Introduction
Certificate Authority Proxy Function (CAPF) Locally Significant Certificates (LSCs) are locally-signed. However, you might require phones to use third-party Certificate Authority (CA)-signed LSCs. This document describes a procedure that helps you achieve this.
Prerequisites
Requirements
Cisco recommends that you have knowledge of Cisco Unified Communication Manager (CUCM).
Components Used
The information in this document is based on CUCM Version 10.5(2); however, this feature works from Version 10.0 and later.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Configure
Here are the steps involved in this procedure, each of which is detailed in its own section:
- Upload the CA-Root Certificate
- Set Offline CA for Certificate Issue to Endpoint
- Generate a Certificate Signing Request (CSR) for the Phones
- Get the Generated CSR from Cisco Unified Communications Manager (CUCM) to the FTP Server
- Get the Phone Certificate from CA
- Convert .cer to .der Format
- Compress the Certificates (.der) to .tgz Format
- Transfer the .tgz file to the Secure Shell FTP (SFTP) Server
- Import the .tgz File to the CUCM Server
- Sign the CSR With Microsoft Windows 2003 Certificate Authority
- Get the Root Certificate from the CA
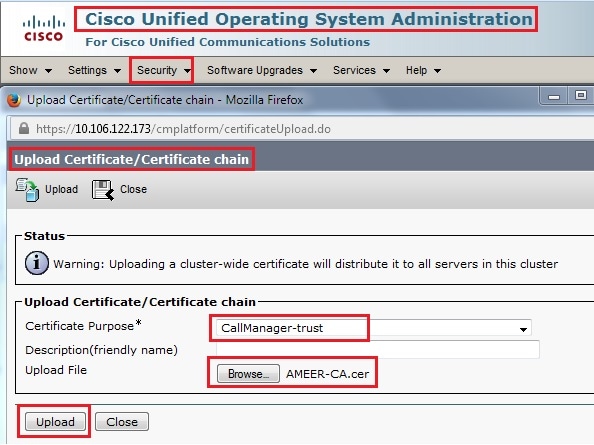
Upload the CA-Root Certificate
- Log into the Cisco Unified Operating System (OS) Administration web GUI.
- Navigate to Security Certificate Management.
- Click Upload Certificate/Certificate chain.
- Choose CallManager-trust under Certificate Purpose.
- Browse to the CA's root certificate and click Upload.
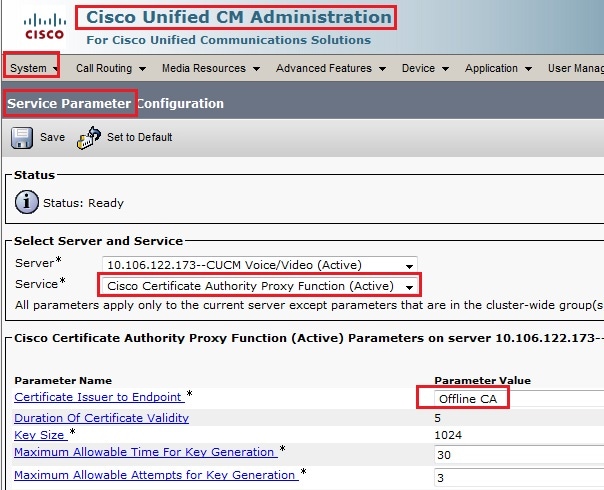
Set Offline CA for Certificate Issue to Endpoint
- Log into the CUCM Administration web GUI.
- Navigate to System > Service Parameter.
- Choose the CUCM Server and select Cisco Certificate Authority Proxy Function for the Service.
- Select Offline CA for Certificate Issue to Endpoint.
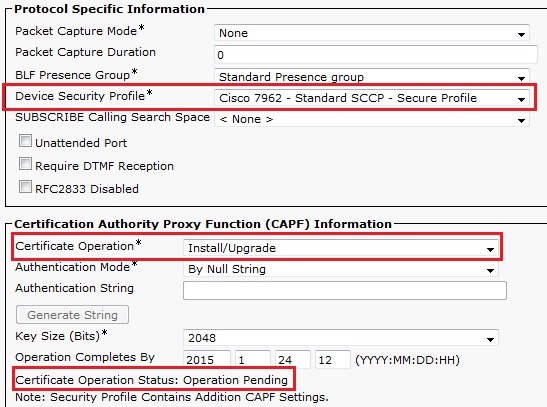
Generate a Certificate Signing Request (CSR) for the Phones
- Log into the CUCM Administration web GUI.
- Navigate to Device Phones.
- Choose the phone whose LSC must be signed by the external CA.
- Change the Device security profile to a secured one (if not present, add one system on the Security Phone Security profile).
- On the phone configuration page, under the CAPF section, choose Install/Upgrade for the Certification Operation. Complete this step for all of the phones whose LSC must be signed by the external CA. You should see Operation Pending for the Certificate Operation Status.
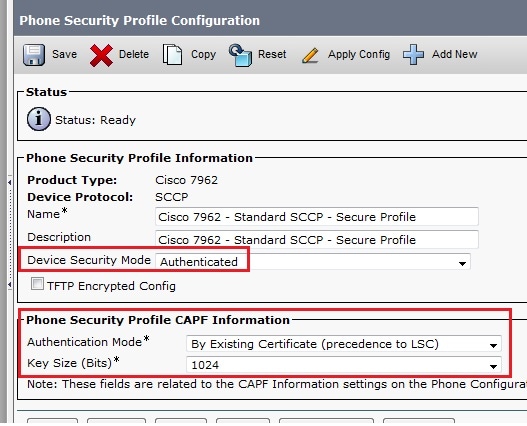
Phone Security profile (7962 model).
Enter the utils capf csr count command in the Secure Shell (SSH) session in order to confirm whether a CSR is generated. (This screen shot shows that a CSR was generated for three phones.)
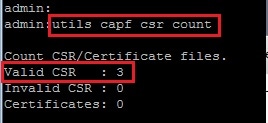
Note: The Certificate Operation Status under the phone's CAPF section remains in the Operation Pending state.
Get the Generated CSR from the CUCM to the FTP (or TFTP) Server
- SSH into the CUCM server.
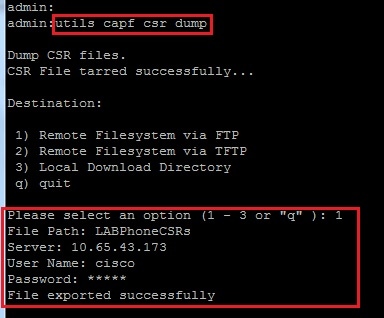
- Execute the utils capf csr dump command. This screen shot shows the dump being transferred to the FTP.
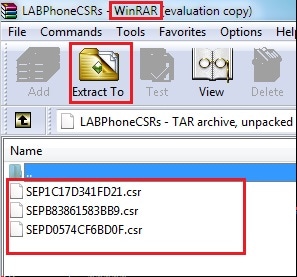
- Open the dump file with WinRAR and extract the CSR to your local machine.
Get the Phone Certificate
- Send the phone's CSRs to the CA.
- The CA provides you with a signed certificate.
Note: You can use a Microsoft Windows 2003 server as the CA. The procedure to sign the CSR with a Microsft Windows 2003 CA is explained later in this document.
Convert .cer to .der Format
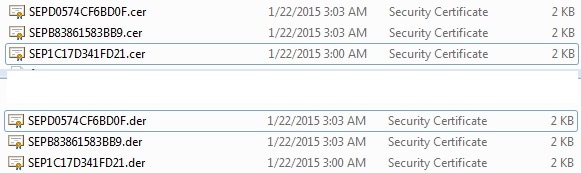
If the received certificates are in .cer format, then rename them to .der.
Compress the Certificates (.der) to .tgz Format
You can use CUCM server's root (Linux) in order to compress the certificate format. You can also do this in a normal Linux system.
- Transfer all of the signed certificates to the Linux system with the SFTP server.
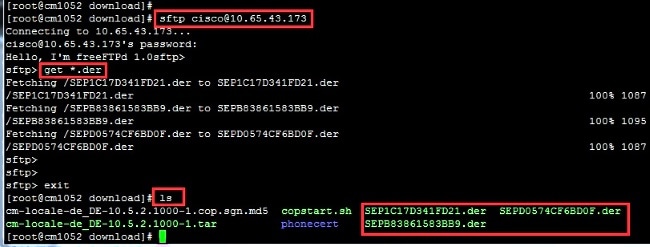
- Enter this command in order to compress all the .der certificates into a .tgz file.
tar -zcvf <file_name>.tgz *.der
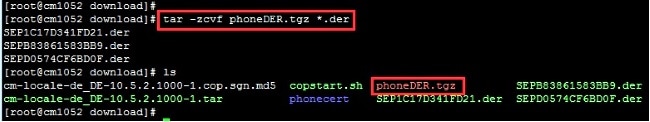
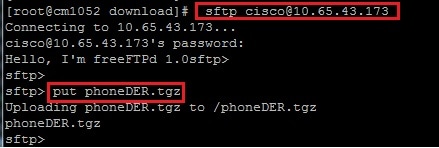
Transfer the .tgz File to the SFTP Server
Complete the steps shown in the screen shot in order to transfer the .tgz file to the SFTP server.
Import the .tgz File to the CUCM Server
- SSH into the CUCM server.
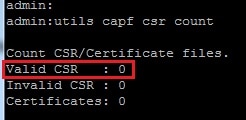
- Execute the utils capf cert import command.

Once the certificates are imported successfully, then you can see the CSR count become zero.
Sign the CSR With Microsoft Windows 2003 Certificate Authority
This is optional information for Microsoft Windows 2003 - CA.
- Open Certification Authority.
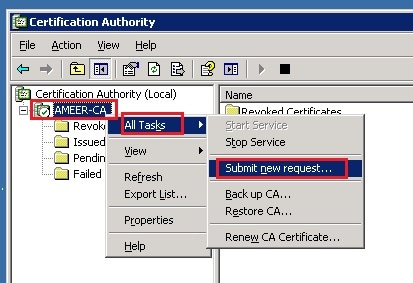
- Right-click the CA and navigate to All Tasks > Submit new request...
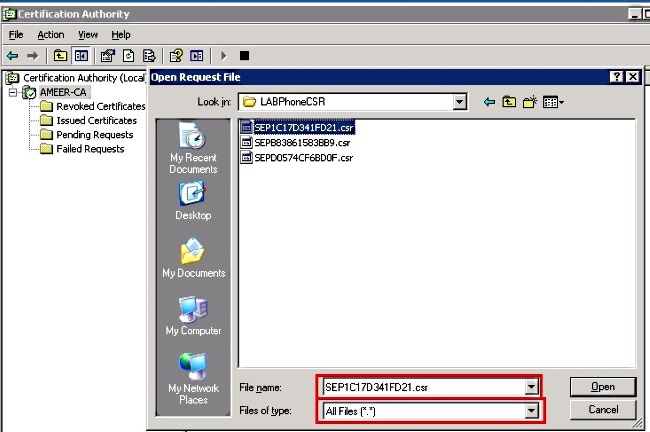
- Select the CSR and click Open. Do this for all the CSRs.
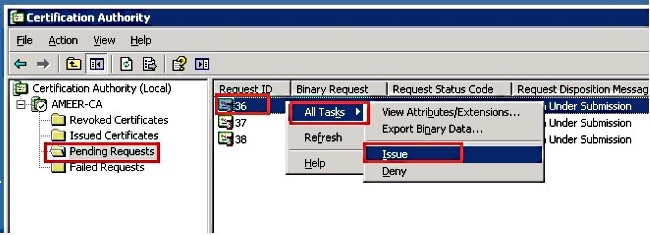
All of the opened CSR display in the Pending Requests folder.
- Right-click each and navigate to All Tasks > Issue in order to issue certificates. Do this for all pending requests.
- In order to download the certificate, choose Issued Certificate.
- Right-click the certificate and click Open.
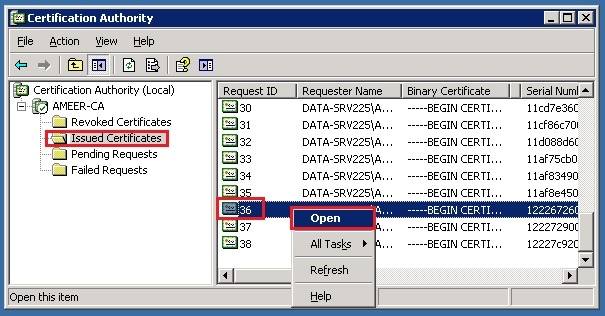
- You can see the certificate details. In order to download the certificate, select the Details tab and choose Copy to File...
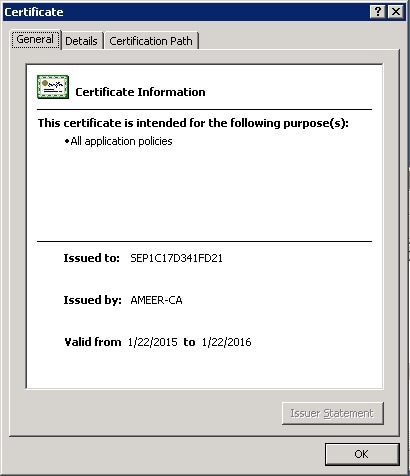
- In the Certificate Export Wizard, choose DER encoded binary X.509 (.CER).
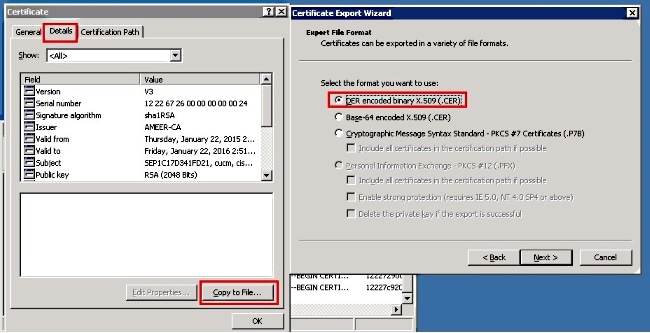
- Name the file something appropriate. This example uses <MAC>.cer format.
- Get the certificates for other phones under the Issued Certificate section with this procedure.
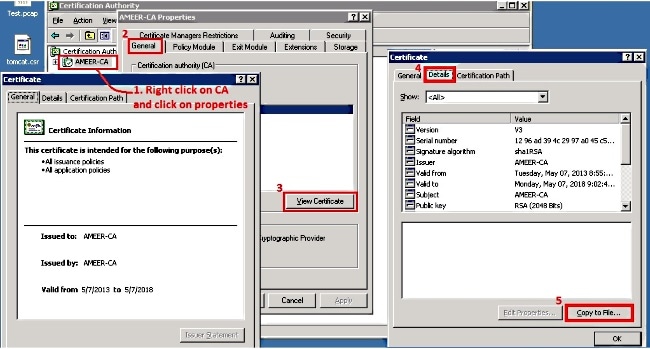
Get the Root Certificate from the CA
- Open Certification Authority.
- Complete the steps shown in this screen shot in order to download the root-CA.
Verify
Use this section in order to confirm that your configuration works properly.
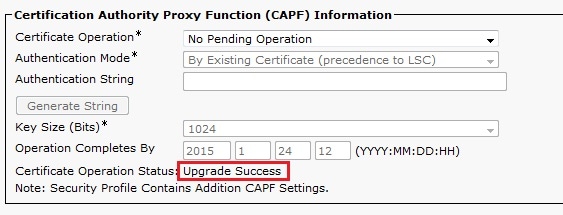
- Go to the phone configuration page.
- Under the CAPF section, the Certificate Operation Status should display as Upgrade Success.
Note: Refer to Generate and Import Third Party CA-Signed LSCs for more information.
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.























 Feedback
Feedback