Wireless BYOD for FlexConnect Deployment Guide
Available Languages
Contents
Introduction
Mobile devices are becoming more computationally powerful and popular among consumers. Millions of these devices are sold to consumers with high-speed Wi-Fi so users can communicate and collaborate. Consumers are now accustomed to the productivity enhancement these mobile devices bring into their lives and are seeking to bring their personal experience into the workspace. This creates the functionality needs of a Bring Your Own Device (BYOD) solution in the workplace.
This document provides the branch deployment for the BYOD solution. An employee connects to a corporate service set identifier (SSID) with his/her new iPad and gets redirected to a self-registration portal. The Cisco Identity Services Engine (ISE) authenticates the user against the corporate Active Directory (AD) and downloads a certificate with an embedded iPad MAC address and username to the iPad, along with a supplicant profile that enforces the use of the Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) as a method for dot1x connectivity. Based on the authorization policy in ISE, the user can then connect with the use of dot1x and gain access to appropriate resources.
ISE functionalities in Cisco Wireless LAN Controller software releases earlier than 7.2.110.0 did not support local switching clients that associate through FlexConnect access points (APs). Release 7.2.110.0 supports these ISE functionalities for FlexConnect APs for local switching and centrally authenticated clients. Furthermore, Release 7.2.110.0 integrated with ISE 1.1.1 provides (but is not limited to) these BYOD solution features for wireless:
- Device profiling and posture
- Device registration and supplicant provisioning
- Onboarding of personal devices (provision iOS or Android devices)
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Catalyst Switchs
- Cisco Wireless LAN (WLAN) Controllers
- Cisco WLAN Controller (WLC) Software Release 7.2.110.0 and later
- 802.11n APs in FlexConnect mode
- Cisco ISE Software Release 1.1.1 and later
- Windows 2008 AD with Certificate Authority (CA)
- DHCP server
- Domain Name System (DNS) server
- Network Time Protocol (NTP)
- Wireless client laptop, smartphone, and tablets (Apple iOS, Android, Windows, and Mac)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Topology
A minimal network setup, as shown in this diagram is required in order to properly implement and test these features:
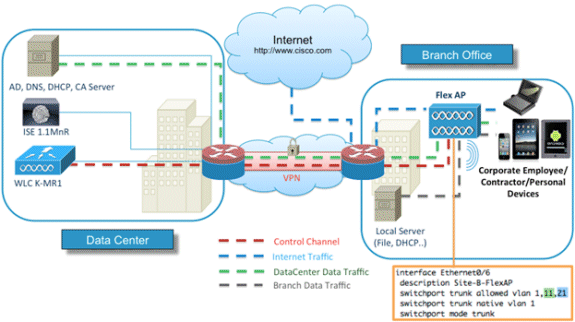
For this simulation, you need a network with a FlexConnect AP, a local/remote site with local DHCP, DNS, the WLC, and the ISE. The FlexConnect AP is connected to a trunk in order to test local switching with multiple VLANs.
Device Registration and Supplicant Provisioning
A device must be registered so that its native supplicant can provisioned for dot1x authentication. Based on the right authentication policy, the user is redirected to the guest page and authenticated by employee credentials. The user sees the device registration page, which asks for their device information. The device provisioning process then begins. If the operating system (OS) is not supported for provisioning, the user is redirected to the Asset Registration Portal in order to mark that device for MAC Authentication Bypass (MAB) access. If the OS is supported, the enrollment process begins and configures the native supplicant of the device for dot1x authentication.
Asset Registration Portal
The Asset Registration Portal is the element of the ISE platform that allows employees to initiate the onboarding of endpoints through an authentication and registration process.
Administrators are able to delete assets from the endpoints identities page. Each employee is able to edit, delete, and blacklist the assets they have registered. Blacklisted endpoints are assigned to a blacklist identity group, and an authorization policy is created in order to prevent network access by blacklisted endpoints.
Self-Registration Portal
In the Central Web Authentication (CWA) flow, employees are redirected to a portal that allows them to enter their credentials, authenticate, and enter the specifics of the particular asset they wish to register. This portal is called the Self Provisioning Portal and is similar to the Device Registration Portal. It allows the employees to enter the MAC address as well as a meaningful escription of the endpoint.
Authentication and Provisioning
Once employees select the Self-Registration Portal, they are challenged to provide a set of valid employee credentials in order to proceed to the provisioning phase. After successful authentication, the endpoint can be provisioned into the endpoints database, and a certificate is generated for the endpoint. A link on the page allows the employee to download the Supplicant Pilot Wizard (SPW).
Provisioning for iOS (iPhone/iPad/iPod)
For EAP-TLS configuration, ISE follows the Apple Over-the-Air (OTA) enrollment process:
- After successful authentication, the evaluation engine evaluates client-provisioning policies, which results in a supplicant profile.
- If the supplicant profile is for the EAP-TLS setting, the OTA process determines whether the ISE is using self-signed or signed by an unknown CA. If one of the conditions is true, the user is asked to download the certificate of either ISE or CA before the enrollment process can begin.
- For other EAP methods, ISE pushes the final profile upon successful authentication.
Provisioning for Android
Because of security considerations, the Android agent must be downloaded from the Android marketplace site and cannot be provisioned from ISE. Cisco uploads a release candidate version of the wizard into the Android marketplace through the Cisco Android marketplace publisher account.
This is the Android provisioning process:
- Cisco uses the Software Development Kit (SDK) in order to create the Android package with a .apk extension.
- Cisco uploads a package into the Android marketplace.
- The user configures the policy in client provisioning with the appropriate parameters.
- After registration of the device, the end user is redirected to the client provisioning service when dot1x authentication fails.
- The provisioning portal page provides a button that redirects user to the Android marketplace portal where they can download the SPW.
- The Cisco SPW is launched and performs provisioning of the supplicant:
- SPW discovers the ISE and downloads the profile from ISE.
- SPW creates a cert/key pair for EAP-TLS.
- SPW makes a Simple Certificate Enrollment Protocol (SCEP) proxy request call to ISE and gets the certificate.
- SPW applies the wireless profiles.
- SPW triggers re-authentication if the profiles are applied successfully.
- SPW exits.
Dual SSID Wireless BYOD Self-Registration
This is the process for dual SSID wireless BYOD self-registration:
- The user associates to the Guest SSID.
- The user opens a browser and is redirected to the ISE CWA Guest Portal.
- The user enters an employee username and password in the Guest Portal.
- ISE authenticates the user, and, based on the fact that they are an employee and not a guest, redirects the user to the Employee Device Registration guest page.
- The MAC address is pre-populated in the Device Registration guest page for the DeviceID. The user enters a description and accepts the Acceptable Use Policy (AUP) if required.
- The user selects Accept and begins to download and install the SPW.
- The supplicant for that user's device is provisioned along with any certificates.
- CoA occurs, and the device reassociates to the corporate SSID (CORP) and authenticates with EAP-TLS (or other authorization method in use for that supplicant).
Single SSID Wireless BYOD Self-Registration
In this scenario, there is a single SSID for corporate access (CORP) that supports both Protected Extensible Authentication Protocol (PEAP) and EAP-TLS. There is no Guest SSID.
This is the process for single SSID wireless BYOD self-registration:
- The user associates to CORP.
- The user enters an employee username and password into the supplicant for the PEAP authentication.
- The ISE authenticates the user, and, based on the PEAP method, provides an authorization policy of accept with redirect to the Employee Device Registration guest page.
- The user opens a browser and is redirected to the Employee Device Registration guest page.
- The MAC address is pre-populated in the Device Registration guest page for the DeviceID. The user enters a description and accepts the AUP.
- The user selects Accept and begins to download and install the SPW.
- The supplicant for that user's device is provisioned along with any certificates.
- CoA occurs, and the device reassociates to the CORP SSID and authenticates with EAP-TLS.
Feature Configuration
Complete these steps in order to begin configuration:
- For this guide, ensure that the WLC version is 7.2.110.0 or later.
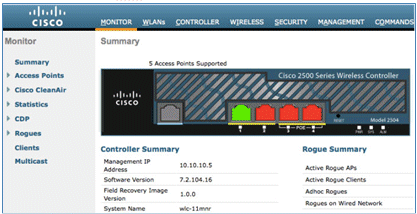
- Navigate to Security > RADIUS > Authentication, and add the RADIUS server to the WLC.
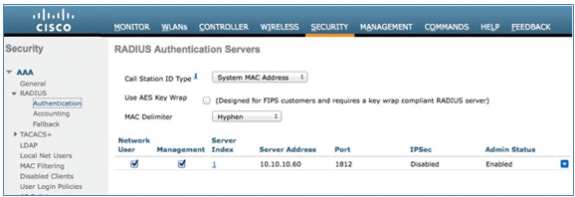
- Add the ISE 1.1.1 to the WLC:
- Enter a Shared Secret.
- Set Support for RFC 3576 to Enabled.
- Add the same ISE server as a RADIUS accounting server.
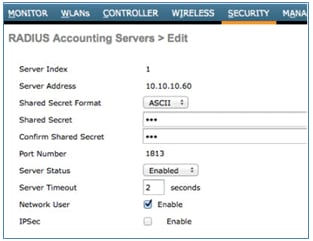
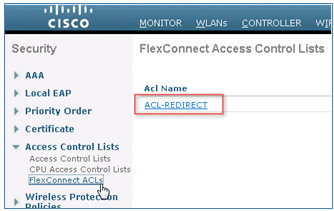
- Create a WLC Pre-Auth ACL to use in the ISE policy later. Navigate to WLC > Security > Access Control Lists > FlexConnect ACLs, and create a new FlexConnect ACL named ACL-REDIRECT (in this example).
- In the ACL rules, permit all traffic to/from the ISE, and permit client traffic during supplicant provisioning.
- For the first rule (sequence 1):
- Set Source to Any.
- Set IP (ISE address)/ Netmask 255.255.255.255.
- Set Action to Permit.
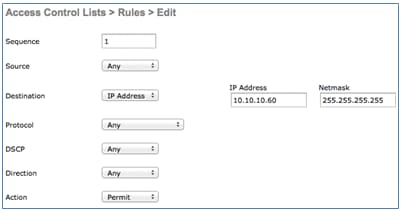
- For the second rule (sequence 2), set source IP (ISE address)/ mask 255.255.255.255 to Any and Action to Permit.
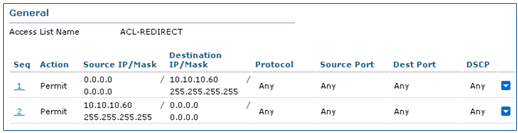
- For the first rule (sequence 1):
- Create a new FlexConnect Group named Flex1 (in this example):
- Navigate to FlexConnect Group > WebPolicies tab.
- Under the WebPolicy ACL field, click Add, and select ACL-REDIRECT or the FlexConnect ACL created previously.
- Confirm that it populates the WebPolicy Access Control Lists field.
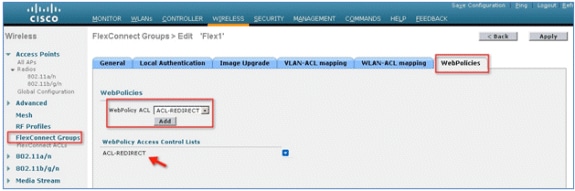
- Click Apply and Save Configuration.
WLAN Configuration
Complete these steps in order to configure the WLAN:
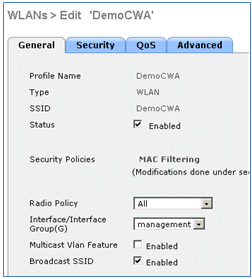
- Create an Open WLAN SSID for the dual SSID example:
- Enter a WLAN name: DemoCWA (in this example).
- Select the Enabled option for Status.
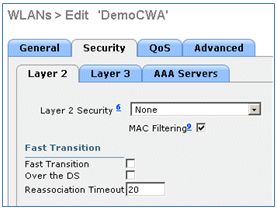
- Navigate to the Security tab > Layer 2 tab, and set these attributes:
- Layer 2 Security: None
- MAC Filtering: Enabled (box is checked)
- Fast Transition: Disabled (box is not checked)
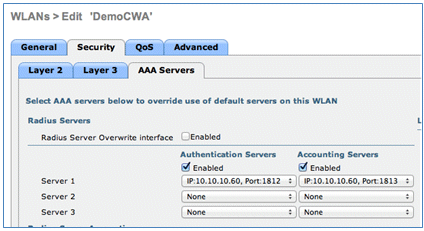
- Go to the AAA Servers tab, and set these attributes:
- Authentication and Account Servers: Enabled
- Server 1: <ISE IP address>
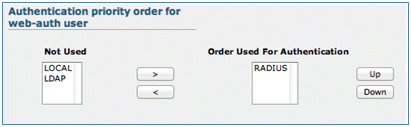
- Scroll down from the AAA Servers tab. Under Authentication priority order for web-auth user, make sure that RADIUS is used for authentication and the others are not used.
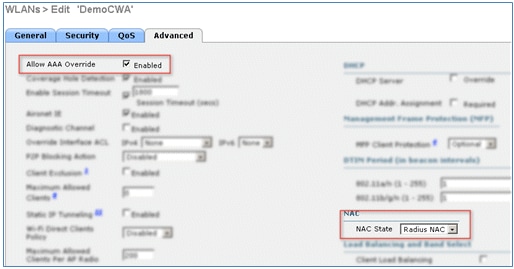
- Go to the Advanced tab, and set these attributes:
- Allow AAA Override: Enabled
- NAC State: Radius NAC
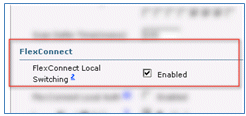
- Scroll down in the Advanced tab, and set FlexConnect Local Switching to Enabled.
- Click Apply and Save Configuration.
- Create a 802.1X WLAN SSID named Demo1x (in this example) for single and dual SSID scenarios.
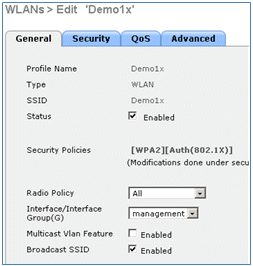
- Navigate to the Security tab > Layer 2 tab, and set these attributes:
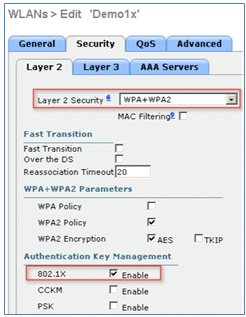
- Layer 2 Security: WPA+WPA2
- Fast Transition: Disabled (box is not checked)
- Authentication Key Management: 802.lX: Enable
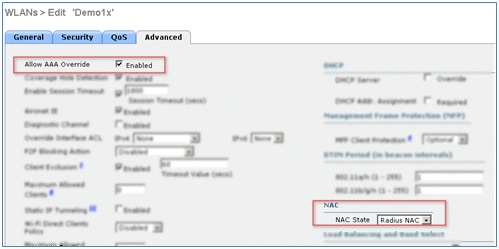
- Go to the Advanced tab, and set these attributes:
- Allow AAA Override: Enabled
- NAC State: Radius NAC
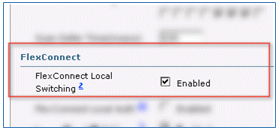
- Scroll down in the Advanced tab, and set FlexConnect Local Switching to Enabled.
- Click Apply and Save Configuration.
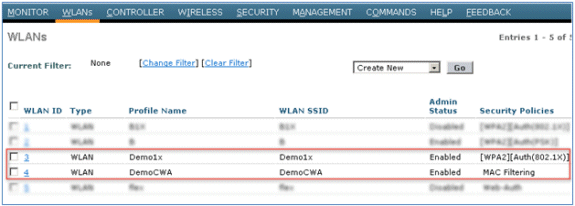
- Confirm that both of the new WLANs were created.
FlexConnect AP Configuration
Complete these steps in order to configure the FlexConnect AP:
- Navigate to WLC > Wireless, and click the target FlexConnect AP.
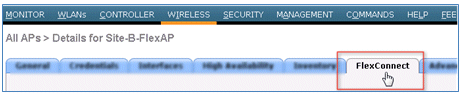
- Click the FlexConnect tab.
- Enable VLAN Support (box is checked), set the Native VLAN ID, and click VLAN Mappings.
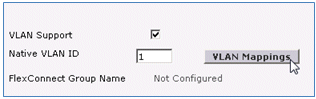
- Set the VLAN ID to 21 (in this example) for the SSID for local switching.
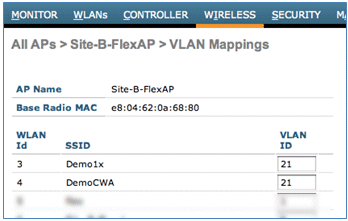
- Click Apply and Save Configuration.
ISE Configuration
Complete these steps in order to configure the ISE:
- Log in to the ISE server: <https://ise>.
- Navigate to Administration > Identity Management > External Identity Sources.
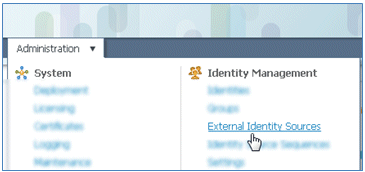
- Click Active Directory.
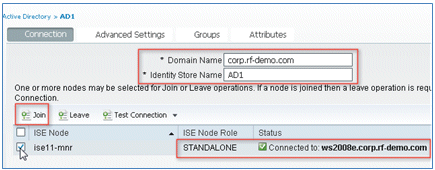
- In the Connection tab:
- Add the Domain Name of corp.rf-demo.com (in this example), and change the Identity Store Name default to AD1.
- Click Save Configuration.
- Click Join, and provide the AD Administrator account username and password required to join.
- The Status must be green. Enable Connected to: (box is checked).
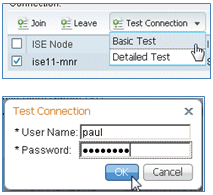
- Perform a basic connection test to the AD with a current domain user.
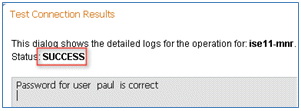
- If the connection to the AD is successful, a dialog confirms that the password is correct.
- Navigate to Administration > Identity Management > External Identity Sources:
- Click Certificate Authentication Profile.
- Click Add for a new Certificate Authentication Profile (CAP).
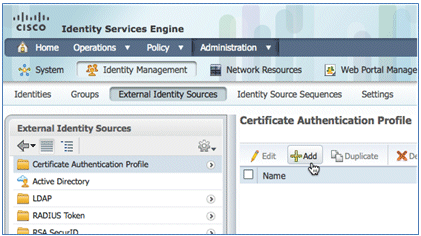
- Enter a name of CertAuth (in this example) for the CAP; for the Principal Username X509 Attribute, select Common Name; then, click Submit.
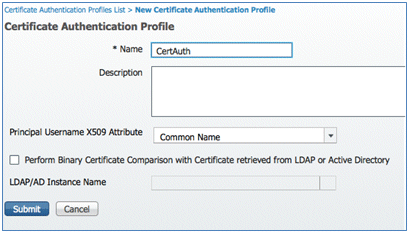
- Confirm that the new CAP is added.
- Navigate to Administration > Identity Management > Identity Source Sequences, and click Add .
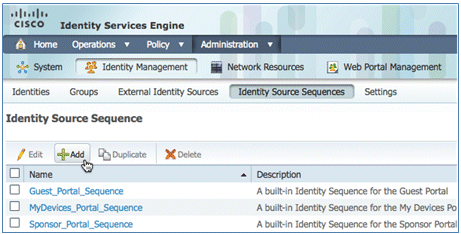
- Give the sequence a name of TestSequence (in this example).
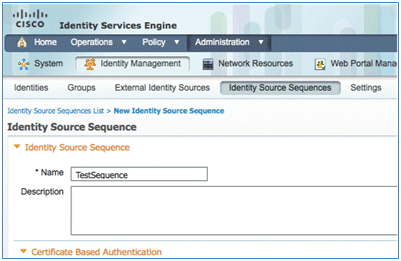
- Scroll down to Certificate Based Authentication:
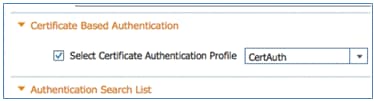
- Enable Select Certificate Authentication Profile (box is checked).
- Select CertAuth (or another CAP profile created earlier).
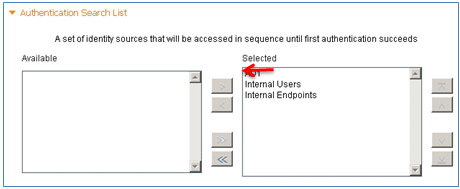
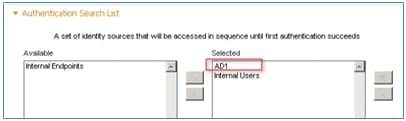
- Scroll down to Authentication Search List:
- Move AD1 from Available to Selected.
- Click the up button in order to move AD1 to the top priority.
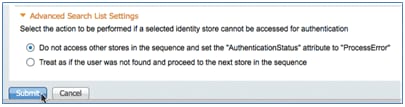
- Click Submit in order to save.
- Confirm that the new Identity Source Sequence is added.
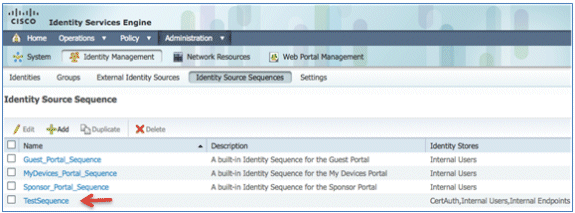
- Use the AD in order to authenticate the My Devices Portal. Navigate to ISE > Administration > Identity Management > Identity Source Sequence, and edit MyDevices_Portal_Sequence.
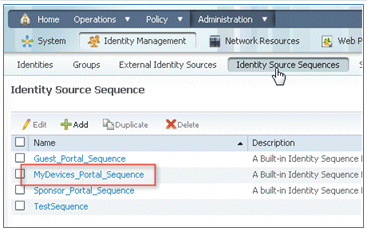
- Add AD1 to the Selected list, and click the up button in order to move AD1 to the top priority.
- Click Save.
- Confirm that the Identity Store sequence for MyDevices_Portal_Sequence contains AD1.

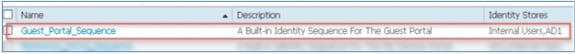
- Repeat steps 16-19 in order to add AD1 for Guest_Portal_Sequence, and click Save.
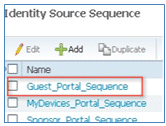
- Confirm that Guest_Portal_Sequence contains AD1.
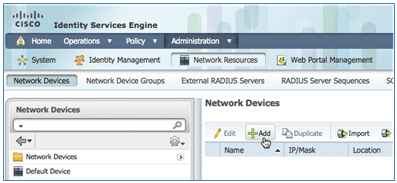
- In order to add the WLC to Network Access Device (WLC), navigate to Administration > Network Resources > Network Devices, and click Add.
- Add the WLC name, IP address, Subnet Mask, and so forth.
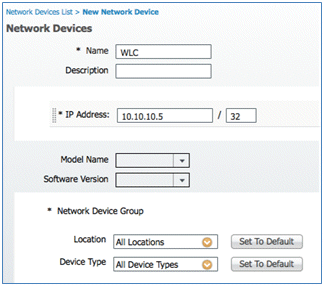
- Scroll down to Authentication Settings, and enter the Shared Secret. This must match the shared secret of the WLC RADIUS.
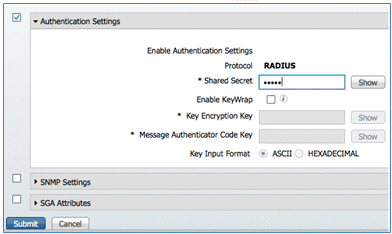
- Click Submit.
- Navigate to ISE > Policy > Policy Elements > Results.
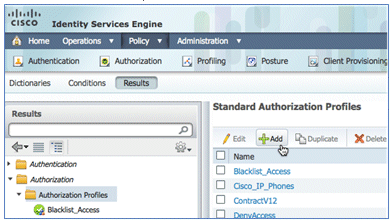
- Expand Results and Authorization, click Authorization Profiles, and click Add for a new profile.
- Give this profile these values:
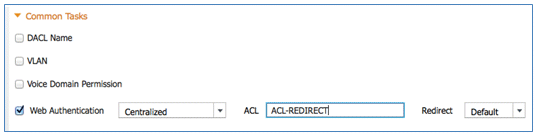
- Name: CWA
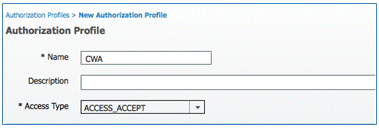
- Enable Web Authentication (box is checked):
- Web Authentication: Centralized
- ACL: ACL-REDIRECT (This must match the WLC pre-auth ACL name.)
- Redirect: Default
- Name: CWA
- Click Submit, and confirm that the CWA authorization profile has been added.
- Click Add in order to create a new authorization profile.
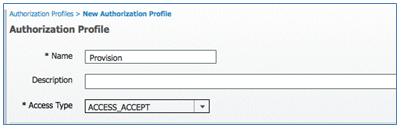
- Give this profile these values:
- Name: Provision
- Enable Web Authentication (box is checked):
- Web Authentication Value: Supplicant Provisioning
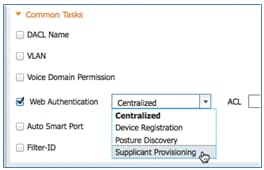
- ACL: ACL-REDIRECT (This must match the WLC pre-auth ACL name.)
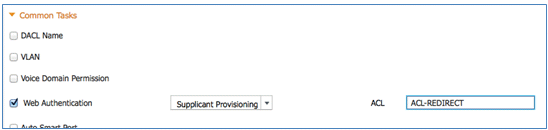
- Web Authentication Value: Supplicant Provisioning
- Name: Provision
- Click Submit, and confirm that the Provision authorization profile was added.
- Scroll down in Results, expand Client Provisioning, and click Resources.
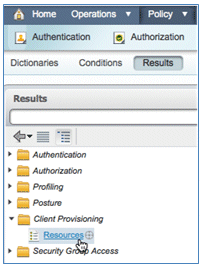
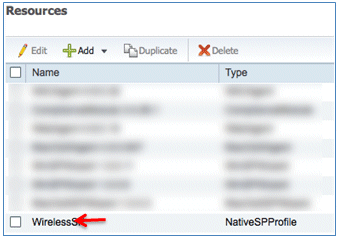
- Select Native Supplicant Profile.
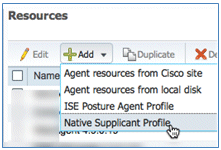
- Give the Profile a name of WirelessSP (in this example).
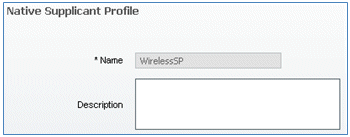
- Enter these values:
- Connection Type: Wireless
- SSID: Demo1x (this value is from the WLC 802.1x WLAN configuration)
- Allowed Protocol: TLS
- Key Size: 1024
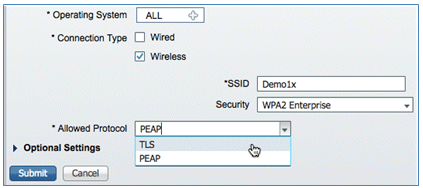
- Click Submit.
- Click Save.
- Confirm that the new profile has been added.
- Navigate to Policy > Client Provisioning.
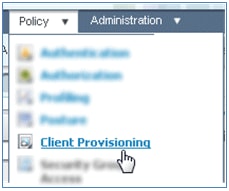
- Enter these values for the provisioning rule of iOS devices:
- Rule Name: iOS
- Identity Groups: Any
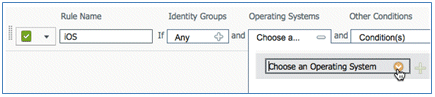
- Operating Systems: Mac iOS All
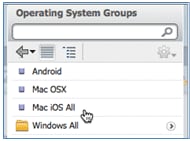
- Results: WirelessSP (this is the Native Supplicant Profile created earlier)

- Navigate to Results > Wizard Profile (drop-down list) > WirelessSP.
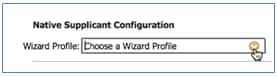
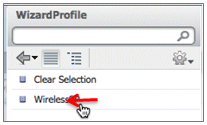
- Navigate to Results > Wizard Profile (drop-down list) > WirelessSP.
- Confirm that the iOS Provisioning Profile was added.
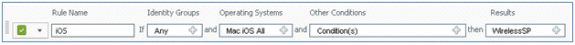
- On the right side of the first rule, locate the Actions drop-down list, and select Duplicate below (or above).
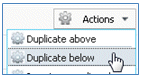
- Change the Name of the new rule to Android.
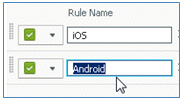
- Change the Operating Systems to Android.
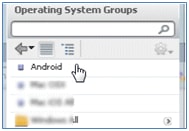
- Leave other values unchanged.
- Click Save (lower left screen).
- Navigate to ISE > Policy > Authentication.
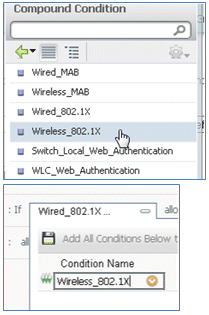
- Modify the condition to include Wireless_MAB, and expand Wired_MAB.
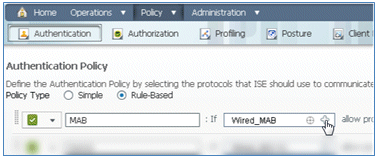
- Click the Condition Name drop-down list.
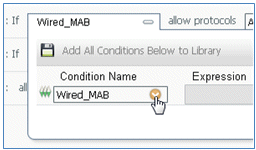
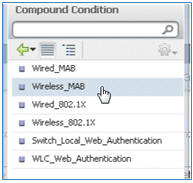
- Select Dictionaries > Compound Condition.
- Select Wireless_MAB.
- To the right of the rule, select the arrow to expand.

- Select these values from the drop-down list:
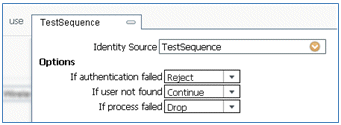
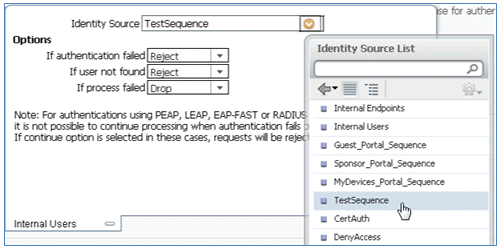
- Identity Source: TestSequence (this is the value created earlier)
- If authentication failed: Reject
- If user not found: Continue
- If process failed: Drop
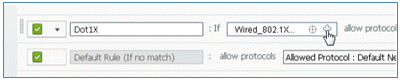
- Go to the Dot1X rule, and change these values:
Condition: Wireless_802.1X
- Identity Source: TestSequence
- Click Save.

- Navigate to ISE > Policy > Authorization.
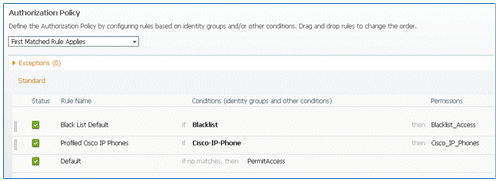
- Default rules (such as Black List Default, Profiled, and Default) are already configured from installation; the first two can be ignored; the Default rule will be edited later.
- To the right of the second rule (Profiled Cisco IP Phones), click the down arrow next to Edit, and select Insert New Rule Below.
A new Standard Rule # is added.
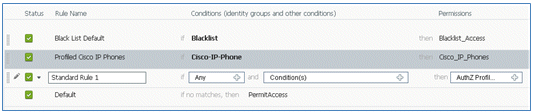
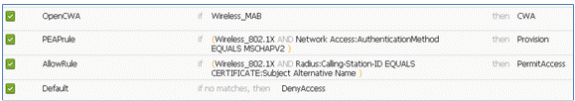
- Change the Rule Name from Standard Rule # to OpenCWA. This rule initiates the registration process on the open WLAN (dual SSID) for users that come to the guest network in order to have devices provisioned.

- Click the plus sign (+) for Condition(s), and click Select Existing Condition from Library.
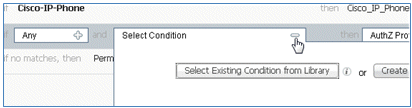
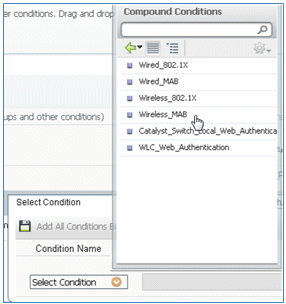
- Select Compound Conditions > Wireless_MAB.
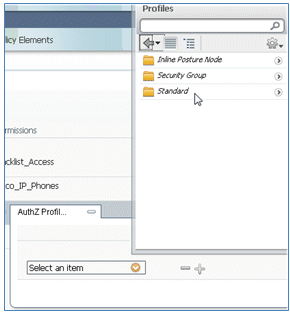
- In the AuthZ Profile, click the plus sign (+), and select Standard.
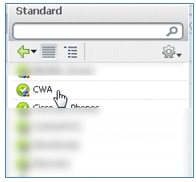
- Select the standard CWA (this is the Authorization Profile created earlier).
- Confirm that the rule is added with the correct Conditions and Authorization.

- Click Done (on the right side of the rule).

- To the right of the same rule, click the down arrow next to Edit, and select Insert New Rule Below.
- Change the Rule Name from Standard Rule # to PEAPrule (in this example). This rule is for PEAP (also used for single SSID scenario) to check that authentication of 802.1X without Transport Layer Security (TLS) and that network supplicant provisioning is initiated with the Provision authorization profile created previously.
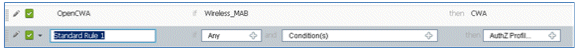
- Change the Condition to Wireless_802.1X.
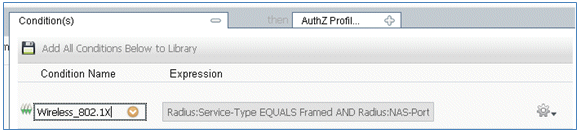
- Click the gear icon on the right side of the condition, and select Add Attribute/Value. This is an 'and' condition, not an 'or' condition.
- Locate and select Network Access.
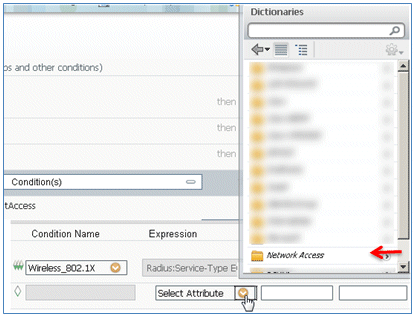
- Select AuthenticationMethod, and enter these values:
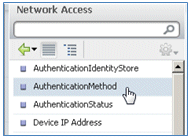
- AuthenticationMethod: Equals
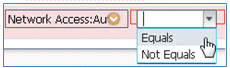
- Select MSCHAPV2.
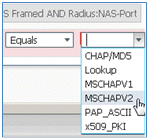
This is an example of the rule; be sure to confirm that the Condition is an AND.
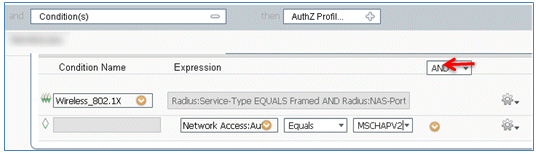
- AuthenticationMethod: Equals
- In AuthZ Profile, select Standard > Provision (this is the Authorization Profile created earlier).
- Click Done.

- To the right of the PEAPrule, click the down arrow next to Edit, and select Insert New Rule Below.
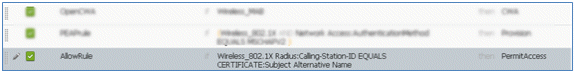
- Change the Rule Name from Standard Rule # to AllowRule (in this example). This rule will be used in order to permit access to registered devices with certificates installed.

- Under Condition(s), select Compound Conditions.
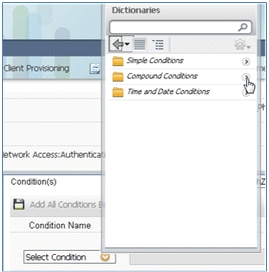
- Select Wireless_802.1X.
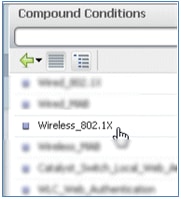
- Add an AND attribute.
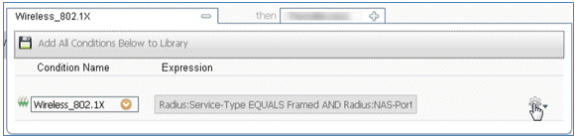
- Click the gear icon on the right side of the condition, and select Add Attribute/Value.
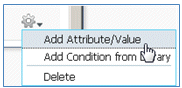
- Locate and select Radius.
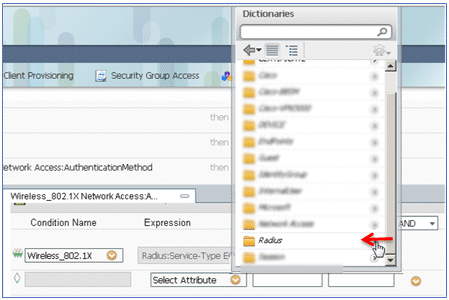
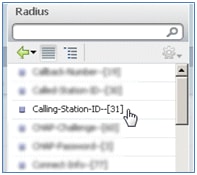
- Select Calling-Station-ID--[31].
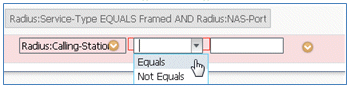
- Select Equals.
- Go to CERTIFICATE, and click the right arrow.
- Select Subject Alternative Name.
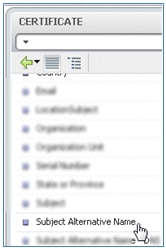
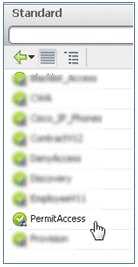
- For the AuthZ Profile, select Standard.
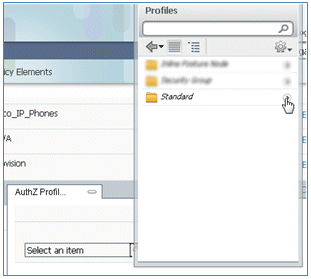
- Select Permit Access.

- Click Done.

This is an example of the rule:
- Locate the Default rule in order to change PermitAccess to DenyAccess.
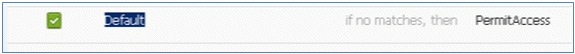
- Click Edit in order to edit the Default rule.

- Go to the existing AuthZ profile of PermitAccess.
- Select Standard.
- Select DenyAccess.
- Confirm that the Default rule has DenyAccess if no matches are found.

- Click Done.

This is an example of the main rules required for this test; they are applicable for either a single SSID or dual SSID scenario.
- Click Save.

- Navigate to ISE > Administration > System > Certificates in order to configure the ISE server with a SCEP profile.
- In Certificate Operations, click SCEP CA Profiles.
- Click Add.
- Enter these values for this profile:
- Name: mySCEP (in this example)
- URL: https://<ca-server>/CertSrv/mscep/ (Check your CA server configuration for the correct address.)
- Click Test Connectivity in order to test connectivity of the SCEP connection.
- This response shows that the server connectivity is successful.
- Click Submit.

- The server responds that the CA Profile was created successfully.
- Confirm that the SCEP CA Profile is added.

User Experience - Provisioning iOS
Dual SSID
This section covers dual SSID and describes how to connect to the guest to be provisioned and how to connect to a 802.1x WLAN.
Complete these steps in order to provision iOS in the dual SSID scenario:
- On the iOS device, go to Wi-Fi Networks, and select DemoCWA (configured open WLAN on WLC).
- Open the Safari browser on the iOS device, and visit a reachable URL (for example, internal/external webserver). The ISE redirects you to the portal. Click Continue.
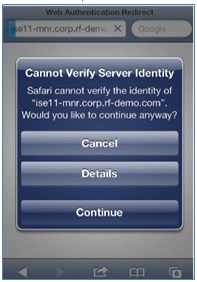
- You are redirected to the Guest Portal for login.
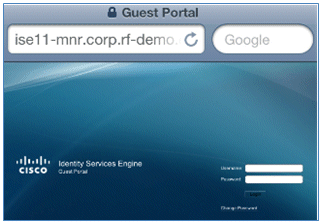
- Log in with an AD user account and password. Install the CA Profile when prompted.
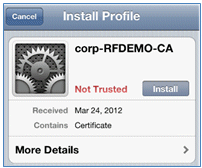
- Click Install trusted certificate of the CA server.
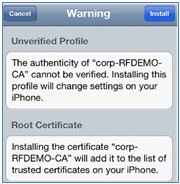
- Click Done once the profile is completely installed.
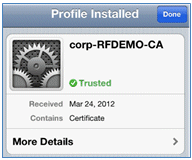
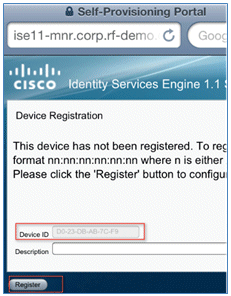
- Return to the browser, and click Register. Make a note of the Device ID that contains the MAC address of the device.
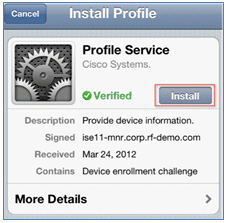
- Click Install in order to install the verified profile.
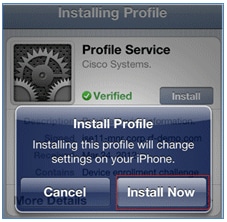
- Click Install Now.
- After the process is completed, the WirelessSP profile confirms that the profile is installed. Click Done.
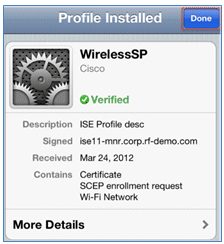
- Go to Wi-Fi Networks, and change the network to Demo1x. Your device is now connected and uses TLS.
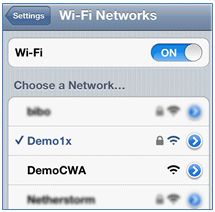
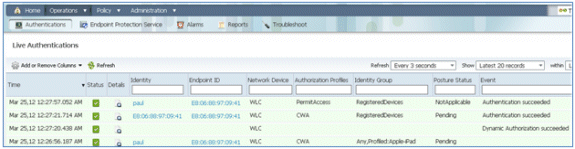
- On the ISE, navigate to Operations > Authentications. The events show the process in which the device is connected to the open guest network, goes through the registration process with supplicant provisioning, and is allowed permit access after registration.
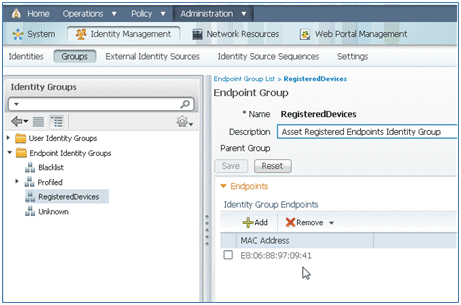
- Navigate to ISE > Administration > Identity Management > Groups > Endpoint Identity Groups > RegisteredDevices. The MAC address has been added to the database.
Single SSID
This section covers single SSID and describes how to connect directly to an 802.1x WLAN, provide AD username/password for PEAP authentication, provision through a guest account, and reconnect with TLS.
Complete these steps in order to provision iOS in the single SSID scenario:
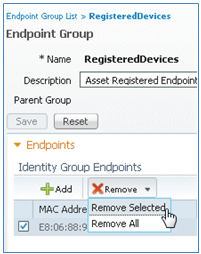
- If you are using the same iOS device, remove the endpoint from the Registered Devices.
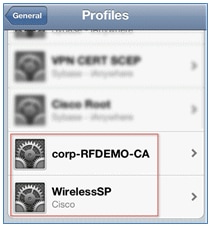
- On the iOS device, navigate to Settings > Generals > Profiles. Remove the profiles installed in this example.
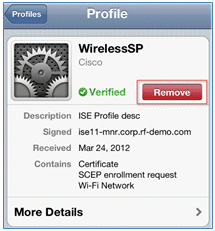
- Click Remove in order to remove the previous profiles.

- Connect directly to the 802.1x with the existing (cleared) device or with a new iOS device.
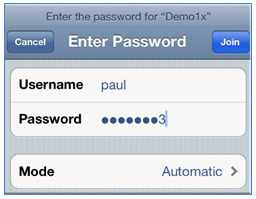
- Connect to Dot1x, enter a Username and Password, and click Join.
- Repeat Steps 90 and on from the ISE Configuration section until the appropriate profiles are completely installed.
- Navigate to ISE > Operations > Authentications in order to monitor the process. This example shows the client that is connected directly to 802.1X WLAN as it is provisioned, disconnects, and reconnects to the same WLAN with the use of TLS.
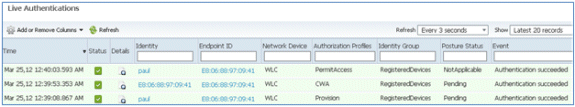
- Navigate to WLC > Monitor > [Client MAC]. In the client detail, note that the client is in the RUN state, its Data Switching is set to local, and the Authentication is Central. This is true for clients that connect to FlexConnect AP.

User Experience - Provisioning Android
Dual SSID
This section covers dual SSID and describes how to connect to the guest to be provisioned and how to connect to an 802.1x WLAN.
The connection process for the Android device is very similar to that for an iOS device (single or dual SSID). However, an important difference is that the Android device requires access to the Internet in order to access Google Marketplace (now Google Play) and download the supplicant agent.
Complete these steps in order to provision an Android device (such as the Samsung Galaxy in this example) in the dual SSID scenario:
- In the Android device, use Wi-Fi in order to connect to DemoCWA, and open the guest WLAN.
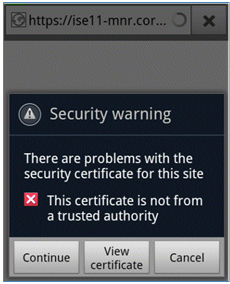
- Accept any certificate in order to connect to the ISE.
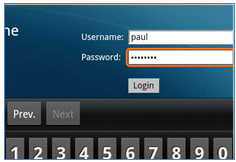
- Enter a Username and Password at the Guest Portal in order to log in.
- Click Register. The device attempts to reach the Internet in order to access Google Marketplace. Add any additional rules to the Pre-Auth ACL (such as ACL-REDIRECT) in the controller in order to allow access to the Internet.
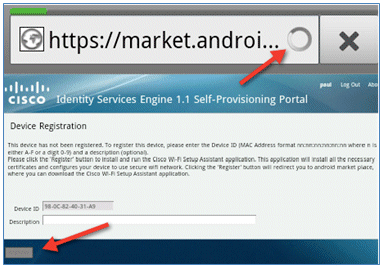
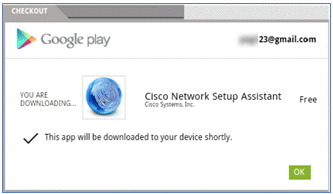
- Google lists Cisco Network Setup as an Android App. Click INSTALL.

- Sign in to Google, and click INSTALL.

- Click OK.
- On the Android device, find the installed Cisco SPW app, and open it.

- Make sure that you are still logged in to the Guest Portal from your Android device.
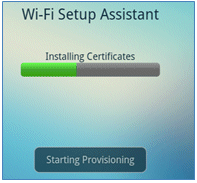
- Click Start in order to start the Wi-Fi Setup Assistant.

- The Cisco SPW begins to install certificates.
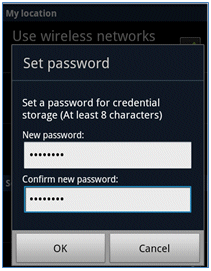
- When prompted, set a password for credential storage.
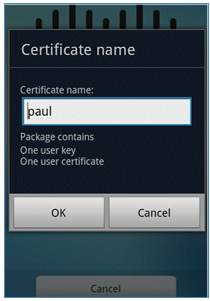
- The Cisco SPW returns with a certificate name, which contains the user key and user certificate. Click OK in order to confirm.
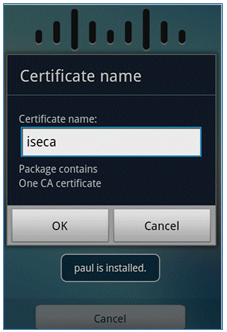
- Cisco SPW continues and prompts for another certificate name, which contains the CA certificate. Enter the name iseca (in this example), then click OK in order to continue.
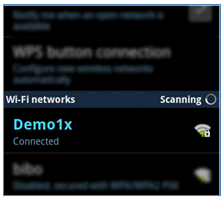
- The Android device is now connected.
My Devices Portal
My Devices Portal allows users to blacklist previously registered devices in the event a device is lost or stolen. It also allows users to re-enlist if needed.
Complete these steps in order to blacklist a device:
- In order to log in to My Devices Portal, open a browser, connect to https://ise-server:8443/mydevices (note the port number 8443), and log in with an AD account.
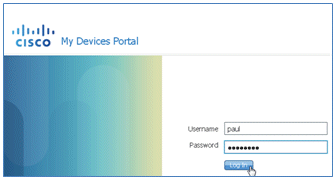
- Locate the device under Device ID, and click Lost? in order to initiate blacklisting of a device.
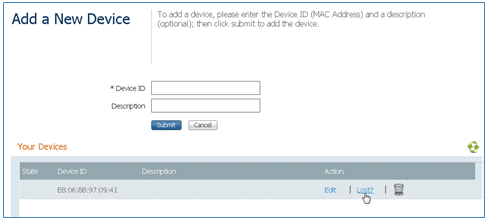
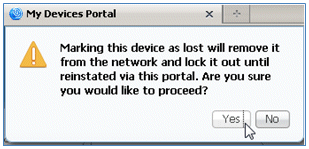
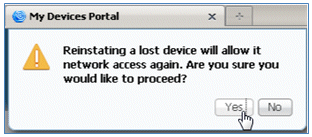
- When the ISE prompts a warning, click Yes in order to proceed.
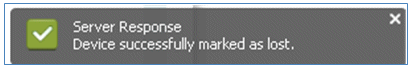
- ISE confirms that the device is marked as lost.
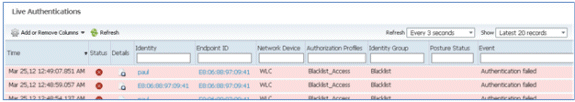
- Any attempt to connect to the network with the previously registered device is now blocked, even if there is a valid certificate installed. This is an example of a blacklisted device that fails authentication:
- An administrator can navigate to ISE > Administration > Identity Management > Groups, click Endpoint Identity Groups > Blacklist, and see the device is blacklisted.
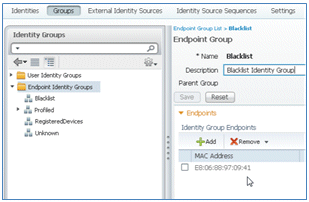
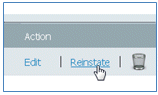
Complete these steps in order to reinstate a blacklisted device:
- From the My Devices Portal, click Reinstate for that device.
- When ISE prompts a warning, click Yes in order to proceed.
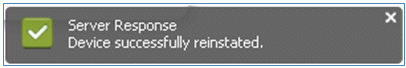
- ISE confirms that the device has been successfully reinstated. Connect the reinstated device to the network in order to test that the device will now be permitted.
Reference - Certificates
ISE not only requires a valid CA root certificate, but also needs a valid certificate signed by CA.
Complete these steps in order to add, bind, and import new trusted CA certificate:
- Navigate to ISE > Administration > System > Certificates, click Local Certificates, and click Add.
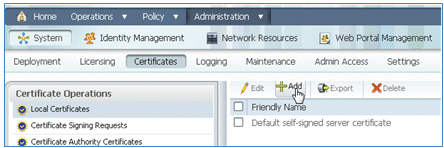
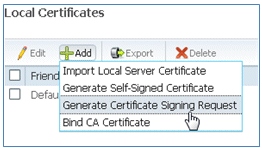
- Select Generate Certificate Signing Request (CSR).
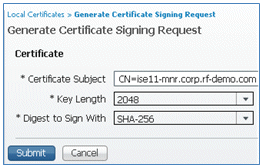
- Enter the Certificate Subject CN=<ISE-SERVER hostname.FQDN>. For the other fields, you can use the default or the values required by your CA setup. Click Submit.
- ISE verifies that the CSR was generated.

- In order to access the CSR, click the Certificate Signing Requests operations.
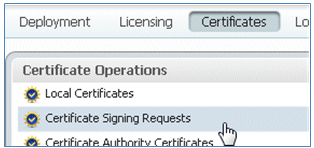
- Select the CSR recently created, then click Export.
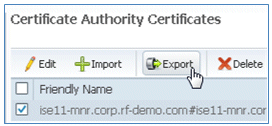
- ISE exports the CSR to a .pem file. Click Save File, then click OK in order to save the file to the local machine.
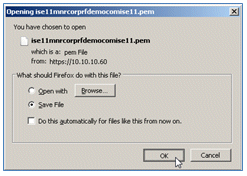
- Locate and open the ISE certificate file with a text editor.
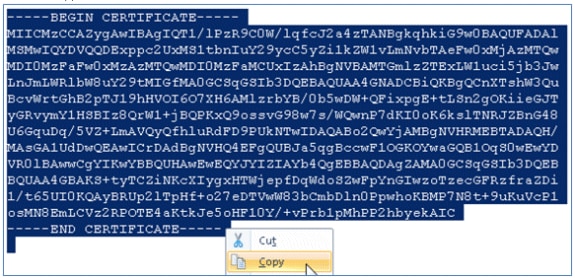
- Copy the entire content of the certificate.
- Connect to the CA server, and log in with an administrator account. The server is a Microsoft 2008 CA at https://10.10.10.10/certsrv (in this example).
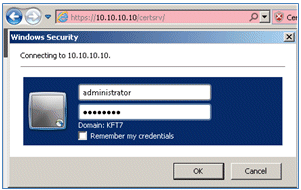
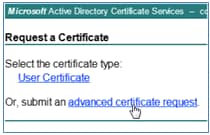
- Click Request a certificate.

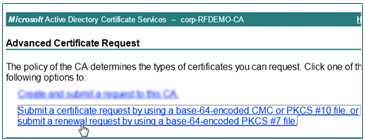
- Click advanced certificate request.
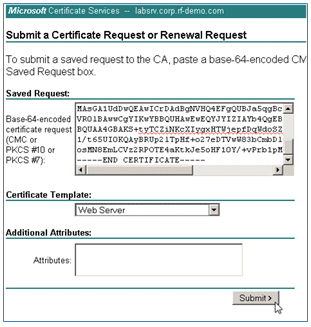
- Click the second option in order to Submit a certificate request by using a base-64-encoded CMC or ... .
- Paste the content from the ISE certificate file (.pem) into the Saved Request field, ensure the Certificate Template is Web Server, and click Submit.
- Click Download certificate.
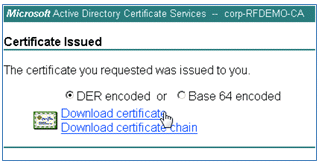
- Save the certnew.cer file; it will be used later in order to bind with the ISE.

- From ISE Certificates, navigate to Local Certificates, and click Add > Bind CA Certificate.
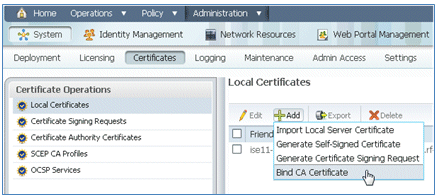
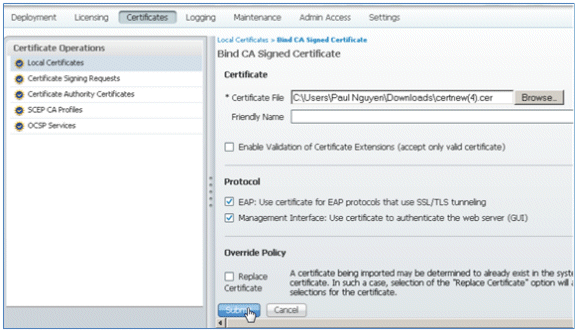
- Browse to the certificate that was saved to the local machine in the previous step, enable both the EAP and Management Interface protocols (boxes are checked), and click Submit. ISE may take several minutes or more in order to restart services.
- Return to the landing page of the CA (https://CA/certsrv/), and click Download a CA certificate, certificate chain, or CRL.
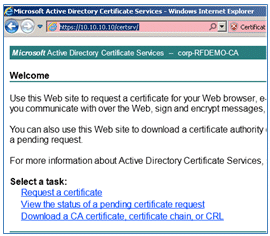
- Click Download CA certificate.
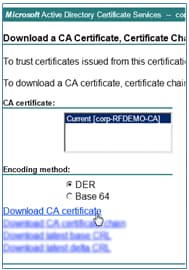
- Save the file to the local machine.

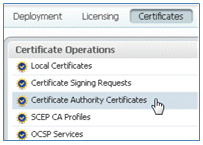
- With the ISE server online, go to Certificates, and click Certificate Authority Certificates.
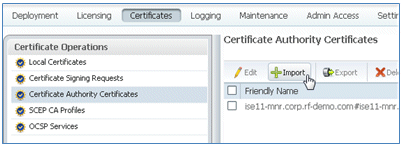
- Click Import.
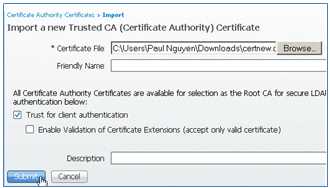
- Browse for the CA certificate, enable Trust for client authentication (box is checked), and click Submit.
- Confirm that the new trusted CA certificate is added.
Related Information
- Cisco Identity Services Engine Hardware Installation Guide, Release 1.0.4
- Cisco 2000 Series Wireless LAN Controllers
- Cisco 4400 Series Wireless LAN Controllers
- Cisco Aironet 3500 Series
- Flex 7500 Wireless Branch Controller Deployment Guide
- Bring Your Own Device - Unified Device Authentication and Consistent Access Experience
- Wireless BYOD with Identity Services Engine
- Technical Support & Documentation - Cisco Systems
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
12-Sep-2013 |
Initial Release |
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)














































































































































































































 Feedback
Feedback