Configure Application-Based Remote Access VPN (Per App VPN) on Mobile Devices Using Cisco Secure Firewall Management Center
About Per App VPN
When a remote user establishes a VPN connection from a mobile device using Secure Client, all the traffic including traffic from personal applications is routed through the VPN.
For mobile devices that run on Android or iOS, you can restrict the applications that traverse the VPN tunnel. This application-based remote access VPN is called Per App VPN.
To use Per App VPN, you must perform the following actions:
-
Install and configure a third-party Mobile Device Manager (MDM) server.
-
Define the list of approved applications that can go over the VPN tunnel in the MDM server.
-
Deploy the Per App configurations from the MDM server to the mobile devices.
-
Configure Per App VPN on the managed headend threat defense.
When an MDM-managed mobile device connects to the VPN using Secure Client, the client validates the applications before tunneling the traffic. The Per App policy configured on the threat defense performs this validation.
The following illustration shows an example of Per App VPN using the threat defense:
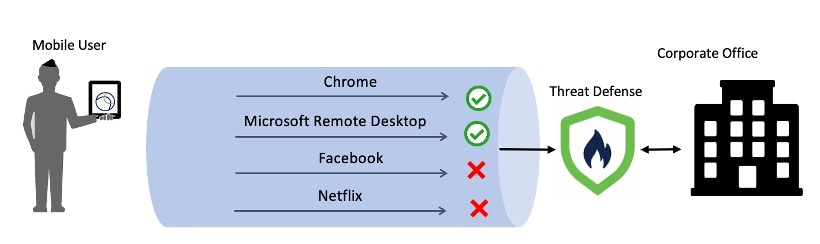
Benefits
-
Limit VPN traffic over the corporate network and free up resources of the VPN headend. You can prevent:
-
Applications such as Netflix, Facebook, and YouTube over the VPN.
-
Trusted cloud applications such as Outlook, and Webex over the VPN.
-
-
Optimize traffic.
-
Minimize latency.
-
Protect the corporate VPN tunnel from unapproved malicious applications on the mobile device.
Is this Guide for You?
This use case is for network administrators who use the management center to configure Per App VPN for remote workers connecting to their organization’s network using remote access VPN.
In versions 6.4 to 6.7, you can enable Per App VPN on an FTD using FlexConfig. For more information, see Configure Application-Based (Per App) Remote Access VPN on Mobile Devices. In version 7.0 and later, you can enable Per App VPN on the threat defense using the management center UI.
System Requirements
The table below shows the supported platforms for this feature.
|
Product |
Version |
Version used in this document |
|---|---|---|
|
Cisco Secure Firewall Threat Defense (formerly Firepower Threat Defense/FTD) |
7.0 and later |
7.3 |
|
Cisco Secure Firewall Management Center (formerly Firepower Management Center/FMC) |
7.0 and later |
7.3 |
|
Cisco Secure Client (formerly AnyConnect) |
4.0 and later |
5.0 |
|
Android Devices |
Android 5.0 and later |
- |
|
Apple iOS devices |
Apple iOS 8.3 and later |
- |
Prerequisites for Configuring Per App VPN Tunnels
Ensure that you have:
-
Configured a remote access VPN policy in the management center.
-
Set up an MDM server and enrolled each mobile device to the MDM server.
For more information, see the MDM documentation.
We recommend that you configure the applications that can traverse the VPN tunnel in the MDM server. This configuration simplifies the headend configuration.
-
Downloaded and installed the Cisco AnyConnect Enterprise Application Selector from the Cisco Software Download Center to your local host.
You need this tool to define the Per App VPN policy.
Licenses:
-
You need one of the following Secure Client licenses:
Secure Client Premier or Secure Client Advantage.
-
Your management center Essentials license must allow export-controlled functionality.
Choose to verify this functionality in the management center.
How to Configure Per App VPN Using Management Center
|
Step |
Do This |
More Info |
|---|---|---|
|
1 |
Ensure that you meet the prerequisites. |
|
|
2 |
Determine which applications should be allowed in the tunnel. |
- |
|
3 |
Determine the application IDs for the mobile applications. |
|
|
4 |
Define a Per App VPN policy for Android and Apple iOS devices. |
Define a Per App VPN Policy for Android and Apple iOS Devices |
|
5 |
Assign the Per App VPN policy to a remote access VPN in the management center. |
Assign the Per App VPN Policy to a Remote Access VPN in the Management Center |
|
6 |
Deploy the configuration on the threat defense. |
On the management center menu bar, click Deploy and then select Deployment. |
Determine the Application IDs for Mobile Applications
If you decide to configure the list of allowed applications on the headend, you must determine the application IDs for each application on each type of endpoint.
 Note |
We recommend that you configure the Per App policy in the MDM server. This configuration simplifies the headend configuration. |
The application ID, or the bundle ID in iOS, is a reverse DNS name. You can use an asterisk as a wildcard. For example, *.* indicates all applications, com.cisco.* indicates all Cisco applications.
To determine the application IDs:
-
Android
-
In a web browser, go to Google Play (https://play.google.com/store/).
-
Click the Apps tab.
-
Click an application that you want to allow in the VPN tunnel.
The application ID is part of the URL.
-
Copy the string after the ‘id=’ parameter.
For Microsoft Remote Desktop, the URL is:
https://play.google.com/store/apps/details?id=com.microsoft.rdc.androidx, and the app id is com.microsoft.rdc.androidx.
For applications that are not available on Google Play, download a package name viewer application to extract the app ID.
-
-
iOS
-
In a web browser, go to Apple App Store (https://www.apple.com/in/app-store/).
-
In the search results, search for an application.
The application ID is part of the URL.
-
Copy the number after the ‘id’ string.
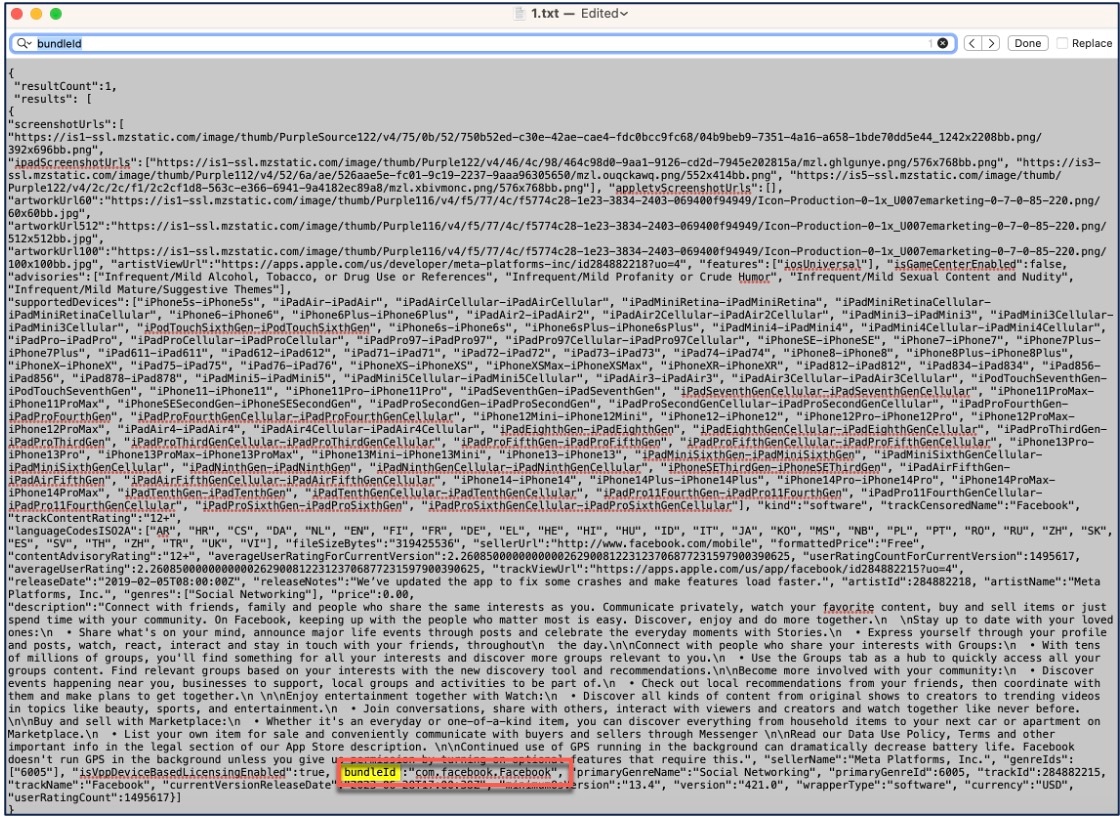
For Facebook, the URL is:
https://apps.apple.com/in/app/facebook/id284882215 and the application ID is 284882215.
-
Open a new browser window, and add the number to the end of the following URL: https://itunes.apple.com/lookup?id=
For Facebook the URL is https://itunes.apple.com/lookup?id=284882215.
-
Download the text file, usually named 1.txt.
-
Open the file in a text editor, and search for ‘bundleId’. For Facebook, the ‘bundleId’ is " com.facebook.Facebook". Use this bundle ID as the app ID.
-
Once you have your list of application IDs, you can define the policy for the mobile device as explained in the procedure below.
Define a Per App VPN Policy for Android and Apple iOS Devices
Use the Cisco AnyConnect Enterprise Application Selector to define the Per App VPN policy.
We recommend that you create a simple ‘Allow All’ policy, and define the allowed applications in the MDM. However, you can specify a list of applications to allow and control the list from the headend. If you want to include specific applications, create a separate rule for each application, using a unique name and the application’s app ID.
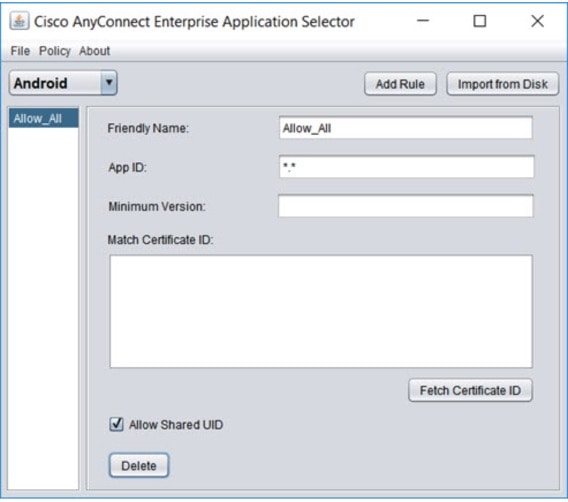
To create an Allow All policy (wildcard policy) that supports both Android and iOS platforms using the AnyConnect Enterprise Application Selector:
-
Choose Android or iOS from the drop-down list as the platform type.
-
Configure the following options:
-
Friendly Name—Enter a name for the policy. For example, Allow_All.
-
App ID—Enter *.* to match all possible applications.
-
Leave the other options.
-
-
Choose to get the base64 encoded string for the policy. This string contains an encrypted XML file that allows the threat defense to see the policies. Copy this value. You need this string when you configure Per App VPN on the threat defense in the next step.
To create a policy for the Microsoft Remote Desktop application using the AnyConnect Enterprise Application Selector:
-
Choose Android from the drop-down list as the platform type.
-
Configure the following options:
-
Friendly Name—Enter the policy name.
-
App ID—For Android, enter com.microsoft.rdc.androidx.
-
Leave the other options.
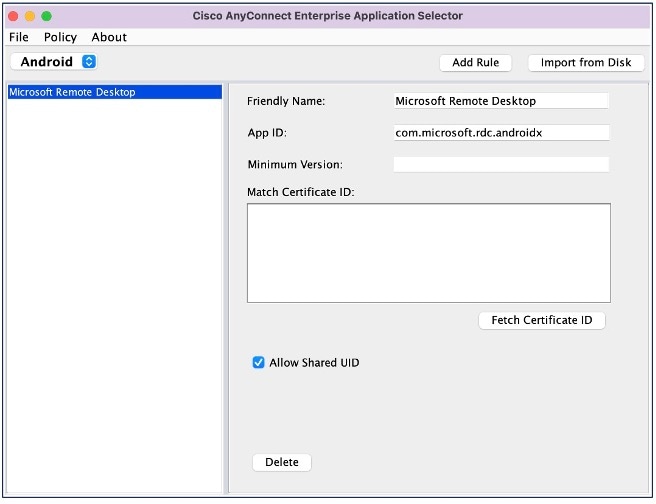
-
-
Choose to get the base64 encoded string for the policy.
Assign the Per App VPN Policy to a Remote Access VPN in the Management Center
Procedure
|
Step 1 |
Choose . |
|
Step 2 |
Select a remote access VPN policy and click Edit. |
|
Step 3 |
Select a connection profile and click Edit. |
|
Step 4 |
Click Edit Group Policy. |
|
Step 5 |
Click the Secure Client tab. |
|
Step 6 |
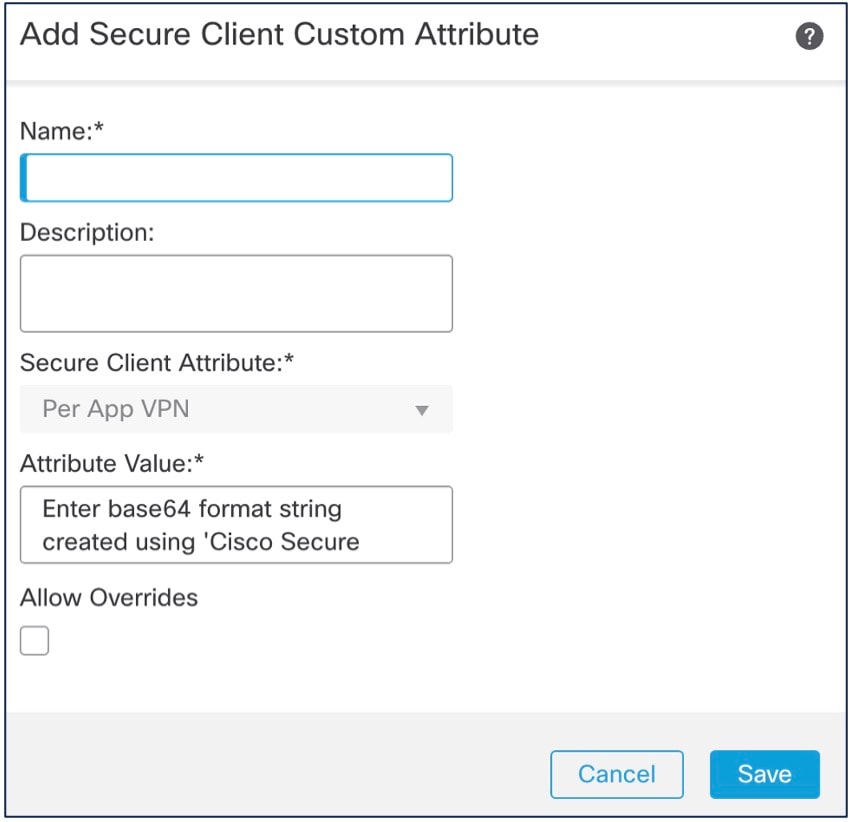
Click Custom Attributes and click +. |
|
Step 7 |
Choose Per App VPN from the Secure Client Attribute drop-down list. |
|
Step 8 |
Choose an object from the Custom Attribute Object drop-down list or click + to add an object. When you add a new custom attribute object for Per App VPN:
|
|
Step 9 |
Click Save and click Add.
|
|
Step 10 |
Click Save. |
What to do next
-
Deploy the configuration on the threat defense.
-
Establish a VPN connection to the threat defense using the Secure Client.
Verify Per App VPN Configuration
On the Threat Defense
Use the following commands on the threat defense to verify the Per App configuration:
|
Command |
Description |
|---|---|
|
show run webvpn |
View details of the Secure Client configurations. |
|
show run group-policy <group_policy_name> |
View details of the remote access VPN group policy for Secure Client. |
|
show vpn-sessiondb anyconnect |
View details of the active Secure Client VPN sessions. |
|
show run anyconnect-custom-data |
View details of the Per App configuration. |
Sample output for sh run webvpn is given below:
firepower# sh run webvpn
webvpn
enable inside
anyconnect-custom-attr perapp description Per-App Allow
http-headers
hsts-server
enable
max-age 31536000
include-sub-domains
no preload
hsts-client
enable
x-content-type-options
x-xss-protection
content-security-policy
anyconnect image disk0:/csm/cisco-secure-client-win-5.0.03076-webdeploy-k9 1 regex "Windows"
anyconnect enable
tunnel-group-list enable
cache
no disable
error-recovery disable
Sample output for sh run anyconnect-custom-data is given below:
firepower# sh run anyconnect-custom-data
anyconnect-custom-data perapp PerAppPolicy
eJw9kFtvgkAQhf8K2ae2GC+rqPFNgYjgBcUL2PRhCyuuZVlkuRv/
Sample output for sh running-config group-policy is given below:
firepower# sh running-config group-policy
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev2 ssl-client
user-authentication-idle-timeout none
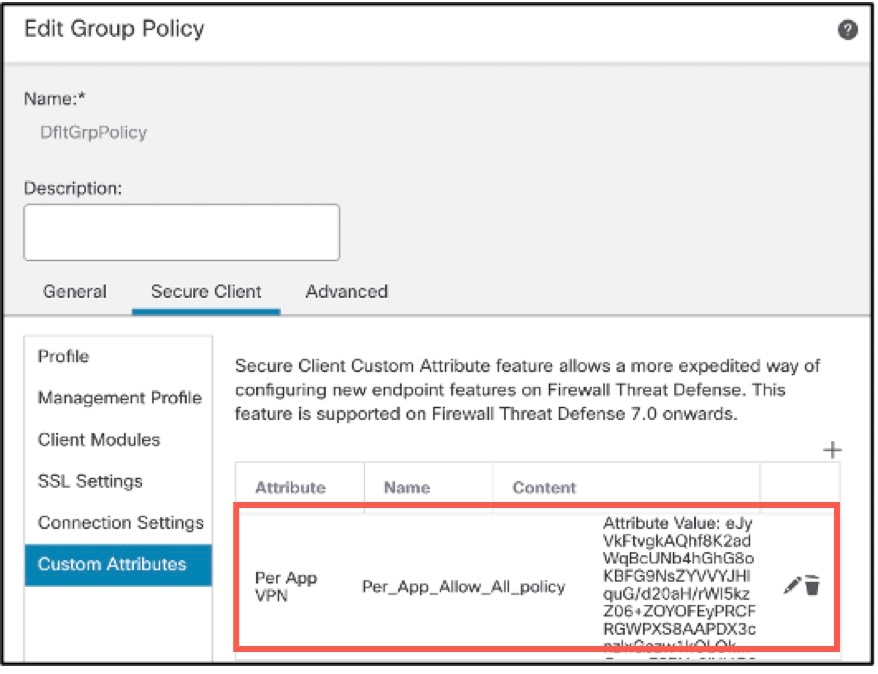
anyconnect-custom perapp value PerAppPolicy
webvpn
anyconnect keep-installer none
anyconnect modules value none
anyconnect ask none default anyconnect
http-comp none
activex-relay disable
file-entry disable
file-browsing disable
url-entry disable
deny-message none
On the Endpoint
After the endpoint establishes a VPN connection with the threat defense, click the Statistics icon of the Secure Client:
-
Tunnel Mode will be “Application Tunnel” instead of “Tunnel All Traffic.”
-
Tunneled Apps will list the applications you enabled for tunneling in the MDM.
 Feedback
Feedback