Understand 802.11r/11k/11v Fast Roams on 9800 WLCs
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes the different outcomes when fast roam methods are enabled/disabled on the wireless clients.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- IEEE 802.11 WLAN Fundamentals.
- IEEE 802.11 WLAN Security.
- IEEE 802.1X/EAP Basics.
- IEEE 802.11r BSS Fast Transition.
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Wireless 9800-L Controller IOS® XE 17.9.4
- Cisco Catalyst 9130AXI Series Access Point.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
This document helps you understand the difference when you have the protocols 802.11r, 802.11v, and 802.11k enabled on a 9800 wireless controller. It also explains what the impact is on the clients when you have them disabled.
802.11r, 802.11v, and 802.11k are all different standards or amendments within the 802.11 family of wireless network protocols.
802.11r: Is the Fast Transition across basic service sets which introduces a new concept where the initial handshake with a new AP is done even before the client roams to the target access point. It is particularly useful in environments where uninterrupted connectivity is crucial, such as in voice-over-IP or real-time stream applications with video or constant stream monitor. With a tuned 802.11r network, devices can roam between access points without the significant experience disruptions or drops in network connectivity.
802.11k: Neighbor List and Assisted Roam (Radio Resource Measurement) leverages the features of radio resource management to improve the overall performance and reliability of wireless networks. It optimizes available radio resources where access points collect and share information about their radio environment. This information includes channel usage, signal strength, and interference levels. It can then be used by client devices to make more informed decisions about which AP to connect to; which results in better load balance, reduced interference, and improved network efficiency.
802.11v: Is a Network assisted Power Save which helps clients to improve the battery life which allows them to sleep longer. It also focuses on how to enhance the efficiency and management of wireless networks. This in turn, enables a better control and coordination between the network infrastructure and client devices when clients roam. The primary features are neighbor reports, service set transitions, load balance, and network-assisted power save. These features enhance client network discovery, selection, and monitoring. It also allows the access points to encourage client devices to roam instead of waiting for the device to make a roam decision.
While 802.11r focuses on seamless transition between APs, 802.11v aims to enhance network management capabilities. The 802.11k is designed to optimize radio resource utilization for better performance and reliability.
Some statements in this document are from book Understanding and Troubleshooting Cisco Catalyst 9800 Series Wireless Controllers Chapter 6, 802.11 Roam section.
Higher-Level Security Roams
When the SSID is configured with L2 higher-level security on top of basic 802.11 Open System authentication, then more frames are required for the initial association and when clients roam. The two most-common security methods standardized and implemented for 802.11 WLANs are:
- WPA/WPA2/WPA3 Personal: A PSK is used to authenticate the clients.
- WPA/WPA2/WPA3 Enterprise: The Extensible Authentication Protocol (EAP) method and 802.1x is used to authenticate the wireless clients, which is to validate the user credentials (username and password), certificates, or tokens via a AAA server.
In this document, WPA2 Enterprise WLAN can be used with EAP-PEAP to show the difference in the use of the IEEE protocols (802.11r, 802.11k, and 802.11v) and how it could affect the wireless roam attempts.
SSID with Fast Roam Protocols Enabled (802.11r, 802.11k, and 802.11v)
The default WLAN configuration has every protocol enabled by default. In the lab, the wireless client attempts to roam between 9130 access points. Since you have the default configuration of the WLAN, in other words, fast roam is enabled addition to 802.11v and 802.11k, you would expect a seamless roam. Here is an example of an over-the-air OTA capture for a roam even:

Here is the RA traces for this roam event:
2023/09/19 21:54:25.912523930 {wncd_x_R0-0}{1}: [client-orch-sm] [15403]: (note): MAC: 62be.a38b.07c5 Re-Association received. BSSID 1416.9d7f.a22e, WLAN Roaming-Enabled, Slot 1 AP 1416.9d7f.a220, Rosalia-9130-1, old BSSID f01d.2d49.dacf
!--- Reassociation Request is received from the client.
2023/09/19 21:54:25.912882280 {wncd_x_R0-0}{1}: [dot11-validate] [15403]: (info): MAC: 62be.a38b.07c5 Dot11 validate dot11r pmkid. 11r PMKID match found
!--- Since 802.11r is enabled, WLC/AP were able to validate/use the PMKID As 802.11r is enabled, the initial handshake with a new AP is done even before the client roams to the target access point. This concept is called Fast Transition. The initial handshake allows a client and the access points to do the Pairwise Transient Key (PTK) calculation in advance. These PTK keys are applied to the client and the access points after the client responds to the reassociation request or responds to the exchange with the new target AP:
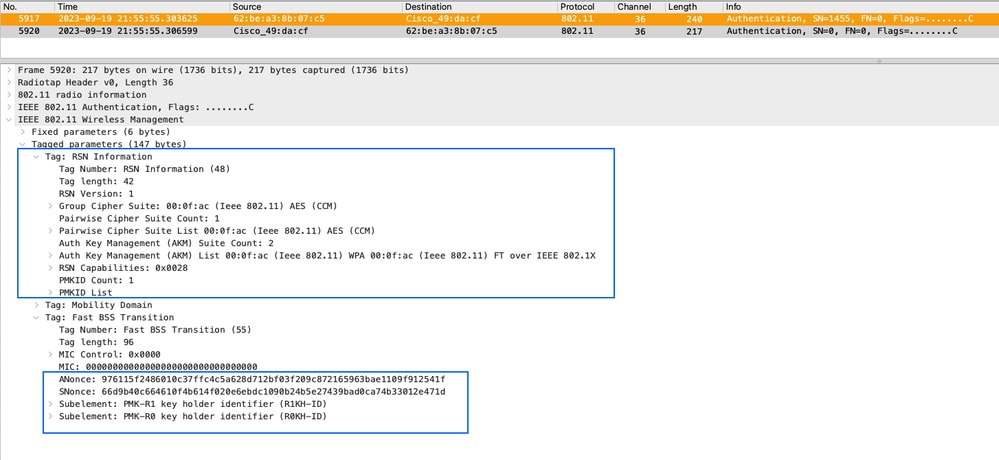
2023/09/19 21:54:25.913247615 {wncd_x_R0-0}{1}: [dot11] [15403]: (note): MAC: 62be.a38b.07c5 Association success. AID 2, Roaming = True, WGB = False, 11r = True, 11w = False Fast roam = True
!--- Reassociation Response is sent to the client.
2023/09/19 21:53:59.692212232 {wncd_x_R0-0}{1}: [client-orch-state] [15403]: (note): MAC: 62be.a38b.07c5 Client state transition: S_CO_IP_LEARN_IN_PROGRESS -> S_CO_RUN
!--- Client took an IP address and moved to run state. SSID with Fast Roam Protocols Disabled (802.11r, 802.11k, and 802.11v)
In this scenario, all of the protocols are disabled on a 802.1x SSID, in this case, the client experiences a full authentication each time the wireless client roams between the access points, next figure shows an example of an over-the-air exchange where you can see the client could not skip the EAP exchange. Therefore, a full re-authentication took place because none of the fast roam methods are enabled:
 Over-The-Air Protocols Disabled
Over-The-Air Protocols Disabled
Here is a summary of the controller RA traces for this roam event:
2023/09/19 21:44:47.425575500 {wncd_x_R0-0}{1}: [client-orch-sm] [15403]: (note): MAC: a2ca.9de1.87c9 Re-Association received. BSSID 1416.9d7f.a22f, WLAN Roaming-Disabled, Slot 1 AP 1416.9d7f.a220, Rosalia-9130-1, old BSSID f01d.2d49.dace
!--- Reasscoiation Request is received from the client.
2023/09/19 21:44:47.425980179 {wncd_x_R0-0}{1}: [dot11-validate] [15403]: (ERR): MAC: a2ca.9de1.87c9 Failed to Dot11 validate dot11i pmkids. No matching pmkid for the pmk available in cache.
!--- Since none of the roam methods are enabled, WLC/AP could not find any PMKID available.
2023/09/19 21:44:47.426252733 {wncd_x_R0-0}{1}: [dot11] [15403]: (note): MAC: a2ca.9de1.87c9 Association success. AID 1, Roaming = True, WGB = False, 11r = False, 11w = False Fast roam = False
!--- Reasscoiation Response is sent to the client.
2023/09/19 21:44:47.444466744 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] Sent EAPOL packet - Version : 3,EAPOL Type : EAP, Payload Length : 5, EAP-Type = Identity
2023/09/19 21:44:47.444469338 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] EAP Packet - REQUEST, ID : 0x1
2023/09/19 21:44:47.444481064 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] EAPOL packet sent to client
2023/09/19 21:44:47.471913767 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] Received EAPOL packet - Version : 1,EAPOL Type : EAP, Payload Length : 13, EAP-Type = Identity
2023/09/19 21:44:47.471916029 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] EAP Packet - RESPONSE, ID : 0x1
2023/09/19 21:44:47.475646582 {wncd_x_R0-0}{1}: [radius] [15403]: (info): RADIUS: Received from id 1812/103 10.201.234.195:0, Access-Challenge, len 129
2023/09/19 21:44:47.627108647 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] Sent EAPOL packet - Version : 3,EAPOL Type : EAP, Payload Length : 39, EAP-Type = PEAP
2023/09/19 21:44:47.627110791 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] EAP Packet - REQUEST, ID : 0x5c
2023/09/19 21:44:47.631319121 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] EAP Packet - RESPONSE, ID : 0x5c
2023/09/19 21:44:47.657492378 {wncd_x_R0-0}{1}: [radius] [15403]: (info): RADIUS: Received from id 1812/183 10.201.234.195:0, Access-Accept, len 297
2023/09/19 21:44:47.657840708 {wncd_x_R0-0}{1}: [dot1x] [15403]: (info): [a2ca.9de1.87c9:capwap_90000002] Received an EAP Success
!--- Full Reauthentication EAP exchange packets.
2023/09/19 21:44:47.658787303 {wncd_x_R0-0}{1}: [client-keymgmt] [15403]: (info): MAC: a2ca.9de1.87c9 EAP key M1 Sent successfully
2023/09/19 21:44:47.662831295 {wncd_x_R0-0}{1}: [client-keymgmt] [15403]: (info): MAC: a2ca.9de1.87c9 M2 Status: EAP key M2 validation success
2023/09/19 21:44:47.662931971 {wncd_x_R0-0}{1}: [client-keymgmt] [15403]: (info): MAC: a2ca.9de1.87c9 EAP key M3 Sent successfully
2023/09/19 21:44:47.665864464 {wncd_x_R0-0}{1}: [client-keymgmt] [15403]: (info): MAC: a2ca.9de1.87c9 M4 Status: EAP key M4 validation is successful
!--- 4-way handshake in order to compute the PTK/GTK keys. SSID with 802.11k Enabled
The 802.11k standard allows clients to request a neighbor report that contains information about APs that are good candidates for a roam within the service set. This enables clients to avoid passive or active RF scan before the client decides to move to a different access point. The C9800 supports a feature called 11k assisted roami, which creates and delivers an optimized neighbor list to the 802.11k clients. The 802.11k neighbor list is generated on demand and can be different for two clients on different APs because the WLC would consider the individual client RF relationship with the surrounded APs.
Clients that do not support 82.11k protocol, do not send neighbor list requests. This enables prediction optimization that helps those clients. As a result, a neighbor list is stored in the mobile station software data structure on C9800.
Clientssend requests for neighbor lists only after they associate with the access points that advertise the RM capability Information Element (IE) in the beacon. This next figure is an example of 802.11k action frames after the client got associated with the access point:
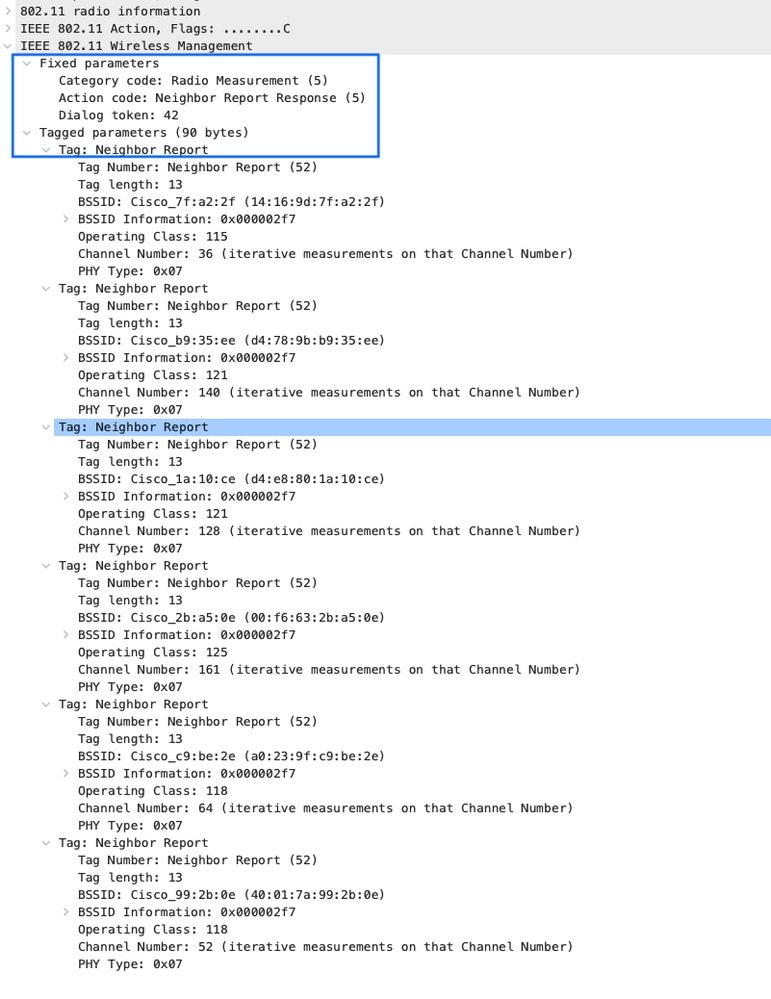 Over-The-Air Neighbor Report
Over-The-Air Neighbor Report
SSID with 802.11v Enabled
With the 802.11v standard, the two main enhancements to the wireless network management include:
-
Network-assisted power save feature: Enhances the client battery performance with a maximum idle period, which indicates the duration where a client can remain in a sleep mode without any data frames sent. The client is notified about this maximum idle period through association and disassociation frames.
If an access point does not receive frames from a wireless client for a certain period of time, it assumes the client left the network and disassociates it. The BSS Max idle period is the amount of time an AP can keep a client associated without having to receive any frame (client can remain asleep, this saves battery). This value is sent to the wireless client through the association and re-association response frame. The next figure shows the value in the re-association response from the access point, where the BSS Max Idle Period is specified in time units. Every time the unit is equal to 1.024 milliseconds:
 Over-The-Air BSS Period Value
Over-The-Air BSS Period Value
- Network-assisted roam: Enables the wireless infrastructure to suggest that the client roam away from its current access point. This provides the client the list of access points that it can roam to in the same extended service set (ESS).
802.11v BSS transition management frames are exchanged in three scenarios:
- Solicited Request: Before the transition to a new access point, the client has the ability to send an 802.11v BSS Transition Management Query to find out better options of access points to reassociate with, and the current AP where the client is connected, respond with a BSS transition management request which provides the list of candidate access points to roam to.
2. Unsolicited load-balance request: A feature that allows the AP to load balance clients across access points on the same controller to avoid AP overload. When the client counts exceed the configured load balance threshold for an AP, any new client that tries to associate with the AP is denied with an association response with status 17 (AP busy). Typically, the denied clients tries to associate to the same loaded AP even after the client gets an association reject, that is if from the RSSI perspective, that AP is their best option. For example, consider 40 users in a conference room serviced by one AP. With an 802.11v BSS Transition Management query, a load balance failure can be handled more smoothly where the AP sends a list of candidate APs to roam to instead.
3. Unsolicited optimized roam request: The wireless clients are expected to scan RF and roam to AP with the highest signal. However, some clients have displayed a sticky behavior where they stay with the AP to which they are associated, even when a neighbor AP provides a stronger signal. This is referred to as a sticky client problem. To address this problem, the 9800 controller supports a feature called optimized roam where the RSSI of the client data packets and data rate are monitored, and the client is proactively disassociated. The 802.11v BSS Transition Management Request enhances optimized roam which tells the client of an imminent disassociation and provides a list of APs to roam to.

Note: From TAC experience, Optimized Roam is not suitable for all networks. Make sure the coverage is good enough between access points to make this work as expected, otherwise more problems could come up if you enable it.
An 802.11v BSS Transition Management Request which when sent by an AP to a client is only a suggestion. The client can honor the suggestion or discard it. The 9800 wireless controller provides a configuration option called Imminent Disassociation for you to force the clients to disassociate if the client does not reassociate with another AP within a defined window of time. You can configure it only from CLI via command bss-transition disassociation-imminent under a specific WLAN profile.
Related Information
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
2.0 |
20-Feb-2024 |
Initial Release |
1.0 |
13-Feb-2024 |
Initial Release |
Contributed by Cisco Engineers
- Rosalia AlhouraniCisco Escalation Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback