Introduzione
In questo documento viene descritto come risolvere l'errore "impossibile trovare il segreto per" in Secure Network Analytics Manager Central Management.
Prerequisiti
Requisiti
Nessun requisito specifico previsto per questo documento.
Componenti usati
Le informazioni fornite in questo documento si basano sulle seguenti versioni software e hardware:
Secure Network Analytics Manager versione 7.1.1 o successiva
Le informazioni discusse in questo documento fanno riferimento a dispositivi usati in uno specifico ambiente di emulazione. Su tutti i dispositivi menzionati nel documento la configurazione è stata ripristinata ai valori predefiniti. Se la rete è operativa, valutare attentamente eventuali conseguenze derivanti dall'uso dei comandi.
Premesse
Questo problema si verifica nei servizi di Central Management che richiedono credenziali quali SNMP v3.
Nessun errore visualizzato in un Central Management pagina stessa.
La distribuzione dispone di un server di gestione primario e secondario.
OSPF (Open Shortest Path First) /lancope/var/logs/containers/svc-central-management.log file nel Gestore primario contiene voci che contengono "unable to find secret for" voci.
Problema
L'errore viene visualizzato in Gestione primaria /lancope/var/logs/containers/svc-central-management.log quando viene apportata una modifica alla configurazione dei gestori secondari. Questa situazione può verificarsi con qualsiasi sezione di configurazione di Gestione centrale configurabile per l'utilizzo dell'autenticazione.
Apr 27 19:47:35 smc-primary docker/svc-central-management[3214]: 2020-04-27 19:47:35.369 INFO [qtp1907431275-88280] FailoverConfigurationSender:129 - Synchronization of Primary’s APPLIANCE a39117ce-ac2b-46eb-837c-facae0cc4abc snapshot to other SMC is successful
Apr 27 19:47:36 smc-primary docker/svc-central-management[3214]: 2020-04-27 19:47:36.982 ERROR [qtp1907431275-88310] GlobalExceptionController:133 - \QError processing GET /cm/config/appliance/a39117ce-ac2b-46eb-837c-facae0cc4abc/config/internal\E
Apr 27 19:47:36 smc-primary docker/svc-central-management[3214]: com.lancope.cm.configuration.service.SecureDataProcessingException: Unable to find secret for ‘0xe9bda01ea881b262ced8e153a3d9cf2a’ <-- The error
Il gestore secondario genera un errore nello stesso momento /lancope/var/logs/containers/svc-cm-agent.log file:
Apr 27 19:47:36 smc-secondary docker/svc-cm-agent[385336]: 2020-04-27 19:47:36.305 INFO [qtp634540230-71] StandardCommandRunner:67 - Running Command(Command(commandType=APPLY_CONFIG, commandId=9ba839e2-6770-4f21-9f7d-cbfe6782c2dc, arguments=Optional[[internetProxy, auditLogDestination, passwordPolicy, smtp, aide, ldapSetup, dnsCache, dns, ssh, fips, ntp, dodin, tlsApplianceIdentity, snmpAgent, tlsClientIdentities, sso, externalServices, localResolution, networkInterfaces, openingMessage, configBackup, host, trustStore, sessionTimeout]]))...
Apr 27 19:47:36 smc-secondary docker/svc-cm-agent[385336]: 2020-04-27 19:47:36.306 INFO [qtp634540230-71] CommandDispatcher:30 - Running APPLY_CONFIG 9ba839e2-6770-4f21-9f7d-cbfe6782c2dc
Apr 27 19:47:37 smc-secondary docker/svc-cm-agent[385336]: 2020-04-27 19:47:37.135 INFO [qtp634540230-71] StandardCommandRunner:69 - Command(Command(commandType=APPLY_CONFIG, commandId=9ba839e2-6770-4f21-9f7d-cbfe6782c2dc, arguments=Optional[[internetProxy, auditLogDestination, passwordPolicy, smtp, aide, ldapSetup, dnsCache, dns, ssh, fips, ntp, dodin, tlsApplianceIdentity, snmpAgent, tlsClientIdentities, sso, externalServices, localResolution, networkInterfaces, openingMessage, configBackup, host, trustStore, sessionTimeout]])) completed, success = false
Apr 27 19:47:37 smc-secondary docker/svc-cm-agent[385336]: 2020-04-27 19:47:37.136 INFO [qtp634540230-71] CommandResultStoreDAO:40 - {“replyLink”:“https://10.209.6.43/cm/config/appliance/a39117ce-ac2b-46eb-837c-facae0cc4abc/command/9ba839e2-6770-4f21-9f7d-cbfe6782c2dc/apply”,“commandResult”:{“type”:“applyConfig”,“successful”:false,“details”:“exit code: 1\nElementIDs without results: aide, auditLogDestination, configBackup, dns, dnsCache, dodin, externalServices, fips, host, internetProxy, ldapSetup, localResolution, networkInterfaces, ntp, openingMessage, passwordPolicy, sessionTimeout, smtp, snmpAgent, ssh, sso, tlsApplianceIdentity, tlsClientIdentities, trustStore\n---STDERR---\nERROR! Attempted to execute \“./ansible-inventory.py\” as inventory script: Inventory script (./ansible-inventory.py) had an execution error: /usr/local/lib/python2.7/dist-packages/urllib3/connectionpool.py:1004: InsecureRequestWarning: Unverified HTTPS request is being made. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.io/en/latest/advanced-usage.html#ssl-warnings\n InsecureRequestWarning,\n/usr/local/lib/python2.7/dist-packages/urllib3/connectionpool.py:1004: InsecureRequestWarning: Unverified HTTPS request is being made. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.io/en/latest/advanced-usage.html#ssl-warnings\n InsecureRequestWarning,\nTraceback (most recent call last):\n File \“/opt/service/ansible/ansible-inventory.py\“, line 48, in <module>\n \“config\“: fetch_configuration(),\n File \“/opt/service/ansible/ansible-inventory.py\“, line 36, in fetch_configuration\n return r.json()[‘configurableElements’]\n File \“/usr/local/lib/python2.7/dist-packages/requests/models.py\“, line 889, in json\n self.content.decode(encoding), **kwargs\n File \“/usr/lib/python2.7/json/__init__.py\“, line 339, in loads\n return _default_decoder.decode(s)\n File \“/usr/lib/python2.7/json/decoder.py\“, line 364, in decode\n obj, end = self.raw_decode(s, idx=_w(s, 0).end())\n File \“/usr/lib/python2.7/json/
Apr 27 19:47:37 smc-secondary docker/svc-cm-agent[385336]: decoder.py\“, line 380, in raw_decode\n obj, end = self.scan_once(s, idx)\nValueError: Expecting ‘,’ delimiter: line 1 column 10305 (char 10304)\n \n\n”,“elementResults”:[“java.util.HashMap”,{}]}}
Apr 27 19:47:37 smc-secondary docker/svc-cm-agent[385336]: 2020-04-27 19:47:37.767 INFO [qtp634540230-71] CommandResultStoreDAO:46 - Previous command result exists. Removing it now.
In Responsabile principale, controllare il contenuto del /lancope/var/services/cm/configuration/{idofsecondarysmcdirectory}/config.json file. con jq . /lancope/var/services/cm/configuration/idofsecondarysmcdirectory/config.json
primary-smc#: jq .configurableElements.snmpAgent /lancope/var/services/cm/configuration/{idofsecondarysmcdirectory}/config.json
{
"agentEnabled": true,
"agentCommunity": "fakePW123",
"agentPort": 161,
"sysLocation": "Somecity ST",
"sysContact": "Example User",
"sysName": "smc-secondary.example.com",
"sysServices": 72,
"sysDescr": "Stealthwatch",
"sysObjectId": "1.3.6.1.4.1.8712.1.1",
"username": "readonly",
"mode": "V3",
"encryptionPass": "0xe9bda01ea881b262ced8e153a3d9cf2a", <-- This is the same value seen in the log file from the Primary Manager
"authPass": "0x6bb67c14beca3b6ba319485441cd24a36f80068d",
}
Soluzione
Passa a Central Management > Actions > Edit Appliance Configuration > Network Services e quindi immettere il Encryption Password e Authentication Password nella sezione Agente SNMP quando è selezionato SNMP VERSION V3. Al termine, selezionare Apply Settings.
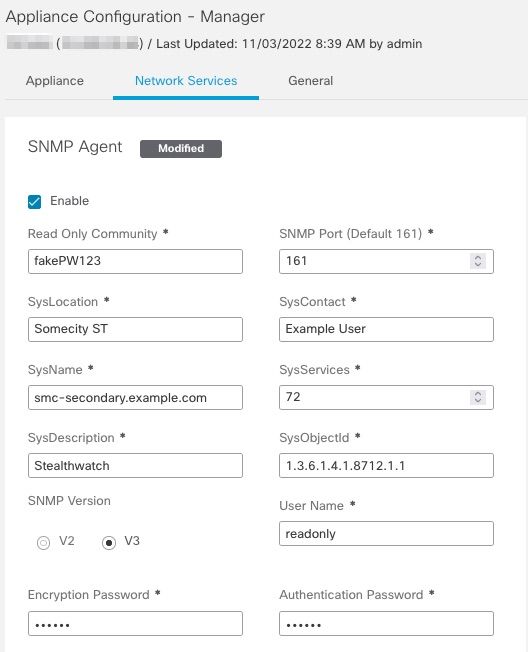 Configurazione agente SNMPv3
Configurazione agente SNMPv3

 Feedback
Feedback