Introduction
This document describes the Ethanalyzer, a Cisco NX-OS integrated packet capture tool for control packets based upon Wireshark.
Background Information
Wireshark is an open-source, network protocol analyzer widely used across many industries and educational institutions. It decodes packets captured by libpcap, the packet capture library. Cisco NX-OS runs on top of the Linux kernel, which uses the libpcap library in order to support packet capture.
With Ethanalyzer, you can:
- Capture packets sent or received by the Supervisor.
- Set the number of packets to be captured.
- Set the length of the packets to be captured.
- Display packets with summary or detailed protocol information.
- Open and save packet data captured.
- Filter packets captured on many criteria.
- Filter packets to be displayed on many criteria.
- Decode the internal 7000 header of the control packet.
Ethanalyzer cannot:
- Warn you when your network experiences problems. However, Ethanalyzer can help you determine the cause of the problem.
- Capture data plane traffic that is forwarded in hardware.
- Support interface-specific capture.
Output Options
This is a summary view of output from the ethanalyzer local interface inband command. The ? option displays help.
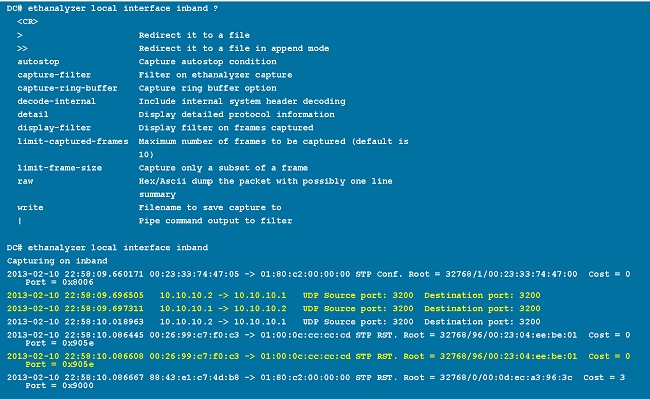
Use the detail option for detailed protocol information. ^C can be used to abort and get the switch prompt back in the middle of a capture if required.
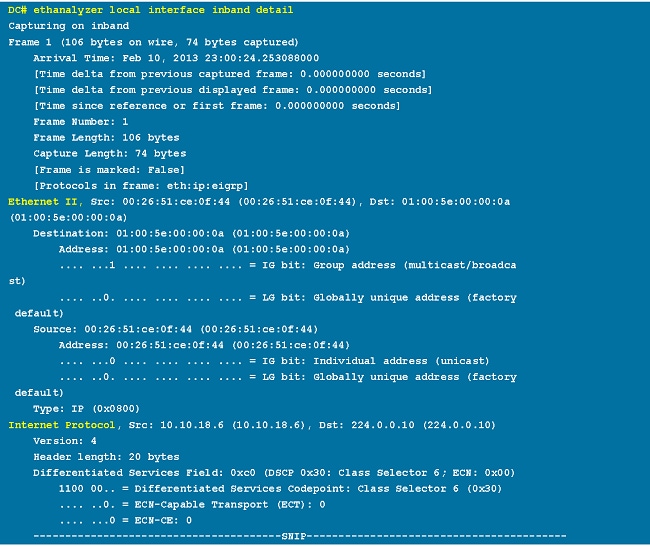
Filter Options
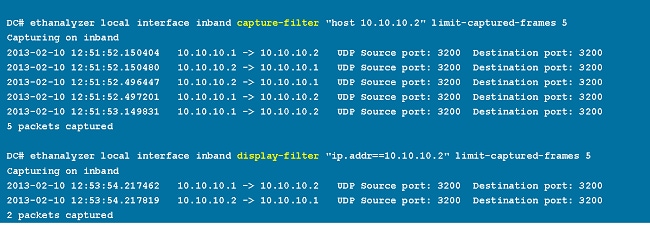
Capture-Filter
Use the capture-filter option in order to select which packets to display or save to disk during capture. A capture filter maintains a high rate of capture while it filters. Because full dissection has not been done on the packets, the filter fields are predefined and limited.
Display-Filter
Use the display-filter option in order to change the view of a capture file (tmp file). A display filter uses fully dissected packets, so you can do very complex and advanced filtering when you analyze a network tracefile. However, the tmp file can fill quickly since it first captures all packets and then displays only the desired packets.
In this example, limit-captured-frames is set to 5. With the capture-filter option, Ethanalyzer shows you five packets which match the filter host 10.10.10.2. With the display-filter option, Ethanalyzer first captures five packets then displays only the packets that match the filter ip.addr==10.10.10.2.
Write Options
Write
The write option lets you write the capture data to a file in one of the storage devices (such as bootflash or logflash) on the Cisco Nexus 7000 Series Switch for later analysis. The capture file size is limited to 10 MB.
An example Ethanalyzer command with a write option is ethanalyzer local interface inband write bootflash: capture_file_name. An example of a write option with capture-filter and an output file name of first-capture is:
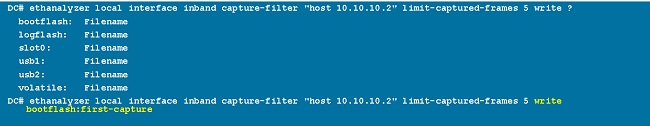
When the capture data is saved to a file, the captured packets are, by default, not displayed in the terminal window. The display option forces Cisco NX-OS to display the packets while it saves the capture data to a file.
Capture-Ring-Buffer
The capture-ring-buffer option creates multiple files after a specified number of seconds, a specified number of files, or a specified file size. Definitions of those options are in this screen shot:
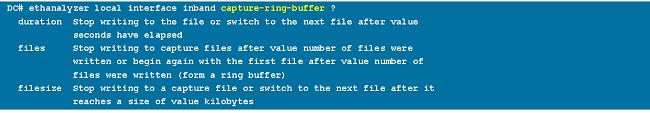
Read Options
The read option lets you read the saved file on the device itself.
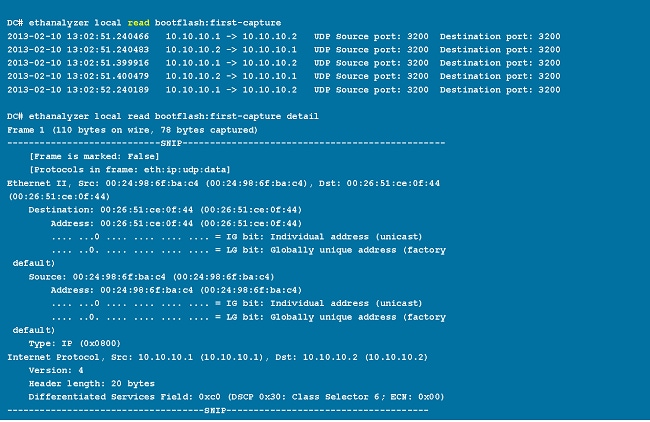
You can also transfer the file to a server or a PC and read it with Wireshark or any other application that can read cap or pcap files.

Decode-Internal with Detail Option
The decode-internal option reports internal information on how the Nexus 7000 forwards the packet. This information helps you understand and troubleshoot the flow of packets through the CPU.

Convert the NX-OS index to hexadecimal, then use the show system internal pixm info ltl x command in order to map the local target logic (LTL) index to a physical or logical interface.
Examples of Capture-Filter Values
Capture Traffic to or from an IP Host
host 10.1.1.1
Capture Traffic to or from a Range of IP Addresses
net 172.16.7.0/24
net 172.16.7.0 mask 255.255.255.0
Capture Traffic from a Range of IP Addresses
src net 172.16.7.0/24
src net 172.16.7.0 mask 255.255.255.0
Capture Traffic to a Range of IP Addresses
dst net 172.16.7.0/24
dst net 172.16.7.0 mask 255.255.255.0
Capture Traffic Only on a Certain Protocol - Capture Only DNS Traffic
DNS is the Domain Name System Protocol.
port 53
Capture Traffic Only on a Certain Protocol - Capture Only DHCP Traffic
DHCP is the Dynamic Host Configuration Protocol.
port 67 or port 68
Capture Traffic Not on a Certain Protocol - Exclude HTTP or SMTP Traffic
SMTP is the Simple Mail Transfer Protocol.
host 172.16.7.3 and not port 80 and not port 25
Capture Traffic Not on a Certain Protocol - Exclude ARP and DNS Traffic
ARP is the Address Resolution Protocol.
port not 53 and not arp
Capture Only IP Traffic - Exclude Lower Layer Protocols like ARP and STP
STP is the Spanning Tree Protocol.
ip
Capture Only Unicast Traffic - Exclude Broadcast and Multicast Announcements
not broadcast and not multicast
Capture Traffic Within a Range of Layer 4 Ports
tcp portrange 1501-1549
Capture Traffic Based on Ethernet Type - Capture EAPOL Traffic
EAPOL is the Extensible Authentication Protocol over LAN.
ether proto 0x888e
IPv6 Capture Workaround
ether proto 0x86dd
Capture Traffic Based on IP Protocol Type
ip proto 89
Reject Ethernet Frames Based on MAC Address - Exclude Traffic That Belongs to the LLDP Multicast Group
LLDP is the Link Layer Discovery Protocol.
not ether dst 01:80:c2:00:00:0e
Capture UDLD, VTP, or CDP Traffic
UDLD is Unidirectional Link Detection, VTP is the VLAN Trunking Protocol, and CDP is the Cisco Discovery Protocol.
ether host 01:00:0c:cc:cc:cc
Capture Traffic to or from a MAC Address
ether host 00:01:02:03:04:05
Note:
and = &&
or = ||
not = !
MAC address format : xx:xx:xx:xx:xx:xx
Common Control Plane Protocols
- UDLD: Destination Media Access Controller (DMAC) = 01-00-0C-CC-CC-CC and EthType = 0x0111
- LACP: DMAC = 01:80:C2:00:00:02 and EthType = 0x8809. LACP stands for Link Aggregation Control Protocol.
- STP: DMAC = 01:80:C2:00:00:00 and EthType = 0x4242 - or - DMAC = 01:00:0C:CC:CC:CD and EthType = 0x010B
- CDP: DMAC = 01-00-0C-CC-CC-CC and EthType = 0x2000
- LLDP: DMAC = 01:80:C2:00:00:0E or 01:80:C2:00:00:03 or 01:80:C2:00:00:00 and EthType = 0x88CC
- DOT1X: DMAC = 01:80:C2:00:00:03 and EthType = 0x888E. DOT1X stands for IEEE 802.1x.
- IPv6: EthType = 0x86DD
- List of UDP and TCP port numbers
Known Issues
Cisco bug ID CSCue48854: Ethanalyzer capture-filter does not capture traffic from CPU on SUP2.
Cisco bug ID CSCtx79409: Cannot use capture filter with decode-internal.
Cisco bug ID CSCvi02546: SUP3 generated packet can have FCS, this is expected behaviour.
Related Information










 Feedback
Feedback