配置、验证Firepower设备注册并对其进行故障排除
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
目录
简介
本文档介绍Firepower威胁防御(FTD)和Firepower管理中心(FMC)之间连接的故障排除过程。
先决条件
要求
本文档没有任何特定的要求。
使用的组件
本文档中的信息基于以下软件和硬件版本:
- FTD软件6.6.x和6.5.x
- FMC软件6.6.x
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
背景信息
本文档介绍托管FTD和托管FMC之间的连接(sftunnel)的操作、验证和故障排除过程。
信息和示例基于FTD,但大多数概念也完全适用于NGIPS(7000/8000系列设备)或ASA55xx上的FirePOWER模块。
FTD支持两种主要管理模式:
- 通过FMC实现机外-也称为远程管理
- 通过Firepower设备管理器(FDM)和/或Cisco Defense Orchestrator (CDO)进行内部部署-也称为本地管理
在远程管理情况下,FTD需要首先使用称为设备注册的进程向FMC注册。
完成注册后,FTD和FMC将建立名为sftunnel(名称源自Sourcefire隧道)的安全隧道。
设计选项
从设计的角度来看,FTD - FMC可以在同一个L3子网中:
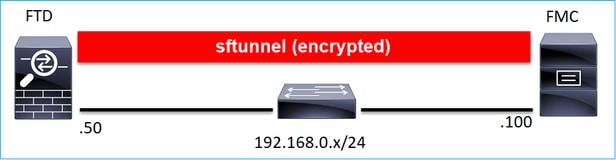
或由不同的网络分隔:
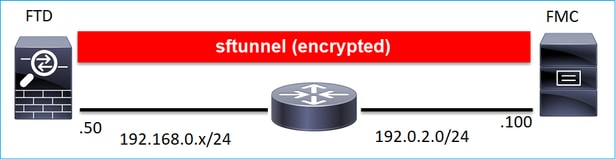
192.0.2.0
注意:sftunnel也可以通过FTD本身。不推荐此设计。原因是FTD数据平面问题可能会中断FTD和FMC之间的通信。
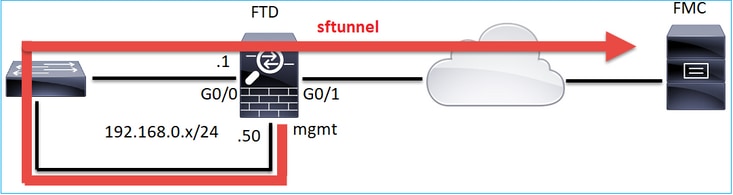
通过sftunnel交换什么信息?
此列表包含通过sftunnel传输的大多数信息:
- 设备心跳(keepalive)
- 时间同步(NTP)
- 事件(连接、入侵/IPS、文件、SSL等)
- 恶意软件查找
- 运行状况事件/警报
- 用户和组信息(用于身份策略)
- FTD HA状态信息
- FTD集群状态信息
- 安全智能(SI)信息/事件
- 威胁情报导向器(TID)信息/事件
- 捕获的文件
- 网络发现事件
- 策略捆绑包(策略部署)
- 软件升级捆绑包
- 软件补丁捆绑包
- VDB
- SRUs
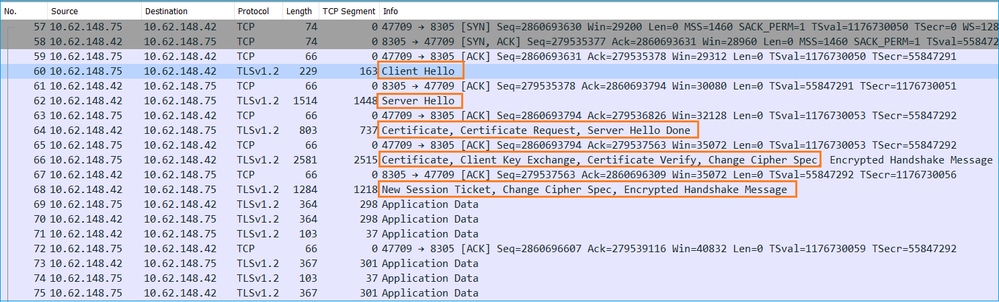
sftunnel使用什么协议/端口?
sftunnel使用TCP端口8305。在后端,它是一条TLS隧道:
如何更改FTD上的Sftunnel TCP端口?
> configure network management-port 8306 Management port changed to 8306.
注意:在这种情况下,还必须更改FMC上的端口(Configuration > Management Interfaces > Shared Settings)。这会影响已注册到同一FMC的所有其他设备。思科强烈建议您保持远程管理端口的默认设置,但如果管理端口与网络上的其他通信冲突,您可以选择其他端口。如果更改管理端口,则必须为部署中需要相互通信的所有设备更改管理端口。
sftunnel建立了多少个连接?
Sftunnel建立2个连接(通道):
- 控制信道
- 事件通道
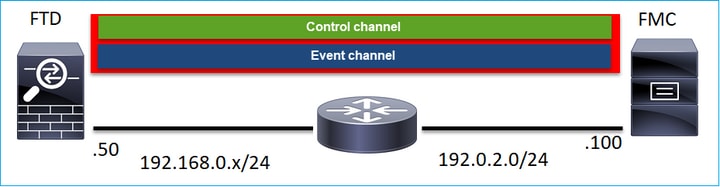
哪个设备启动每个信道?
这要看情况。检查本文档其余部分中介绍的方案。
配置
注册基础知识
FTD CLI
在FTD上,设备注册的基本语法为:
> configure manager add <FMC Host> <Registration Key> <NAT ID>
| 价值 | 描述 |
| FMC主机 | 这可以是:
|
| 注册密钥 | 这是用于设备注册的共享密钥字母数字字符串(2到36个字符)。仅允许使用字母数字、连字符(-)、下划线(_)和句点(.)。 |
| NAT ID | 当一端未指定IP地址时,在FMC和设备之间的注册过程中使用的字母数字字符串。在FMC上指定相同的NAT ID。 |
有关其他详细信息,请查看思科Firepower威胁防御命令参考
FMC用户界面
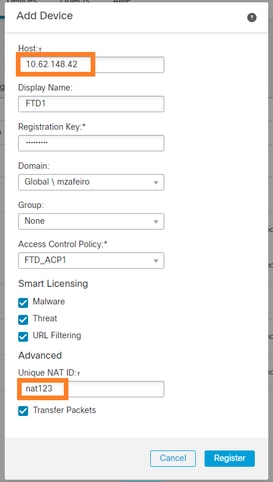
在FMC上,导航到设备>设备管理。选择Add > Device
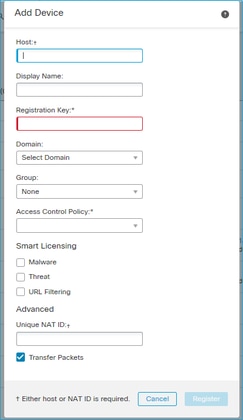
- 在Host中指定FTD IP地址。
- 在Display Name(显示名称)中,指定您想要的任何内容。
- 注册密钥必须与FTD CLI中指定的密钥匹配。
- 如果使用多个域,请指定要在其中添加FTD的域。
- 在Group中,指定要在其下添加FTD的设备组。
- 在“访问控制策略”(Access Control Policy)中,指定要在FTD上部署的安全策略。
- 智能许可:指定已配置功能所需的许可证。
- NAT ID:在本文档后面介绍的特定场景中需要。
有关其他详细信息,请查看《Firepower管理中心配置指南》,向Firepower管理中心添加设备
场景 1.FMC和FTD静态IP地址
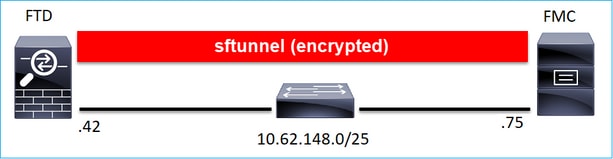
FTD CLI
> configure manager add <FMC Static IP> <Registration Key>
例如:
> configure manager add 10.62.148.75 Cisco-123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
背景信息
输入FTD命令后,FTD会每20秒尝试连接到FMC,但由于尚未配置FMC,因此它会以TCP RST回复:
> capture-traffic Please choose domain to capture traffic from: 0 - eth0 1 - Global Selection? 0 Please specify tcpdump options desired. (or enter '?' for a list of supported options) Options: -n host 10.62.148.75 HS_PACKET_BUFFER_SIZE is set to 4. tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 18:53:33.365513 IP 10.62.148.42.46946 > 10.62.148.75.8305: Flags [S], seq 2274592861, win 29200, options [mss 1460,sackOK,TS val 55808298 ecr 0,nop,wscale 7], length 0 18:53:33.365698 IP 10.62.148.75.8305 > 10.62.148.42.46946: Flags [R.], seq 0, ack 2274592862, win 0, length 0 18:53:53.365973 IP 10.62.148.42.57607 > 10.62.148.75.8305: Flags [S], seq 1267517632, win 29200, options [mss 1460,sackOK,TS val 55810298 ecr 0,nop,wscale 7], length 0 18:53:53.366193 IP 10.62.148.75.8305 > 10.62.148.42.57607: Flags [R.], seq 0, ack 1267517633, win 0, length 0 18:54:13.366383 IP 10.62.148.42.55484 > 10.62.148.75.8305: Flags [S], seq 4285875151, win 29200, options [mss 1460,sackOK,TS val 55812298 ecr 0,nop,wscale 7], length 0 18:54:13.368805 IP 10.62.148.75.8305 > 10.62.148.42.55484: Flags [R.], seq 0, ack 4285875152, win 0, length 0
设备注册状态:
> show managers Host : 10.62.148.75 Registration Key : **** Registration : pending RPC Status : Type : Manager Host : 10.62.148.75 Registration : Pending
FTD在端口TCP 8305上侦听:
admin@vFTD66:~$ netstat -na | grep 8305 tcp 0 0 10.62.148.42:8305 0.0.0.0:* LISTEN
FMC用户界面
在这种情况下,请指定:
- 主机(FTD的IP地址)
- 显示名称
- 注册密钥(必须与在FTD上配置的密钥匹配)
- 访问控制策略
- 域
- 智能许可信息
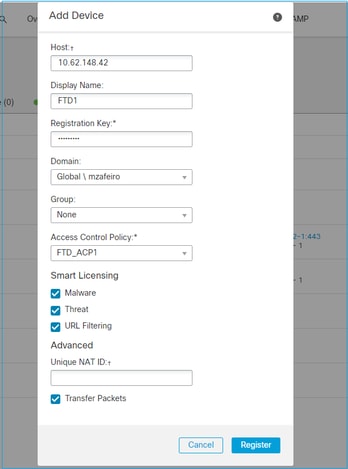
选择注册
注册过程开始:
FMC开始侦听端口TCP 8305:
admin@FMC2000-2:~$ netstat -na | grep 8305 tcp 0 0 10.62.148.75:8305 0.0.0.0:* LISTEN
FMC在后台启动TCP连接:
20:15:55.437434 IP 10.62.148.42.49396 > 10.62.148.75.8305: Flags [S], seq 655146775, win 29200, options [mss 1460,sackOK,TS val 56302505 ecr 0,nop,wscale 7], length 0 20:15:55.437685 IP 10.62.148.75.8305 > 10.62.148.42.49396: Flags [R.], seq 0, ack 655146776, win 0, length 0 20:16:00.463637 ARP, Request who-has 10.62.148.42 tell 10.62.148.75, length 46 20:16:00.463655 ARP, Reply 10.62.148.42 is-at 00:50:56:85:7b:1f, length 28 20:16:08.342057 IP 10.62.148.75.50693 > 10.62.148.42.8305: Flags [S], seq 2704366385, win 29200, options [mss 1460,sackOK,TS val 1181294721 ecr 0,nop,wscale 7], length 0 20:16:08.342144 IP 10.62.148.42.8305 > 10.62.148.75.50693: Flags [S.], seq 1829769842, ack 2704366386, win 28960, options [mss 1460,sackOK,TS val 56303795 ecr 1181294721,nop,wscale 7], length 0 20:16:08.342322 IP 10.62.148.75.50693 > 10.62.148.42.8305: Flags [.], ack 1, win 229, options [nop,nop,TS val 1181294722 ecr 56303795], length 0 20:16:08.342919 IP 10.62.148.75.50693 > 10.62.148.42.8305: Flags [P.], seq 1:164, ack 1, win 229, options [nop,nop,TS val 1181294722 ecr 56303795], length 163 20:16:08.342953 IP 10.62.148.42.8305 > 10.62.148.75.50693: Flags [.], ack 164, win 235, options [nop,nop,TS val 56303795 ecr 1181294722], length 0
已建立sftunnel控制信道:
admin@FMC2000-2:~$ netstat -na | grep 8305 tcp 0 0 10.62.148.75:8305 0.0.0.0:* LISTEN tcp 0 0 10.62.148.75:50693 10.62.148.42:8305 ESTABLISHED
> sftunnel-status
SFTUNNEL Start Time: Sat Apr 18 20:14:20 2020
Both IPv4 and IPv6 connectivity is supported
Broadcast count = 4
Reserved SSL connections: 0
Management Interfaces: 1
eth0 (control events) 10.62.148.42,
***********************
**RUN STATUS****ksec-fs2k-2-mgmt.cisco.com*************
Cipher used = AES256-GCM-SHA384 (strength:256 bits)
ChannelA Connected: Yes, Interface eth0
ChannelB Connected: No
Registration: Completed.
IPv4 Connection to peer '10.62.148.75' Start Time: Sat Apr 18 20:16:08 2020
PEER INFO:
sw_version 6.6.0
sw_build 90
Management Interfaces: 1
eth0 (control events) 10.62.148.75,
Peer channel Channel-A is valid type (CONTROL), using 'eth0', connected to '10.62.148.75' via '10.62.148.42'
Peer channel Channel-B is not valid
几分钟后,事件通道建立。Event channel的发起者可以是任一端。在本示例中,它是FMC:
20:21:15.347587 IP 10.62.148.75.43957 > 10.62.148.42.8305: Flags [S], seq 3414498581, win 29200, options [mss 1460,sackOK,TS val 1181601702 ecr 0,nop,wscale 7], length 0 20:21:15.347660 IP 10.62.148.42.8305 > 10.62.148.75.43957: Flags [S.], seq 2735864611, ack 3414498582, win 28960, options [mss 1460,sackOK,TS val 56334496 ecr 1181601702,nop,wscale 7], length 0 20:21:15.347825 IP 10.62.148.75.43957 > 10.62.148.42.8305: Flags [.], ack 1, win 229, options [nop,nop,TS val 1181601703 ecr 56334496], length 0 20:21:15.348415 IP 10.62.148.75.43957 > 10.62.148.42.8305: Flags [P.], seq 1:164, ack 1, win 229, options [nop,nop,TS val 1181601703 ecr 56334496], length 163
随机源端口表示连接发起方:
admin@FMC2000-2:~$ netstat -na | grep 10.62.148.42 tcp 0 0 10.62.148.75:50693 10.62.148.42:8305 ESTABLISHED tcp 0 0 10.62.148.75:43957 10.62.148.42:8305 ESTABLISHED
如果Event channel由FTD启动,则输出为:
admin@FMC2000-2:~$ netstat -na | grep 10.62.148.42 tcp 0 0 10.62.148.75:58409 10.62.148.42:8305 ESTABLISHED tcp 0 0 10.62.148.75:8305 10.62.148.42:46167 ESTABLISHED
从FTD端:
> sftunnel-status
SFTUNNEL Start Time: Sat Apr 18 20:14:20 2020
Both IPv4 and IPv6 connectivity is supported
Broadcast count = 6
Reserved SSL connections: 0
Management Interfaces: 1
eth0 (control events) 10.62.148.42,
***********************
**RUN STATUS****ksec-fs2k-2-mgmt.cisco.com*************
Cipher used = AES256-GCM-SHA384 (strength:256 bits)
ChannelA Connected: Yes, Interface eth0
Cipher used = AES256-GCM-SHA384 (strength:256 bits)
ChannelB Connected: Yes, Interface eth0
Registration: Completed.
IPv4 Connection to peer '10.62.148.75' Start Time: Sat Apr 18 20:16:08 2020
PEER INFO:
sw_version 6.6.0
sw_build 90
Management Interfaces: 1
eth0 (control events) 10.62.148.75,
Peer channel Channel-A is valid type (CONTROL), using 'eth0', connected to '10.62.148.75' via '10.62.148.42'
Peer channel Channel-B is valid type (EVENT), using 'eth0', connected to '10.62.148.75' via '10.62.148.42'
> show managers Type : Manager Host : 10.62.148.75 Registration : Completed >
场景 2:FTD DHCP IP地址- FMC静态IP地址
在此场景中,FTD管理接口从DHCP服务器获取其IP地址:
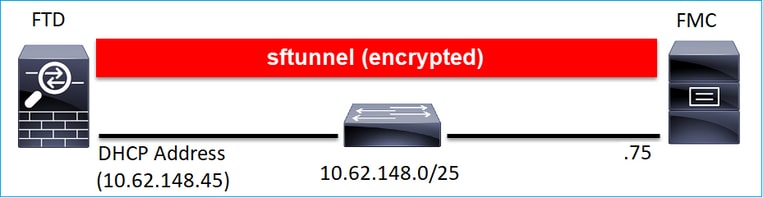
FTD CLI
必须指定NAT ID:
> configure manager add <FMC Static IP> <Registration Key> <NAT ID>
例如:
> configure manager add 10.62.148.75 Cisco-123 nat123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC. >
FTD注册状态:
> show managers Host : 10.62.148.75 Registration Key : **** Registration : pending RPC Status : Type : Manager Host : 10.62.148.75 Registration : Pending
FMC用户界面
在这种情况下,请指定:
- 显示名称
- 注册密钥(必须与在FTD上配置的密钥匹配)
- 访问控制策略
- 域
- 智能许可信息
- NAT ID(如果未指定主机,则需要此ID。它必须与在FTD上配置的相匹配)
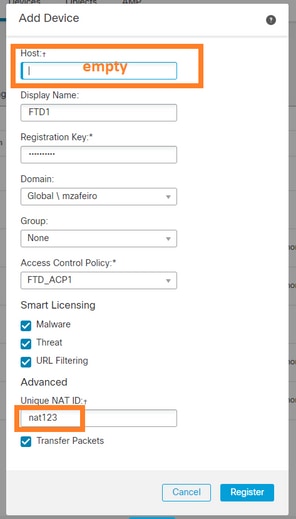
在这种情况下,由谁启动sftunnel?
FTD启动两个信道连接:
ftd1:/home/admin# netstat -an | grep 148.75 tcp 0 0 10.62.148.45:40273 10.62.148.75:8305 ESTABLISHED tcp 0 0 10.62.148.45:39673 10.62.148.75:8305 ESTABLISHED
场景 3:FTD静态IP地址- FMC DHCP IP地址
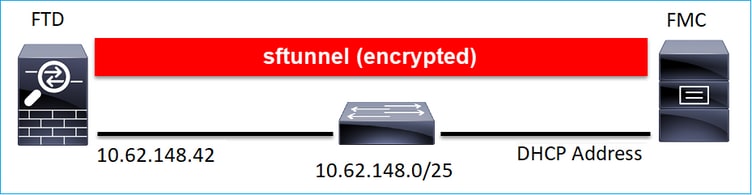
> configure manager add DONTRESOLVE Cisco-123 nat123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC. >
注意:使用DONTRESOLVE时需要NAT ID。
FMC用户界面
在这种情况下,请指定:
- FTD IP地址
- 显示名称
- 注册密钥(必须与在FTD上配置的密钥匹配)
- 访问控制策略
- 域
- 智能许可信息
- NAT ID(必须与FTD上配置的NAT ID匹配)
完成注册后的FTD:
> show managers Type : Manager Host : 5a8454ea-8273-11ea-a7d3-d07d71db8f19DONTRESOLVE Registration : Completed
在这种情况下,由谁启动sftunnel?
- FMC启动控制信道。
- 事件信道可以由任一端发起。
root@FMC2000-2:/Volume/home/admin# netstat -an | grep 148.42 tcp 0 0 10.62.148.75:50465 10.62.148.42:8305 ESTABLISHED tcp 0 0 10.62.148.75:48445 10.62.148.42:8305 ESTABLISHED
场景 4.FTD注册到FMC HA
在FTD上,仅配置活动FMC:
> configure manager add 10.62.184.22 cisco123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
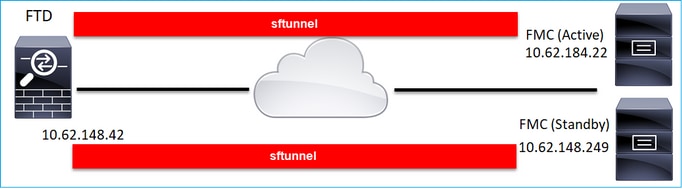
注意:确保TCP端口8305流量可以从FTD发送到两个FMC。
首先,建立指向活动FMC的sftunnel:
> show managers Type : Manager Host : 10.62.184.22 Registration : Completed
几分钟后,FTD开始注册到备用FMC:
> show managers Type : Manager Host : 10.62.184.22 Registration : Completed Type : Manager Host : 10.62.148.249 Registration : Completed
在FTD后端中,建立了2个控制信道(每个FMC一个)和2个事件信道(每个FMC一个):
ftd1:/home/admin# netstat -an | grep 8305 tcp 0 0 10.62.148.42:8305 10.62.184.22:36975 ESTABLISHED tcp 0 0 10.62.148.42:42197 10.62.184.22:8305 ESTABLISHED tcp 0 0 10.62.148.42:8305 10.62.148.249:45373 ESTABLISHED tcp 0 0 10.62.148.42:8305 10.62.148.249:51893 ESTABLISHED
方案 5.FTD HA
在FTD HA的情况下,每台设备都具有通往FMC的单独隧道:
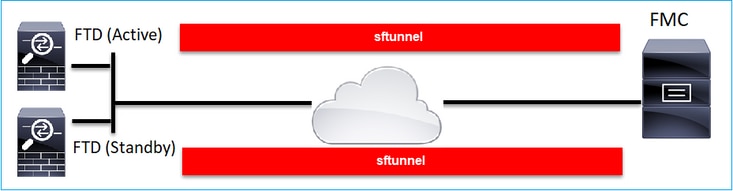
您独立注册两个FTD,然后从FMC形成FTD HA。有关详细信息,请查看:
方案 6.FTD集群
对于FTD集群,每台设备都有一个通往FMC的单独隧道。从6.3 FMC版本开始,您只需将FTD控制单元注册到FMC。然后,FMC处理其余的单元,并自动发现+注册它们。
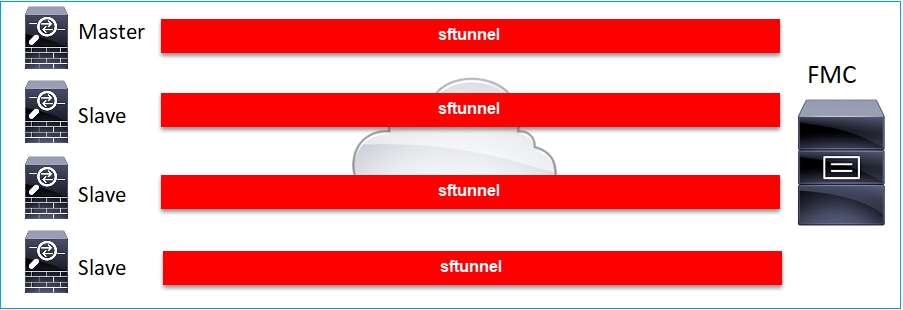
注意:我们建议添加控制单元以实现最佳性能,但您可以添加集群的任何单元。有关其他详细信息,请检查:创建Firepower威胁防御集群
排除常见问题
1. FTD CLI上的语法无效
如果FTD上的语法无效,并且注册尝试失败,则FMC UI会显示一条相当普通的错误消息:
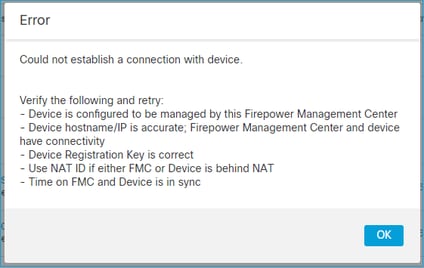
在此命令中,关键字key是注册密钥,而cisco123是NAT ID。在技术上不存在关键字时,添加关键字密钥的情况相当常见:
> configure manager add 10.62.148.75 key cisco123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
建议操作
使用正确的语法,不要使用不存在的关键字。
> configure manager add 10.62.148.75 cisco123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
2. FTD - FMC之间的注册密钥不匹配
FMC UI显示:
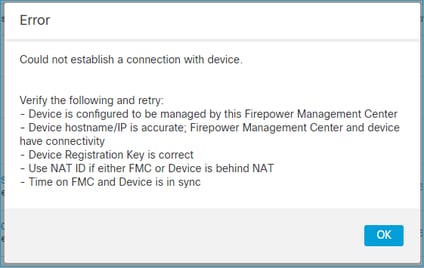
建议操作
在FTD上,检查/ngfw/var/log/messages文件以了解身份验证问题。
方法1 -检查过去的日志
> system support view-files Type a sub-dir name to list its contents: s Type the name of the file to view ([b] to go back, [Ctrl+C] to exit) > messages Apr 19 04:02:05 vFTD66 syslog-ng[1440]: Configuration reload request received, reloading configuration; Apr 19 04:02:07 vFTD66 SF-IMS[3116]: [3116] pm:control [INFO] ControlHandler auditing message->type 0x9017, from '', cmd '/ngf w/usr/bin/perl /ngfw/usr/local/sf/bin/run_hm.pl --persistent', pid 19455 (uid 0, gid 0) /authenticate Apr 19 20:17:14 vFTD66 SF-IMS[18974]: [19131] sftunneld:sf_ssl [WARN] Accept: Failed to authenticate peer '10.62.148.75' <- The problem
方法2 -检查实时日志
> expert ftd1:~$ sudo su Password: ftd1::/home/admin# tail -f /ngfw/var/log/messages
在FTD上,检查/etc/sf/sftunnel.conf文件的内容,以确保注册密钥正确:
ftd1:~$ cat /etc/sf/sftunnel.conf | grep reg_key
reg_key cisco-123;
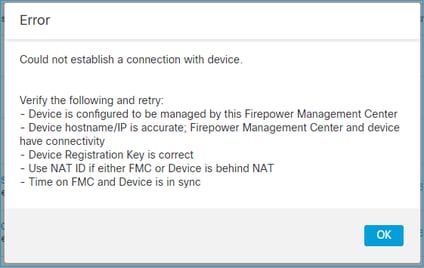
3. FTD - FMC之间的连接问题
FMC UI显示:
推荐的操作
- 确保路径中没有阻止流量的设备(例如防火墙)(TCP 8305)。对于FMC HA,请确保允许到TCP端口8305的流量流向两个FMC。
- 执行捕获以验证双向通信。在FTD上,使用capture-traffic 命令。确保存在TCP三次握手,并且没有TCP FIN或RST数据包。
> capture-traffic Please choose domain to capture traffic from: 0 - eth0 1 - Global Selection? 0 Please specify tcpdump options desired. (or enter '?' for a list of supported options) Options: -n host 10.62.148.75 HS_PACKET_BUFFER_SIZE is set to 4. tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 20:56:09.393655 IP 10.62.148.42.53198 > 10.62.148.75.8305: Flags [S], seq 3349394953, win 29200, options [mss 1460,sackOK,TS val 1033596 ecr 0,nop,wscale 7], length 0 20:56:09.393877 IP 10.62.148.75.8305 > 10.62.148.42.53198: Flags [R.], seq 0, ack 3349394954, win 0, length 0 20:56:14.397412 ARP, Request who-has 10.62.148.75 tell 10.62.148.42, length 28 20:56:14.397602 ARP, Reply 10.62.148.75 is-at a4:6c:2a:9e:ea:10, length 46
同样,在FMC上进行捕获以确保双向通信:
root@FMC2000-2:/var/common# tcpdump -i eth0 host 10.62.148.42 -n -w sftunnel.pcap
还建议以pcap格式导出捕获并检查数据包内容:
ftd1:/home/admin# tcpdump -i eth0 host 10.62.148.75 -n -w tunnel.pcap HS_PACKET_BUFFER_SIZE is set to 4. tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
可能的原因:
- FMC未添加FTD设备。
- 路径中的设备(例如,防火墙)阻止或修改流量。
- 路径中的数据包路由不正确。
- FTD或FMC上的sftunnel进程已关闭(检查场景6)
- 路径中存在MTU问题(检查场景)。
对于捕获分析,请检查以下文档:
4. FTD - FMC之间的软件不兼容
FMC UI显示:
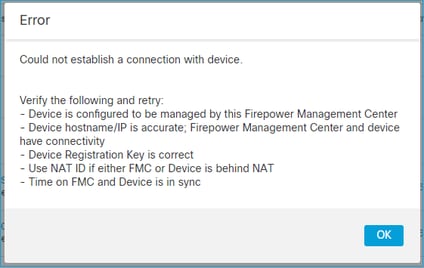
建议操作
检查FTD /ngfw/var/log/messages文件:
Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_connections [INFO] Need to send SW version and Published Services to 10.62.148.247 Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_channel [INFO] >> ChannelState do_dataio_for_heartbeat peer 10.62.148.247 / channelA / CONTROL [ msgSock & ssl_context ] << Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_heartbeat [INFO] Saved SW VERSION from peer 10.62.148.247 (10.10.0.4) Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:ssl_mac [WARN] FMC(manager) 10.62.148.247 send unsupported version 10.10.0.4 Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_connections [INFO] <<<<<<<<<<<<<<<<<<<<<< ShutDownPeer 10.62.148.247 >>>>>>>>>>>>>>>>>>>>>>>> Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:stream_file [INFO] Stream CTX destroyed for 10.62.148.247 Apr 19 22:08:09 mzafeiro_vFTD66 SF-IMS[12730]: [12830] sftunneld:sf_channel [INFO] >> ChannelState ShutDownPeer peer 10.62.148.247 / channelA / CONTROL [ msgSock & ssl_context ] <<
检查Firepower兼容性列表:
5. FTD和FMC之间的时间差
FTD-FMC通信对两台设备之间的时间差非常敏感。要求同一NTP服务器同步FTD和FMC。
具体来说,当FTD安装在类似41xx或93xx的平台上时,其时间设置从父机箱(FXOS)进行。
建议操作
确保机箱管理器(FCM)和FMC使用同一时间源(NTP服务器)
6. sftunnel进程关闭或禁用
在FTD上,sftunnel进程处理注册进程。下面是管理器配置前的进程状态:
> pmtool status … sftunnel (system) - Waiting Command: /ngfw/usr/local/sf/bin/sftunnel -d -f /etc/sf/sftunnel.conf PID File: /ngfw/var/sf/run/sftunnel.pid Enable File: /ngfw/etc/sf/sftunnel.conf CPU Affinity: Priority: 0 Next start: Mon Apr 20 06:12:06 2020 Required by: sfmgr,sfmbservice,sfipproxy CGroups: memory=System/ProcessHigh
注册状态:
> show managers No managers configured.
配置管理器:
> configure manager add 10.62.148.75 cisco123 Manager successfully configured. Please make note of reg_key as this will be required while adding Device in FMC.
现在该过程已启动:
> pmtool status … sftunnel (system) - Running 24386 Command: /ngfw/usr/local/sf/bin/sftunnel -d -f /etc/sf/sftunnel.conf PID File: /ngfw/var/sf/run/sftunnel.pid Enable File: /ngfw/etc/sf/sftunnel.conf CPU Affinity: Priority: 0 Next start: Mon Apr 20 07:12:35 2020 Required by: sfmgr,sfmbservice,sfipproxy CGroups: memory=System/ProcessHigh(enrolled)
在极少数情况下,进程可以关闭或禁用:
> pmtool status … sftunnel (system) - User Disabled Command: /ngfw/usr/local/sf/bin/sftunnel -d -f /etc/sf/sftunnel.conf PID File: /ngfw/var/sf/run/sftunnel.pid Enable File: /ngfw/etc/sf/sftunnel.conf CPU Affinity: Priority: 0 Next start: Mon Apr 20 07:09:46 2020 Required by: sfmgr,sfmbservice,sfipproxy CGroups: memory=System/ProcessHigh
管理器状态看起来正常:
> show managers Host : 10.62.148.75 Registration Key : **** Registration : pending RPC Status :
另一方面,设备注册失败:
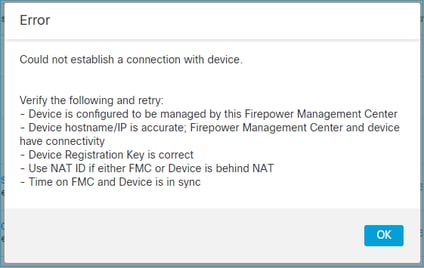
在FTD上,/ngfw/var/log/messages中看不到相关消息
建议操作
收集FTD故障排除文件并联系思科TAC
7. 辅助FMC上的FTD等待注册
在某些情况下,初始FTD注册到FMC HA设置后,FTD设备不会添加到辅助FMC。
建议操作
使用本文档中介绍的步骤:
使用CLI解决Firepower管理中心高可用性中的设备注册问题
警告:此过程是强制性的,因为它包含取消注册设备。这会影响FTD设备配置(已删除)。建议仅在初始FTD注册和设置期间使用此程序。在不同情况下,收集FTD和FMC故障排除文件并联系思科TAC。
8. 由于路径MTU,注册失败
在Cisco TAC中可以看到,sftunnel流量必须通过具有小MTU的链路传输。sftunnel数据包具有不分段位设置,因此不允许分段:
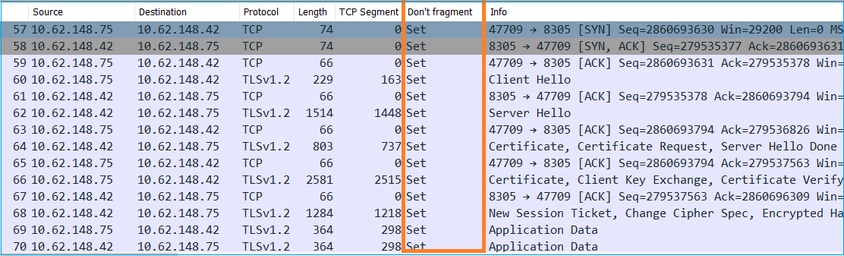
此外,在/ngfw/var/log/messages文件中,您可以看到如下消息:
消息:10-09 14:41:11 ftd1 SF-IMS[7428]: [6612] sftunneld:sf_ssl [ERROR] 连接:SSL握手失败
建议操作
要验证是否存在由于分段导致的数据包丢失,请捕获FTD、FMC上的数据包,最好捕获路径中的设备。检查两端是否都收到数据包。
在FTD上,降低FTD管理接口上的MTU。默认值为 1500 字节。管理接口的最大值为1500,事件接口的最大值为9000。FTD 6.6版本中已添加该命令。
示例
> configure network mtu 1300 MTU set successfully to 1300 from 1500 for eth0 Refreshing Network Config... Interface eth0 speed is set to '10000baseT/Full'
确认
> show network ===============[ System Information ]=============== Hostname : ksec-sfvm-kali-3.cisco.com DNS Servers : 192.168.200.100 Management port : 8305 IPv4 Default route Gateway : 10.62.148.1 Netmask : 0.0.0.0 ======================[ eth0 ]====================== State : Enabled Link : Up Channels : Management & Events Mode : Non-Autonegotiation MDI/MDIX : Auto/MDIX MTU : 1300 MAC Address : 00:50:56:85:7B:1F ----------------------[ IPv4 ]---------------------- Configuration : Manual Address : 10.62.148.42 Netmask : 255.255.255.128 Gateway : 10.62.148.1 ----------------------[ IPv6 ]----------------------
要从FTD验证路径MTU,您可以使用以下命令:
root@firepower:/home/admin# ping -M do -s 1472 10.62.148.75
do 选项设置ICMP数据包中的不分段位。此外,如果指定1472,设备将发送1500字节:(IP报头= 20字节)+(ICMP报头= 8字节)+(1472字节ICMP数据)
在FMC上,按照本文档中的说明降低FMC管理接口上的MTU值:
9. 从机箱管理器UI进行引导程序更改后,FTD将取消注册
这适用于FP41xx和FP93xx平台,记录在Cisco Bug ID CSCvn45138中 。
。
一般来说,除非执行灾难恢复,否则不能从机箱管理器(FCM)执行引导程序更改。
建议操作
如果您执行了引导程序更改并且匹配了条件(FTD-FMC通信中断,而FTD在引导程序更改后启动),则必须删除并再次将FTD注册到FMC。
10. 由于ICMP重定向消息,FTD失去对FMC的访问
此问题可能会影响注册过程或在注册后中断FTD-FMC通信。
在这种情况下,问题是将ICMP重定向消息发送到FTD管理接口以及黑洞FTD-FMC通信的网络设备。
如何识别此问题
在本例中,10.100.1.1是FMC IP地址。在FTD上,由于FTD在管理接口上收到的ICMP重定向消息,存在缓存路由:
ftd1:/ngfw/var/common# ip route get 10.100.1.1
10.100.1.1 via 10.10.1.1 dev br1 src 10.10.1.23
cache <redirected>
建议操作
第 1 步
在发送重定向消息的设备(例如,上游L3交换机、路由器等)上禁用ICMP重定向。
步骤 2
从FTD CLI清除FTD路由缓存:
ftd1:/ngfw/var/common# ip route flush 10.100.1.1
如果未重定向,则如下所示:
ftd1:/ngfw/var/common# ip route get 10.100.1.1
10.100.1.1 via 10.62.148.1 dev eth0 src 10.10.1.23
cache mtu 1500 advmss 1460 hoplimit 64
参考
- 了解ICMP重定向消息
- 思科漏洞ID CSCvm53282 FTD:由ICMP重定向添加的路由表将永久停滞在路由表缓存中
相关信息
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
3.0 |
14-Aug-2023 |
已更新参与者列表。 |
2.0 |
19-Jul-2022 |
文章针对格式、机器翻译、术语、SEO、风格要求等进行了更新,以满足当前的思科指南。 |
1.0 |
20-May-2020 |
初始版本 |
由思科工程师提供
- 米基斯·扎菲鲁迪斯思科TAC工程师
- 伊尔金·卡西莫夫思科TAC工程师
 反馈
反馈