CUWN 8.1 WLC and FC AP - EoGRE Tunnel Gateway Deployment Guide
Available Languages
Contents
- CUWN 8.1 WLC and FC AP - EoGRE Tunnel Gateway Deployment Guide
- WLC EoGRE Tunneling
- Supported Controller and APs
- EoGRE Tunnels System Design Options
- Design 1: WLC based EoGRE Tunnel
- Redundancy of the EoGRE Tunnels
- EoGRE Tunnel DHCP Option-82 Design
- Installing WLC EoGRE
- Configuring WLC EoGRE tunnel
- Typical Deployment: WLC EoGRE Topology
- Design 2: FlexConnect AP based EoGRE Tunnel
- Basic Flex AP EoGRE Configuration
- Typical Deployment: Flex Connect AP - EoGRE Topology
- Show Commands
- Example Configuration of the EoGRE Feature
- References
CUWN 8.1 WLC and FC AP - EoGRE Tunnel Gateway Deployment Guide

WLC EoGRE Tunneling
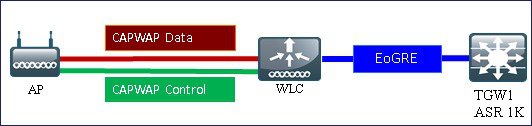
Ethernet over GRE (EoGRE) is a new aggregation solution for aggregating Wi-Fi traffic from hotspots. This solution enables customer premises equipment (CPE) devices to bridge the Ethernet traffic coming from an end host, and encapsulate the traffic in Ethernet packets over an IP GRE tunnel. When the IP GRE tunnels are terminated on a service provider broadband network gateway, the end host’s traffic is terminated and subscriber sessions are initiated for the end host.
Client can maintain IP address and policy across heterogeneous access networks with different technologies and/or vendors.
Bypass MAC address scaling limitation of the L2 switch connecting to the WLC.
Lawful Intercept (LI)
The EoGRE Tunneling offers the following benefits for mobile operators:The EoGRE tunneling offers the following benefits for wireline and Wi-Fi operators:The EoGRE tunneling offers the following benefits for subscribers:
Provides enhanced quality of experience to subscribers on WiFi networks.
Provides unified billing across access networks.
Provides mobility across radio access technologies—3G or 4G to WiFi and WiFi to WiFi.
Provides multiple options within the Wi-Fi platform, thereby enabling location-based services.
Design 1: WLC based EoGRE Tunnel
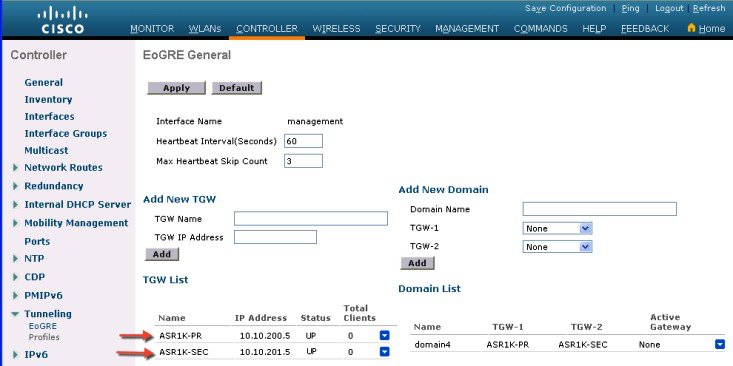
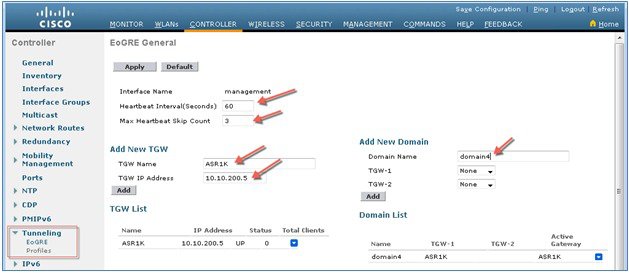
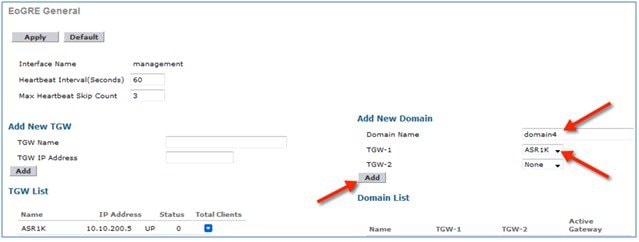
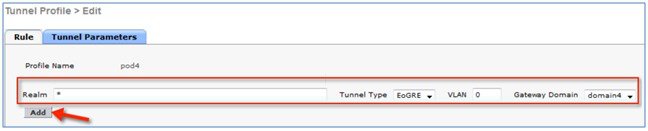
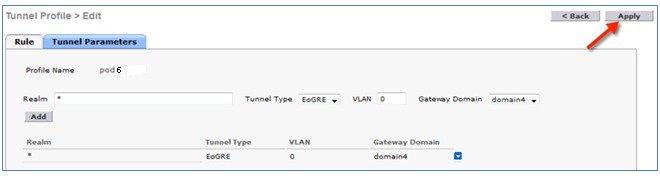
In this design model, a tunnel gets generated from WLC to the tunnel gateway such as ASR 1000. In release 8.1 and above, controller supports up to 10 tunnel gateways and 10 domains. Each of the 10 EoGRE Profiles can be configured with up to 16 rules. When realms are configured, it will be a user name followed by @. Realm is a string after @, for example, user_name@realm. Two or more tunnels can be configured for redundancy, so that when the primary or active tunnel fails, the secondary or standby tunnel will take over the operation of the EoGRE tunnel. Intra-controller and Inter-controller mobility is also supported with the EoGRE tunnel configuration.
The WLC in release 8.1 supports two tunnel type configurations on the northbound interface:
Note
In this deployment guide, only EoGRE tunnel is discussed.
Only one type of tunnel is supported per WLAN. EoGRE is supported on either open or 802.1x based WLANs. Tunneled clients support EAP-SIM or EAP-AKA mode only. Other authentication modes are not supported by the tunneled clients.
When open SSID WLAN is used, either all local/simple or all tunneled clients are supported but cannot be mixed on the same WLAN. However, 802.1x authenticated simple or tunneled EoGRE clients are supported on the same WLAN.
Based on authentication, clients will be separated into local or tunneled mode.
The WLC supports two types of user’s traffic such as Remote-Tunneled and Local on the same WLAN.
Local users traffic is defined as traffic that is locally bridged by the WLC.
Remote-Tunneled user traffic is defined as traffic of remote-tunnel users and is tunneled by the WLC to a TGW.
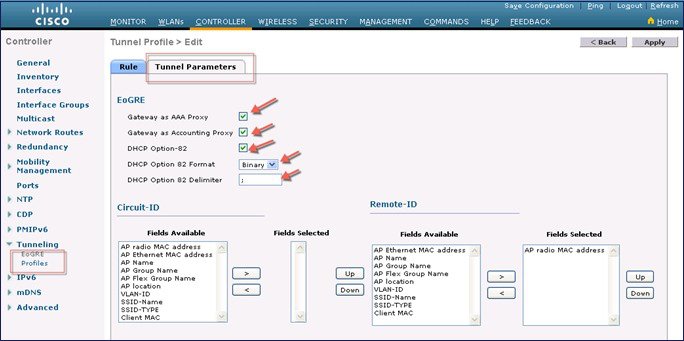
AAA override for EoGRE users is supported. Tunnel gateway can also act as AAA proxy.
If AAA Override is enabled on the controller for EoGRE EAP authenticated clients:
WLC parses Access Accept and looks for MPC-Protocol-Type, such as EoGRE, GTPv2 or PMIPv6.
If the Protocol-Type AVP exists, WLC looks for all parameters related to that tunnel-type. The static profile is ignored and the AAA provided parameters are used to setup tunnel.
If AVP is not present, WLC uses static profile on WLC to determine tunnel type based on the realm extracted from user name.
If some of the parameters are not present, the authentication fails. For example, if everything is present except T-GW IP, then the client authentication fails.
If the MPC-Protocol-Type is None, then it will be simple IP.
Some of the attributes that can be returned by the AAA server are: User-Name, Calling-Station-Id, gw-domain-name, mn-service, cisco-mpc-protocol-interface, and eogre_vlan_id.
Redundancy of the EoGRE Tunnels
Two or more tunnels can be configured for redundancy, so that when the primary or active tunnel fails, the secondary or standby tunnel will take over the operation of the EoGRE tunnel. Keep-alive messages are sent periodically and the periodicity is configurable, that is, how many keep-alives can be missed before tunnel is considered as down. This is a global command and is applicable for all types of tunnels. In EoGRE tunnels design, DTLS ICMP packets are sent to the tunnel gateway. When EoGRE tunnel is created, ICMP echo request packet is sent to tunnel gateway. After receiving, ICMP echo response is sent back updating the tunnel gateway status.
When primary tunnel fails, the clients will de-authenticate and dis-associate from the primary WAG. If a secondary WAG is available, the controller will establish a secondary tunnel and reconnect to the secondary WAG, if the secondary tunnel is configured as shown in the following example. After secondary tunnel is established, the remote-client devices will re-authenticate and re-associate to WAG and will renew their IP addresses from the DHCP server on the secondary WAG. Clients will remain connected to the secondary WAG even if the primary WAG comes back on line.
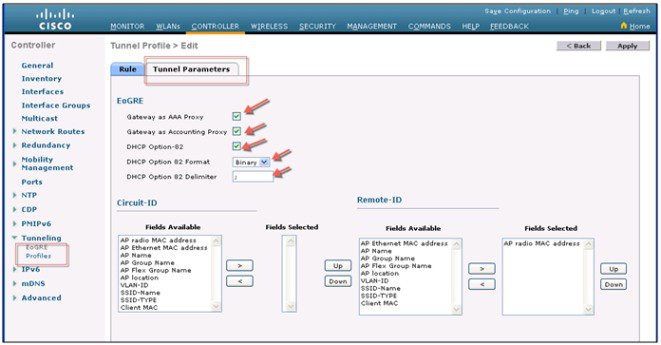
EoGRE Tunnel DHCP Option-82 Design
The DHCP option-82 for EoGRE clients is inserted at the WLC in the bridge mode. The DHCP request packets from the clients are punted up to the controller as with any other DHCP packets. In the controller, based on the client type, the EoGRE clients are handled specially. For EoGRE clients, the DHCP option-82 configurations are picked from the Tunnel Profile data base. The global DHCP configurations have no impact on EoGRE clients.
The DHCP code in controller inserts DHCP option-82 parameters based on the tunnel profile configurations. Also, the EoGRE tunnel header information is added in the controller. The controller assembles the complete DHCP packet along with EoGRE tunnel headers and sends out on the tunnel.
The configuration commands gives flexibility to configuring option-82 format, delimiter character, remote-id, and circuit-id. The remote-id and circuit-id can be easily configured by providing up to a maximum of five different parameter-ids supported. The parameters entered will overwrite the previously entered configurations. If no parameters are input, the remote-id and circuit-id will be erased and no parameter for that field will be sent.
Configuration commands
config tunnel profile eogre <profile name> dhCP-Opt-82 enable / disable
config tunnel profile eogre <profile name> dhCP-Opt-82 format binary / ascii
config tunnel profile eogre <profile name> dhCP-Opt-82 delimiter <delimiter character>
config tunnel profile eogre <profile name> dhCP-Opt-82 remote-id <Paramater ID - 1> <Paramater ID - 2> <Paramater ID - 3> <Paramater ID - 4> <Paramater ID - 5>
config tunnel profile eogre <profile name> dhCP-Opt-82 circuit-id <Paramater ID - 1> <Paramater ID - 2> <Paramater ID - 3> <Paramater ID - 4> <Paramater ID - 5>
Installing WLC EoGRE
Procedure
Configuring WLC EoGRE tunnel
Procedure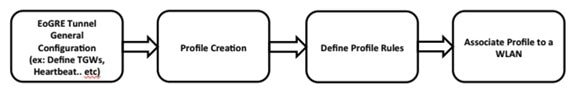
Note
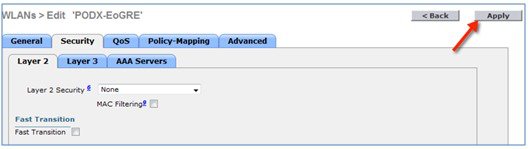
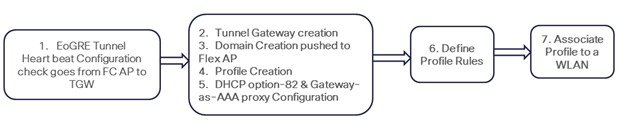
EoGRE tunnel configuration can be performed through GUI or CLI.
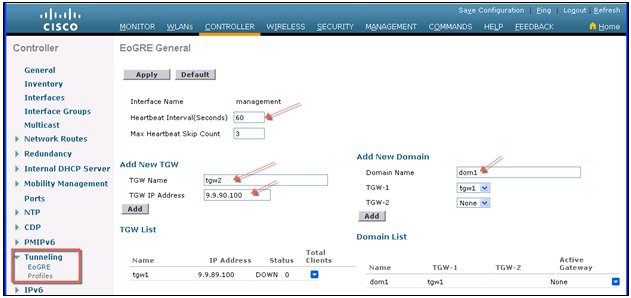
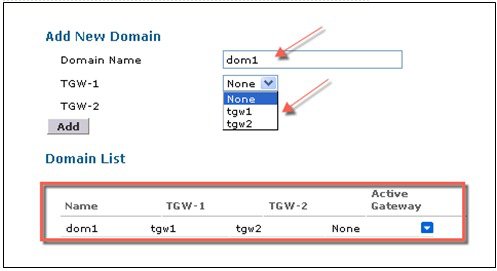
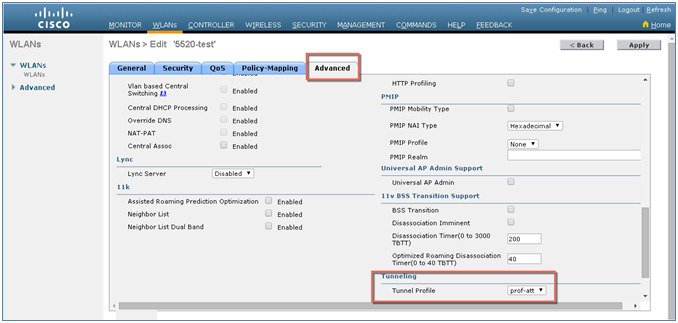
To configure the WLC EoGRE tunnel through GUI, perform the following steps:
Typical Deployment: WLC EoGRE Topology
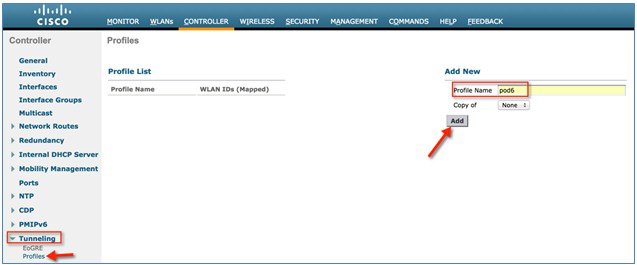
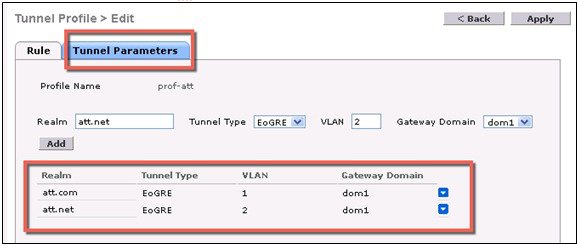
ProcedureIn this typical EoGRE deployment configuration, two users MN1 and MN2 are connected to Realm @att.com and two other users MN3 and MN4 are connected to Realm @att.net. When the users MN1 and MN2 connect, they must be on the VLAN1 and TGW1 and users MN3 and MN4 must connect to VLAN2 and TGW2 as shown in the following figure. In this setup, two profiles with one realm in each are created and mapped to TGW1 and TGW2 accordingly in the same domain.
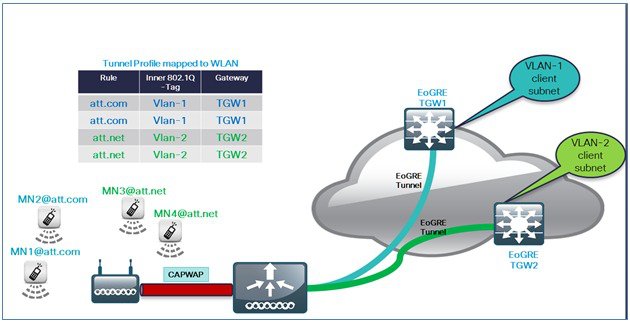
To configure WLC EoGRE, perform the following steps:
Design 2: FlexConnect AP based EoGRE Tunnel
CAPWAP Control Path (Flex AP-WLC)
EoGRE Data Path (Flex AP-TGW)
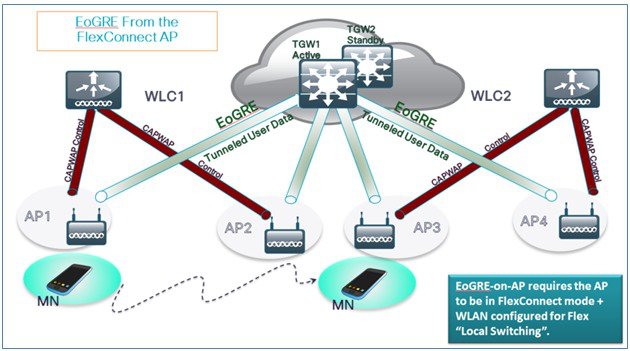
Once tunnel is established, data flows from FC AP directly to the TGW.
In this design, direct tunneling from the AP offers data and control planes separation from the controller and the AP. The central data throughput is limited only by the capacity of the core network with optimal data-path routing towards the core of the network. The inter/intra controller mobility is not supported but client can still roam in the same FlexConnect group in Locally Switched mode.
FlexConnect AP – EoGRE is supported on Open and 802.1x based WLANs.
802.1x authenticated “simple” and “tunneled” EoGRE clients are supported on the same WLAN.
Based on authentication, clients are separated into local or tunneled mode.
Tunneled clients support EAP-SIM or EAP-AKA modes.
Open SSID WLAN supports either all local or all tunneled clients.
AAA override for EoGRE users is supported.
Tunnel GW can also act as AAA proxy.
Flex Connect AP supports TGW failure detection and switch over to alternate TGW.
TGW supports Fault Tolerance with Active/Standby mode.
Inter and Intra Controller mobility is supported in connected FlexAP mode.
In Stand-Alone mode, mobility supported only within FlexConnect group tunnel GW can be configured as AAA and Accounting proxy.
Tunnel GW supports “Configurable” DHCP Option-82.
Basic Flex AP EoGRE Configuration
When configuring Flex AP with EoGRE tunnel:
Same tunnel configurations apply to WLC or FC AP tunnels when profile is applied on the WLAN.
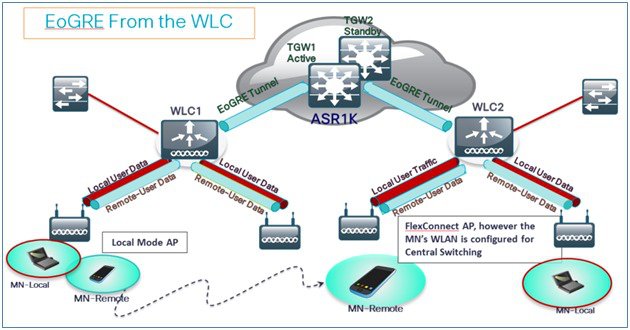
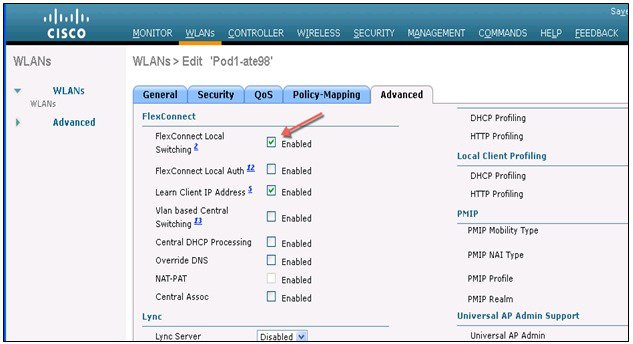
When FC AP is in Locally Switched mode, the FC AP gateway tunnel automatically applies.
Clients connected to Local Mode AP communicates through the WLC-TGW tunnel.
Clients connected to FC AP communicates through the FC AP-TGW tunnel.
Client selection is also impacted by the AAA or Profile override.
Note
In redundancy tunnel configuration mode, the keep-alive pings will be sent from every FC AP that is configured in the EoGRE tunnel mode.
Typical Deployment: Flex Connect AP - EoGRE Topology
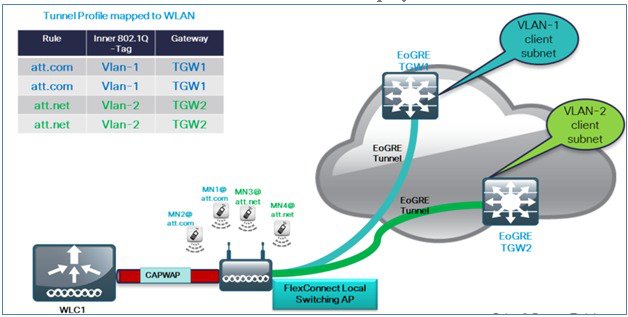
In this typical FC AP -EoGRE tunnel deployment configuration, two users MN1 and MN2 are connected to Realm @att.com and two other users MN3 and MN4 are connected to Realm @att.net. When users MN1 and MN2 connect, they should be on the VLAN1 and TGW1 and users MN3 and MN4 should connect to VLAN-2 and TGW2 as shown in the following figure. In this setup, two profiles with one realm in each will be created and mapped to TGW1 and TGW2 accordingly in the same domain. In this deployment scenario, the tunnel will be setup directly between FlexConnect AP in a Locally switched mode and TGW1 and TGW2; all data traffic will flow bypassing the controller.
Note
In this configuration, EoGRE tunnel TGW, Domain, Profile Rules, and Realms are setup exactly in the same manner as in the deployment scenario with WLC-EoGRE. The only change is FC AP is setup in the Locally Switched mode.
Note
Only FlexConnect Local Switching option has to be configured on the FG AP or FC Group to enable FC AP-TGW tunnel. Other WLC EoGRE configurations will apply to FC AP-EoGRE settings.
Show Commands
Show Commands on WLC
Show tunnel eogre summary
show tunnel eogre gateway summary
show tunnel eogre domain summary
show tunnel profile summary
show tunnel profile detail <profile name>
show ap eogre domain <ap-name>
Show ap eogre gateway <ap-name>
Show Commands on AP
show dot11 eogre-tunnel domain summary
show dot11 eogre-tunnel gateway summary
show capwap reap associations
show capwap client detailrcb
Example Configuration of the EoGRE Feature
Sample Configuration on ASR 1K
aaa new-model
!
aaa group server radius AAA_SERVER_CAR
server-private 5.3.1.76 auth-port 2145 acct-port 2146 key cisco
!
aaa authentication login default none
aaa authentication login ISG_PROXY_LIST group AAA_SERVER_CAR
aaa authorization network ISG_PROXY_LIST group AAA_SERVER_CAR
aaa authorization subscriber-service default local group AAA_SERVER_CAR
aaa accounting network PROXY_TO_CAR
action-type start-stop
group AAA_SERVER_CAR
!
aaa accounting network ISG_PROXY_LIST start-stop group AAA_SERVER_CAR
!
Intelligent Wireless Access Gateway Configuration Guide
46 OL-30226-06
Service Provider WiFi: Support for Integrated Ethernet Over GRE
Example: Configuring the EoGRE Feature
aaa server radius dynamic-author
client 5.3.1.76 server-key cisco
auth-type any
ignore server-key
!!
ip dhcp excluded-address 172.16.254.254
!
ip dhcp pool ISG_SIMPLE_IP
network 172.16.0.0 255.255.0.0
default-router 172.16.254.254
domain-name cisco.com
!
policy-map type control EOGRE_L2_ISG
class type control always event session-start
2 authorize aaa list ISG_PROXY_LIST password cisco identifier mac-address
4 set-timer IP_UNAUTH_TIMER 5
!
class type control always event service-start
1 service-policy type service identifier service-name
2 collect identifier nas-port
!
!
interface Loopback0
ip address 9.9.9.9 255.255.255.255
interface GigabitEthernet1/0/0
ip address 192.168.0.9 255.255.255.0
negotiation auto
!
interface GigabitEthernet1/0/0.778
description "to ASR5K GGSN"
encapsulation dot1Q 778
ip address 172.16.199.9 255.255.255.0
!
interface Tunnel10
description "EoGRE Tunnel for Simple IP subscribers"
mac-address 0000.5e00.5213
ip address 172.16.254.254 255.255.0.0
no ip redirects
tunnel source 172.16.199.9
tunnel mode ethernet gre ipv4
service-policy type control EOGRE_L2_ISG
ip subscriber l2-connected
initiator unclassified mac-address
initiator dhcp
interface Tunnel100
description "IPv4 EoGRE Tunnel for PMIP/GTP subscribers"
ip unnumbered Loopback0
tunnel source GigabitEthernet1/0/0
tunnel mode ethernet gre ipv4
tunnel vlan 100
service-policy type control EOGRE_L2_ISG
ip subscriber l2-connected
initiator unclassified mac-address
initiator dhcp
!
interface Tunnel200
description "IPv6 EoGRE Tunnel for PMIP/GTP subscribers"
ip unnumbered Loopback0
tunnel source 2001:161::9
tunnel mode ethernet gre ipv6
tunnel vlan 200
service-policy type control EOGRE_L2_ISG
ip subscriber l2-connected
initiator unclassified mac-address
initiator dhcp
!
mcsa
enable sessionmgr
!
ipv6 mobile pmipv6-domain D1
replay-protection timestamp window 255
lma LMA_5K
Intelligent Wireless Access Gateway Configuration Guide
OL-30226-06 47
Service Provider WiFi: Support for Integrated Ethernet Over GRE
Example: Configuring the EoGRE Feature
ipv4-address 192.168.199.1
!
ipv6 mobile pmipv6-mag M1 domain D1
sessionmgr
role 3GPP
address ipv4 9.9.9.9
interface Tunnel100
interface Tunnel200
lma LMA_5K D1
ipv4-address 192.168.199.1
encap gre-ipv4
!
ntp master
!
gtp
information-element rat-type wlan
interface local GigabitEthernet1/0/0.778
apn 1
apn-name gtp.com
ip address ggsn 172.16.199.1
fixed link-layer address 00ab.00cd.00ef
default-gw 20.100.254.254 prefix-len 16
dns-server 20.100.254.254
dhcp-server 20.100.254.254
!
end
You can use the following commands to check and show subscriber session information:
show ip dhcp sip statistics
show subscriber statistics
show subscriber session
show ipv6 mobile pmipv6 mag binding
show gtp pdp-context all
show interface tunnel-name
Copyright © 2015, Cisco Systems, Inc. All rights reserved.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)






 Feedback
Feedback