Catalyst 6500/6000 Switches NetFlow Configuration and Troubleshooting
Available Languages
Contents
Introduction
This document provides an example to configure NetFlow on the Catalyst 6500/6000 Switch that runs Native IOS or Hybrid OS. It can be necessary to monitor the traffic that flows through the Catalyst 6500/6000 when it acts as a core device in the network.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:
-
Catalyst 6500 with Supervisor Engine 32, MSFC2A and PFC3
-
Catalyst 6500 that runs Cisco IOS? Software Release 12.2(18)SXF4
Note: Netflow configurations are also supported on Route Switch Processor 720, Supervisor Engine 720. There is no difference between Supervisor Engine 720 and Route Switch Processor 720 as far as NetFlow is concerned. So the same configuration applies for both for Supervisor Engine 720 and Route Switch Processor 720.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Background Information
NetFlow is a Cisco IOS application that provides statistics on packets that flow through the router. NetFlow collects statistics globally from traffic that flows through the switch and stores the statistics in the NetFlow table. You can use the command line to access the NetFlow table. You can also export the NetFlow statistics to a reporting server which is called a NetFlow collector. You need to configure NetFlow Data Export (NDE) on the switch in order to export the NetFlow statistics to a NetFlow collector. Netflow will only monitor traffic that is CEF/Fast-switched. To enable fast switching enter the ip route-cache command to the interfaces that are need to be monitored.
There are few points you should know before you configure NetFlow:
-
The NetFlow cache on the Multilayer Switch Feature Card (MSFC) captures statistics for flows routed in software.
-
The NetFlow cache on the Policy Feature Card (PFC) captures statistics for flows routed in hardware.
-
A flow mask defines the format of a cache entry in the NetFlow cache table. There are a few types of flow masks supported by PFC, and NetFlow uses only one flow mask for all statistics. You can configure the flow mask type depending on your requirement. This is the list of flow masks available in the PFC:
-
source-only—A less-specific flow mask. The PFC maintains one entry for each source IP address. All flows from a given source IP address use this entry.
-
destination—A less-specific flow mask. The PFC maintains one entry for each destination IP address. All flows to a given destination IP address use this entry.
-
destination-source—A more-specific flow mask. The PFC maintains one entry for each source and destination IP address pair. All flows between same source and destination IP addresses use this entry.
-
destination-source-interface—A more-specific flow mask. Adds the source VLAN Simple Network Management Protocol (SNMP) ifIndex to the information in the destination-source flow mask.
-
full—A more-specific flow mask. The PFC creates and maintains a separate cache entry for each IP flow. A full entry includes the source IP address, destination IP address, protocol, and protocol interfaces.
-
full-interface—The most-specific flow mask. Adds the source VLAN SNMP ifIndex to the information in the full-flow mask.
-
-
NDE on the PFC supports NDE versions 5 and 7 for the statistics captured on the PFC.
Note: In PFC3B or PFC3BXL mode with Cisco IOS Software Release 12.2(18)SXE and later, you can configure NDE in order to collect statistics for both routed and bridged traffic. In PFC3A mode or with releases earlier than Cisco IOS Software Release 12.2(18)SXE, NDE collects statistics only for routed traffic.
Configure
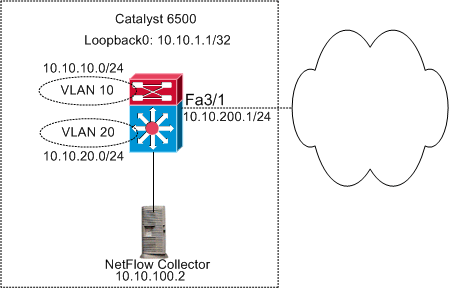
The configuration example in this section shows how to configure NetFlow on the switch and how to configure NDE in order to export the NetFlow cache to the NetFlow collector. It also discusses the optional parameters which can be used to tune NetFlow to suit your network. In this example, the Catalyst 6500 Switch has two VLANs, 10 and 20, for the inside of the network. The interface fa3/1 is connected to the outside of the network.
In this section, you are presented with the information to configure the features described in this document.
Note: The configuration of Netflow neither disrupts the traffic nor disables the configured interface.
Network Diagram
This document uses this network setup:
Configurations in Native IOS
This document uses these configurations:
Enable NetFlow
The first step to configure NetFlow in your network is to enable NetFlow in both the MSFC and PFC. This example shows the step-by-step process on how to enable NetFlow:
-
Enable Netflow on the PFC.
-
Configure flow mask on the PFC.
-
Enable NetFlow on the MSFC.
-
Enable NetFlow for Layer 2-switched traffic on the PFC.
| Switch |
|---|
Switch(config)#interface Vlan10 Switch(config-if)#ip address 10.10.10.1 255.255.255.0 Switch(config-if)#exit Switch(config)#interface Vlan20 Switch(config-if)#ip address 10.10.20.1 255.255.255.0 Switch(config-if)#exit Switch(config)#interface loopback 0 Switch(config-if)#ip address 10.10.1.1 255.255.255.255 Switch(config-if)#exit Switch(config)#interface fastEthernet 3/1 Switch(config-if)#no switchport Switch(config-if)#ip address 10.10.200.1 255.255.255.0 Switch(config-if)#exit !--- This configuration shows that !--- the VLANs are configured with IP addresses. ! Switch(config)#mls netflow !--- Enables NetFlow on the PFC. ! Switch(config)#mls flow ip full !--- Configures flow mask on the PFC. !--- In this example, flow mask is configured as full. ! Switch(config)#interface Vlan10 Switch(config-if)#ip route-cache flow Switch(config-if)#exit Switch(config)#interface Vlan20 Switch(config-if)#ip route-cache flow Switch(config-if)#exit Switch(config)#interface fastEthernet 3/1 Switch(config-if)#ip route-cache flow Switch(config-if)#exit !--- Enables NetFlow on the MSFC. Switch(config)#ip flow ingress layer2-switched vlan 10,20 !--- Enables NetFlow for Layer 2-switched traffic on the PFC. !--- It also enables the NDE for Layer 2-switched traffic on the PFC. |
Configure NDE
NetFlow maintains the active NetFlow in the NetFlow cache table. You can issue the show mls netflow ip command in order to view the active NetFlow cache in the switch. Once the NetFlow cache expires, you no longer see the NetFlow traffic that uses the command line. You can export the expired NetFlow cache to the NetFlow data collector. If you use the NetFlow data collector to store the historical NetFlow traffic, you need to configure the NDE on the Catalyst 6500 Switch. There are many NetFlow collectors available. This includes Cisco NetFlow Collector and Cisco CS-Mars. It is not necessary for the NDE sender version be the same as the ip-flow export version because the NDE sender is about Layer 2 traffic and ip route-cache flow is about Layer 3 traffic.You can see the list of NetFlow collectors in Table 2 of Introduction to Cisco IOS NetFlow - A Technical Overview. This section explains the NDE configuration on the Catalyst 6500 Switch.
-
Configure NDE on the PFC.
-
Configure NDE on the MSFC.
-
Enable NDE for Layer 2-switched traffic on the PFC.
| Switch |
|---|
Switch(config)#mls nde sender version 5 !--- Configures NDE in the PFC. This example configures NDE version 5. !--- You need to configure the version based on your NetFlow collector. !--- The mls nde sender command configures !--- the NDE with default version 7. If your NetFlow collector supports !--- version 7 NDE format, you need to issue the !--- mls nde sender command. ! Switch(config)#ip flow-export source loopback 0 Switch(config)#ip flow-export destination 10.10.100.2 9996 !--- Configures NDE on the MSFC with the NetFlow collector IP address !--- and the application port number 9996. This port number varies !--- depending on the NetFlow collector you use. Switch(config)#ip flow export layer2-switched vlan 10,20 !--- Enabling ip flow ingress as in the Enable NetFlow Section !--- automatically enables ip flow export. !--- If you disabled ip flow export earlier, you can enable it as mentioned. !--- Show run does not show the ip flow export command. |
Optional Configuration
There are few optional configurations available in NetFlow. This depends on your network design, the amount of traffic that flows on the network, and your requirement on the NetFlow data. These are brief descriptions of the optional configurations:
-
multilayer switching (MLS) aging—If the NetFlow traffic is active, the NetFlow cache does not expire. If it does not expire, the NetFlow cache does not export to the NetFlow data collector. In order to ensure periodic reporting of continuously active flows, entries for continuously active flows expire at the end of the interval which is configured with the mls aging long command (default 32 minutes). This output shows the default mls cache aging interval:
asnml-c6509-01#show mls netflow aging enable timeout packet threshold ------ ------- ---------------- normal aging true 300 N/A fast aging false 32 100 long aging true 1920 N/A -
NetFlow sampling—By default, NetFlow captures all the packets in the flow. When you use NetFlow sampling, you can capture a subset of packets. NetFlow sampling can be enabled either as time-based or packet-based.
-
NetFlow aggregation—Aggregation cache is an additional NetFlow cache table in the switch that has the aggregated flow statistics of the NetFlow traffic. The Catalyst 6500 has different schemes such as source prefix, destination prefix, and protocol port for NetFlow aggregation. You can configure more than one scheme in the switch and you can use NDE in order to export the statistics to the NetFlow collector. NetFlow aggregation caches reduce the bandwidth required between the switch and the NetFlow collector.
-
NDE flow filters—You can configure an NDE flow filter to export only interested NetFlow cache. After you configure a filter, only expired and purged flows that match the specified filter criteria are exported. You can filter the NetFlow cache entry based on the source address, destination address, source port, and destination port.
-
NetFlow Cache Entries—You can increase or decrease number of NetFlow entries in the NetFlow cache.
This section explains the optional configuration. This configuration varies depending on your requirement.
-
Configure MLS aging
-
Configure NetFlow sampling
-
Configure NetFlow aggregation
-
Configure NDE flow filter
-
Configure NetFlow Cache Entries
| Switch |
|---|
Switch(config)#mls aging long 300 !--- Configures the switch to delete the active NetFlow !--- cache entries after 5 minutes. The default value is 32 minutes. ! Switch(config)#mls aging normal 120 !--- Configures the switch to delete the inactive NetFlow !--- cache entries after 2 minutes. The default value is 5 minutes. ! Switch(config)#mls sampling time-based 64 !--- 1 out of 64 packets is sampled for the NetFlow cache. By default, !--- sampling is disabled and every packet is captured into the NetFlow cache. ! Switch(config)#ip flow-aggregation cache protocol-port Switch(config-flow-cache)#cache entries 1024 Switch(config-flow-cache)#cache timeout active 30 Switch(config-flow-cache)#cache timeout inactive 300 Switch(config-flow-cache)#export destination 10.10.100.2 9996 Switch(config-flow-cache)#enabled Switch(config-flow-cache)#exit !--- Configures protocol and port aggregation scheme. ! Switch(config)#mls nde flow exclude protocol tcp dest-port 23 !--- Configures the NDE not to export the traffic with destination port tcp 23. ! Switch(config)#ip flow-cache entries 128000 !--- The change in number of entries take effect after either the next reboot or !--- when netflow is turned off on all interfaces. |
Configurations in Hybrid OS
This section shows a configuration example for the Catalyst 6500 Switch that runs Hybrid OS. The configuration uses the same diagram as in the IOS section. The document uses these configurations:
Enable NetFlow
It is assumed that the VLANs are already created in the supervisor module and the VLAN interface IPs are assigned in the MSFC. Here the NetFlow is enabled both in the supervisor module and in the MSFC. Netflow can only be enabled on Layer 3 interfaces.
| Switch |
|---|
Catos(enable)set mls flow full !--- Enables NetFlow and configures flow mask on the supervisor module. !--- In this example, flow mask is configured as full. ! MSFC(config)#interface Vlan10 MSFC(config-if)#ip route-cache flow MSFC(config-if)#exit MSFC(config)#interface Vlan20 MSFC(config-if)#ip route-cache flow MSFC(config-if)#exit MSFC(config)#interface fastEthernet 3/1 MSFC(config-if)#ip route-cache flow MSFC(config-if)#exit !--- Enables NetFlow on the MSFC. |
Configure NDE
This section shows the NDE configuration on both the supervisor module and MSFC. In this example, VLAN 1 is used instead of loopback 0.
| Switch |
|---|
Catos(enable)set mls nde enable Catos(enable)set mls nde version 7 Catos(enable)set mls nde 10.10.100.2 9996 !--- Configures NDE in the supervisor. This example configures NDE version 7. ! MSFC(config)#ip flow-export version 5 MSFC(config)#ip flow-export source vlan 1 MSFC(config)#ip flow-export destination 10.10.100.2 9996 !--- Configures NDE on the MSFC with the NetFlow collector IP address !--- and the application port number 9996. This port number varies !--- depending on the NetFlow collector you use. |
Optional Configuration
This example shows the NetFlow aging time configuration in supervisor module.
| Switch |
|---|
Catos(enable)set mls agingtime long-duration 300 !--- Configures the switch to delete the active NetFlow !--- cache entries after 5 minutes. The default value is 32 minutes. ! Switch(config)#set mls agingtime 120 !--- Configures the switch to delete the inactive NetFlow !--- cache entries after 2 minutes. The default value is 5 minutes. |
Verify
This section shows how to verify the NetFlow cache table and NDE. Also, a sample NetFlow collector output is provided.
The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output.
-
The show mls netflow ip command displays the NetFlow cache entries in the supervisor module. This is a sample output:
Switch#show mls netflow ip Displaying Netflow entries in Supervisor Earl DstIP SrcIP Prot:SrcPort:DstPort Src i/f :AdjPtr ----------------------------------------------------------------------------- Pkts Bytes Age LastSeen Attributes --------------------------------------------------- 10.10.10.100 10.10.10.1 tcp :telnet :2960 -- :0x0 26 1223 101 20:35:41 L2 - Dynamic 10.10.20.2 10.10.20.1 tcp :11837 :179 -- :0x0 6 315 174 20:35:29 L2 - Dynamic 10.10.200.1 10.10.200.2 tcp :21124 :179 -- :0x0 0 0 176 20:35:28 L3 - Dynamic 10.10.20.1 10.10.20.2 tcp :179 :11837 -- :0x0 0 0 174 20:35:29 L3 - Dynamic 171.68.222.140 10.10.10.100 udp :3046 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 10.10.10.100 64.101.128.56 udp :dns :2955 -- :0x0 6 944 178 20:34:29 L3 - Dynamic 10.10.200.2 10.10.200.1 tcp :179 :21124 -- :0x0 5 269 133 20:35:28 L2 - Dynamic 0.0.0.0 0.0.0.0 0 :0 :0 -- :0x0 87 10488 133 20:35:29 L3 - Dynamic 171.68.222.136 10.10.10.100 udp :3047 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 10.10.10.100 171.70.144.201 icmp:0 :0 -- :0x0 1 60 71 20:34:30 L3 - Dynamic 171.68.222.140 10.10.10.100 udp :3045 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 10.10.10.100 64.101.128.92 tcp :3128 :2993 -- :0x0 20 13256 102 20:34:00 L3 - Dynamic 10.10.10.100 171.68.222.140 udp :1029 :3045 -- :0x0 1 368 2 20:35:39 L3 - Dynamic 171.68.222.140 10.10.10.100 icmp:771 :0 -- :0x0 1 176 2 20:35:39 L3 - Dynamic 10.10.10.100 10.16.151.97 udp :1029 :3048 -- :0x0 1 366 2 20:35:39 L3 - Dynamic 10.16.151.97 10.10.10.100 udp :3045 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 171.68.222.136 10.10.10.100 udp :3049 :1029 -- :0x0 2 152 2 20:35:39 L3 - Dynamic 171.68.222.136 10.10.10.100 udp :3045 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 64.101.128.56 10.10.10.100 udp :2955 :dns -- :0x0 6 389 178 20:34:29 L3 - Dynamic 10.10.10.100 171.68.222.136 udp :1029 :3045 -- :0x0 1 366 2 20:35:39 L3 - Dynamic 171.68.222.136 10.10.10.100 udp :3050 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 10.16.151.97 10.10.10.100 udp :3048 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 10.10.10.100 64.101.128.92 tcp :3128 :2991 -- :0x0 15 4889 106 20:34:00 L3 - Dynamic 10.10.10.100 10.16.151.97 udp :1029 :3045 -- :0x0 1 366 2 20:35:39 L3 - Dynamic 171.68.222.140 10.10.10.100 udp :3051 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 10.16.151.97 10.10.10.100 icmp:771 :0 -- :0x0 1 176 2 20:35:39 L3 - Dynamic 10.10.10.100 64.101.128.92 tcp :3128 :2992 -- :0x0 16 7019 106 20:34:00 L3 - Dynamic 10.10.10.100 171.68.222.136 udp :1029 :3047 -- :0x0 1 366 2 20:35:39 L3 - Dynamic 10.16.151.97 10.10.10.100 udp :3052 :1029 -- :0x0 1 46 2 20:35:39 L3 - Dynamic 10.10.10.100 171.68.222.140 udp :1029 :3046 -- :0x0 1 368 2 20:35:39 L3 - Dynamic 10.10.10.1 10.10.10.100 tcp :2960 :telnet -- :0x0 0 0 101 20:35:41 L3 - Dynamic 10.10.10.100 171.68.222.136 udp :1029 :3049 -- :0x0 2 961 2 20:35:39 L3 - Dynamic 171.68.222.136 10.10.10.100 udp :3053 :1029 -- :0x0 2 152 2 20:35:40 L3 - Dynamic 10.10.10.100 171.68.222.136 udp :1029 :3050 -- :0x0 1 366 2 20:35:39 L3 - Dynamic 10.10.10.100 171.68.222.136 udp :1029 :3053 -- :0x0 2 961 1 20:35:40 L3 - Dynamic 10.10.10.100 171.68.222.140 udp :1029 :3051 -- :0x0 1 368 2 20:35:39 L3 - Dynamic 10.10.10.100 10.16.151.97 udp :1029 :3052 -- :0x0 1 366 2 20:35:39 L3 - Dynamic 172.22.1.110 10.10.200.1 udp :52039 :9996 -- :0x0 9 876 209 20:35:12 L2 - Dynamic 10.175.52.255 10.10.10.100 udp :137 :137 -- :0x0 3 234 72 20:34:31 L2 - Dynamic 171.70.144.201 10.10.10.100 icmp:8 :0 -- :0x0 1 60 72 20:34:29 L3 - Dynamic
In a production environment, this output is huge. The show mls netflow ip command has a few options to list only the interested traffic. This output shows the list of options:
Switch#show mls netflow ip ? count total number of mls entries destination show entries with destination ip address detail display additional per-flow detail dynamic hardware created netflow statistics entries flow flow module Show for module nowrap no text wrap qos qos statistics source show entries with source ip address sw-installed s/w installed netflow entries | Output modifiers <cr>
-
The show mls nde command displays the NetFlow export information. This information shows which NetFlow collector it exports and the number of packets it exports. This is a sample output:
Switch#show mls nde Netflow Data Export enabled Exporting flows to 10.10.100.2 (9996) Exporting flows from 10.10.1.1 (52039) Version: 5 Layer2 flow creation is enabled on vlan 10,20 Layer2 flow export is enabled on vlan 10,20 Include Filter not configured Exclude Filter not configured Total Netflow Data Export Packets are: 337 packets, 0 no packets, 3304 records Total Netflow Data Export Send Errors: IPWRITE_NO_FIB = 0 IPWRITE_ADJ_FAILED = 0 IPWRITE_PROCESS = 0 IPWRITE_ENQUEUE_FAILED = 0 IPWRITE_IPC_FAILED = 0 IPWRITE_OUTPUT_FAILED = 0 IPWRITE_MTU_FAILED = 0 IPWRITE_ENCAPFIX_FAILED = 0 Netflow Aggregation DisabledIssue the clear mls nde flow counters command in order to clear the NDE statistics.
-
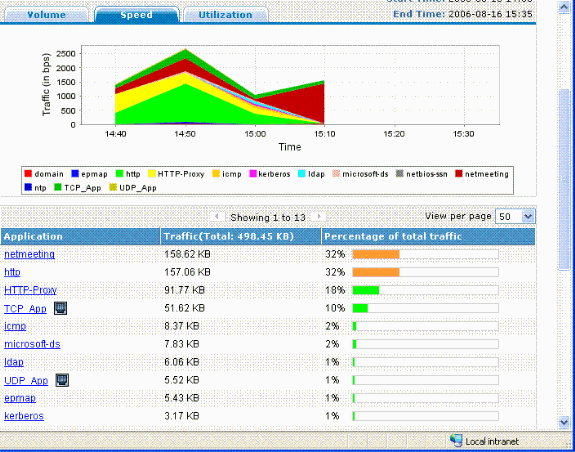
This diagram shows a sample output from a NetFlow collector:
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
There are some points you need to know in order to make sure your configuration works:
-
You must enable NetFlow on the MSFC Layer 3 interfaces in order to support NDE on the PFC, and NDE on the MSFC. You must configure the switch as per the Enable NetFlow section. If you do not need Layer 2 bridged traffic enabled, undo the ip flow ingress layer2-switched command with the no ip flow ingress layer2-switched command.
-
You cannot enable NetFlow on the Network Address Translation (NAT) enabled interfaces if you have configured the full and interface-full flow masks. This means if the interface is configured with either the ip nat inside command or the ip nat outside command and you have configured the full and interface-full flow masks, then you cannot enable NetFlow on the interface. You see this error message:
%FM_EARL7-4-FEAT_FLOWMASK_REQ_CONFLICT: Feature NDE requested flowmask Int f Full Flow Least conflicts with other features on interface Vlan52, flowmask re quest Unsuccessful for the feature
-
The Policy Feature Card 3 (PFC3) and Policy Feature Card 2 (PFC2) do not use the NetFlow table for Layer 3 switching in hardware.
-
NetFlow aggregation uses NDE version 8. You need to make sure your NetFlow collector supports the version 8 format.
Note: NetFlow on the current Cisco Catalyst 6500 Supervisor 720 family is only an ingress interface feature. Cisco IOS Software Release 12.2(33)SXH and later support per-interface NDE, which enables PFC NetFlow data collection on a per-interface basis. With Cisco IOS software releases earlier than Cisco IOS SoftwareEelease 12.2(33)SXH, NetFlow on the PFC can be only be enabled and disabled globally.
-
Netflow must be enabled on the local router in order to perform a Layer 2 analysis.
MLS Aging Disabled
In the Cisco Catalyst 6500 Switches that are run with Native IOS, MLS long aging fails to age the NetFlow cache entries when you enable Server Load Balancing (SLB). This issue is documented in Cisco bug ID CSCea83612 (registered customers only) . Upgrade to the latest Cisco IOS that is not affected by this bug.
NetFlow Displays Traffic in a Single Direction
After you enable NetFlow, the show mls netflow ip command shows only the traffic in a single direction. By default, NetFlow caches only the ingress traffic. Issue the ip route-cache flow command on both the inbound and outbound interfaces in order to cache both inbound and outbound traffic.
NetFlow Does Not Display Switched or Bridged Traffic
By default, NetFlow does not show statistics for traffic going across the same VLAN, but only for traffic that comes in from one VLAN and out to another. For example, VLAN interfaces, when those interfaces have the ip route-cache flow command configured individually.
Note: To view the statistics for traffic going across the same VLAN, disable software switched netflow, i.e. do not configure ip route-cache flow on the layer 3 interface.
In order to enable the creation of switched, bridged, and Layer 2 IP flows for a specific VLAN, issue the ip flow layer2-switched command.
In order to enable the collection of switched, bridged, and IP flows in Layer 2, issue the ip flow ingress layer2-switched vlan {num | vlanlist} command. In order to enable the export of switched, bridged, and IP flows in Layer 2, issue the ip flow export layer2-switched vlan {num | vlanlist} command.
The command is supported on Supervisor Engine 720 in PFC3B and PFC3BXL mode only and on Supervisor Engine 2 with a PFC2.
Before you use this command on Catalyst 6500 Series Switches that are configured with Supervisor Engine 720, you must ensure that a corresponding VLAN interface is available and has a valid IP address. This guideline does not apply to Catalyst 6500 Series Switches that are configured with Supervisor Engine 2. When NetFlow information is exported by the supervisor 720 Engine to the collector for analysis, the tcp flag is set to ZERO. This is due to the hardware limitation of Supervisor 720 as it uses EARL7 ASIC. The support for TCP flag is integrated in EARL8 ASIC.
Source IP address and Destination IP address are not seen in IP Flow
These are the reasons for IP Flow does not show the source and destination IP address.
-
The packets are blocked by an ACL.
-
The packets are being process switched.
-
Multicast traffic
-
Packets destined for the router
-
Tunnels (IPIP, GRE, IPSEC, L2TP) & WCCP
-
Static route to null0
-
DstIf is NULL when the traffic is dropped because of CAR.
In order to avoid this issue, use the ip flow ingress infer-fields command in order to enable Netflow with inferred input/output interfaces and source/destination informations.
If the flows on the subinterfaces are need to be checked, then there are two options:
-
Configure ip route-cache flow in the main interface. This sends the flows from all the subinterfaces.
-
Configure ip flow ingress on the subinterfaces, which in this case, the main interface does not have any netflow configuration, and it sends the flow from each subinterface where the ip flow ingress command is enabled.
Support for Bridged-Flow Statistics on VLANs
This feature is supported on the Supervisor Engine 1 or 1A/PFC, Supervisor Engine 2/PFC2 and no MSFC/MSFC2 is required. This feature is supported on the Supervisor 720/PFC3BXL with limited functionality from Cisco Catalyst OS 8.5(1) or later releases.
Use the set mls bridged-flow-statistics command in order to enable or disable the bridged-flow statistics for the specified VLANs. You can enter one or multiple VLANs. You can enable the NetFlow table entry creation on a per-VLAN basis. But, because the bridged-flow statistics and per-VLAN entry creation use the same mechanism for the collection of the statistics, the VLAN entries can overlap.
Incorrect BGP_NEXTHOP in NetFlow
If the NetFlow BGP Next Hop is configured to support for Accounting and Analysis, then the BGP Next Hop is different than the normal next hop.
The NetFlow cache does not capture the BGP Next Hop when the route to that BGP Next Hop is recursively load-shared through several IGP links. Instead, the NetFlow cache captures the effective simple next hop from a random selection of the load-shared routes to which the BGP route recurses. Therefore, the NetFlow BGP Next Hop is not supported when you have recursive load sharing links.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
01-Dec-2013 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)

 Feedback
Feedback