在FP9300(机箱内)上配置FTD集群
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
目录
简介
本文档介绍如何在FPR9300设备上配置和验证集群功能。
警告:本文档中提供的信息包括集群的初始安装/配置。本文档不适用于设备更换(退货授权 — RMA)流程
先决条件
要求
本文档没有任何特定的要求。
使用的组件
本文档中的信息基于以下软件和硬件版本:
- 运行1.1(4.95)的思科Firepower 9300安全设备
- 运行6.0.1的Firepower威胁防御(FTD)(内部版本1213)
- 运行6.0.1.1的FireSIGHT管理中心(FMC)(内部版本1023)
实验完成时间:1 小时.
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
背景信息
- 在带FTD设备的FPR9300上,您可以在所有受支持版本上配置机箱内集群。
- 机箱间集群在6.2中引入。
- 端口通道48创建为集群控制链路。对于机箱内集群,此链路使用Firepower 9300背板进行集群通信。
- 不支持单个数据接口,管理接口除外。
- 管理接口分配给集群中的所有设备。
配置
网络图

任务1.为FTD集群创建必要接口
任务要求:
创建集群、管理接口和端口通道数据接口。
解决方案:
步骤1.创建端口通道数据接口。
要创建新接口,您必须登录FPR9300机箱管理器并导航至接口选项卡。
选择Add Port Channel并使用以下参数创建新的端口通道接口:
| 端口通道ID |
5 |
| 类型 |
数据 |
| enable |
Yes |
| 成员ID |
Ethernet1/3、Ethernet 1/4 |
选择OK以保存配置,如图所示。

步骤2.创建管理接口。
在Interfaces选项卡上,选择该接口,单击Edit并配置Management Type接口。
单击OK保存配置,如图所示。

步骤3.创建集群控制链路接口。
单击“添加端口通道”按钮,然后使用这些参数创建一个新的端口通道接口,如图所示。
| 端口通道ID |
48 |
| 类型 |
集群 |
| enable |
Yes |
| 成员ID |
- |

任务2.创建FTD集群
任务要求:
创建FTD集群设备。
解决方案:
步骤1.导航至Logical Devices,然后单击Add Device按钮。
创建FTD集群,如下所示:
| 设备名 |
FTD_cluster |
| 模板 |
思科Firepower威胁防御 |
| 映像版本 |
6.0.1.1213 |
| 设备模式 |
集群 |
要添加设备,请单击OK,如图所示。

步骤2.配置和部署FTD集群。
创建FTD设备后,系统会将您重定向到Provisioning- device_name窗口。
点击设备图标以启动配置,如图所示。
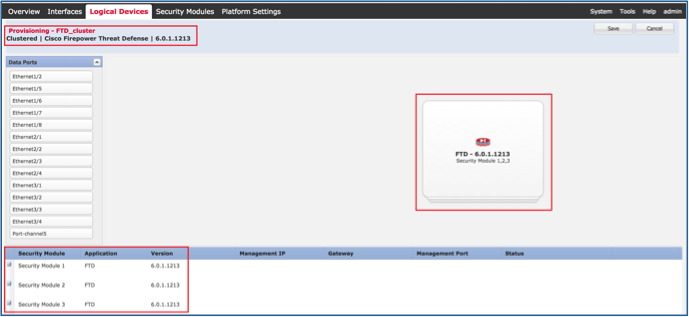
使用这些设置配置FTD集群信息选项卡,如图所示。
| 群集密钥 |
思科 |
| 群集组名称 |
FTD_cluster |
| 管理接口 |
以太网接口1/1 |

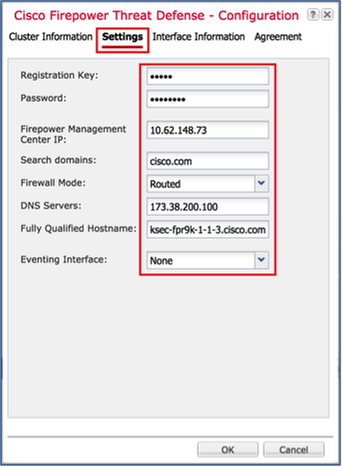
使用这些设置配置FTD设置选项卡,如图所示。
| 注册密钥 |
思科 |
| 密码 |
管理123 |
| Firepower管理中心IP |
10.62.148.73 |
| 搜索域 |
cisco.com |
| 防火墙模式 |
路由 |
| DNS Servers |
173.38.200.100 |
| 完全限定主机名 |
ksec-fpr9k-1-1-3.cisco.com |
| 事件接口 |
无 |
使用这些设置配置FTD接口信息选项卡,如图所示。
| 地址类型 |
仅IPv4 |
| 安全模块1 |
|
| 管理IP |
10.62.148.67 |
| 网络掩码 |
255.255.255.128 |
| 网关 |
10.62.148.1 |
| 安全模块2 |
|
| 管理IP |
10.62.148.68 |
| 网络掩码 |
255.255.255.128 |
| 网关 |
10.62.148.1 |
| 安全模块3 |
|
| 管理IP |
10.62.148.69 |
| 网络掩码 |
255.255.255.128 |
| 网关 |
10.62.148.1 |

接受“协议”选项卡上的协议,然后单击“确定”,如图所示。

步骤3.为FTD分配数据接口。
展开Data Ports区域,然后点击要分配给FTD的每个接口。完成后,选择Save以创建FTD集群,如图所示。
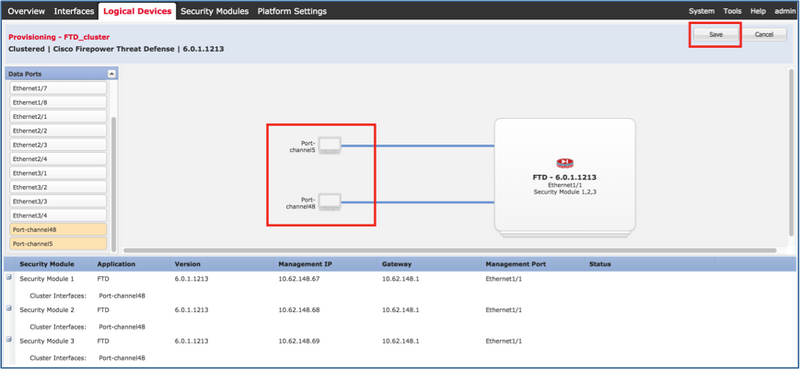
等待几分钟,以便集群部署,然后进行主设备选举。
验证:
- 从FPR9300 GUI,如图所示。

- 从FPR9300 CLI
FPR9K-1-A# FPR9K-1-A# scope ssa FPR9K-1-A /ssa # show app-instance Application Name Slot ID Admin State Operational State Running Version Startup Version Cluster Oper State -------------------- ---------- --------------- -------------------- --------------- --------------- ------------------ ftd 1 Enabled Online 6.0.1.1213 6.0.1.1213 In Cluster ftd 2 Enabled Online 6.0.1.1213 6.0.1.1213 In Cluster ftd 3 Enabled Online 6.0.1.1213 6.0.1.1213 In Cluster
- 从LINA(ASA)CLI
firepower# show cluster info
Cluster FTD_cluster: On
Interface mode: spanned
This is "unit-1-1" in state MASTER
ID : 0
Version : 9.6(1)
Serial No.: FLM19216KK6
CCL IP : 127.2.1.1
CCL MAC : 0015.c500.016f
Last join : 21:51:03 CEST Aug 8 2016
Last leave: N/A
Other members in the cluster:
Unit "unit-1-3" in state SLAVE
ID : 1
Version : 9.6(1)
Serial No.: FLM19206H7T
CCL IP : 127.2.1.3
CCL MAC : 0015.c500.018f
Last join : 21:51:05 CEST Aug 8 2016
Last leave: N/A
Unit "unit-1-2" in state SLAVE
ID : 2
Version : 9.6(1)
Serial No.: FLM19206H71
CCL IP : 127.2.1.2
CCL MAC : 0015.c500.019f
Last join : 21:51:30 CEST Aug 8 2016
Last leave: N/A
firepower# cluster exec show cluster interface-mode cluster interface-mode spanned unit-1-3:************************************************************* cluster interface-mode spanned unit-1-2:************************************************************* cluster interface-mode spanned firepower#
firepower# cluster exec show cluster history
==========================================================================
From State To State Reason
==========================================================================
21:49:25 CEST Aug 8 2016
DISABLED DISABLED Disabled at startup
21:50:18 CEST Aug 8 2016
DISABLED ELECTION Enabled from CLI
21:51:03 CEST Aug 8 2016
ELECTION MASTER_POST_CONFIG Enabled from CLI
21:51:03 CEST Aug 8 2016
MASTER_POST_CONFIG MASTER Master post config done and waiting for ntfy
==========================================================================
unit-1-3:*************************************************************
==========================================================================
From State To State Reason
==========================================================================
21:49:44 CEST Aug 8 2016
DISABLED DISABLED Disabled at startup
21:50:37 CEST Aug 8 2016
DISABLED ELECTION Enabled from CLI
21:50:37 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:41 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:41 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:46 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:46 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:51 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:51 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:56 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:56 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:01 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:51:01 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:04 CEST Aug 8 2016
ONCALL SLAVE_COLD Received cluster control message
21:51:04 CEST Aug 8 2016
SLAVE_COLD SLAVE_APP_SYNC Client progression done
21:51:05 CEST Aug 8 2016
SLAVE_APP_SYNC SLAVE_CONFIG Slave application configuration sync done
21:51:17 CEST Aug 8 2016
SLAVE_CONFIG SLAVE_BULK_SYNC Configuration replication finished
21:51:29 CEST Aug 8 2016
SLAVE_BULK_SYNC SLAVE Configuration replication finished
==========================================================================
unit-1-2:*************************************************************
==========================================================================
From State To State Reason
==========================================================================
21:49:24 CEST Aug 8 2016
DISABLED DISABLED Disabled at startup
21:50:16 CEST Aug 8 2016
DISABLED ELECTION Enabled from CLI
21:50:17 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:21 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:21 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:26 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:26 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:31 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:31 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:36 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:36 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:41 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:41 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:46 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:46 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:51 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:51 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:50:56 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:50:56 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:01 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:51:01 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:06 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:51:06 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:12 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:51:12 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:17 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:51:17 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:22 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:51:22 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:27 CEST Aug 8 2016
ONCALL ELECTION Received cluster control message
21:51:27 CEST Aug 8 2016
ELECTION ONCALL Received cluster control message
21:51:30 CEST Aug 8 2016
ONCALL SLAVE_COLD Received cluster control message
21:51:30 CEST Aug 8 2016
SLAVE_COLD SLAVE_APP_SYNC Client progression done
21:51:31 CEST Aug 8 2016
SLAVE_APP_SYNC SLAVE_CONFIG Slave application configuration sync done
21:51:43 CEST Aug 8 2016
SLAVE_CONFIG SLAVE_BULK_SYNC Configuration replication finished
21:51:55 CEST Aug 8 2016
SLAVE_BULK_SYNC SLAVE Configuration replication finished
==========================================================================
firepower#
任务3.将FTD集群注册到FMC
任务要求:
将逻辑设备添加到FMC,然后将其分组到集群。
解决方案:
步骤1.将逻辑设备添加到FMC。与FMC版本6.3一样,您必须仅注册一个FTD设备(建议成为主设备)。 其余FTD由FMC自动发现。
登录FMC并导航至“设备”>“设备管理”选项卡,然后单击“添加设备”。
使用映像中所述的设置添加第一个逻辑设备。
单击“Register(注册)”开始注册。
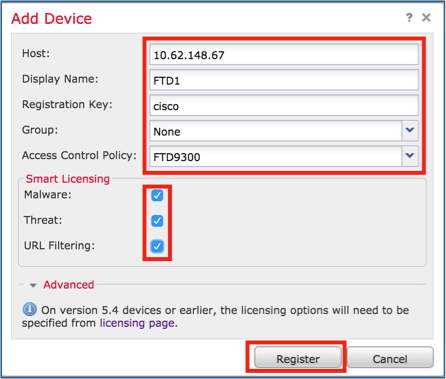
验证如图所示。

任务4.在FMC上配置端口通道子接口
任务要求:
为端口通道数据接口配置子接口。
解决方案:
步骤1.从FMC GUI中,选择“FTD_cluster编辑”按钮。
导航至接口选项卡,然后单击添加接口>子接口,如图所示。

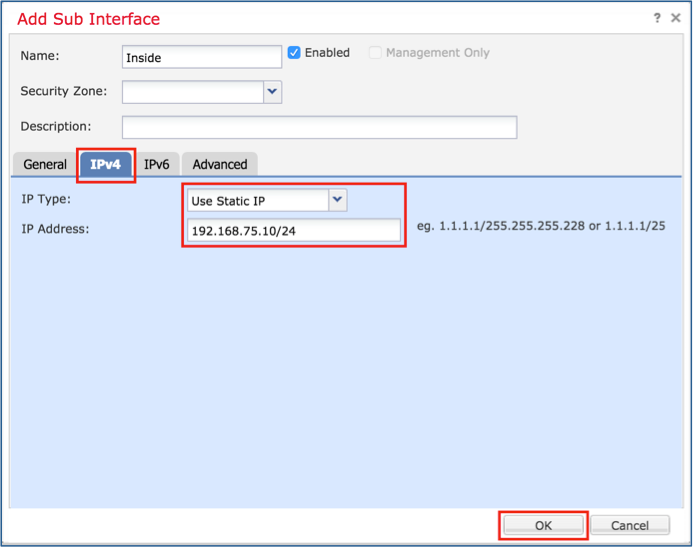
使用这些详细信息配置第一个子接口。选择OK以应用更改,如图所示。
| 名称 |
内部 |
| General 选项卡 |
|
| 接口 |
端口通道5 |
| 子接口ID |
201 |
| VLAN ID |
201 |
| IPv4选项卡 |
|
| IP类型 |
使用静态IP |
| IP Address |
192.168.75.10/24 |

使用这些详细信息配置第二个子接口。
| 名称 |
外部 |
| General 选项卡 |
|
| 接口 |
端口通道5 |
| 子接口ID |
210 |
| VLAN ID |
210 |
| IPv4选项卡 |
|
| IP类型 |
使用静态IP |
| IP Address |
192.168.76.10/24 |
单击OK以创建子接口。单击Save,然后Deploy changes to the FTD_cluster,如图所示。
验证:
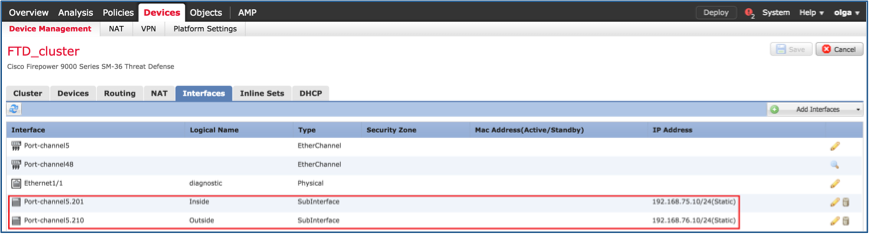
任务5.检验基本连通性
任务要求:
创建捕获并检查两台虚拟机之间的连接。
解决方案:
步骤1.在所有集群设备上创建捕获。
导航至主设备的LINA(ASA)CLI,并为内部和外部接口创建捕获。
firepower# firepower# cluster exec capture capi interface inside match icmp any any unit-1-1(LOCAL):****************************************************** unit-1-3:************************************************************* unit-1-2:************************************************************* firepower# firepower# cluster exec capture capo interface outside match icmp any any unit-1-1(LOCAL):****************************************************** unit-1-3:************************************************************* unit-1-2:************************************************************* firepower#
验证:
firepower# cluster exec show capture unit-1-1(LOCAL):****************************************************** capture capi type raw-data interface Inside [Capturing - 0 bytes] match icmp any any capture capo type raw-data interface Outside [Capturing - 0 bytes] match icmp any any unit-1-3:************************************************************* capture capi type raw-data interface Inside [Capturing - 0 bytes] match icmp any any capture capo type raw-data interface Outside [Capturing - 0 bytes] match icmp any any unit-1-2:************************************************************* capture capi type raw-data interface Inside [Capturing - 0 bytes] match icmp any any capture capo type raw-data interface Outside [Capturing - 0 bytes] match icmp any any firepower#
步骤2.从VM1对VM2执行ping测试。
对4个数据包进行测试。在测试后检查捕获输出:
firepower# cluster exec show capture unit-1-1(LOCAL):****************************************************** capture capi type raw-data interface Inside [Capturing - 0 bytes] match icmp any any capture capo type raw-data interface Outside [Capturing - 0 bytes] match icmp any any unit-1-3:************************************************************* capture capi type raw-data interface Inside [Capturing - 752 bytes] match icmp any any capture capo type raw-data interface Outside [Capturing - 752 bytes] match icmp any any unit-1-2:************************************************************* capture capi type raw-data interface Inside [Capturing - 0 bytes] match icmp any any capture capo type raw-data interface Outside [Capturing - 0 bytes] match icmp any any firepower#
运行命令以检查特定设备上的捕获输出:
firepower# cluster exec unit unit-1-3 show capture capi 8 packets captured 1: 12:58:36.162253 802.1Q vlan#201 P0 192.168.75.100 > 192.168.76.100: icmp: echo request 2: 12:58:36.162955 802.1Q vlan#201 P0 192.168.76.100 > 192.168.75.100: icmp: echo reply 3: 12:58:37.173834 802.1Q vlan#201 P0 192.168.75.100 > 192.168.76.100: icmp: echo request 4: 12:58:37.174368 802.1Q vlan#201 P0 192.168.76.100 > 192.168.75.100: icmp: echo reply 5: 12:58:38.187642 802.1Q vlan#201 P0 192.168.75.100 > 192.168.76.100: icmp: echo request 6: 12:58:38.188115 802.1Q vlan#201 P0 192.168.76.100 > 192.168.75.100: icmp: echo reply 7: 12:58:39.201832 802.1Q vlan#201 P0 192.168.75.100 > 192.168.76.100: icmp: echo request 8: 12:58:39.202321 802.1Q vlan#201 P0 192.168.76.100 > 192.168.75.100: icmp: echo reply 8 packets shown firepower# cluster exec unit unit-1-3 show capture capo 8 packets captured 1: 12:58:36.162543 802.1Q vlan#210 P0 192.168.75.100 > 192.168.76.100: icmp: echo request 2: 12:58:36.162894 802.1Q vlan#210 P0 192.168.76.100 > 192.168.75.100: icmp: echo reply 3: 12:58:37.174002 802.1Q vlan#210 P0 192.168.75.100 > 192.168.76.100: icmp: echo request 4: 12:58:37.174307 802.1Q vlan#210 P0 192.168.76.100 > 192.168.75.100: icmp: echo reply 5: 12:58:38.187764 802.1Q vlan#210 P0 192.168.75.100 > 192.168.76.100: icmp: echo request 6: 12:58:38.188085 802.1Q vlan#210 P0 192.168.76.100 > 192.168.75.100: icmp: echo reply 7: 12:58:39.201954 802.1Q vlan#210 P0 192.168.75.100 > 192.168.76.100: icmp: echo request 8: 12:58:39.202290 802.1Q vlan#210 P0 192.168.76.100 > 192.168.75.100: icmp: echo reply 8 packets shown firepower#
完成此任务后,使用下一个命令删除捕获:
firepower# cluster exec no capture capi unit-1-1(LOCAL):****************************************************** unit-1-3:************************************************************* unit-1-2:************************************************************* firepower# cluster exec no capture capo unit-1-1(LOCAL):****************************************************** unit-1-3:************************************************************* unit-1-2:*************************************************************
步骤3.从VM2下载文件到VM1。
VM1预配置为FTP服务器,VM2预配置为FTP客户端。
使用以下内容创建新捕获:
firepower# cluster exec capture capi interface inside match ip host 192.168.75.100 host 192.168.76.100 unit-1-1(LOCAL):****************************************************** unit-1-3:************************************************************* unit-1-2:************************************************************* firepower# cluster exec capture capo interface outside match ip host 192.168.775.100 host 192.168.76.100 unit-1-1(LOCAL):****************************************************** unit-1-3:************************************************************* unit-1-2:*************************************************************
使用FTP客户端将文件从VM2下载到VM1。
检查show conn输出:
firepower# cluster exec show conn all
unit-1-1(LOCAL):******************************************************
20 in use, 21 most used
Cluster:
fwd connections: 0 in use, 2 most used
dir connections: 0 in use, 52 most used
centralized connections: 0 in use, 6 most used
TCP Outside 192.168.76.100:49175 Inside 192.168.75.100:21, idle 0:00:32, bytes 665, flags UIOeN
UDP cluster 255.255.255.255:49495 NP Identity Ifc 127.2.1.1:49495, idle 0:00:00, bytes 17858058, flags -
TCP cluster 127.2.1.3:10844 NP Identity Ifc 127.2.1.1:38296, idle 0:00:33, bytes 5496, flags UI
…….
TCP cluster 127.2.1.3:59588 NP Identity Ifc 127.2.1.1:10850, idle 0:00:33, bytes 132, flags UO
unit-1-3:*************************************************************
12 in use, 16 most used
Cluster:
fwd connections: 0 in use, 4 most used
dir connections: 1 in use, 10 most used
centralized connections: 0 in use, 0 most used
TCP Outside 192.168.76.100:49175 Inside 192.168.75.100:21, idle 0:00:34, bytes 0, flags y
TCP cluster 127.2.1.1:10851 NP Identity Ifc 127.2.1.3:48493, idle 0:00:52, bytes 224, flags UI
……..
TCP cluster 127.2.1.1:64070 NP Identity Ifc 127.2.1.3:10847, idle 0:00:11, bytes 806, flags UO
unit-1-2:*************************************************************
12 in use, 15 most used
Cluster:
fwd connections: 0 in use, 2 most used
dir connections: 0 in use, 3 most used
centralized connections: 0 in use, 0 most used
TCP cluster 127.2.1.1:10851 NP Identity Ifc 127.2.1.2:64136, idle 0:00:53, bytes 224, flags UI
……..
TCP cluster 127.2.1.1:15859 NP Identity Ifc 127.2.1.2:10847, idle 0:00:11, bytes 807, flags UO
显示捕获输出:
firepower# cluster exec show cap unit-1-1(LOCAL):****************************************************** capture capi type raw-data interface Inside [Buffer Full - 523954 bytes] match ip host 192.168.75.100 host 192.168.76.100 capture capo type raw-data interface Outside [Buffer Full - 524028 bytes] match ip host 192.168.75.100 host 192.168.76.100 unit-1-3:************************************************************* capture capi type raw-data interface Inside [Buffer Full - 524062 bytes] match ip host 192.168.75.100 host 192.168.76.100 capture capo type raw-data interface Outside [Buffer Full - 524228 bytes] match ip host 192.168.75.100 host 192.168.76.100 unit-1-2:************************************************************* capture capi type raw-data interface Inside [Capturing - 0 bytes] match ip host 192.168.75.100 host 192.168.76.100 capture capo type raw-data interface Outside [Capturing - 0 bytes] match ip host 192.168.75.100 host 192.168.76.100
从机箱管理器UI捕获集群
在下图中,您可以看到FPR9300上具有2个端口通道(8和48)的3单元集群。 逻辑设备是ASA,但在FTD的情况下将是相同的概念。需要记住的重要一点是,尽管有3个集群单元,但从捕获角度看,只有一个逻辑设备:


任务6.从集群中删除从设备
任务要求:
登录FMC并从集群中删除从属设备。
解决方案:
步骤1.登录FMC并导航至Device > Device Management。
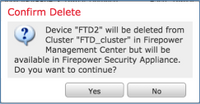
点击从设备旁边的垃圾桶图标,如图所示。

系统将显示确认窗口。选择是以确认,如图所示。
验证:
- 从FMC,如图所示。

- 从FXOS CLI。
FPR9K-1-A# scope ssa FPR9K-1-A /ssa # show app-instance Application Name Slot ID Admin State Operational State Running Version Startup Version Cluster Oper State -------------------- ---------- --------------- -------------------- --------------- --------------- ------------------ ftd 1 Enabled Online 6.0.1.1213 6.0.1.1213 In Cluster ftd 2 Enabled Online 6.0.1.1213 6.0.1.1213 In Cluster ftd 3 Enabled Online 6.0.1.1213 6.0.1.1213 In Cluster
- 从LINA(ASA)CLI。
firepower# show cluster info
Cluster FTD_cluster: On
Interface mode: spanned
This is "unit-1-1" in state MASTER
ID : 0
Version : 9.6(1)
Serial No.: FLM19216KK6
CCL IP : 127.2.1.1
CCL MAC : 0015.c500.016f
Last join : 21:51:03 CEST Aug 8 2016
Last leave: N/A
Other members in the cluster:
Unit "unit-1-3" in state SLAVE
ID : 1
Version : 9.6(1)
Serial No.: FLM19206H7T
CCL IP : 127.2.1.3
CCL MAC : 0015.c500.018f
Last join : 21:51:05 CEST Aug 8 2016
Last leave: N/A
Unit "unit-1-2" in state SLAVE
ID : 2
Version : 9.6(1)
Serial No.: FLM19206H71
CCL IP : 127.2.1.2
CCL MAC : 0015.c500.019f
Last join : 21:51:30 CEST Aug 8 2016
Last leave: N/A
firepower#
注意:设备从FMC未注册,但仍是FPR9300上的集群成员。
验证
使用本部分可确认配置能否正常运行。
验证已完成,并涵盖在各个任务中。
故障排除
目前没有针对此配置的故障排除信息。
相关信息
- Cisco Firepower管理中心配置指南的所有版本均位于以下位置:
https://www.cisco.com/c/en/us/td/docs/security/firepower/roadmap/firepower-roadmap.html#id_47280。
- FXOS机箱管理器和CLI配置指南的所有版本均可在以下位置找到:
- 思科全球技术支持中心(TAC)强烈推荐此可视化指南,以深入了解思科Firepower下一代安全技术的实用知识,包括本文中提到的知识:
http://www.ciscopress.com/title/9781587144806。
- 对于与Firepower技术相关的所有配置和故障排除技术说明。
https://www.cisco.com/c/en/us/support/security/defense-center/tsd-products-support-series-home.html。
由思科工程师提供
- Olha YakovenkoCisco TAC Engineer
- John LongCisco TAC Engineer
 反馈
反馈