Configurar certificado para comunicação FND para SSM
Opções de download
Linguagem imparcial
O conjunto de documentação deste produto faz o possível para usar uma linguagem imparcial. Para os fins deste conjunto de documentação, a imparcialidade é definida como uma linguagem que não implica em discriminação baseada em idade, deficiência, gênero, identidade racial, identidade étnica, orientação sexual, status socioeconômico e interseccionalidade. Pode haver exceções na documentação devido à linguagem codificada nas interfaces de usuário do software do produto, linguagem usada com base na documentação de RFP ou linguagem usada por um produto de terceiros referenciado. Saiba mais sobre como a Cisco está usando a linguagem inclusiva.
Sobre esta tradução
A Cisco traduziu este documento com a ajuda de tecnologias de tradução automática e humana para oferecer conteúdo de suporte aos seus usuários no seu próprio idioma, independentemente da localização. Observe que mesmo a melhor tradução automática não será tão precisa quanto as realizadas por um tradutor profissional. A Cisco Systems, Inc. não se responsabiliza pela precisão destas traduções e recomenda que o documento original em inglês (link fornecido) seja sempre consultado.
Introduction
Este documento descreve como configurar corretamente problemas de comunicação entre o Field Network Diretor (FND) e o Software Security Module (SSM).
Problema
Desde o FND 4.4, a comunicação entre o servidor de aplicativos FND e o serviço SSM requer autenticação mútua.
Se essa autenticação mútua não estiver configurada corretamente ou os certificados não corresponderem, a conexão do FND para o SSM será recusada.
Isso pode ser visto em server.log, se o registro estiver definido como debug, como a seguir:
7645: SLC-FND: Jun 20 2019 13:22:49.929 +0000: %IOTFND-7-UNSPECIFIED: %[ch=SSMClient][sev=DEBUG][tid=http-/0.0.0.0:443-5]: Sending request to SSM Server. Request :https://127.0.0.1:8445/api/v0/ssmws/loadKeyStore.json
7646: SLC-FND: Jun 20 2019 13:22:49.930 +0000: %IOTFND-7-UNSPECIFIED: %[ch=BasicClientConnectionManager][sev=DEBUG][tid=http-/0.0.0.0:443-5]: Get connection for route {s}->https://127.0.0.1:8445
7647: SLC-FND: Jun 20 2019 13:22:49.931 +0000: %IOTFND-7-UNSPECIFIED: %[ch=DefaultClientConnectionOperator][sev=DEBUG][tid=http-/0.0.0.0:443-5]: Connecting to 127.0.0.1:8445
7648: SLC-FND: Jun 20 2019 13:22:49.938 +0000: %IOTFND-7-UNSPECIFIED: %[ch=DefaultClientConnection][sev=DEBUG][tid=http-/0.0.0.0:443-5]: Connection org.apache.http.impl.conn.DefaultClientConnection@370804ff closed
7649: SLC-FND: Jun 20 2019 13:22:49.938 +0000: %IOTFND-7-UNSPECIFIED: %[ch=DefaultClientConnection][sev=DEBUG][tid=http-/0.0.0.0:443-5]: Connection org.apache.http.impl.conn.DefaultClientConnection@370804ff shut down
7650: SLC-FND: Jun 20 2019 13:22:49.938 +0000: %IOTFND-7-UNSPECIFIED: %[ch=BasicClientConnectionManager][sev=DEBUG][tid=http-/0.0.0.0:443-5]: Releasing connection org.apache.http.impl.conn.ManagedClientConnectionImpl@7bc2e02f
7651: SLC-FND: Jun 20 2019 13:22:49.938 +0000: %IOTFND-7-UNSPECIFIED: %[ch=BasicClientConnectionManager][sev=DEBUG][tid=http-/0.0.0.0:443-5]: Connection can be kept alive for 9223372036854775807 MILLISECONDS
7652: SLC-FND: Jun 20 2019 13:22:49.938 +0000: %IOTFND-7-UNSPECIFIED: %[ch=SSMClient][sev=DEBUG][tid=http-/0.0.0.0:443-5][part=7652.1/114]: Please verify SSM server status. No response received.
7653: SLC-FND: Jun 20 2019 13:22:49.938 +0000: %IOTFND-7-UNSPECIFIED: %[ch=SSMClient][sev=DEBUG][tid=http-/0.0.0.0:443-5][part=7652.2/114]: javax.net.ssl.SSLPeerUnverifiedException: peer not authenticated
Solução
O certificado usado pelo servidor FND para fazer a autenticação do cliente no servidor SSM é o certificado Web FND do jbossas_keystore.
Para que o SSM confie neste certificado, você precisa passar por estas etapas:
1. Exporte o certificado da Web com o uso da GUI. Navegue até Admin > Gerenciamento do sistema > Certificados > Certificado para Web e clique em Download (base64) como mostrado na imagem.
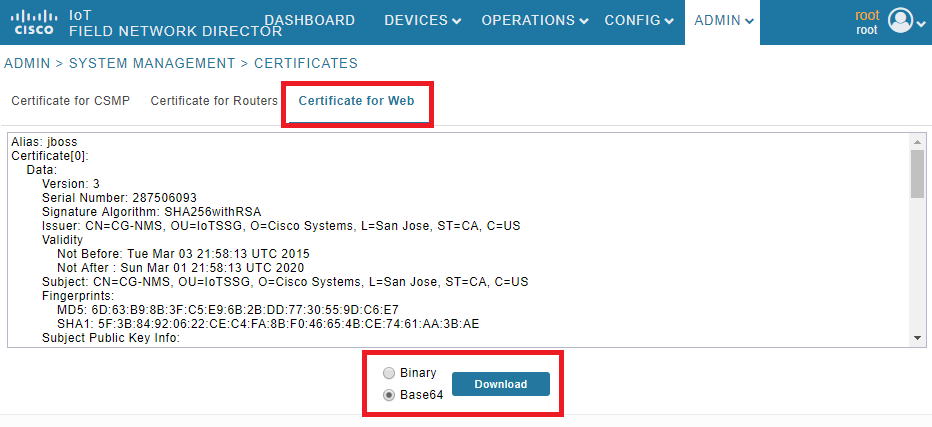
2. Copie o arquivo de texto ou crie um novo arquivo no servidor FND com o conteúdo do certificado da Etapa 1. Para este exemplo, o arquivo é salvo em /opt/cgms/server/cgms/conf/webcert.crt:
[root@fndnms ~]# vi /opt/cgms/server/cgms/conf/webcert.crt [root@fndnms ~]# cat /opt/cgms/server/cgms/conf/webcert.crt -----BEGIN CERTIFICATE----- MIIDbTCCAlWgAwIBAgIEESL+rTANBgkqhkiG9w0BAQsFADBnMQswCQYDVQQGEwJV UzELMAkGA1UECBMCQ0ExETAPBgNVBAcTCFNhbiBKb3NlMRYwFAYDVQQKEw1DaXNj byBTeXN0ZW1zMQ8wDQYDVQQLEwZJb1RTU0cxDzANBgNVBAMTBkNHLU5NUzAeFw0x NTAzMDMyMTU4MTNaFw0yMDAzMDEyMTU4MTNaMGcxCzAJBgNVBAYTAlVTMQswCQYD VQQIEwJDQTERMA8GA1UEBxMIU2FuIEpvc2UxFjAUBgNVBAoTDUNpc2NvIFN5c3Rl bXMxDzANBgNVBAsTBklvVFNTRzEPMA0GA1UEAxMGQ0ctTk1TMIIBIjANBgkqhkiG 9w0BAQEFAAOCAQ8AMIIBCgKCAQEAlsgdELNUFi9eXHcb550y0UgbPMgucsKqT1+E xmwEri517fo+BHdg6AuXpDP4KvLW1/cx8xqWbheKAfPht/HqiFX0ltZdoWaQcaJz YJOiuL/W3BwQW6UMWPnC1p/Dgnz+qR3JQpR20hC4ymHIIVwKwVfiaJZAnSFNKaZ4 uhOuJDkEC0ZyBbp5Y2Mi9zVRTv/g98p0IqpOjxV0JUtlRkWkjkvCma/Q6dZzSdle YZzyAS/ud4KVxytKKoxBBDPrtPRbT6lu2VMyWe26cRjPCveZffBABoSvLjptnb7H mxJMW7EbL+zjTAL/GmHh8J9P16MX7EoePCPCQdwPRdfQ3GkTKwIDAQABoyEwHzAd BgNVHQ4EFgQUfyFoDj0hJLtUu6ZtKCHuisCQfl4wDQYJKoZIhvcNAQELBQADggEB AF9fVfEwqbP4BszGHfzTa8pf4zUPJ3Lcz1z6RxwtyGXq8oZK8YQWRpa2NQKLDnve VjXSdOBvDKRYqPkZeAmTRS0BobeZr2NdHb/FNXMlR6eBm56UrefW+VdQE7syOmGq Ynlwb/1KF/Fkyp2xVk7nHCtHl+I90l3DlyPmGbQ/TxgA6PXY6V6d571IARNdohYm qZ/3B+ZK/F4PLOcUwWDtxTBFnlElyq+YjhZiqsCmsxI1GWqleWltUVGMXNM1YLN5 N1KAbOeC0O4n2MqzTWTU9Ss51WfceWsBoSPO+4xyzcRDZmo7IWZiwp4ZAO3eYOz/ 4aUEdBZxv29+QQ7dq6ZZOXQ= -----END CERTIFICATE-----
3. Execute este comando para importar o certificado como confiável no ssm_web_keystore:
[root@fndnms ~]# keytool -import -trustcacerts -alias fnd -keystore /opt/cgms-ssm/conf/ssm_web_keystore -file /opt/cgms/server/cgms/conf/webcert.crt
Enter keystore password:
Owner: CN=CG-NMS, OU=IoTSSG, O=Cisco Systems, L=San Jose, ST=CA, C=US
Issuer: CN=CG-NMS, OU=IoTSSG, O=Cisco Systems, L=San Jose, ST=CA, C=US
Serial number: 1122fead
Valid from: Tue Mar 03 22:58:13 CET 2015 until: Sun Mar 01 22:58:13 CET 2020
Certificate fingerprints:
MD5: 6D:63:B9:8B:3F:C5:E9:6B:2B:DD:77:30:55:9D:C6:E7
SHA1: 5F:3B:84:92:06:22:CE:C4:FA:8B:F0:46:65:4B:CE:74:61:AA:3B:AE
SHA256: 1C:59:50:40:92:09:66:D3:67:E9:AE:CA:6D:C8:25:88:FF:A8:26:F7:62:8A:13:EB:0E:EC:57:32:DB:03:94:31
Signature algorithm name: SHA256withRSA
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 7F 21 68 0E 3D 21 24 BB 54 BB A6 6D 28 21 EE 8A .!h.=!$.T..m(!..
0010: C0 90 7E 5E ...^
]
]
Trust this certificate? [no]: yes
Certificate was added to keystore
4. Depois que o certificado tiver sido importado, reinicie o serviço SSM:
[root@fndnms ~]# systemctl restart ssm
[root@fndnms ~]# systemctl status ssm
● ssm.service - (null)
Loaded: loaded (/etc/rc.d/init.d/ssm; bad; vendor preset: disabled)
Active: active (running) since Thu 2019-06-20 17:44:11 CEST; 5s ago
Docs: man:systemd-sysv-generator(8)
Process: 11463 ExecStop=/etc/rc.d/init.d/ssm stop (code=exited, status=0/SUCCESS)
Process: 11477 ExecStart=/etc/rc.d/init.d/ssm start (code=exited, status=0/SUCCESS)
CGroup: /system.slice/ssm.service
└─11485 java -server -Xms128m -Xmx1g -XX:MaxPermSize=256m -server -XX:+HeapDumpOnOutOfMemoryError -XX:HeapDumpPath=/opt/cgms-ssm/log -XX:-OmitStackTraceInFastThrow -Dbase.dir=/opt/cgms-ssm -Dlog4j...
Jun 20 17:44:10 fndnms systemd[1]: Starting (null)...
Jun 20 17:44:11 fndnms ssm[11477]: Starting Software Security Module Server: [ OK ]
Jun 20 17:44:11 fndnms systemd[1]: Started (null).
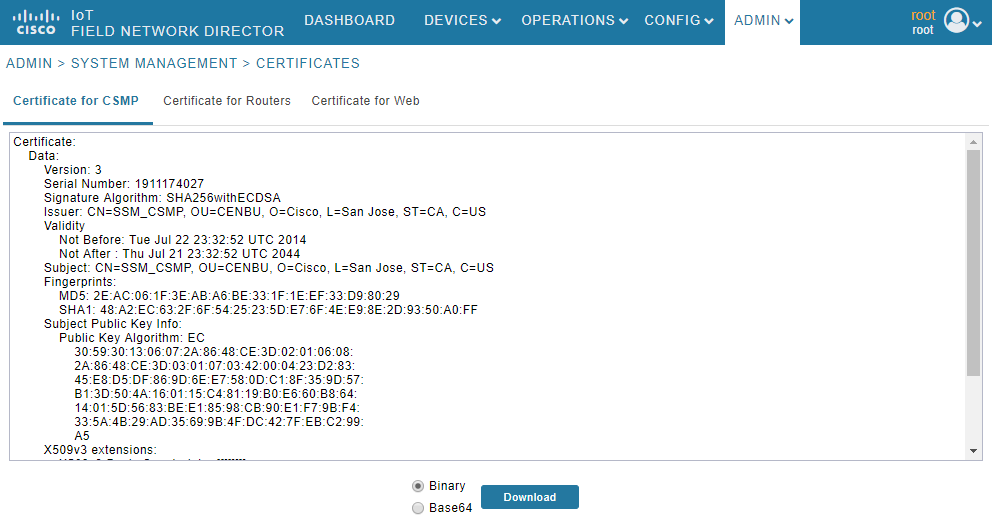
Você pode verificar se o FND é capaz de se comunicar com o SSM. Navegue até Admin > Certificados > Certificado para CSMP na GUI do FND.
Se tudo correr bem, você poderá ver o certificado CSMP no SSM como mostrado na imagem.
Colaborado por engenheiros da Cisco
- Jens DepuydtCisco TAC Engineer
Contate a Cisco
- Abrir um caso de suporte

- (É necessário um Contrato de Serviço da Cisco)
 Feedback
Feedback