Configure Verify and Troubleshoot Wired Guest in Wireless LAN Controller
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to configure, verify, and troubleshoot wired guest access in 9800 and IRCM with external web authentication.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
9800 WLC
AireOS WLC
Mobility Tunnel
ISE
It is assumed that a mobility tunnel between the two WLCs has been established prior to configuring wired guest access.
This aspect is outside the scope of this configuration example. For detailed instructions, please refer to the attached document titled Configuring Mobility Topologies on 9800
Components Used
9800 WLC version 17.12.1
5520 WLC version 8.10.185.0
ISE version 3.1.0.518
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
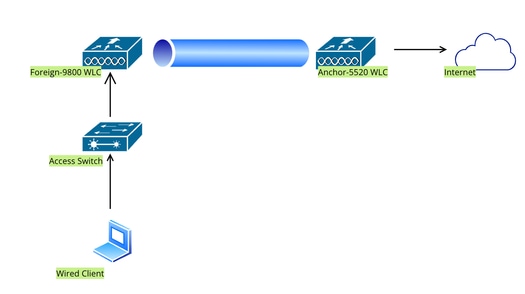
Configure Wired Guest on catalyst 9800 anchored to another catalyst 9800
Network Diagram
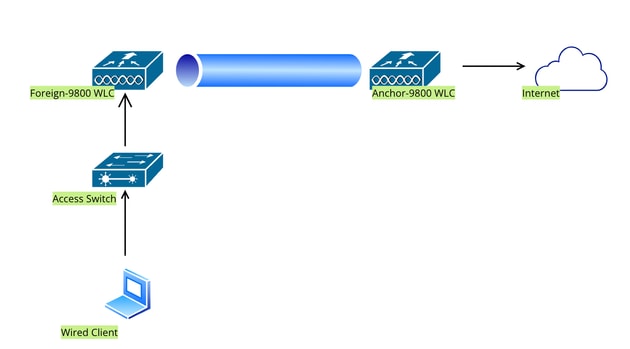 Network Topology
Network Topology
Configuration on Foreign 9800 WLC
Configure Web Parameter map
Step1: Navigate to Configuration > Security > Web Auth, select Global, verify the virtual IP address of the controller and Trustpoint mapping, and ensure the type is set to webauth.
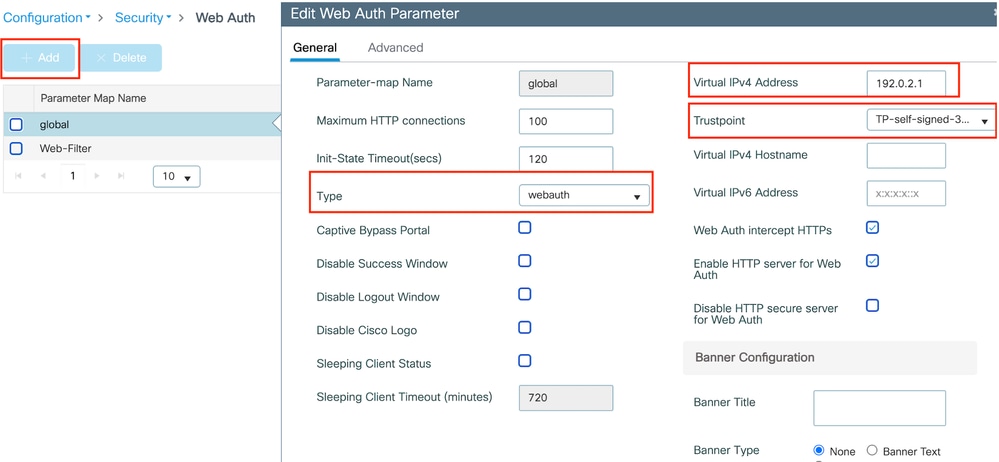 Global parameter map
Global parameter map

Note: Web Auth intercept HTTPs is an optional setting. If HTTPS redirection is required, the Web Auth intercept HTTPS option must be enabled. However, this configuration is not recommended as it increases CPU usage.
Step2: Under the Advanced tab, configure the external web page URL for client redirection. Set "Redirect URL for Login" and "Redirect On-Failure"; "Redirect On-Success" is optional. Once configured, a preview of the redirect URL is displayed on the Web Auth profile.
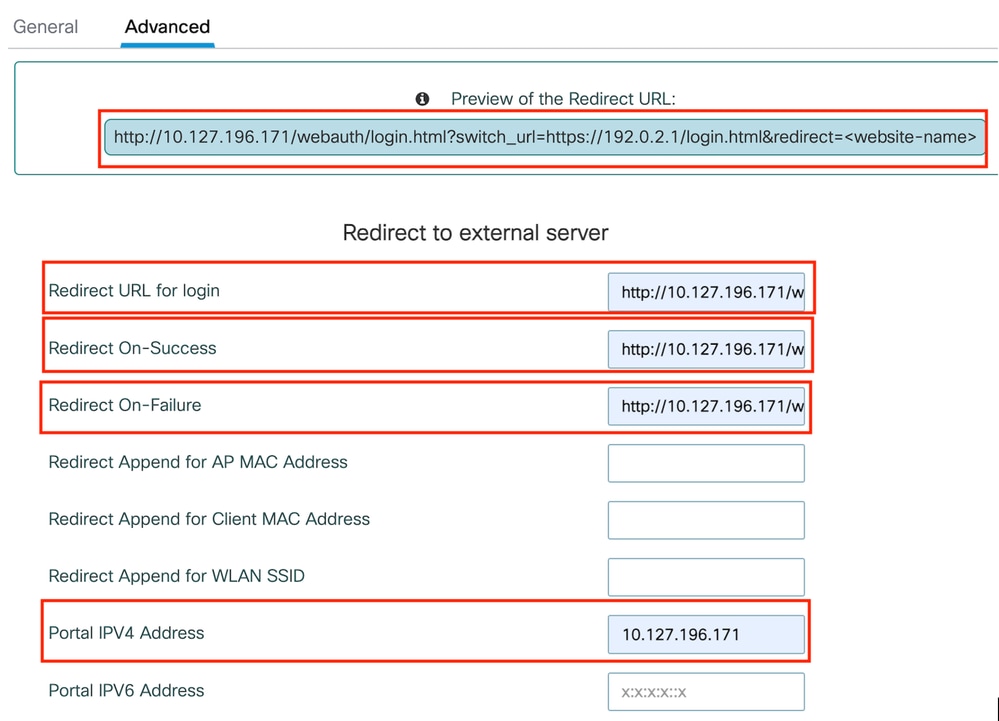 Advanced tab
Advanced tab
CLI Configuration
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
redirect for-login http://10.127.196.171/webauth/login.html
redirect on-success http://10.127.196.171/webauth/logout.html
redirect on-failure http://10.127.196.171/webauth/failed.html
redirect portal ipv4 10.127.196.171
intercept-https-enable
trustpoint TP-self-signed-3915430211
webauth-http-enable
Note: In this scenario, the global parameter map is used. As per requirement configure a custom web parameter map by selecting Add and, set the redirect URL under the Advanced tab. The Trustpoint and Virtual IP settings is inherited from the global profile.
AAA Settings:
Step1: Create a Radius Server:
Navigate to Configuration > Security > AAA, click "Add" under the Server/Group section, and on the "Create AAA Radius Server" page, enter the server name, IP address, and Shared Secret.
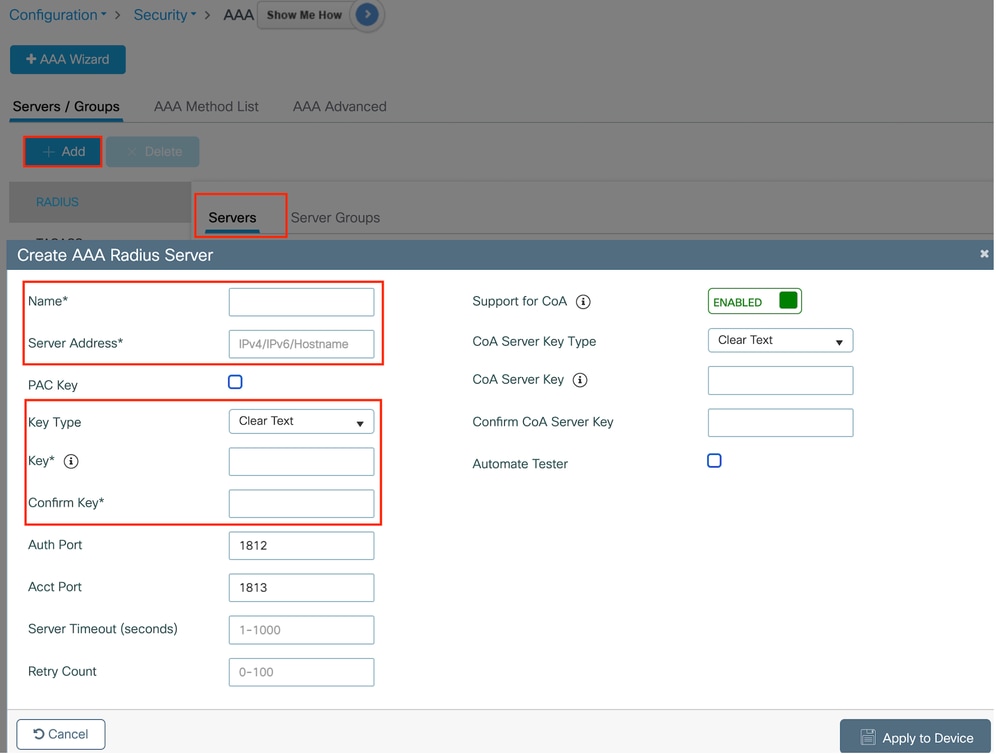 Radius server configuration
Radius server configuration
CLI Configuration
radius server ISE-Auth
address ipv4 10.197.224.122 auth-port 1812 acct-port 1813
key *****
server name ISE-Auth
Step 2: Create a RADIUS Server Group:
Select "Add" under the Server Groups section to define a server group and toggle the servers to be included in the group configuration.
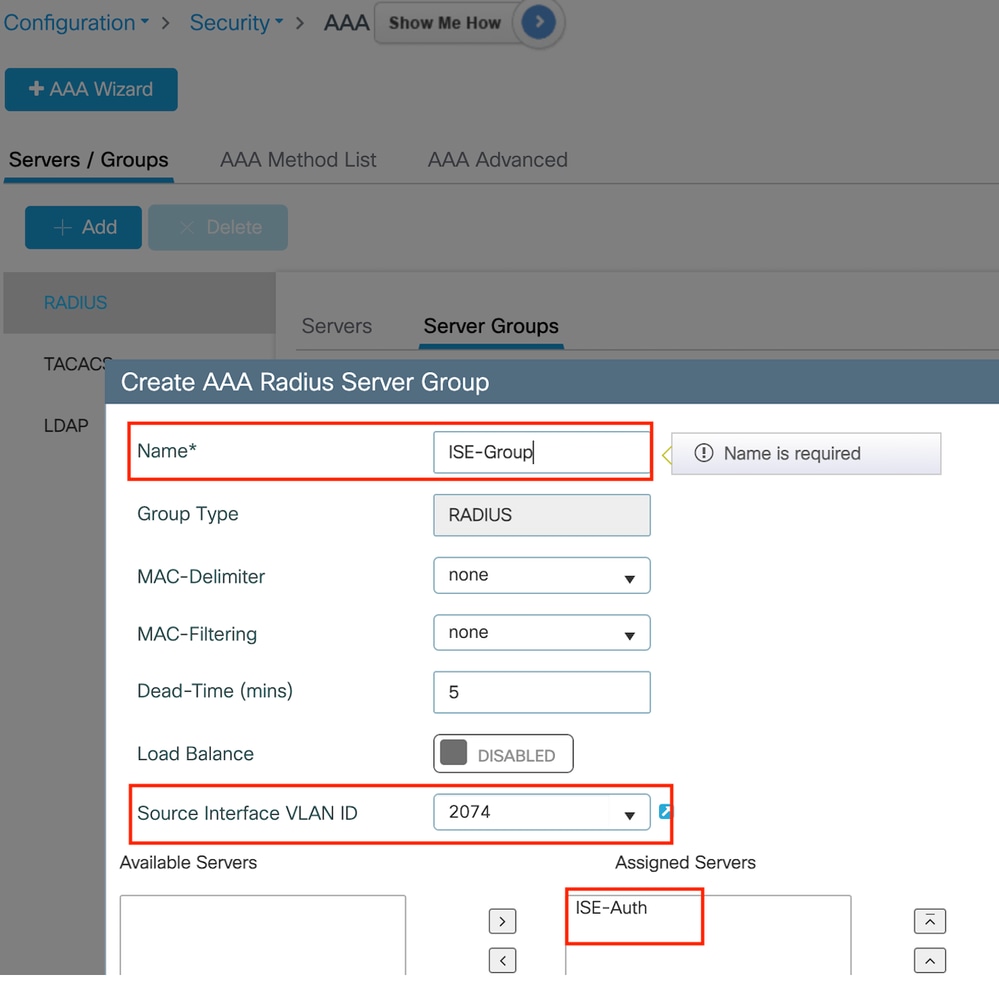 Radius server group
Radius server group
CLI Configuration
aaa group server radius ISE-Group
server name ISE-Auth
ip radius source-interface Vlan2074
deadtime 5
Step3: Configure AAA Method List:
Navigate to the AAA Method List tab, select Add under Authentication, define a method list name with Type as "login" and Group type as "Group," and map the configured authentication server group under the Assigned Server Group section.
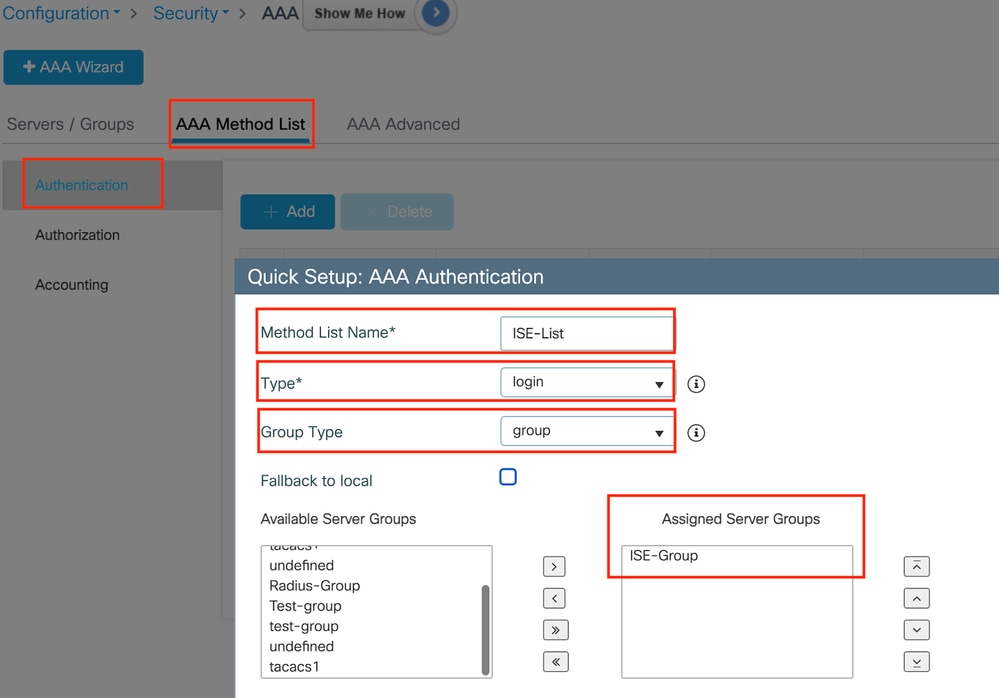 Authentication method list
Authentication method list
CLI configuration
aaa authentication login ISE-List group ISE-Group
Configure Policy profile
Step1: Navigate to Configuration > Tags & Profiles > Policy, name your new profile in the General tab, and enable it using the status toggle.
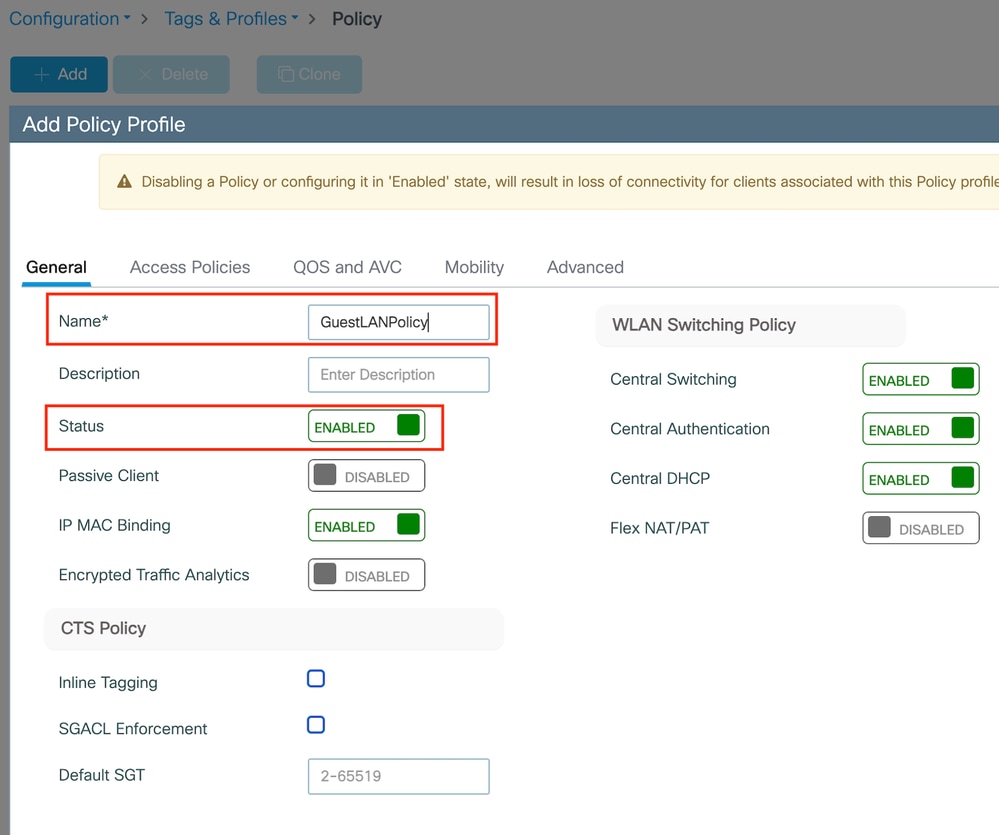 Policy Profile
Policy Profile
Step2: Under the Access Policies tab, assign a random vlan as vlan mapping is completed on the anchor controller. In this example, vlan 1 is configured
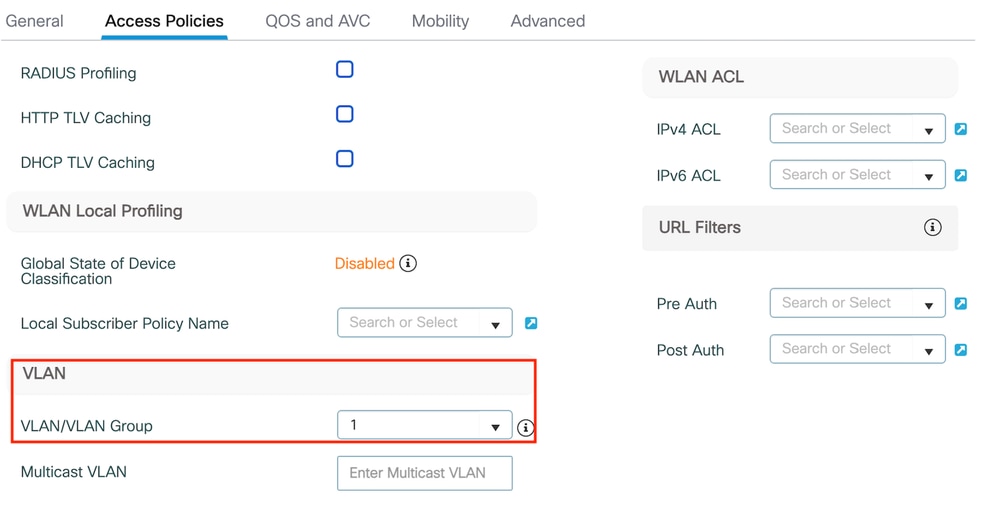 Access Policy tab
Access Policy tab
Step3:Under the Mobility tab, toggle the Anchor controller to Primary (1) and optionally configure Secondary and Tertiary mobility tunnels for redundancy requirements
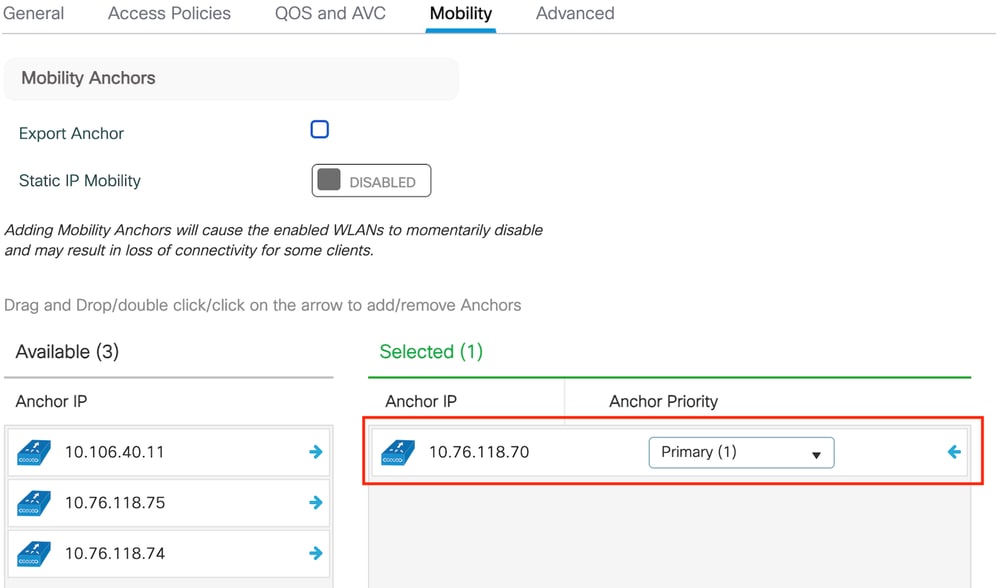 Mobility map
Mobility map
CLI Configuration
wireless profile policy GuestLANPolicy
mobility anchor 10.76.118.70 priority 1
no shutdown
Configure Guest LAN profile
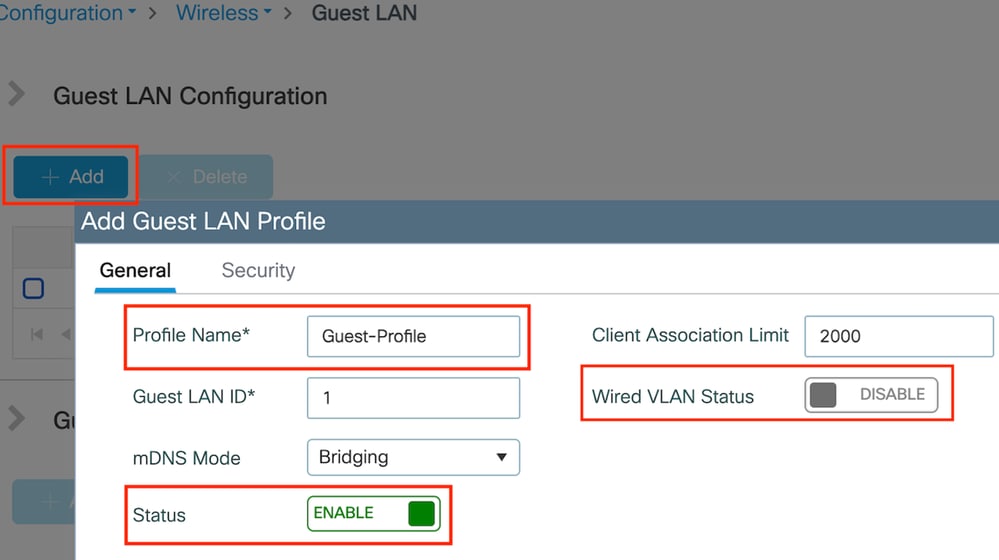
Step1: Navigate to Configuration > Wireless > Guest LAN, select Add, configure a unique profile name, enable Wired VLAN, enter the VLAN ID for wired guest users, and toggle the profile status to Enabled.
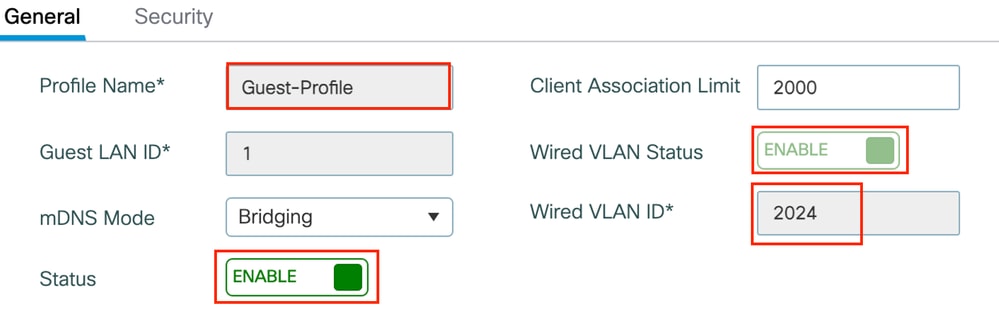 Guest LAN Profile
Guest LAN Profile
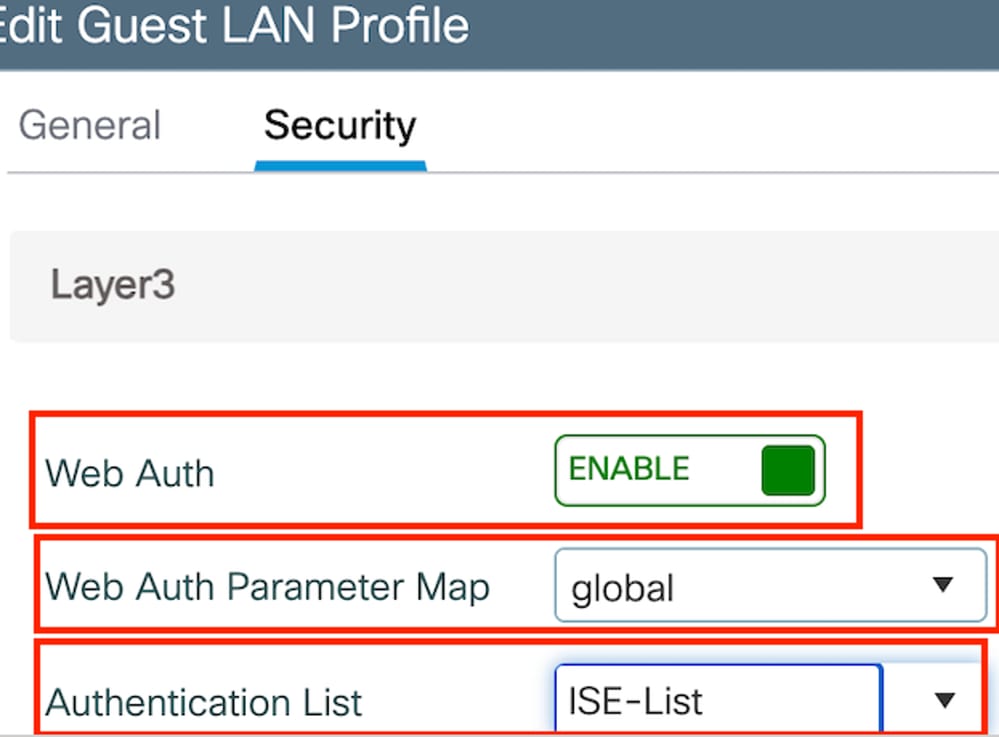
Step2: Under the Security tab, enable Web Auth, map the Web Auth parameter map, and select the Radius server from the Authentication drop-down list.
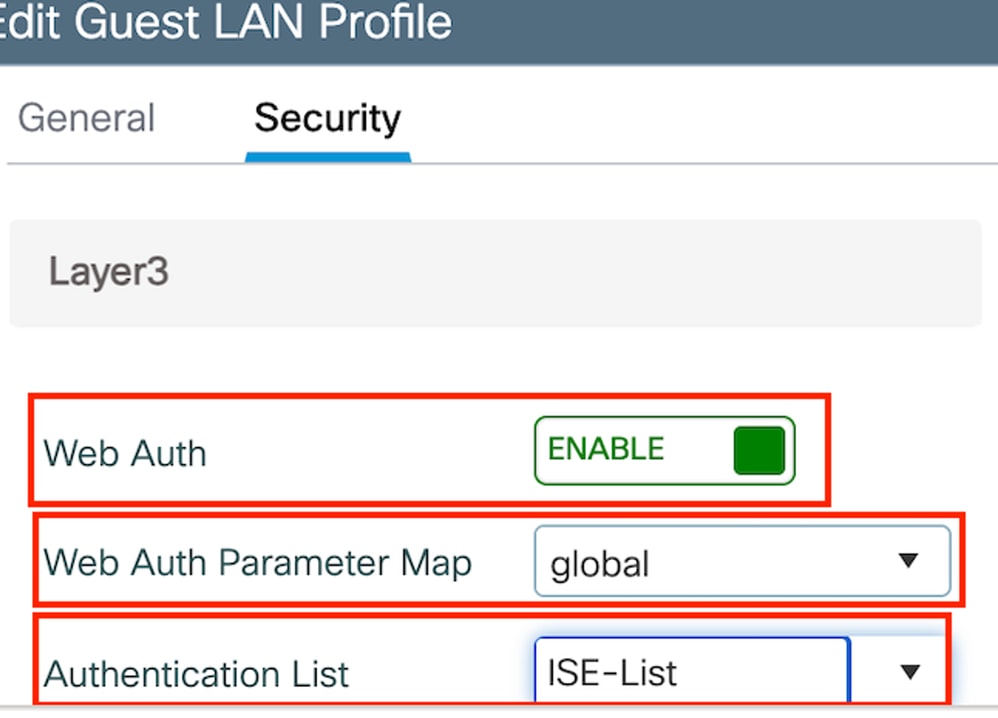 Guest LAN security tab
Guest LAN security tabCLI Configuration
guest-lan profile-name Guest-Profile 1 wired-vlan 2024
security web-auth authentication-list ISE-List
security web-auth parameter-map globalGuest LAN MAP
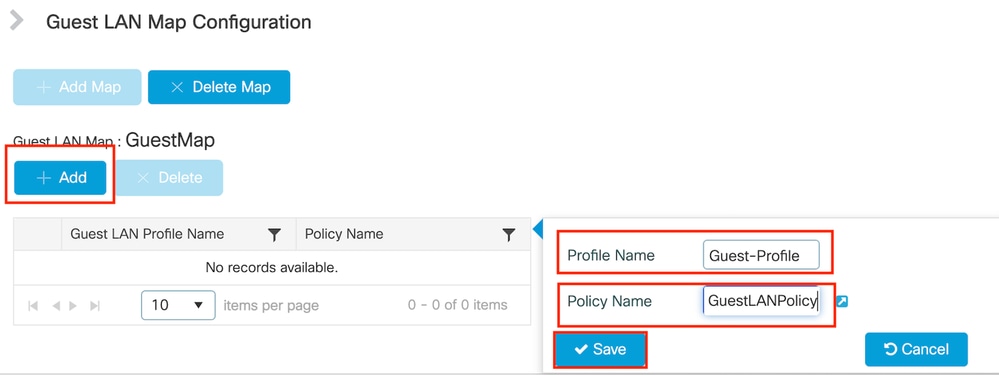
Navigate to Configuration > Wireless > Guest LAN.
Under the Guest LAN MAP configuration section, select Add and map the Policy profile and Guest LAN profile
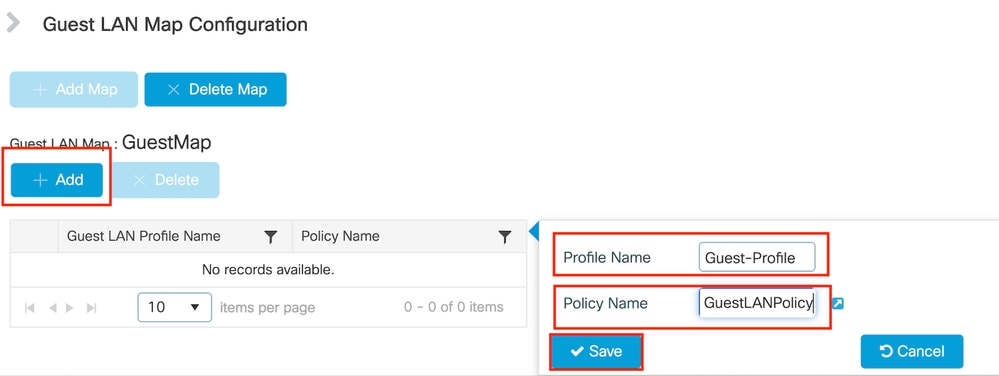 Guest LAN MAP
Guest LAN MAP
CLI Configuration
wireless guest-lan map GuestMap
guest-lan Guest-Profile policy GuestLANPolicy
Configuration on Anchor 9800 WLC
Configure Web Parameter map
Step1: Navigate to Configuration > Security > Web Auth, select Global, verify the virtual IP address of the controller and Trustpoint mapping, and ensure the type is set to webauth.
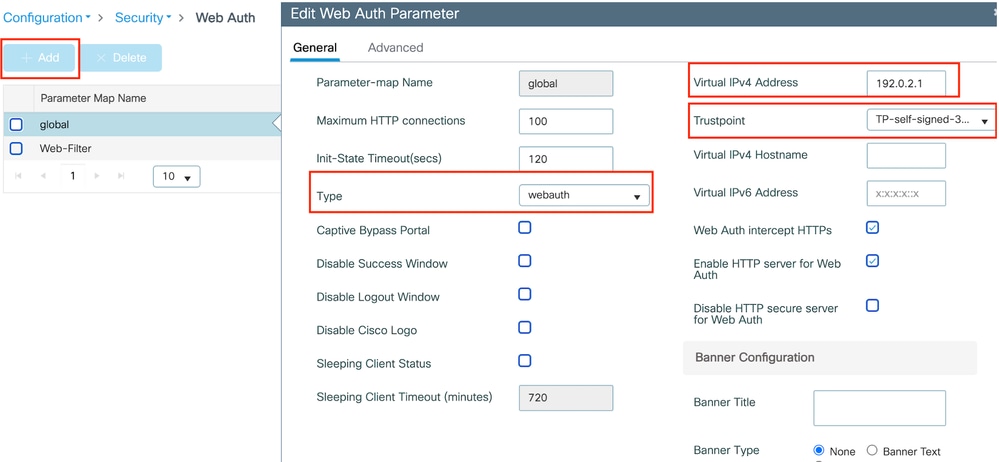 Global parameter map
Global parameter map
Step2: Under the Advanced tab, configure the external web page URL for client redirection. Set "Redirect URL for Login" and "Redirect On-Failure"; "Redirect On-Success" is optional.
Once configured, a preview of the redirect URL is displayed on the Web Auth profile.
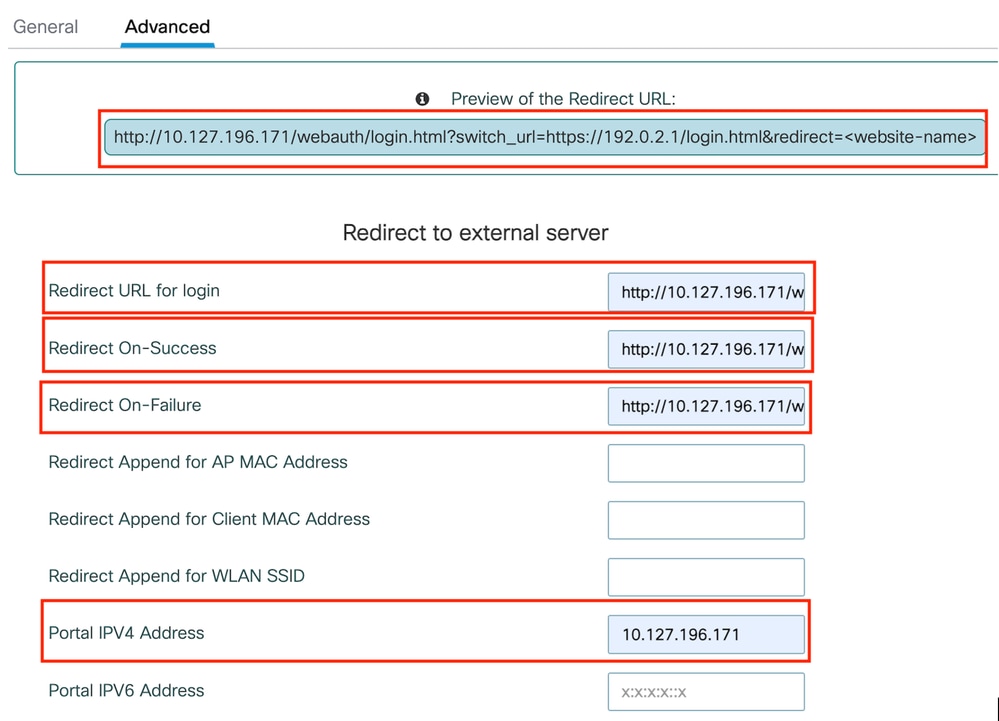 Advanced tab
Advanced tab
CLI Configuration
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
redirect for-login http://10.127.196.171/webauth/login.html
redirect on-success http://10.127.196.171/webauth/logout.html
redirect on-failure http://10.127.196.171/webauth/failed.html
redirect portal ipv4 10.127.196.171
intercept-https-enable.
trustpoint TP-self-signed-3915430211
webauth-http-enable
AAA Settings:
Step1: Create a Radius Server:
Navigate to Configuration > Security > AAA, click Add under the Server/Group section, and on the "Create AAA Radius Server" page, enter the server name, IP address, and Shared Secret.
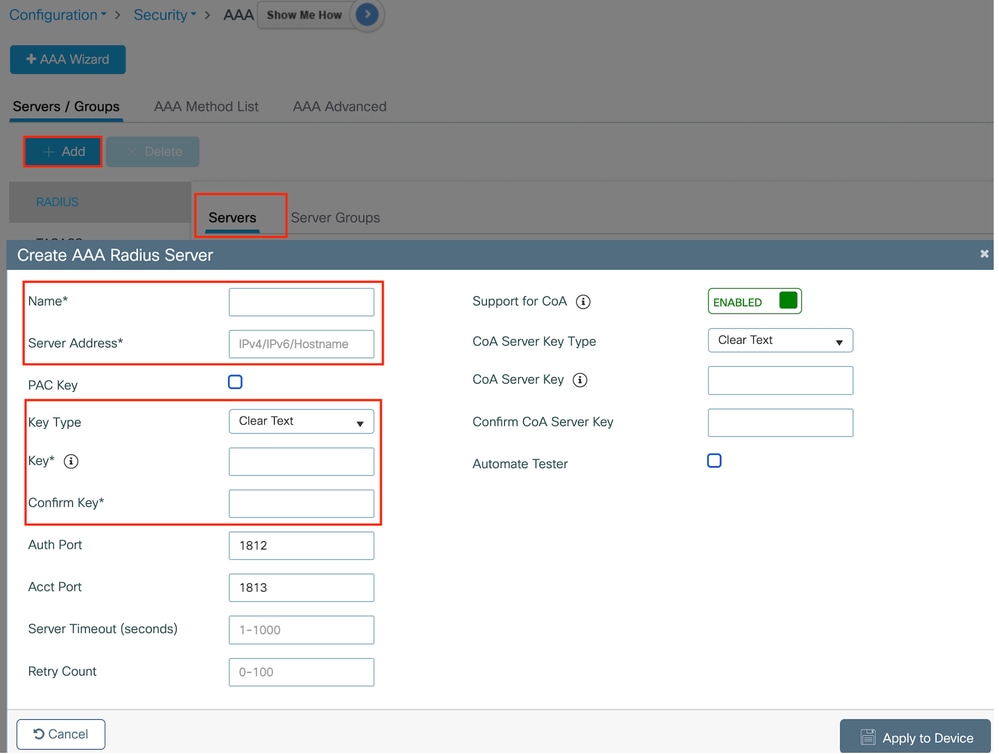 Radius server configuration
Radius server configuration
CLI Configuration
radius server ISE-Auth
address ipv4 10.197.224.122 auth-port 1812 acct-port 1813
key *****
server name ISE-Auth
Step 2: Create a RADIUS Server Group:
Select Add under the Server Groups section to define a server group and toggle the servers to be included in the group configuration.
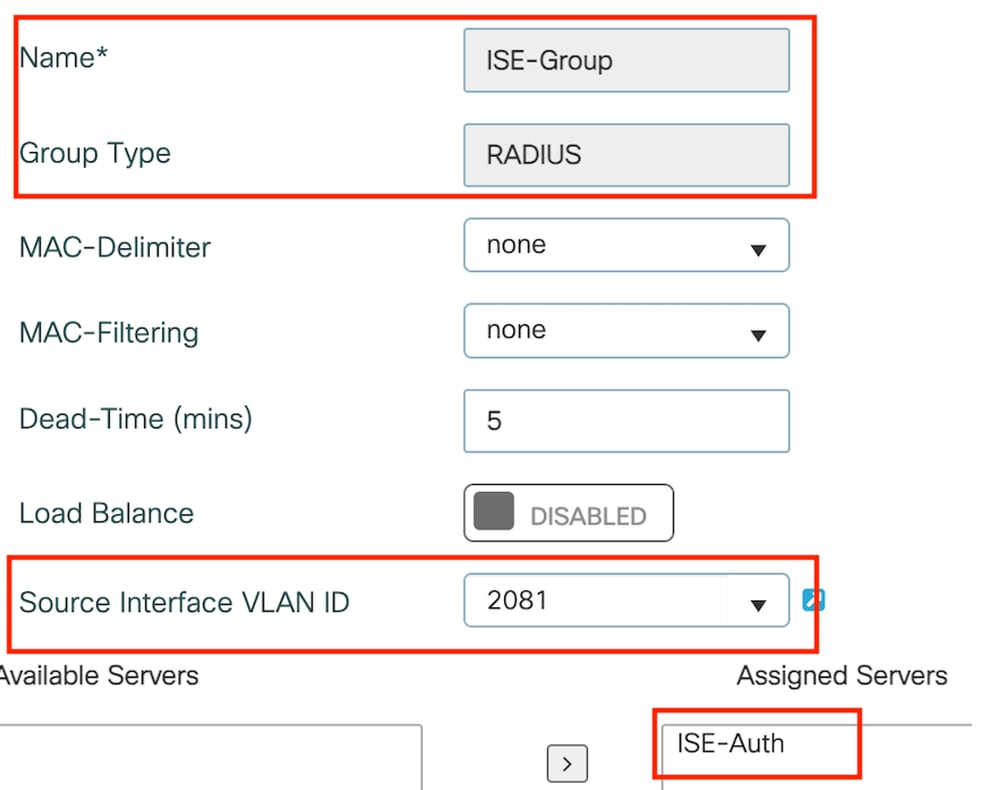 Anchor radius group
Anchor radius group
CLI Configuration
aaa group server radius ISE-Group
server name ISE-Auth
ip radius source-interface Vlan2081
deadtime 5
Step3: Configure AAA Method List:
Navigate to the AAA Method List tab, select Add under Authentication, define a method list name with Type as "login" and Group type as "Group," and map the configured authentication server group under the Assigned Server Group section.
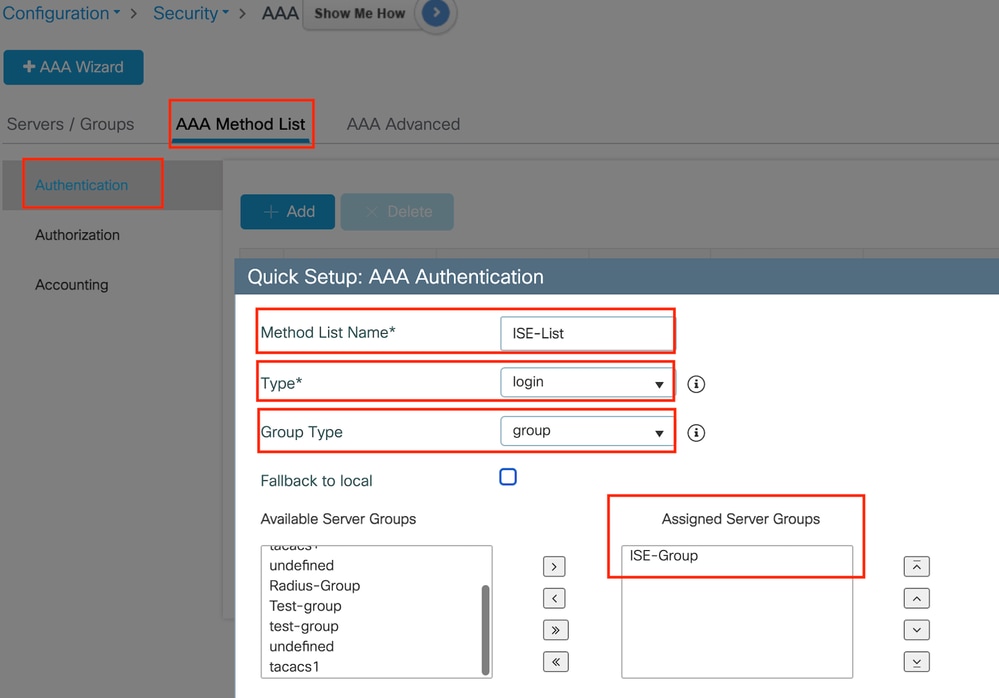 Authentication method list
Authentication method list
CLI configuration
aaa authentication login ISE-List group ISE-GroupConfigure Policy profile
Step1: Navigate to Configuration > Tag & Profiles > Policy, configure the policy profile with the same name as on the foreign controller and enable the profile.
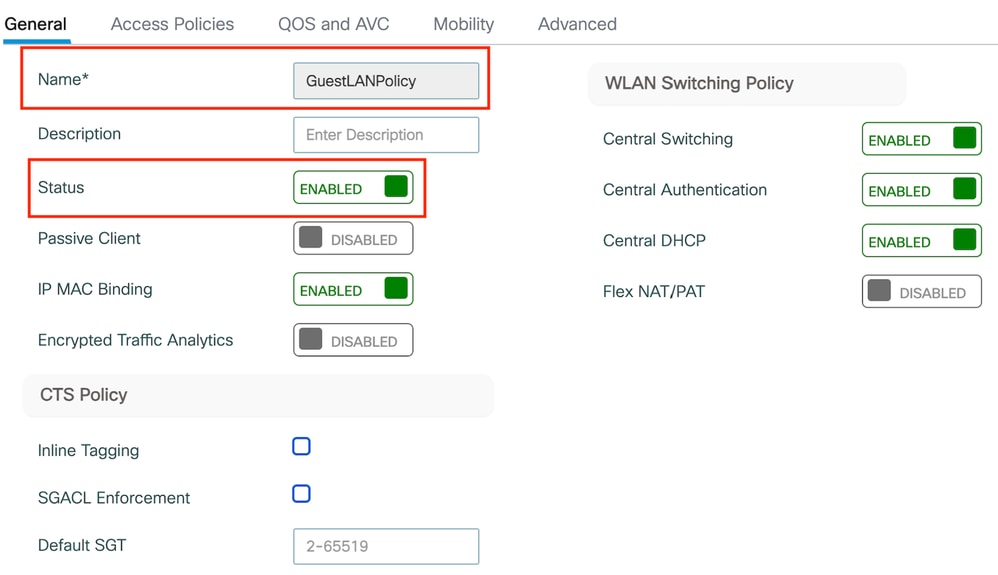 Anchor Policy Profile
Anchor Policy Profile
Step2: Under the Access Policies, map the wired client vlan from the drop down list
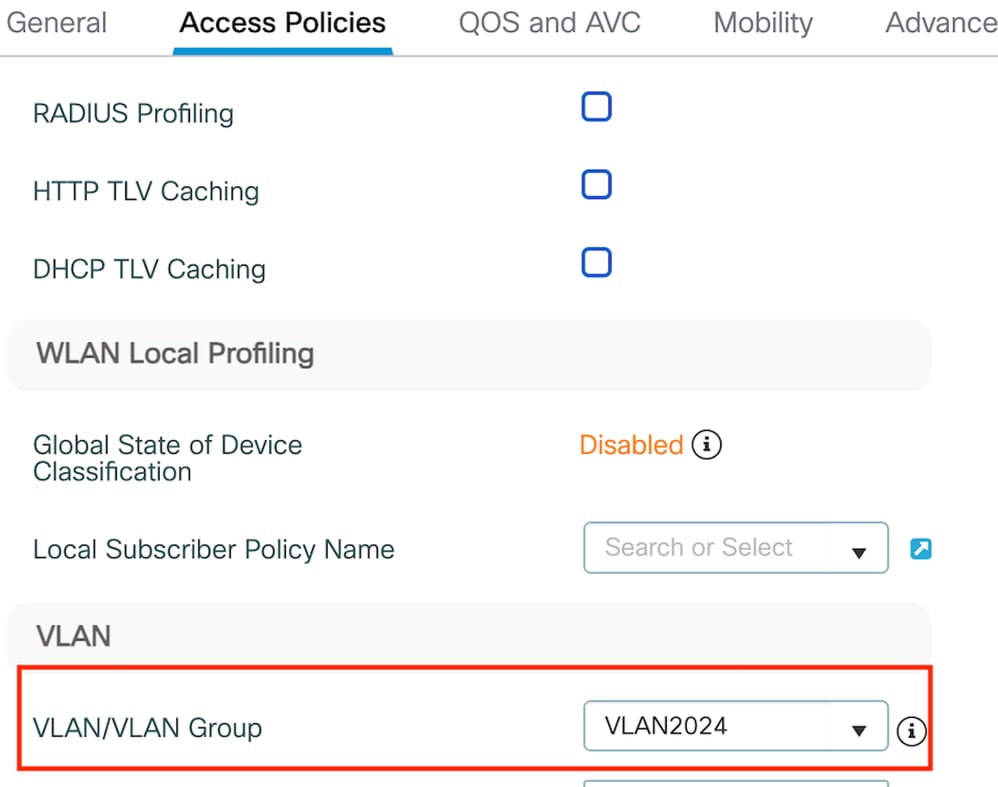 Access Policies tab
Access Policies tab

Note: Configuration of the policy profile must match on both the Foreign and Anchor controllers, except for the VLAN.
Step3: Under the Mobility tab, check box Export Anchor.
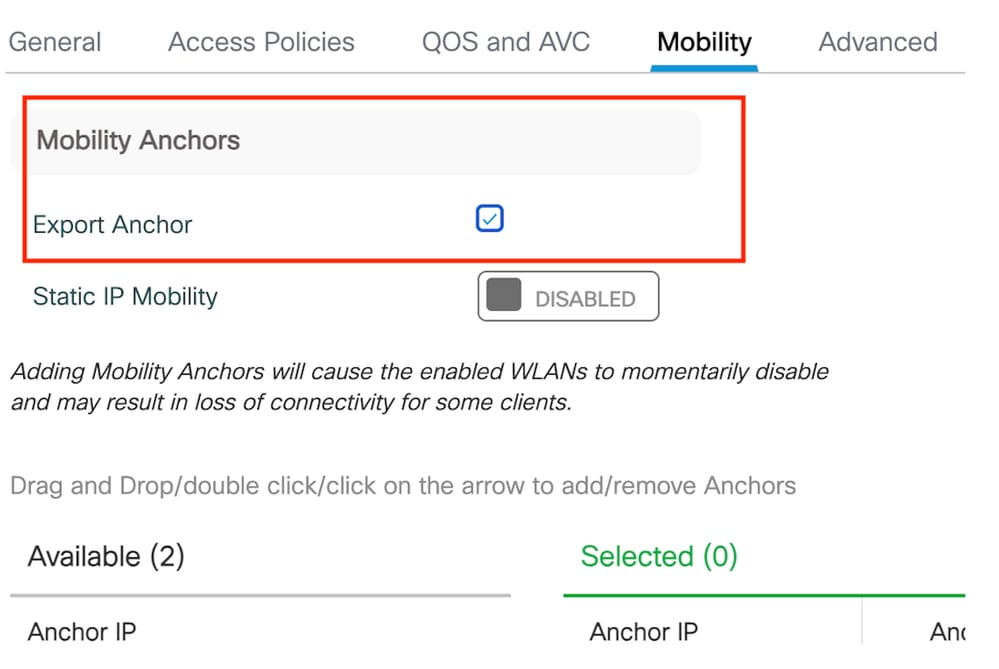 Export Anchor
Export Anchor

Note: This configuration designates the 9800 Wireless LAN Controller (WLC) as the anchor WLC for any WLAN associated with the specified Policy Profile. When a foreign 9800 WLC redirects clients to the anchor WLC, it provides details about the WLAN and the Policy Profile assigned to the client. This enables the anchor WLC to apply the appropriate local Policy Profile based on the received information.
CLI Configuration
wireless profile policy GuestLANPolicy
mobility anchor
vlan VLAN2024
no shutdown
Configure Guest LAN Profile
Step1: Navigate to Configuration > Wireless > Guest LAN, then select Add to create and configure the Guest LAN profile. Ensure the profile name matches that of the foreign controller. Note that the Wired VLAN must be disabled on the Anchor controller.
 Guest LAN Profile
Guest LAN Profile
Step2: In the security settings, enable Web Auth and then configure the Web Auth parameter map and Authentication List.

Note: The Guest LAN profile configuration must be identical between the Foreign and Anchor controllers except for the Wired VLAN status
CLI Configuration
guest-lan profile-name Guest-Profile 1
security web-auth authentication-list ISE-List
security web-auth parameter-map global
Guest LAN MAP
Step1: Navigate to Configuration > Wireless > Guest LAN. In the Guest LAN MAP configuration section, select Add and map the Policy Profile to the Guest LAN profile.
 Guest LAN MAP
Guest LAN MAP
wireless guest-lan map GuestMap
guest-lan Guest-Profile policy GuestLANPolicy
Configure Wired Guest on catalyst 9800 anchored to AireOS 5520 Controller
 Network Topology
Network Topology
Configuration on Foreign 9800 WLC
Configure Web Parameter map
Step1: Navigate to Configuration > Security > Web Auth and select Global. Verify that the virtual IP address of the controller and the Trustpoint are correctly mapped on the profile, with the type set to webauth.
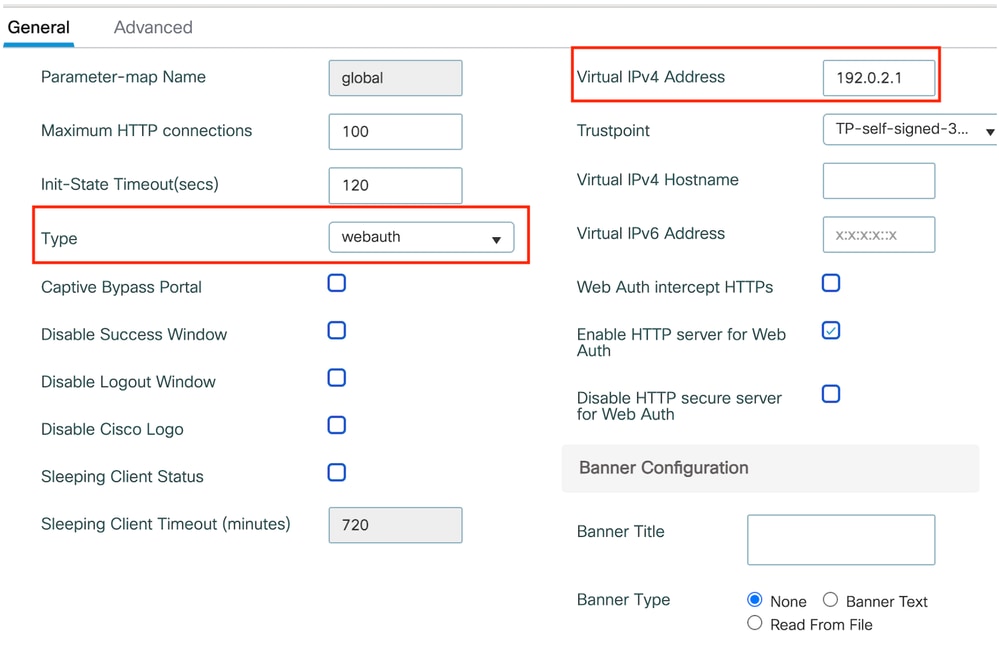 Web Parameter map
Web Parameter map
Step2: Under the Advanced tab, specify the external web page URL to which clients must be redirected. Configure the Redirect URL for Login and Redirect On-Failure. The Redirect On-Success setting is an optional configuration.
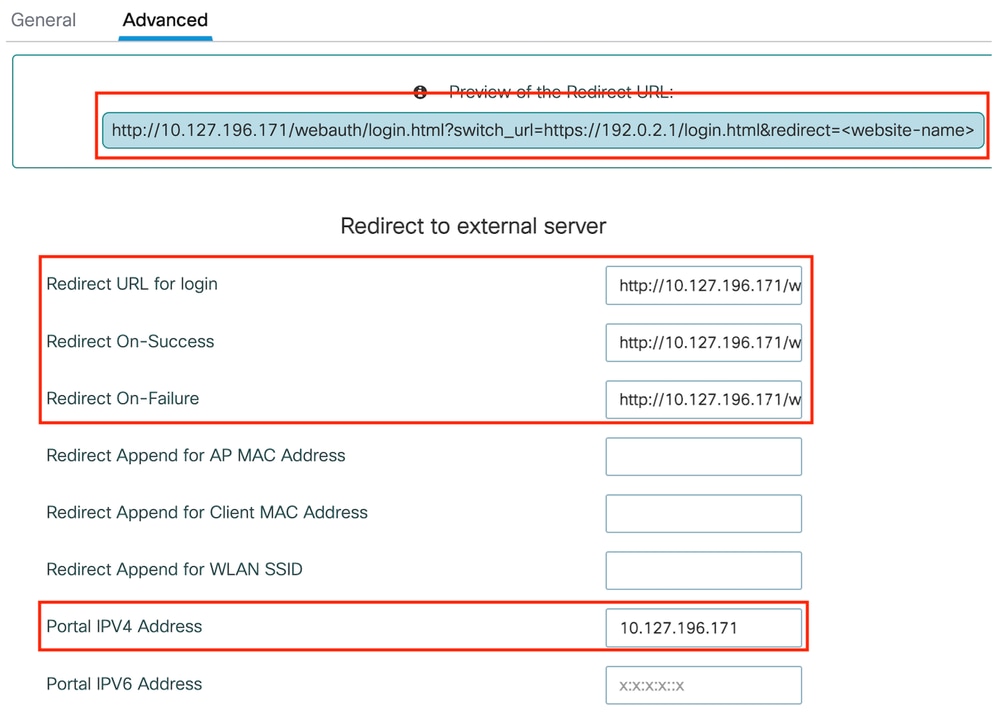 Advanced tab
Advanced tab
CLI configuration
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
redirect for-login http://10.127.196.171/webauth/login.html
redirect on-success http://10.127.196.171/webauth/logout.html
redirect on-failure http://10.127.196.171/webauth/failed.html
redirect portal ipv4 10.127.196.171
trustpoint TP-self-signed-3010594951
webauth-http-enable

Note: For AAA configuration, please refer to the configuration details provided in "" section for the Foreign 9800 WLC.
Configure Policy profile
Step1: Navigate to Configuration > Tags & Profiles > Policy. Select Add, and in the General tab, provide a name for the profile and enable the status toggle.
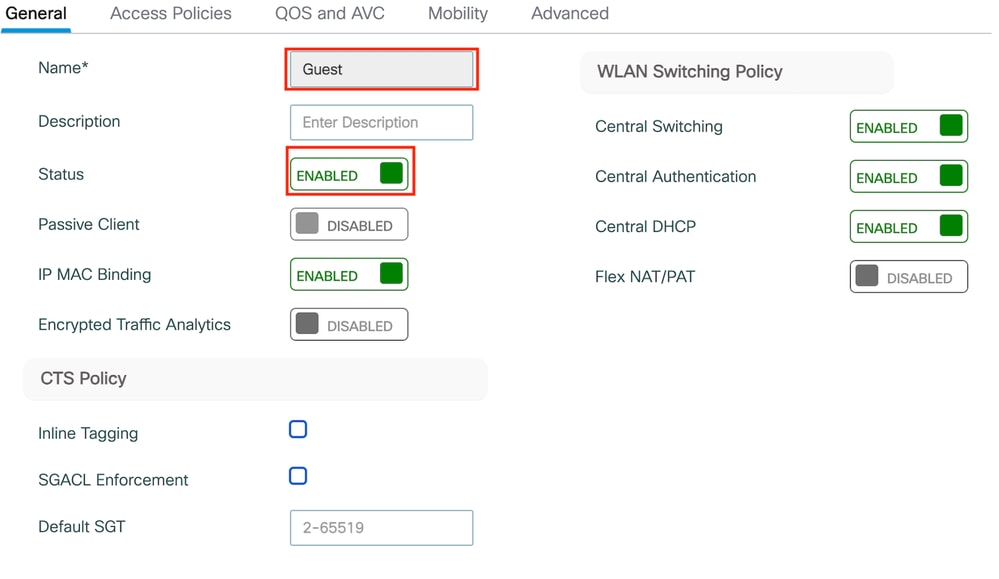 Policy profile
Policy profile
Step2: In the Access Policies tab, assign a random VLAN.
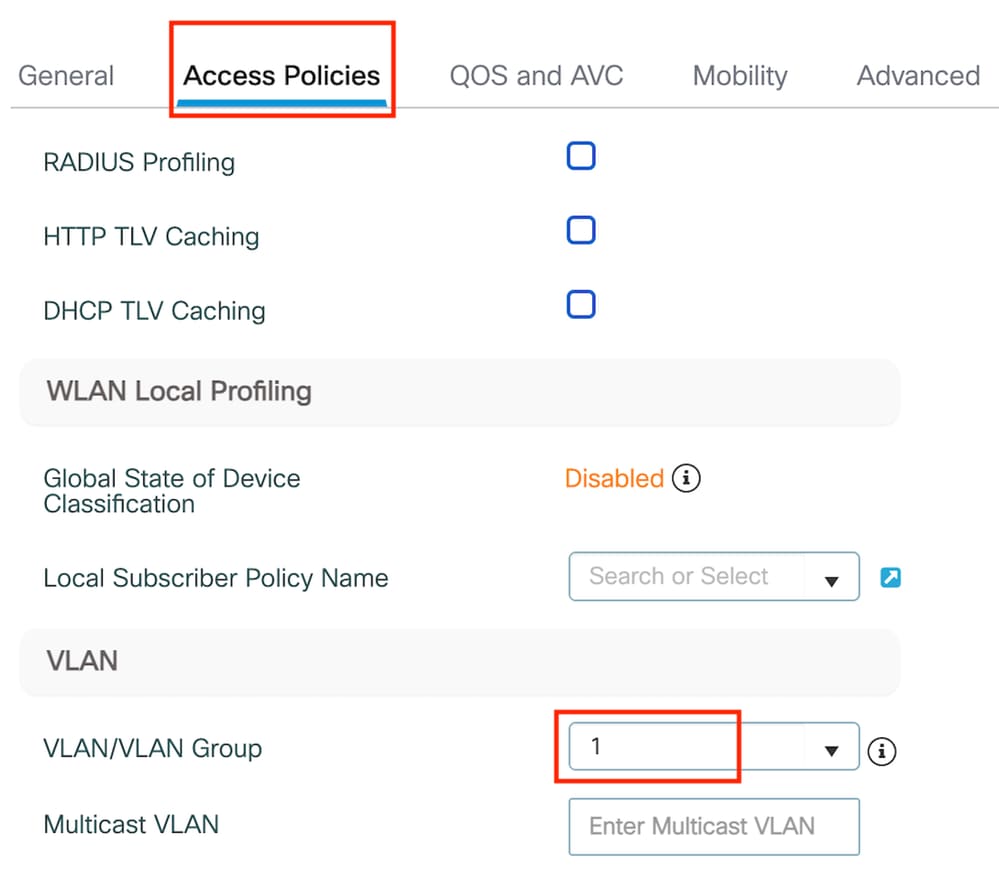 Access Policies
Access Policies
Step3: In the Mobility tab, toggle the Anchor controller and set its priority to Primary (1)
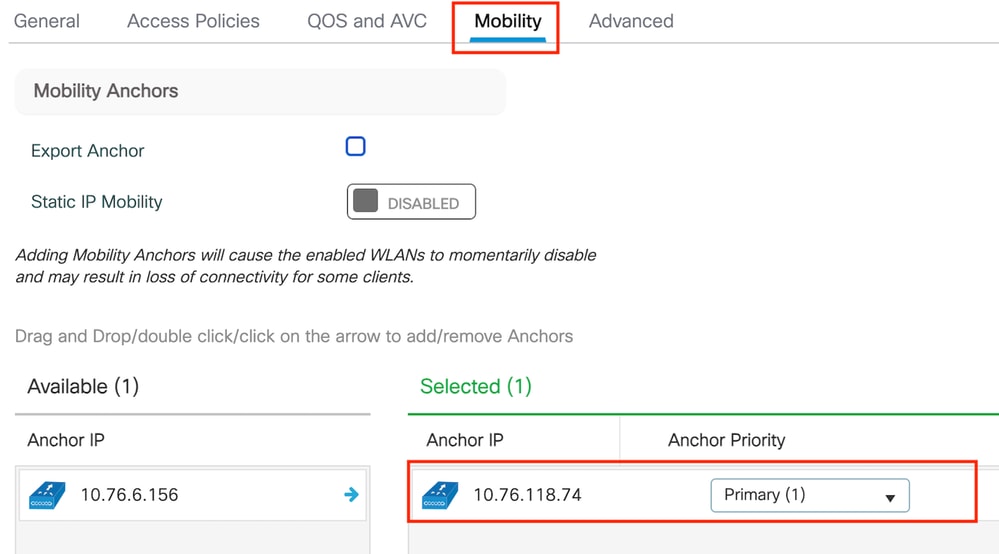 Mobility tab
Mobility tab

Note: The Policy profile of the 9800 Foreign WLC must match with the Guest LAN profile of the 5520 Anchor WLC except for the vlan configuration
CLI Configuration
wireless profile policy Guest
no accounting-interim
exclusionlist timeout 180
no flex umbrella dhcp-dns-option
mobility anchor 10.76.118.74 priority 1
no shutdown
Configure Guest LAN profile
Step1: Navigate to Configuration > Wireless > Guest LAN and select Add. Configure a unique profile name and enable Wired VLAN, specifying the VLAN ID dedicated for wired guest users. Finally, toggle the profile status to Enabled.
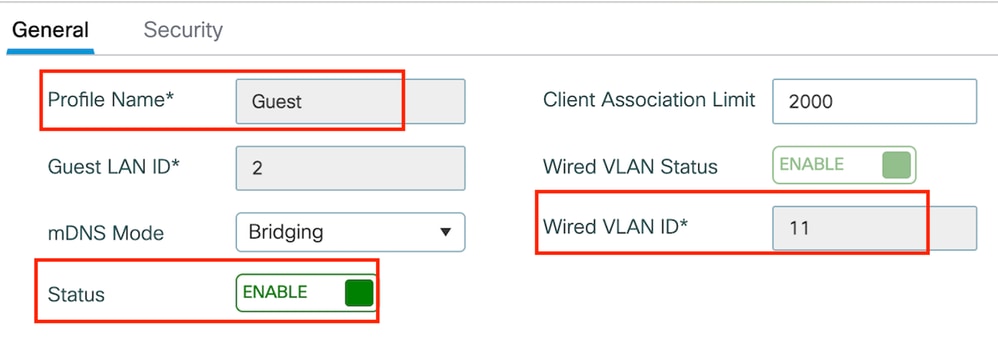 Guest LAN Policy
Guest LAN Policy
Step2: Under the Security tab, enable Web Auth, map the Web Auth parameter map, and select the RADIUS server from the Authentication drop-down list.
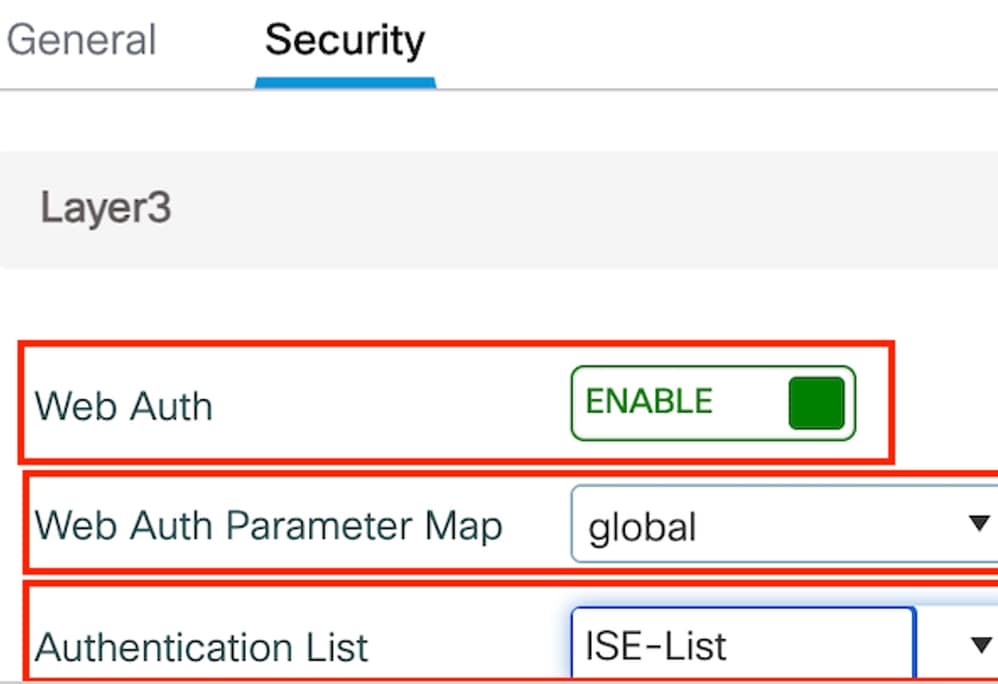 Security tab
Security tab

Note: The Guest LAN profile name must be the same for the 9800 Foreign and 5520 Anchor controller
CLI Configuration
guest-lan profile-name Guest 2 wired-vlan 11
security web-auth authentication-list ISE-List
security web-auth parameter-map global
Guest LAN MAP
Step1: Navigate to Configuration > Wireless > Guest LAN. In the Guest LAN MAP configuration section, select Add and map the Policy Profile to the Guest LAN profile.
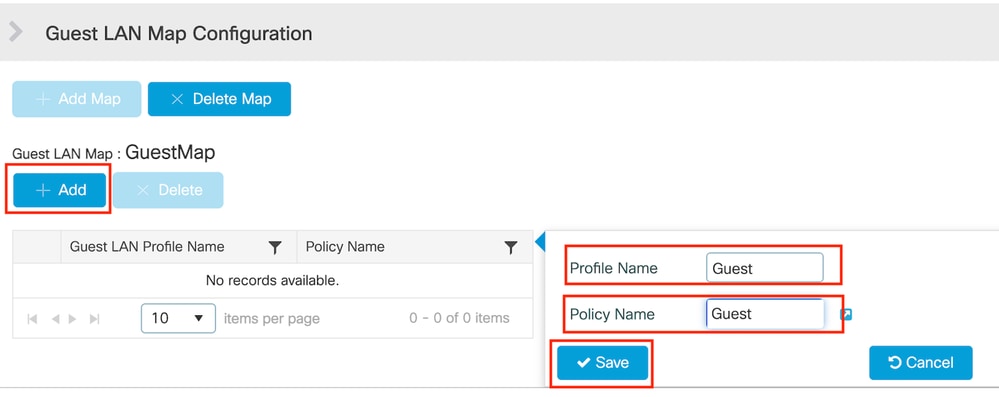 Guest LAN MAP
Guest LAN MAP
CLI Configuration
wireless guest-lan map GuestMap
guest-lan Guest policy Guest
Configuration on Anchor 5520 WLC
Configure Web Authentication
Step1: Navigate to Security > Web Auth > Web Login Page. Set the Web Authentication type to External (Redirect to external server) and configure the external Web Auth URL. The Redirect URL after login is optional and can be configured if clients need to be redirected to a dedicated page after successful authentication.
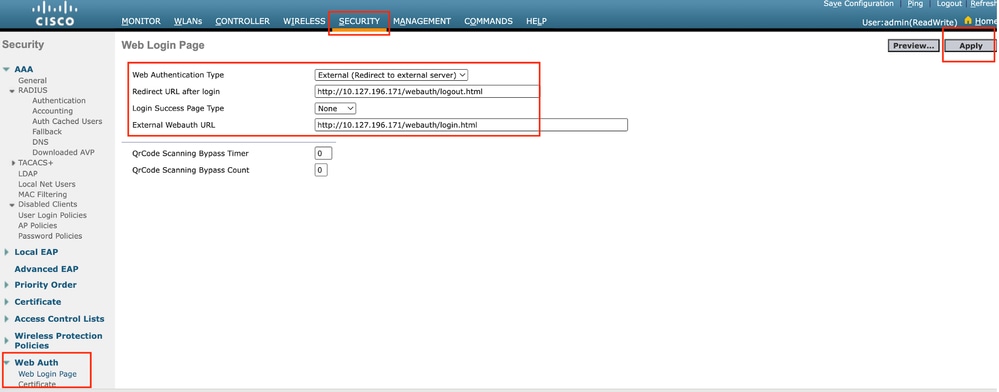 Web Auth settings
Web Auth settings
AAA Settings:
Step1: Configure radius server
Navigate to Security > Radius > Authentication > New.
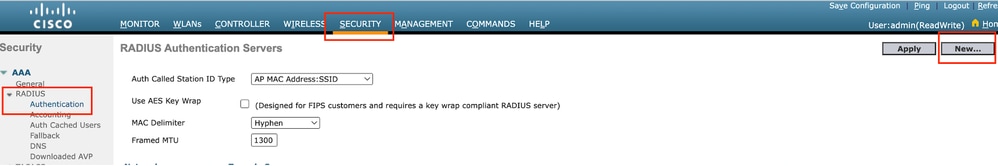 Radius Server
Radius Server
Step2: Configure the RADIUS server IP and shared secret on the controller. Toggle the server status to Enabled and check the Network User checkbox.
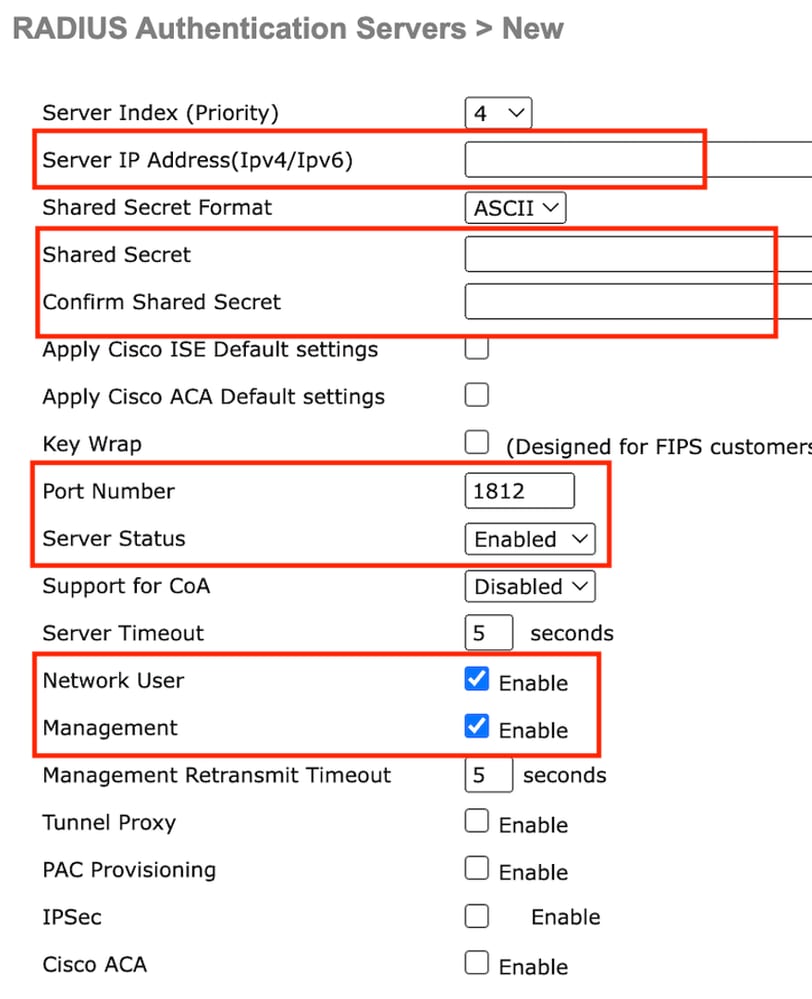 Server configuration
Server configuration
Configure Access Control List
Step1: Navigate to Security > Access Control List and select New. Create a Pre-Authentication ACL that permits traffic to DNS and the external web server.
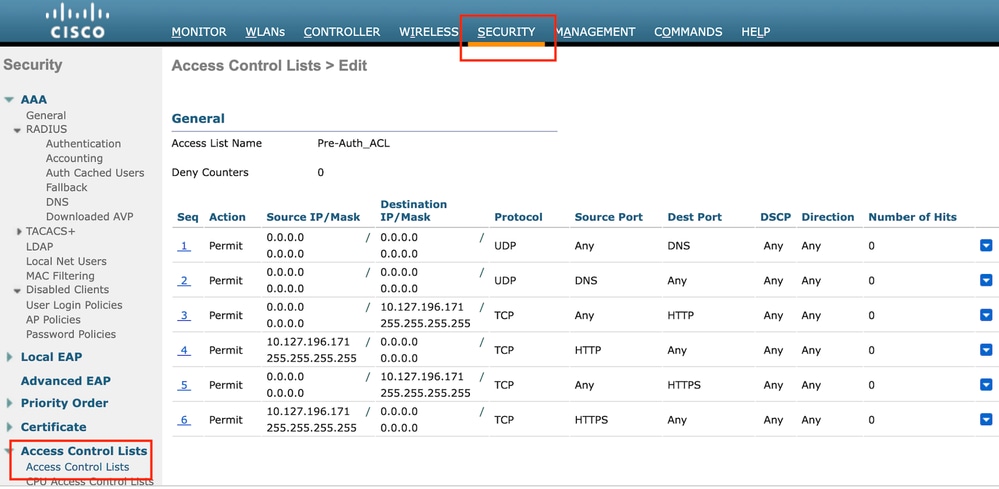 Access list to permit traffic to web server
Access list to permit traffic to web server
Configure Guest LAN profile
Step1: Navigate to WLANs > select Create New .
Select Type as Guest LAN and configure the same name as the policy profile of the 9800 Foreign controller.
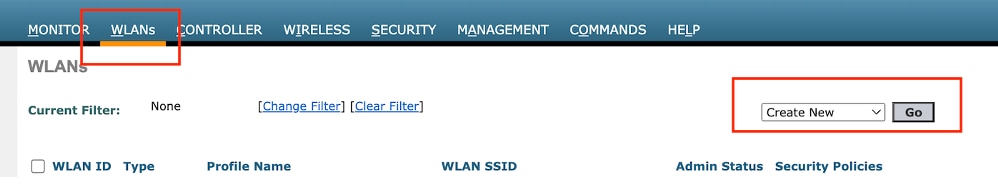 Create Guest LAN
Create Guest LAN
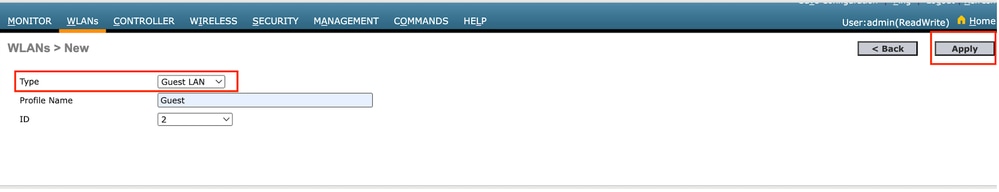 Guest LAN Profile
Guest LAN Profile
Step2: Map the Ingress and Egress interfaces on the Guest LAN profile.
The Ingress interface in this case is none because the ingress interface is the EoIP tunnel from the Foreign controller.
The Egress interface is the VLAN where the wired client physically connects .
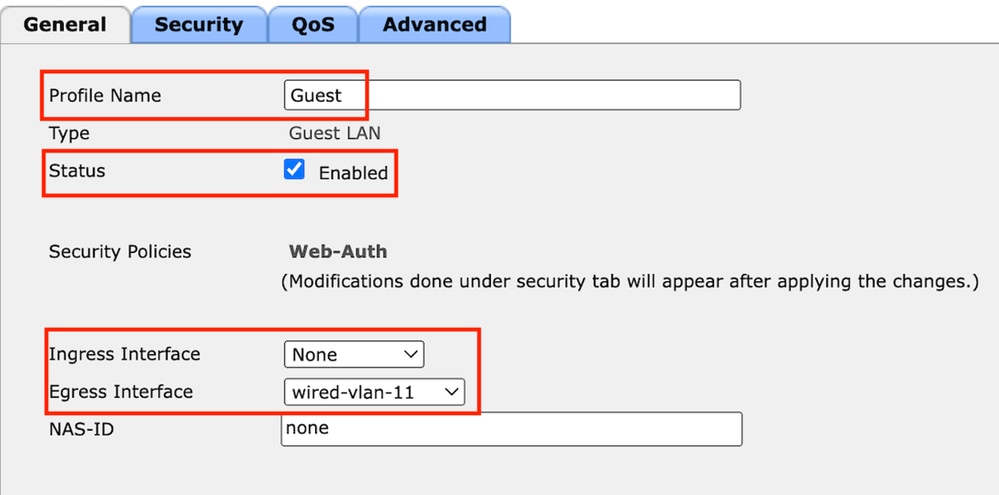 Guest LAN profile
Guest LAN profile
Step3: Under the Security tab, select Layer 3 security as Web Authentication and map the pre-authentication ACL.
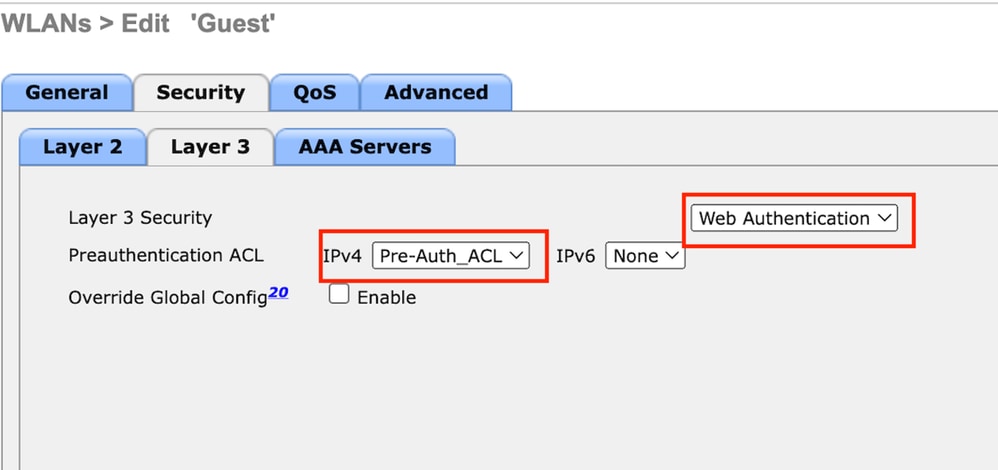 Guest LAN security tab
Guest LAN security tab
Step4: Navigate to Security > AAA Server.
Select the drop down and map the radius server to the Guest LAN profile.
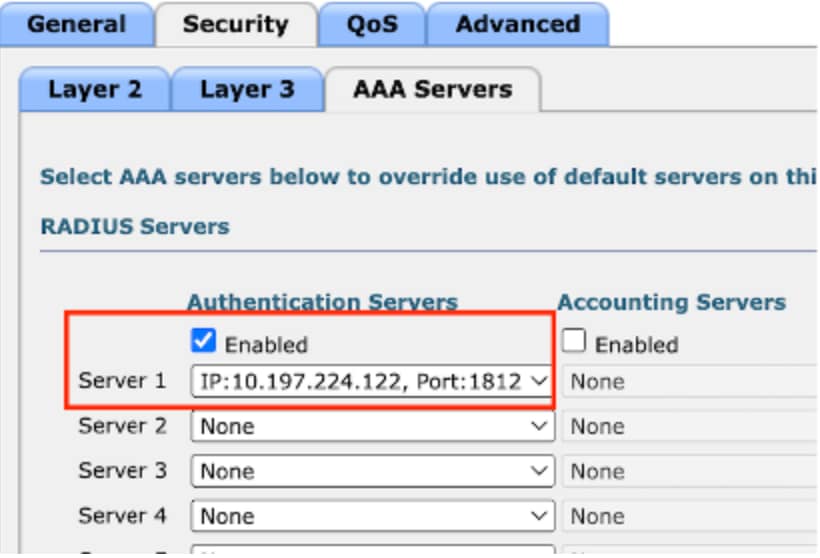 Map radius server to guest LAN profile
Map radius server to guest LAN profile
Step5: Navigate to WLAN. Hover over the drop down icon of the Guest LAN profile and select Mobility Anchors.

Step6: Select Mobility Anchor Create to configure the controller as export anchor for this Guest LAN profile.
 Mobility Anchor Create
Mobility Anchor Create
Configure Wired Guest on AireOS 5520 anchored to catalyst 9800
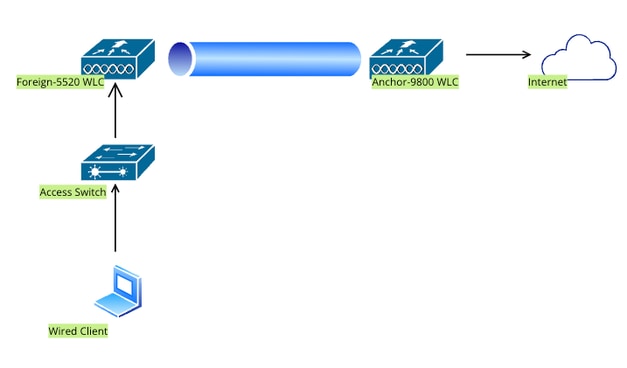 Network Topology
Network Topology
Configuration on Foreign 5520 WLC
Controller Interface Configuration
Step1: Navigate to Controller > Interfaces > New. Configure an Interface name, VLAN ID and enable Guest LAN.
Wired Guest requires two dynamic interfaces.
First, create a Layer 2 dynamic interface and designate it as Guest LAN. This interface serves as the ingress interface for Guest LAN, where wired clients physically connect.
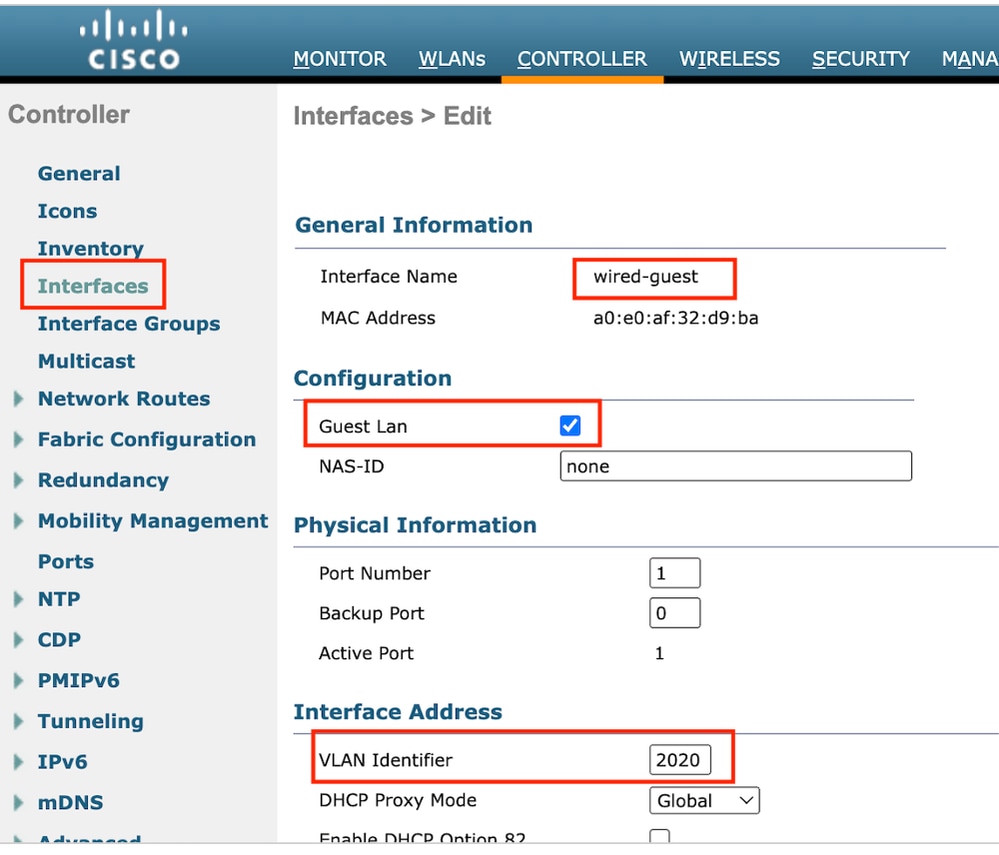 Ingress Interface
Ingress Interface
Step2: Navigate to Controller > Interfaces > New. Configure an Interface name, VLAN ID.
The second dynamic interface must be a Layer 3 interface on the controller, the wired clients receive IP address from this vlan subnet. This interface serves as the egress interface for the Guest LAN profile.
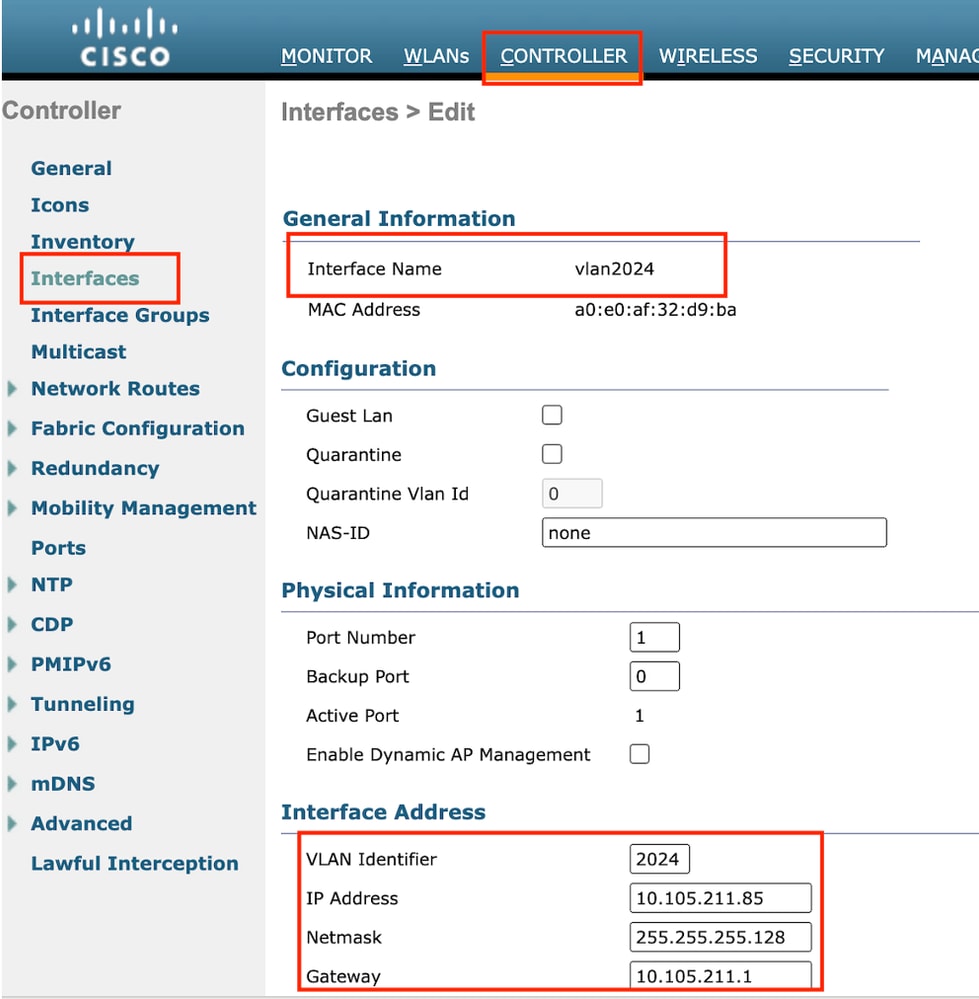 Egress Interface
Egress Interface
Switch Port configuration
Wired Guest users connect to Access layer switch, these designated ports must be configured with VLAN in which Guest LAN is enabled on the controller
Access layer switch port configuration
interface gigabitEthernet <x/x/x>
description Wired Guest Access
switchport access vlan 2020
switchport mode access
end
Foreign controller uplink port configuration
interface TenGigabitEthernet<x/x/x>
description Trunk port to the Foreign WLC
switchport mode trunk
switchport trunk native vlan 2081
switchport trunk allowed vlan 2081,2020
end
Anchor controller uplink port configuration
interface TenGigabitEthernet<x/x/x>
description Trunk port to the Anchor WLC
switchport mode trunk
switchport trunk native vlan 2081
switchport trunk allowed vlan 2081,2024
end
Configure Web Authentication
Step1: Navigate to Security > Web Auth > Web Login Page. Set the Web Authentication type to External (Redirect to external server) and configure the external Web Auth URL. The Redirect URL after login is optional and can be configured if clients need to be redirected to a dedicated page after successful authentication.
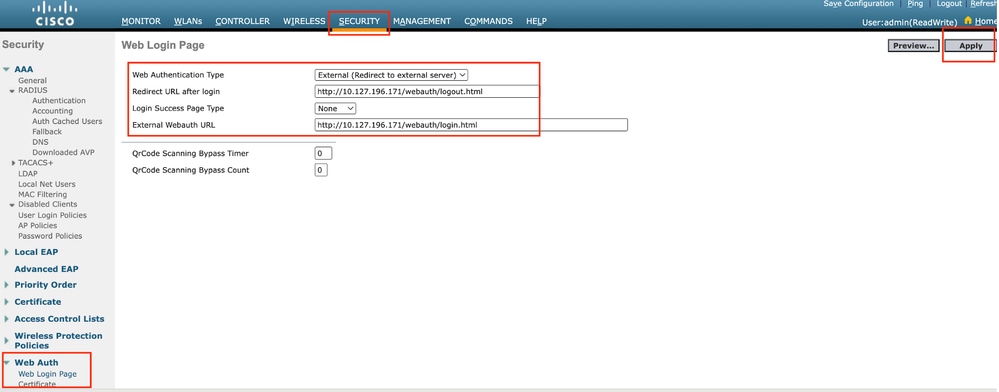 Web Auth settings
Web Auth settings
AAA Settings:
Step1: Configure radius server
Navigate to Security > Radius > Authentication > New.
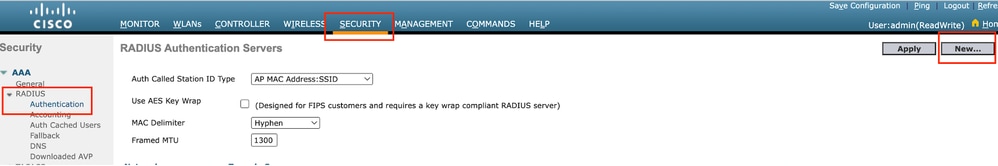 Radius Server
Radius Server
Step2: Configure the RADIUS server IP and shared secret on the controller. Toggle the server status to Enabled and check the Network User checkbox.
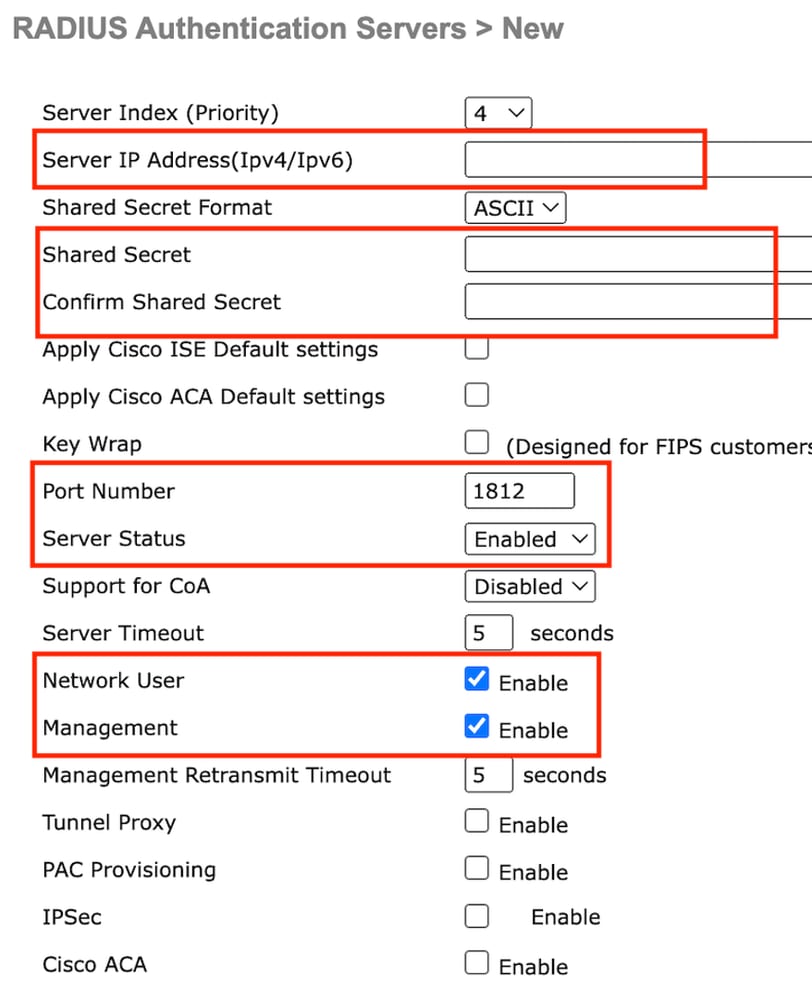 Server configuration
Server configuration
Configure Access Control List
Step1: Navigate to Security > Access Control List and select New. Create a Pre-Authentication ACL that permits traffic to DNS and the external web server.
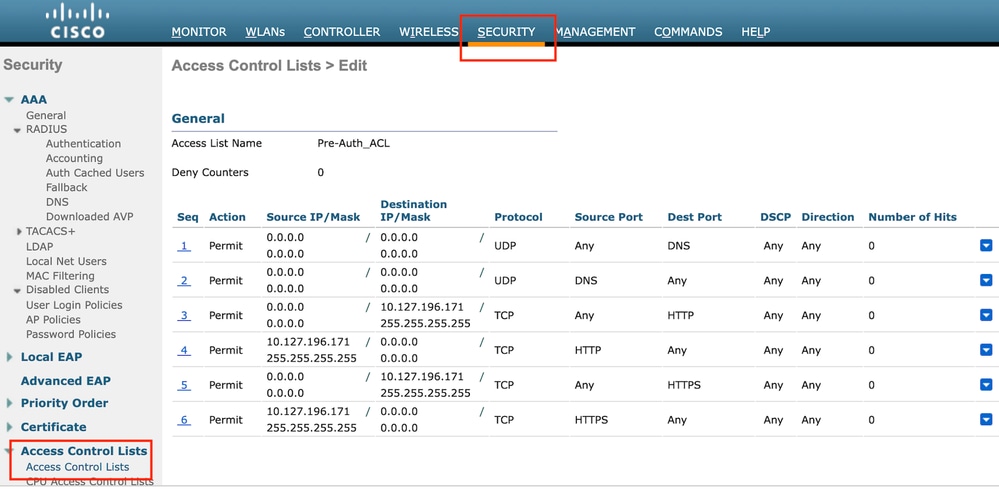 Access list to permit traffic to web server
Access list to permit traffic to web server
Configure Guest LAN profile
Step1: Navigate to WLAN > Create New > Go.
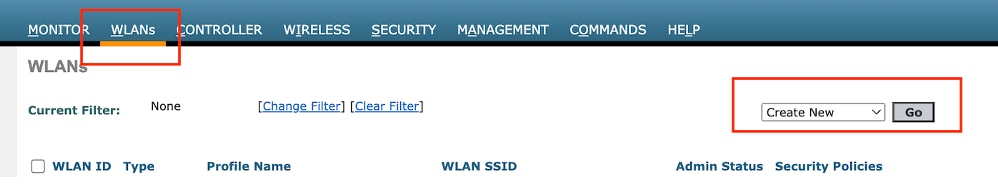 Guest LAN Profile
Guest LAN Profile
Select Type as Guest LAN and configure a profile name. The same name must be configured on the policy profile and Guest LAN profile of the 9800 Anchor controller.
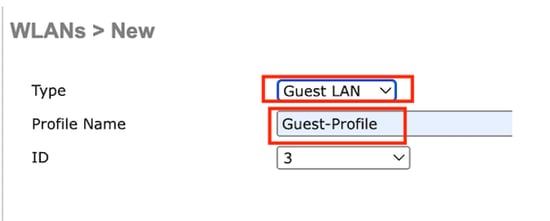 Guest LAN Profile
Guest LAN Profile
Step2: Under the General tab, Map the Ingress and Egress interface on the Guest LAN profile.
Ingress interface is the vlan to which the wired clients physically connect.
Egress interface is the vlan subnet that the clients request for IP address.
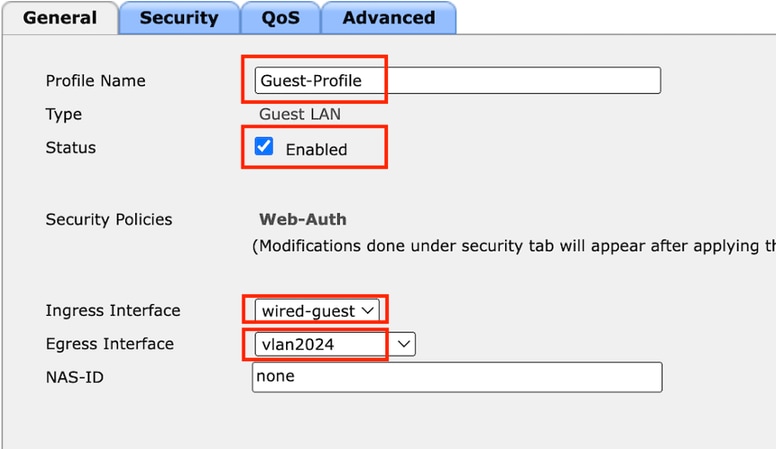 Guest LAN Profile
Guest LAN Profile
Step3: Navigate to Security > Layer 3.
Select Layer 3 Security as Web Authentication and map the Pre-Authentication ACL.
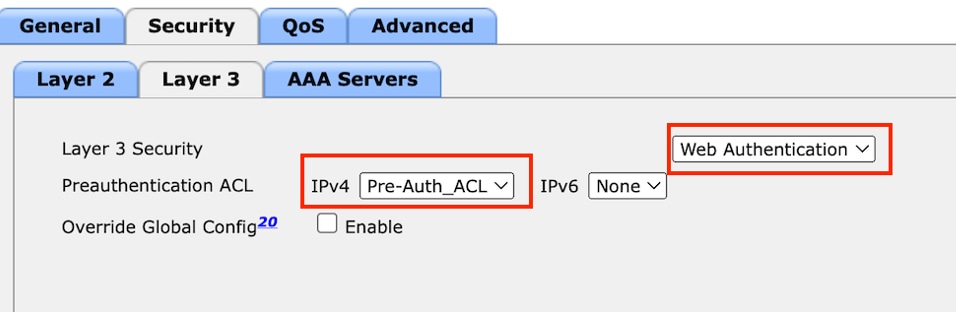 Layer 3 security tab
Layer 3 security tab
Step4:
Under AAA servers tab, map the Radius server and checkbox Enabled.
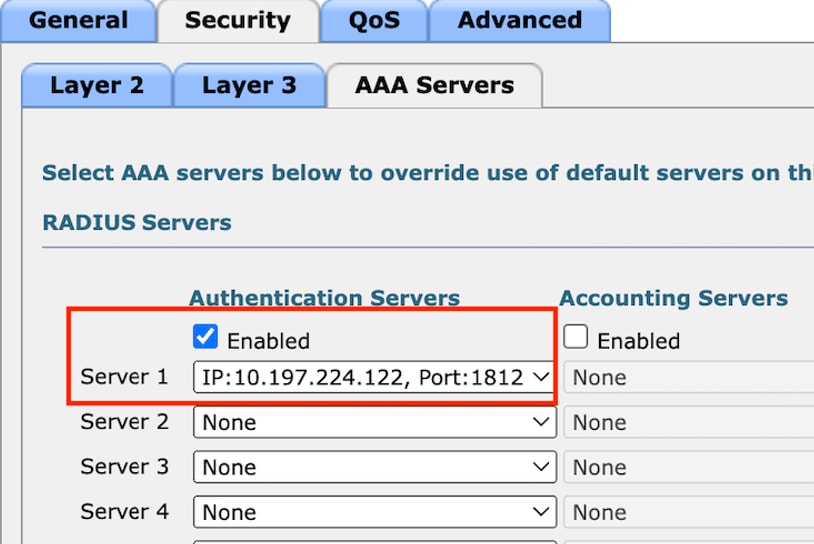 Mapping radius servers to Guest LAN profile
Mapping radius servers to Guest LAN profile
Step5: Navigate to WLAN page and hover over the downdown icon of Guest LAN profile and select Mobility Anchors.
 Mobility Anchors
Mobility Anchors
Step6: Map the mobility Anchor from the drop down list to the Guest LAN Profile.
 Mapping mobility anchor to Guest LAN
Mapping mobility anchor to Guest LAN
Configuration on Anchor 9800 WLC
Configure Web Parameter map
Step1: Navigate to Configuration > Security > Web Auth and select Global. Verify that the virtual IP address of the controller and the Trustpoint are correctly mapped on the profile, with the type set to webauth.
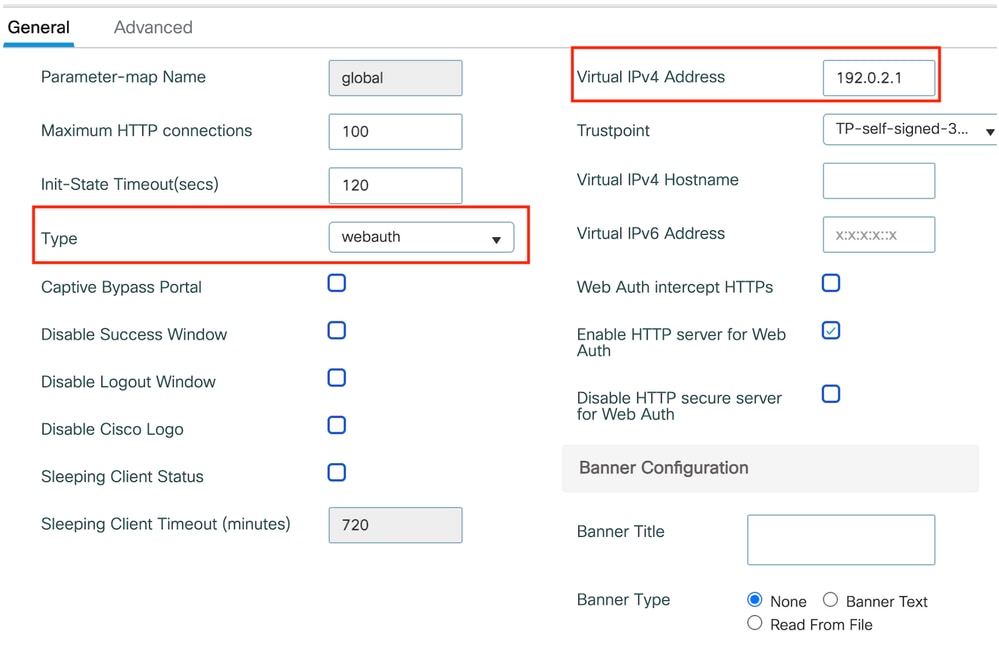 Web Parameter map
Web Parameter map
Step2: Under the Advanced tab, specify the external web page URL to which clients must be redirected. Configure the Redirect URL for Login and Redirect On-Failure. The Redirect On-Success setting is an optional configuration.
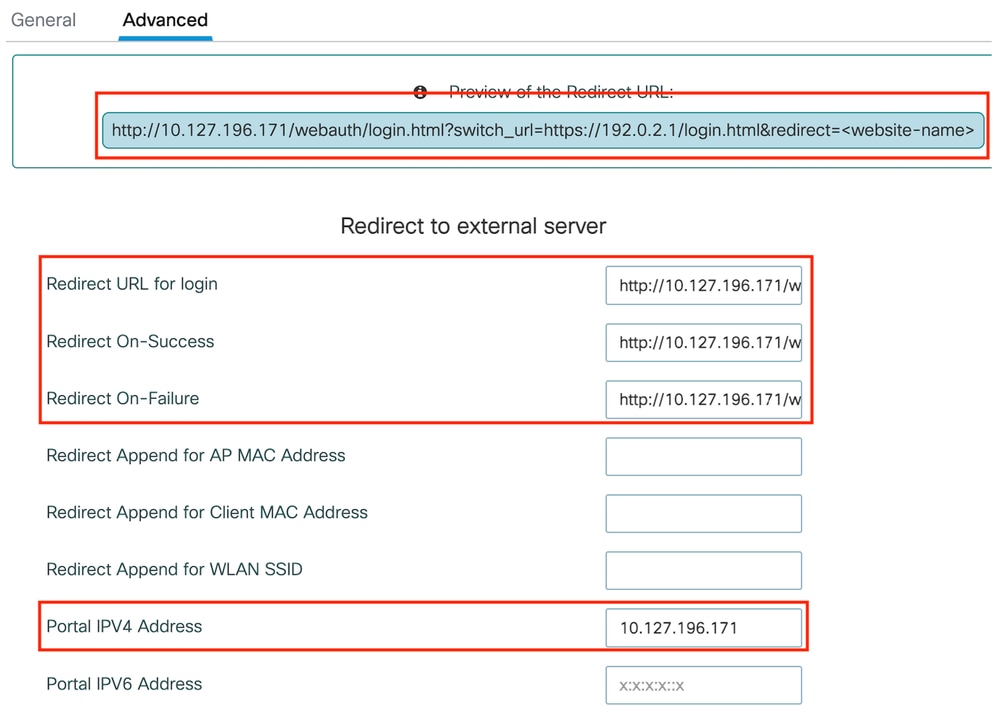 Advanced tab
Advanced tab
CLI configuration
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
redirect for-login http://10.127.196.171/webauth/login.html
redirect on-success http://10.127.196.171/webauth/logout.html
redirect on-failure http://10.127.196.171/webauth/failed.html
redirect portal ipv4 10.127.196.171
trustpoint TP-self-signed-3010594951
webauth-http-enable
Note: For AAA configuration, please refer to the configuration details provided in "Configure Wired Guest on catalyst 9800 anchored to another catalyst 9800" section for the Foreign 9800 WLC.
Configure Policy profile
Step1:Navigate to Configuration > Tags & Profiles > Policy. Configure the policy profile with the same name used for the Guest LAN profile of the Foreign controller.
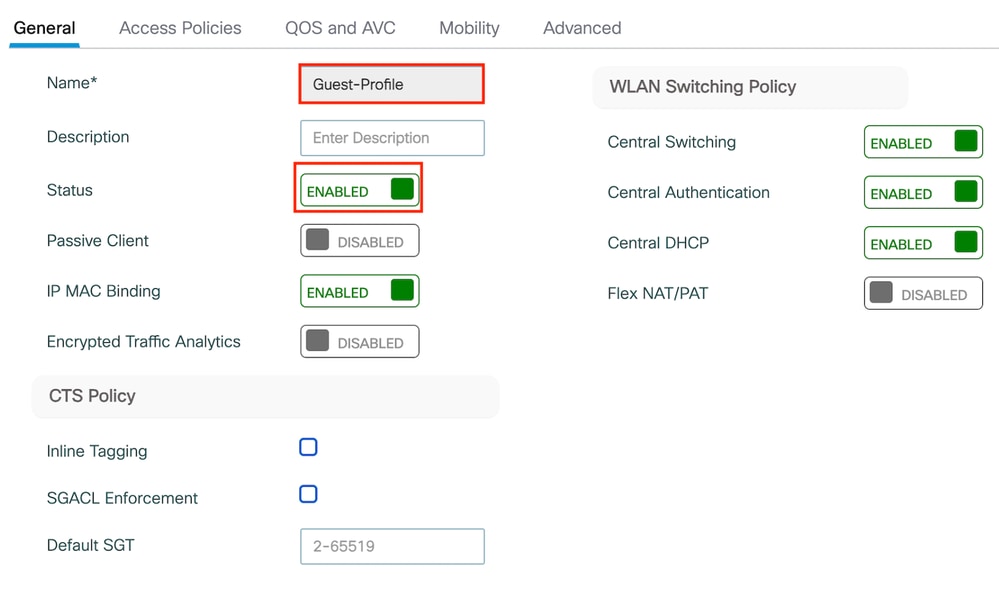 Policy Profile
Policy Profile
Step2: Under the Access Policies tab, map the wired client vlan from the drop down list
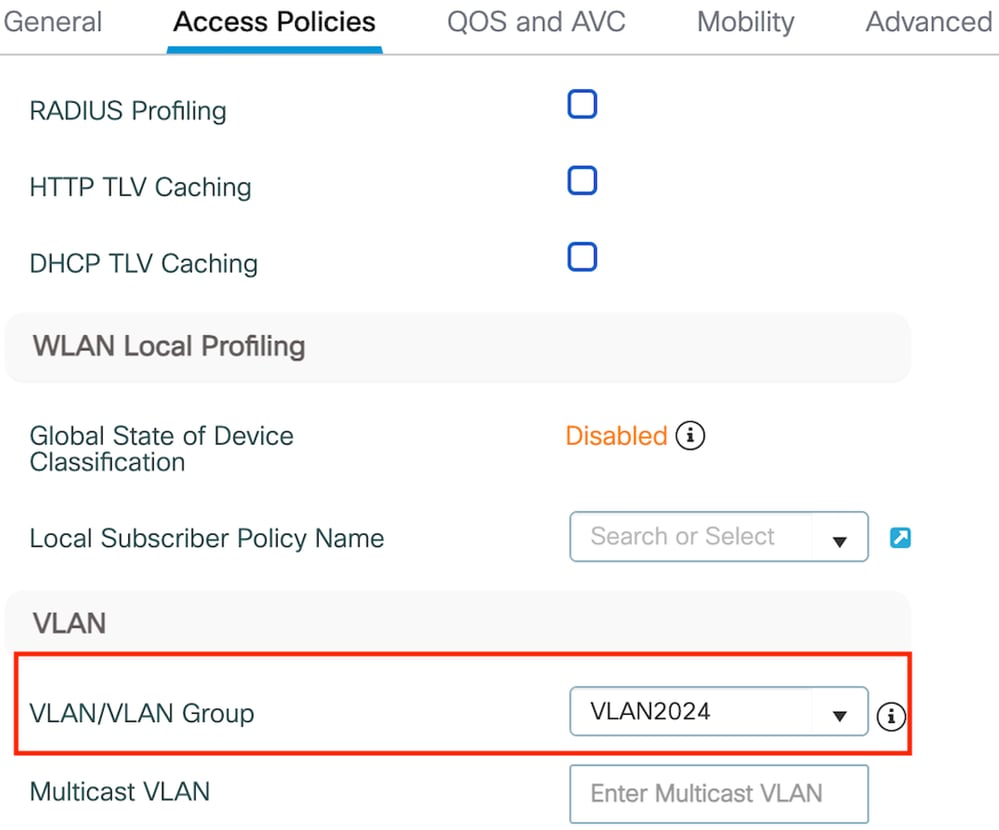 Access Policies
Access Policies
Step3: Under the Mobility tab, check box Export Anchor.
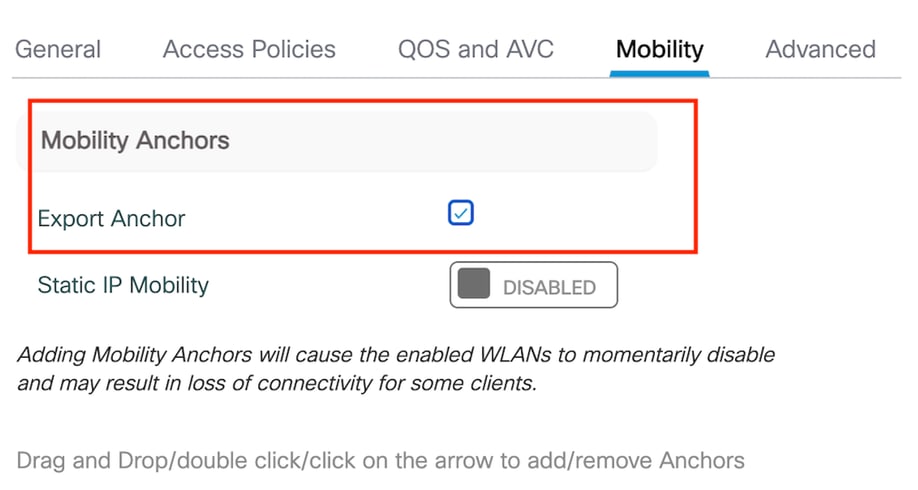 Mobility Tab
Mobility Tab
CLI Configuration
wireless profile policy Guest-Profile
no accounting-interim
exclusionlist timeout 180
no flex umbrella dhcp-dns-option
mobility anchor
vlan VLAN2024
no shutdown
Configure Guest LAN profile
Step1: Navigate to Configuration > Wireless > Guest LAN and select Add to configure the Guest LAN profile and disable Wired VLAN status.
Guest LAN profile name on Anchor must be same as the Guest LAN profile on Foreign WLC.
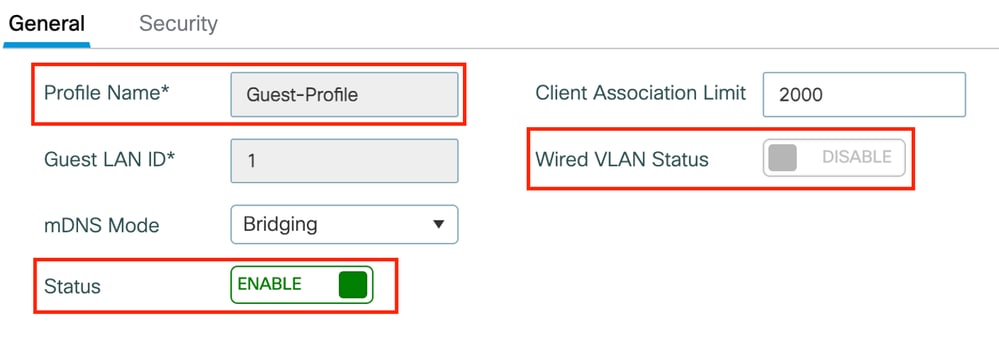 Guest LAN Profile
Guest LAN Profile
Step2: Under the Security tab, enable Web Auth. Select the Web Auth parameter map and Authentication List from the drop down list
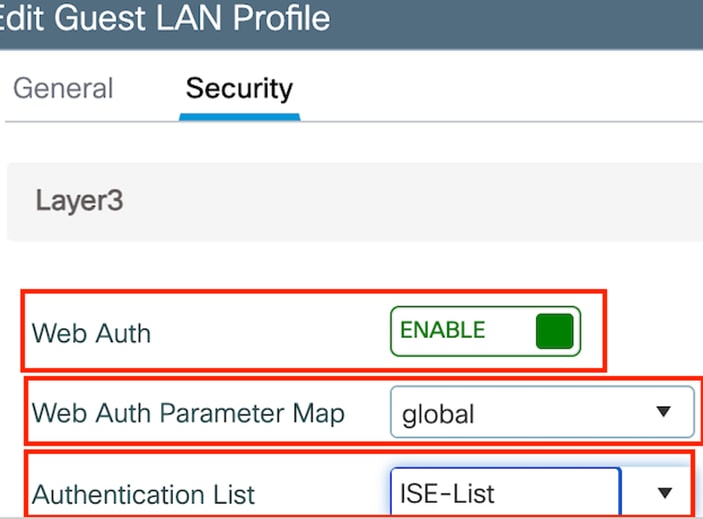 Guest LAN Security tab
Guest LAN Security tab
CLI Configuration
guest-lan profile-name Guest-Profile 1
security web-auth authentication-list ISE-List
security web-auth parameter-map global
Guest LAN MAP
Step1: Navigate to Configuration > Wireless > Guest LAN. In the Guest LAN MAP configuration section, select Add and map the Policy Profile to the Guest LAN profile.
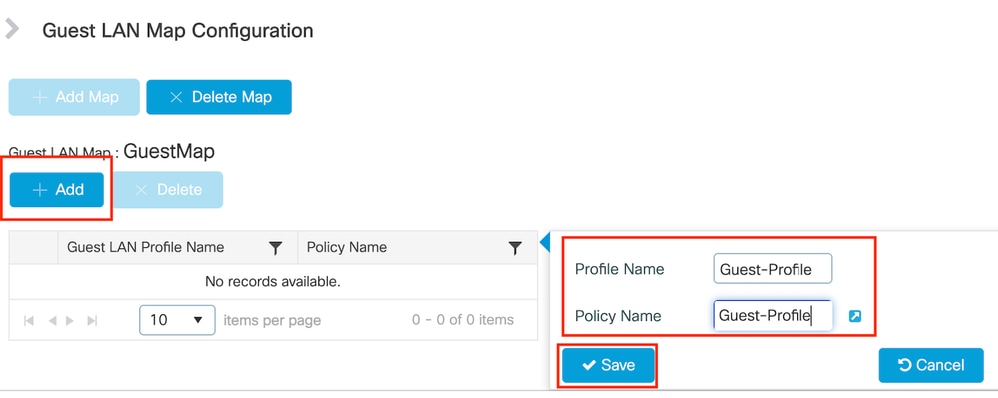 Guest LAN MAP
Guest LAN MAP
Verify
Validate controller Configuration
#show guest-lan summary
GLAN GLAN Profile Name Status
------------------------------------------------
1 Guest-Profile UP
2 Guest UP
#show guest-lan id 1
Guest-LAN Profile Name : Guest
================================================
Guest-LAN ID : 2
Wired-Vlan : 11
Status : Enabled
Number of Active Clients : 0
Max Associated Clients : 2000
Security
WebAuth : Enabled
Webauth Parameter Map : global
Webauth Authentication List : ISE-List
Webauth Authorization List : Not configured
mDNS Gateway Status : Bridge
#show parameter-map type webauth global
Parameter Map Name : global
Type : webauth
Redirect:
For Login : http://10.127.196.171/webauth/login.html
On Success : http://10.127.196.171/webauth/logout.html
On Failure : http://10.127.196.171/webauth/failed.html
Portal ipv4 : 10.127.196.171
Virtual-ipv4 : 192.0.2.1
#show parameter-map type webauth name <profile name> (If custom web parameter profile is used)
#show wireless guest-lan-map summary
GLAN Profile Name Policy Name
------------------------------------------------------------------------------
Guest Guest
#show wireless mobility summary
IP Public Ip MAC Address Group Name Multicast IPv4 Multicast IPv6 Status PMTU
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
10.76.118.70 10.76.118.70 f4bd.9e59.314b cisco1 0.0.0.0 :: Up 1385
#show ip http server status
HTTP server status: Enabled
HTTP server port: 80
HTTP server active supplementary listener ports: 21111
HTTP server authentication method: local
HTTP secure server capability: Present
HTTP secure server status: Enabled
HTTP secure server port: 443
HTTP secure server trustpoint: TP-self-signed-3010594951
>show guest-lan summary
Number of Guest LANs............................. 1
GLAN ID GLAN Profile Name Status Interface Name
------- ------------------------------------- -------- --------------------
2 Guest Enabled wired-vlan-11
>show guest-lan 2
Guest LAN Identifier............................. 2
Profile Name..................................... Guest
Status........................................... Enabled
Interface........................................ wired-vlan-11
Radius Servers
Authentication................................ 10.197.224.122 1812 *
Web Based Authentication...................... Enabled
Web Authentication Timeout.................... 300
IPv4 ACL........................................ Pre-Auth_ACL
Mobility Anchor List
GLAN ID IP Address Status
------- --------------- ------
2 10.76.118.74 Up
>show custom-web all
Radius Authentication Method..................... PAP
Cisco Logo....................................... Enabled
CustomLogo....................................... None
Custom Title..................................... None
Custom Message................................... None
Custom Redirect URL.............................. http://10.127.196.171/webauth/logout.html
Web Authentication Login Success Page Mode....... None
Web Authentication Type.......................... External
Logout-popup..................................... Enabled
External Web Authentication URL.................. http://10.127.196.171/webauth/login.html
QR Code Scanning Bypass Timer.................... 0
QR Code Scanning Bypass Count.................... 0
>show custom-web guest-lan 2
Guest LAN Status.............................. Enabled
Web Security Policy........................... Web Based Authentication
WebAuth Type.................................. External
Global Status................................. EnabledValidate client Policy state
On Foreign,
#show wireless client summary
Client policy manager state on the Foreign controller is RUN after the client associates successfully.
MAC Address AP Name Type ID State Protocol Method Role
-------------------------------------------------------------------------------------------------------------------------
a0ce.c8c3.a9b5 N/A GLAN 1 Run 802.3 Web Auth Export Foreign
>show client detail a0ce.c8c3.a9b5
Client MAC Address............................... a0:ce:c8:c3:a9:b5
Client Username ................................. N/A
Client Webauth Username ......................... N/A
Client State..................................... Associated
User Authenticated by ........................... None
Client User Group................................
Client NAC OOB State............................. Access
guest-lan........................................ 1
Wireless LAN Profile Name........................ Guest-Profile
Mobility State................................... Export Foreign
Mobility Anchor IP Address....................... 10.76.118.70
Security Policy Completed........................ Yes
Policy Manager State............................. RUN
Pre-auth IPv4 ACL Name........................... Pre-Auth_ACL
EAP Type......................................... Unknown
Interface........................................ wired-guest-egress
VLAN............................................. 2024
Quarantine VLAN.................................. 0
On Anchor,
Client state transistion must be monitored on the Anchor controller.
Client policy manager state is in Web Auth pending .
MAC Address AP Name Type ID State Protocol Method Role
-------------------------------------------------------------------------------------------------------------------------
a0ce.c8c3.a9b5 10.76.6.156 GLAN 1 Webauth Pending 802.3 Web Auth Export Anchor
Once the client authenticates, the policy manager state transitions to RUN state.
MAC Address AP Name Type ID State Protocol Method Role
-------------------------------------------------------------------------------------------------------------------------
a0ce.c8c3.a9b5 10.76.6.156 GLAN 1 Run 802.3 Web Auth Export Anchor
#show wireless client mac-address a0ce.c8c3.a9b5 detail
Client MAC Address : a0ce.c8c3.a9b5
Client MAC Type : Universally Administered Address
Client DUID: NA
Client IPv4 Address : 10.105.211.69
Client State : Associated
Policy Profile : Guest-Profile
Flex Profile : N/A
Guest Lan:
GLAN Id: 1
GLAN Name: Guest-Profile
Mobility:
Foreign IP Address : 10.76.118.74
Point of Attachment : 0xA0000003
Point of Presence : 0
Move Count : 1
Mobility Role : Export Anchor
Mobility Roam Type : L3 Requested
Policy Manager State: Webauth Pending
Last Policy Manager State : IP Learn Complete
Client Entry Create Time : 35 seconds
VLAN : VLAN2024
Session Manager:
Point of Attachment : mobility_a0000003
IIF ID : 0xA0000003
Authorized : FALSE
Session timeout : 28800
Common Session ID: 4a764c0a0000008ea0285466
Acct Session ID : 0x00000000
Auth Method Status List
Method : Web Auth
Webauth State : Login
Webauth Method : Webauth
Server Policies:
Resultant Policies:
URL Redirect ACL : WA-v4-int-10.127.196.171
Preauth ACL : WA-sec-10.127.196.171
VLAN Name : VLAN2024
VLAN : 2024
Absolute-Timer : 28800
Client moves to RUN state after successful web authentication.
show wireless client mac-address a0ce.c8c3.a9b5 detail
Client MAC Address : a0ce.c8c3.a9b5
Client MAC Type : Universally Administered Address
Client DUID: NA
Client IPv4 Address : 10.105.211.69
Client Username : testuser
Client State : Associated
Policy Profile : Guest-Profile
Flex Profile : N/A
Guest Lan:
GLAN Id: 1
GLAN Name: Guest-Profile
Wireless LAN Network Name (SSID) : N/A
BSSID : N/A
Connected For : 81 seconds
Protocol : 802.3
Policy Manager State: Run
Last Policy Manager State : Webauth Pending
Client Entry Create Time : 81 seconds
VLAN : VLAN2024
Last Tried Aaa Server Details:
Server IP : 10.197.224.122
Auth Method Status List
Method : Web Auth
Webauth State : Authz
Webauth Method : Webauth
Resultant Policies:
URL Redirect ACL : IP-Adm-V4-LOGOUT-ACL
VLAN Name : VLAN2024
VLAN : 2024
Absolute-Timer : 28800
>show client detail a0:ce:c8:c3:a9:b5
Client MAC Address............................... a0:ce:c8:c3:a9:b5
Client Username ................................. N/A
Client Webauth Username ......................... N/A
Client State..................................... Associated
Wireless LAN Profile Name........................ Guest
WLAN Profile check for roaming................... Disabled
Hotspot (802.11u)................................ Not Supported
Connected For ................................... 90 secs
IP Address....................................... 10.105.211.75
Gateway Address.................................. 10.105.211.1
Netmask.......................................... 255.255.255.128
Mobility State................................... Export Anchor
Mobility Foreign IP Address...................... 10.76.118.70
Security Policy Completed........................ No
Policy Manager State............................. WEBAUTH_REQD
Pre-auth IPv4 ACL Name........................... Pre-Auth_ACLPre-auth
IPv4 ACL Applied Status................. Yes
Pre-auth IPv4 ACL Applied Status................. Yes
After Authentication client transistions to RUN state.
show client detail a0:ce:c8:c3:a9:b5
Client MAC Address............................... a0:ce:c8:c3:a9:b5
Client Username ................................. testuser
Client Webauth Username ......................... testuser
Client State..................................... Associated
User Authenticated by ........................... RADIUS Server
Client User Group................................ testuser
Client NAC OOB State............................. Access
Connected For ................................... 37 secs
IP Address....................................... 10.105.211.75
Gateway Address.................................. 10.105.211.1
Netmask.......................................... 255.255.255.128
Mobility State................................... Export Anchor
Mobility Foreign IP Address...................... 10.76.118.70
Security Policy Completed........................ Yes
Policy Manager State............................. RUN
Pre-auth IPv4 ACL Name........................... Pre-Auth_ACL
Pre-auth IPv4 ACL Applied Status................. Yes
EAP Type......................................... Unknown
Interface........................................ wired-vlan-11
VLAN............................................. 11
Quarantine VLAN.................................. 0
Troubleshoot
AireOS Controller debug
Enable client debug
>debug client <H.H.H>
To verify if debugging is enabled
>show debugging
To disable debug
debug disable-all
9800 Radioactive trace
Activate Radio Active Tracing to generate client debug traces for the specified MAC address in the CLI.
Steps to enable Radioactive Tracing:
Ensure all the conditional debugs are disabled.
clear platform condition allEnable debug for specified mac address.
debug wireless mac <H.H.H> monitor-time <Time is seconds>After reproducing the issue, disable debugging to halt the RA trace collection.
no debug wireless mac <H.H.H>
Once the RA trace is stopped, the debug file is generated in the controller's bootflash.
show bootflash: | include ra_trace
2728 179 Jul 17 2024 15:13:54.0000000000 +00:00 ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log
Copy the file to an external server.
copy bootflash:ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log tftp://<IP address>/ra-FILENAME.txt
Display the debug log:
more bootflash:ra_trace_MAC_aaaabbbbcccc_HHMMSS.XXX_timezone_DayWeek_Month_Day_year.log
Enable RA trace in GUI,
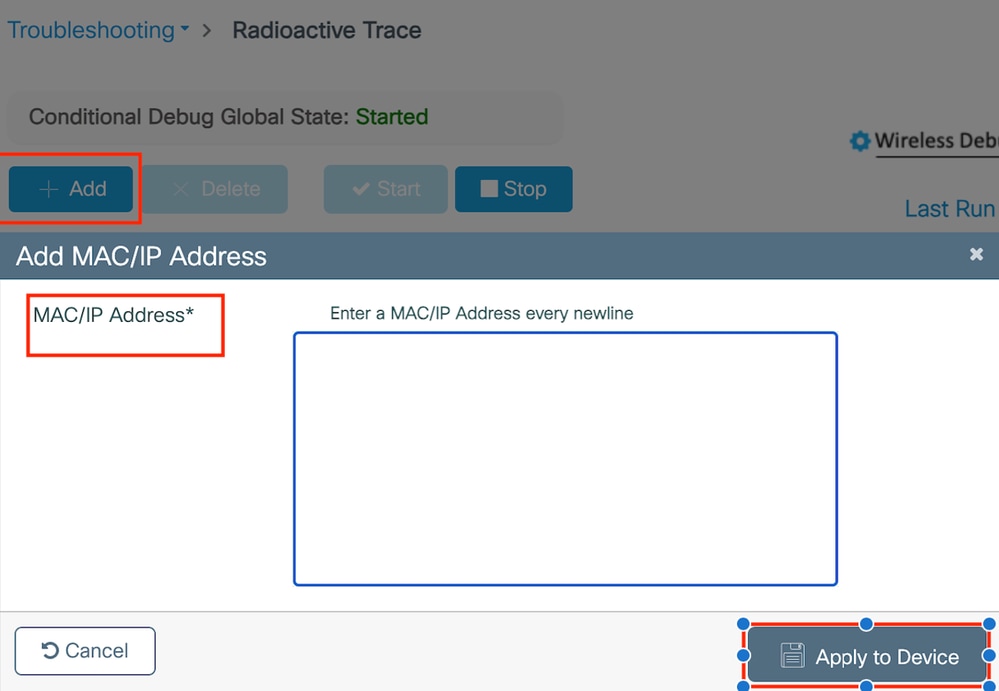 Enable RA trace on WebUI
Enable RA trace on WebUI
Embedded Packet Capture
Navigate to Troubleshooting > Packet Capture. Enter the capture name and specify the client's MAC address as the inner filter MAC. Set the buffer size to 100 and choose the uplink interface to monitor incoming and outgoing packets.
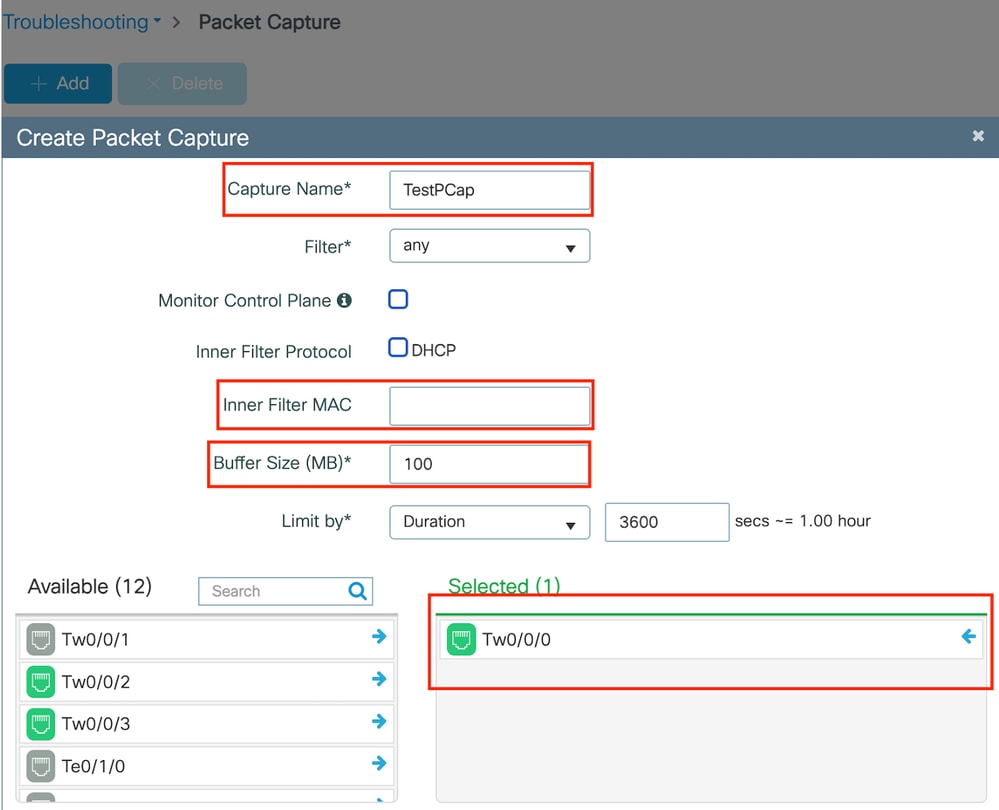 Embedded Packet Capture
Embedded Packet Capture

Note: Select the "Monitor Control Traffic" option to view traffic redirected to the system CPU and reinjected into the data plane.
Navigate to Troubleshooting > Packet Capture and select Start to capture packets.
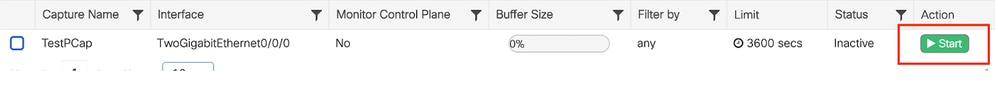 Start Packet Capture
Start Packet Capture
CLI configuration
monitor capture TestPCap inner mac <H.H.H>
monitor capture TestPCap buffer size 100
monitor capture TestPCap interface twoGigabitEthernet 0/0/0 both
monitor capture TestPCap start
<Reporduce the issue>
monitor capture TestPCap stopshow monitor capture TestPCap
Status Information for Capture TestPCap
Target Type:
Interface: TwoGigabitEthernet0/0/0, Direction: BOTH
Status : Inactive
Filter Details:
Capture all packets
Inner Filter Details:
Mac: 6c7e.67e3.6db9
Continuous capture: disabled
Buffer Details:
Buffer Type: LINEAR (default)
Buffer Size (in MB): 100
Limit Details:
Number of Packets to capture: 0 (no limit)
Packet Capture duration: 3600
Packet Size to capture: 0 (no limit)
Maximum number of packets to capture per second: 1000
Packet sampling rate: 0 (no sampling)
Export packet capture to external TFTP server.
monitor capture TestPCap export tftp://<IP address>/ TestPCap.pcap
Navigate to Troubleshooting > Packet Capture and select Export to download the capture file on the local machine.
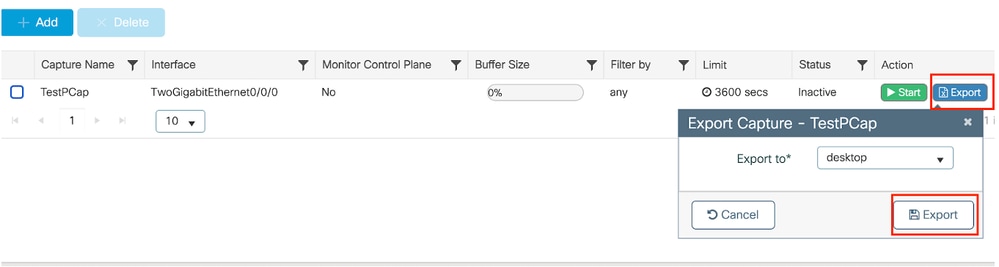 Download EPC
Download EPC
Working log snippets
AireOS Foreign Controller client debug log
Wired packet received from wired client
*apfReceiveTask: May 27 12:00:55.127: a0:ce:c8:c3:a9:b5 Wired Guest packet from 10.105.211.69 on mobile
Foreign controller building export anchor request
*apfReceiveTask: May 27 12:00:56.083: a0:ce:c8:c3:a9:b5 Attempting anchor export for mobile a0:ce:c8:c3:a9:b5
*apfReceiveTask: May 27 12:00:56.083: a0:ce:c8:c3:a9:b5 mmAnchorExportSend: Building ExportForeignLradMac Payload Lrad Mac: 00:00:00:00:00:00
*apfReceiveTask: May 27 12:00:56.083: a0:ce:c8:c3:a9:b5 SGT Payload built in Export Anchor Req 0
Foreign controller sends Export anchor request to the anchor controller.
*apfReceiveTask: May 27 12:00:56.083: a0:ce:c8:c3:a9:b5 Export Anchor request sent to 10.76.118.70
Anchor controller sends acknowledgement for the Anchor request for client
*Dot1x_NW_MsgTask_5: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 Recvd Exp Anchor Ack for mobile a0:ce:c8:c3:a9:b5 from 10.76.118.70
Mobility role for the clients on the Foreign controller is updated to export Foreign.
*apfReceiveTask: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 0.0.0.0 DHCP_REQD (7) mobility role update request from Unassociated to Export Foreign
Peer = 10.76.118.70, Old Anchor = 10.76.118.70, New Anchor = 10.76.118.70
Client transistioned into RUN state.
*apfReceiveTask: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=ExpForeign, client state=APF_MS_STATE_ASSOCIATED
*apfReceiveTask: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 Stopping deletion of Mobile Station: (callerId: 75)
*apfReceiveTask: May 27 12:00:56.091: a0:ce:c8:c3:a9:b5 Moving client to run state
9800 Foreign controller radioactive trace
Client associates to the controller.
2024/07/15 04:10:29.087608331 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
Mobility discovery is in progress after association.
2024/07/15 04:10:29.091585813 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_MOBILITY_DISCOVERY_IN_PROGRESS
2024/07/15 04:10:29.091605761 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_MOBILITY_DISCOVERY_IN_PROGRESS -> S_CO_MOBILITY_DISCOVERY_IN_PROGRESS
Once Mobility discovery is processed, client roam type is updates to L3 requested.
2024/07/15 04:10:29.091664605 {wncd_x_R0-0}{1}: [mm-transition] [17765]: (info): MAC: a0ce.c8c3.a9b5 MMIF FSM transition: S_MA_INIT -> S_MA_MOBILITY_DISCOVERY_PROCESSED_TR on E_MA_MOBILITY_DISCOVERY
2024/07/15 04:10:29.091693445 {wncd_x_R0-0}{1}: [mm-client] [17765]: (info): MAC: a0ce.c8c3.a9b5 Roam type changed - None -> L3 Requested
Foreign controller is sending the export anchor request to the Anchor WLC.
2024/07/15 04:10:32.093245394 {mobilityd_R0-0}{1}: [mm-client] [18316]: (debug): MAC: a0ce.c8c3.a9b5 Export Anchor Request successfully processed.
2024/07/15 04:10:32.093253788 {mobilityd_R0-0}{1}: [mm-client] [18316]: (debug): MAC: a0ce.c8c3.a9b5 Forwarding Export Anchor Request to Anchor.
2024/07/15 04:10:32.093274405 {mobilityd_R0-0}{1}: [mm-client] [18316]: (info): MAC: a0ce.c8c3.a9b5 Forwarding export_anchor_req, sub type: 0 of XID (6396) from (WNCD[0]) to (ipv4: 10.76.118.70 )
Export Anchor response is received from the Anchor controller and vlan is applied from the user profile.
2024/07/15 04:10:32.106775213 {mobilityd_R0-0}{1}: [mm-transition] [18316]: (info): MAC: a0ce.c8c3.a9b5 MMFSM transition: S_MC_WAIT_EXP_ANC_RSP -> S_MC_EXP_ANC_RSP_RCVD_TR on E_MC_EXP_ANC_RSP_RCVD from ipv4: 10.76.118.70
2024/07/15 04:10:32.106811183 {mobilityd_R0-0}{1}: [mm-client] [18316]: (debug): MAC: a0ce.c8c3.a9b5 Export Anchor Response successfully processed.
2024/07/15 04:10:32.107183692 {wncd_x_R0-0}{1}: [epm-misc] [17765]: (info): [a0ce.c8c3.a9b5:Tw0/0/0] Anchor Vlan-id 2024 processed
2024/07/15 04:10:32.107247304 {wncd_x_R0-0}{1}: [svm] [17765]: (info): [a0ce.c8c3.a9b5] Applied User Profile: :
2024/07/15 04:10:32.107250258 {wncd_x_R0-0}{1}: [aaa-attr-inf] [17765]: (info): Applied User Profile: anchor-vlan 0 2024 (0x7e8)
Once the Export Anchor request is processed, client mobility role is updated to Export Foreign.
2024/07/15 04:10:32.107490972 {wncd_x_R0-0}{1}: [mm-client] [17765]: (debug): MAC: a0ce.c8c3.a9b5 Processed Export Anchor Response.
2024/07/15 04:10:32.107502336 {wncd_x_R0-0}{1}: [mm-client] [17765]: (info): MAC: a0ce.c8c3.a9b5 Mobility role changed - Unassoc -> Export Foreign
2024/07/15 04:10:32.107533732 {wncd_x_R0-0}{1}: [sanet-shim-translate] [17765]: (info): Anchor Vlan: 2024
2024/07/15 04:10:32.107592251 {wncd_x_R0-0}{1}: [mm-client] [17765]: (note): MAC: a0ce.c8c3.a9b5 Mobility Successful Guest Lan Client. Roam Type L3 Requested, Client IFID: 0xa0000007, Client Role: Export Foreign PoA: phy IfId PoP: 0xa0000005
Client transitions into IP learn state.
2024/07/15 04:10:32.108210365 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_DPATH_PLUMB_IN_PROGRESS -> S_CO_IP_LEARN_IN_PROGRESS
2024/07/15 04:10:32.108293096 {wncd_x_R0-0}{1}: [client-orch-sm] [17765]: (debug): MAC: a0ce.c8c3.a9b5 Received ip learn response. method: IPLEARN_METHOD_ROAMING
After IP learn, client moves to RUN state on the Foreign WLC.
2024/07/15 04:10:32.108521618 {wncd_x_R0-0}{1}: [client-orch-state] [17765]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_IP_LEARN_IN_PROGRESS -> S_CO_RUN
AireOS Anchor controller client deubg log
Export Anchor request reveived from the Foreign controller.
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 Anchor Export Request Recvd for mobile a0:ce:c8:c3:a9:b5 from 10.76.118.70 type : 16 subtype : 0 seq no : 0 xid : 1292566528
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 mmAnchorExportRcv: Extracting mmPayloadExportForeignLradMac
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 mmAnchorExportRcv Ssid=Guest useProfileName=0 profileNameToUse=0Security Policy=0x2010
Local bridging vlan is applied for the client.
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 Updated local bridging VLAN to 11 while applying WLAN policy
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 Applying Interface(wired-vlan-11) policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 0
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 After applying Interface(wired-vlan-11) policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 11
Mobility role is updated to Export Anchor and client state transistoned Associated.
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5 0.0.0.0 START (0) mobility role update request from Unassociated to Export Anchor
Peer = 10.76.118.70, Old Anchor = 0.0.0.0, New Anchor = 10.76.118.74
Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5
add client MAC a0:ce:c8:c3:a9:b5 IP 10.76.118.70
*Dot1x_NW_MsgTask_5: May 28 10:46:27.831: a0:ce:c8:c3:a9:b5
Sent message to add a0:ce:c8:c3:a9:b5 on member IP 10.76.118.70
*Dot1x_NW_MsgTask_5: May 28 10:46:27.832: a0:ce:c8:c3:a9:b5 mmAnchorExportRcv (mm_listen.c:7933) Changing state for mobile a0:ce:c8:c3:a9:b5 on AP 00:00:00:00:00:00 from Idle to Associated
Mobility is completed, client state is associated and mobility role is Export Anchor.
*Dot1x_NW_MsgTask_5: May 28 10:46:27.832: a0:ce:c8:c3:a9:b5 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=ExpAnchor, client state=APF_MS_STATE_ASSOCIATED
Client IP address is learnt on the controller and state transistoned from DHCP required to Web auth required.
*dtlArpTask: May 28 10:46:58.356: a0:ce:c8:c3:a9:b5 Static IP client associated to interface wired-vlan-11 which can support client subnet.
*dtlArpTask: May 28 10:46:58.356: a0:ce:c8:c3:a9:b5 dtlArpSetType: Changing ARP Type from 0 ---> 1 for station a0:ce:c8:c3:a9:b5
*dtlArpTask: May 28 10:46:58.356: a0:ce:c8:c3:a9:b5 10.105.211.75 DHCP_REQD (7) Change state to WEBAUTH_REQD (8) last state DHCP_REQD (7)
Webauth URL is being formulated by adding the external redirect url and controller Virtaul ip address.
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Preparing redirect URL according to configured Web-Auth type
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Web-auth type External, using URL:http://10.127.196.171/webauth/login.html
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Added switch_url, redirect URL is now http://10.127.196.171/webauth/login.html?switch_url=https://192.0.2.1/login.html
Added Client mac address and WLAN to the URL.
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Added client_mac , redirect URL is now http://10.127.196.171/webauth/login.html?switch_url= https://192.0.2.1/login.html&client_mac=a0:ce:c8:c3:a9:b5
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Added wlan, redirect URL is now
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- Added wlan, redirect URL is now http://10.127.196.171/webauth/login.html?switch_url= https://192.0.2.1/login.html&client_mac=a0:ce:c8:c3:a9:b5&wlan=Guest
Final URL after parcing the HTTP GET for host 10.105.211.1
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- parser host is 10.105.211.1
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- parser path is /auth/discovery
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5-added redirect=, URL is now http://10.127.196.171/webauth/login.html?switch_url=https://192.0.2.1/login.html&client_mac=a0:ce:c8:c3:a9:b5&wlan=Guest&redirect=10.105.211.1/auth/discovery?architecture=9
Redirect URL is sent to the client in the 200 OK response packet.
*webauthRedirect: May 28 10:46:58.500: a0:ce:c8:c3:a9:b5- 200 send_data =HTTP/1.1 200 OK
Location:http://10.127.196.171/webauth/login.html?switch_url=https://192.0.2.1/login.html&client_mac=a0:ce:c8:c3:a9:b5&wlan=Guest&redirect=10.105.211.1/auth/discovery?architecture=9 Client establishes a TCP connection with redirect url host. Once the clients submit the login username and password on the portal a radius request is sent by the controller to radius server
Once the controller receives an Access-Accept, the client closed the TCP session and is moved to RUN state.
*aaaQueueReader: May 28 10:46:59:077: a0:ce:c8:c3:a9:b5 Sending the packet to v4 host 10.197.224.122:1812
*aaaQueueReader: May 28 10:46:59:077: a0:ce:c8:c3:a9:b5 Successful transmission of Authentication Packet (pktId 127) to 10.197.224.122:1812
*aaaQueueReader: May 28 10:46:59:077: AVP[01] User-Name................................testuser (17 bytes)
*aaaQueueReader: May 28 10:46:59:077: AVP[03] Calling-Station-Id.......................a0-ce-c8-c3-a9-b5 (17 bytes)
*aaaQueueReader: May 28 10:46:59:077: AVP[04] Nas-Port.................................0x00000008 (8) (4 bytes)
*aaaQueueReader: May 28 10:46:59:077: AVP[05] Nas-Ip-Address...........................0x0a4c7646 (184548604) (4 bytes)
*aaaQueueReader: May 28 10:46:59:077: AVP[06] NAS-Identifier...........................POD1586-CT5520 (14 bytes)
*aaaQueueReader: May 28 10:46:59:500: a0:ce:c8:c3:a9:b5 radiusServerFallbackPassiveStateUpdate: RADIUS server is ready 10.197.224.122 port 1812 index 0 active 1
*radiusTransportThread: May 28 10:46:59:500: a0:ce:c8:c3:a9:b5 Access-Accept received from RADIUS server 10.197.224.122 (qid:5) with port:1812, pktId:127
*Dot1x_NW_MsgTask_5: May 28 10:46:59:500: a0:ce:c8:c3:a9:b5 Processing Access-Accept for mobile a0:ce:c8:c3:a9:b5
*apfReceiveTask: May 28 10:46:59:500: a0:ce:c8:c3:a9:b5 Moving client to run state
9800 Anchor controller radioactive trace
Mobility announce message for the client from the Foreign controller.
2024/07/15 15:10:20.614677358 {mobilityd_R0-0}{1}: [mm-client] [15259]: (debug): MAC: a0ce.c8c3.a9b5 Received mobile_announce, sub type: 0 of XID (6394) from (ipv4: 10.76.6.156 )
Export anchor request received from the foreign controller when the client is associating for which Export anchor response is sent by the Anchor controller which can be verified on the Foreign controller RA trace.
2024/07/15 15:10:22.615246594 {mobilityd_R0-0}{1}: [mm-transition] [15259]: (info): MAC: a0ce.c8c3.a9b5 MMFSM transition: S_MC_INIT -> S_MC_ANCHOR_EXP_ANC_REQ_RCVD_TR on E_MC_EXP_ANC_REQ_RCVD from ipv4: 10.76.6.156
Client is moved to associating state and mobility role is transistioned to Export Anchor.
2024/07/15 15:10:22.616156811 {wncd_x_R0-0}{1}: [client-orch-state] [14709]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2024/07/15 15:10:22.627358367 {wncd_x_R0-0}{1}: [mm-client] [14709]: (note): MAC: a0ce.c8c3.a9b5 Mobility Successful. Roam Type L3 Requested, Sub Roam Type MM_SUB_ROAM_TYPE_NONE, Client IFID: 0xa0000005, Client Role: Export Anchor PoA: 0xa0000001 PoP: 0x0
2024/07/15 15:10:22.627462963 {wncd_x_R0-0}{1}: [dot11] [14709]: (note): MAC: a0ce.c8c3.a9b5 Client datapath entry params - ssid:Guest-Profile,slot_id:0 bssid ifid: 0x0, radio_ifid: 0x0, wlan_ifid: 0xf0408001
2024/07/15 15:10:22.627490485 {mobilityd_R0-0}{1}: [mm-client] [15259]: (debug): MAC: a0ce.c8c3.a9b5 Export Anchor Response successfully processed.
2024/07/15 15:10:22.627494963 {mobilityd_R0-0}{1}: [mm-client] [15259]: (debug): MAC: a0ce.c8c3.a9b5 Forwarding Anchor Response to Foreign.
IP learn is completed, client IP learnt through ARP .
2024/07/15 15:10:22.628124206 {wncd_x_R0-0}{1}: [client-iplearn] [14709]: (info): MAC: a0ce.c8c3.a9b5 IP-learn state transition: S_IPLEARN_INIT -> S_IPLEARN_IN_PROGRESS
2024/07/15 15:10:23.627064171 {wncd_x_R0-0}{1}: [sisf-packet] [14709]: (info): RX: ARP from interface mobility_a0000001 on vlan 2024 Source MAC: a0ce.c8c3.a9b5 Dest MAC: ffff.ffff.ffff ARP REQUEST, ARP sender MAC: a0ce.c8c3.a9b5 ARP target MAC: 0000.0000.0000 ARP sender IP: 10.105.211.69, ARP target IP: 10.105.211.1,
2024/07/15 15:10:24.469704913 {wncd_x_R0-0}{1}: [client-iplearn] [14709]: (note): MAC: a0ce.c8c3.a9b5 Client IP learn successful. Method: ARP IP: 10.105.211.69
2024/07/15 15:10:24.470527056 {wncd_x_R0-0}{1}: [client-iplearn] [14709]: (info): MAC: a0ce.c8c3.a9b5 IP-learn state transition: S_IPLEARN_IN_PROGRESS -> S_IPLEARN_COMPLETE
2024/07/15 15:10:24.470587596 {wncd_x_R0-0}{1}: [client-orch-sm] [14709]: (debug): MAC: a0ce.c8c3.a9b5 Received ip learn response. method: IPLEARN_METHOD_ARP
2024/07/15 15:10:24.470613094 {wncd_x_R0-0}{1}: [client-orch-sm] [14709]: (debug): MAC: a0ce.c8c3.a9b5 Triggered L3 authentication. status = 0x0, Success
Client policy state is in web auth pending.
2024/07/15 15:10:24.470748350 {wncd_x_R0-0}{1}: [client-auth] [14709]: (info): MAC: a0ce.c8c3.a9b5 Client auth-interface state transition: S_AUTHIF_L2_WEBAUTH_DONE -> S_AUTHIF_WEBAUTH_PENDING
TCP handshake is spoofed by the controller. When the client sends a HTTP GET, a 200 OK response frame is sent which contains the redirect URL.
The client must establish a TCP handshake with the redirect URL and load the page.
2024/07/15 15:11:37.579177010 {wncd_x_R0-0}{1}: [webauth-httpd] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]HTTP GET request
2024/07/15 15:11:37.579190912 {wncd_x_R0-0}{1}: [webauth-httpd] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]Parse GET, src [10.105.211.69] dst [10.3.3.3] url [http://10.3.3.3/favicon.ico]
2024/07/15 15:11:37.579226658 {wncd_x_R0-0}{1}: [webauth-state] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]Param-map used: global
2024/07/15 15:11:37.579230650 {wncd_x_R0-0}{1}: [webauth-state] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]State LOGIN -> LOGIN
2024/07/15 15:11:47.123072893 {wncd_x_R0-0}{1}: [webauth-httpd] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]GET rcvd when in LOGIN state
2024/07/15 15:11:47.123082753 {wnc2024/07/15 15:12:04.280574375 {wncd_x_R0-0}{1}: [webauth-httpd] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]POST rcvd when in LOGIN state
When the client submits the login credentials on the web portal page, an Access-Request packet is sent to the radius server for authentication.
2024/07/15 15:12:04.281076844 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: Send Access-Request to 10.197.224.122:1812 id 0/0, len 363
2024/07/15 15:12:04.281087672 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: authenticator e3 01 8f 5d 8e 52 fc cb - e0 d7 03 da c1 a2 09 e6
2024/07/15 15:12:04.281093278 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: Calling-Station-Id [31] 19 "a0-ce-c8-c3-a9-b5"
2024/07/15 15:12:04.281097034 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: User-Name [1] 10 "testuser"
2024/07/15 15:12:04.281148298 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: Cisco AVpair [1] 16 "method=webauth"
Access-Accept is received from the radius server, webauth is successful.
2024/07/15 15:12:04.683597101 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: Received from id 1812/0 10.197.224.122:0, Access-Accept, len 105
2024/07/15 15:12:04.683607762 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: authenticator 52 3e b0 13 99 ab a7 15 - 57 76 47 a1 fb e3 b8 99
2024/07/15 15:12:04.683614780 {wncd_x_R0-0}{1}: [radius] [14709]: (info): RADIUS: User-Name [1] 10 "testuser"
Authentication is successful and client policy state is at RUN.
2024/07/15 15:12:04.683901842 {wncd_x_R0-0}{1}: [webauth-state] [14709]: (info): mobility_a0000001[a0ce.c8c3.a9b5][ 10.105.211.69]State AUTHENTICATING -> AUTHC_SUCCESS
2024/07/15 15:12:04.690643388 {wncd_x_R0-0}{1}: [errmsg] [14709]: (info): %CLIENT_ORCH_LOG-6-CLIENT_ADDED_TO_RUN_STATE: R0/0: wncd: Username entry (testuser) joined with ssid (Guest-Profile) for device with MAC: a0ce.c8c3.a9b5 on channel (0)
2024/07/15 15:12:04.690726966 {wncd_x_R0-0}{1}: [aaa-attr-inf] [14709]: (info): [ Applied attribute :bsn-vlan-interface-name 0 "VLAN2024" ]
2024/07/15 15:12:04.691064276 {wncd_x_R0-0}{1}: [client-orch-state] [14709]: (note): MAC: a0ce.c8c3.a9b5 Client state transition: S_CO_L3_AUTH_IN_PROGRESS -> S_CO_RUN
Embedded packet capture analysis
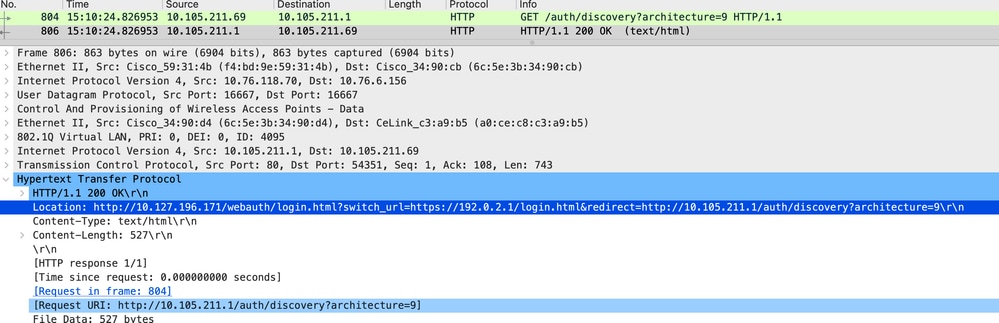 Client is redirected to the portal page
Client is redirected to the portal page
Session is closed after receiving the redirect URL.
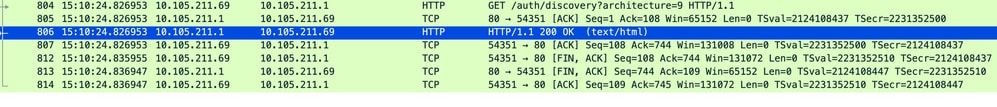 TCP session is closed after receiving the redirect URL
TCP session is closed after receiving the redirect URL
Client initiates TCP 3 way handshake to the redirect URL host and sends a HTTP GET request.
Once the page loads, the login credentials are submiited on the portal, the controller sends a Access Request to the radius server to authenticate the client.
After successful authentication, the TCP session to the web server is closed and on the controller, the client policy manager state is transistioned to RUN.
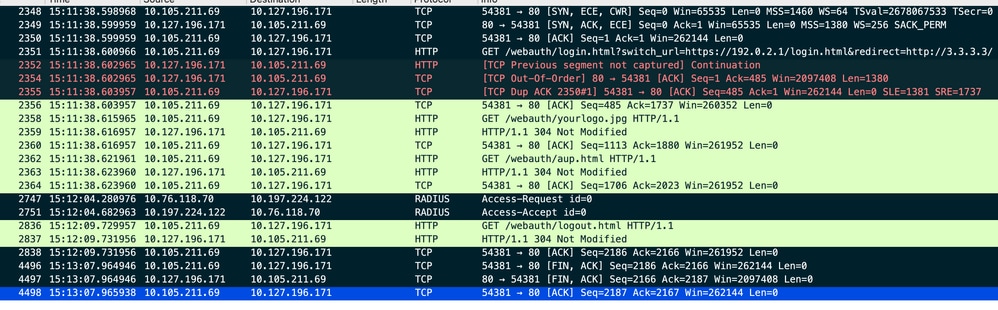 Client sends a HTTP GET request to the portal page and completes the authentication successfullyu
Client sends a HTTP GET request to the portal page and completes the authentication successfullyu
Radius Access Request packet
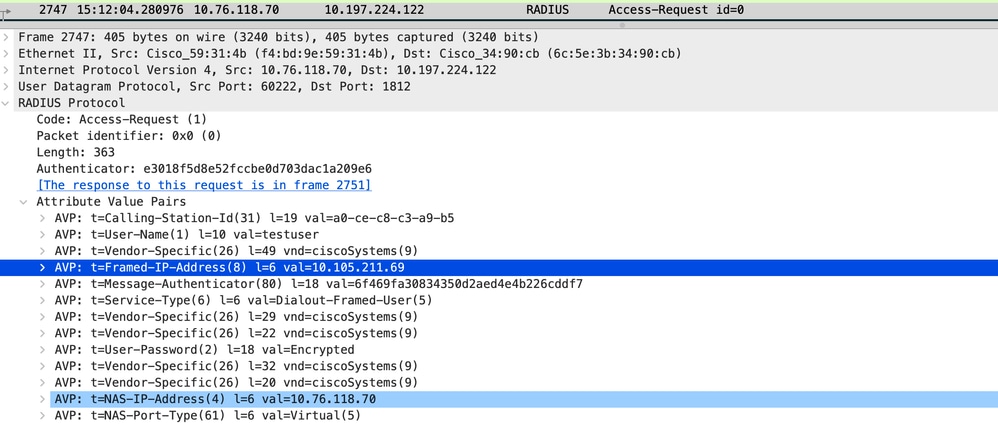 Access Request Packet
Access Request Packet
Radius Access Accept Packet
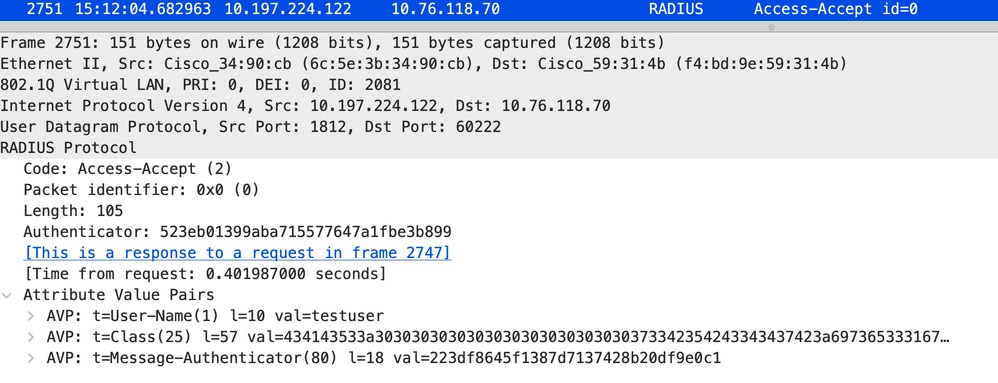 Access Accept packet
Access Accept packet
Related Article
Configure WLAN Anchor Mobility Feature on Catalyst 9800
Wired Guest Access using AireOS Controllers Configuration Example
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
29-Jul-2024
|
Initial Release |
Contributed by Cisco Engineers
- Vinesh VeerarasuTechnical Consulting Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback