Validación de Intelligent Traffic Director mediante el método IP de origen
Lenguaje no discriminatorio
El conjunto de documentos para este producto aspira al uso de un lenguaje no discriminatorio. A los fines de esta documentación, "no discriminatorio" se refiere al lenguaje que no implica discriminación por motivos de edad, discapacidad, género, identidad de raza, identidad étnica, orientación sexual, nivel socioeconómico e interseccionalidad. Puede haber excepciones en la documentación debido al lenguaje que se encuentra ya en las interfaces de usuario del software del producto, el lenguaje utilizado en función de la documentación de la RFP o el lenguaje utilizado por un producto de terceros al que se hace referencia. Obtenga más información sobre cómo Cisco utiliza el lenguaje inclusivo.
Acerca de esta traducción
Cisco ha traducido este documento combinando la traducción automática y los recursos humanos a fin de ofrecer a nuestros usuarios en todo el mundo contenido en su propio idioma. Tenga en cuenta que incluso la mejor traducción automática podría no ser tan precisa como la proporcionada por un traductor profesional. Cisco Systems, Inc. no asume ninguna responsabilidad por la precisión de estas traducciones y recomienda remitirse siempre al documento original escrito en inglés (insertar vínculo URL).
Introducción
Este documento describe la manera de verificar tanto el plano de control como el plano de datos de Intelligent Traffic Director (ITD) en la plataforma Nexus 9K.
Prerequisites
Requirements
Cisco recomienda que tenga conocimiento sobre estos temas:
- Software Nexus NX-OS.
- Lista de acceso (ACL).
- Acuerdo de nivel de servicio de IP (IP SLA).
- Routing basado en políticas (PBR).
- Intelligent Traffic Director (ITD).
Componentes Utilizados
La información de este documento se basa en Cisco Nexus 9000 con NXOS versión 10.2(5).
La información que contiene este documento se creó a partir de los dispositivos en un ambiente de laboratorio específico. Todos los dispositivos que se utilizan en este documento se pusieron en funcionamiento con una configuración verificada (predeterminada). Si tiene una red en vivo, asegúrese de entender el posible impacto de cualquier comando.
Configurar
ITD es una solución inteligente, basada en hardware y de varios terabits que le permite crear una arquitectura escalable para la distribución, el equilibrio de carga y la redirección del tráfico de las capas 3 y 4.
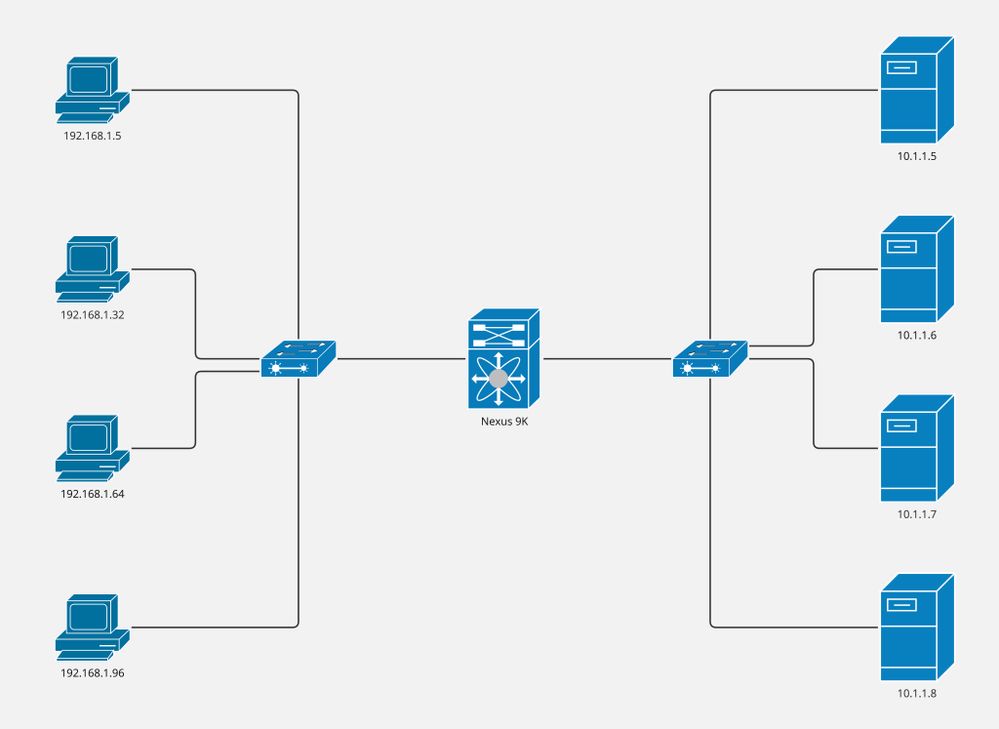
Diagrama de la red
- Ordenadores: 4
- Servidores: 4
- Switches de capa 2: 2
- Switches Nexus 9000: 1

Nota: los switches de capa 2 combinan la conexión entre servidores/ordenadores y los switches Nexus 9000, donde se ejecuta ITD.
Configuraciones
Esta configuración se implementa en el switch Nexus 9000 y solo cubre la parte ITD. Los ordenadores forman parte de la VLAN 5 y los servidores forman parte de la VLAN 10, mientras que Nexus 9K es el gateway de ambas VLAN.
Paso 1. Active las funciones necesarias.
feature itd
feature sla sender
feature sla responder
feature pbrPaso 2. Defina el grupo de dispositivos, señalando a los nodos, e indique el método de sondeo.
itd device-group CiscoGroup
probe icmp frequency 5 timeout 5 retry-down-count 2 retry-up-count 2
node ip 10.1.1.5
node ip 10.1.1.6
node ip 10.1.1.7
node ip 10.1.1.8Paso 3. Defina el servicio. Los usuarios pueden indicar una IP virtual o incluir una lista de acceso.

Nota: NX-OS divide el último octeto por el número de bloques indicados. Para este ejemplo, dividimos 256 entre 8. Por lo tanto, cada cubeta incluye 32 hosts.
Bucket 1: From x.x.x.0 to x.x.x.31
Bucket 2: From x.x.x.32 to x.x.x.63
Bucket 3: From x.x.x.64 to x.x.x.95
Bucket 4: From x.x.x.96 to x.x.x.127
Bucket 5: From x.x.x.128 to x.x.x.159
Bucket 6: From x.x.x.160 to x.x.x.191
Bucket 7: From x.x.x.192 to x.x.x.223
Bucket 8: From x.x.x.224 to x.x.x.255itd CiscoService
device-group CiscoGroup
virtual ip 192.168.255.1 255.255.255.255 advertise enable
ingress interface Vlan5
failaction node reassign
load-balance method src ip buckets 8
no shutPaso 4. Habilitar estadísticas para el servicio definido.
itd statistics CiscoServiceVerificación
1. Confirme que el servicio ITD está activo y que el estado del nodo es correcto.
Nexus# show itd CiscoService brief
Legend:
C-S(Config-State): A-Active,S-Standby,F-Failed
ST(Status): ST-Standby,LF-Link Failed,PF-Probe Failed,PD-Peer Down,IA-Inactive,SH-Shut,HD-Hold-down
Name LB Scheme Status Buckets Interface
-------------- ---------- -------- --------- --------------
CiscoService src-ip ACTIVE 8 Vlan5
Source Interface
----------------
Device Group Probe Port VRF
-------------------------------------------------- ----- ------ ---------
CiscoGroup ICMP
Virtual IP Netmask/Prefix Protocol Port
------------------------------------------------------ ------------ ----------
192.168.255.1 / 255.255.255.255 IP 0
Node IP Cluster-id C-S WGT Probe Port Probe-IP STS
------------------------- ---------- -- --- ---- ----- --------------- --
1 10.1.1.5 A 1 ICMP OK
2 10.1.1.6 A 1 ICMP OK
3 10.1.1.7 A 1 ICMP OK
4 10.1.1.8 A 1 ICMP OK2. Confirme que la política de ruta se creó y se asoció con la interfaz de ingreso.

Nota: La política de ruta se aplica en running-config (bajo la interfaz de ingreso) hasta NXOS 10.1(2), a partir de NXOS 10.2(1) puede encontrar la política de ruta asociada en el sistema con el comando show ip policy.
Nexus# show ip policy
Interface Route-map Status VRF-Name
Vlan5 CiscoService_itd_pool Active default
3. Confirme que el route-map se generó correctamente, asociado con los nodos esperados, e indique el seguimiento (IP SLA).

Nota: Se espera que tenga una entrada de mapa de rutas por cubeta.
Se espera que tenga una pista por nodo.
Nexus# show route-map dynamic CiscoService_itd_pool
route-map CiscoService_itd_pool, permit, sequence 10
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_1
Set clauses:
ip next-hop verify-availability 10.1.1.5 track 2 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 11
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_2
Set clauses:
ip next-hop verify-availability 10.1.1.6 track 3 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 12
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_3
Set clauses:
ip next-hop verify-availability 10.1.1.7 track 4 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 13
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_4
Set clauses:
ip next-hop verify-availability 10.1.1.8 track 5 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 14
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_5
Set clauses:
ip next-hop verify-availability 10.1.1.5 track 2 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 15
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_6
Set clauses:
ip next-hop verify-availability 10.1.1.6 track 3 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 16
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_7
Set clauses:
ip next-hop verify-availability 10.1.1.7 track 4 [ UP ] force-order
route-map CiscoService_itd_pool, permit, sequence 17
Match clauses:
ip address (access-lists): CiscoService_itd_vip_1_bucket_8
Set clauses:
ip next-hop verify-availability 10.1.1.8 track 5 [ UP ] force-order 4. La lista de acceso de confirmación se generó correctamente y tiene la condición de coincidencia de IP esperada.

Nota: Las ACL se generan en running-config hasta NXOS 9.3(2), a partir de NXOS 9.3(3) podemos encontrar ACL en el sistema mediante el comando show ip access-list dynamic.
Nexus# show ip access-lists CiscoService_itd_vip_1_bucket_1 dynamic
IP access list CiscoService_itd_vip_1_bucket_1
10 permit ip 1.1.1.0 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_2 dynamic
IP access list CiscoService_itd_vip_1_bucket_2
10 permit ip 1.1.1.32 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_3 dynamic
IP access list CiscoService_itd_vip_1_bucket_3
10 permit ip 1.1.1.64 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_4 dynamic
IP access list CiscoService_itd_vip_1_bucket_4
10 permit ip 1.1.1.96 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_5 dynamic
IP access list CiscoService_itd_vip_1_bucket_5
10 permit ip 1.1.1.128 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_6 dynamic
IP access list CiscoService_itd_vip_1_bucket_6
10 permit ip 1.1.1.160 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_7 dynamic
IP access list CiscoService_itd_vip_1_bucket_7
10 permit ip 1.1.1.192 255.255.255.31 192.168.255.1/32
513E-A-15-C9336C-FX-2-1# show ip access-lists CiscoService_itd_vip_1_bucket_8 dynamic
IP access list CiscoService_itd_vip_1_bucket_8
10 permit ip 1.1.1.224 255.255.255.31 192.168.255.1/32 5. Asegúrese de que las listas de acceso estén programadas en TCAM.
Nexus# show system internal access-list input entries detail | begin "VLAN 5"
VLAN 5 :
=========
INSTANCE 0x0
---------------
Tcam 1 resource usage:
----------------------
LBL B = 0x1
Bank 1
------
IPv4 Class
Policies: PBR(CiscoService_itd_vip_1_bucket_8)
Netflow profile: 0
Netflow deny profile: 0
Entries:
[Index] Entry [Stats]
---------------------
[0x0000:0x0002:0x0002] permit ip 0.0.0.0/0 224.0.0.0/4 routeable 0x1 [0]
[0x0002:0x0004:0x0004] permit ip 0.0.0.0/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0003:0x0005:0x0005] permit ip 0.0.0.32/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0004:0x0006:0x0006] permit ip 0.0.0.64/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0005:0x0007:0x0007] permit ip 0.0.0.96/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000b:0x000d:0x000d] permit ip 0.0.0.128/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000c:0x000e:0x000e] permit ip 0.0.0.160/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000d:0x000f:0x000f] permit ip 0.0.0.192/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000e:0x0010:0x0010] permit ip 0.0.0.224/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000f:0x0011:0x0011] permit ip 0.0.0.0/0 0.0.0.0/0 routeable 0x1 [0]
L4 protocol cam entries usage: none
No mac protocol cam entries are in use
INSTANCE 0x1
---------------
Tcam 1 resource usage:
----------------------
LBL B = 0x1
Bank 1
------
IPv4 Class
Policies: PBR(CiscoService_itd_vip_1_bucket_8)
Netflow profile: 0
Netflow deny profile: 0
Entries:
[Index] Entry [Stats]
---------------------
[0x0000:0x0002:0x0002] permit ip 0.0.0.0/0 224.0.0.0/4 routeable 0x1 [0]
[0x0002:0x0004:0x0004] permit ip 0.0.0.0/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0003:0x0005:0x0005] permit ip 0.0.0.32/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0004:0x0006:0x0006] permit ip 0.0.0.64/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x0005:0x0007:0x0007] permit ip 0.0.0.96/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000b:0x000d:0x000d] permit ip 0.0.0.128/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000c:0x000e:0x000e] permit ip 0.0.0.160/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000d:0x000f:0x000f] permit ip 0.0.0.192/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000e:0x0010:0x0010] permit ip 0.0.0.224/0.0.0.224 192.168.255.1/32 routeable 0x1 [0]
[0x000f:0x0011:0x0011] permit ip 0.0.0.0/0 0.0.0.0/0 routeable 0x1 [0]
L4 protocol cam entries usage: none
No mac protocol cam entries are in use6. Envíe el tráfico a la dirección IP virtual y confirme el aumento de los contadores (número de paquetes) para el nodo esperado.
Nexus# show itd CiscoService statistics
Service Device Group VIP/mask #Packets
-------------------------------------------------------------------------------------------------------------------------------------------
CiscoService CiscoGroup 192.168.255.1 / 255.255.255.255 0 (0%)
Traffic Bucket Assigned to Mode Original Node #Packets
--------------- -------------- ----- -------------- ---------
CiscoService_itd_vip_1_bucket_1 10.1.1.5 Redirect 10.1.1.5 0 (0%)
CiscoService_itd_vip_1_bucket_5 10.1.1.5 Redirect 10.1.1.5 0 (0%)
Traffic Bucket Assigned to Mode Original Node #Packets
--------------- -------------- ----- -------------- ---------
CiscoService_itd_vip_1_bucket_2 10.1.1.6 Redirect 10.1.1.6 0 (0%)
CiscoService_itd_vip_1_bucket_6 10.1.1.6 Redirect 10.1.1.6 0 (0%)
Traffic Bucket Assigned to Mode Original Node #Packets
--------------- -------------- ----- -------------- ---------
CiscoService_itd_vip_1_bucket_3 10.1.1.7 Redirect 10.1.1.7 0 (0%)
CiscoService_itd_vip_1_bucket_7 10.1.1.7 Redirect 10.1.1.7 0 (0%)
Traffic Bucket Assigned to Mode Original Node #Packets
--------------- -------------- ----- -------------- ---------
CiscoService_itd_vip_1_bucket_4 10.1.1.8 Redirect 10.1.1.8 0 (0%)
CiscoService_itd_vip_1_bucket_8 10.1.1.8 Redirect 10.1.1.8 0 (0%)Historial de revisiones
| Revisión | Fecha de publicación | Comentarios |
|---|---|---|
1.0 |
21-Jul-2023 |
Versión inicial |
Con la colaboración de ingenieros de Cisco
- Bidkar Herson Paez LamponTechnical Consulting Engineer
Contacte a Cisco
- Abrir un caso de soporte

- (Requiere un Cisco Service Contract)
 Comentarios
Comentarios