|
N9K-C9348GC-FXP1
|
48 x 100M/1G BASE-T downlinks
4 x 10/25-Gbps SFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
48 x 100M/1G BASE-T downlinks
4 x 10/25-Gbps SFP28 uplinks
2 x 40/100-Gbps QSFP28 uplinks
|
Same as default port configuration
|
3.1(1)
|
|
N9K-C93180LC-EX
|
24 x 40 Gbps QSFP28 downlinks (ports 1-24)
2 x 40/100 Gbps QSFP28 uplinks (ports 25, 27)
4 x 40/100 Gbps QSFP28 uplinks (ports 29-32)
Or
12 x 100 Gbps QSFP28 downlinks (odd number ports from 1-24)
2 x 40/100 Gbps QSFP28 uplinks (ports 25, 27)
4 x 40/100 Gbps QSFP28 uplinks (ports 29-32)
|
18 x 40-Gbps QSFP28 downlinks (from 1-24)
6 x 40-Gbps QSFP28 uplinks(from 1-24)
2 x 40/100-Gbps QSFP28 uplinks(25, 27)
4 x 40/100-Gbps QSFP28 uplinks(29-32)
Or
6 x 100-Gbps QSFP28 downlinks(odd number from 1-24)
6 x 100-Gbps QSFP28 uplinks(odd number from 1-24)
2 x 40/100-Gbps QSFP28 uplinks(25, 27)
4 x 40/100-Gbps QSFP28 uplinks(29-32)
|
24 x 40-Gbps QSFP28 downlinks(1-24)
2 x 40/100-Gbps QSFP28 downlinks(25, 27)
4 x 40/100-Gbps QSFP28 uplinks(29-32)
Or
12 x 100-Gbps QSFP28 downlinks(odd number from 1-24)
2 x 40/100-Gbps QSFP28 downlinks (25, 27)
4 x 40/100-Gbps QSFP28 uplinks(29-32)
|
3.1(1)
|
|
N9K-C93180YC-EX
N9K-C93180YC-FX
N9K-C93180YC-FX3
|
48 x 10/25-Gbps fiber downlinks
6 x 40/100-Gbps QSFP28 uplinks
|
Same as default port configuration
|
48 x 10/25-Gbps fiber downlinks
4 x 40/100-Gbps QSFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
3.1(1)
|
|
48 x 10/25-Gbps fiber uplinks
6 x 40/100-Gbps QSFP28 uplinks
|
4.0(1)
|
|
5.1(3)
|
|
N9K-C93108TC-EX2
N9K-C93108TC-FX2
N9K-C93108TC-FX3
|
48 x 10GBASE-T downlinks
6 x 40/100-Gbps QSFP28 uplinks
|
Same as default port configuration
|
48 x 10/25-Gbps fiber downlinks
4 x 40/100-Gbps QSFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
3.1(1)
|
|
4.0(1)
|
|
5.1(3)
|
|
N9K-C9336C-FX2
|
30 x 40/100-Gbps QSFP28 downlinks
6 x 40/100-Gbps QSFP28 uplinks
|
18 x 40/100-Gbps QSFP28 downlinks
18 x 40/100-Gbps QSFP28 uplinks
|
Same as default port configuration
|
3.2(1)
|
|
18 x 40/100-Gbps QSFP28 downlinks
18 x 40/100-Gbps QSFP28 uplinks
|
34 x 40/100-Gbps QSFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
3.2(3)
|
|
36 x 40/100-Gbps QSFP28 uplinks
|
34 x 40/100-Gbps QSFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
4.1(1)
|
|
N9K-93240YC-FX2
|
48 x 10/25-Gbps fiber downlinks
12 x 40/100-Gbps QSFP28 uplinks
|
Same as default port configuration
|
48 x 10/25-Gbps fiber downlinks
10 x 40/100-Gbps QSFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
4.0(1)
|
|
48 x 10/25-Gbps fiber uplinks
12 x 40/100-Gbps QSFP28 uplinks
|
4.1(1)
|
|
N9K-C93216TC-FX2
|
96 x 10G BASE-T downlinks
12 x 40/100-Gbps QSFP28 uplinks
|
Same as default port configuration
|
96 x 10G BASE-T downlinks
10 x 40/100-Gbps QSFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
4.1(2)
|
|
N9K-C93360YC-FX2
|
96 x 10/25-Gbps SFP28 downlinks
12 x 40/100-Gbps QSFP28 uplinks
|
44 x 10/25Gbps SFP28 downlinks
52 x 10/25Gbps SFP28 uplinks
12 x 40/100Gbps QSFP28 uplinks
|
96 x 10/25-Gbps SFP28 downlinks
10 x 40/100-Gbps QSFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
4.1(2)
|
|
N9K-C93600CD-GX
|
28 x 40/100 Gbps QSFP28 downlinks (ports 1-28)
8 x 40/100/400 Gbps QSFP-DD uplinks (ports 29-36)
|
28 x 40/100-Gbps QSFP28 uplinks
8 x 40/100/400-Gbps QSFP-DD uplinks
|
28 x 40/100-Gbps QSFP28 downlinks
6 x 40/100/400-Gbps QSFP-DD downlinks
2 x 40/100/400-Gbps QSFP-DD uplinks
|
4.2(2)
|
|
N9K-C9364C-GX
|
48 x 40/100 Gbps QSFP28 downlinks (ports 1-48)
16 x 40/100 Gbps QSFP28 uplinks (ports 49-64)
|
64 x 40/100-Gbps QSFP28 uplinks
|
62 x 40/100-Gbps QSFP28 downlinks
2 x 40/100-Gbps QSFP28 uplinks
|
4.2(3)
|
|
N9K-C9316D-GX
|
12 x 40/100/400 Gbps QSFP-DD downlinks (ports 1-12)
4 x 40/100/400 Gbps QSFP-DD uplinks (ports 13-16)
|
16 x 40/100/400 Gbps QSFP-DD uplinks
|
14 x 40/100/400 Gbps QSFP-DD downlinks
|
5.1(4)
|



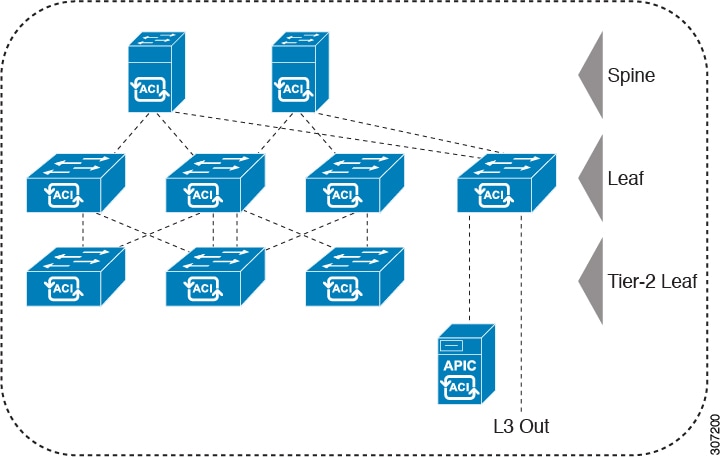








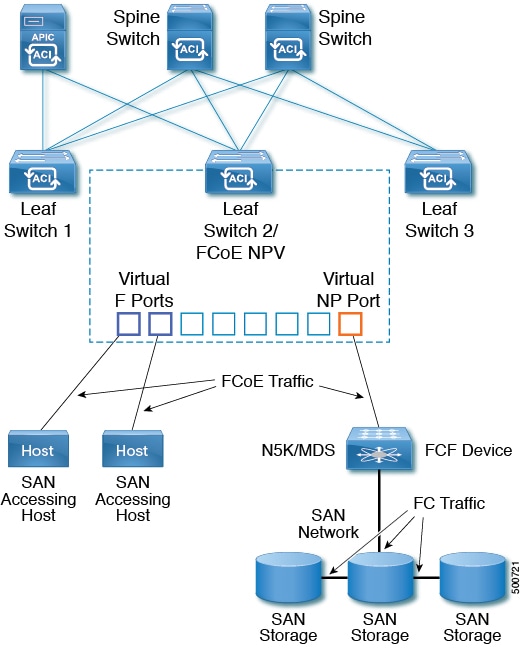






 Feedback
Feedback