Securing the Utility Grid
Cisco IoT Solution Brief
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- US/Canada 800-553-2447
- Worldwide Support Phone Numbers
- All Tools
 Feedback
Feedback
Securing the grid
Introduction to Cisco Grid Security Solutions
The cyber security of the utility grid and the associated operational monitoring and control networks have caused increasing concern and regulatory mandates on a global level. Organizations simply cannot modernize the utility grid without incorporating cybersecurity — it is a requirement for operating in the 21st century. Cybersecurity must be a key component of a grid modernization effort.
While utilities are transforming operations infrastructure toward grid modernization, cyber threats become a major concern. Significant changes in the operational model and adoption of newer more cost-effective technologies are being driven by flat to declining revenues and grid stability issues. The legacy, often proprietary, control systems are no longer efficient to operate and are virtually impossible to secure. The adage “You cannot secure what you cannot see” has never been more applicable. Asset visibility, controls to mitigate attacks, and the cooperation between Information Technology (IT) and Operations Technology (OT) are required.
A comprehensive security architecture with proven integration is a more operational and cost-effective answer. Integrating IT and OT around security and leveraging the experience of IT with implemented systems are the right approaches. A well thought-out, implemented, and operationally-effective security posture requires a partnership between IT and OT and starts at the foundation — the network.

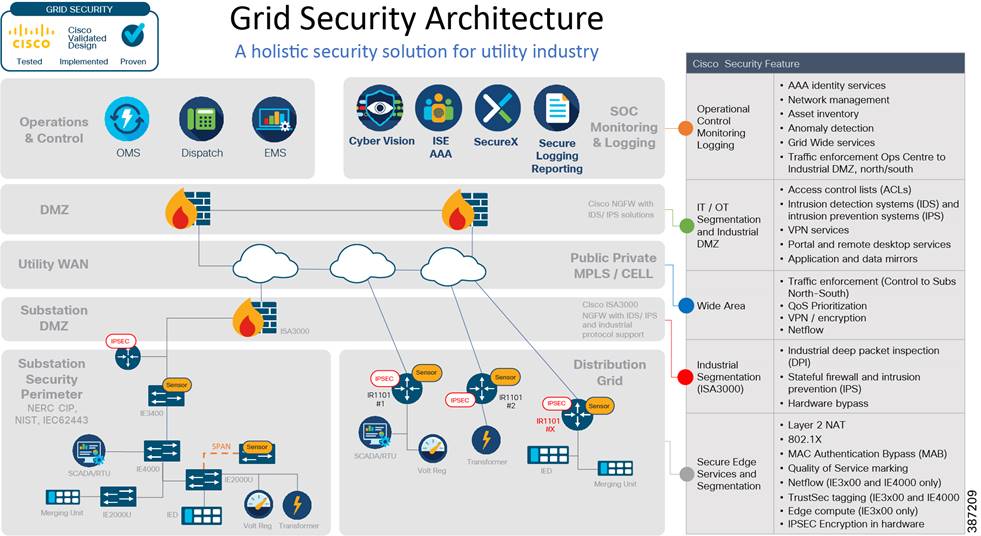
The Grid Security CVD provides a holistic cybersecurity architecture to protect utility networks and processes while addressing the key security and compliance concerns of the utility grid operators.
The journey to securing the utility network
Control networks connect devices that have been deployed over a period of many years – sometimes even decades – when cybersecurity wasn’t a concern. When utilities attempt to secure their operational network, they encounter three primary issues:
● A lack of visibility: Utility operators often don’t have an accurate inventory of what’s on their industrial network. Without this, they have limited ability to build a secure communications architecture.
● A lack of visibility also means operators are often unaware of which devices are communicating, and where those communications are going. You cannot control what you cannot see.
● OT devices and processes are managed by the operations team. Cybersecurity is generally driven by the IT and security teams. All these stakeholders need to collaborate to build the specific security policies and enrich events with context so that security does not disrupt production.
Addressing these issues and building a secure industrial network will not happen overnight. To ensure success, Cisco promotes a phased approach where each phase builds the foundation for the next so that you can enhance your security posture at your own pace as you demonstrate value to all stakeholders.
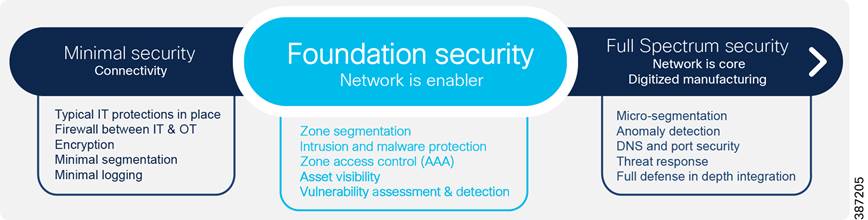
The move from Minimal phase to Foundational is about establishing, controlling and segmenting zones and traffic flows between those zones. Separation of IT and OT is one example and should be completed as defined in Minimal. The idea to take it to the next level is to segment and monitor traffic across the WAN and provide segmentation in the substations with logging. An IoT “aware” firewall is a perfect fit here.
Key requirements
The figure above depicts the key requirements as part of the journey to secure operational networks and can guide the development of a security lifecycle process. The ability to leverage the network with device identification, separation, and segmentation based on security levels and application criticality now enables an effective security posture. This posture can protect, detect, and respond to advanced cyber-security threats as part of this comprehensive security lifecycle. Compliance standards such as NERC-CIP and others are addressed in this guide as part of that complete security lifecycle. This security solution brief and the Cisco Grid Security CVD provide the blueprints to meet these requirements.
Foundational security
Identify: Unknown and unpatched assets
The utility grid has gone virtually unchanged for many years with assets operating in place for decades. Asset discovery often requires time consuming, costly, and even hazardous manual inspections that are error prone and may easily become obsolete. This is a security risk and a compliance issue. Cisco Cyber Vision can discover these devices automatically, providing significant levels of device detail and security posture assessments.
Protect: Lack of separation and segmentation
Separation and segmentation are the basis of security best practices, providing numerous points of inspection. Separating and controlling the flow of malicious traffic are best accomplished at the network level.
Many regulatory bodies such as NERC-CIP, IEC, NIST, ENISA and others are dictating the separation and segmentation of operational and monitoring, control traffic, physical security, and the wider IT traffic from each other throughout the network. The ruggedized industrial security appliance ISA 3000 with next generation firewall (NGFW), TrustSec, and encryption techniques are part of the Cisco Secure Architecture that leverages these tools to achieve the system-wide segmentation required.
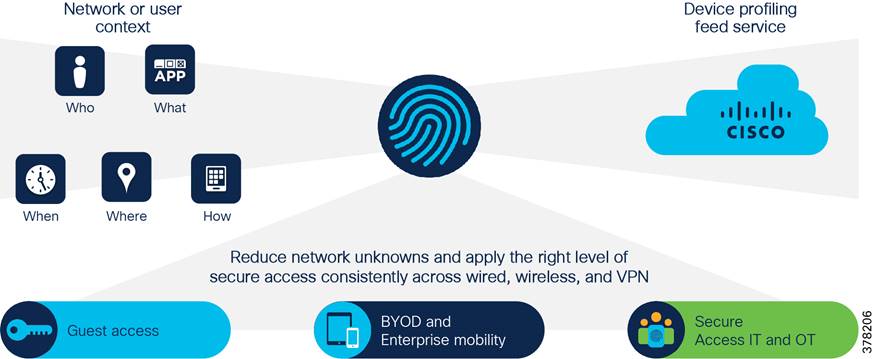
Protect: Secure remote access
Remote access security starts by establishing trust in the device and the device user identity before access to the network is granted. Secure access allows a utility to reduce costly manual intervention and the ability to leverage trusted third parties. The Cisco ISA 3000 firewalls establish a secure demilitarized zone (DMZ) and inspection points.
Remote workers use Cisco AnyConnect from their devices to connect into the trusted network. The Cisco Identity Service Engine (ISE) uses standards-based tools like 802.1x and MAC profiling with profiles on each edge port. All features are supported on the Cisco industrial Ethernet switching portfolio including the IE3400, IE4000, and IE5000 family.
Protect: Data privacy and integrity
Grid operators depend on secure data transport for real-time data monitoring, remote operational modifications and results. Compliance mandates separation of critical data and the encryption of data exiting a physical perimeter. Logging information must also be securely delivered and maintained. Data privacy is a foundational tenant of our secure architecture. Data security leverages port security on Cisco industrial Ethernet switches, and uses a wide variety of encryption technologies on the ISA 3000 or any of the Cisco Industrial Routers IR1101, IR807, or CGR-2010.
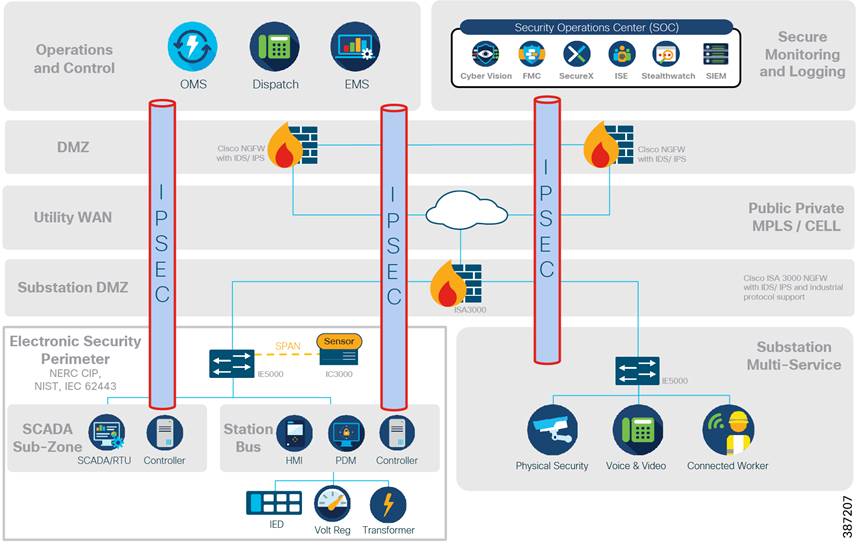
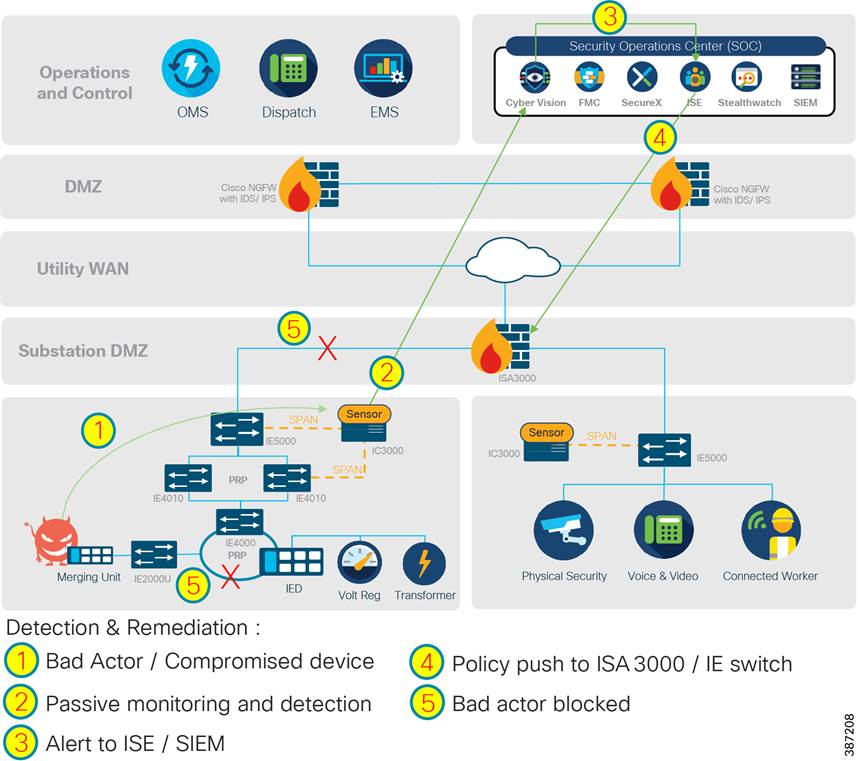
Detect and respond
Utilities face several challenges when it comes to detecting and responding to cybersecurity attacks. The first is a lack of visibility. Operators can only stop malicious activities they can see. Another is a lack of reliable mitigation. Stopping cyberattacks requires a variety of cybersecurity technologies working together seamlessly, including a fully integrated security architecture that can discover threats and provide the information necessary for mitigation. The solution includes Cyber Vision, Stealthwatch, SecureX and the ISA 3000 industrial firewall.
Compliance requirements
A well-architected and comprehensive security solution can provide a secure, compliant, and operationally efficient OT network. A single system is easier to maintain, more reliable and trusted, with fewer integration costs and ongoing operational costs, thus reducing both capex and opex over the life of the system. The components and architecture described here are all part of a comprehensive NERC CIP compliant posture. Patching, asset information, data privacy, segmentation, detection and trust are all key parts of the current NERC CIP mandates.
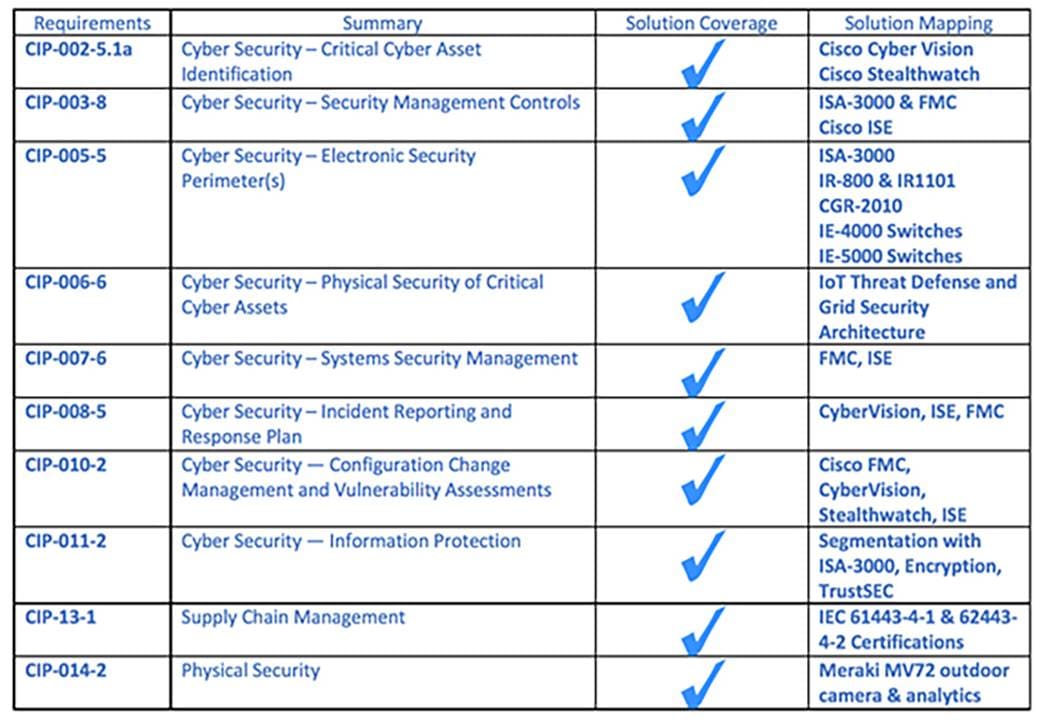
A matrix mapping NERC-CIP mandates to Cisco solutions is located at the end of this document.

Defense in depth
A solid security architecture leverages a defense-in-depth approach. This guide details the integration of multiple security tools and devices to accomplish this in an OT environment, which Cisco refers to as Internet of Things (IoT) Threat Defense. This holistic “full spectrum” security solution addresses the unique requirements of the utility network with best practices and compliance requirements like those found in NERC CIP and IEC 62443 and the NIST framework.
This solution is based on industry-leading innovations in Cisco IoT security and networking technologies that are built into Cisco Cyber Vision, Cisco 3000 Series Industrial Security Appliances (ISA), Cisco IC3000 Industrial Compute Gateway, and Cisco Industrial Ethernet IE3300, IE3400, IE4000, IE5000 Series Switches with integration with Cisco Identity Services Engine (ISE), Cisco Stealthwatch®, and Cisco TrustSec®.
These integrated systems improve operational capabilities and protection to systems; the integration and centralized management significantly reduce operational costs, time and exposure for the utility. This is the benefit of a one-source system versus integrating numerous point products from multiple vendors.
A validated security solution
Cisco’s team of validation engineers build out these solutions based on detailed use cases from real-world environments and scenarios. They test the full solution to the limit of its capabilities and document the results in a Cisco Validated Design (CVD). These documents can be found here: www.cisco.com/go/iotcvd
Cisco is a leader in securing enterprise networks. Cisco is also a leader in industrial networking. We are leveraging these unique portfolios of products and solutions, together with threat intelligence from Talos®, one of the world’s largest security research teams, to make security inherent and embedded in the industrial network.
Cisco is not only “IT approved” but is “IT preferred”, helping you streamline and accelerate security deployments in the industrial spaces.
Cyber Vision
Cisco Cyber Vision is an asset inventory, network monitoring and threat-detection platform specifically designed to secure industrial control systems (ICS). It enables industrial organizations to gain full visibility into their industrial networks so they can ensure process integrity, build secure infrastructures, drive regulatory compliance, and enforce security policies to control risks.
Port security
The Cisco IE3400, IE4000, IE5000 Series switches deliver Gigabit connectivity to the Cisco ruggedized switching portfolio with superior high-bandwidth switching capacity and proven Cisco IOS Software. The Cisco IE Switching Series provides highly secure access to support resilient and scalable networks while adhering to industry compliance requirements.
ISA 3000 Industrial Security Appliance
The Cisco ISA 3000 Industrial Security Appliance is a next generation firewall specifically designed for harsh industrial environments. Fully certified for deployment in power grid networks and substations (IEC 61850-3 and IEEE 1613) it leverages threat intelligence from Cisco Talos to detect intrusions, is fully integrated with Cisco Firepower Management Center to enforce access control and security policies, and also offers industrial protocol decoders to control communication content and compliance.
Stealthwatch
Cisco Stealthwatch improves threat defense with network visibility and security analytics. It helps gain situational awareness of all users, devices, and traffic on the network, so threats can be responded to quickly and effectively. Stealthwatch leverages NetFlow data from network infrastructure devices. The data is collected and analyzed to provide a complete picture of network activity.
SecureX
Cisco SecureX integrates intelligence from Firepower Management Center, Cyber Vision, Identity Services Engine, Stealthwatch, Advanced Malware Protection and Umbrella. This seamless integration among Cisco security products makes deeper investigations really easy, and it also lets you take corrective action directly from its interface without having to log into another product.
Identity Services Engine
Cisco Identity Services Engine (ISE) enables micro-segmentation to the device level and fine-grain access control can be created per user and device. Consistent security policies can be created across the entire network based on context. Cisco ISE becomes the policy engine for users and assets that require access to the industrial network.
Mapping NERC-CIP compliance with Cisco security solutions
 Feedback
Feedback