Configurar PBR com SLAs IP para ISP DUAL no FTD Gerenciado pelo FMC
Opções de download
Linguagem imparcial
O conjunto de documentação deste produto faz o possível para usar uma linguagem imparcial. Para os fins deste conjunto de documentação, a imparcialidade é definida como uma linguagem que não implica em discriminação baseada em idade, deficiência, gênero, identidade racial, identidade étnica, orientação sexual, status socioeconômico e interseccionalidade. Pode haver exceções na documentação devido à linguagem codificada nas interfaces de usuário do software do produto, linguagem usada com base na documentação de RFP ou linguagem usada por um produto de terceiros referenciado. Saiba mais sobre como a Cisco está usando a linguagem inclusiva.
Sobre esta tradução
A Cisco traduziu este documento com a ajuda de tecnologias de tradução automática e humana para oferecer conteúdo de suporte aos seus usuários no seu próprio idioma, independentemente da localização. Observe que mesmo a melhor tradução automática não será tão precisa quanto as realizadas por um tradutor profissional. A Cisco Systems, Inc. não se responsabiliza pela precisão destas traduções e recomenda que o documento original em inglês (link fornecido) seja sempre consultado.
Contents
Introdução
Este documento descreve como configurar o PBR junto com os SLAs IP em um FTD que é gerenciado pelo (FMC).
Contribuição de Daniel Perez Verti Vazquez, engenheiro do Cisco TAC.
Pré-requisitos
Requisitos
A Cisco recomenda que você tenha conhecimento destes tópicos:
- configuração de PBR em
Cisco Adaptive Security Appliance (ASA) - FlexConfig ativado
Firepower - SLAs IP
Componentes Utilizados
As informações neste documento são baseadas nestas versões de software e hardware:
- Cisco FTD versão 7.0.0 (Build 94)
- Cisco FMC versão 7.0.0 (Build 94)
As informações neste documento foram criadas a partir de dispositivos em um ambiente de laboratório específico. Todos os dispositivos utilizados neste documento foram iniciados com uma configuração (padrão) inicial. Se a rede estiver ativa, certifique-se de que você entenda o impacto potencial de qualquer comando.
Informações de Apoio
Este documento descreve como configurar Policy Based Routing (PBR) junto com Internet Protocol Service Level Agreement (IP SLA) em um Cisco Firepower Threat Defense (FTD) que é gerenciado pelo Cisco Firepower Management Center (FMC).
O roteamento tradicional toma decisões de encaminhamento com base apenas nos endereços IP de destino. O PBR é uma alternativa aos protocolos de roteamento e roteamento estático.
Ele fornece um controle mais granular sobre o roteamento, pois permite o uso de parâmetros como endereços IP de origem ou portas de origem e destino como critérios de roteamento além do endereço IP de destino.
Possíveis cenários para PBR incluem aplicativos sensíveis à origem ou tráfego em links dedicados.
Junto com o PBR, os SLAs IP podem ser implementados para garantir a disponibilidade do próximo salto. Um SLA IP é um mecanismo que monitora a conectividade de ponta a ponta através da troca de pacotes regulares.
No momento da publicação, o PBR não é suportado diretamente pelo FMC Graphical User Interface (GUI) , a configuração do recurso requer o uso de políticas FlexConfig.
Por outro lado, somente Internet Control Message Protocol (ICMP) os SLAs são suportados pelo FTD.
Neste exemplo, o PBR é usado para rotear pacotes em um circuito primário Internet Service Provider (ISP) com base no endereço IP de origem.
Enquanto isso, um SLA IP monitora a conectividade e força um recuo para o circuito de backup em caso de qualquer falha.
Configurar
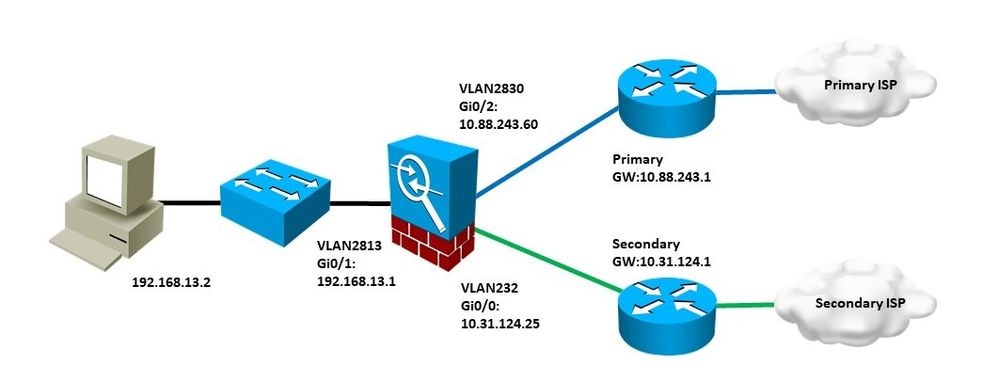
Diagrama de Rede
Neste exemplo, o Cisco FTD tem duas interfaces externas: VLAN230 e VLAN232. Cada uma se conecta a um ISP diferente.
O tráfego da rede interna VLAN2813 é roteado através do ISP primário que usa PBR.
O mapa de rotas PBR toma decisões de encaminhamento com base apenas no endereço IP de origem (tudo o que é recebido da VLAN2813 deve ser roteado para 10.88.243.1 na VLAN230) e é aplicado na interface GigabitEthernet 0/1 de FTD.
Enquanto isso, o FTD usa SLAs IP para monitorar a conectividade com cada gateway do ISP. Em caso de qualquer falha na VLAN230, o FTD faz failovers para o circuito de backup na VLAN232.
Configurações
Etapa 1. Configurar a lista de acesso PBR
Na primeira etapa da configuração de PBR, defina quais pacotes devem ser sujeitos à política de roteamento. O PBR usa mapas de rotas e lista de acesso para identificar o tráfego.
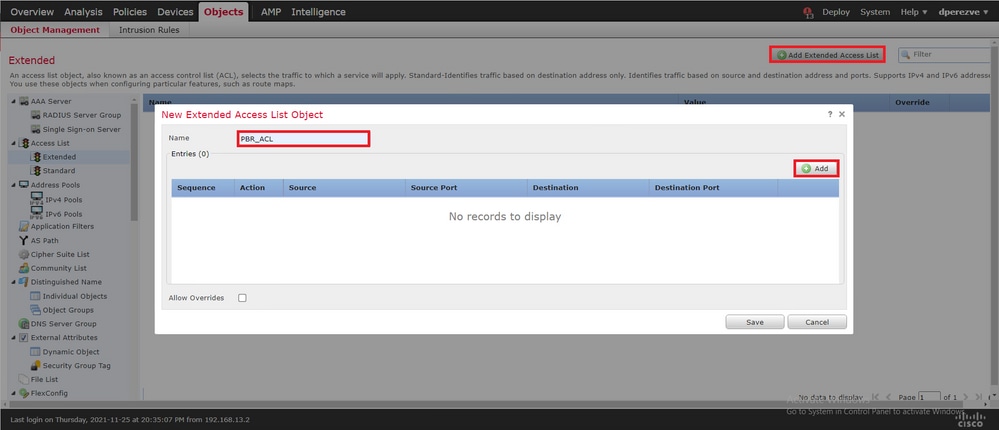
Para definir uma lista de acesso para os critérios de correspondência, navegue para Objects > Object Management e selecione Extended na Access List categoria no sumário.

Clique em . Add Extended Access List Na janela, New Extended Access List Object atribua um nome para o objeto e, em seguida, selecione o Add botão para começar com a configuração da lista de acesso.
Na janela, Add Extended Access List Entry selecione o objeto que representa a rede interna, neste caso, VLAN2813.
Clique em Add to Source para defini-la como a origem da lista de acesso.
Clique em Add para criar a entrada.

Clique em . Save O objeto deve ser adicionado à lista de objetos.

Etapa 2. Configurar o mapa de rota PBR
Depois que a lista de acesso PBR estiver configurada, atribua-a a um mapa de rotas. O mapa de rotas avalia o tráfego em relação às cláusulas de correspondência definidas na lista de acesso.
Após uma correspondência, o mapa de rotas executa as ações definidas na política de roteamento.
Para definir o mapa de rotas, navegue até Objects > Object Management o sumário e selecione-o Route Map .

Clique em Add Route Map >. No campo New Route Map Object Atribuir um nome para o objeto, clique em Add para criar uma nova entrada do mapa de rotas.

Na janela, Add Route Map Entry defina um número de sequência para a posição da nova entrada.
Navegue para IPv4 > Match Clauses e selecione Extended no menu Available Access List suspenso.
Selecione o objeto da lista de acesso criado na Etapa 1.
Clique em Add para criar a entrada.
Note: O FTD suporta até 65536 (de 0 a 65535) entradas diferentes. Quanto menor o número, maior a avaliação de prioridade.

Clique em Save . Adicione o objeto à lista de objetos.

Etapa 3. Configurar objetos de texto FlexConfig
A próxima etapa envolve a definição de objetos de texto FlexConfig que representam Gateways padrão para cada circuito. Esses objetos de texto são usados posteriormente na configuração do objeto FlexConfig que associa o PBR aos SLAs.
Para definir um objeto de texto FlexConfig, navegue até Objects > Object Management e selecione Text Object na categoria FlexConfig no sumário.
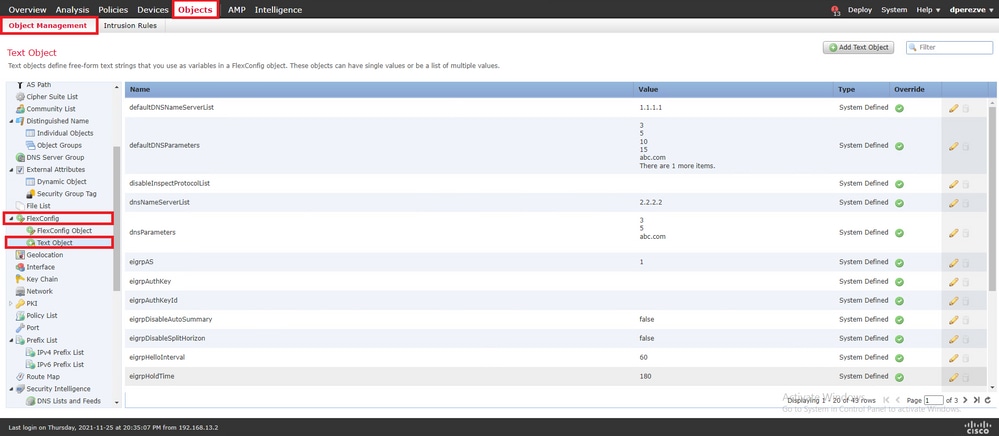
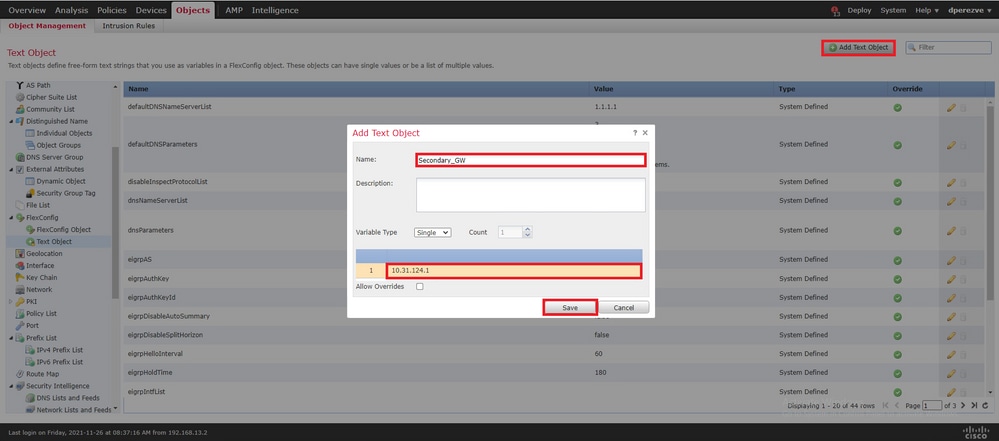
Clique em . Add Text Object Na Add Text Object janela, atribua um nome ao objeto que representa o Gateway principal e especifique o endereço IPv4 desse dispositivo.
Clique Save para adicionar o novo objeto.
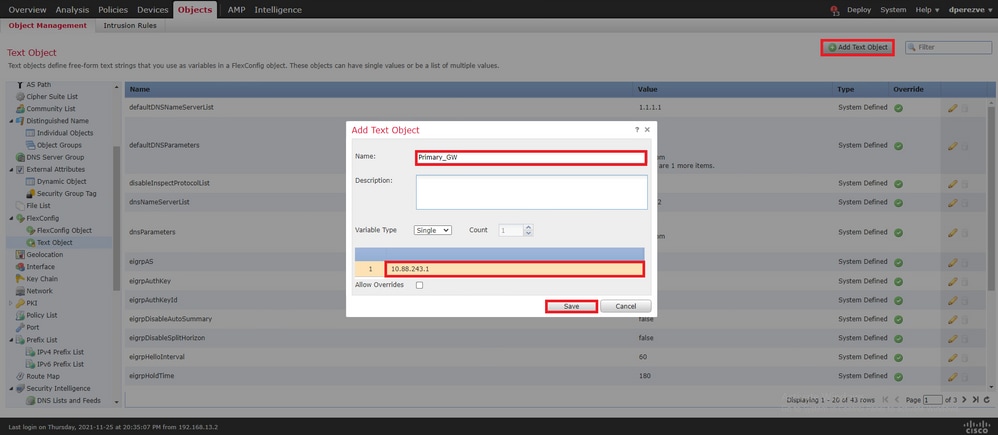
Clique Add Text Object novamente para criar um segundo objeto, desta vez para o Gateway no circuito de backup.
Preencha o novo objeto com o nome e endereço IP apropriados e clique em Save .
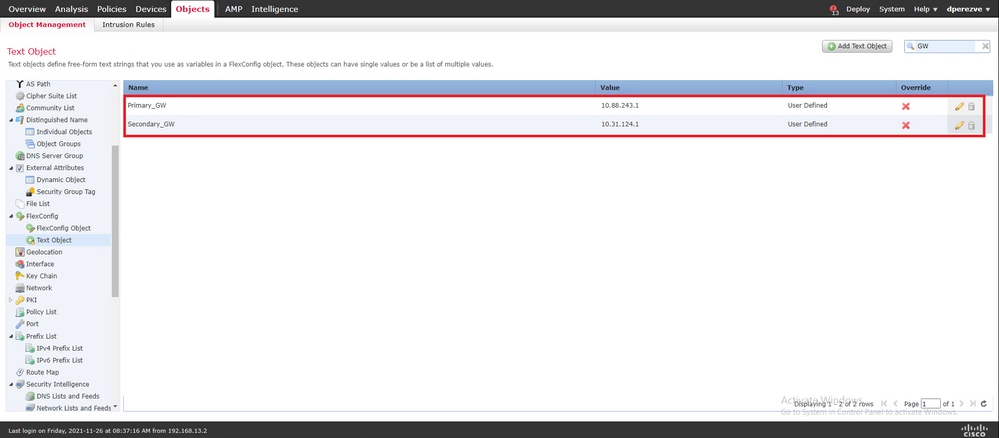
Os dois objetos devem ser adicionados à lista junto com os objetos padrão.
Etapa 4. Configurar o monitor de SLA
Para definir os objetos de SLA usados para monitorar a conectividade com cada Gateway, navegue até Objects > Object Management o sumário e selecione SLA Monitor -o.

Selecione o Add SLA Monitor objeto.
Na janela, New SLA Monitor defina um nome junto com um identificador para a operação do SLA, o endereço IP do dispositivo que deve ser monitorado (nesse caso, o Gateway principal) e a interface ou zona através da qual o dispositivo pode ser alcançado.
Além disso, também é possível ajustar o tempo limite e o limite. Clique em . Save
Note: O FTD suporta até 2.000 operações de SLA. Os valores da ID do SLA variam de 1 a 2147483647.
Note: Se os valores de tempo limite e limite não forem especificados, o FTD usará os temporizadores padrão: 5000 milissegundos em cada caso.

Selecione o Add SLA Monitor botão mais uma vez para criar um segundo objeto, desta vez para o Gateway no circuito de backup.
Preencha o novo objeto com as informações apropriadas, verifique se o ID do SLA é diferente daquele definido para o Gateway principal e salve as alterações.

Os dois objetos devem ser adicionados à lista.

Etapa 4. Configurar rotas estáticas com o Route Track
Depois que os objetos SLA IP forem criados, defina uma rota para cada Gateway e associe-os aos SLAs.
Na verdade, essas rotas não fornecem conectividade de dentro para fora (todo o roteamento é executado por PBR); em vez disso, elas são necessárias para rastrear a conectividade com os Gateways por meio de SLAs.
Para configurar rotas estáticas, navegue até Devices > Device Management , edite o FTD disponível e selecione Static Route no índice na Routing guia.
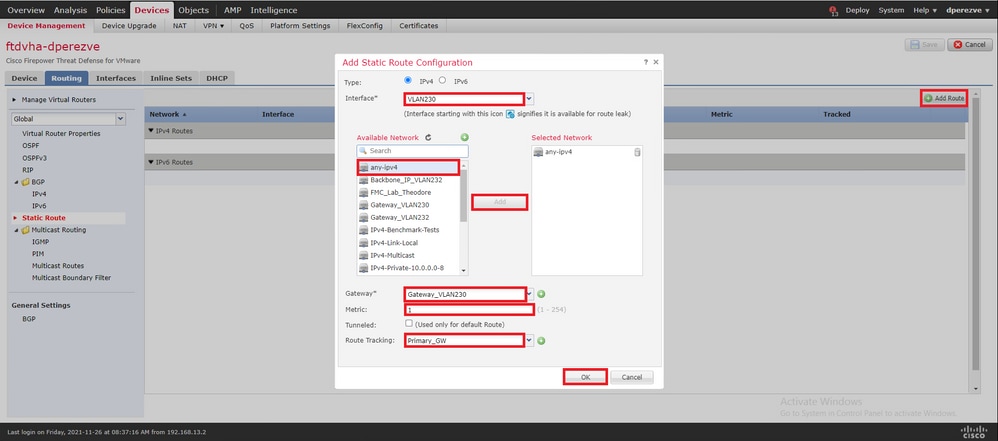
Na janela Add Static Route Configuration , no menu suspenso Interface, especifique o nome da interface por meio da qual o Gateway principal deve estar acessível.
Em seguida, selecione a rede de destino e o Gateway principal no Gateway menu suspenso.
Especifique uma métrica para a rota e no menu Route Track suspenso e selecione o objeto SLA para o gateway principal criado na Etapa 3.
Clique em OK para adicionar a nova rota.
Uma segunda rota estática deve ser configurada para o Gateway de backup.
Clique Add Route para definir uma nova rota estática.
Preencha o Add Static Route Configuration com as informações do Gateway de backup e verifique se a métrica dessa rota é superior à configurada na primeira rota.

As duas rotas devem ser adicionadas à lista.

Etapa 5. Configurar o objeto FlexConfig do PBR
Habilite os SLAs no mapa de rota usado para o PBR e aplique esse mapa de rota em uma interface do FTD.
Até agora, o mapa de rotas foi associado apenas à lista de acesso que define os critérios de correspondência. No entanto, os últimos ajustes não são suportados pela GUI do FMC, portanto um objeto FlexConfig é necessário.
Para definir o objeto PBR FlexConfig, navegue Objects > Object Management para e selecione FlexConfig Object na FlexConfig categoria no sumário.
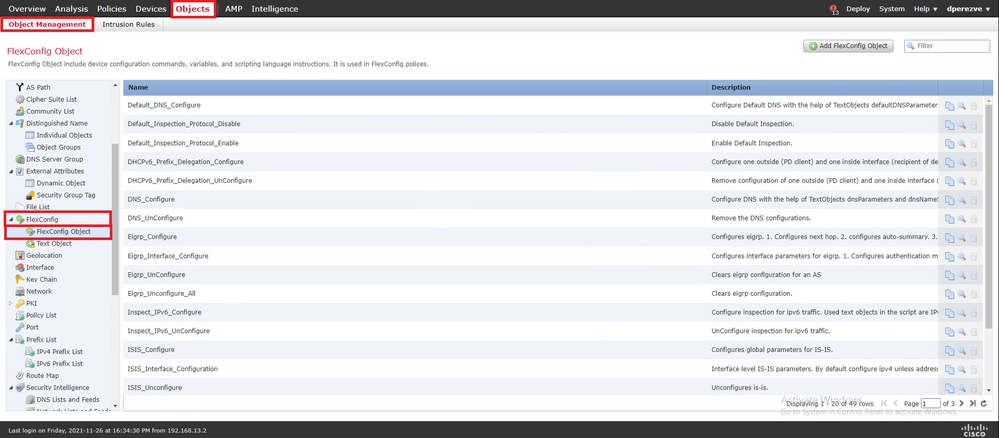
Selecione o Add FlexConfig Object botão. Na janela, Add FlexConfig Object atribua um nome e navegue até Insert > Insert Policy Object > Route Map .
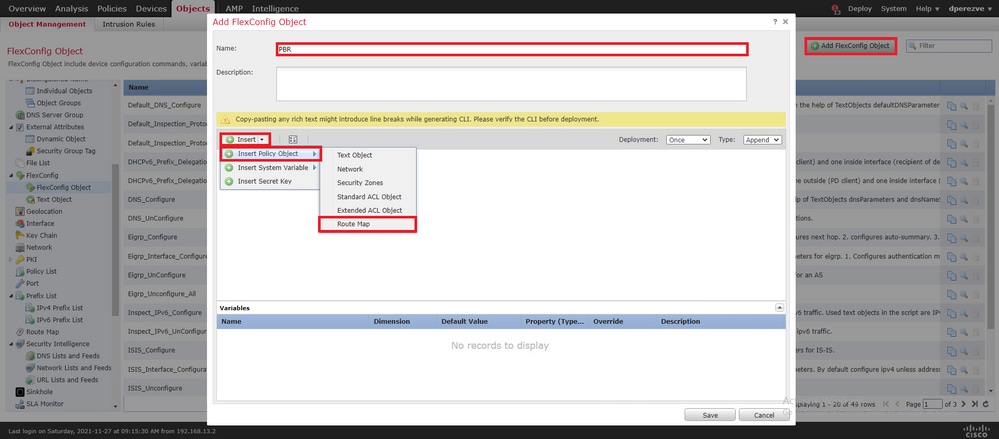
Na janela, Insert Route Map Variable atribua um nome para a variável e selecione o objeto PBR criado na Etapa 2.
Clique Save para adicionar o mapa de rotas como parte do objeto FlexConfig.


Além da variável de mapa de rotas, devemos adicionar os objetos de texto FlexConfig que representam cada Gateway (definido na Etapa 3). Na janela, Add FlexConfig Object navegue até Insert > Insert Policy Object > Text Object .
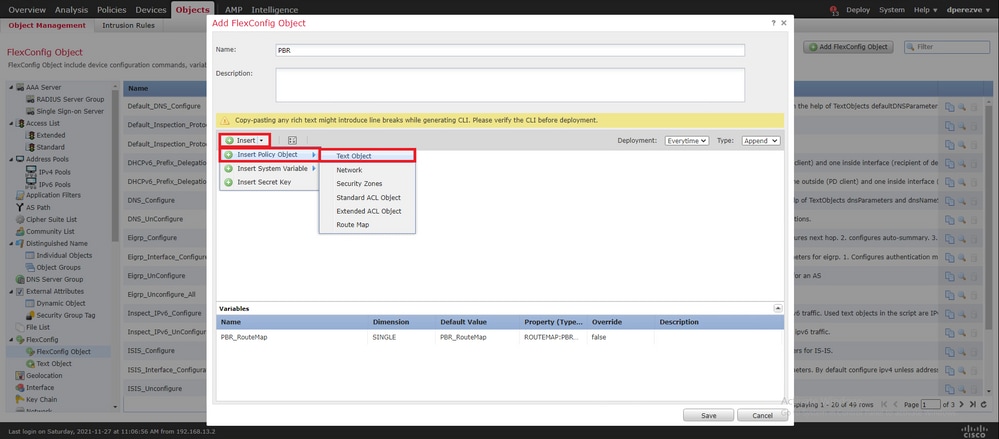
Na janela, Insert Text Object Variable atribua um nome para a variável e selecione o objeto de texto que representa o Gateway primário definido na Etapa 3.
Clique Save no botão para adicioná-lo ao objeto FlexConfig.
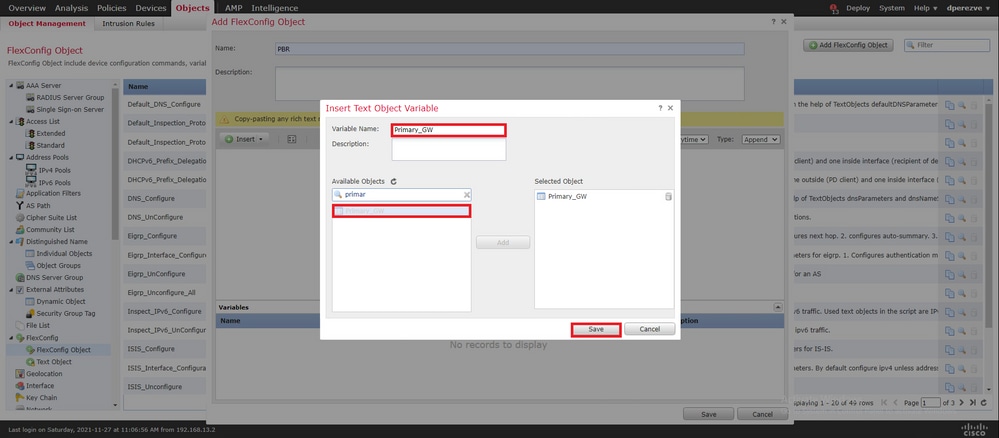
Repita essas últimas etapas para o Gateway de backup. No final do processo, as duas variáveis devem ser acrescentadas ao objeto FlexConfig.

A sintaxe para a configuração do PBR deve ser a mesma do Cisco ASA. O número de sequência para o mapa de rotas deve corresponder ao configurado na Etapa 2 (10 neste caso), bem como as IDs de SLA.
Para configurar o PBR para verificar a disponibilidade do próximo salto, o set ip next-hop verify-availability comando deve ser usado.
O mapa de rotas deve ser aplicado à interface interna, neste caso, VLAN2813. Use o policy-route route-map comando na configuração da interface.
Clique em Save quando a configuração estiver concluída.
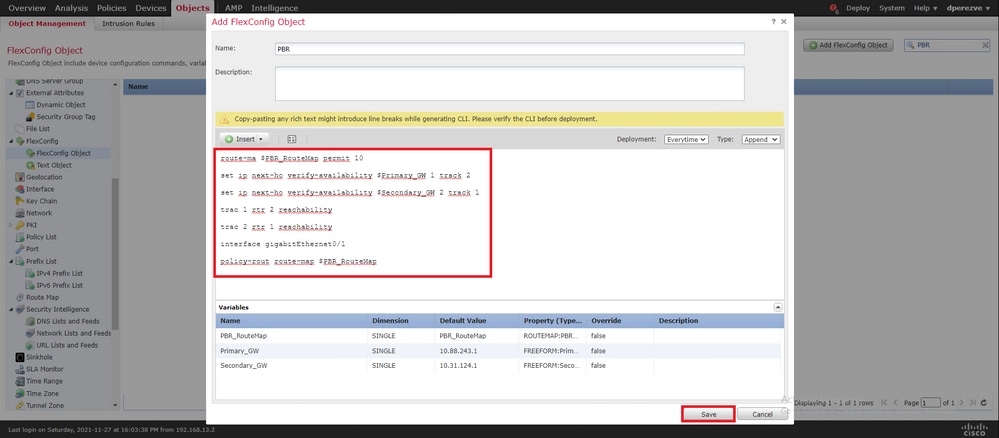
O objeto FlexConfig deve ser adicionado à lista.
Etapa 6. Atribuir objeto FlexConfig PBR à política FlexConfig
Navegue até Devices > FlexConfig a política FlexConfig em mãos e edite-a.
Selecione o objeto PBR FlexConfig Available FlexConfig no sumário, salve as alterações e implante as alterações no FTD.

Verificar
Após o término da implantação, o FTD deve enviar solicitações de eco ICMP regulares aos dispositivos monitorados para garantir a acessibilidade. Enquanto isso, uma rota rastreada para o Gateway principal deve ser adicionada à tabela de roteamento.
firepower# show route-map
route-map PBR_RouteMap, permit, sequence 10
Match clauses:
ip address (access-lists): PBR_ACL
Set clauses:
ip next-hop verify-availability 10.88.243.1 1 track 2 [up]
ip next-hop verify-availability 10.31.124.1 2 track 1 [up]
firepower# show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF
Gateway of last resort is 10.88.243.1 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 10.88.243.1, VLAN230
C 10.31.124.0 255.255.255.0 is directly connected, VLAN232
L 10.31.124.25 255.255.255.255 is directly connected, VLAN232
C 10.88.243.0 255.255.255.0 is directly connected, VLAN230
L 10.88.243.60 255.255.255.255 is directly connected, VLAN230
C 192.168.13.0 255.255.255.0 is directly connected, VLAN2813
L 192.168.13.1 255.255.255.255 is directly connected, VLAN2813Como a conectividade com o Gateway principal está ativa, o tráfego da sub-rede interna (VLAN2813) deve ser encaminhado através do circuito ISP principal.
firepower# packet-tracer input vlan2813 icmp 192.168.13.2 8 0 8.8.8.8 detailed
Phase: 1
Type: PBR-LOOKUP
Subtype: policy-route
Result: ALLOW
Config:
route-map PBR_RouteMap permit 10
match ip address PBR_ACL
set ip next-hop verify-availability 10.88.243.1 1 track 2
set ip next-hop verify-availability 10.31.124.1 2 track 1
Additional Information:
Matched route-map PBR_RouteMap, sequence 10, permit
Found next-hop 10.88.243.1 using egress ifc VLAN230
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172250, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 3
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=176701, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN230) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170013860, priority=6, domain=nat, deny=false
hits=168893, user_data=0x1461af306540, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN230(vrfid:0)
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188129, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=176710, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 7
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172250, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 8
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=176702, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 9
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN230) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170013860, priority=6, domain=nat, deny=false
hits=168893, user_data=0x1461af306540, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN230(vrfid:0)
Phase: 10
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188129, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 11
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=176710, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 12
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172250, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 13
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=176702, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 14
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN230) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170013860, priority=6, domain=nat, deny=false
hits=168894, user_data=0x1461af306540, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN230(vrfid:0)
Phase: 15
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188129, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 16
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=176710, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 17
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172250, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 18
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=176702, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 19
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN230) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170013860, priority=6, domain=nat, deny=false
hits=168894, user_data=0x1461af306540, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN230(vrfid:0)
Phase: 20
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188130, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 21
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=176710, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 22
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172250, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 23
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=176702, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 24
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN230) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170013860, priority=6, domain=nat, deny=false
hits=168894, user_data=0x1461af306540, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN230(vrfid:0)
Phase: 25
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188130, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 26
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=176711, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=anyError: not enough buffer space to print ASP rule
Result:
input-interface: VLAN2813(vrfid:0)
input-status: up
input-line-status: up
output-interface: VLAN230(vrfid:0)
output-status: up
output-line-status: up
Action: allow
Se o FTD não receber uma resposta de eco do Gateway primário dentro do temporizador de limite especificado no objeto Monitor de SLA, o host será considerado inalcançável e marcado como inativo. A rota rastreada para o Gateway principal também é substituída pela rota rastreada para o peer de backup.
firepower# show route-map
route-map PBR_RouteMap, permit, sequence 10
Match clauses:
ip address (access-lists): PBR_ACL
Set clauses:
ip next-hop verify-availability 10.88.243.1 1 track 2 [down]
ip next-hop verify-availability 10.31.124.1 2 track 1 [up]
firepower# show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF
Gateway of last resort is 10.31.124.1 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [2/0] via 10.31.124.1, VLAN232
C 10.31.124.0 255.255.255.0 is directly connected, VLAN232
L 10.31.124.25 255.255.255.255 is directly connected, VLAN232
C 192.168.13.0 255.255.255.0 is directly connected, VLAN2813
L 192.168.13.1 255.255.255.255 is directly connected, VLAN2813
O 622001 de mensagens informativas é gerado sempre que o FTD adiciona ou remove uma rota rastreada da tabela de roteamento.
firepower# show logg | i 622001
%FTD-6-622001: Removing tracked route 0.0.0.0 0.0.0.0 10.31.124.1, distance 2, table default, on interface VLAN232%FTD-6-305012: Teardown dynamic UDP translation from VLAN2813:192.168.13.5/49641 to VLAN230:10.88.243.60/49641 duration 0:02:10Agora, todo o tráfego de VLAN2813 deve ser encaminhado através do circuito ISP de backup.
firepower# packet-tracer input vlan2813 icmp 192.168.13.2 8 0 8.8.8.8 detailed
Phase: 1
Type: PBR-LOOKUP
Subtype: policy-route
Result: ALLOW
Config:
route-map PBR_RouteMap permit 10
match ip address PBR_ACL
set ip next-hop verify-availability 10.88.243.1 1 track 2
set ip next-hop verify-availability 10.31.124.1 2 track 1
Additional Information:
Matched route-map PBR_RouteMap, sequence 10, permit
Found next-hop 10.31.124.1 using egress ifc VLAN232
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172729, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 3
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=177180, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN232) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170032540, priority=6, domain=nat, deny=false
hits=8251, user_data=0x1461af306740, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN232(vrfid:0)
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188612, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=177189, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 7
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172729, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 8
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=177181, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 9
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN232) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170032540, priority=6, domain=nat, deny=false
hits=8251, user_data=0x1461af306740, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN232(vrfid:0)
Phase: 10
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188612, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 11
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=177189, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 12
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172729, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 13
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=177181, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 14
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN232) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170032540, priority=6, domain=nat, deny=false
hits=8252, user_data=0x1461af306740, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN232(vrfid:0)
Phase: 15
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188612, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 16
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=177189, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 17
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172729, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 18
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=177181, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 19
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN232) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170032540, priority=6, domain=nat, deny=false
hits=8252, user_data=0x1461af306740, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN232(vrfid:0)
Phase: 20
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188613, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 21
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=177189, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 22
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced trust ip ifc VLAN2813 object VLAN2813 any rule-id 268437505 event-log flow-end
access-list CSM_FW_ACL_ remark rule-id 268437505: PREFILTER POLICY: ftdvha-dperezve
access-list CSM_FW_ACL_ remark rule-id 268437505: RULE: Internet_Traffic
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461708f7a90, priority=12, domain=permit, trust
hits=172729, user_data=0x146183cf8380, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any, ifc=VLAN2813(vrfid:0)
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 23
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170d472a0, priority=7, domain=conn-set, deny=false
hits=177181, user_data=0x146170d413f0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Phase: 24
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (VLAN2813,VLAN232) after-auto source dynamic VLAN2813 interface
Additional Information:
Forward Flow based lookup yields rule:
in id=0x146170032540, priority=6, domain=nat, deny=false
hits=8252, user_data=0x1461af306740, cs_id=0x0, flags=0x0, protocol=0
src ip/id=192.168.13.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=VLAN232(vrfid:0)
Phase: 25
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461af9c3320, priority=0, domain=nat-per-session, deny=true
hits=188613, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 26
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x1461aff02da0, priority=0, domain=inspect-ip-options, deny=true
hits=177190, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=VLAN2813(vrfid:0), output_ifc=any
Result:
input-interface: VLAN2813(vrfid:0)
input-status: up
input-line-status: up
output-interface: VLAN232(vrfid:0)
output-status: up
output-line-status: up
Action: allow
Troubleshooting
Para validar em qual entrada de PBR é aplicada interesting traffic , execute o comando debug policy-route.
firepower# debug policy-route
debug policy-route enabled at level 1
firepower# pbr: policy based route lookup called for 192.168.13.5/45951 to 208.67.220.220/53 proto 17 sub_proto 0 received on interface VLAN2813, NSGs, nsg_id=none
pbr: First matching rule from ACL(2)
pbr: route map PBR_RouteMap, sequence 10, permit; proceed with policy routing
pbr: evaluating verified next-hop 10.88.243.1
pbr: policy based routing applied; egress_ifc = VLAN230 : next_hop = 10.88.243.1
pbr: policy based route lookup called for 192.168.13.5/56099 to 208.67.220.220/53 proto 17 sub_proto 0 received on interface VLAN2813, NSGs, nsg_id=none
pbr: First matching rule from ACL(2)
pbr: route map PBR_RouteMap, sequence 10, permit; proceed with policy routing
pbr: evaluating verified next-hop 10.88.243.1
pbr: policy based routing applied; egress_ifc = VLAN230 : next_hop = 10.88.243.1
pbr: policy based route lookup called for 192.168.13.2/24 to 8.8.8.8/0 proto 1 sub_proto 8 received on interface VLAN2813, NSGs, nsg_id=none
pbr: First matching rule from ACL(2)
pbr: route map PBR_RouteMap, sequence 10, permit; proceed with policy routing
pbr: evaluating verified next-hop 10.88.243.1
pbr: policy based routing applied; egress_ifc = VLAN230 : next_hop = 10.88.243.1
pbr: policy based route lookup called for 192.168.13.5/40669 to 208.67.220.220/53 proto 17 sub_proto 0 received on interface VLAN2813, NSGs, nsg_id=none
Histórico de revisões
| Revisão | Data de publicação | Comentários |
|---|---|---|
1.0 |
29-Nov-2021 |
Versão inicial |
Colaborado por engenheiros da Cisco
- Daniel Perez Vertti VazquezEngenheiro do Cisco TAC
Contate a Cisco
- Abrir um caso de suporte

- (É necessário um Contrato de Serviço da Cisco)
 Feedback
Feedback