Implementing NAT-PT for IPv6
Available Languages
Table Of Contents
Prerequisites for Implementing NAT-PT for IPv6
Restrictions for Implementing NAT-PT for IPv6
Information About Implementing NAT-PT for IPv6
Port Address Translation or Overload
IPv6 Virtual Fragmentation Reassembly
How to Implement NAT-PT for IPv6
Configuring Basic IPv6 to IPv4 Connectivity for NAT-PT for IPv6
Configuring IPv4-Mapped NAT-PT
Configuring Mappings for IPv6 Hosts Accessing IPv4 Hosts
Configuring Mappings for IPv4 Hosts Accessing IPv6 Hosts
Configuring PAT for IPv6 to IPv4 Address Mappings
Configuring IPv6 Virtual Fragmentation Reassembly
Verifying NAT-PT Configuration and Operation
Configuration Examples for NAT-PT for IPv6
Example: Static NAT-PT Configuration
Example: Dynamic NAT-PT Configuration for IPv6 Hosts Accessing IPv4 Hosts
Example: Dynamic NAT-PT Configuration for IPv4 Hosts Accessing IPv6 Hosts
Example: Configuring IPv6 Virtual Fragmentation Reassembly
Feature Information for Implementing NAT-PT for IPv6
Implementing NAT-PT for IPv6
First Published: July 25, 2011Last Updated: July 25, 2011Network Address Translation—Protocol Translation (NAT-PT) is an IPv6 to IPv4 translation mechanism, as defined in RFC 2765 and RFC 2766, allowing IPv6-only devices to communicate with IPv4-only devices and vice versa.
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the "Feature Information for Implementing NAT-PT for IPv6" section.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Contents
•
Prerequisites for Implementing NAT-PT for IPv6
•
Restrictions for Implementing NAT-PT for IPv6
•
Information About Implementing NAT-PT for IPv6
•
How to Implement NAT-PT for IPv6
•
Configuration Examples for NAT-PT for IPv6
•
Feature Information for Implementing NAT-PT for IPv6
Prerequisites for Implementing NAT-PT for IPv6
Before implementing NAT-PT, you must configure IPv4 and IPv6 on the router interfaces that need to communicate between IPv4-only and IPv6-only networks.
Restrictions for Implementing NAT-PT for IPv6
•
NAT-PT is not supported in Cisco Express Forwarding.
•
NAT-PT provides limited Application Layer Gateway (ALG) support—ALG support for Internet Control Message Protocol (ICMP), File Transfer Protocol (FTP), and Domain Naming System (DNS).
•
NAT-PT has the same restrictions that apply to IPv4 NAT where NAT-PT does not provide end-to-end security and the NAT-PT router can be a single point of failure in the network.
•
Users must decide whether to use Static NAT-PT operation, Dynamic NAT-PT operation, Port Address Translation (PAT), or IPv4-mapped operation. Deciding which operation to use determines how a user will configure and operate NAT-PT.
•
Bridge-Group Virtual interfaces (BVIs) in IPv6 are not supported with NAT-PT and wireless interfaces Dot11Radio.
Information About Implementing NAT-PT for IPv6
This section provides an overview of NAT-PT for Cisco IOS software. Users can configure NAT-PT using one of the following operations—static NAT-PT, dynamic NAT-PT, Port Address Translation (PAT), or IPv4-mapped operation—which are described in the following sections:
•
Port Address Translation or Overload
•
IPv6 Virtual Fragmentation Reassembly
NAT-PT Overview
NAT-PT for Cisco IOS software was designed using RFC 2766 and RFC 2765 as a migration tool to help customers transition their IPv4 networks to IPv6 networks. Using a protocol translator between IPv6 and IPv4 allows direct communication between hosts speaking a different network protocol. Users can use either static definitions or IPv4-mapped definitions for NAT-PT operation.
Figure 1 shows NAT-PT runs on a router between an IPv6 network and an IPv4 network to connect an IPv6-only node with an IPv4-only node.
Figure 1 NAT-PT Basic Operation

Although IPv6 solves addressing issues for customers, a long transition period is likely before customers move to an exclusive IPv6 network environment. During the transition period, any new IPv6-only networks will need to continue to communicate with existing IPv4 networks. NAT-PT is designed to be deployed to allow direct communication between IPv6-only networks and IPv4-only networks. For a service provider customer, an example could be an IPv6-only client trying to access an IPv4-only web server. Enterprise customers will also migrate to IPv6 in stages, and many of their IPv4-only networks will be operational for several years. Dual stack networks may have some IPv6-only hosts configured to take advantage of the IPv6 autoconfiguration, global addressing, and simpler management, and these hosts can use NAT-PT to communicate with existing IPv4-only networks in the same organization.
One of the benefits of NAT-PT is that no changes are required to existing hosts, because all the NAT-PT configurations are performed at the NAT-PT router. Customers with existing stable IPv4 networks can introduce an IPv6 network and use NAT-PT to allow communication without disrupting the existing network. To further illustrate the seamless transition, File Transfer Protocol (FTP) can be used between IPv4 and IPv6 networks, just as within an IPv4 network. Packet fragmentation is enabled by default when IPv6 is configured, allowing IPv6 and IPv4 networks to resolve fragmentation problems between the networks. Without the ability to resolve fragmentation, connectivity could become intermittent when fragmented packets might be dropped or improperly interpreted.
Cisco has developed other transition techniques including dual stack, IPv6 over MPLS, and tunneling. NAT-PT should not be used when other native communication techniques exist. If a host is configured as a dual stack host with both IPv4 and IPv6, we do not recommend using NAT-PT to communicate between the dual stack host and an IPv6-only or IPv4-only host. NAT-PT is not recommended for a scenario in which an IPv6-only network is trying to communicate to another IPv6-only network via an IPv4 backbone or vice versa, because NAT-PT would require a double translation to be performed. In this scenario, tunneling techniques would be recommended.
The following sections describe the operations that may be used to configure NAT-PT. Users have the option to use one of the following operations for NAT-PT operation, but not all four.
Static NAT-PT Operation
Static NAT-PT uses static translation rules to map one IPv6 address to one IPv4 address. IPv6 network nodes communicate with IPv4 network nodes using an IPv6 mapping of the IPv4 address configured on the NAT-PT router.
Figure 2 shows how the IPv6-only node named A can communicate with the IPv4-only node named C using NAT-PT. The NAT-PT device is configured to map the source IPv6 address for node A of 2001:DB8:bbbb:1::1 to the IPv4 address 192.168.99.2. NAT-PT is also configured to map the source address of IPv4 node C, 192.168.30.1 to 2001:DB8::a. When packets with a source IPv6 address of node A are received at the NAT-PT router, they are translated to have a destination address to match node C in the IPv4-only network. NAT-PT can also be configured to match a source IPv4 address and translate the packet to an IPv6 destination address to allow an IPv4-only host communicate with an IPv6-only host.
If you have multiple IPv6-only or IPv4-only hosts that need to communicate, you may need to configure many static NAT-PT mappings. Static NAT-PT is useful when applications or servers require access to a stable IPv4 address, such as accessing an external IPv4 DNS server.
Figure 2 Static NAT-PT Operation

Dynamic NAT-PT Operation
Dynamic NAT-PT allows multiple NAT-PT mappings by allocating addresses from a pool. NAT-PT is configured with a pool of IPv6 and/or IPv4 addresses. At the start of a NAT-PT session a temporary address is dynamically allocated from the pool. The number of addresses available in the address pool determines the maximum number of concurrent sessions. The NAT-PT device records each mapping between addresses in a dynamic state table.
Figure 3 shows how dynamic NAT-PT operates. The IPv6-only node B can communicate with the IPv4-only node D using dynamic NAT-PT. The NAT-PT device is configured with an IPv6 access list, prefix list, or route map to determine which packets are to be translated by NAT-PT. A pool of IPv4 addresses—10.21.8.1 to 10.21.8.10 in Figure 3— is also configured. When an IPv6 packet to be translated is identified, NAT-PT uses the configured mapping rules and assigns a temporary IPv4 address from the configured pool of IPv4 addresses.
Figure 3 Dynamic NAT-PT Operation
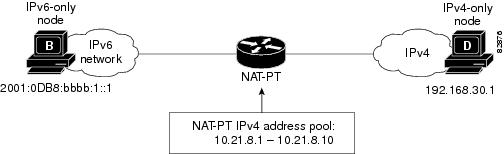
Dynamic NAT-PT translation operation requires at least one static mapping for the IPv4 DNS server.
After the IPv6 to IPv4 connection is established, the reply packets going from IPv4 to IPv6 take advantage of the previously established dynamic mapping to translate back from IPv4 to IPv6. If the connection is initiated by an IPv4-only host, then the explanation is reversed.
Port Address Translation or Overload
Port Address Translation (PAT), also known as Overload, allows a single IPv4 address to be used among multiple sessions by multiplexing on the port number to associate several IPv6 users with a single IPv4 address. PAT can be accomplished through a specific interface or through a pool of addresses. Figure 4 shows multiple IPv6 addresses from the IPv6 network linked to a single IPv4 interface into the IPv4 network.
Figure 4 Port Address Translation

IPv4-Mapped Operation
Customers can also send traffic from their IPv6 network to an IPv4 network without configuring IPv6 destination address mapping. A packet arriving at an interface is checked to discover if it has a NAT-PT prefix that was configured with the ipv6 nat prefix v4-mapped command. If the prefix matches, then an access-list check is performed to discover if the source address matches the access list or prefix list. If the prefix does not match, the packet is dropped.
If the prefix matches, source address translation is performed. If a rule has been configured for the source address translation, the last 32 bits of the destination IPv6 address is used as the IPv4 destination and a flow entry is created.
With an IPv4-mapping configuration on the router, when the DNS ALG IPv4 address is converted to an IPv6 address, the IPv6 address is processed and the DNS packets from IPv4 network get their ALGs translated into the IPv6 network.
IPv6 Virtual Fragmentation Reassembly
Fragmentation is a process of breaking down an IP datagram into smaller packets to be transmitted over different types of network media. Non-initial fragments of a fragmented IPv6 packet is used to pass through IPsec and NAT64 without any examination due to the lack of the L4 header, which usually is only available on the initial fragment. The IPv6 Virtual Fragmentation Reassembly (VFR) feature provides the ability to collect the fragments and provide L4 info for all fragments for IPsec and NAT64 features.
How to Implement NAT-PT for IPv6
•
Configuring Basic IPv6 to IPv4 Connectivity for NAT-PT for IPv6
•
Configuring IPv4-Mapped NAT-PT
•
Configuring Mappings for IPv6 Hosts Accessing IPv4 Hosts
•
Configuring Mappings for IPv4 Hosts Accessing IPv6 Hosts
•
Configuring PAT for IPv6 to IPv4 Address Mappings
•
Configuring IPv6 Virtual Fragmentation Reassembly
•
Verifying NAT-PT Configuration and Operation
Configuring Basic IPv6 to IPv4 Connectivity for NAT-PT for IPv6
Perform this task to configure basic IPv6 to IPv4 connectivity for NAT-PT, which consists of configuring the NAT-PT prefix globally, and enable NAT-PT on an interface. For NAT-PT to be operational, NAT-PT must be enabled on both the incoming and outgoing interfaces.
An IPv6 prefix with a prefix length of 96 must be specified for NAT-PT to use. The IPv6 prefix can be a unique local unicast prefix, a subnet of your allocated IPv6 prefix, or even an extra prefix obtained from your Internet service provider (ISP). The NAT-PT prefix is used to match a destination address of an IPv6 packet. If the match is successful, NAT-PT will use the configured address mapping rules to translate the IPv6 packet to an IPv4 packet. The NAT-PT prefix can be configured globally or with different IPv6 prefixes on individual interfaces. Using a different NAT-PT prefix on several interfaces allows the NAT-PT router to support an IPv6 network with multiple exit points to IPv4 networks.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
ipv6 nat prefix ipv6-prefix/prefix-length
4.
interface type number
5.
ipv6 address ipv6-prefix {/prefix-length | link-local}
6.
ipv6 nat
7.
exit
8.
interface type number
9.
ip address ip-address mask [secondary]
10.
ipv6 nat
DETAILED STEPS
Configuring IPv4-Mapped NAT-PT
Perform this task to enable customers to send traffic from their IPv6 network to an IPv4 network without configuring IPv6 destination address mapping. This task shows the ipv6 nat prefix v4-mapped command configured on a specified interface, but the command could alternatively be configured globally:
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface type number
4.
ipv6 nat prefix ipv6-prefix v4-mapped {access-list-name | ipv6-prefix}
DETAILED STEPS
Configuring Mappings for IPv6 Hosts Accessing IPv4 Hosts
Perform this task to configure static or dynamic IPv6 to IPv4 address mappings. The dynamic address mappings include assigning a pool of IPv4 addresses and using an access list, prefix list, or route map to define which packets are to be translated.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
ipv6 nat v6v4 source ipv6-address ipv4-address
or
ipv6 nat v6v4 source {list access-list-name | route-map map-name} pool name4.
ipv6 nat v6v4 pool name start-ipv4 end-ipv4 prefix-length prefix-length
5.
ipv6 nat translation [max-entries number] {timeout | udp-timeout | dns-timeout | tcp-timeout | finrst-timeout | icmp-timeout} {seconds | never}
6.
ipv6 access-list access-list-name
7.
permit protocol {source-ipv6-prefix/prefix-length | any | host source-ipv6-address} [operator [port-number]] {destination-ipv6-prefix/prefix-length | any | host destination-ipv6-address}
8.
exit
9.
show ipv6 nat translations [icmp | tcp | udp] [verbose]
10.
show ipv6 nat statistics
DETAILED STEPS
Configuring Mappings for IPv4 Hosts Accessing IPv6 Hosts
Perform this optional task to configure static or dynamic IPv4 to IPv6 address mappings. The dynamic address mappings include assigning a pool of IPv6 addresses and using an access list, prefix list, or route map to define which packets are to be translated.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
ipv6 nat v4v6 source ipv4-address ipv6-address
or
ipv6 nat v4v6 source list {access-list-number | name} pool name4.
ipv6 nat v4v6 pool name start-ipv6 end-ipv6 prefix-length prefix-length
5.
access-list {access-list-name | number} {deny | permit} [source source-wildcard] [log]
DETAILED STEPS
Configuring PAT for IPv6 to IPv4 Address Mappings
Perform this task to configure PAT for IPv6 to IPv4 address mappings. Multiple IPv6 addresses are mapped to a single IPv4 address or to a pool of IPv4 addresses and using an access list, prefix list, or route map to define which packets are to be translated.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
ipv6 nat v6v4 source {list access-list-name | route-map map-name} pool name overload
or
ipv6 nat v6v4 source {list access-list-name | route-map map-name} interface interface name overload
4.
ipv6 nat v6v4 pool name start-ipv4 end-ipv4 prefix-length prefix-length
5.
ipv6 nat translation [max-entries number] {timeout | udp-timeout | dns-timeout | tcp-timeout | finrst-timeout | icmp-timeout} {seconds | never}
6.
ipv6 access-list access-list-name
7.
permit protocol {source-ipv6-prefix/prefix-length | any | host source-ipv6-address} [operator [port-number]] {destination-ipv6-prefix/prefix-length | any | host destination-ipv6-address}
DETAILED STEPS
Configuring IPv6 Virtual Fragmentation Reassembly
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface type number
4.
ipv6 virtual-reassembly [in | out] [max-reassemblies maxreassemblies] [max-fragments max-fragments] [timeout seconds] [drop-fragments]
5.
exit
6.
show ipv6 virtual-reassembly interface interface-type
7.
show ipv6 virtual-reassembly features interface interface-type
DETAILED STEPS
Verifying NAT-PT Configuration and Operation
SUMMARY STEPS
1.
clear ipv6 nat translation *
2.
enable
3.
debug ipv6 nat [detailed | port]
DETAILED STEPS
Examples
•
Sample Output from the show ipv6 nat translations Command
•
Sample Output from the show ipv6 nat statistics Command
•
Sample Output from the clear ipv6 nat translation Command
•
Sample Output from the debug ipv6 nat Command
Sample Output from the show ipv6 nat translations Command
In the following example, output information about active NAT-PT translations is displayed using the show ipv6 nat translations command:
Router# show ipv6 nat translationsProt IPv4 source IPv6 sourceIPv4 destination IPv6 destination--- --- ---192.168.123.2 2001:DB8::2--- --- ---192.168.122.10 2001:DB8::10tcp 192.168.124.8,11047 2001:DB8:3::8,11047192.168.123.2,23 2001:DB8::2,23udp 192.168.124.8,52922 2001:DB8:3::8,52922192.168.123.2,69 2001::2,69udp 192.168.124.8,52922 2001:DB8:3::8,52922192.168.123.2,52922 2001:DB8::2,52922--- 192.168.124.8 2001:DB8:3::8192.168.123.2 2001:DB8::2--- 192.168.124.8 2001:DB8:3::8--- ------ 192.168.121.4 2001:DB8:5::4--- ---In the following example, detailed output information about active NAT-PT translations is displayed using the show ipv6 nat translations command with the verbose keyword:
Router# show ipv6 nat translations verboseProt IPv4 source IPv6 sourceIPv4 destination IPv6 destination--- --- ---192.168.123.2 2001:DB8::2create 00:04:24, use 00:03:24,--- --- ---192.168.122.10 2001:DB8::10create 00:04:24, use 00:04:24,tcp 192.168.124.8,11047 2001:DB8:3::8,11047192.168.123.2,23 2001:DB8::2,23create 00:03:24, use 00:03:20, left 00:16:39,udp 192.168.124.8,52922 2001:DB8:3::8,52922192.168.123.2,69 2001:DB8::2,69create 00:02:51, use 00:02:37, left 00:17:22,udp 192.168.124.8,52922 2001:DB8:3::8,52922192.168.123.2,52922 2001:DB8::2,52922create 00:02:48, use 00:02:30, left 00:17:29,--- 192.168.124.8 2001:DB8:3::8192.168.123.2 2001:DB8::2create 00:03:24, use 00:02:34, left 00:17:25,--- 192.168.124.8 2001:DB8:3::8--- ---create 00:04:24, use 00:03:24,--- 192.168.121.4 2001:DB8:5::4--- ---create 00:04:25, use 00:04:25,Sample Output from the show ipv6 nat statistics Command
In the following example, output information about NAT-PT statistics is displayed using the show ipv6 nat statistics command:
Router# show ipv6 nat statisticsTotal active translations: 4 (4 static, 0 dynamic; 0 extended)NAT-PT interfaces:Ethernet3/1, Ethernet3/3Hits: 0 Misses: 0Expired translations: 0Sample Output from the clear ipv6 nat translation Command
In the following example, all dynamic NAT-PT translations are cleared from the dynamic translation state table using the clear ipv6 nat translation command with the * keyword. When the output information about active NAT-PT translations is then displayed using the show ipv6 nat translations command, only the static translation configurations remain. Compare this show command output with the output from the show ipv6 nat translations command in Step 1.
Router# clear ipv6 nat translation *Router# show ipv6 nat translationsProt IPv4 source IPv6 sourceIPv4 destination IPv6 destination--- --- ---192.168.123.2 2001:DB8::2--- --- ---192.168.122.10 2001:DB8::10--- 192.168.124.8 2001:DB8:3::8--- ------ 192.168.121.4 2001:DB8:5::4--- ---Sample Output from the debug ipv6 nat Command
In the following example, debugging messages for NAT-PT translation events are displayed using the debug ipv6 nat command:
Router# debug ipv6 nat00:06:06: IPv6 NAT: icmp src (2001:DB8:3002::8) -> (192.168.124.8), dst (2001:DB8:2001::2) -> (192.168.123.2)00:06:06: IPv6 NAT: icmp src (192.168.123.2) -> (2001:DB8:2001::2), dst (192.168.124.8) -> (2001:DB8:3002::8)00:06:06: IPv6 NAT: icmp src (2001:DB8:3002::8) -> (192.168.124.8), dst (2001:DB8:2001::2) -> (192.168.123.2)00:06:06: IPv6 NAT: icmp src (192.168.123.2) -> (2001:DB8:2001::2), dst (192.168.124.8) -> (2001:DB8:3002::8)00:06:06: IPv6 NAT: tcp src (2001:DB8:3002::8) -> (192.168.124.8), dst (2001:DB8:2001::2) -> (192.168.123.2)00:06:06: IPv6 NAT: tcp src (192.168.123.2) -> (2001:DB8:2001::2), dst (192.168.124.8) -> (2001:DB8:3002::8)00:06:06: IPv6 NAT: tcp src (2001:DB8:3002::8) -> (192.168.124.8), dst (2001:DB8:2001::2) -> (192.168.123.2)00:06:06: IPv6 NAT: tcp src (2001:DB8:3002::8) -> (192.168.124.8), dst (2001:DB8:2001::2) -> (192.168.123.2)00:06:06: IPv6 NAT: tcp src (2001:DB8:3002::8) -> (192.168.124.8), dst (2001:DB8:2001::2) -> (192.168.123.2)00:06:06: IPv6 NAT: tcp src (192.168.123.2) -> (2001:DB8:2001::2), dst (192.168.124.8) -> (2001:DB8:3002::8)Configuration Examples for NAT-PT for IPv6
•
Example: Static NAT-PT Configuration
•
Example: Dynamic NAT-PT Configuration for IPv6 Hosts Accessing IPv4 Hosts
•
Example: Dynamic NAT-PT Configuration for IPv4 Hosts Accessing IPv6 Hosts
•
Example: Configuring IPv6 Virtual Fragmentation Reassembly
Example: Static NAT-PT Configuration
The following example configures the NAT-PT prefix globally, enables NAT-PT on two interfaces, and configures two static NAT-PT mappings. Ethernet interface 3/1 is configured as IPv6 only, and Ethernet interface 3/3 is configured as IPv4 only.
interface Ethernet3/1ipv6 address 2001:DB8:3002::9/64ipv6 enableipv6 nat!interface Ethernet3/3ip address 192.168.30.9 255.255.255.0ipv6 nat!ipv6 nat v4v6 source 192.168.30.1 2001:DB8:0::2ipv6 nat v6v4 source 2001:DB8:bbbb:1::1 10.21.8.10ipv6 nat prefix 2001:DB8:0::/96Example: Enabling Traffic to be Sent from an IPv6 Network to an IPv4 Network without Using IPv6 Destination Address Mapping
In the following example, the access list permits any IPv6 source address with the prefix 2001::/96 to go to the destination with a 2000::/96 prefix. The destination is then translated to the last 32 bit of its IPv6 address; for example: source address = 2001::1, destination address = 2000::192.168.1.1. The destination then becomes 192.168.1.1 in the IPv4 network:
ipv6 nat prefix 2000::/96 v4-mapped v4map_aclipv6 access-list v4map_aclpermit ipv6 2001::/96 2000::/96Example: Dynamic NAT-PT Configuration for IPv6 Hosts Accessing IPv4 Hosts
The following example configures the NAT-PT prefix globally, enables NAT-PT on two interfaces, and configures one static NAT-PT mapping (used, for example, to access a DNS server). A dynamic NAT-PT mapping is also configured to map IPv6 addresses to IPv4 addresses using a pool of IPv4 addresses named v4pool. The packets to be translated by NAT-PT are filtered using an IPv6 access list named pt-list1. The User Datagram Protocol (UDP) translation entries are configured to time out after 10 minutes. Ethernet interface 3/1 is configured as IPv6 only, and Ethernet interface 3/3 is configured as IPv4 only.
interface Ethernet3/1ipv6 address 2001:DB8:bbbb:1::9/64ipv6 enableipv6 nat!interface Ethernet3/3ip address 192.168.30.9 255.255.255.0ipv6 nat!ipv6 nat v4v6 source 192.168.30.1 2001:DB8:0::2ipv6 nat v6v4 source list pt-list1 pool v4poolipv6 nat v6v4 pool v4pool 10.21.8.1 10.21.8.10 prefix-length 24ipv6 nat translation udp-timeout 600ipv6 nat prefix 2001:DB8:1::/96!ipv6 access-list pt-list1permit ipv6 2001:DB8:bbbb:1::/64 anyExample: Dynamic NAT-PT Configuration for IPv4 Hosts Accessing IPv6 Hosts
The following example configures the NAT-PT prefix globally, enables NAT-PT on two interfaces, and configures one static NAT-PT mapping (used, for example, to access a DNS server). A dynamic NAT-PT mapping is also configured to map IPv4 addresses to IPv6 addresses using a pool of IPv6 addresses named v6pool. The packets to be translated by NAT-PT are filtered using an access list named pt-list2. Ethernet interface 3/1 is configured as IPv6 only, and Ethernet interface 3/3 is configured as IPv4 only.
interface Ethernet3/1ipv6 address 2001:DB8:bbbb:1::9/64ipv6 enableipv6 nat!interface Ethernet3/3ip address 192.168.30.9 255.255.255.0ipv6 nat!ipv6 nat v4v6 source list 72 pool v6poolipv6 nat v4v6 pool v6pool 2001:DB8:0::1 2001:DB8:0::2 prefix-length 128ipv6 nat v6v4 source 2001:DB8:bbbb:1::1 10.21.8.0ipv6 nat prefix 2001:DB8:0::/96!access-list 72 permit 192.168.30.0 0.0.0.255Example: Configuring IPv6 Virtual Fragmentation Reassembly
<<Example OK?>>
Router# show ipv6 virtual-reassembly interface gigabitethernet1/1/1GigabitEthernet1/1/1:IPv6 Virtual Fragment Reassembly (VFR) is ENABLED(in)Concurrent reassemblies (max-reassemblies): 64Fragments per reassembly (max-fragments): 16Reassembly timeout (timeout): 3 secondsDrop fragments: OFFCurrent reassembly count: 0Current fragment count: 0Total reassembly count: 6950Total reassembly timeout count: 9GigabitEthernet1/1/1:IPv6 Virtual Fragment Reassembly (VFR) is ENABLED(out)Concurrent reassemblies (max-reassemblies): 64Fragments per reassembly (max-fragments): 16Reassembly timeout (timeout): 3 secondsDrop fragments: OFFCurrent reassembly count: 0Current fragment count: 0Total reassembly count: 0Total reassembly timeout count: 0Additional References
Related Documents
IPv6 supported features
"Start Here: Cisco IOS XE Software Release Specifics for IPv6 Features," Cisco IOS XE IPv6 Configuration Guide
Basic IPv6 configuration tasks
"Implementing IPv6 Addressing and Basic Connectivity," Cisco IOS XE IPv6 Configuration Guide
IPv6 commands: complete command syntax, command mode, defaults, usage guidelines, and examples
Standards
No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature.
—
MIBs
None
To locate and download MIBs for selected platforms, Cisco software releases, and feature sets, use Cisco MIB Locator found at the following URL:
RFCs
RFC 2765
Stateless IP/ICMP Translation Algorithm (SIIT)
RFC 2766
Network Address Translation - Protocol Translation (NAT-PT)
Technical Assistance
Feature Information for Implementing NAT-PT for IPv6
Table 1 lists the features in this module and provides links to specific configuration information.
Use Cisco Feature Navigator to find information about platform support and software image support. Cisco Feature Navigator enables you to determine which software images support a specific software release, feature set, or platform. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.

Note
Table 1 lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Table 1 Feature Information for Implementing NAT-PT for IPv6
NAT Protocol Translation
Cisco IOS XE Release 3.4S
NAT-PT is an IPv6-IPv4 translation mechanism that allows IPv6-only devices to communicate with IPv4-only devices and vice versa. NAT-PT is not supported in Cisco Express Forwarding.
NAT-PT—Support for DNS ALG
Cisco IOS XE Release 3.4S
IPv6 provides DNS ALG support.
The following section provides information about this feature:
NAT-PT—Support for FTP ALG
Cisco IOS XE Release 3.4S
IPv6 provides FTP ALG support.
The following section provides information about this feature:
NAT-PT—Support for Fragmentation
Cisco IOS XE Release 3.4S
Packet fragmentation is enabled by default when IPv6 is configured, allowing IPv6 and IPv4 networks to resolve fragmentation problems between the networks.
The following section provides information about this feature:
IPv6 Virtual Fragmentation Reassembly
Cisco IOS XE Release 3.4S
The IPv6 VFR feature provides the ability to collect the fragments and provide L4 info for all fragments for IPsec and NAT64 features.
The following section provides information about this feature:
•
IPv6 Virtual Fragmentation Reassembly
•
Configuring IPv6 Virtual Fragmentation Reassembly
Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1005R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
© 2002-2011 Cisco Systems, Inc. All rights reserved.
 Feedback
Feedback