Configure 9800 WLC and Aruba ClearPass - Guest Access & FlexConnect
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes the integration of the Catalyst 9800 Wireless LAN Controller (WLC) with Aruba ClearPass.
Prerequisites
This guide assumes these components have been configured and verified:
- All pertinent components are synced to Network Time Protocol (NTP) and verified to have the correct time (required for certificate validation)
- Operational DNS Server (required for Guest traffic flows, Certificate Revocation List (CRL) validation)
- Operational DHCP Server
- An optional Certificate authority (CA) (required to sign the CPPM hosted Guest Portal)
- Catalyst 9800 WLC
- Aruba ClearPass Server (Requires Platform License, Access License, Onboard License)
- Vmware ESXi
Requirements
Cisco recommends that you have knowledge of these topics:
- C9800 deployment and New Configuration Model
- Flexconnect Switching on C9800
- 9800 CWA Authentication (refer to https://www.cisco.com/c/en/us/support/docs/wireless/catalyst-9800-series-wireless-controllers/213920-central-web-authentication-cwa-on-cata.html)
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Catalyst C9800-L-C that runs 17.3.4c
- Cisco Catalyst C9130AX
- Aruba ClearPass, 6-8-0-109592 and 6.8-3 patch
- MS Windows Server
- Active Directory (GP configured for automated machine-based certificate issuance to managed endpoints)
- DHCP Server with option 43 and option 60
- DNS Server
- NTP Server to time-sync all the components
- The CA
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
The integration of the Catalyst 9800 WLC implementation utilizes Central Web Authentication (CWA) for wireless clients in a Flexconnect mode of Access Point (AP) deployment.
Guest wireless authentication is supported by Guest Portal with an anonymous acceptable user policy (AUP) page, hosted on Aruba Clearpass in a secure demilitarized zone (DMZ) segment.
The diagram conveys the details of the Guest Wifi access exchanges before the guest user is allowed onto the network:
1. The guest user associates with the Guest Wifi in a remote office.
2. The initial RADIUS Access Request is proxied by C9800 to the RADIUS server.
3. The server looks up the supplied guest MAC address in the local MAC Endpoint Database.
If the MAC address is not found, then the server responds with a MAC Authentication Bypass (MAB) profile. This RADIUS response includes:
- URL Redirect Access Control List (ACL)
- URL Redirect
4. The client goes through the IP Learn process where it is assigned an IP address.
5. C9800 transitions the guest client (identified by its MAC address) to the 'Web Auth Pending' state.
6. Most modern device OS in association with guest WLANs perform some sort of captive portal detection.
The exact detection mechanism is dependent on specific OS implementation. The client OS opens a pop-up (pseudo browser) dialog with a page redirected by C9800 to the guest portal URL hosted by the RADIUS server supplied as part of the RADIUS Access-Accept response.
7. Guest User accepts the Terms and Conditions on the presented pop-up ClearPass sets a flag for the client MAC address in its Endpoint Database (DB) to indicate the client has completed an authentication and initiates a RADIUS Change of Authorization (CoA), by the selection of an interface based on the routing table (if there are multiple interfaces present on ClearPass).
8. WLC transitions the Guest Client to the 'Run' State and the user is granted access to the Internet with no further redirects.
Note: For Cisco 9800 Foreign, Anchor Wireless Controller state flow diagram with RADIUS and externally hosted Guest Portal, refer to the Appendix section in this article.
 Guest Central Web Authentication (CWA) State Diagram
Guest Central Web Authentication (CWA) State Diagram
Traffic Flow for CWA Guest Enterprise Deployment
In a typical enterprise deployment with multiple branch offices, each branch office is set up to provide secure, segmented access to guests through a Guest Portal once the guest accepts EULA.
In this configuration example, 9800 CWA is used for guest access via integration to a separate ClearPass instance exclusively deployed for guest users in the secure DMZ of the network.
The guests must accept the terms and conditions laid out in the web-consent pop-up portal provided by the DMZ ClearPass server. This configuration example focuses on the Anonymous Guest Access method (that is, no guest username/password is required in order to authenticate to the Guest Portal).
The traffic flow that corresponds to this deployment is shown in the image:
1. RADIUS - MAB phase
2. Guest Client URL redirect to Guest Portal
3. After guest acceptance of EULA on the Guest Portal, RADIUS CoA Reauthenticate is issued from CPPM to 9800 WLC
4. The guest is allowed access to the Internet
Network Diagram
Note: For lab demo purposes, a single/combined Aruba CPPM Server instance is used in order to serve both Guest and Corp SSID Network Access Server (NAS) functions. Best practice implementation suggests independent NAS instances.

Configure
In this configuration example, a new configuration model on C9800 is leveraged in order to create the necessary profiles and tags to provide dot1x Corporate Access and CWA guest Access to the enterprise branch. The resultant configuration is summarized in this image:

Configure Guest Wireless Access C9800 Parameters
C9800 - AAA Configuration for Guest
Note: About Cisco bug ID CSCvh03827, ensure the defined Authentication, Authorization, and Accounting (AAA) servers are not load-balanced, as the mechanism relies on SessionID persistency in WLC to ClearPass RADIUS exchanges.
Step 1. Add the Aruba ClearPass DMZ server(s) to the 9800 WLC configuration and create an authentication method list. Navigate to Configuration > Security > AAA > Servers/Groups > RADIUS > Servers > +Add and enter the RADIUS server information.

Step 2. Define AAA Server Group for guests and assign the server configured in Step 1. to this server group. Navigate to Configuration > Security > AAA > Servers/Groups > RADIUS > Groups > +Add.

Step 3. Define an Authorization method list for guest access and map the server group created in Step 2. Navigate to Configuration > Security > AAA > AAA Method List > Authorization > +Add. Choose Type Network and then AAA Server Group configured in Step 2.

Step 4. Create an Accounting method list for guest access and map the server group created in Step 2. Navigate to Configuration > Security > AAA > AAA Method List > Accounting > +Add. Choose Type Identity from the drop-down menu and then AAA Server Group configured in Step 2.

C9800 - Configure Redirection ACL
The redirect ACL defines what traffic must be redirected to the Guest Portal versus allowed to pass with no redirection. Here, the ACL deny implies bypass redirect or pass through, while permit implies redirect to the portal. For each traffic class, you must consider the direction of traffic when you create Access Control Entries (ACEs) and create ACEs that match both ingress and egress traffic.
Navigate to Configuration > Security > ACL, and define a new ACL named CAPTIVE_PORTAL_REDIRECT. Configure the ACL with these ACEs:
- ACE1: Allows bidirectional Internet Control Message Protocol (ICMP) traffic to bypass redirection and is primarily used to verify reachability.
- ACE10, ACE30: Allows bidirectional DNS traffic flow to DNS server 10.0.10.4 and not be redirected to the portal. A DNS lookup and interception for response are required to trigger the guest flow.
- ACE70, ACE80, ACE110, ACE120: Allows HTTP and HTTPS access to the guest captive portal for the user to be presented with the portal.
- ACE150: All HTTP traffic (UDP port 80) is redirected.

C9800 - Guest WLAN Profile Configuration
Step 1. Navigate to Configuration > Tags & Profiles > Wireless > +Add. Create a new SSID Profile WP_Guest, with the broadcast of SSID 'Guest' that guest clients associate with.

Under the same Add WLAN dialog, navigate to the Security > Layer 2 Tab.
- Layer 2 Security Mode: None
- MAC Filtering: Enabled
- Authorization list: AAA_Authz_CPPM from the drop-down menu (configured under Step 3. as part of AAA configuration)

C9800 - Guest Policy Profile Definition
On C9800 WLC GUI, navigate to Configuration > Tags & Profiles > Policy > +Add.
Name: PP_Guest
Status: Enabled
Central Switching: Disabled
Central Authentication: Enabled
Central DHCP: Disabled
Central Association: Disabled


Navigate to the Access Policies tab in the same Add Policy Profile dialog.
- RADIUS Profiling: Enabled
- VLAN/VLAN Group: 210 (that is, VLAN 210 is the Guest local VLAN at each branch location)
Note: Guest VLAN for Flex must not have to be defined on the 9800 WLC under VLANs, in the VLAN/VLAN Group type VLAN number.
Known defect: Cisco bug ID CSCvn48234 causes SSID not to be broadcasted if the same Flex guest VLAN is defined under WLC and in the Flex Profile.

In the same Add Policy Profile dialog, navigate to the Advanced tab.
- Allow AAA Override: Enabled
- NAC State: Enabled
- NAC Type: RADIUS
- Accounting List: AAA_Accounting_CPPM (that is defined in Step 4. as part of AAA configuration)

Note: 'Network Admission Control (NAC) State - Enable' is required in order to enable C9800 WLC to accept RADIUS CoA messages.
C9800 - Policy Tag
On C9800 GUI, navigate to Configuration > Tags & Profiles > Tags > Policy > +Add.
- Name: PT_CAN01
- Description: Policy Tag for CAN01 Branch Site
In the same dialog Add Policy Tag, under WLAN-POLICY MAPS, click +Add, and map the previously created WLAN Profile to the Policy Profile:
- WLAN Profile: WP_Guest
- Policy Profile: PP_Guest

C9800 - AP Join Profile
On C9800 WLC GUI, navigate to Configuration > Tags & Profiles > AP Join > +Add.
- Name: Branch_AP_Profile
- NTP Server: 10.0.10.4 (refer to the lab topology diagram). This is the NTP server that is used by APs in Branch to synchronize.

C9800 - Flex Profile
The profiles and tags are modular and can be reused for multiple sites.
In the case of FlexConnect deployment, if the same VLAN IDs are used at all of the branch sites, you can re-use the same flex profile.
Step 1. On a C9800 WLC GUI, navigate to Configuration > Tags & Profiles > Flex > +Add.
- Name: FP_Branch
- Native VLAN ID: 10 (only required if you have a non-default native VLAN where you want to have an AP management interface)

On the same Add Flex Profile dialogue, navigate to the Policy ACL tab and click +Add.
- ACL Name: CAPTIVE_PORTAL_REDIRECT
- Central Web Auth: Enabled
On a Flexconnect deployment, each managed AP is expected to download the redirect ACL locally as redirection happens at the AP and not on the C9800.

On the same Add Flex Profile dialogue, navigate to the VLAN tab and click +Add (refer to the lab topology diagram).
- VLAN Name: guest
- VLAN Id: 210

C9800 - Site Tag
On 9800 WLC GUI, navigate to Configuration > Tags & Profiles > Tags > Site > Add.
Note: Create a unique Site Tag for each Remote Site that must support the two wireless SSIDs as described.
There is a 1-1 mapping between a geographical location, Site Tag, and a Flex Profile configuration.
A flex connect site must have a flex connect profile associated with it. You can have a maximum of 100 access points for each Flex Connect site.
- Name: ST_CAN01
- AP Join Profile: Branch_AP_Profile
- Flex Profile: FP_Branch
- Enable Local Site: Disabled

C9800 - RF Profile
On 9800 WLC GUI, navigate to Configuration > Tags & Profiles > Tags > RF > Add.
- Name: Branch_RF
- 5 GHz Band Radio Frequency (RF) Profile: Typical_Client_Density_5gh (system-defined option)
- 2.4 GHz Band RF Profile: Typical_Client_Density_2gh (system-defined option)

C9800 - Assign Tags to AP
There are two options available in order to assign defined Tags to individual APs in the deployment:
- AP name-based assignment, which leverages regex rules that match patterns in the AP Name field (Configure > Tags & Profiles > Tags > AP > Filter)
- AP Ethernet MAC address based assignment (Configure > Tags & Profiles > Tags > AP > Static)
In production deployment with the Cisco DNA Center, it is highly recommended to either use DNAC and AP PNP Workflow or use a static bulk Comma-Separated Values (CSV) upload method available in 9800 in order to avoid manual per-AP assignment. Navigate to Configure > Tags & Profiles > Tags > AP > Static > Add (Note the Upload File option).
- AP MAC Address: <AP_ETHERNET_MAC>
- Policy Tag Name: PT_CAN01
- Site Tag Name: ST_CAN01
- RF Tag Name: Branch_RF
Note: As of Cisco IOS® XE 17.3.4c there is a maximum of 1,000 regex rules per controller limitation. If the number of sites in the deployment exceeds this number, the static per-MAC assignment must be leveraged.

Note: Alternatively, to leverage the AP-name regex-based tag assignment method, navigate to Configure > Tags & Profiles > Tags > AP > Filter > Add.
- Name: BR_CAN01
- AP name regex: BR-CAN01-.(7) (This rule matches on AP name convention adopted within the organization. In this example, the Tags are assigned to APs that have an AP Name field that contains 'BR_CAN01-' followed by any seven characters.)
- Priority: 1
- Policy Tag Name: PT_CAN01 (as defined)
- Site Tag Name: ST_CAN01
- RF Tag Name: Branch_RF

Configure Aruba CPPM Instance
For production/best practices based on Aruba CPPM configuration, contact your local HPE Aruba SE resource.
Aruba ClearPass Server Initial Configuration
Aruba ClearPass is deployed with the use of the Open Virtualization Format (OVF) template on the ESXi <> server that allocates these resources:
- Two reserved virtual CPUs
- 6 GB RAM
- 80 GB disk (must be added manually after initial VM deployment before the machine is powered on)
Apply for Licenses
Apply for a platform license via Administration > Server Manager > Licensing. Add Platform, Access, and Onboard licenses.
Server Hostname
Navigate to Administration > Server Manager > Server Configuration and choose the newly provisioned CPPM server.
- Hostname: cppm
- FQDN: cppm.example.com
- Verify Management Port IP Addressing and DNS

Generate CPPM Web Server Certificate (HTTPS)
This certificate is used when the ClearPass Guest Portal page is presented via HTTPS to guest clients who connect to the Guest Wifi in the Branch.
Step 1. Upload the CA pub chain certificate.
Navigate to Administration > Certificates > Trust List > Add.
- Usage: Enable Others

Step 2. Create Certificate Signing Request.
Navigate to Administration > Certificates > Certificate Store > Server Certificates > Usage: HTTPS Server Certificate.
- Click the Create Certificate Signing Request
- Common Name: CPPM
- Organization: cppm.example.com
Ensure to populate the SAN field (a common name must be present in SAN as well as IP and other FQDNs as needed). The format is DNS <fqdn1>,DNS:<fqdn2>,IP<ip1>.

Step 3. In your CA of choice, sign the newly generated CPPM HTTPS Service CSR.
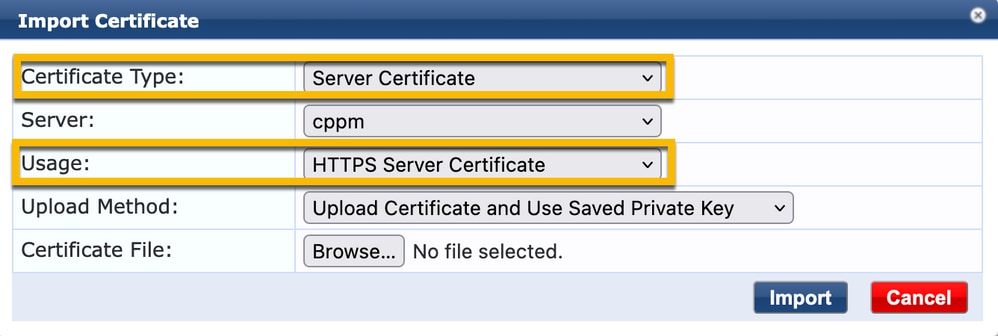
Step 4. Navigate to Certificate Template > Web Server > Import Certificate.
- Certificate Type: Server Certificate
- Usage: HTTP Server Certificate
- Certificate File: Browse, and choose CA signed CPPM HTTPS Service certificate
Define C9800 WLC as a Network Device
Navigate to Configuration > Network > Devices > Add.
- Name: WLC_9800_Branch
- IP or Subnet Address: 10.85.54.99 (refer to lab topology diagram)
- RADIUS Shared Cisco: <WLC RADIUS password>
- Vendor Name: Cisco
- Enable RADIUS Dynamic Authorization: 1700

Guest Portal Page and CoA Timers
It is very important to set the correct timer values throughout the configuration. If timers are not tuned, you are likely to run into a cycling Web Portal redirect with the client, not in 'Run State'.
Timers to pay attention to:
- Portal Web Login timer: This timer delays your redirect page before it allows access to the guest portal page to notify the CPPM service of state transition, register the Endpoint custom attribute 'Allow-Guest-Internet' value, and trigger the CoA process from CPPM to WLC. Navigate to
Guest > Configuration > Pages > Web Logins.
- Choose Guest Portal Name: Lab Anonymous Guest Registration (this Guest Portal page configuration is detailed as shown)
- ClickEdit
- Login Delay: 6 seconds

- ClearPass CoA delay timer: This delays the origination of CoA messages from ClearPass to WLC. This is required for CPPM to successfully transition the state of the Client Endpoint internally before CoA Acknowledgement (ACK) comes back from WLC. Lab tests show the sub-millisecond response times from WLC, and if CPPM has not finished updating the Endpoint attributes, the new RADIUS session from WLC is matched to the Unauthenticated MAB Service enforcement policy, and the client is given a redirect page again. Navigate to
CPPM > Administration > Server Manager > Server Configurationand chooseCPPM Server > Service Parameters.
- RADIUS Dynamic Authorization (DM/CoA) Delay - Set to six seconds

ClearPass - Guest CWA Configuration
ClearPass-side CWA Configuration is composed of (3) Service Points/Stages:
|
ClearPass Component |
Service Type |
Purpose |
|
1. Policy Manager |
Service: Mac Authentication |
If the custom attribute |
|
2. Guest |
Web Logins |
Present Anonymous login AUP page. |
|
3. Policy Manager |
Service: Web-based Authentication |
Update Endpoint to |
ClearPass Endpoint Metadata Attribute: Allow-Guest-Internet
Create a metadata attribute of type Boolean in order to track the Guest Endpoint state as the client transitions between the 'Webauth Pending' and 'Run' state:
- New guests that connect to Wifi have a default metadata attribute set in order to Allow-Guest-Internet=false. Based on this attribute the client auth goes through the MAB service
- Guest client when you click the AUP Accept button, has its metadata attribute updated in order to Allow-Guest-Internet=true. Subsequent MAB based on this attribute set to True allows non-redirected access to the Internet
Navigate to ClearPass > Configuration > Endpoints, pick any endpoint from the list, click the Attributes tab, add Allow-Guest-Internet with the value false and Save.
Note: You can also edit the same endpoint, and delete this attribute right after - this step simply creates a field in the Endpoints metadata DB that can be used in policies.

ClearPass Reauthenticate Enforcement Policy Configuration
Create an Enforcement Profile that is assigned to the guest client immediately after the client accepts AUP on the Guest Portal page.
Navigate to ClearPass > Configuration > Profiles > Add.
- Template: RADIUS Dynamic Authorization
- Name: Cisco_WLC_Guest_COA

|
Radius:IETF |
Calling-Station-Id |
%{Radius:IETF:Calling-Station-Id} |
|
Radius:Cisco |
Cisco-AVPair |
subscriber:command=reauthenticate |
|
Radius:Cisco |
Cisco-AVPair |
%{Radius:Cisco:Cisco-AVPair:subscriber:audit-session-id} |
|
Radius:Cisco |
Cisco-AVPair |
subscriber:reauthenticate-type=last-type=last |
ClearPass Guest Portal Redirect Enforcement Profile Configuration
Create an Enforcement Profile that is applied to the Guest during the initial MAB phase, when the MAC address is not found in the CPPM Endpoint Database with 'Allow-Guest-Internet' set to 'true'.
This causes the 9800 WLC to redirect the Guest client to the CPPM Guest Portal for external authentication.
Navigate to ClearPass > Enforcement > Profiles > Add.
- Name: Cisco_Portal_Redirect
- Type: RADIUS
- Action: Accept
 ClearPass Redirect Enforcement Profile
ClearPass Redirect Enforcement Profile
In the same dialogue, under the Attributes tab, configure two Attributes as per this image:
 ClearPass Redirect Profile Attributes
ClearPass Redirect Profile Attributes
The url-redirect-acl attribute is set to CAPTIVE-PORTAL-REDIRECT, which is the name of the ACL created on C9800.
Note: Only the reference to the ACL is passed in the RADIUS message, and not the ACL contents. It is important that the name of the ACL created on 9800 WLC matches exactly with the value of this RADIUS attribute as shown.
The url-redirect attribute is composed of several parameters:
- The target URL where the Guest Portal is hosted, https://cppm.example.com/guest/iaccept.php
- Guest Client MAC, macro %{Connection:Client-Mac-Address-Hyphen}
- Authenticator IP (9800 WLC triggers the redirect), macro %{Radius:IETF:NAS-IP-Address}
- cmd-login action
The URL of the ClearPass Guest Web Login Page is seen when you navigate to CPPM > Guest > Configuration > Pages > Web Logins > Edit.
In this example, the Guest Portal page name in CPPM is defined as iaccept.
Note: The configuration steps for the Guest Portal page are as described.

Note: For Cisco devices, normally audit_session_id is used, but, that is not supported by other vendors.
ClearPass Metadata Enforcement Profile Configuration
Configure Enforcement Profile in order to update Endpoint metadata attribute that is used for state transition tacking by CPPM.
This profile is applied to the MAC Address entry of the Guest Client in the Endpoint database and sets the Allow-Guest-Internet
Navigate to ClearPass > Enforcement > Profiles > Add.
- Template: ClearPass Entity Update Enforcement
- Type: Post_Authentication

In the same dialogue, the Attributes tab.
- Type: Endpoint
- Name: Allow-Guest-Internet
Note: For this name to appear in the dropdown menu, you must manually define this field for at least one Endpoint as described in the steps.
- Value: true

ClearPass Guest Internet Access Enforcement Policy Configuration
Navigate to ClearPass > Enforcement > Policies > Add.
- Name: WLC Cisco Guest Allow
- Enforcement Type: RADIUS
- Default Profile: Cisco_Portal_Redirect

In the same dialogue, navigate to the Rules tab and click Add Rule.
- Type: Endpoint
- Name: Allow-Guest-Internet
- Operator: EQUALS
- Value True
- Profile Names / Choose to Add: [RADIUS] [Allow Access Profile]

ClearPass Guest Post-AUP Enforcement Policy Configuration
Navigate to ClearPass > Enforcement > Policies > Add.
- Name: Cisco WLC Webauth Enforcement Policy
- Enforcement Type: WEBAUTH (SNMP/Agent/CLI/CoA)
- Default Profile: [RADIUS_CoA] Cisco_Reauthenticate_Session

In the same dialogue, navigate to Rules > Add.
- Conditions: Authentication
- Name: Status
- Operator: EQUALS
- Value: User
- Profile Names: <add each>:
- [Post Authentication] [Update Endpoint Known]
- [Post Authentication] [Make-Cisco-Guest-Valid]
- [RADIUS_CoA] [Cisco_WLC_Guest_COA]

Note: If you run into a scenario with a continuous Guest Portal redirect pseudo browser pop-up, it is indicative that either the CPPM Timers require adjustments or that the RADIUS CoA messages are not properly exchanged between CPPM and 9800 WLC. Verify these sites.
- Navigate to CPPM > Monitoring > Live Monitoring > Access Tracker, and ensure the RADIUS log entry contains RADIUS CoA details.
- On 9800 WLC, navigate to Troubleshooting > Packet Capture, enable PCAP on the interface where the arrival of RADIUS CoA packets is expected, and verify RADIUS CoA messages are received from the CPPM.
ClearPass MAB Authentication Service Configuration
The service is matched on Attribute Value (AV) pair Radius: Cisco | CiscoAVPair | cisco-wlan-ssid
Navigate to ClearPass > Configuration > Services > Add.
Service Tab:
- Name: GuestPortal - Mac Auth
- Type: MAC Authentication
- More Options: Choose Authorization, Profile Endpoints
Add match rule:
- Type: Radius: Cisco
- Name: Cisco-AVPair
- Operator: EQUALS
- Value: cisco-wlan-ssid=Guest (match your configured Guest SSID name)
Note: 'Guest' is the name of the broadcasted Guest SSID by 9800 WLC.

While in the same dialogue, choose the Authentication Tab.
- Authentication Methods: Remove [MAC AUTH], Add [Allow All MAC AUTH]
- Authentication Sources: [Endpoints Repository][Local SQL DB], [Guest User Repository][Local SQL DB]

While in the same dialogue, choose the Enforcement Tab.
- Enforcement Policy: WLC Cisco Guest Allow

While in the same dialogue, choose the Enforcement Tab.

ClearPass Webauth Service Configuration
Navigate to ClearPass > Enforcement > Policies > Add.
- Name: Guest_Portal_Webauth
- Type: Web-based Authentication

While in the same dialogue, under the Enforcement tab, the Enforcement Policy: Cisco WLC Webauth Enforcement Policy.

ClearPass - Web Login
For the Anonymous AUP Guest Portal page, use a single username with no password field.
The username that is used must have these fields defined/set:
username_auth | Username Authentication: | 1
In order to set the 'username_auth' field for a user, that field must be first exposed in the 'edit user' form. Navigate to ClearPass > Guest > Configuration > Pages > Forms, and choose create_user form.

Choose visitor_name (row 20), and click Insert After.


Now create the username in order to use behind the AUP Guest Portal page.
Navigate to CPPM > Guest > Guest > Manage Accounts > Create.
- Guest Name: GuestWiFi
- Company Name: Cisco
- Email Address: guest@example.com
- Username Authentication: Allow guest access with the use of their username only: Enabled
- Account Activation: Now
- Account Expiration: The account does not expire
- Terms of Use: I am the sponsor: Enabled

Create a Web Login Form. Navigate to CPPM > Guest > Configuration > Web Logins.
Name: Lab Anonymous Guest Portal
Page Name: iaccept
Vendor Settings: Aruba Networks
Login Method: Server-initiated - Change of authorization (RFC 3576) sent to the controller
Authentication: Anonymous - Does not require a username or password
Anonymous User: GuestWifi
Terms: require a Terms and Conditions confirmation
Log In Label: accept and connect
Default URL: www.example.com
Login Delay: 6
Update Endpoint: Mark the MAC address of the user as a known endpoint
Advanced: Customize attributes stored with the endpoint, the Endpoint Attributes in the post-auth section:
username | Username
visitor_name | Visitor Name
cn | Visitor Name
visitor_phone | Visitor Phone
email | Email
mail | Email
sponsor_name | Sponsor Name
sponsor_email | Sponsor Email
Allow-Guest-Internet | true
Verification - Guest CWA Authorization
In the CPPM, navigate to Live Monitoring > Access Tracker.
The New Guest user connects and triggers MAB Service.
Summary Tab:

In the same dialogue, navigate to the Input Tab.

In the same dialogue, navigate to the Output Tab.

Appendix
For reference purposes, a state flow diagram is presented here for Cisco 9800 Foreign, Anchor controller interactions with RADIUS Server and externally hosted Guest Portal.
 Guest Central Web Authentication State Diagram with Anchor WLC
Guest Central Web Authentication State Diagram with Anchor WLC
Related Information
It is important to note that the 9800 WLC does not reliably use the same UDP source port for a given wireless client RADIUS transaction. This is something ClearPass can be sensitive to. It is also important to base any RADIUS load balancing on the client calling-station-id and not try to rely on UDP source port from the WLC side.
- Cisco 9800 Deployment Best Practices Guide
- Understand Catalyst 9800 Wireless Controllers Configuration Model
- Understand FlexConnect on Catalyst 9800 Wireless Controller
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
3.0 |
20-Jun-2024 |
Added a note about the source port RADIUS balancing |
2.0 |
22-Jul-2022 |
Initial Release |
1.0 |
23-Jun-2022 |
Initial Release |
Contributed by
- Igor ManassypovSystems Architect
- Francis GirardTechnical Solutions Architect
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)

 Feedback
Feedback