New and Changed Information
The following table provides an overview of the significant changes up to this current release. The table does not provide an exhaustive list of all changes or of the new features up to this release.
|
Cisco APIC Release Version |
Feature |
||
|---|---|---|---|
|
6.1(3) |
Modified GUI for enhanced user experience and ease of use. |
||
|
6.1(2) |
Support for shared services using route-leak across EPGs and support for microsegment (useg) EPGs. |
||
|
6.1(1) |
Support for Cisco APIC and Cisco ISE integration.
|
Overview of the Cisco APIC-ISE integration
Cisco employs various controllers to manage policy, including the Application Policy Infrastructure Controller (APIC) in the Data Center and the Cisco Identity Services Engine (ISE) in campus and enterprise environments. Traditionally, these controllers operate independently, functioning as isolated systems. Both Cisco APIC and Cisco ISE facilitate the classification of devices, endpoints, and/or users into groups for policy enforcement, this classification criteria is referred to as context.
Integrating ISE with Cisco ACI provides a solution that allows Cisco ISE and APICs to communicate and share context information using Cisco pxGrid (Platform Exchange Grid). This integration enables the exchange of group information between Cisco APIC and ISE and is part of the Common Policy architecture, which supports the sharing of group context among various controllers connected to ISE as a central context exchange hub.
Important terms used frequently in this document:
-
Endpoint Group (EPG): is a logical entity containing a group of endpoints, belonging to the same Bridge Domain (BD), and sharing the same network and security policies. An EPG can belong to only one bridge domain.
-
Endpoint Security Group (ESG): is a logical entity that contains a collection of physical or virtual network endpoints. An ESG is associated to a single VRF instance. ESGs allow you to define a security policy that spans across multiple bridge domains. With ESGs, you can group and apply policy to any number of endpoints across any number of BDs under a given VRF.
-
Security Group Tag (SGT): is a unique tag that is assigned to a unique role. It represents the privilege of the source user, device, or entity and is tagged at the ingress of the Cisco TrustSec domain.
-
Trustsec: is a security architecture that uses SGTs for enforcing access control policies on the network.
-
pxGrid: is an open and scalable IETF-approved standard that enables cross-platform network collaboration. Platforms can share or publish context as well as consume or subscribe to context from other platforms.
-
Binding: SGTs, EPGs, and ESGs are distinct terminologies that serve the same purpose. They all classify an IP address associated with a user, device, or service into a specified group. The IP address to group association is referred to as a binding.
-
Inbound SGT Domain Rules: are rules that are used to map SGT bindings with specific SGT domains.
-
Outbound SGT Domain Rules: are rules that are used to assign SGT bindings to APIC as external EPGs.
This document cannot be used alone. Refer to the Cisco ISE Administrator Guide, Release 3.4 which has relevant details, and configurations performed using Cisco ISE.
Integrating Cisco APIC with Cisco ISE
This document provides details of the Cisco APIC-ISE integration. In this integration, the ISE controller is responsible for managing the sharing of group context between domains. Configurations are performed from the ISE controller. Cisco APIC provides visibility into this integration from the Cisco APIC UI, including status of the integration connections and group and binding information for the groups being shared between the two domains.
The ISE integration supports Multi-Pod, multi-tenant, multi-VRF, and EPG (or ESG) context for APIC. You can set up a bi-directional connection to multiple ACI fabrics, including single pod and Multi-Pod fabrics, directly from ISE and start exchanging SGT/EPG/ESG context. The EPGs (or ESGs) in ACI are normalized and stored in ISE as SGTs. This enables all the domain controllers that consume context from ISE, to configure policies for traffic from user/devices in the campus/branch to end-point groups in the data center. The SGTs in ISE are normalized and stored in ACI as external EPGs.
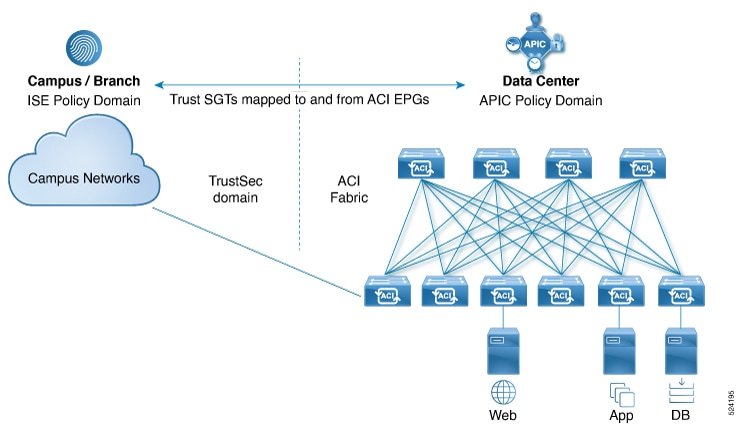
ISE publishes the SGTs and bindings over the pxGrid channel to APIC. The SGTs and bindings are programmed as external EPGs (EEPGs) with subnet bindings allowing APIC to classify and apply policy on packets coming into the ACI fabric based on the group membership in ISE. Similarly, APIC publishes EPG and ESG group and endpoint information to ISE where it is translated to SGTs and bindings, allowing ISE to classify and apply policy on packets coming into the campus network from the ACI fabric.
Advantages of the Cisco APIC-ISE integration
-
Establishes context independently within each domain. The context is then normalized and stored as SGTs, allowing for sharing across different domains.
-
Allows for consistent SGT-based policies for a simple, unified policy experience.
-
Enforces consistent access policies between users, devices and application workloads.
Cisco APIC-ISE terminology
|
Cisco APIC |
Cisco ISE |
|---|---|
|
End Point Group (EPG) or End Point Security Group (ESG) |
Security Group Tag (SGT) |
|
IP-EPG Bindings |
IP-SGT Bindings |
|
Contracts |
TrustSec Policy |
Guidelines and limitations for the Cisco APIC-ISE integration
Guidelines
-
The supported ISE version is ISE 3.4P1.
-
ISE to ACI connection is established on one of the controllers of the APIC cluster. If the node with the ISE-ACI connection is down, takeover time by the other nodes of the cluster is around five minutes.
-
Shared services are supported between campus SGT to EPG or campus SGT to SGT.
Limitations
-
The VRF containing SGT associated L3Out can be in ingress mode or egress mode.
VRFs containing L3Outs with SGT external EPGs (referred to as campus SGT L3Out in this document) can be configured in ingress or egress policy control enforcement direction.
Restrictions with ingress policy control enforcement direction:
-
Intersite L3Out.
-
Dynamic EPG classification (DEC) cannot co-exist with configurations in the same L3Out.
-
EPGs need to be providers for shared service contracts.
-
For pure non-border leaf to campus-border leaf traffic, policy is applied at the campus-border leaf node.
-
-
One SGT is associated to one ISE-ACI connection. One SGT to multiple ISE-ACI connections is not supported. As multiple ISE connections are programming SGTs in ACI, each ISE connection must configure a unique SGT name when programmed under the same L3Out.
-
A few seconds of traffic loss may be seen for prefixes learned on a campus SGT L3Out when the first SGT (external EPG) is configured by ISE.
-
Configuration rollback is not supported. If you try to perform a rollback, there are chances of configuration discrepancies between ISE and ACI and you may need to remove and/or re-apply the configurations in ISE to keep ISE and ACI in sync.
Supported scale numbers for the Cisco APIC-ISE integration
|
Parameter |
Scale |
|---|---|
|
ACI Sites or ACI Clusters |
75 |
|
Maximum number of ISE connections per ACI fabric |
3 |
|
Tenants per ACI fabric |
10 |
|
VRFs per ACI fabric |
50 |
|
Maximum L3Outs per ACI fabric |
500 |
|
Maximum SGTs Per L3Out |
250 |
|
Maximum EPG/ESG Published from 1 ACI fabric to ISE |
500 |
|
Maximum SGTs Subscribed from all ISEs by 1 ACI Fabric |
500 |
|
Maximum SGTs – ISE |
50000 |
|
Maximum Trustsec Matrix |
10000 |
|
Maximum IPv4 and IPv6 Bindings Per ACI Fabric Per ISE Connection |
32000 |
|
Maximum IPv4 and IPv6 Bindings for Solution |
2 million |
|
Maximum IPv4 Bindings Received by 1 ACI Fabric from all ISE Connections |
64000 |
|
Maximum IPv6 Bindings Received by 1 ACI Fabric from all ISE Connections |
64000 |
|
Maximum IPv4 and IPv6 Bindings Received by 1 ACI Fabric from all ISE Connections |
64000 |
 Note |
SGT bindings serve as host prefixes for external EPGs. |
Using Cisco APIC for network visiblity
ISE creates a connection to the APIC, establishes a pxGRID channel between ISE and APIC. The SGTs created in ISE are published as external EPGs in APIC.
Complete these prerequisites on Cisco ISE:
-
Enable pxGrid and SXP services in a standalone/deployment setup.
-
Configure DNS so that ACI can recognize ISE and vice versa.
-
Create an ACI connection, this is indicated as an object on APIC.
Complete these prerequisites on Cisco APIC:
-
Configure standard APIC configurations such as, tenants, VRFs, L3Out, contracts.
-
Configure application EPGs and/or ESGs.
-
Configure a DNS server for ISE pxGrid devices.
-
Configure a DNS server and ensure ISE FQDN is reachable from the APIC.
There are two locations on the APIC GUI where you can get ISE-configured details.
Details from the Integrations tab
Use the following procedure to get details of the ACI connection created in ISE.
Before you begin
On the ISE GUI, configure an ACI connection (example: S1_ACI). You can add multiple ACI connections on Cisco ISE.
Procedure
|
Step 1 |
Log in to the Cisco APIC GUI. |
|
Step 2 |
Navigate to Integrations > ISE Integrations. The ACI-ISE connections are displayed. 
|
|
Step 3 |
Click a connection name to get more information about each connection. The details displayed for each connection are: Overview, Connection Details, Endpoints, Configuration, History. The details for each of these tabs are available as clickable tiles, such as General, Endpoints, etc. Click a tile to get a new pop-up screen that displays the details. 
Details displayed in the Overview tab:
Details displayed in the Connections tab:
Details displayed in the Endpoints tab:
Details displayed in the Configuration tab: 
Details displayed in the History tab: Displays standard event and audit logs. |
Details from the Tenants tab
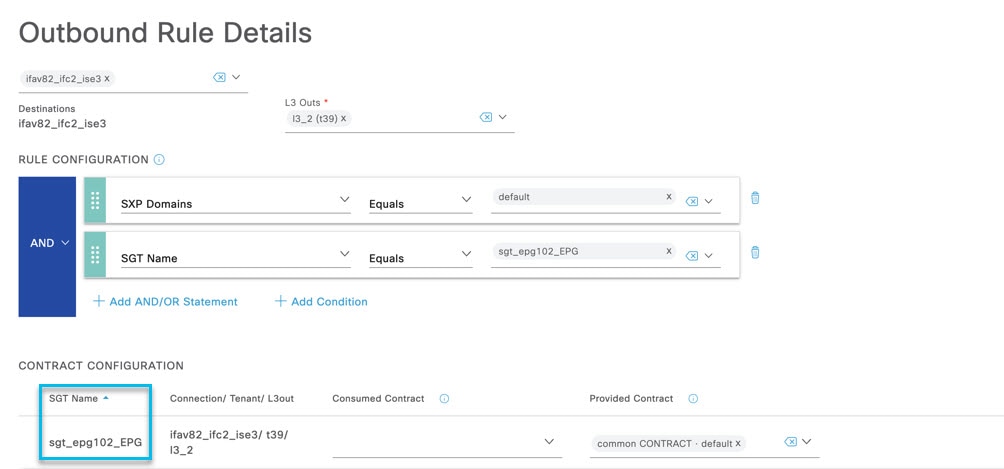
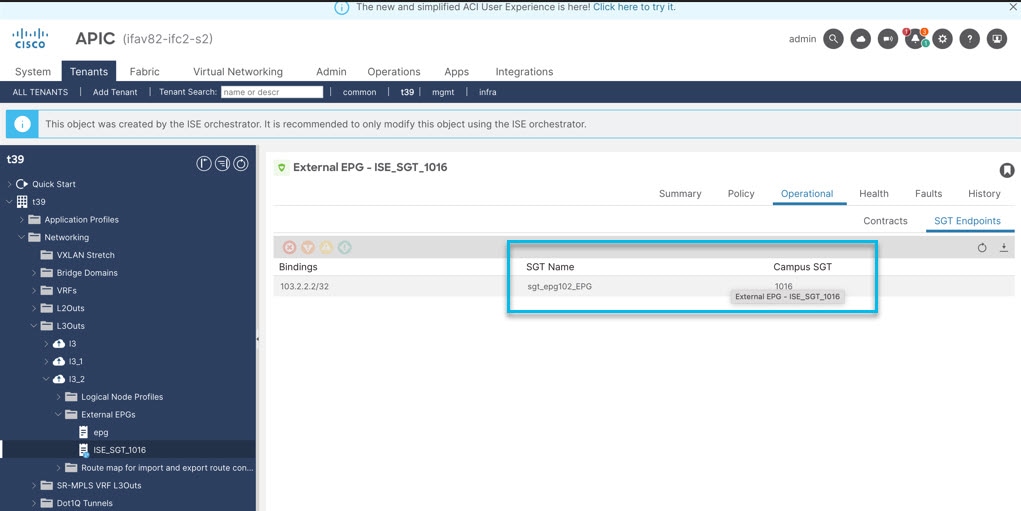
When ISE publishes the SGTs to APIC, the SGTs are configured as external EPGs under a tenant L3Out.
Use the following procedure to get details of the external EPGs (EEPG) created on APIC, based on the SGTs published by ISE.
Figures 3 and 4 display the SGTs created on ISE which are available as EEPGs on APIC. The corresponding EEPG on APIC for the
SGT created on ISE, sgt_epg102_EPG, is ISE_SGT_1016.
Procedure
|
Step 1 |
Log in to the Cisco APIC GUI. |
||
|
Step 2 |
Navigate to Tenants > Web-App > Networking > L3Outs > External EPGs. The outbound SGTs created on ISE are displayed here (APIC GUI) as external EPGs. |
||
|
Step 3 |
Click an SGT displayed under the EEPGs to get details about it on the right side of the screen. A banner is displayed at the top of the screen stating that the object was created using ISE and you can modify the object only using the ISE orchestrator. |
||
|
Step 4 |
To check the bindings attached to the selected SGT, on the right side pane, click Operational > SGT Endpoints.
|
Configure route leaking for shared services
Procedure
|
Step 1 |
On the Cisco APIC GUI, click the Tenants tab. |
|
Step 2 |
Navigate to Networking > L3Outs> L3_out_name > External EPGs. Right-click and select Create External EPG. |
|
Step 3 |
On the Create External EPG window that is displayed, enter the required details. |
|
Step 4 |
In the Subnets pane, click (+). |
|
Step 5 |
On the Create Subnet window that is displayed, enter the IP address and select the Shared Route Control Subnet check-box. The subnet here is the IP prefix learned through the campus SGT L3Out. |
|
Step 6 |
Click OK, and then Submit (External EPG window). 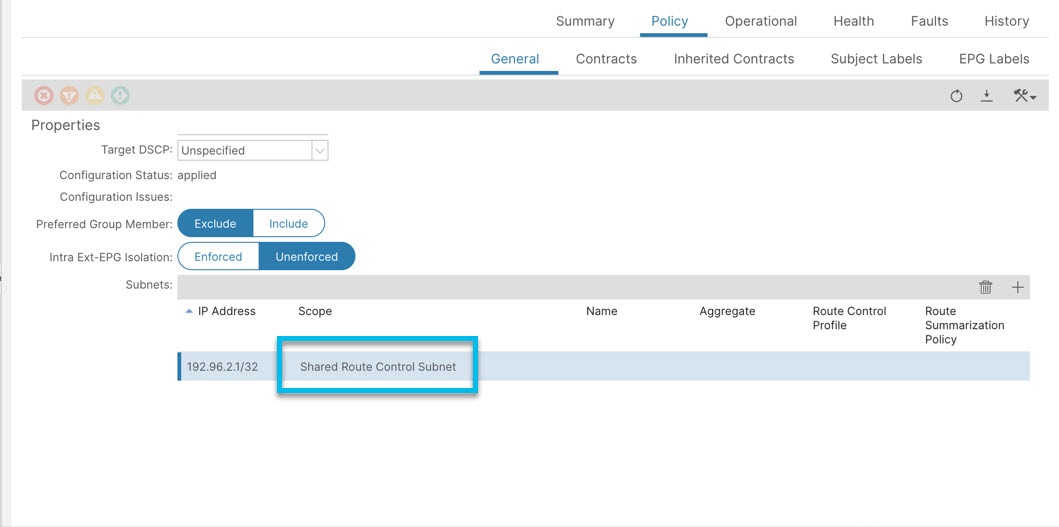 |
|
Step 7 |
Click the created external EPG and select the Policy > Contracts tab. |
|
Step 8 |
Click the Actions icon, and select a contract from the drop-down list. 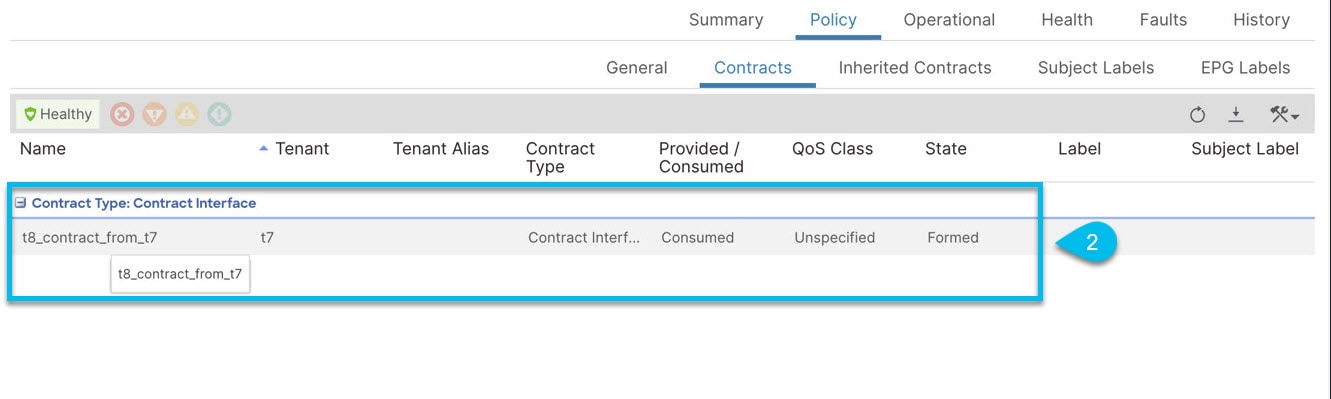
|
|
Step 9 |
(On the ISE GUI) Deploy the ISE SGT with the IP prefix and contract from ISE. Ensure to select the same shared contract as was defined for the external EPG on APIC. |
 Feedback
Feedback