Configurazione della DMVPN gerarchica fase 3 con spoke multi-subnet
Opzioni per il download
Linguaggio senza pregiudizi
La documentazione per questo prodotto è stata redatta cercando di utilizzare un linguaggio senza pregiudizi. Ai fini di questa documentazione, per linguaggio senza di pregiudizi si intende un linguaggio che non implica discriminazioni basate su età, disabilità, genere, identità razziale, identità etnica, orientamento sessuale, status socioeconomico e intersezionalità. Le eventuali eccezioni possono dipendere dal linguaggio codificato nelle interfacce utente del software del prodotto, dal linguaggio utilizzato nella documentazione RFP o dal linguaggio utilizzato in prodotti di terze parti a cui si fa riferimento. Scopri di più sul modo in cui Cisco utilizza il linguaggio inclusivo.
Informazioni su questa traduzione
Cisco ha tradotto questo documento utilizzando una combinazione di tecnologie automatiche e umane per offrire ai nostri utenti in tutto il mondo contenuti di supporto nella propria lingua. Si noti che anche la migliore traduzione automatica non sarà mai accurata come quella fornita da un traduttore professionista. Cisco Systems, Inc. non si assume alcuna responsabilità per l’accuratezza di queste traduzioni e consiglia di consultare sempre il documento originale in inglese (disponibile al link fornito).
Sommario
Introduzione
In questo documento viene illustrato come configurare una DMVPN (Hierarchical Dynamic Multipoint VPN) di fase 3 con spoke multi-subnet.
Prerequisiti
Requisiti
Cisco raccomanda la conoscenza dei seguenti argomenti:
Nota: per la DMVPN gerarchica con spoke multi-subnet, verificare che i router abbiano risolto il bug di CSCug42027. Con i router che eseguono la versione IOS senza la correzione di CSCug42027 , quando il tunnel spoke-to-spoke viene formato tra gli spoke in subnet diverse, il traffico spoke-to-spoke fallisce.
CSCug42027 viene risolto nelle seguenti versioni IOS e IOS-XE:
- 15.3(3)S / 3.10 e successive.
- 15.4(3)M e versioni successive.
- 15.4(1)T e successive.
Componenti usati
Le informazioni di questo documento si basano sulle seguenti versioni hardware e software:
- Cisco 2911 Integrated Services Router con Cisco IOS® versione 15.5(2)T
Le informazioni discusse in questo documento fanno riferimento a dispositivi usati in uno specifico ambiente di emulazione. Su tutti i dispositivi menzionati nel documento la configurazione è stata ripristinata ai valori predefiniti. Se la rete è operativa, valutare attentamente eventuali conseguenze derivanti dall'uso dei comandi.
Premesse
L'impostazione gerarchica (più di un livello) consente topologie di rete DMVPN basate su albero più complesse. Le topologie basate su albero consentono di creare reti DMVPN con hub regionali che sono spoke di hub centrali. Questa architettura consente all'hub regionale di gestire i dati e al protocollo NHRP (Next Hop Resolution Protocol) di controllare il traffico per i relativi spoke regionali. Tuttavia, consente ancora di costruire tunnel spoke tra qualsiasi spoke all'interno della rete DMVPN, sia che si trovino nella stessa regione o meno. Questa architettura consente inoltre al layout di rete DMVPN di avvicinarsi maggiormente ai modelli di flusso di dati regionali o gerarchici.
Configurazione
In questa sezione vengono presentate le informazioni necessarie per configurare le funzionalità descritte più avanti nel documento.
Esempio di rete
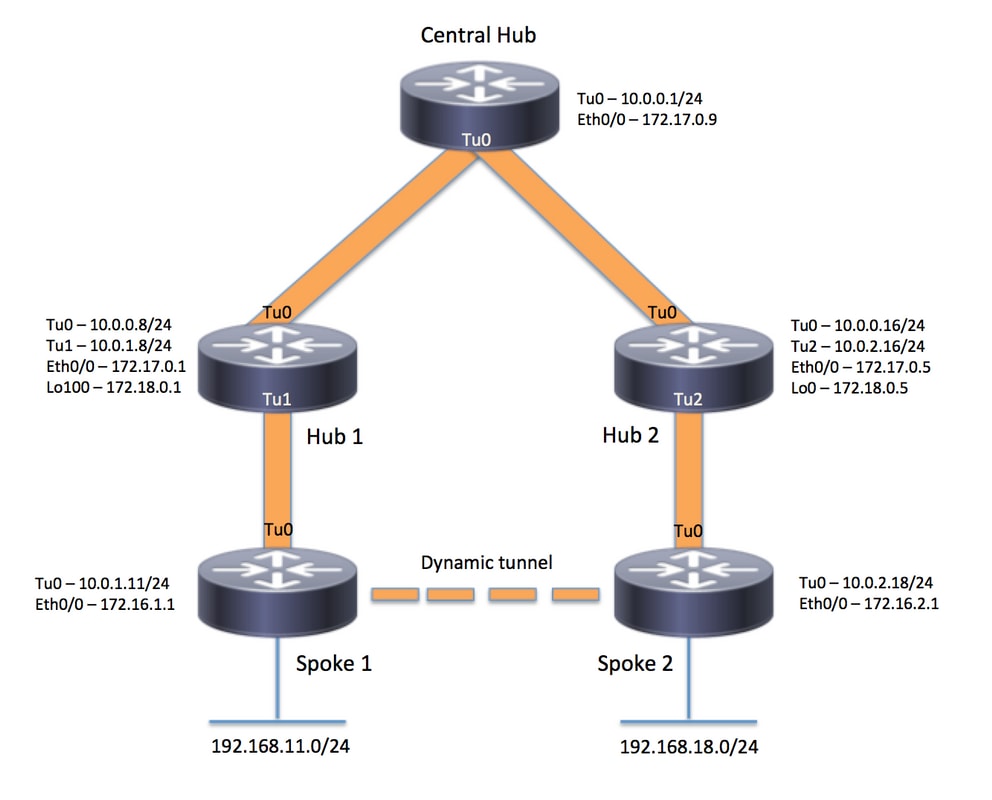
Configurazioni
Nota: in questo esempio vengono incluse solo le sezioni rilevanti della configurazione.
Hub centrale (Hub0)
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname central_hub
!
crypto isakmp policy 1
encr aes 256
hash sha256
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0
!
crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac
mode transport
!
crypto ipsec profile profile-dmvpn
set transform-set transform-dmvpn
!
interface Loopback1
ip address 192.168.1.1 255.255.255.0
!
interface Tunnel0
bandwidth 1000
ip address 10.0.0.1 255.255.255.0
no ip redirects
ip mtu 1400
no ip split-horizon eigrp 1
ip nhrp authentication test
ip nhrp map multicast dynamic
ip nhrp network-id 100000
ip nhrp shortcut
ip nhrp redirect
ip summary-address eigrp 1 192.168.0.0 255.255.192.0
ip tcp adjust-mss 1360
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 100000
tunnel protection ipsec profile profile-dmvpn
!
interface Ethernet0/0
ip address 172.17.0.9 255.255.255.252
!
router eigrp 1
network 10.0.0.0 0.0.0.255
network 192.168.1.0
!
ip route 0.0.0.0 0.0.0.0 172.17.0.10
!
end
Hub Regione 1 (Hub 1)
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname hub_1
!
crypto isakmp policy 1
encr aes 256
hash sha256
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0
!
crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac
mode transport
!
crypto ipsec profile profile-dmvpn
set transform-set transform-dmvpn
!
crypto ipsec profile profile-dmvpn-1
set transform-set transform-dmvpn
!
interface Loopback1
ip address 192.168.8.1 255.255.255.0
!
interface Loopback100
ip address 172.18.0.1 255.255.255.252
!
interface Tunnel0
bandwidth 1000
ip address 10.0.0.8 255.255.255.0
no ip redirects
ip mtu 1400
no ip split-horizon eigrp 1
ip nhrp authentication test
ip nhrp network-id 100000
ip nhrp nhs 10.0.0.1 nbma 172.17.0.9 multicast
ip nhrp shortcut
ip nhrp redirect
ip summary-address eigrp 1 192.168.8.0 255.255.248.0
ip tcp adjust-mss 1360
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 100000
tunnel protection ipsec profile profile-dmvpn
!
interface Tunnel1
bandwidth 1000
ip address 10.0.1.8 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication test
ip nhrp map multicast dynamic
ip nhrp network-id 100000
ip nhrp redirect
ip summary-address eigrp 1 192.168.8.0 255.255.248.0
ip summary-address eigrp 1 192.168.100.0 255.255.252.0
ip tcp adjust-mss 1360
tunnel source Loopback100
tunnel mode gre multipoint
tunnel key 100000
tunnel protection ipsec profile profile-dmvpn-1
!
interface Ethernet0/0
ip address 172.17.0.1 255.255.255.252
!
router eigrp 1
network 10.0.0.0 0.0.0.255
network 10.0.1.0 0.0.0.255
network 192.168.8.0
!
ip route 0.0.0.0 0.0.0.0 172.17.0.2
!
end
Hub Regione 2 (Hub 2)
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname hub_2
!
crypto isakmp policy 1
encr aes 256
hash sha256
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0
!
crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac
mode transport
!
crypto ipsec profile profile-dmvpn
set transform-set transform-dmvpn
!
crypto ipsec profile profile-dmvpn-1
set transform-set transform-dmvpn
!
interface Loopback0
ip address 172.18.0.5 255.255.255.252
!
interface Loopback1
ip address 192.168.16.1 255.255.255.0
!
interface Tunnel0
bandwidth 1000
ip address 10.0.0.16 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication test
ip nhrp network-id 100000
ip nhrp holdtime 360
ip nhrp nhs 10.0.0.1 nbma 172.17.0.9 multicast
ip nhrp shortcut
ip nhrp redirect
ip summary-address eigrp 1 192.168.16.0 255.255.248.0
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 100000
tunnel protection ipsec profile profile-dmvpn
!
interface Tunnel2
bandwidth 1000
ip address 10.0.2.16 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication test
ip nhrp map multicast dynamic
ip nhrp network-id 100000
ip nhrp holdtime 360
ip nhrp redirect
ip summary-address eigrp 1 192.168.16.0 255.255.248.0
ip summary-address eigrp 1 192.168.100.0 255.255.252.0
tunnel source Loopback0
tunnel mode gre multipoint
tunnel key 100000
tunnel protection ipsec profile profile-dmvpn-1
!
interface Ethernet0/0
ip address 172.17.0.5 255.255.255.252
!
router eigrp 1
network 10.0.0.0 0.0.0.255
network 10.0.2.0 0.0.0.255
network 192.168.16.0
!
ip route 0.0.0.0 0.0.0.0 172.17.0.6
!
end
Raggio regione 1 (Raggio 1)
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname spoke_1
!
crypto isakmp policy 1
encr aes 256
hash sha256
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0
crypto isakmp keepalive 10
!
crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac
mode transport
!
crypto ipsec profile profile-dmvpn
set transform-set transform-dmvpn
!
interface Loopback1
ip address 192.168.11.1 255.255.255.0
!
interface Tunnel0
bandwidth 1000
ip address 10.0.1.11 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication test
ip nhrp network-id 100000
ip nhrp nhs 10.0.1.8 nbma 172.18.0.1 multicast
ip nhrp shortcut
ip tcp adjust-mss 1360
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 100000
tunnel protection ipsec profile profile-dmvpn
!
interface Ethernet0/0
ip address 172.16.1.1 255.255.255.252
!
router eigrp 1
network 10.0.0.0 0.0.0.255
network 10.0.1.0 0.0.0.255
network 192.168.11.0
!
ip route 0.0.0.0 0.0.0.0 172.16.1.2
!
end
Regione 2 raggio (raggio 2)
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname spoke_2
!
crypto isakmp policy 1
encr aes 256
hash sha256
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0
crypto isakmp keepalive 10
!
crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac
mode transport
!
crypto ipsec profile profile-dmvpn
set transform-set transform-dmvpn
!
interface Loopback1
ip address 192.168.18.1 255.255.255.0
!
interface Tunnel0
bandwidth 1000
ip address 10.0.2.18 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication test
ip nhrp network-id 100000
ip nhrp nhs 10.0.2.16 nbma 172.18.0.5 multicast
ip nhrp shortcut
ip tcp adjust-mss 1360
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 100000
tunnel protection ipsec profile profile-dmvpn
!
interface Ethernet0/0
ip address 172.16.2.1 255.255.255.252
!
router eigrp 1
network 10.0.2.0 0.0.0.255
network 192.168.18.0
!
ip route 0.0.0.0 0.0.0.0 172.16.2.2
!
end
Informazioni sul flusso di pacchetti dati e NHRP
In questa immagine viene mostrato il primo flusso di pacchetti di dati seguito dal flusso di richiesta e risposta alla risoluzione NHRP:

Flusso del primo pacchetto dati
Passaggio 1. Ping ICMP avviato dal raggio 1, destinazione = 192.168.18.10, origine = 192.168.11.1
- Ricerca route completata per 192.168.18.10. Come mostrato di seguito, l'hop successivo è 10.0.1.8 (indirizzo tunnel dell'hub 1)
- La ricerca nella cache NHRP viene eseguita per la destinazione 192.168.18.10 su Tunnel0, ma in questa fase non viene trovata alcuna voce.
- La ricerca nella cache NHRP viene eseguita per l'hop successivo, ad esempio 10.0.1.8 su Tunnel0. Come mostrato di seguito, la voce è presente e la sessione di crittografia è attiva.
- Il pacchetto di richiesta echo ICMP viene inoltrato all'hop successivo, ad esempio Hub1, sul tunnel esistente.
spoke_1#show ip route 192.168.18.10
Routing entry for 192.168.0.0/18, supernet
Known via "eigrp 1", distance 90, metric 5248000, type internal
Redistributing via eigrp 1
Last update from 10.0.1.8 on Tunnel0, 02:30:37 ago
Routing Descriptor Blocks:
* 10.0.1.8, from 10.0.1.8, 02:30:37 ago, via Tunnel0
Route metric is 5248000, traffic share count is 1
Total delay is 105000 microseconds, minimum bandwidth is 1000 Kbit
Reliability 255/255, minimum MTU 1400 bytes
Loading 1/255, Hops 2
spoke_1#show ip nhrp
10.0.1.8/32 via 10.0.1.8
Tunnel0 created 02:31:32, never expire
Type: static, Flags: used
NBMA address: 172.18.0.1
Passaggio 2. Pacchetto ICMP ricevuto sull'hub 1
- Ricerca route completata per 192.168.18.10. L'hop successivo è 10.0.0.1 (indirizzo tunnel dell'hub 0).
- Poiché l'hub 1 non è il punto di uscita e il pacchetto deve essere inoltrato a un'altra interfaccia all'interno dello stesso cloud DMVPN, l'hub 1 invia un indiretto/reindirizzamento NHRP al spoke 1.
- Allo stesso tempo, il pacchetto di dati viene inoltrato all'hub0.
*Apr 13 19:06:07.592: NHRP: Send Traffic Indication via Tunnel1 vrf 0, packet size: 96
*Apr 13 19:06:07.592: src: 10.0.1.8, dst: 192.168.11.1
*Apr 13 19:06:07.592: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Apr 13 19:06:07.592: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.592: pktsz: 96 extoff: 68
*Apr 13 19:06:07.592: (M) traffic code: redirect(0)
*Apr 13 19:06:07.592: src NBMA: 172.18.0.1
*Apr 13 19:06:07.592: src protocol: 10.0.1.8, dst protocol: 192.168.11.1
*Apr 13 19:06:07.592: Contents of nhrp traffic indication packet:
*Apr 13 19:06:07.592: 45 00 00 64 00 01 00 00 FE 01 1E 3C C0 A8 0B 01
*Apr 13 19:06:07.592: C0 A8 12 0A 08 00 A1 C8 00 01 00
Passaggio 3. Pacchetto ICMP ricevuto sull'hub 0
- Ricerca route completata per 192.168.18.10. L'hop successivo è 10.0.0.16 (indirizzo tunnel dell'hub 2) su Tunnel0
- Poiché l'hub 0 non è il punto di uscita e il pacchetto deve essere inoltrato nuovamente alla stessa cloud DMVPN tramite la stessa interfaccia, l'hub 0 invia il riferimento indiretto NHRP al spoke 1 all'hub 1.
- Il pacchetto dati viene inoltrato all'hub 2.
*Apr 13 19:06:07.591: NHRP: Send Traffic Indication via Tunnel0 vrf 0, packet size: 96
*Apr 13 19:06:07.591: src: 10.0.0.1, dst: 192.168.11.1
*Apr 13 19:06:07.591: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Apr 13 19:06:07.591: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.591: pktsz: 96 extoff: 68
*Apr 13 19:06:07.591: (M) traffic code: redirect(0)
*Apr 13 19:06:07.591: src NBMA: 172.17.0.9
*Apr 13 19:06:07.591: src protocol: 10.0.0.1, dst protocol: 192.168.11.1
*Apr 13 19:06:07.592: Contents of nhrp traffic indication packet:
*Apr 13 19:06:07.592: 45 00 00 64 00 01 00 00 FD 01 1F 3C C0 A8 0B 01
*Apr 13 19:06:07.592: C0 A8 12 0A 08 00 A1 C8 00 01 00
Passaggio 4. Pacchetto ICMP ricevuto sull'hub 2
- Ricerca route completata per 192.168.18.10. L'hop successivo è 10.0.2.18 (indirizzo tunnel di Spoke2) su Tunnel2
- Poiché l'hub 2 non è il punto di uscita e il pacchetto deve essere inoltrato a un'altra interfaccia all'interno dello stesso cloud DMVPN, l'hub 2 invia il riferimento indiretto NHRP al spoke 1 attraverso l'hub 0.
- Il pacchetto di dati viene inoltrato al raggio 2.
*Apr 13 19:06:07.592: NHRP: Send Traffic Indication via Tunnel0 vrf 0, packet size: 96
*Apr 13 19:06:07.593: src: 10.0.0.16, dst: 192.168.11.1
*Apr 13 19:06:07.593: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Apr 13 19:06:07.593: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.593: pktsz: 96 extoff: 68
*Apr 13 19:06:07.593: (M) traffic code: redirect(0)
*Apr 13 19:06:07.593: src NBMA: 172.17.0.5
*Apr 13 19:06:07.593: src protocol: 10.0.0.16, dst protocol: 192.168.11.1
*Apr 13 19:06:07.593: Contents of nhrp traffic indication packet:
*Apr 13 19:06:07.593: 45 00 00 64 00 01 00 00 FC 01 20 3C C0 A8 0B 01
*Apr 13 19:06:07.593: C0 A8 12 0A 08 00 A1 C8 00 01 00
Passaggio 5. Pacchetto ICMP ricevuto sul spoke 2
La ricerca del percorso viene eseguita per 192.168.18.10 ed è una rete connessa localmente. Inoltra la richiesta ICMP alla destinazione.
Flusso della richiesta di risoluzione NHRP
Raggio 1
- Viene ricevuta l'indicazione NHRP inviata dall'hub 1 alla destinazione 192.168.18.10.
- È stata inserita una voce incompleta della cache NHRP per 192.168.18.10/32.
- Ricerca route completata per 192.168.18.10. L'hop successivo è 10.0.1.8 (Hub 1) su Tunnel0
- La ricerca nella cache NHRP viene eseguita per l'hop successivo 10.0.1.8 su Tunnel0. Viene trovata una voce e il socket di crittografia è attivo (ad esempio, il tunnel esiste)
- Il raggio 1 invia una richiesta di risoluzione NHRP per 192.168.18.10/32 all'hub 1 tramite il raggio esistente al tunnel hub1 regionale.
*Apr 13 19:06:07.596: NHRP: Receive Traffic Indication via Tunnel0 vrf 0, packet size: 96
*Apr 13 19:06:07.596: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Apr 13 19:06:07.596: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.596: pktsz: 96 extoff: 68
*Apr 13 19:06:07.596: (M) traffic code: redirect(0)
*Apr 13 19:06:07.596: src NBMA: 172.18.0.1
*Apr 13 19:06:07.596: src protocol: 10.0.1.8, dst protocol: 192.168.11.1
*Apr 13 19:06:07.596: Contents of nhrp traffic indication packet:
*Apr 13 19:06:07.596: 45 00 00 64 00 01 00 00 FE 01 1E 3C C0 A8 0B 01
*Apr 13 19:06:07.596: C0 A8 12 0A 08 00 A1 C8 00 01 00
*Apr 13 19:06:07.596: NHRP: Attempting to create instance PDB for (0x0)
*Apr 13 19:06:07.609: NHRP: Send Resolution Request via Tunnel0 vrf 0, packet size: 84
*Apr 13 19:06:07.609: src: 10.0.1.11, dst: 192.168.18.10
*Apr 13 19:06:07.609: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Apr 13 19:06:07.609: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.609: pktsz: 84 extoff: 52
*Apr 13 19:06:07.609: (M) flags: "router auth src-stable nat ", reqid: 3
*Apr 13 19:06:07.609: src NBMA: 172.16.1.1
*Apr 13 19:06:07.609: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.609: (C-1) code: no error(0)
*Apr 13 19:06:07.609: prefix: 32, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.609: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
Hub 1
- Viene ricevuta la richiesta di risoluzione NHRP dal raggio 1 per la destinazione 192.168.18.1/32.
- Ricerca route completata per 192.168.18.1. L'hop successivo è 10.0.0.1 (Hub 0) su Tunnel0
- L'ID di rete NHRP per l'ingresso e l'uscita è lo stesso e il nodo locale non è il punto di uscita.
- La ricerca nella cache NHRP viene eseguita per l'hop successivo 10.0.0.1 su Tunnel0, viene trovata una voce e il socket di crittografia è attivo (tunnel esistente)
- L'hub 1 inoltra la richiesta di risoluzione NHRP per 192.168.18.10/32 all'hub 0 sul tunnel esistente
*Apr 13 19:06:07.610: NHRP: Receive Resolution Request via Tunnel1 vrf 0, packet size: 84
*Apr 13 19:06:07.610: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Apr 13 19:06:07.610: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.610: pktsz: 84 extoff: 52
*Apr 13 19:06:07.610: (M) flags: "router auth src-stable nat ", reqid: 3
*Apr 13 19:06:07.610: src NBMA: 172.16.1.1
*Apr 13 19:06:07.610: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.610: (C-1) code: no error(0)
*Apr 13 19:06:07.610: prefix: 32, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.610: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
*Apr 13 19:06:07.610: NHRP: Forwarding Resolution Request via Tunnel0 vrf 0, packet size: 104
*Apr 13 19:06:07.610: src: 10.0.0.8, dst: 192.168.18.10
*Apr 13 19:06:07.610: (F) afn: AF_IP(1), type: IP(800), hop: 254, ver: 1
*Apr 13 19:06:07.610: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.610: pktsz: 104 extoff: 52
*Apr 13 19:06:07.610: (M) flags: "router auth src-stable nat ", reqid: 3
*Apr 13 19:06:07.610: src NBMA: 172.16.1.1
*Apr 13 19:06:07.610: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.610: (C-1) code: no error(0)
*Apr 13 19:06:07.610: prefix: 32, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.610: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
Hub 0
- La richiesta di risoluzione NHRP viene ricevuta per la destinazione 192.168.18.1/32, inoltrata dall'hub 1.
- Ricerca route completata per 192.168.18.1. L'hop successivo è 10.0.0.16 (Hub 2) su Tunnel0
- L'ID di rete NHRP per l'ingresso e l'uscita è lo stesso e il nodo locale non è il punto di uscita.
- La ricerca nella cache NHRP viene eseguita per l'hop successivo 10.0.0.16 sul tunnel0, viene trovata una voce e il socket di crittografia è attivo (tunnel esistente)
- L'hub 0 inoltra la richiesta di risoluzione NHRP per 192.168.18.1/32 all'hub 2 sul tunnel esistente.
*Apr 13 19:06:07.611: NHRP: Receive Resolution Request via Tunnel0 vrf 0, packet size: 104
*Apr 13 19:06:07.611: (F) afn: AF_IP(1), type: IP(800), hop: 254, ver: 1
*Apr 13 19:06:07.611: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.611: pktsz: 104 extoff: 52
*Apr 13 19:06:07.611: (M) flags: "router auth src-stable nat ", reqid: 3
*Apr 13 19:06:07.611: src NBMA: 172.16.1.1
*Apr 13 19:06:07.611: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.611: (C-1) code: no error(0)
*Apr 13 19:06:07.611: prefix: 32, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.611: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
*Apr 13 19:06:07.611: NHRP: Forwarding Resolution Request via Tunnel0 vrf 0, packet size: 124
*Apr 13 19:06:07.611: src: 10.0.0.1, dst: 192.168.18.10
*Apr 13 19:06:07.611: (F) afn: AF_IP(1), type: IP(800), hop: 253, ver: 1
*Apr 13 19:06:07.611: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.612: pktsz: 124 extoff: 52
*Apr 13 19:06:07.612: (M) flags: "router auth src-stable nat ", reqid: 3
*Apr 13 19:06:07.612: src NBMA: 172.16.1.1
*Apr 13 19:06:07.612: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.612: (C-1) code: no error(0)
*Apr 13 19:06:07.612: prefix: 32, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.612: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
Hub 2
- La richiesta di risoluzione NHRP viene ricevuta da Spoke 1 per la destinazione 192.168.18.10/32, inoltrata dall'hub 0
- La ricerca del percorso è stata eseguita per 192.168.18.10, l'hop successivo è 10.0.2.18 (spoke 2) sul tunnel 2
- L'ID di rete NHRP per l'ingresso e l'uscita è lo stesso e il nodo locale non è il punto di uscita.
- Ricerca nella cache NHRP eseguita per l'hop successivo 10.0.2.18 sul tunnel2, viene trovata una voce e il socket di crittografia è attivo (tunnel esistente)
- L'hub 2 inoltra la richiesta di risoluzione NHRP per 192.168.18.1/32 al spoke 2 sul tunnel esistente
*Apr 13 19:06:07.613: NHRP: Receive Resolution Request via Tunnel0 vrf 0, packet size: 124
*Apr 13 19:06:07.613: (F) afn: AF_IP(1), type: IP(800), hop: 253, ver: 1
*Apr 13 19:06:07.613: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.613: pktsz: 124 extoff: 52
*Apr 13 19:06:07.613: (M) flags: "router auth src-stable nat ", reqid: 3
*Apr 13 19:06:07.613: src NBMA: 172.16.1.1
*Apr 13 19:06:07.613: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.613: (C-1) code: no error(0)
*Apr 13 19:06:07.613: prefix: 32, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.613: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
*Apr 13 19:06:07.613: NHRP: Forwarding Resolution Request via Tunnel2 vrf 0, packet size: 144
*Apr 13 19:06:07.613: src: 10.0.2.16, dst: 192.168.18.10
*Apr 13 19:06:07.613: (F) afn: AF_IP(1), type: IP(800), hop: 252, ver: 1
*Apr 13 19:06:07.613: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.613: pktsz: 144 extoff: 52
*Apr 13 19:06:07.613: (M) flags: "router auth src-stable nat ", reqid: 3
*Apr 13 19:06:07.613: src NBMA: 172.16.1.1
*Apr 13 19:06:07.613: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.613: (C-1) code: no error(0)
*Apr 13 19:06:07.613: prefix: 32, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.613: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
Raggio 2
- La richiesta di risoluzione NHRP viene ricevuta per la destinazione 192.168.18.1/32, inoltrata dall'hub 2
- La ricerca dei percorsi viene eseguita per 192.168.18.10, una rete connessa localmente.
- Spoke 2 è il punto di uscita e genera la risposta di risoluzione per 192.168.18.10, prefisso /24
- Spoke 2 inserisce la voce della cache NHRP per 10.0.1.11 (Spoke 1) utilizzando le informazioni della richiesta di risoluzione NHRP.
- Il spoke 2 avvia il tunnel VPN con endpoint remoto = indirizzo NBMA del spoke 1. Il tunnel dinamico Spoke-Spoke viene negoziato.
- Poi Spoke 2 invia la risposta di risoluzione NHRP per 192.168.18.10/24 al Spoke 1 sul tunnel dinamico che è stato appena costruito.
*Apr 13 19:06:07.613: NHRP: Receive Resolution Request via Tunnel0 vrf 0, packet size: 144
*Apr 13 19:06:07.613: (F) afn: AF_IP(1), type: IP(800), hop: 252, ver: 1
*Apr 13 19:06:07.613: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.613: pktsz: 144 extoff: 52
*Apr 13 19:06:07.613: (M) flags: "router auth src-stable nat ", reqid: 3
*Apr 13 19:06:07.613: src NBMA: 172.16.1.1
*Apr 13 19:06:07.613: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.614: (C-1) code: no error(0)
*Apr 13 19:06:07.614: prefix: 32, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.614: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
*Apr 13 19:06:07.672: NHRP: Send Resolution Reply via Tunnel0 vrf 0, packet size: 172
*Apr 13 19:06:07.672: src: 10.0.2.18, dst: 10.0.1.11
*Apr 13 19:06:07.672: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Apr 13 19:06:07.672: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.672: pktsz: 172 extoff: 60
*Apr 13 19:06:07.672: (M) flags: "router auth dst-stable unique src-stable nat ", reqid: 3
*Apr 13 19:06:07.672: src NBMA: 172.16.1.1
*Apr 13 19:06:07.672: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.672: (C-1) code: no error(0)
*Apr 13 19:06:07.672: prefix: 24, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.672: addr_len: 4(NSAP), subaddr_len: 0(NSAP), proto_len: 4, pref: 0
*Apr 13 19:06:07.672: client NBMA: 172.16.2.1
*Apr 13 19:06:07.672: client protocol: 10.0.2.18
Raggio1
- La risposta alla risoluzione NHRP viene ricevuta dal raggio 2 per la destinazione 192.168.18.10, prefisso /24 sul tunnel dinamico.
- La voce della cache NHRP per 192.168.18.0/24 viene ora aggiornata con l'hop successivo = 10.0.2.18, NBMA = 172.16.2.1
- Una route NHRP viene aggiunta nella RIB per la rete 192.168.18.10, hop successivo = 10.0.2.18.
*Apr 13 19:06:07.675: NHRP: Receive Resolution Reply via Tunnel0 vrf 0, packet size: 232
*Apr 13 19:06:07.675: (F) afn: AF_IP(1), type: IP(800), hop: 252, ver: 1
*Apr 13 19:06:07.675: shtl: 4(NSAP), sstl: 0(NSAP)
*Apr 13 19:06:07.675: pktsz: 232 extoff: 60
*Apr 13 19:06:07.675: (M) flags: "router auth dst-stable unique src-stable nat ", reqid: 3
*Apr 13 19:06:07.675: src NBMA: 172.16.1.1
*Apr 13 19:06:07.675: src protocol: 10.0.1.11, dst protocol: 192.168.18.10
*Apr 13 19:06:07.675: (C-1) code: no error(0)
*Apr 13 19:06:07.675: prefix: 24, mtu: 17912, hd_time: 7200
*Apr 13 19:06:07.675: addr_len: 4(NSAP), subaddr_len: 0(NSAP), proto_len: 4, pref: 0
*Apr 13 19:06:07.675: client NBMA: 172.16.2.1
*Apr 13 19:06:07.675: client protocol: 10.0.2.18
*Apr 13 19:06:07.676: NHRP: Adding route entry for 192.168.18.0/24 () to RIB
*Apr 13 19:06:07.676: NHRP: Route addition to RIB Successful
*Apr 13 19:06:07.676: NHRP: Route watch started for 192.168.18.0/23
*Apr 13 19:06:07.676: NHRP: Adding route entry for 10.0.2.18/32 (Tunnel0) to RIB
*Apr 13 19:06:07.676: NHRP: Route addition to RIB Successful .
spoke_1#show ip route 192.168.18.10
Routing entry for 192.168.18.0/24
Known via "nhrp", distance 250, metric 1
Last update from 10.0.2.18 00:09:46 ago
Routing Descriptor Blocks:
* 10.0.2.18, from 10.0.2.18, 00:09:46 ago
Route metric is 1, traffic share count is 1
MPLS label: none
Verifica
Nota: Cisco CLI Analyzer (solo utenti registrati) supporta alcuni comandi show. Usare Cisco CLI Analyzer per visualizzare un'analisi dell'output del comando show.
Prima della creazione del tunnel Spoke-Spoke, ovvero quando viene formata la voce dei collegamenti NHRP
spoke_1#show ip nhrp
10.0.1.8/32 via 10.0.1.8
Tunnel0 created 02:19:32, never expire
Type: static, Flags: used
NBMA address: 172.18.0.1
spoke_1#
spoke_1#show ip route next-hop-override
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is 172.16.1.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 172.16.1.2
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
D 10.0.0.0/24 [90/5120000] via 10.0.1.8, 02:20:14, Tunnel0
C 10.0.1.0/24 is directly connected, Tunnel0
L 10.0.1.11/32 is directly connected, Tunnel0
D 10.0.2.0/24 [90/6681600] via 10.0.1.8, 02:20:03, Tunnel0
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.1.0/30 is directly connected, Ethernet0/0
L 172.16.1.1/32 is directly connected, Ethernet0/0
172.25.0.0/32 is subnetted, 1 subnets
C 172.25.179.254 is directly connected, Loopback0
D 192.168.0.0/18 [90/5248000] via 10.0.1.8, 02:20:03, Tunnel0 <<<< Summary route received from hub1
D 192.168.8.0/21 [90/3968000] via 10.0.1.8, 02:20:14, Tunnel0
192.168.11.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.11.0/24 is directly connected, Loopback1
L 192.168.11.1/32 is directly connected, Loopback1
spoke_1#
spoke_1#show dmvpn detail
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
T1 - Route Installed, T2 - Nexthop-override
C - CTS Capable
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface Tunnel0 is up/up, Addr. is 10.0.1.11, VRF ""
Tunnel Src./Dest. addr: 172.16.1.1/MGRE, Tunnel VRF ""
Protocol/Transport: "multi-GRE/IP", Protect "profile-dmvpn"
Interface State Control: Disabled
nhrp event-publisher : Disabled
IPv4 NHS:
10.0.1.8 RE NBMA Address: 172.18.0.1 priority = 0 cluster = 0
Type:Spoke, Total NBMA Peers (v4/v6): 1
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb Target Network
----- --------------- --------------- ----- -------- ----- -----------------
1 172.18.0.1 10.0.1.8 UP 00:02:31 S 10.0.1.8/32 <<<< Tunnel to the regional hub 1
Crypto Session Details:
--------------------------------------------------------------------------------
Interface: Tunnel0
Session: [0xF5F94CC8]
Session ID: 0
IKEv1 SA: local 172.16.1.1/500 remote 172.18.0.1/500 Active <<<<< Crypto session to the regional hub 1
Capabilities:D connid:1019 lifetime:23:57:28
Crypto Session Status: UP-ACTIVE
fvrf: (none), Phase1_id: 172.18.0.1
IPSEC FLOW: permit 47 host 172.16.1.1 host 172.18.0.1
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 35 drop 0 life (KB/Sec) 4153195/3448
Outbound: #pkts enc'ed 35 drop 0 life (KB/Sec) 4153195/3448
Outbound SPI : 0xACACB658, transform : esp-256-aes esp-sha-hmac
Socket State: Open
Pending DMVPN Sessions:
spoke_1#
Dopo il formato del tunnel dinamico spoke, ovvero dopo il formato della voce di collegamento NHRP
spoke_1#show ip nhrp
10.0.1.8/32 via 10.0.1.8
Tunnel0 created 02:24:04, never expire
Type: static, Flags: used
NBMA address: 172.18.0.1
10.0.2.18/32 via 10.0.2.18 <<<<<<<<<<< The new NHRP cache entry for spoke 2 that was learnt
Tunnel0 created 00:01:41, expire 01:58:18
Type: dynamic, Flags: router used nhop rib
NBMA address: 172.16.2.1
192.168.11.0/24 via 10.0.1.11
Tunnel0 created 00:01:26, expire 01:58:33
Type: dynamic, Flags: router unique local
NBMA address: 172.16.1.1
(no-socket)
192.168.18.0/24 via 10.0.2.18 <<<<<<<<<<<<< New NHRP cache entry formed for the remote subnet behind spoke2 that was learnt
Tunnel0 created 00:01:41, expire 01:58:18
Type: dynamic, Flags: router rib
NBMA address: 172.16.2.1
spoke_1#
spoke_1#sh ip route next-hop-override
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is 172.16.1.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 172.16.1.2
10.0.0.0/8 is variably subnetted, 5 subnets, 2 masks
D 10.0.0.0/24 [90/5120000] via 10.0.1.8, 02:23:57, Tunnel0
C 10.0.1.0/24 is directly connected, Tunnel0
L 10.0.1.11/32 is directly connected, Tunnel0
D 10.0.2.0/24 [90/6681600] via 10.0.1.8, 02:23:46, Tunnel0
H 10.0.2.18/32 is directly connected, 00:01:48, Tunnel0
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.1.0/30 is directly connected, Ethernet0/0
L 172.16.1.1/32 is directly connected, Ethernet0/0
172.25.0.0/32 is subnetted, 1 subnets
C 172.25.179.254 is directly connected, Loopback0
D 192.168.0.0/18 [90/5248000] via 10.0.1.8, 02:23:46, Tunnel0
D 192.168.8.0/21 [90/3968000] via 10.0.1.8, 02:23:57, Tunnel0
192.168.11.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.11.0/24 is directly connected, Loopback1
L 192.168.11.1/32 is directly connected, Loopback1
H 192.168.18.0/24 [250/1] via 10.0.2.18, 00:01:48
spoke_1#
spoke_1#sh dmvpn detail
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
T1 - Route Installed, T2 - Nexthop-override
C - CTS Capable
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface Tunnel0 is up/up, Addr. is 10.0.1.11, VRF ""
Tunnel Src./Dest. addr: 172.16.1.1/MGRE, Tunnel VRF ""
Protocol/Transport: "multi-GRE/IP", Protect "profile-dmvpn"
Interface State Control: Disabled
nhrp event-publisher : Disabled
IPv4 NHS:
10.0.1.8 RE NBMA Address: 172.18.0.1 priority = 0 cluster = 0
Type:Spoke, Total NBMA Peers (v4/v6): 3
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb Target Network
----- --------------- --------------- ----- -------- ----- -----------------
1 172.18.0.1 10.0.1.8 UP 00:05:44 S 10.0.1.8/32
2 172.16.2.1 10.0.2.18 UP 00:01:51 DT1 10.0.2.18/32 <<<< Entry for spoke2's tunnel
172.16.2.1 10.0.2.18 UP 00:01:51 DT1 192.168.18.0/24 <<<< Entry for the subnet behind spoke2 that was learnt
1 172.16.1.1 10.0.1.11 UP 00:01:37 DLX 192.168.11.0/24 <<<< Entry formed for the local subnet
Crypto Session Details:
--------------------------------------------------------------------------------
Interface: Tunnel0
Session: [0xF5F94DC0]
Session ID: 0
IKEv1 SA: local 172.16.1.1/500 remote 172.18.0.1/500 Active
Capabilities:D connid:1019 lifetime:23:54:15
Crypto Session Status: UP-ACTIVE
fvrf: (none), Phase1_id: 172.18.0.1
IPSEC FLOW: permit 47 host 172.16.1.1 host 172.18.0.1
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 8 drop 0 life (KB/Sec) 4153188/3255
Outbound: #pkts enc'ed 9 drop 0 life (KB/Sec) 4153188/3255
Outbound SPI : 0xACACB658, transform : esp-256-aes esp-sha-hmac
Socket State: Open
Interface: Tunnel0
Session: [0xF5F94CC8]
Session ID: 0
IKEv1 SA: local 172.16.1.1/500 remote 172.16.2.1/500 Active
Capabilities:D connid:1020 lifetime:23:58:08
Crypto Session Status: UP-ACTIVE
fvrf: (none), Phase1_id: 172.16.2.1
IPSEC FLOW: permit 47 host 172.16.1.1 host 172.16.2.1
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 10 drop 0 life (KB/Sec) 4185320/3488
Outbound: #pkts enc'ed 10 drop 0 life (KB/Sec) 4185318/3488
Outbound SPI : 0xCAD04C8B, transform : esp-256-aes esp-sha-hmac
Socket State: Open
Pending DMVPN Sessions:
Motivo della voce della cache NHRP locale (senza socket) illustrato in precedenza
Il flag locale fa riferimento alle voci di mapping NHRP per le reti locali del router (servite da questo router). Queste voci vengono create quando il router risponde a una richiesta di risoluzione NHRP con queste informazioni e vengono utilizzate per archiviare l'indirizzo IP del tunnel di tutti gli altri nodi NHRP a cui ha inviato queste informazioni. Se per qualche motivo il router perde l'accesso a questa rete locale (non può più servire questa rete), invierà un messaggio di rimozione NHRP a tutti i nodi NHRP remoti elencati nella voce "locale" (show ip nhrp detail) per chiedere ai nodi remoti di cancellare queste informazioni dalle rispettive tabelle di mapping NHRP.
Non viene rilevato alcun socket per le voci di mapping NHRP per le quali non è necessario né si desidera attivare IPSec per impostare la crittografia.
spoke_1#sh ip nhrp 192.168.11.0 detail
192.168.11.0/24 via 10.0.1.11
Tunnel0 created 00:01:01, expire 01:58:58
Type: dynamic, Flags: router unique local
NBMA address: 172.16.1.1
(no-socket)
Requester: 10.0.2.18 Request ID: 2
Risoluzione dei problemi
Le informazioni contenute in questa sezione permettono di risolvere i problemi relativi alla configurazione.
Nota: consultare le informazioni importanti sui comandi di debug prima di usare i comandi di debug.
La risoluzione dei problemi di DMVPN prevede la risoluzione dei problemi a 4 livelli nell'ordine seguente:
- Livello di routing fisico (NBMA o endpoint del tunnel)
- Livello crittografia IPsec
- Livello di incapsulamento GRE
- Livello Protocolli di routing dinamico
Prima di risolvere il problema, è consigliabile eseguire i seguenti comandi:
!! Enable msec debug and log timestamps
service timestamps debug datetime msec
service timestamps log datetime msec
!! To help correlate the debug output with the show command outputs
terminal exec prompt timestamp
Livello di routing fisico (NBMA o endpoint del tunnel)
Verificare se è possibile eseguire il ping tra l'hub e l'indirizzo NBMA dello spoke e tra l'indirizzo NBMA dell'hub (dall'output di show ip nhrp sullo spoke). I ping devono uscire direttamente dall'interfaccia fisica, non tramite il tunnel DMVPN. Se l'operazione non riesce, controllare il routing e gli eventuali firewall tra i router hub e spoke.
Livello crittografia IPSec
Eseguire i comandi seguenti per controllare le associazioni di protezione ISAKMP e IPsec tra gli indirizzi NBMA dell'hub e dello spoke.
show crypto isakmp sa detail
show crypto ipsec sa peer <NBMA-address-peer>
Questi debug possono essere attivati per risolvere i problemi relativi al livello di crittografia IPSec:
!! Use the conditional debugs to restrict the debug output for a specific peer.
debug crypto condition peer ipv4 <NBMA address of the peer>
debug crypto isakmp
debug crypto ipsec
NHRP
Lo spoke invia regolarmente richieste di registrazione NHRP, ogni 1/3 di tempo di attesa NHRP (sullo spoke) o valore di timeout di registrazione ip nhrp<seconds>. È possibile controllare questo sul raggio eseguendo:
show ip nhrp nhs detail
show ip nhrp traffic
Utilizzare i comandi descritti in precedenza per verificare se il spoke invia richieste di registrazione NHRP e riceve risposte dall'hub.
Per verificare se l'hub dispone della voce di mapping NHRP per lo spoke nella cache NHRP dell'hub, eseguire questo comando:
show ip nhrp <spoke-tunnel-ip-address>
Per risolvere i problemi relativi al protocollo NHRP, è possibile utilizzare i seguenti debug:
!! Enable conditional NHRP debugs
debug nhrp condition peer tunnel <tunnel address of the peer>
OR
debug nhrp condition peer nbma <nbma address of the peer>
debug nhrp
debug nhrp packet
Livello protocolli di routing dinamico
A seconda del protocollo di routing dinamico utilizzato, consultare i seguenti documenti:
Informazioni correlate
Contributo dei tecnici Cisco
- Nitin DhingraCisco TAC Engineer
- Rudresh VeerappajiCisco TAC Engineer
 Feedback
Feedback