802.1x Host and Session Authentication on Sx500 Series Stackable Switches
Available Languages
Objectives
802.1X is an IEEE standard for Port based Network Access Control (PNAC). This networking protocol provides an authentication method to devices that are connected to the ports. 802.1x has three parts: the supplicant, which is a client device that provides credentials to the network device; the authenticator, which is the network device that can include Ethernet switches or wireless access points; and the authentication server, which typically is a host running software supporting the networking protocols.
Host and Session Authentication defines what 802.1x mode a specified port uses. The three modes are single host, multiple hosts, and multiple sessions. Single host mode only allows one authorized host to access the port. Multiple hosts mode only requires the first host to be authorized. Then all other hosts are allowed access. Multiple sessions allows for multiple hosts. In multiple sessions mode each host must be authorized. If single host mode is selected, violation settings can be enforced.
This article explains how to configure Host and Session Authentication on the Sx500 Series Stackable Switches.
Applicable Devices
• Sx500 Series Stackable Switches
Software Version
• 1.2.7.76
Host and Session Authentication
Step 1. Log in to the web configuration utility and choose Security > 802.1X > Host and Session Authentication. The Host and Session Authentication page opens.


Step 2. Click the radio button of the port you want to modify and click Edit.

Step 3. (Optional) From the Unit/Slot and Port drop-down lists choose the port to configure. The unit identifies whether the switch is active or a member in the stack. The slot identifies which switch is connected to which slot (slot 1 is SF500 and slot 2 is SG500).
If you are unfamiliar with the terms used, check out Cisco Business: Glossary of New Terms.

Step 4. Click the radio button that corresponds to the desired authentication mode in the Host Authentication field.
• Single Host — Only a single authorized host can access the port.
• Multiple Host (802.1X) — Multiple hosts can be attached to a single 802.1x enabled port. Only the first host must be authorized, then all other hosts have access to the network. If the host authentication fails for the first host, all attached clients are denied access to the network.
• Multiple Sessions — Multiple hosts can be attached to a single 802.1x enabled port. Each host must be authenticated.
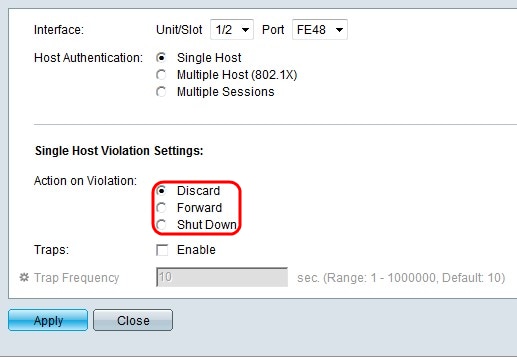
Step 5. If Single Host is selected in Step 4, click the radio button that corresponds to the desired action in the Action on Violation field. This action determines what will happen to the packets arriving to the host if a violation occurs. A violation occurs if the host does not pass the authentication process.
• Discard — Discards the packets.
• Forward — Forwards the packets.
• Shut Down — Discards the packets and shuts down the port. The port remains down until reactivated or until the switch is rebooted.

Step 6. Check Enable in the Traps field to enable traps. Traps are generated SNMP messages used to report system events. The trap will force the connected device to send a SNMP message to the single host that a violation has occurred. To know about the configuration of SNMP trap refer to the article, Configuration of SNMP Trap Settings on Sx500 Series Stackable Switches.

Step 7. Enter the desired time allowed between sent traps in the Trap Frequency field. This field defines how often traps are sent to the host.
Step 8. Click Apply.
If you would like more information on 802.1x Prot Authentication on your Cisco Switch, click on one of the following links:
- Configure 802.1x Port Authentication Setting on a Switch
- Cisco 500 Series Stackable Managed Switch Administration Guide
- Security Configuration on Sx500 Series Switches (Contains links to several articles)
 Feedback
Feedback