Start Here: Cisco Firepower 1010
Available Languages
Table of Contents
Start Here: Cisco Firepower 1010
Firepower Threat Defense Links
Start Here: Cisco Firepower 1010
The Firepower 1010 supports either Firepower Threat Defense (FTD) or Adaptive Security Appliance (ASA) software, and your hardware comes preinstalled with one of these systems. To reimage to the other system, see: https://cisco.com/go/asa-ftd-reimage. (To determine which system you have, follow either the FTD or ASA instructions until you log into the on-device manager; the manager indicates which system you have.) This document tells how to cable and set up the Firepower 1010 using the following managers, depending on your software:
- FTD with FDM —Manage the FTD using Firepower Device Manager (FDM) (a simplified, single device manager included on the device).
Note![]() : To use Cisco Defense Orchestrator (a cloud-based, multidevice manager), first follow the FDM instructions, then see https://cisco.com/go/cdo-onboard.
: To use Cisco Defense Orchestrator (a cloud-based, multidevice manager), first follow the FDM instructions, then see https://cisco.com/go/cdo-onboard.
Note![]() : To instead use the Firepower Management Center (FMC) (a full-featured, multidevice manager on a separate server), see https://cisco.com/go/fmc-fp1010-quick.
: To instead use the Firepower Management Center (FMC) (a full-featured, multidevice manager on a separate server), see https://cisco.com/go/fmc-fp1010-quick.
- ASA with ASDM —Manage the ASA using the Adaptive Security Device Manager (ASDM) (a single device manager included on the device).
Note![]() : To use the ASA CLI, see https://cisco.com/go/asa-config.
: To use the ASA CLI, see https://cisco.com/go/asa-config.
Note![]() : To use Cisco Defense Orchestrator (a cloud-based, multidevice manager), first follow the ASDM instructions, then see https://cisco.com/go/cdo-onboard.
: To use Cisco Defense Orchestrator (a cloud-based, multidevice manager), first follow the ASDM instructions, then see https://cisco.com/go/cdo-onboard.
Note![]() : To manage the ASA with the Cisco Security Manager (multi-device manager on a separate server), see https://cisco.com/go/csm-docs.
: To manage the ASA with the Cisco Security Manager (multi-device manager on a separate server), see https://cisco.com/go/csm-docs.
FTD with FDM
1.![]() Install your chassis. See https://cisco.com/go/firepower1010-install and https://cisco.com/go/firepower1000-compliance.
Install your chassis. See https://cisco.com/go/firepower1010-install and https://cisco.com/go/firepower1000-compliance.
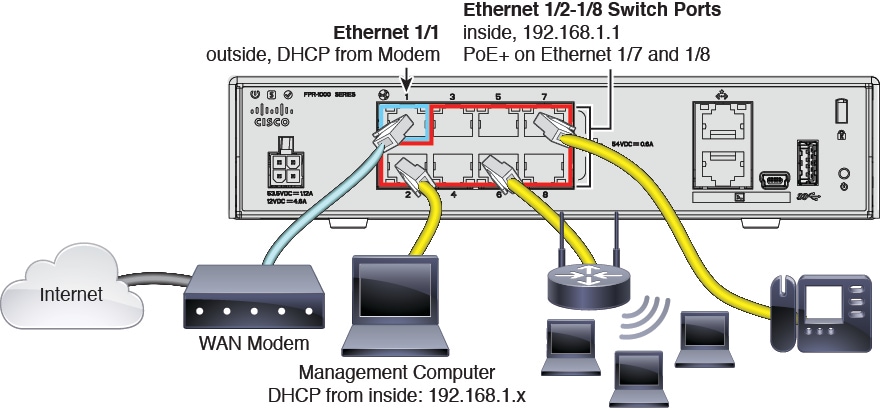
3.![]() Connect your browser to FDM on one of the inside interfaces, Ethernet 1/2 to 1/8: https://192.168.1.1. Username: admin ; password: Admin123. Note: Version 6.4 and earlier uses a software switch for inside ports, and does not support PoE+.
Connect your browser to FDM on one of the inside interfaces, Ethernet 1/2 to 1/8: https://192.168.1.1. Username: admin ; password: Admin123. Note: Version 6.4 and earlier uses a software switch for inside ports, and does not support PoE+.
4.![]() Complete the Device Setup wizard. Note: This process sets the manager to FDM. If you later want to use FMC, you can clear your configuration and start over: at the FTD CLI, use the configure manager delete and then configure manager add commands.
Complete the Device Setup wizard. Note: This process sets the manager to FDM. If you later want to use FMC, you can clear your configuration and start over: at the FTD CLI, use the configure manager delete and then configure manager add commands.
5.![]() See the getting started guide to continue your configuration: https:/cisco.com/go/fdm-fp1010-quick.
See the getting started guide to continue your configuration: https:/cisco.com/go/fdm-fp1010-quick.
ASA with ASDM
1.![]() Install your chassis. See https://cisco.com/go/firepower1010-install and https://cisco.com/go/firepower1000-compliance.
Install your chassis. See https://cisco.com/go/firepower1010-install and https://cisco.com/go/firepower1000-compliance.

3.![]() Connect your browser to ASDM on one of the inside interfaces, Ethernet 1/2 to 1/8: https://192.168.1.1/admin. Leave the username and password empty.
Connect your browser to ASDM on one of the inside interfaces, Ethernet 1/2 to 1/8: https://192.168.1.1/admin. Leave the username and password empty.
4.![]() Choose Wizards > Startup Wizard to configure additional ASA settings.
Choose Wizards > Startup Wizard to configure additional ASA settings.
5.![]() See the getting started guide to continue your configuration: https://cisco.com/go/asa-fp1010-quick.
See the getting started guide to continue your configuration: https://cisco.com/go/asa-fp1010-quick.
Firepower Threat Defense Links
1.![]() Determine Smart License needs. See the licensing document:
Determine Smart License needs. See the licensing document:
https://cisco.com/go/firepower-licensing
2.![]() Install the Firepower 1010. See the hardware installation guide:
Install the Firepower 1010. See the hardware installation guide:
https://cisco.com/go/firepower1010-install
3.![]() Choose a manager and perform initial setup:
Choose a manager and perform initial setup:
–![]() Firepower Device Manager —A simplified, single device manager included on the device.
Firepower Device Manager —A simplified, single device manager included on the device.
https://cisco.com/go/fdm-fp1010-quick
–![]() Firepower Management Center —A full-featured, multidevice manager on a separate server.
Firepower Management Center —A full-featured, multidevice manager on a separate server.
https://cisco.com/go/fmc-fp1010-quick
Note![]() : To use Cisco Defense Orchestrator (A cloud-based, multidevice manager), see https://cisco.com/go/cdo-onboard.
: To use Cisco Defense Orchestrator (A cloud-based, multidevice manager), see https://cisco.com/go/cdo-onboard.
4.![]() Check the release notes for important information. Choose the release notes for your version:
Check the release notes for important information. Choose the release notes for your version:
https://cisco.com/go/ftd-notes
5.![]() Configure the Firepower 1010. Choose the configuration guide for your manager version:
Configure the Firepower 1010. Choose the configuration guide for your manager version:
https://cisco.com/go/ftd-config
–![]() All Firepower Threat Defense documentation: https://cisco.com/go/ftd-docs
All Firepower Threat Defense documentation: https://cisco.com/go/ftd-docs
–![]() Software downloads: https://cisco.com/go/ftd-software
Software downloads: https://cisco.com/go/ftd-software
Note: A Cisco.com login and Cisco service contract are required.
–![]() Troubleshooting TechNotes: https://cisco.com/go/ftd-technotes
Troubleshooting TechNotes: https://cisco.com/go/ftd-technotes
–![]() Next-Generation Firewall Resource Center: https://cisco.com/go/ngfw-resource
Next-Generation Firewall Resource Center: https://cisco.com/go/ngfw-resource
ASA Links
1.![]() Install the Firepower 1010. See the hardware installation guide:
Install the Firepower 1010. See the hardware installation guide:
https://cisco.com/go/firepower1010-install
2.![]() Perform initial setup. See the getting started guide:
Perform initial setup. See the getting started guide:
https://cisco.com/go/asa-fp1010-quick
3.![]() Check the release notes for important notes. Choose the ASDM or CLI release notes for your version:
Check the release notes for important notes. Choose the ASDM or CLI release notes for your version:
4.![]() Configure the ASA. Choose the ASDM or CLI configuration guide for your version:
Configure the ASA. Choose the ASDM or CLI configuration guide for your version:
https://cisco.com/go/asa-config
Note![]() : To use Cisco Defense Orchestrator (A cloud-based, multidevice manager), see https://cisco.com/go/cdo-onboard.
: To use Cisco Defense Orchestrator (A cloud-based, multidevice manager), see https://cisco.com/go/cdo-onboard.
Note![]() : To manage the ASA with the Cisco Security Manager, see https://cisco.com/go/csm-docs.
: To manage the ASA with the Cisco Security Manager, see https://cisco.com/go/csm-docs.
–![]() All ASA documentation: https://cisco.com/go/asadocs
All ASA documentation: https://cisco.com/go/asadocs
–![]() Software downloads: https://cisco.com/go/asa-firepower-sw
Software downloads: https://cisco.com/go/asa-firepower-sw
Note: A Cisco.com login and Cisco service contract are required.
–![]() Troubleshooting TechNotes: https://cisco.com/go/asa-technotes
Troubleshooting TechNotes: https://cisco.com/go/asa-technotes
Common Links
https://supportforums.cisco.com
https://cisco.com/go/firepower1000-compliance
–![]() Warranty and end user license agreement: https://cisco.com/go/warranty
Warranty and end user license agreement: https://cisco.com/go/warranty
–![]() AnyConnect license: https://cisco.com/go/anyconnect-license
AnyConnect license: https://cisco.com/go/anyconnect-license
–![]() Privacy portal: https://cisco.com/go/privacy
Privacy portal: https://cisco.com/go/privacy
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback