RADIUS Attributes
Available Languages
Table Of Contents
Supported IETF RADIUS Attributes
Comprehensive List of IETF RADIUS Attribute Descriptions
Vendor-Proprietary RADIUS Attributes
Supported Vendor-Proprietary RADIUS Attributes
Comprehensive List of Vendor-Proprietary RADIUS Attribute Descriptions
RADIUS Vendor-Specific Attributes (VSA)
RADIUS Disconnect-Cause Attribute Values
RADIUS Attributes
Remote Authentication Dial-In User Service (RADIUS) attributes are used to define specific authentication, authorization, and accounting elements in a user profile, which is stored on the RADIUS daemon. This appendix lists the RADIUS attributes currently supported.
In This Appendix
This appendix is divided into five sections:
•
Vendor-Proprietary RADIUS Attributes
•
RADIUS Vendor-Specific Attributes (VSA)
•
RADIUS Disconnect-Cause Attribute Values
RADIUS Attributes Overview
This section contains information important to understanding how RADIUS attributes exchange authentication, authorization, and accounting (AAA) information between a client and server and includes the following sections:
IETF Attributes Versus VSAs
RADIUS Internet Engineering Task Force (IETF) attributes are the original set of 255 standard attributes that are used to communicate AAA information between a client and a server. Because IETF attributes are standard, the attribute data is predefined and well known; thus all clients and servers who exchange AAA information via IETF attributes must agree on attribute data such as the exact meaning of the attributes and the general bounds of the values for each attribute.
RADIUS vendor-specific Attributes (VSAs) derived from one IETF attribute—Vendor-Specific (attribute 26). Attribute 26 allows a vendor to create an additional 255 attributes however they wish. That is, a vendor can create an attribute that does not match the data of any IETF attribute and encapsulate it behind attribute 26; thus, the newly created attribute is accepted if the user accepts attribute 26.
For more information on VSAs, refer to the section "RADIUS Vendor-Specific Attributes (VSA)" later in this appendix.
RADIUS Packet Format
The data passing between a RADIUS server and a RADIUS client is exchanged in RADIUS packets. The data fields are transmitted from left to right.
Figure 43 shows the fields within a RADIUS packet.

Note
For a diagram of VSAs, which is an extension of Figure 43, refer to Figure 44.
Figure 43 RADIUS Packet Diagram

Each RADIUS packet contains the following information:
•
Code—The code field is one octet; it identifies one of the following types of RADIUS packets:
–
Access-Request (1)
–
Access-Accept (2)
–
Access-Reject (3)
–
Accounting-Request (4)
–
Accounting-Response (5)
•
Identifier—The identifier field is one octet; it helps the RADIUS server match requests and responses and detect duplicate requests.
•
Length—The length field is two octets; it specifies the length of the entire packet.
•
Authenticator—The authenticator field is 16 octets. The most significant octet is transmitted first; it is used to authenticate the reply from the RADIUS server. Two types of authenticators are as follows:
–
Request-Authentication: Available in Access-Request and Accounting-Request packets
–
Response-Authenticator: Available in Access-Accept, Access-Reject, Access-Challenge, and Accounting-Response packets
RADIUS Packet Types
Access-Request packet—Sent from a client to a RADIUS server. The packet contains information that allows the RADIUS server to determine whether to allow access to a specific network access server (NAS), which will allow access to the user. Any user performing authentication must submit an Access-Request packet. Once an Access-Request packet is received, the RADIUS server must forward a reply.
Access-Accept packet—Once a RADIUS server receives an Access-Request packet, it must send an Access-Accept packet if all attribute values in the Access-Request packet are acceptable. Access-Accept packets provide the configuration information necessary for the client to provide service to the user.
Access-Reject packet—Once a RADIUS server receives an Access-Request packet, it must send an Access-Reject packet if any of the attribute values are not acceptable.
Access-Challenge packet—Once the RADIUS server receives an Access-Accept packet, it can send the client an Access-Challenge packet, which requires a response. If the client does not know how to respond or if the packets are invalid, the RADIUS server discards the packets. If the client responds to the packet, a new Access-Request packet should be sent with the original Access-Request packet.
Accounting-Request packet—Sent from a client to a RADIUS accounting server, which provides accounting information. If the RADIUS server successfully records the Accounting-Request packet, it must submit an Accounting Response packet.
Accounting-Response packet—Sent by the RADIUS accounting server to the client to acknowledge that the Accounting-Request has been received and recorded successfully.
RADIUS Files
Understanding the types of files used by RADIUS is important for communicating AAA information from a client to a server. Each file defines a level of authentication or authorization for the user: The dictionary file defines which attributes the user's NAS can implement; the clients file defines which users are allowed to make requests to the RADIUS server; the users files defines which user requests the RADIUS server will authenticate based on security and configuration data.
•
Dictionary File
•
Clients File
•
Users File
Dictionary File
A dictionary file provides two types of entries: a list of attributes that are dependent upon which attributes your NAS supports and a value. However, you can add your own set of attributes to your dictionary for custom solutions. It defines attribute values, thereby allowing you to interpret attribute output such as parsing requests. A dictionary file contains the following information:
•
Name—The ASCII string "name" of the attribute, such as User-Name.
•
ID—The numerical "name" of the attribute; for example, User-Name attribute is attribute 1.
•
Value type—Each attribute can be specified as one of the following five value types:
–
abinary—0 to 254 octets.
–
date—32-bit value in big endian order. For example, seconds since 00:00:00 GMT, JAN. 1, 1970.
–
ipaddr—4 octets in network byte order.
–
integer—32-bit value in big endian order (high byte first).
–
string—0 to 253 octets.
When the data type for a particular attribute is an integer, you can optionally expand the integer to equate to some string. The follow sample dictionary includes an integer-based attribute and its corresponding values:
# dictionary sample of integer entry#ATTRIBUTE Service-Type 6 integerVALUE Service-Type Login 1VALUE Service-Type Framed 2VALUE Service-Type Callback-Login 3VALUE Service-Type Callback-Framed 4VALUE Service-Type Outbound 5VALUE Service-Type Administrative 6VALUE Service-Type NAS-Prompt 7VALUE Service-Type Authenticate-Only 8VALUE Service-Type Callback-NAS-Prompt 9VALUE Service-Type Call-Check 10VALUE Service-Type Callback-Administrative 11Clients File
A clients file is important because it contains a list of RADIUS clients that are allowed to send authentication and accounting requests to the RADIUS server. To receive authentication, the name and authentication key the client sends the server must be an exact match with the data contained in clients file.
The following is an example of a clients file. The key, as shown in this example, must be the same as the radius-server key SomeSecret command.
#Client Name Key#---------------- ---------------10.1.2.3:256 testnas01 bananasnas02 MoNkEysnas07.foo.com SomeSecretUsers File
A RADIUS users file contains an entry for each user that the RADIUS server will authenticate; each entry, which is also referred to as a user profile, establishes an attribute the user can access.
The first line in any user profile is always a "user access" line; that is, the server must check the attributes on the first line before it can grant access to the user. The first line contains the name of the user, which can be up to 252 characters, followed by authentication information such as the password of the user.
Additional lines, which are associated with the user access line, indicate the attribute reply that is sent to the requesting client or server. The attributes sent in the reply must be defined in the dictionary file.
When looking at a user file, please note the the data to the left of the equal (=) character is an attribute defined in the dictionary file, and the data to the right of the equal character in the configuration data.

Note
A blank line cannot appear anywhere within a user profile.
The following is an example of a RADIUS user profile (Merit Daemon format). In this example, the user name is cisco.com, the password is cisco, and the user can access five tunnel attributes.
# This user profile includes RADIUS tunneling attributesdomain.com Password="cisco" Service-Type=OutboundTunnel-Type = :1:L2TPTunnel-Medium-Type = :1:IPTunnel-Server-Endpoint = :1:10.0.0.1Tunnel-Password = :1:"welcome"Tunnel-Assignment-ID = :1:"nas"Supporting Documentation
For more information on RADIUS IETF and Vendor-Proprietary Attributes, refer to the following documents:
•
Cisco AAA Implementation Case Study
•
"Configuring RADIUS," "Configuring Authentication," "Configuring Authorization," and "Configuring Accounting" chapters in this book.
•
IETF RADIUS RFCs
–
RFC 2865, Remote Authentication Dial In User Service (RADIUS)
–
RFC 2866, RADIUS Accounting
–
RFC 2867, RADIUS Accounting Modifications for Tunnel Protocol Support
–
RFC 2868, RADIUS Attributes for Tunnel Protocol Support
–
RFC 2869, RADIUS Extensions
•
RADIUS Vendor-Specific Attributes Voice Implementation Guide
RADIUS IETF Attributes
This section contains the following sections:
•
Supported IETF RADIUS Attributes
•
Comprehensive List of IETF RADIUS Attribute Descriptions
Supported IETF RADIUS Attributes
Table 30 lists Cisco-supported IETF RADIUS attributes and the Cisco IOS release in which they are implemented. In cases where the attribute has a security server-specific format, the format is specified.
Refer to Table 31 for a description of each listed attribute.

Note
Attributes implemented in special (AA) or early development (T) releases will be added to the next mainline image.
Table 30 Supported RADIUS IETF Attributes
1
User-Name
yes
yes
yes
yes
yes
yes
yes
yes
2
User-Password
yes
yes
yes
yes
yes
yes
yes
yes
3
CHAP-Password
yes
yes
yes
yes
yes
yes
yes
yes
4
NAS-IP Address
yes
yes
yes
yes
yes
yes
yes
yes
5
NAS-Port
yes
yes
yes
yes
yes
yes
yes
yes
6
Service-Type
yes
yes
yes
yes
yes
yes
yes
yes
7
Framed-Protocol
yes
yes
yes
yes
yes
yes
yes
yes
8
Framed-IP-Address
yes
yes
yes
yes
yes
yes
yes
yes
9
Framed-IP-Netmask
yes
yes
yes
yes
yes
yes
yes
yes
10
Framed-Routing
yes
yes
yes
yes
yes
yes
yes
yes
11
Filter-Id
yes
yes
yes
yes
yes
yes
yes
yes
12
Framed-MTU
yes
yes
yes
yes
yes
yes
yes
yes
13
Framed-Compression
yes
yes
yes
yes
yes
yes
yes
yes
14
Login-IP-Host
yes
yes
yes
yes
yes
yes
yes
yes
15
Login-Service
yes
yes
yes
yes
yes
yes
yes
yes
16
Login-TCP-Port
yes
yes
yes
yes
yes
yes
yes
yes
18
Reply-Message
yes
yes
yes
yes
yes
yes
yes
yes
19
Callback-Number
no
no
no
no
no
no
yes
yes
20
Callback-ID
no
no
no
no
no
no
no
no
22
Framed-Route
yes
yes
yes
yes
yes
yes
yes
yes
23
Framed-IPX-Network
no
no
no
no
no
no
no
no
24
State
yes
yes
yes
yes
yes
yes
yes
yes
25
Class
yes
yes
yes
yes
yes
yes
yes
yes
26
Vendor-Specific
yes
yes
yes
yes
yes
yes
yes
yes
27
Session-Timeout
yes
yes
yes
yes
yes
yes
yes
yes
28
Idle-Timeout
yes
yes
yes
yes
yes
yes
yes
yes
29
Termination-Action
no
no
no
no
no
no
no
no
30
Called-Station-Id
yes
yes
yes
yes
yes
yes
yes
yes
31
Calling-Station-Id
yes
yes
yes
yes
yes
yes
yes
yes
32
NAS-Identifier
no
no
no
no
no
no
no
yes
33
Proxy-State
no
no
no
no
no
no
no
no
34
Login-LAT-Service
yes
yes
yes
yes
yes
yes
yes
yes
35
Login-LAT-Node
no
no
no
no
no
no
no
yes
36
Login-LAT-Group
no
no
no
no
no
no
no
no
37
Framed-AppleTalk-Link
no
no
no
no
no
no
no
no
38
Framed-AppleTalk- Network
no
no
no
no
no
no
no
no
39
Framed-AppleTalk-Zone
no
no
no
no
no
no
no
no
40
Acct-Status-Type
yes
yes
yes
yes
yes
yes
yes
yes
41
Acct-Delay-Time
yes
yes
yes
yes
yes
yes
yes
yes
42
Acct-Input-Octets
yes
yes
yes
yes
yes
yes
yes
yes
43
Acct-Output-Octets
yes
yes
yes
yes
yes
yes
yes
yes
44
Acct-Session-Id
yes
yes
yes
yes
yes
yes
yes
yes
45
Acct-Authentic
yes
yes
yes
yes
yes
yes
yes
yes
46
Acct-Session-Time
yes
yes
yes
yes
yes
yes
yes
yes
47
Acct-Input-Packets
yes
yes
yes
yes
yes
yes
yes
yes
48
Acct-Output-Packets
yes
yes
yes
yes
yes
yes
yes
yes
49
Acct-Terminate-Cause
no
no
no
yes
yes
yes
yes
yes
50
Acct-Multi-Session-Id
no
yes
yes
yes
yes
yes
yes
yes
51
Acct-Link-Count
no
yes
yes
yes
yes
yes
yes
yes
52
Acct-Input-Gigawords
no
no
no
no
no
no
no
no
53
Acct-Output-Gigawords
no
no
no
no
no
no
no
no
55
Event-Timestamp
no
no
no
no
no
no
no
yes
60
CHAP-Challenge
yes
yes
yes
yes
yes
yes
yes
yes
61
NAS-Port-Type
yes
yes
yes
yes
yes
yes
yes
yes
62
Port-Limit
yes
yes
yes
yes
yes
yes
yes
yes
63
Login-LAT-Port
no
no
no
no
no
no
no
no
64
Tunnel-Type1
no
no
no
no
no
no
yes
yes
65
Tunnel-Medium-Type1
no
no
no
no
no
no
yes
yes
66
Tunnel-Client-Endpoint
no
no
no
no
no
no
yes
yes
67
Tunnel-Server-Endpoint1
no
no
no
no
no
no
yes
yes
68
Acct-Tunnel-Connection-ID
no
no
no
no
no
no
yes
yes
69
Tunnel-Password1
no
no
no
no
no
no
yes
yes
70
ARAP-Password
no
no
no
no
no
no
no
no
71
ARAP-Features
no
no
no
no
no
no
no
no
72
ARAP-Zone-Access
no
no
no
no
no
no
no
no
73
ARAP-Security
no
no
no
no
no
no
no
no
74
ARAP-Security-Data
no
no
no
no
no
no
no
no
75
Password-Retry
no
no
no
no
no
no
no
no
76
Prompt
no
no
no
no
no
no
yes
yes
77
Connect-Info
no
no
no
no
no
no
no
yes
78
Configuration-Token
no
no
no
no
no
no
no
no
79
EAP-Message
no
no
no
no
no
no
no
no
80
Message-Authenticator
no
no
no
no
no
no
no
no
81
Tunnel-Private-Group-ID
no
no
no
no
no
no
no
no
82
Tunnel-Assignment-ID1
no
no
no
no
no
no
yes
yes
83
Tunnel-Preference
no
no
no
no
no
no
no
yes
84
ARAP-Challenge-Response
no
no
no
no
no
no
no
no
85
Acct-Interim-Interval
no
no
no
no
no
no
yes
yes
86
Acct-Tunnel-Packets-Lost
no
no
no
no
no
no
no
no
87
NAS-Port-ID
no
no
no
no
no
no
no
no
88
Framed-Pool
no
no
no
no
no
no
no
no
90
Tunnel-Client-Auth-ID2
no
no
no
no
no
no
no
yes
91
Tunnel-Server-Auth-ID
no
no
no
no
no
no
no
yes
200
IETF-Token-Immediate
no
no
no
no
no
no
no
no
1 This RADIUS attribute complies with the following two draft IETF documents: RFC 2868, RADIUS Attributes for Tunnel Protocol Support and RFC 2867 RADIUS Accounting Modifications for Tunnel Protocol Support.
2 This RADIUS attribute complies with RFC 2865 and RFC 2868.
Comprehensive List of IETF RADIUS Attribute Descriptions
Table 31 lists and describes IETF RADIUS attributes. In cases where the attribute has a security server-specific format, the format is specified.
Table 31 RADIUS IETF Attributes
1
User-Name
Indicates the name of the user being authenticated by the RADIUS server.
2
User-Password
Indicates the user's password or the user's input following an Access-Challenge. Passwords longer than 16 characters are encrypted using RFC 2865 specifications.
3
CHAP-Password
Indicates the response value provided by a PPP Challenge-Handshake Authentication Protocol (CHAP) user in response to an Access-Challenge.
4
NAS-IP Address
Specifies the IP address of the network access server that is requesting authentication. The default value is 0.0.0.0/0.
5
NAS-Port
Indicates the physical port number of the network access server that is authenticating the user. The NAS-Port value (32 bits) consists of one or two 16-bit values (depending on the setting of the radius-server extended-portnames command). Each 16-bit number should be viewed as a 5-digit decimal integer for interpretation as follows:
For asynchronous terminal lines, async network interfaces, and virtual async interfaces, the value is 00ttt, where ttt is the line number or async interface unit number.
For ordinary synchronous network interface, the value is 10xxx.
For channels on a primary rate ISDN interface, the value is 2ppcc.
For channels on a basic rate ISDN interface, the value is 3bb0c.
For other types of interfaces, the value is 6nnss.
6
Service-Type
Indicates the type of service requested or the type of service to be provided.
•
In a request:
Framed for known PPP or SLIP connection.
Administrative-user for enable command.•
In response:
Login—Make a connection.
Framed—Start SLIP or PPP.
Administrative User—Start an EXEC or enable ok.Exec User—Start an EXEC session.
Service type is indicated by a particular numeric value as follows:
•
1: Login
•
2: Framed
•
3: Callback-Login
•
4: Callback-Framed
•
5: Outbound
•
6: Administrative
•
7: NAS-Prompt
•
8: Authenticate Only
•
9: Callback-NAS-Prompt
7
Framed-Protocol
Indicates the framing to be used for framed access. No other framing is allowed.
Framing is indicated by a numeric value as follows:
•
1: PPP
•
2: SLIP
•
3: ARA
•
4: Gandalf-proprietary single-link/multilink protocol
•
5: Xylogics-proprietary IPX/SLIP
8
Framed-IP-Address
Indicates the IP address to be configured for the user, by sending the IP address of a user to the RADIUS server in the access-request. To enable this command, use the radius-server attribute 8 include-in-access-req command in global configuration mode.
9
Framed-IP-Netmask
Indicates the IP netmask to be configured for the user when the user is a router to a network. This attribute value results in a static route being added for Framed-IP-Address with the mask specified.
10
Framed-Routing
Indicates the routing method for the user when the user is a router to a network. Only "None" and "Send and Listen" values are supported for this attribute.
Routing method is indicated by a numeric value as follows:
•
0: None
•
1: Send routing packets
•
2: Listen for routing packets
•
3: Send routing packets and listen for routing packets
11
Filter-Id
Indicates the name of the filter list for the user and is formatted as follows: %d, %d.in, or %d.out. This attribute is associated with the most recent service-type command. For login and EXEC, use %d or %d.out as the line access list value from 0 to 199. For Framed service, use %d or %d.out as interface output access list, and %d.in for input access list. The numbers are self-encoding to the protocol to which they refer.
12
Framed-MTU
Indicates the maximum transmission unit (MTU) that can be configured for the user when the MTU is not negotiated by PPP or some other means.
13
Framed-Compression
Indicates a compression protocol used for the link. This attribute results in a "/compress" being added to the PPP or SLIP autocommand generated during EXEC authorization. Not currently implemented for non-EXEC authorization.
Compression protocol is indicated by a numeric value as follows:
•
0: None
•
1: VJ-TCP/IP header compression
•
2: IPX header compression
14
Login-IP-Host
Indicates the host to which the user will connect when the Login-Service attribute is included. (This begins immediately after login.)
15
Login-Service
Indicates the service that should be used to connect the user to the login host.
Service is indicated by a numeric value as follows:
•
0: Telnet
•
1: Rlogin
•
2: TCP-Clear
•
3: PortMaster
•
4: LAT
16
Login-TCP-Port
Defines the TCP port with which the user is to be connected when the Login-Service attribute is also present.
18
Reply-Message
Indicates text that might be displayed to the user via the RADIUS server. You can include this attribute in user files; however, you cannot exceed a maximum of 16 Reply-Message entries per profile.
19
Callback-Number
Defines a dialing string to be used for callback.
20
Callback-ID
Defines the name (consisting of one or more octets) of a place to be called, to be interpreted by the network access server.
22
Framed-Route
Provides routing information to be configured for the user on this network access server. The RADIUS RFC format (net/bits [router [metric]]) and the old style dotted mask (net mask [router [metric]]) are supported. If the router field is omitted or 0, the peer IP address is used. Metrics are currently ignored. This attribute is access-request packets.
23
Framed-IPX-Network
Defines the IPX network number configured for the user.
24
State
Allows state information to be maintained between the network access server and the RADIUS server. This attribute is applicable only to CHAP challenges.
25
Class
(Accounting) Arbitrary value that the network access server includes in all accounting packets for this user if supplied by the RADIUS server.
26
Vendor-Specific
Allows vendors to support their own extended attributes not suitable for general use. The Cisco RADIUS implementation supports one vendor-specific option using the format recommended in the specification. Cisco's vendor-ID is 9, and the supported option has vendor-type 1, which is named "cisco-avpair." The value is a string of the format:
protocol : attribute sep value"Protocol" is a value of the Cisco "protocol" attribute for a particular type of authorization. "Attribute" and "value" are an appropriate AV pair defined in the Cisco TACACS+ specification, and "sep" is "=" for mandatory attributes and "*" for optional attributes. This allows the full set of features available for TACACS+ authorization to also be used for RADIUS. For example:
cisco-avpair= "ip:addr-pool=first"cisco-avpair= "shell:priv-lvl=15"The first example causes Cisco's "multiple named ip address pools" feature to be activated during IP authorization (during PPP's IPCP address assignment). The second example causes a user logging in from a network access server to have immediate access to EXEC commands.
Table 35 lists supported vendor-specific RADIUS attributes (IETF attribute 26). The "TACACS+ Attribute-Value Pairs" appendix provides a complete list of supported TACACS+ attribute-value (AV) pairs that can be used with IETF attribute 26. (RFC 2865)
27
Session-Timeout
Sets the maximum number of seconds of service to be provided to the user before the session terminates. This attribute value becomes the per-user "absolute timeout."
28
Idle-Timeout
Sets the maximum number of consecutive seconds of idle connection allowed to the user before the session terminates. This attribute value becomes the per-user "session-timeout."
29
Termination-Action
Termination is indicated by a numeric value as follows:
•
0: Default
•
1: RADIUS request
30
Called-Station-Id
(Accounting) Allows the network access server to send the telephone number the user called as part of the Access-Request packet (using Dialed Number Identification Service [DNIS] or similar technology). This attribute is only supported on ISDN, and modem calls on the Cisco AS5200 if used with PRI.
31
Calling-Station-Id
(Accounting) Allows the network access server to send the telephone number the call came from as part of the Access-Request packet (using Automatic Number Identification or similar technology). This attribute has the same value as "remote-addr" from TACACS+. This attribute is only supported on ISDN, and modem calls on the Cisco AS5200 if used with PRI.
32
NAS-Identifier
String identifying the network access server originating the Access-Request. Use the radius-server attribute 32 include-in-access-req global configuration command to send RADIUS attribute 32 in an Access-Request. By default, the FQDN is sent in the attribute when the format is not specified.
33
Proxy-State
Attribute that can be sent by a proxy server to another server when forwarding Access-Requests; this must be returned unmodified in the Access-Accept, Access-Reject or Access-Challenge and removed by the proxy server before sending the response to the network access server.
34
Login-LAT-Service
Indicates the system with which the user is to be connected by LAT. This attribute is only available in the EXEC mode.
35
Login-LAT-Node
Indicates the node with which the user is to be automatically connected by LAT.
36
Login-LAT-Group
Identifies the LAT group codes that this user is authorized to use.
37
Framed-AppleTalk-Link
Indicates the AppleTalk network number that should be used for serial links to the user, which is another AppleTalk router.
38
Framed-AppleTalk-
NetworkIndicates the AppleTalk network number that the network access server uses to allocate an AppleTalk node for the user.
39
Framed-AppleTalk-Zone
Indicates the AppleTalk Default Zone to be used for this user.
40
Acct-Status-Type
(Accounting) Indicates whether this Accounting-Request marks the beginning of the user service (start) or the end (stop).
41
Acct-Delay-Time
(Accounting) Indicates how many seconds the client has been trying to send a particular record.
42
Acct-Input-Octets
(Accounting) Indicates how many octets have been received from the port over the course of this service being provided.
43
Acct-Output-Octets
(Accounting) Indicates how many octets have been sent to the port in the course of delivering this service.
44
Acct-Session-Id
(Accounting) A unique accounting identifier that makes it easy to match start and stop records in a log file. Acct-Session ID numbers restart at 1 each time the router is power cycled or the software is reloaded. To send this attribute in access-request packets, use the radius-server attribute 44 include-in-access-req command in global configuration mode.
45
Acct-Authentic
(Accounting) Indicates how the user was authenticated, whether by RADIUS, the network access server itself, or another remote authentication protocol. This attribute is set to "radius" for users authenticated by RADIUS; "remote" for TACACS+ and Kerberos; or "local" for local, enable, line, and if-needed methods. For all other methods, the attribute is omitted.
46
Acct-Session-Time
(Accounting) Indicates how long (in seconds) the user has received service.
47
Acct-Input-Packets
(Accounting) Indicates how many packets have been received from the port over the course of this service being provided to a framed user.
48
Acct-Output-Packets
(Accounting) Indicates how many packets have been sent to the port in the course of delivering this service to a framed user.
49
Acct-Terminate-Cause
(Accounting) Reports details on why the connection was terminated. Termination causes are indicated by a numeric value as follows:
1.
User request
2.
Lost carrier
3.
Lost service
4.
Idle timeout
5.
Session timeout
6.
Admin reset
7.
Admin reboot
8.
Port error
9.
NAS error
10.
NAS request
11.
NAS reboot
12.
Port unneeded
13.
Port pre-empted
14.
Port suspended
15.
Service unavailable
16.
Callback
17.
User error
18.
Host request
Note
For attribute 49, Cisco IOS supports values 1 to 6, 9, 12, and 15 to 18.
50
Acct-Multi-Session-Id
(Accounting) A unique accounting identifier used to link multiple related sessions in a log file.
Each linked session in a multilink session has a unique Acct-Session-Id value, but shares the same Acct-Multi-Session-Id.
51
Acct-Link-Count
(Accounting) Indicates the number of links known in a given multilink session at the time an accounting record is generated. The network access server can include this attribute in any accounting request that might have multiple links.
52
Acct-Input-Gigawords
Indicates how many times the Acct-Input-Octets counter has wrapped around 2^32 over the course of the provided service.
53
Acct-Output-Gigawords
Indicates how many times the Acct-Output-Octets counter has wrapped around 2^32 while delivering service.
55
Event-Timestamp
Records the time that the event occurred on the NAS; the timestamp sent in attribute 55 is in seconds since January 1, 1970 00:00 UTC. To send RADIUS attribute 55 in accounting packets, use the radius-server attribute 55 include-in-acct-req command.
Note
Before the Event-Timestamp attribute can be sent in accounting packets, you must configure the clock on the router. (For information on setting the clock on your router, refer to section "Performing Basic System Management" in the chapter "System Management" of the Cisco IOS Configuration Fundamentals Configuration Guide.)
To avoid configuring the clock on the router every time the router is reloaded, you can enable the clock calendar-valid command. (For information on this command, refer to the chapter "Basic System Management Commands" in the Cisco IOS Configuration Fundamentals Command Reference.60
CHAP-Challenge
Contains the Challenge Handshake Authentication Protocol challenge sent by the network access server to a PPP CHAP user.
61
NAS-Port-Type
Indicates the type of physical port the network access server is using to authenticate the user. Physical ports are indicated by a numeric value as follows:
•
0: Asynchronous
•
1: Synchronous
•
2: ISDN-Synchronous
•
3: ISDN-Asynchronous (V.120)
•
4: ISDN-Asynchronous (V.110)
•
5: Virtual
62
Port-Limit
Sets the maximum number of ports provided to the user by the NAS.
63
Login-LAT-Port
Defines the port with which the user is to be connected by LAT.
64
Tunnel-Type1
Indicates the tunneling protocol(s) used. Cisco IOS software supports two possible values for this attribute: L2TP and L2F. If this attribute is not set, L2F is used as a default.
65
Tunnel-Medium-Type1
Indicates the transport medium type to use to create a tunnel. This attribute has only one available value for this release: IP. If no value is set for this attribute, IP is used as the default.
66
Tunnel-Client-Endpoint
Contains the address of the initiator end of the tunnel. It may be included in both Access-Request and Access-Accept packets to indicate the address from which a new tunnel is to be initiated. If the Tunnel-Client-Endpoint attribute is included in an Access-Request packet, the RADIUS server should take the value as a hint; the server is not obligated to honor the hint, however. This attribute should be included in Accounting-Request packets that contain Acct-Status-Type attributes with values of either Start or Stop, in which case it indicates the address from which the tunnel was initiated. This attribute, along with the Tunnel-Server-Endpoint and Acct-Tunnel-Connection-ID attributes, may be used to provide a globally unique means to identify a tunnel for accounting and auditing purposes.
An enhancement has been added for the network access server to accept a value of 127.0.0.X for this attribute such that:
127.0.0.0 would indicate that loopback0 IP address is to be used
127.0.0.1 would indicate that loopback1 IP address is to be used
...
127.0.0.X would indicate that loopbackX IP address is to be usedfor the actual tunnel client endpoint IP address. This enhancement adds scalability across multiple network access servers.
67
Tunnel-Server-Endpoint1
Indicates the address of the server end of the tunnel. The format of this attribute varies depending on the value of Tunnel-Medium-Type. Because this release only supports IP as a tunnel medium type, the IP address or the host name of LNS is valid for this attribute.
68
Acct-Tunnel-Connection-ID
Indicates the identifier assigned to the tunnel session. This attribute should be included in Accounting-Request packets that contain an Acct-Status-Type attribute having the value Start, Stop, or any of the values described above. This attribute, along with the Tunnel-Client-Endpoint and Tunnel-Server-Endpoint attributes, may be used to provide a means to uniquely identify a tunnel session for auditing purposes.
69
Tunnel-Password1
Defines the password to be used to authenticate to a remote server. This attribute is converted into different AAA attributes based on the value of Tunnel-Type: AAA_ATTR_l2tp_tunnel_pw (L2TP), AAA_ATTR_nas_password (L2F), and AAA_ATTR_gw_password (L2F).
By default, all passwords received are encrypted, which can cause authorization failures when a NAS attempts to decrypt a nonencrypted password. To enable attribute 69 to receive nonencrypted passwords, use the radius-server attribute 69 clear global configuration command.
70
ARAP-Password
Identifies an Access-Request packet containing a Framed-Protocol of ARAP.
71
ARAP-Features
Includes password information that the NAS should send to the user in an ARAP "feature flags" packet.
72
ARAP-Zone-Access
Indicates how the ARAP zone list for the user should be used.
73
ARAP-Security
Identifies the ARAP Security Module to be used in an Access-Challenge packet.
74
ARAP-Security-Data
Contains the actual security module challenge or response. It can be found in Access-Challenge and Access-Request packets.
75
Password-Retry
Indicates how many times a user may attempt authentication before being disconnected.
76
Prompt
Indicates to the NAS whether it should echo the user's response as it is entered or not echo it. (0=no echo, 1=echo)
77
Connect-Info
Provides additional call information for modem calls. This attribute is generated in start and stop accounting records.
78
Configuration-Token
Indicates a type of user profile to be used. This attribute should be used in large distributed authentication networks based on proxy. It is sent from a RADIUS Proxy Server to a RADIUS Proxy Client in an Access-Accept; it should not be sent to a NAS.
79
EAP-Message
Encapsulates Extended Access Protocol (EAP) packets that allow the NAS to authenticate dial-in users via EAP without having to understand the EAP protocol.
80
Message-Authenticator
Prevents spoofing Access-Requests using CHAP, ARAP, or EAP authentication methods.
81
Tunnel-Private-Group-ID
Indicates the group ID for a particular tunneled session.
82
Tunnel-Assignment-ID1
Indicates to the tunnel initiator the particular tunnel to which a session is assigned.
83
Tunnel-Preference
Indicates the relative preference assigned to each tunnel. This attribute should be included if more than one set of tunneling attributes is returned by the RADIUS server to the tunnel initiator.
84
ARAP-Challenge-Response
Contains the response to the challenge of the dial-in client.
85
Acct-Interim-Interval
Indicates the number of seconds between each interim update in seconds for this specific session. This value can only appear in the Access-Accept message.
86
Acct-Tunnel-Packets-Lost
Indicates the number of packets lost on a given link. This attribute should be included in Accounting-Request packets that contain an Acct-Status-Type attribute having the value Tunnel-Link-Stop.
87
NAS-Port-ID
Contains a text string which identifies the port of the NAS that is authenticating the user.
88
Framed-Pool
Contains the name of an assigned address pool that should be used to assign an address for the user. If a NAS does not support multiple address pools, the NAS should ignore this attribute.
90
Tunnel-Client-Auth-ID
Specifies the name used by the tunnel initiator (also known as the NAS) when authenticating tunnel setup with the tunnel terminator. Supports L2F and L2TP protocols.
91
Tunnel-Server-Auth-ID
Specifies the name used by the tunnel terminator (also known as the Home Gateway) when authenticating tunnel setup with the tunnel initiator. Supports L2F and L2TP protocols.
200
IETF-Token-Immediate
Determines how RADIUS treats passwords received from login-users when their file entry specifies a hand-held security card server.
The value for this attribute is indicated by a numeric value as follows:
•
0: No, meaning that the password is ignored.
•
1: Yes, meaning that the password is used for authentication.
1 This RADIUS attribute complies with the following two IETF documents: RFC 2868, RADIUS Attributes for Tunnel Protocol Support and RFC 2867, RADIUS Accounting Modifications for Tunnel Protocol Support.
Vendor-Proprietary RADIUS Attributes
Although an Internet Engineering Task Force (IETF) draft standard for RADIUS specifies a method for communicating vendor-proprietary information between the network access server and the RADIUS server, some vendors have extended the RADIUS attribute set for specific applications.
This section contains the following sections:
•
Supported Vendor-Proprietary RADIUS Attributes
•
Comprehensive List of Vendor-Proprietary RADIUS Attribute Descriptions
Supported Vendor-Proprietary RADIUS Attributes
Table 32 lists Cisco-supported vendor-proprietary RADIUS attributes and the Cisco IOS release in which they are implemented. In cases where the attribute has a security server-specific format, the format is specified. Refer to Table 33 for a list of descriptions.

Note
Attributes implemented in special (AA) or early development (T) releases will be added to the next mainline image.
Comprehensive List of Vendor-Proprietary RADIUS Attribute Descriptions
Table 33 lists and describes the known vendor-proprietary RADIUS attributes.
Table 33 Vendor-Proprietary RADIUS Attributes
17
Change-Password
Specifies a request to change the password of a user.
21
Password-Expiration
Specifies an expiration date for a user's password in the user's file entry.
68
Tunnel-ID
(Ascend 5) Specifies the string assigned by RADIUS for each session using CLID or DNIS tunneling. When accounting is implemented, this value is used for accounting.
108
My-Endpoint-Disc-Alias
(Ascend 5) No description available.
109
My-Name-Alias
(Ascend 5) No description available.
110
Remote-FW
(Ascend 5) No description available.
111
Multicast-GLeave-Delay
(Ascend 5) No description available.
112
CBCP-Enable
(Ascend 5) No description available.
113
CBCP-Mode
(Ascend 5) No description available.
114
CBCP-Delay
(Ascend 5) No description available.
115
CBCP-Trunk-Group
(Ascend 5) No description available.
116
Appletalk-Route
(Ascend 5) No description available.
117
Appletalk-Peer-Mode
(Ascend 5) No description available.
118
Route-Appletalk
(Ascend 5) No description available.
119
FCP-Parameter
(Ascend 5) No description available.
120
Modem-PortNo
(Ascend 5) No description available.
121
Modem-SlotNo
(Ascend 5) No description available.
122
Modem-ShelfNo
(Ascend 5) No description available.
123
Call-Attempt-Limit
(Ascend 5) No description available.
124
Call-Block-Duration
(Ascend 5) No description available.
125
Maximum-Call-Duration
(Ascend 5) No description available.
126
Router-Preference
(Ascend 5) No description available.
127
Tunneling-Protocol
(Ascend 5) No description available.
128
Shared-Profile-Enable
(Ascend 5) No description available.
129
Primary-Home-Agent
(Ascend 5) No description available.
130
Secondary-Home-Agent
(Ascend 5) No description available.
131
Dialout-Allowed
(Ascend 5) No description available.
133
BACP-Enable
(Ascend 5) No description available.
134
DHCP-Maximum-Leases
(Ascend 5) No description available.
135
Primary-DNS-Server
Identifies a primary DNS server that can be requested by Microsoft PPP clients from the network access server during IPCP negotiation.
136
Secondary-DNS-Server
Identifies a secondary DNS server that can be requested by Microsoft PPP clients from the network access server during IPCP negotiation.
137
Client-Assign-DNS
No description available.
138
User-Acct-Type
No description available.
139
User-Acct-Host
No description available.
140
User-Acct-Port
No description available.
141
User-Acct-Key
No description available.
142
User-Acct-Base
No description available.
143
User-Acct-Time
No description available.
144
Assign-IP-Client
No description available.
145
Assign-IP-Server
No description available.
146
Assign-IP-Global-Pool
No description available.
147
DHCP-Reply
No description available.
148
DHCP-Pool-Number
No description available.
149
Expect-Callback
No description available.
150
Event-Type
No description available.
151
Session-Svr-Key
No description available.
152
Multicast-Rate-Limit
No description available.
153
IF-Netmask
No description available.
154
Remote-Addr
No description available.
155
Multicast-Client
No description available.
156
FR-Circuit-Name
No description available.
157
FR-LinkUp
No description available.
158
FR-Nailed-Grp
No description available.
159
FR-Type
No description available.
160
FR-Link-Mgt
No description available.
161
FR-N391
No description available.
162
FR-DCE-N392
No description available.
163
FR-DTE-N392
No description available.
164
FR-DCE-N393
No description available.
165
FR-DTE-N393
No description available.
166
FR-T391
No description available.
167
FR-T392
No description available.
168
Bridge-Address
No description available.
169
TS-Idle-Limit
No description available.
170
TS-Idle-Mode
No description available.
171
DBA-Monitor
No description available.
172
Base-Channel-Count
No description available.
173
Minimum-Channels
No description available.
174
IPX-Route
No description available.
175
FT1-Caller
No description available.
176
Backup
No description available.
177
Call-Type
No description available.
178
Group
No description available.
179
FR-DLCI
No description available.
180
FR-Profile-Name
No description available.
181
Ara-PW
No description available.
182
IPX-Node-Addr
No description available.
183
Home-Agent-IP-Addr
Indicates the home agent's IP address (in dotted decimal format) when using Ascend Tunnel Management Protocol (ATMP).
184
Home-Agent-Password
With ATMP, specifies the password that the foreign agent uses to authenticate itself.
185
Home-Network-Name
With ATMP, indicates the name of the connection profile to which the home agent sends all packets.
186
Home-Agent-UDP-Port
Indicates the UDP port number the foreign agent uses to send ATMP messages to the home agent.
187
Multilink-ID
Reports the identification number of the multilink bundle when the session closes. This attribute applies to sessions that are part of a multilink bundle. The Multilink-ID attribute is sent in authentication-response packets.
188
Num-In-Multilink
Reports the number of sessions remaining in a multilink bundle when the session reported in an accounting-stop packet closes. This attribute applies to sessions that are part of a multilink bundle. The Num-In-Multilink attribute is sent in authentication-response packets and in some accounting-request packets.
189
First-Dest
Records the destination IP address of the first packet received after authentication.
190
Pre-Input-Octets
Records the number of input octets before authentication. The Pre-Input-Octets attribute is sent in accounting-stop records.
191
Pre-Output-Octets
Records the number of output octets before authentication. The Pre-Output-Octets attribute is sent in accounting-stop records.
192
Pre-Input-Packets
Records the number of input packets before authentication. The Pre-Input-Packets attribute is sent in accounting-stop records.
193
Pre-Output-Packets
Records the number of output packets before authentication. The Pre-Output-Packets attribute is sent in accounting-stop records.
194
Maximum-Time
Specifies the maximum length of time (in seconds) allowed for any session. After the session reaches the time limit, its connection is dropped.
195
Disconnect-Cause
Specifies the reason a connection was taken offline. The Disconnect-Cause attribute is sent in accounting-stop records. This attribute also causes stop records to be generated without first generating start records if disconnection occurs before authentication is performed. For more information, refer to Table 36 for a list of Disconnect-Cause values and their meanings.
196
Connect-Progress
Indicates the connection state before the connection is disconnected.
197
Data-Rate
Specifies the average number of bits per second over the course of the connection's lifetime. The Data-Rate attribute is sent in accounting-stop records.
198
PreSession-Time
Specifies the length of time, in seconds, from when a call first connects to when it completes authentication. The PreSession-Time attribute is sent in accounting-stop records.
199
Token-Idle
Indicates the maximum amount of time (in minutes) a cached token can remain alive between authentications.
201
Require-Auth
Defines whether additional authentication is required for class that has been CLID authenticated.
202
Number-Sessions
Specifies the number of active sessions (per class) reported to the RADIUS accounting server.
203
Authen-Alias
Defines the RADIUS server's login name during PPP authentication.
204
Token-Expiry
Defines the lifetime of a cached token.
205
Menu-Selector
Defines a string to be used to cue a user to input data.
206
Menu-Item
Specifies a single menu-item for a user-profile. Up to 20 menu items can be assigned per profile.
207
PW-Warntime
(Ascend 5) No description available.
208
PW-Lifetime
Enables you to specify on a per-user basis the number of days that a password is valid.
209
IP-Direct
When you include this attribute in a user's file entry, a framed route is installed to the routing and bridging tables.
Note
Packet routing is dependent upon the entire table, not just this newly installed entry. The inclusion of this attribute does not guarantee that all packets should be sent to the specified IP address; thus, this attribute is not fully supported.
These attribute limitations occur because the Cisco router cannot bypass all internal routing and bridging tables and send packets to a specified IP address.210
PPP-VJ-Slot-Comp
Instructs the Cisco router not to use slot compression when sending VJ-compressed packets over a PPP link.
211
PPP-VJ-1172
Instructs PPP to use the 0x0037 value for VJ compression.
212
PPP-Async-Map
Gives the Cisco router the asynchronous control character map for the PPP session. The specified control characters are passed through the PPP link as data and used by applications running over the link.
213
Third-Prompt
Defines a third prompt (after username and password) for additional user input.
214
Send-Secret
Enables an encrypted password to be used in place of a regular password in outdial profiles.
215
Receive-Secret
Enables an encrypted password to be verified by the RADIUS server.
216
IPX-Peer-Mode
(Ascend 5) No description available.
217
IP-Pool-Definition
Defines a pool of addresses using the following format: X a.b.c Z; where X is the pool index number, a.b.c is the pool's starting IP address, and Z is the number of IP addresses in the pool. For example, 3 10.0.0.1 5 allocates 10.0.0.1 through 10.0.0.5 for dynamic assignment.
218
Assign-IP-Pool
Tells the router to assign the user and IP address from the IP pool.
219
FR-Direct
Defines whether the connection profile operates in Frame Relay redirect mode.
220
FR-Direct-Profile
Defines the name of the Frame Relay profile carrying this connection to the Frame Relay switch.
221
FR-Direct-DLCI
Indicates the DLCI carrying this connection to the Frame Relay switch.
222
Handle-IPX
Indicates how NCP watchdog requests will be handled.
223
Netware-Timeout
Defines, in minutes, how long the RADIUS server responds to NCP watchdog packets.
224
IPX-Alias
Allows you to define an alias for IPX routers requiring numbered interfaces.
225
Metric
No description available.
226
PRI-Number-Type
No description available.
227
Dial-Number
Defines the number to dial.
228
Route-IP
Indicates whether IP routing is allowed for the user's file entry.
229
Route-IPX
Allows you to enable IPX routing.
230
Bridge
No description available.
231
Send-Auth
Defines the protocol to use (PAP or CHAP) for username-password authentication following CLID authentication.
232
Send-Passwd
Enables the RADIUS server to specify the password that is sent to the remote end of a connection on outgoing calls.
233
Link-Compression
Defines whether to turn on or turn off "stac" compression over a PPP link.
Link compression is defined as a numeric value as follows:
•
0: None
•
1: Stac
•
2: Stac-Draft-9
•
3: MS-Stac
234
Target-Util
Specifies the load-threshold percentage value for bringing up an additional channel when PPP multilink is defined.
235
Maximum-Channels
Specifies allowed/allocatable maximum number of channels.
236
Inc-Channel-Count
No description available.
237
Dec-Channel-Count
No description available.
238
Seconds-of-History
No description available.
239
History-Weigh-Type
No description available.
240
Add-Seconds
No description available.
241
Remove-Seconds
No description available.
242
Data-Filter
Defines per-user IP data filters. These filters are retrieved only when a call is placed using a RADIUS outgoing profile or answered using a RADIUS incoming profile. Filter entries are applied on a first-match basis; therefore, the order in which filter entries are entered is important.
243
Call-Filter
Defines per-user IP data filters. On a Cisco router, this attribute is identical to the Data-Filter attribute.
244
Idle-Limit
Specifies the maximum time (in seconds) that any session can be idle. When the session reaches the idle time limit, its connection is dropped.
245
Preempt-Limit
No description available.
246
Callback
Allows you to enable or disable callback.
247
Data-Svc
No description available.
248
Force-56
Determines whether the network access server uses only the 56 K portion of a channel, even when all 64 K appear to be available.
249
Billing Number
No description available.
250
Call-By-Call
No description available.
251
Transit-Number
No description available.
252
Host-Info
No description available.
253
PPP-Address
Indicates the IP address reported to the calling unit during PPP IPCP negotiations.
254
MPP-Idle-Percent
No description available.
255
Xmit-Rate
(Ascend 5) No description available.
For more information on vendor-proprietary RADIUS attributes, refer to the section "Configuring Router for Vendor-Proprietary RADIUS Server Communication" in the chapter "Configuring RADIUS."
RADIUS Vendor-Specific Attributes (VSA)
The Internet Engineering Task Force (IETF) draft standard specifies a method for communicating vendor-specific information between the network access server and the RADIUS server by using the vendor-specific attribute (attribute 26). Attribute 26 encapsulates vendor specific attributes, thereby, allowing vendors to support their own extended attributes otherwise not suitable for general use.
The Cisco RADIUS implementation supports one vendor-specific option using the format recommended in the specification. Cisco's vendor-ID is 9, and the supported option has vendor-type 1, which is named "cisco-avpair." The value is a string of the following format:
protocol : attribute sep value *"Protocol" is a value of the Cisco "protocol" attribute for a particular type of authorization; protocols that can be used include IP, IPX, VPDN, VOIP, SHELL, RSVP, SIP, AIRNET, OUTBOUND. "Attribute" and "value" are an appropriate attribute-value (AV) pair defined in the Cisco TACACS+ specification, and "sep" is "=" for mandatory attributes and "*" for optional attributes. This allows the full set of features available for TACACS+ authorization to also be used for RADIUS.
For example, the following AV pair causes Cisco's "multiple named ip address pools" feature to be activated during IP authorization (during PPP's IPCP address assignment):
cisco-avpair= "ip:addr-pool=first"If you add an "*" immediately after the value, the AV pair "ip:addr-pool=first" becomes optional. Note that any AV pair can be made optional.
cisco-avpair= "ip:addr-pool=first*"The following example shows how to cause a user logging in from a network access server to have immediate access to EXEC commands:
cisco-avpair= "shell:priv-lvl=15"
Attribute 26 contains the following three elements:
•
Type
•
Length
•
String (also known as data)
–
Vendor-Id
–
Vendor-Type
–
Vendor-Length
–
Vendor-Data
Figure 44 shows the packet format for a VSA encapsulated "behind" attribute 26.
Figure 44 VSA Encapsulated Behind Attribute 26
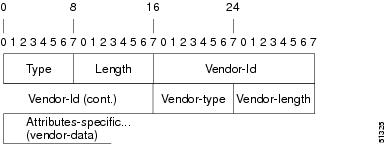

Note
It is up to the vendor to specify the format of their VSA. The Attribute-Specific field (also known as Vendor-Data) is dependent on the vendor's definition of that attribute.
Table 34 describes significant fields listed in Table 35. Table 35 lists supported vendor-specific RADIUS attributes (IETF attribute 26).
For more information on configuring your NAS to recognize and use VSAs, refer to the section "Configuring Router to Use Vendor-Specific RADIUS Attributes" of the chapter "Configuring RADIUS."
RADIUS Disconnect-Cause Attribute Values
Disconnect-cause attribute values specify the reason a connection was taken offline. The attribute values are sent in Accounting request packets. These values are sent at the end of a session, even if the session fails to be authenticated. If the session is not authenticated, the attribute can cause stop records to be generated without first generating start records.
Table 36 lists the cause codes, values, and descriptions for the Disconnect-Cause (195) attribute.

Note
The Disconnect-Cause is incremented by 1000 when it is used in RADIUS AVPairs; for example, disc-cause 4 becomes 1004.
For Q.850 cause codes and descriptions, see the section "Internal Cause Codes for SIP and H.323" in the chapter "Cause Codes and Debug Values" of the Cisco IOS Voice Troubleshooting and Monitoring.
 Feedback
Feedback