Introduction
This document defines how to configure external web auth with Converged Access controllers. The guest portal page and credentials authentication are both on Identity Services Engine (ISE) in this example.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
1. Cisco converged access controllers.
2. Web authentication
3. Cisco ISE
Components Used
The information in this document is based on these software and hardware versions:
1. Cisco 5760 controller (NGWC on the below diagram), 03.06.05E
2. ISE 2.2
Configure
Network Diagram
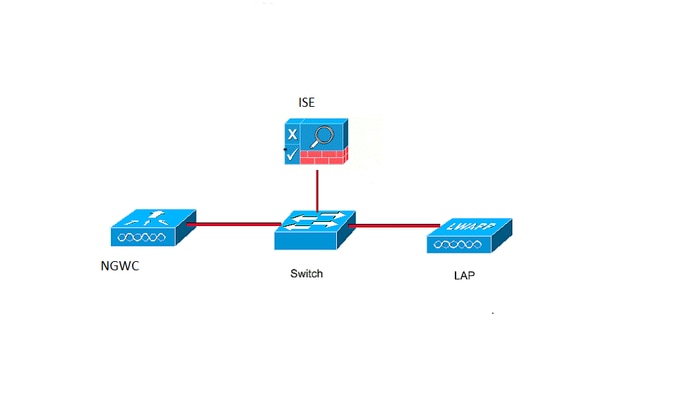
CLI Configuration
Radius configuration on controller
step 1 : Define external radius server
radius server ISE.161
address ipv4 10.48.39.161 auth-port 1812 acct-port 1813
timeout 10
retransmit 5
key Cisco123
step 2:. Define AAA radius group and specify the radius server to be used
aaa group server radius ISE-Group
server name ISE.161
deadtime 10
step 3. Define method list pointing to the radius group and map it under the WLAN.
aaa authentication login webauth group ISE-Group
Parameter Map configuration
step 4. Configure global parameter map with virtual ip address which is required for external and internal webauth. Logout button uses virtual ip. Its always a good practice to configure a non-routable virtual ip.
parameter-map type webauth global
type webauth
virtual-ip ipv4 1.1.1.1
step 5 : Configure a named parameter map.It will act like a type of webauth method. This will be called under the WLAN config.
parameter-map type webauth web
type webauth
redirect for-login https://10.48.39.161:8443/portal/PortalSetup.action?portal=0c712cd0-6d90-11e5-978e-005056bf2f0a
redirect portal ipv4 10.48.39.161
Pre authentication ACL. This will also be called under the WLAN.
step 6: Configure Preauth_ACL which allows access to ISE, DHCP and DNS before authentication is over
ip access-list extended Preauth_ACL
permit ip any host 10.48.39.161
permit ip host 10.48.39.161 any
permit udp any eq bootps any
permit udp any any eq bootpc
permit udp any eq bootpc any
permit udp any eq domain any
permit udp any any eq domain
WLAN config
step 7 : configure the WLAN
wlan ext-webauth 7 ext-webauth
client vlan vlan232
ip access-group web Preauth_ACL
no security wpa
no security wpa akm dot1x
no security wpa wpa2
no security wpa wpa2 ciphers aes
security web-auth
security web-auth authentication-list webauth
security web-auth parameter-map web
session-timeout 1800
no shutdown
step 8 : Turn on http server.
ip http server
ip http secure-server (for secure web-auth, use 'no' to disable secure web)
GUI configuration
We are following here the same steps as above. The screenshots are just provided for cross-reference.
step 1 : Define an external radius server

step 2:. Define AAA radius group and specify the radius server to be used
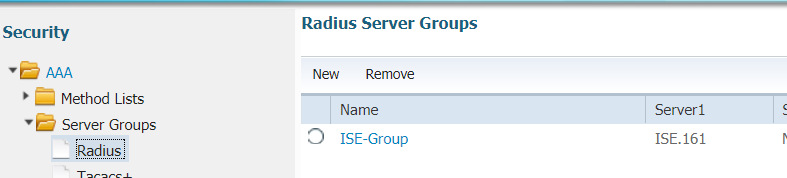
step 3. Define method list pointing to the radius group and map it under the WLAN.

Parameter Map configuration
step 4. Configure global parameter map with virtual ip address which is required for external and internal webauth. Logout button uses virtual ip. Its always a good practice to configure a non-routable virtual ip.
step 5 : Configure a named parameter map.It will act like a type of webauth method. This will be called under the WLAN config.
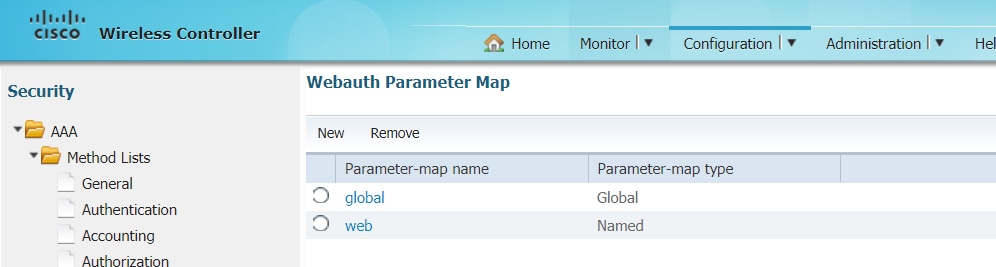
Pre authentication ACL. This will also be called under the WLAN.
step 6: Configure Preauth_ACL which allows access to ISE, DHCP and DNS before authentication is over


WLAN config
step 7 : configure the WLAN

Verify
Connect a client and make sure that if you open a browser, the client will be redirected to your login portal page. The below screenshot illustrates the ISE guest portal page.

Once proper credentials are submitted, the success page will be shown :
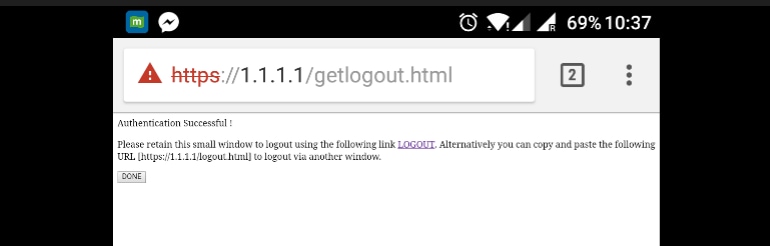
The ISE server will report two authentication : one on the guest page itself (the bottom line with only the username) and a second authentication once the WLC provides the same username/password through radius authentication (only this authentication will make the client move to the success phase). If the radius authentication (with mac address and WLC details as NAS) does not occur, the radius configuration is to be verified.













 Feedback
Feedback