L2TP Security
Available Languages
Table Of Contents
Related Features and Technologies
Supported Standards, MIBs, and RFCs
Configuring NAS-Initiated VPDN Tunneling with L2TP Security
Configuring Client-Initiated VPDN Tunneling with L2TP Security
Verifying Session Establishment
Configuring IPSec Protection of LAC-Initiated L2TP Tunnels Example
Configuring IPSec Protection of Client-Initiated L2TP Tunnels Example
L2TP Security
Feature History for L2TP Security
Finding Support Information for Platforms and Cisco IOS Software Images
Use Cisco Feature Navigator to find information about platform support and Cisco IOS software image support. Access Cisco Feature Navigator at http://www.cisco.com/go/fn. You must have an account on Cisco.com. If you do not have an account or have forgotten your username or password, click Cancel at the login dialog box and follow the instructions that appear.
This document describes the L2TP Security feature in Cisco IOS Release 12.2(11)T. It includes the following sections:
•
Supported Standards, MIBs, and RFCs
Feature Overview
The L2TP Security feature provides enhanced security for tunneled PPP frames between the Layer 2 Transport Protocol (L2TP) access concentrator (LAC) and the L2TP network server (LNS). Previous releases of the Cisco IOS software provided only a one-time, optional mutual authentication during tunnel setup with no authentication of subsequent data packets or control messages. In situations where the L2TP is used to tunnel PPP sessions over an untrusted infrastructure such as the Internet, the security attributes of L2TP and PPP are inadequate. PPP provides no protection of the L2TP tunnel, and current PPP encryption protocols provide inadequate key management and no authentication or integrity mechanisms. The L2TP Security feature allows the robust security features of IP Security (IPSec) to protect the L2TP tunnel and the PPP sessions within the tunnel. In addition, the L2TP Security feature provides built-in keepalives and standardized interfaces for user authentication and accounting to authentication, authorization, and accounting (AAA) servers.
The deployment of Microsoft Windows 2000 demands the integration of IPSec with L2TP because this is the default virtual private dialup network (VPDN) networking scenario. This integration of protocols is also used for LAN-to-LAN VPDN connections in Microsoft Windows 2000. The L2TP Security feature provides integration of IPSec with L2TP in a solution that is scalable to large networks with minimal configuration.
Benefits
The enhanced security provided by the L2TP Security feature increases the integrity and confidentiality of tunneled PPP sessions within a standardized, well deployed Layer 2 tunneling solution. The robust security features of IPSec and Internet Key Exchange (IKE) include confidentiality, integrity checking, replay protection, authentication and key management. Traditional routing protocols such as Routing Information Protocol (RIP), Open Shortest Path First (OSPF), and Interior Gateway Routing Protocol (IGRP) will run transparently because a real PPP interface is associated with the secure tunnel. Additional benefits include built in keepalives and standardized interfaces for user authentication and accounting to AAA servers, interface statistics, standardized MIBs, and multiprotocol support.
Related Features and Technologies
•
L2TP Large-Scale Dial-Out
•
Timer and Retry Enhancements for L2TP and L2F
•
VPDN Group Session Limiting
Related Documents
•
Cisco IOS Dial Technologies Configuration Guide, Release 12.2
•
Cisco IOS Dial Technologies Command Reference, Release 12.2
•
Cisco IOS Security Configuration Guide, Release 12.2
•
Cisco IOS Security Command Reference, Release 12.2
Supported Platforms
•
Cisco 806
•
Cisco 1600 series
•
Cisco 1700 series
•
Cisco 2691
•
Cisco 3620
•
Cisco 3640
•
Cisco 3660
•
Cisco 3700 series
•
Cisco 7100 series
•
Cisco 7200 series
•
Cisco 7500 series
•
Cisco AS5300
•
Cisco AS5400
•
Cisco AS5800
•
Cisco IGX 8400 URM
Determining Platform Support Through Cisco Feature Navigator
Cisco IOS software is packaged in feature sets that are supported on specific platforms. To get updated information regarding platform support for this feature, access Cisco Feature Navigator. Cisco Feature Navigator dynamically updates the list of supported platforms as new platform support is added for the feature.
Cisco Feature Navigator is a web-based tool that enables you to quickly determine which Cisco IOS software images support a specific set of features and which features are supported in a specific Cisco IOS image. You can search by feature or release. Under the release section, you can compare releases side by side to display both the features unique to each software release and the features in common.
To access Cisco Feature Navigator, you must have an account on Cisco.com. If you have forgotten or lost your account information, send a blank e-mail to cco-locksmith@cisco.com. An automatic check will verify that your e-mail address is registered with Cisco.com. If the check is successful, account details with a new random password will be e-mailed to you. Qualified users can establish an account on Cisco.com by following the directions found at this URL:
Cisco Feature Navigator is updated regularly when major Cisco IOS software releases and technology releases occur. For the most current information, go to the Cisco Feature Navigator home page at the following URL:
Availability of Cisco IOS Software Images
Platform support for particular Cisco IOS software releases is dependent on the availability of the software images for those platforms. Software images for some platforms may be deferred, delayed, or changed without prior notice. For updated information about platform support and availability of software images for each Cisco IOS software release, refer to the online release notes or, if supported, Cisco Feature Navigator.
Supported Standards, MIBs, and RFCs
Standards
No new or modified standards are supported by this feature.
MIBs
No new or modified MIBs are supported by this feature.
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL:
http://tools.cisco.com/ITDIT/MIBS/servlet/index
If Cisco MIB Locator does not support the MIB information that you need, you can also obtain a list of supported MIBs and download MIBs from the Cisco MIBs page at the following URL:
http://www.cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml
To access Cisco MIB Locator, you must have an account on Cisco.com. If you have forgotten or lost your account information, send a blank e-mail to cco-locksmith@cisco.com. An automatic check will verify that your e-mail address is registered with Cisco.com. If the check is successful, account details with a new random password will be e-mailed to you. Qualified users can establish an account on Cisco.com by following the directions found at this URL:
RFCs
•
RFC 1661, The Point-to-Point Protocol (PPP)
•
RFC 2401, Security Architecture for the Internet Protocol (IPSec)
•
RFC 2409, The Internet Key Exchange (IKE)
•
RFC 2637, Point to Point Tunneling Protocol (PPTP)
•
RFC 2661, Layer Two Transport Protocol (L2TP)
•
RFC 3193, Securing L2TP Using IPSec
Prerequisites
The interface between the LAC and LNS must be configured for IP and must support IPSec.
To use the L2TP Security feature for client-initiated dial-in using compulsory tunneling, the interface between the client and the LAC must support PPP.
To use the L2TP Security feature for client-initiated dail-in using voluntary tunneling, the client software must support L2TP and IPSec. This is the default VPDN networking scenario in Microsoft Windows 2000.
Configuration Tasks
See the following sections for configuration tasks for the L2TP Security feature. Each task in the list is identified as either required or optional:
•
Configuring NAS-Initiated VPDN Tunneling with L2TP Security (optional)
•
Configuring Client-Initiated VPDN Tunneling with L2TP Security (optional)
Configuring NAS-Initiated VPDN Tunneling with L2TP Security
In the NAS-initiated (compulsory) tunneling scenario depicted in Figure 1, the client connects to the LAC through a media that supports PPP, such as a dialup modem, DSL, ISDN, or a cable modem. If the connection from the client to the LAC is considered secure such as a modem, ISDN or a DSL connection the client may choose not to provide additional security. The PPP session is securely tunneled from the LAC to the LNS without any required knowledge or interaction by the client.
Figure 1 NAS-Initiated Tunneling
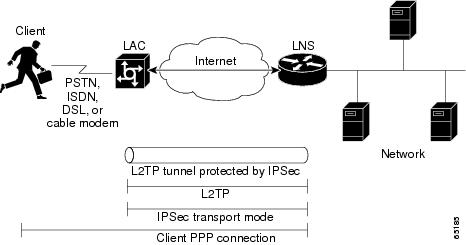
To configure the L2TP Security feature for compulsory tunneling, perform the tasks described in the following sections to configure the client, LAC, and LNS:
•
Configuring the Client (required)
•
Configuring the LAC (required)
•
Configuring the LNS (required)
Configuring the Client
To use the L2TP Security feature for NAS-initiated dial-in using compulsory tunneling, configure the interface between the client and the LAC for PPP. For more information on configuring PPP on the client, refer to the Cisco IOS Dial Technologies Configuration Guide, Release 12.2.
Configuring the LAC
To configure the LAC to use the L2TP Security feature, perform the required tasks described in the following sections:
•
Configuring the Interface Between the LAC and the LNS (required)
•
Configuring IPSec Protection of a L2TP Tunnel at the LAC (required)
•
Creating the Security Profile at the LAC (required)
Configuring the Interface Between the LAC and the LNS
To configure the interface between the LAC and the LNS, use the following commands beginning in global configuration mode:
Configuring IPSec Protection of a L2TP Tunnel at the LAC
To configure a VPDN group to tunnel PPP sessions with IPSec protection, use the following commands beginning in global configuration mode:
Creating the Security Profile at the LAC
To create an IKE policy and a crypto profile configuration associated with the VPDN group, you must first configure phase 1 ISAKMP policy and an IPSec transform set. For more information on configuring phase 1 ISAKMP policies and IPSec transform, sets refer to the Cisco IOS Security Configuration Guide, Release 12.2. Once the phase 1 ISAKMP policy and an IPSec transform set have been configured, use the following commands beginning in global configuration mode:
Configuring the LNS
To configure the LNS to use the L2TP Security feature, perform the required tasks described in the following sections:
•
Configuring the Interface Between the LNS and the LAC (required)
•
Configuring IPSec Protection of an L2TP Tunnel at the LNS (required)
•
Creating the Security Profile at the LNS (required)
Configuring the Interface Between the LNS and the LAC
To configure the interface between the LNS and the LAC, use the following commands in global configuration mode:
Configuring IPSec Protection of an L2TP Tunnel at the LNS
To configure a VPDN group to tunnel PPP sessions with IPSec protection, use the following commands beginning in global configuration mode:
Creating the Security Profile at the LNS
To create an IKE policy and a crypto profile configuration associated with the VPDN group, you must first configure phase 1 ISAKMP policy and an IPSec transform set. For more information on configuring phase 1 ISAKMP policies and IPSec transform, sets refer to the Cisco IOS Security Configuration Guide, Release 12.2. Once the phase 1 ISAKMP policy and an IPSec transform set have been configured, use the following commands beginning in global configuration mode:
Configuring Client-Initiated VPDN Tunneling with L2TP Security
In the client-initiated (voluntary) tunneling scenario depicted in Figure 2, the client initiates an L2TP tunnel to the LNS without the intermediate NAS participating in tunnel negotiation or establishment. The client must manage the software that initiates the tunnel. Microsoft Windows 2000 supports this VPDN scenario. In this scenario, extended services processor (ESP) with authentication must always be used.
Figure 2 Client-Initiated Tunneling

To configure the L2TP Security feature for voluntary tunneling, you must configure the LNS to interface with the LAC by performing the tasks described in the "Configuring the Interface Between the LNS and the LAC"section.
In addition, perform the tasks in the following sections, which are unique to configuring the NAS for client-initiated dial-in using voluntary tunneling:
•
Configuring IPSec Protection of a VPDN Session at the LNS (required)
•
Creating the Security Profile at the LNS (required)
Configuring IPSec Protection of a VPDN Session at the LNS
To configure a VPDN group to tunnel PPP sessions with IPSec protection, use the following commands beginning in global configuration mode:
Creating the Security Profile at the LNS
To create an IKE policy and a crypto profile configuration associated with the VPDN group, use the following commands beginning in global configuration mode:
Verifying Session Establishment
To verify the establishment and security of an L2TP tunnel, perform the following steps:
Step 1
Enable the debug crypto socket and debug vpdn l2x-events commands. The crypto socket messages command allows you to view socket messages and verify that the socket is created and moved to the active state. The vpdn l2x-events command tracks incoming and outgoing L2TP packets.
router# debug crypto socketrouter# debug vpdn l2x-events*Mar 1 00:56:46.959:CRYPTO_SS(L2X Security):Passive open, socket info:local 10.0.0.13/1701, remote 10.0.0.12/1701, prot 17, ifc Fa0/0*Mar 1 00:56:47.291:L2TP:I SCCRQ from ebooth02 tnl 5107*Mar 1 00:56:47.295:L2X:Requested security for socket, UDP socket info:local 10.0.0.13(1701), remote 10.0.0.12(1701)*Mar 1 00:56:47.295:Tnl 13582 L2TP:Got a challenge in SCCRQ, ebooth02*Mar 1 00:56:47.295:Tnl 13582 L2TP:New tunnel created for remote ebooth02, address 10.0.0.12*Mar 1 00:56:47.295:Tnl 13582 L2TP:O SCCRP to ebooth02 tnlid 5107*Mar 1 00:56:47.295:Tnl 13582 L2TP:Control channel retransmit delay set to 1 seconds*Mar 1 00:56:47.299:Tnl 13582 L2TP:Tunnel state change from idle to wait-ctl-reply*Mar 1 00:56:47.299:CRYPTO_SS(L2X Security):Completed binding of application to socketStep 2
Use the show crypto map tag crypto-map-name command to verify that a crypto map was dynamically created for the L2TP tunnel.
router# show crypto map tag l2tpsecCrypto Map "l2tpsec" 10 ipsec-isakmpNo matching address list set.Current peer:0.0.0.0Security association lifetime:4608000 kilobytes/3600 secondsPFS (Y/N):NTransform sets={ esp, }Crypto Map "l2tpsec" 20 ipsec-isakmpPeer = 10.0.0.13Extended IP access listaccess-list permit udp host 10.0.0.12 port = 1701 host 10.0.0.13 port = 1701Current peer:10.0.0.13Security association lifetime:4608000 kilobytes/3600 secondsPFS (Y/N):NTransform sets={ esp, }Interfaces using crypto map l2tpsec:FastEthernet0/0Step 3
To verify that packets are being encrypted/decrypted for the secure tunnel, use the show crypto engine connections active command.
router#show crypto engine connections activeID Interface IP-Address State Algorithm Encrypt Decrypt1 FastEthernet0/0 10.0.0.13 set HMAC_SHA+DES_56_CB 0 02000 FastEthernet0/0 10.0.0.13 set HMAC_SHA+DES_56_CB 0 622001 FastEthernet0/0 10.0.0.13 set HMAC_SHA+DES_56_CB 64 0
Configuration Examples
This section provides the following configuration examples:
•
Configuring IPSec Protection of LAC-Initiated L2TP Tunnels Example
•
Configuring IPSec Protection of Client-Initiated L2TP Tunnels Example
Configuring IPSec Protection of LAC-Initiated L2TP Tunnels Example
The following example configures L2TP Security on the client, LAC, and LNS for a compulsory tunneling scenario.
Client Configuration
! PPP configuration on the client.interface Serial1/0ip address negotiatedencapsulation pppclockrate 128000no cdp enableppp chap hostname userSerial10@cisco.comppp chap password ciscoLAC Configuration
! Passwords for the L2TP tunnel authentication.username LAC password 0 ciscousername LNS password 0 cisco!! VPDN configuration to tunnel users with the domain cisco.com! to the LNS. This configuration has l2tp tunnel authentication! enabled.!vpdn enableno vpdn logging!vpdn-group 1request-dialinprotocol l2tpdomain cisco.cominitiate-to ip 10.0.0.13local name LACl2tp security crypto-profile l2tp keep-sal2tp tunnel password cisco!crypto isakmp policy 1authentication pre-sharecrypto isakmp key cisco address 10.0.0.13!crypto ipsec transform-set esp-des-sha-transport esp-des esp-sha-hmacmode transport!! Crypto profile configuration which is bound to the vpdn-group shown above.crypto map l2tpsec 10 ipsec-isakmp profile l2tpset transform-set esp-des-sha-transport!interface FastEthernet0/0ip address 10.0.0.12 255.255.255.0crypto map l2tpsecLNS Configuration
! PPP client username and password needed for CHAP authentication.username userSerial10@cisco.com password 0 cisco!! Passwords for the L2TP tunnel authentication.username LAC password 0 ciscousername LNS password 0 cisco!! Using address pool to assign client an IP address.ip address-pool local!! VPDN configuration.vpdn enable!vpdn-group 1accept-dialinprotocol anyvirtual-template 1terminate-from hostname LAClcp renegotiation on-mismatchl2tp security crypto-profile l2tp keep-sa!crypto isakmp policy 1authentication pre-sharecrypto isakmp key cisco address 10.0.0.12!crypto ipsec transform-set esp-des-sha-transport esp-des esp-sha-hmacmode transport!crypto map l2tpsec 10 ipsec-isakmp profile l2tpset transform-set esp-des-sha-transport!interface FastEthernet0/0ip address 10.0.0.13 255.255.255.0speed 10half-duplexcrypto map l2tpsecConfiguring IPSec Protection of Client-Initiated L2TP Tunnels Example
The following example configures L2TP Security on the LNS for a voluntary tunneling scenario.
LNS Configuration
! PPP client username and password needed for CHAP authentication.username userSerial10@cisco.com password 0 cisco! Passwords for the L2TP tunnel authentication.username LAC password 0 ciscousername LNS password 0 cisco!! Using address pool to assign client an IP address.ip address-pool local!! VPDN configuration.vpdn enable!vpdn-group dial-inaccept-dialinprotocol l2tpvirtual-template 1l2tp security crypto-profile l2tpno l2tp tunnel authenticationip pmtu!crypto ipsec transform-set esp-des-sha-transport esp-des esp-sha-hmacmode transport!crypto map l2tpsec 10 ipsec-isakmp profile l2tpset transform-set esp-des-sha-transportset security-association lifetime seconds 120!interface FastEthernet0/0ip address 10.0.0.13 255.255.255.0speed 10half-duplexcrypto map l2tpsecCommand Reference
This section documents new or modified commands. All other commands used with this feature are documented in the Cisco IOS Release 12.2 command reference publications.
New Commands
Modified Commands
ip pmtu
To enable the discovery of a path maximum transmission unit (MTU) for Layer 2 traffic, use the ip pmtu command in VPDN group configuration mode or pseudowire class configuration mode. To disable path MTU discovery, use the no form of this command.
ip pmtu
no ip pmtu
Syntax Description
This command has no arguments or keywords.
Defaults
Path MTU discovery is disabled.
Command Modes
VPDN group configuration
Pseudowire class configurationCommand History
Usage Guidelines
When issued in VPDN group configuration mode, the ip pmtu command enables any Layer 2 Tunnel Protocol (L2TP) tunnel associated with the specified virtual private dial-up network (VPDN) group to participate in path MTU discovery.
When issued in pseudowire class configuration mode, the ip pmtu command enables any Layer 2 session derived from the specified pseudowire class configuration to participate in path MTU discovery.
Path MTU checks decrease switching performance; therefore this option is disabled by default.
The ip pmtu command enables the processing of Internet Control Message Protocol (ICMP) unreachable messages that indicate fragmentation errors in the IP backbone network carrying the tunneled traffic. The MTU of the Layer 2 session is updated according to the MTU information contained in the ICMP unreachable message.
The ip pmtu command also enables MTU checking for IP packets that are sent into a Layer 2 session with the Don't Fragment (DF) bit set. If an IP packet is larger than the MTU of the tunnel, the packet is dropped and an ICMP unreachable message is sent. If an IP packet is smaller than the MTU of the tunnel, the DF bit in the packet header is reflected from the inner IP header to the tunnel header.
Examples
The following example configures a VPDN group named "dial-in" on an L2TP network server and uses the ip pmtu command to specify that L2TP tunnels will participate in path MTU discovery:
vpdn-group dial-inaccept-dialinprotocol l2tpvirtual-template 1l2tp security crypto-profile l2tpno l2tp tunnel authenticationlcp renegotiation on-mismatchip pmtuThe following example shows how to enable the discovery of the path MTU for pseudowires that have been created from the pseudowire class named "ether-pw":
Router(config)# pseudowire-class ether-pwRouter(config-pw)# ip pmtuRelated Commands
ip dfbit set
Enables the DF bit in the outer Layer 2 tunnel header.
pseudowire-class
Specifies the name of an L2TP pseudowire class and enters pseudowire class configuration mode.
l2tp security crypto-profile
To enable a virtual private dialup network (VPDN) group to be protected by IP Security (IPSec), use the l2tp security crypto-profile command in VPDN group configuration mode. To disable IPSec security for a VPDN group, use the no form of this command.
l2tp security crypto-profile profile-name [keep-sa]
no l2tp security crypto-profile profile-name [keep-sa]
Syntax Description
Defaults
IPSec security is disabled.
SAs are destroyed on tunnel teardown.Command Modes
VPDN group configuration
Command History
Usage Guidelines
A crypto profile must be configured using the crypto map (global IPSec) command before it can be associated with a VPDN group using the l2tp security crypto-profile command. Enabling this command for a VPDN group ensures that no L2TP packets will be processed unless they have IPSec protection.
The keep-sa keyword can be used to prevent the destruction of IKE phase 1 SAs when the L2TP tunnel between the L2TP access concentrator (LAC) and L2TP network server (LNS) is considered permanent, and the IP addresses of the LAC and LNS rarely change. This option is not useful with short-lived tunnels, such as those generated by client-initiated L2TP tunneling.
Examples
The following example configures VPDN group 1, associates it with the crypto profile named l2tp, and prevents the destruction of IKE phase 1 SAs:
vpdn-group 1request-dialinprotocol l2tpdomain cisco.cominitiate-to ip 10.0.0.13local name LACl2tp security crypto-profile l2tp keep-saRelated Commands
crypto map (global IPSec)
Creates or modifies a crypto map entry or creates a crypto profile that provides a template for configuration of dynamically created crypto maps.
crypto map (global IPSec)
To enter crypto map configuration mode and create or modify a crypto map entry, to create a crypto profile that provides a template for configuration of dynamically created crypto maps, or to configure a client accounting list, use the crypto map command in global configuration mode. To delete a crypto map entry, profile, or set, use the no form of this command.
crypto map map-name seq-num [ipsec-manual]
crypto map map-name seq-num [ipsec-isakmp] [dynamic dynamic-map-name] [discover] [profile profile-name]
crypto map map-name [client-accounting-list aaalist]
no crypto map map-name seq-num

Note
Issue the crypto map map-name seq-num command without a keyword to modify an existing crypto map entry.
Syntax Description
Defaults
No crypto maps exist.
Peer discovery is not enabled.
Command Modes
Global configuration
Command History
Usage Guidelines
Use this command to create a new crypto map entry, to create a crypto map profile, or to modify an existing crypto map entry or profile.
After a crypto map entry has been created, you cannot change the parameters specified at the global configuration level because these parameters determine which of the configuration commands are valid at the crypto map level. For example, after a map entry has been created using the ipsec-isakmp keyword, you cannot change it to the option specified by the ipsec-manual keyword; you must delete and reenter the map entry.
After you define crypto map entries, you can assign the crypto map set to interfaces using the crypto map (interface IPSec) command.
Crypto Map Functions
Crypto maps provide two functions: filtering and classifying traffic to be protected and defining the policy to be applied to that traffic. The first use affects the flow of traffic on an interface; the second affects the negotiation performed (via IKE) on behalf of that traffic.
IPSec crypto maps define the following:
•
What traffic should be protected
•
To which IPSec peers the protected traffic can be forwarded—these are the peers with which an SA can be established
•
Which transform sets are acceptable for use with the protected traffic
•
How keys and security associations should be used or managed (or what the keys are, if IKE is not used)
Multiple Crypto Map Entries with the Same Map Name Form a Crypto Map Set
A crypto map set is a collection of crypto map entries, each with a different seq-num argument but the same map-name argument. Therefore, for a given interface, you could have certain traffic forwarded to one IPSec peer with specified security applied to that traffic and other traffic forwarded to the same or a different IPSec peer with different IPSec security applied. To accomplish differential forwarding you would create two crypto maps, each with the same map-name argument, but each with a different seq-num argument. Crypto profiles must have unique names within a crypto map set.
Sequence Numbers
The number you assign to the seq-num argument should not be arbitrary. This number is used to rank multiple crypto map entries within a crypto map set. Within a crypto map set, a crypto map entry with a lower seq-num is evaluated before a map entry with a higher seq-num; that is, the map entry with the lower number has a higher priority.
For example, consider a crypto map set that contains three crypto map entries: mymap 10, mymap 20, and mymap 30. The crypto map set named "mymap" is applied to serial interface 0. When traffic passes through serial interface 0, the traffic is evaluated first for mymap 10. If the traffic matches any access list permit statement entry in the extended access list in mymap 10, the traffic will be processed according to the information defined in mymap 10 (including establishing IPSec SAs when necessary). If the traffic does not match the mymap 10 access list, the traffic will be evaluated for mymap 20, and then mymap 30, until the traffic matches a permit entry in a map entry. (If the traffic does not match a permit entry in any crypto map entry, it will be forwarded without any IPSec security.)
Dynamic Crypto Maps
Refer to the "Usage Guidelines" section of the crypto dynamic-map command for a discussion on dynamic crypto maps.
Crypto map entries that reference dynamic map sets should be the lowest priority map entries, allowing inbound SA negotiation requests to try to match the static maps first. Only after the request does not match any of the static maps, do you want it to be evaluated against the dynamic map set.
To make a crypto map entry referencing a dynamic crypto map set the lowest priority map entry, give the map entry the highest seq-num of all the map entries in a crypto map set.
Create dynamic crypto map entries using the crypto dynamic-map command. After you create a dynamic crypto map set, add the dynamic crypto map set to a static crypto map set with the crypto map (global IPSec) command using the dynamic keyword.
TED
TED is an enhancement to the IPSec feature. Defining a dynamic crypto map allows you to dynamically determine an IPSec peer; however, only the receiving router has this ability. With TED, the initiating router can dynamically determine an IPSec peer for secure IPSec communications.
Dynamic TED helps to simplify IPSec configuration on the individual routers within a large network. Each node has a simple configuration that defines the local network that the router is protecting and the IPSec transforms that are required.

Note
TED helps only in discovering peers; otherwise, TED does not function any differently from normal IPSec. Thus, TED does not improve the scalability of IPSec (in terms of performance or the number of peers or tunnels).
Crypto Map Profiles
Crypto map profiles are created using the profile profile-name keyword and argument combination. Crypto map profiles are used as configuration templates for dynamically creating crypto maps on demand for use with the Layer 2 Transport Protocol (L2TP) Security feature. The relevant SAs the crypto map profile will be cloned and used to protect IP traffic on the L2TP tunnel.

Note
The set peer and match address commands are ignored by crypto profiles and should not be configured in the crypto map definition.
Examples
The following example shows the minimum required crypto map configuration when IKE will be used to establish the SAs:
crypto map mymap 10 ipsec-isakmpmatch address 101set transform-set my_t_set1set peer 10.0.0.1The following example shows the minimum required crypto map configuration when the SAs are manually established:
crypto transform-set someset ah-md5-hmac esp-descrypto map mymap 10 ipsec-manualmatch address 102set transform-set somesetset peer 10.0.0.5set session-key inbound ah 256 98765432109876549876543210987654set session-key outbound ah 256 fedcbafedcbafedcfedcbafedcbafedcset session-key inbound esp 256 cipher 0123456789012345set session-key outbound esp 256 cipher abcdefabcdefabcdThe following example configures an IPSec crypto map set that includes a reference to a dynamic crypto map set.
Crypto map "mymap 10" allows SAs to be established between the router and either (or both) of two remote IPSec peers for traffic matching access list 101. Crypto map "mymap 20" allows either of two transform sets to be negotiated with the remote peer for traffic matching access list 102.
Crypto map entry "mymap 30" references the dynamic crypto map set "mydynamicmap," which can be used to process inbound SA negotiation requests that do not match "mymap" entries 10 or 20. In this case, if the peer specifies a transform set that matches one of the transform sets specified in "mydynamicmap," for a flow permitted by the access list 103, IPSec will accept the request and set up SAs with the remote peer without previously knowing about the remote peer. If the request is accepted, the resulting SAs (and temporary crypto map entry) are established according to the settings specified by the remote peer.
The access list associated with "mydynamicmap 10" is also used as a filter. Inbound packets that match any access list permit statement in this list are dropped for not being IPSec protected. (The same is true for access lists associated with static crypto maps entries.) Outbound packets that match a permit statement without an existing corresponding IPSec SA are also dropped.
crypto map mymap 10 ipsec-isakmpmatch address 101set transform-set my_t_set1set peer 10.0.0.1set peer 10.0.0.2crypto map mymap 20 ipsec-isakmpmatch address 102set transform-set my_t_set1 my_t_set2set peer 10.0.0.3crypto map mymap 30 ipsec-isakmp dynamic mydynamicmap!crypto dynamic-map mydynamicmap 10match address 103set transform-set my_t_set1 my_t_set2 my_t_set3The following example configures TED on a Cisco router:
crypto map testtag 10 ipsec-isakmp dynamic dmap discoverThe following example configures a crypto profile to be used as a template for dynamically created crypto maps when IPSec is used to protect an L2TP tunnel:
crypto map l2tpsec 10 ipsec-isakmp profile l2tpRelated Commands

Copyright © 2002-2005 Cisco Systems, Inc. All rights reserved.
 Feedback
Feedback