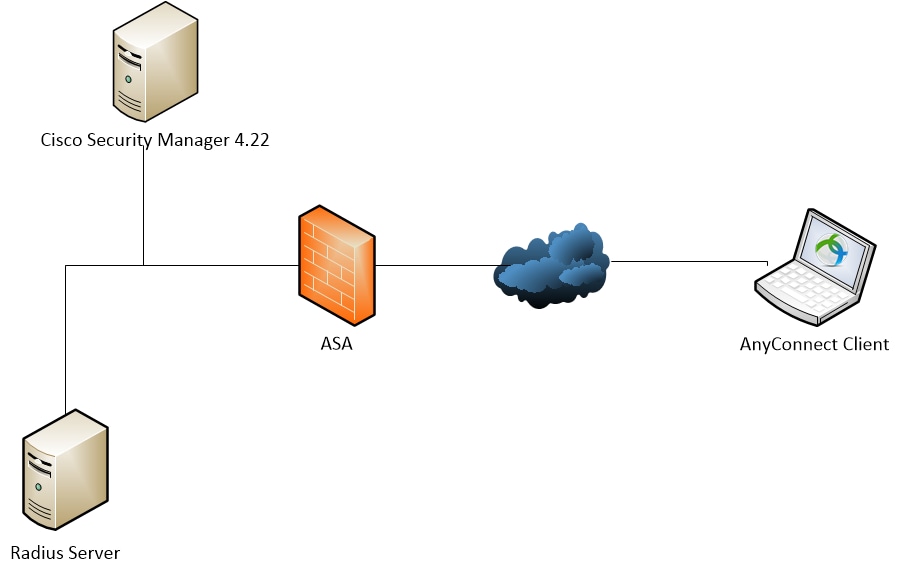 Network Diagram
Network Diagram
Step 1. Configure the SSLVPN Access
Navigate to Policies > SSL VPN > Access:
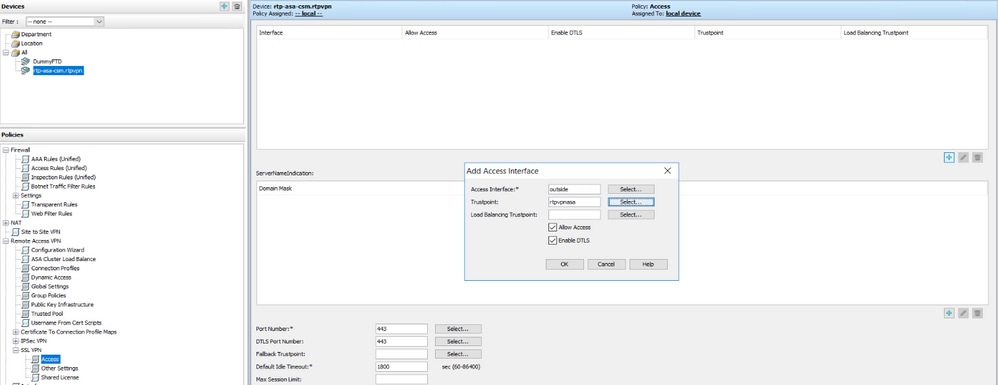 CSM SSL Configuration
CSM SSL Configuration
After configuring the Access Interface, ensure you click Save:
 Save Botton
Save Botton
Step 2. Configure the Authentication Server
Navigate to Policy Object Manager > All Object Types > AAA Servers > Add Add Botton.
Add Botton.
Configure the IP of the server, the source interface, the protocol, and the key:
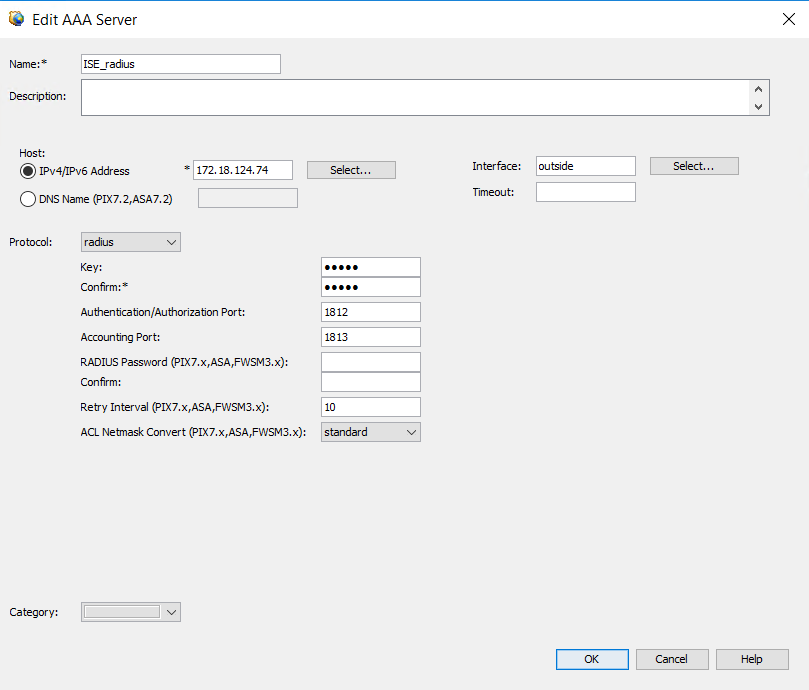 AAA Server Configuration
AAA Server Configuration
Now add the AAA Server, AAA Server Groups > Add  Add Botton.
Add Botton.
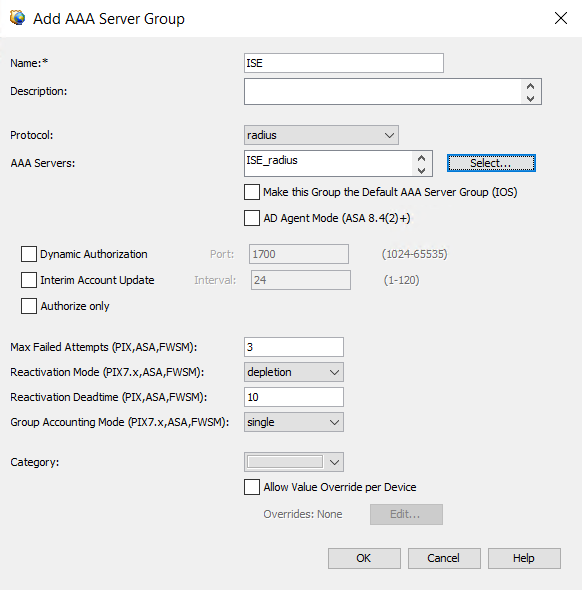 AAA Server Group Configuration
AAA Server Group Configuration
Step 3. Configure the Connection Profile
Navigate to Policies > Connection Profiles > Add Add Botton.
Add Botton.
Here, you must configure the IPv4 Global Address Pool (AnyConnect pool),Group PolicyAAA,and Group Alias/URL:
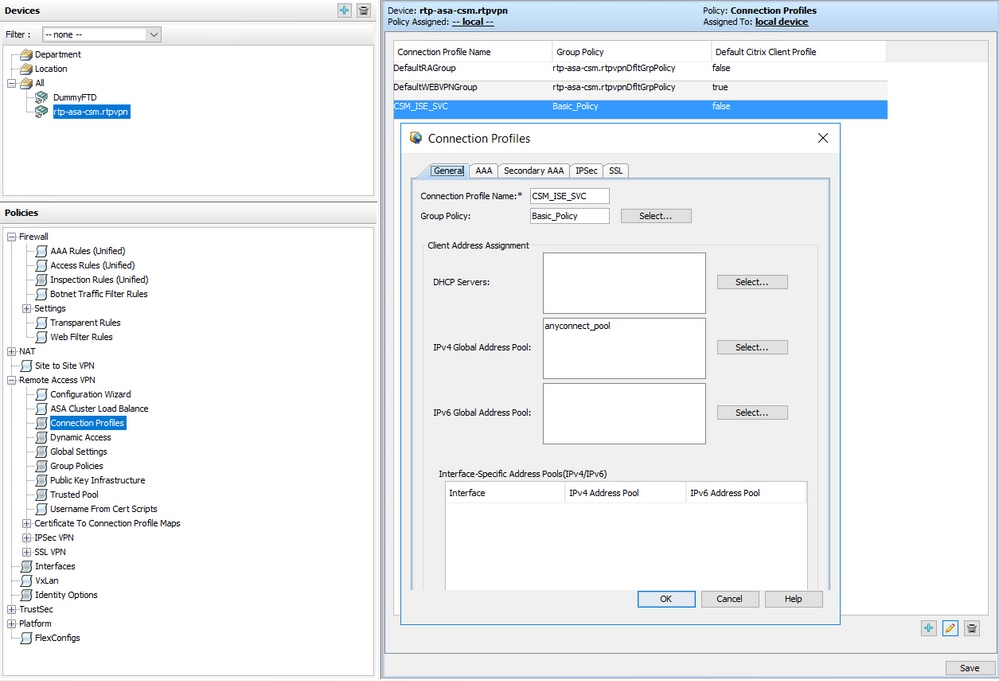 Connection Profile Configuration
Connection Profile Configuration
In order to choose the AAA server, click the AAA tab and choose the server created in Step 2.:
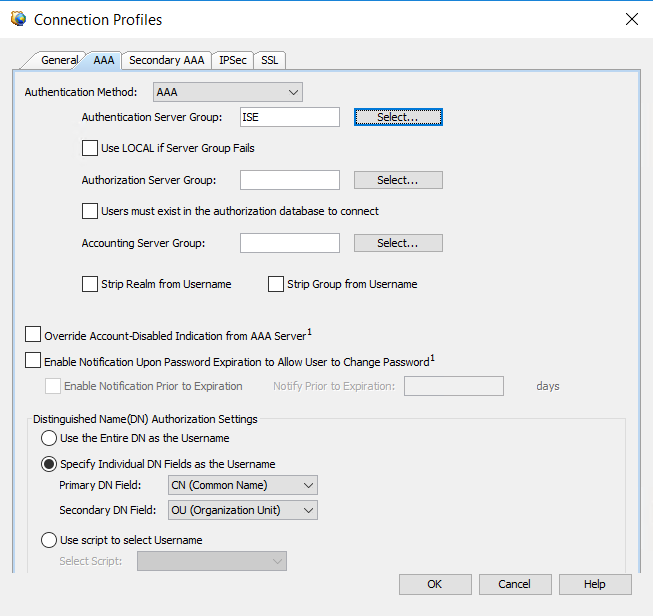 Connection Profile AAA Configuration
Connection Profile AAA Configuration
In order to configure a group alias/group URL, DNS, or WINS server in the connection profile, click the SSL tab:
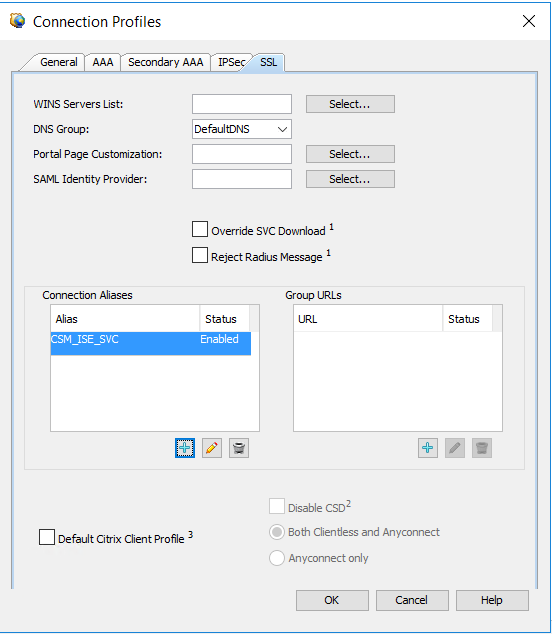 Connection Profile SSL Configuration
Connection Profile SSL Configuration
Step 4. Deploy
Click the deploy icon Deploy Botton.
Deploy Botton.
Verify
This section provides information you can use in order to verify your configuration.
Through CSM:
Navigate toHealth and Performance Monitor > Tools > Device Selector > Select the ASA > Next > Select Remote Access Users.
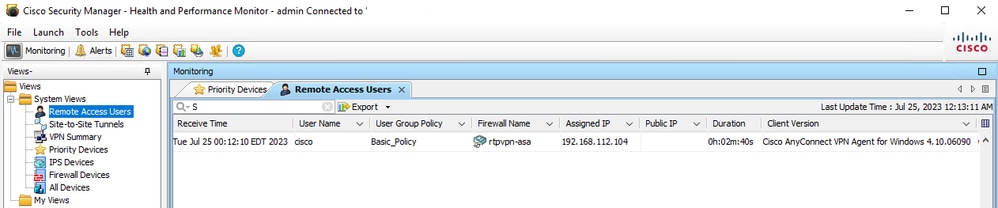 HPM Monitor
HPM Monitor

Note: The VPN user shows up based on the HPM refresh timer.
Through CLI:
ASA#show vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : cisco Index : 23719
Assigned IP : 192.168.10.1 Public IP : 209.165.201.25
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES-GCM-256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA384
Bytes Tx : 15856 Bytes Rx : 3545
Group Policy : Basic_Policy Tunnel Group : CSM_ISE_SVC
Login Time : 02:29:42 UTC Tue Jul 25 2023
Duration : 0h:01m:16s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 0e26864905ca700064bf3396
Security Grp : none
Troubleshoot
In order to check possible failures during the LDAP authentication or the anyconnect establishment, you can execute these commands on the CLI:
debug radius all
debug webvpn anyconnect 255














 Feedback
Feedback