简介
本文档介绍如何使用REST API在Firepower设备管理版本6.7上启用简单网络管理协议(SNMP)。
先决条件
要求
Cisco 建议您了解以下主题:
- 由Firepower设备管理(FDM) 6.7版管理的Firepower威胁防御(FTD)
- REST API知识
- SNMP知识
使用的组件
由Firepower设备管理版本6.7管理的Firepower威胁防御。
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
背景信息
6.7中的新功能
FTD设备REST API支持配置和管理SNMP服务器、用户、主机和主机组。借助FP 6.7中的SNMP FTD设备REST API支持:
- 用户可以通过FTD设备REST API配置SNMP来管理网络。
- 可以添加/更新或通过FTD设备REST API管理SNMP服务器、用户和主机/主机组。
本文档中包含的示例描述了FDM API Explorer采取的配置步骤。
注:当FTD运行版本6.7并由FDM管理时,只能通过REST API配置SNMP。
功能概述- SNMP FTD设备REST API支持
- 此功能将添加特定于SNMP的新FDM URL终端。
- 这些新的API可用于配置SNMP轮询和陷阱来监控系统。
- 通过API(Firepower设备上的管理信息库[MIB])进行SNMP配置后,可进行NMS/SNMP客户端上的轮询或陷阱通知。
SNMP API/URL终端
| URL |
方法 |
型号 |
| /devicesettings/default/snmpservers |
GET |
SNMP服务器 |
| /devicesettings/default/snmpservers/{objId} |
PUT、GET |
SNMP服务器 |
| /object/snmphosts |
POST、GET |
SNMPHost |
| /object/snmphosts/{objId} |
PUT、DELETE、GET |
SNMPHost |
| /object/snmpusergroups |
POST、GET |
SNMPUserGroup |
| /object/snmpusergroups/{objId} |
PUT、DELETE、GET |
SNMPUserGroup |
| /object/snmpusers |
POST、GET |
SNMPUser |
| /object/snmpusers/{objId} |
PUT、DELETE、GET |
SNMPUser |
配置
SNMP主机有3个主要版本:
- SNMP V1
- SNMP V2C
- SNMP V3
每种协议都有特定的securityConfiguration格式。 对于V1和V2C:它包含社区字符串和用于将配置标识为V1或V2C的类型字段。
对于SNMP V3:它包含一个有效的SNMP V3用户和用于将配置标识为V3的类型字段。
SNMP v3
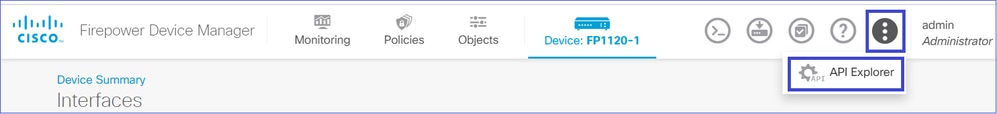
1. 访问FDM API资源管理器。
要从FDM GUI访问FDM REST API资源管理器,请选择3点,然后选择API资源管理器。或者,导航至URL API Explorer。
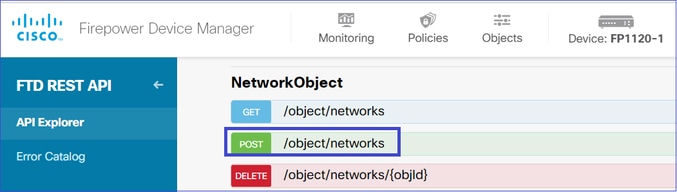
2. 网络对象配置
为SNMP主机创建新的网络对象。在FDM API资源管理器上,选择NetworkObject,然后选择POST /object/networks:
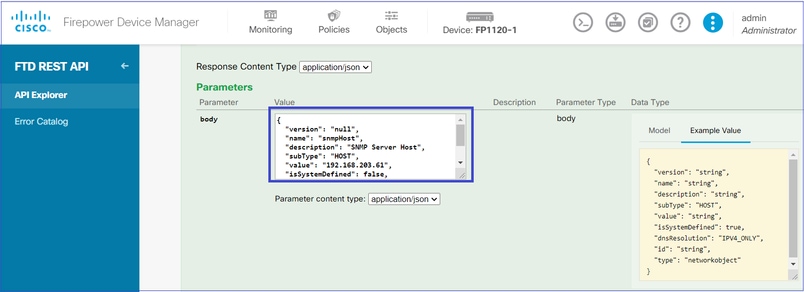
SNMP主机JSON格式如下。将此JSON粘贴到body部分并更改IP address on值,以匹配SNMP主机IP地址:
{
"version": "null",
"name": "snmpHost",
"description": "SNMP Server Host",
"subType": "HOST",
"value": "192.168.203.61",
"isSystemDefined": false,
"dnsResolution": "IPV4_ONLY",
"type": "networkobject"
}
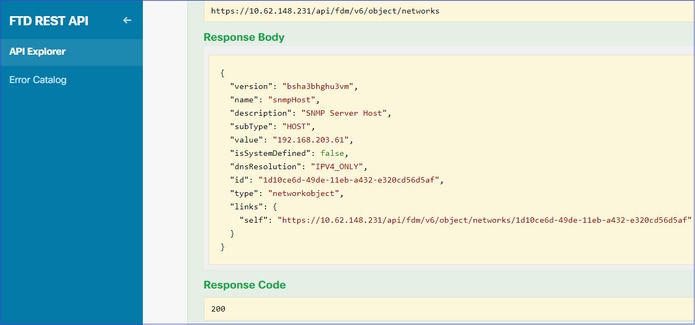
向下滚动并选择TRY IT OUT!按钮以执行API调用。成功的调用返回响应代码200。
将JSON数据从响应正文复制到记事本。稍后,您需要填写有关SNMP主机的信息。
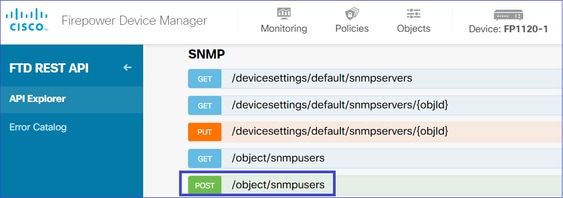
3. 创建新的SNMPv3用户。
在FDM API Explorer上,选择SNMP,然后选择POST /object/snmpusers。
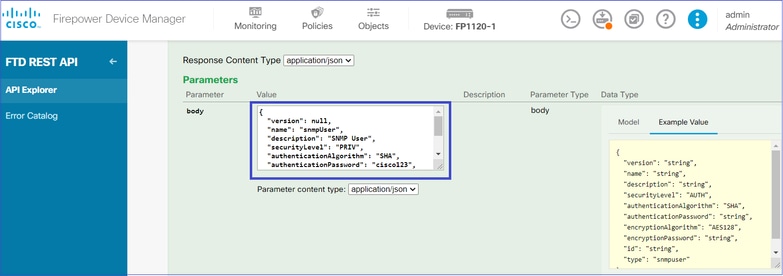
将此JSON数据复制到记事本并修改您感兴趣的部分(例如,authenticationPassword、encryptionPassword或算法):
{
"version": null,
"name": "snmpUser",
"description": "SNMP User",
"securityLevel": "PRIV",
"authenticationAlgorithm": "SHA",
"authenticationPassword": "cisco123",
"encryptionAlgorithm": "AES128",
"encryptionPassword": "cisco123",
"id": null,
"type": "snmpuser"
}
注意:示例中使用的密码仅用于演示目的。在生产环境中,请确保使用强密码
将修改后的JSON数据复制到正文部分:
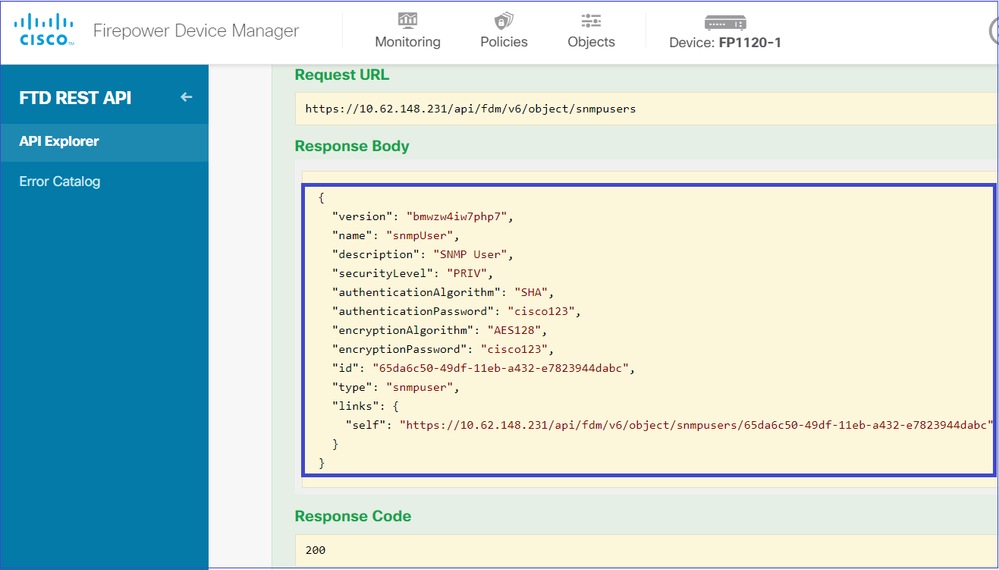
向下滚动并选择TRY IT OUT!按钮以执行API调用。成功的调用返回响应代码200。将JSON数据从响应正文复制到记事本。稍后,您需要填写有关SNMP用户的信息。
4. 获取接口信息。
在FDM API资源管理器上,选择Interface,然后选择GET /devices/default/interfaces。您需要从连接到SNMP服务器的接口收集信息。
向下滚动并选择TRY IT OUT!按钮以执行API调用。成功的调用返回响应代码200。将JSON数据从响应正文复制到记事本。稍后,您需要填写有关接口的信息。
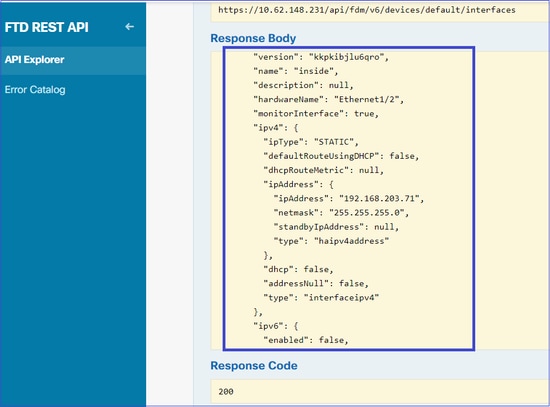
请记住来自JSON数据的接口版本、名称、ID和类型。来自内部接口的JSON数据示例:
{
"version": "kkpkibjlu6qro",
"name": "inside",
"description": null,
"hardwareName": "Ethernet1/2",
"monitorInterface": true,
"ipv4": {
"ipType": "STATIC",
"defaultRouteUsingDHCP": false,
"dhcpRouteMetric": null,
"ipAddress": {
"ipAddress": "192.168.203.71",
"netmask": "255.255.255.0",
"standbyIpAddress": null,
"type": "haipv4address"
},
"dhcp": false,
"addressNull": false,
"type": "interfaceipv4"
},
"ipv6": {
"enabled": false,
"autoConfig": false,
"dhcpForManagedConfig": false,
"dhcpForOtherConfig": false,
"enableRA": false,
"dadAttempts": 1,
"linkLocalAddress": {
"ipAddress": "",
"standbyIpAddress": "",
"type": "haipv6address"
},
"ipAddresses": [
{
"ipAddress": "",
"standbyIpAddress": "",
"type": "haipv6address"
}
],
"prefixes": null,
"type": "interfaceipv6"
},
"managementOnly": false,
"managementInterface": false,
"mode": "ROUTED",
"linkState": "UP",
"mtu": 1500,
"enabled": true,
"macAddress": null,
"standbyMacAddress": null,
"pppoe": null,
"speedType": "AUTO",
"duplexType": "AUTO",
"present": true,
"tenGigabitInterface": false,
"gigabitInterface": false,
"id": "fc3d07d4-49d2-11eb-85a8-65aec636a0fc",
"type": "physicalinterface",
"links": {
"self": "https://10.62.148.231/api/fdm/v6/devices/default/interfaces/fc3d07d4-49d2-11eb-85a8-65aec636a0fc"
}
},
从JSON数据中,您可以看到内部接口有需要与SNMP服务器关联的数据:
- 版本:kkpkibjlu6qro
- 名称:inside,iid:fc3d07d4-49d2-11eb-85a8-65aec636a0fc,
- 类型:physicalinterface、
5. 创建新的SNMPv3主机。
在FDM API Explorer中,选择SNMP,然后在SNMP下选择POST /object/snmphosts/。
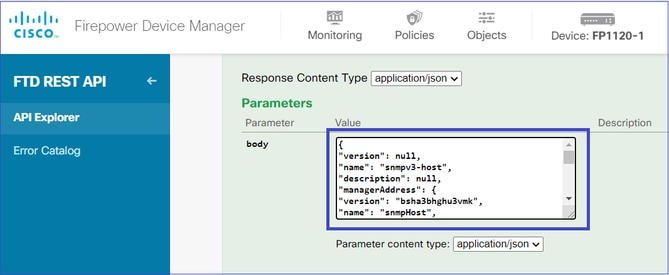
使用此JSON作为模板。将之前步骤中的数据复制并粘贴到模板中:
{
"version": null,
"name": "snmpv3-host",
"description": null,
"managerAddress": {
"version": "bsha3bhghu3vmk",
"name": "snmpHost",
"id": "1d10ce6d-49de-11eb-a432-e320cd56d5af",
"type": "networkobject"
},
"pollEnabled": true,
"trapEnabled": true,
"securityConfiguration": {
"authentication": {
"version": "bmwzw4iw7php7",
"name": "snmpUser",
"id": "65da6c50-49df-11eb-a432-e7823944dabc",
"type": "snmpuser"
},
"type": "snmpv3securityconfiguration"
},
"interface": {
"version": "kkpkibjlu6qro",
"name": "inside",
"id": "fc3d07d4-49d2-11eb-85a8-65aec636a0fc",
"type": "physicalinterface"
},
"id": null,
"type": "snmphost"
}

注意:
- 使用从步骤1接收的信息替换managerAddress id、类型、版本和名称中的值。
- 使用从步骤2接收的信息替换身份验证中的值。
- 使用从步骤3接收的数据替换interface中的值。对于SNMP2,没有身份验证,类型为snmpv2csecurityconfiguration,而不是snmpv3securityconfiguration。
将修改后的JSON数据复制到正文部分。
向下滚动并选择TRY IT OUT!按钮以执行API调用。成功的调用返回响应代码200。
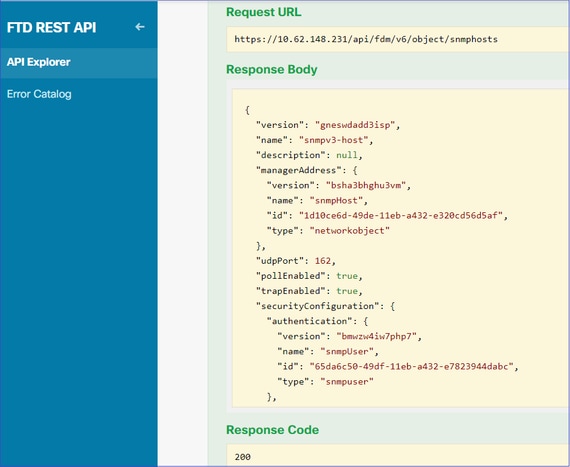
导航到FDM GUI并部署更改。您可以看到大多数SNMP配置:
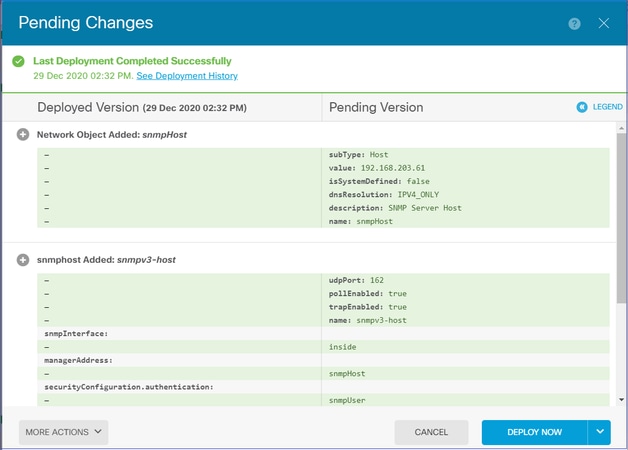
SNMP v2c
对于v2c,您不需要创建用户,但仍需要:
- 创建网络对象配置(与SNMPv3部分中所述相同)
- 获取接口信息(与SNMPv3部分中所述相同)
- 创建新的SNMPv2c主机对象
以下是创建SNMPv2c对象的JSON负载的示例:
{
"version": null,
"name": "snmpv2-Host",
"description": null,
"managerAddress": {
"version": "bsha3bhghu3vmk",
"name": "snmpv4hostgrp",
"id": "1d10ce6d-49de-11eb-a432-e320cd56d5af",
"type": "networkobject"
},
"pollEnabled": true,
"trapEnabled": true,
"securityConfiguration": {
"community": "cisco123",
"type": "snmpv2csecurityconfiguration"
},
"interface": {
"version": "kkpkibjlu6qro",
"name": "inside",
"id": "fc3d07d4-49d2-11eb-85a8-65aec636a0fc",
"type": "physicalinterface"
},
"id": null,
"type": "snmphost"
}
使用POST方法部署JSON负载:
向下滚动并选择TRY IT OUT!按钮以执行API调用。成功的调用返回响应代码200。
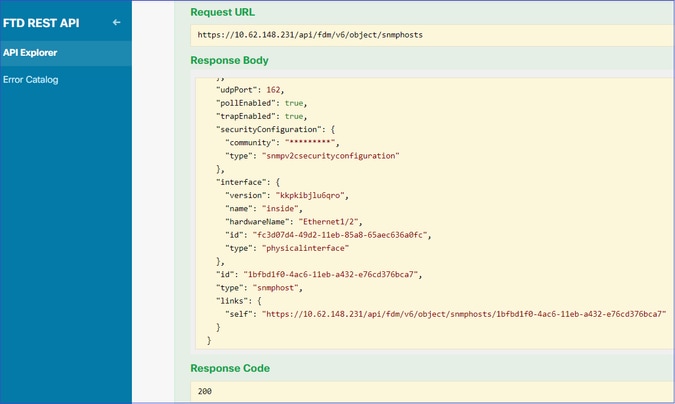
SNMP配置删除
步骤1:
获取SNMP主机信息(SNMP > /object/snmphosts):
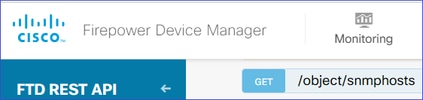
向下滚动并选择TRY IT OUT!按钮以执行API调用。成功的调用返回响应代码200。
您会获得一个对象列表。记下要删除的snmphost对象的id:
{
"items": [
{
"version": "ofaasthu26ulx",
"name": "snmpv2-Host",
"description": null,
"managerAddress": {
"version": "bsha3bhghu3vm",
"name": "snmpHost",
"id": "1d10ce6d-49de-11eb-a432-e320cd56d5af",
"type": "networkobject"
},
"udpPort": 162,
"pollEnabled": true,
"trapEnabled": true,
"securityConfiguration": {
"community": "*********",
"type": "snmpv2csecurityconfiguration"
},
"interface": {
"version": "kkpkibjlu6qro",¬
"name": "inside",
"hardwareName": "Ethernet1/2",
"id": "fc3d07d4-49d2-11eb-85a8-65aec636a0fc",
"type": "physicalinterface"
},
"id": "1bfbd1f0-4ac6-11eb-a432-e76cd376bca7",
"type": "snmphost",
"links": {
"self": "https://10.62.148.231/api/fdm/v6/object/snmphosts/1bfbd1f0-4ac6-11eb-a432-e76cd376bca7"
}
},
第二步:
在SNMP > /object/snmphosts{objId}中选择DELETE选项。粘贴在步骤1中收集的ID:
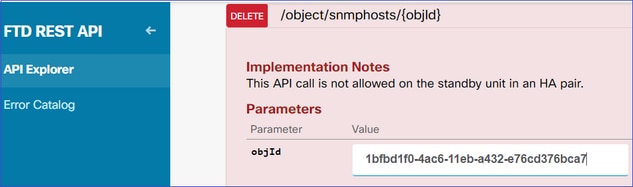
向下滚动并选择TRY IT OUT!按钮以执行API调用。该调用返回响应代码400。
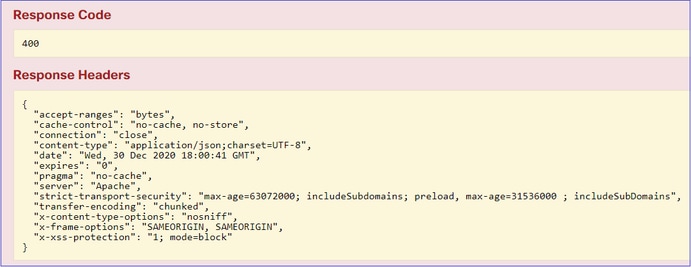
第三步:
部署更改:
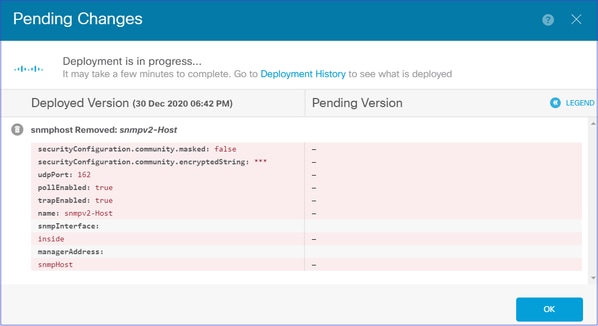
部署将删除主机信息:
FP1120-1# show run snmp-server
snmp-server group AUTH v3 auth
snmp-server group PRIV v3 priv
snmp-server group NOAUTH v3 noauth
snmp-server location null
snmp-server contact null
snmp-server community *****
v2c的snmpwalk失败:
root@kali2:~# snmpwalk -v2c -c cisco123 -OS 192.168.203.71
Timeout: No Response from 192.168.203.71
对于v3,必须按此顺序删除对象。
- SNMP主机(成功的返回代码为204)
- SNMP用户(成功的返回代码为204)
如果尝试以错误的顺序删除对象,则会出现以下错误:
{
"error": {
"severity": "ERROR",
"key": "Validation",
"messages": [
{
"description": "You cannot delete the object because it contains SNMPHost: snmpv3-host2, SNMPHost: snmpv3-host.
You must remove the object from all parts of the configuration before you can delete it.",
"code": "deleteObjWithRel",
"location": ""
}
]
}
}
验证
SNMP v3验证
部署后,导航至FTD CLI以验证SNMP配置。请注意,engineID值是自动生成的。
FP1120-1# connect ftd
> system support diagnostic-cli
Attaching to Diagnostic CLI ... Press 'Ctrl+a then d' to detach.
Type help or '?' for a list of available commands.
FP1120-1> enable
Password:
FP1120-1# show run all snmp-server
snmp-server group AUTH v3 auth
snmp-server group PRIV v3 priv
snmp-server group NOAUTH v3 noauth
snmp-server user snmpUser PRIV v3 engineID 80000009febdf0129a799ef469aba2d5fcf1bfd7e86135a1f8 encrypted auth sha ca:1b:18:f3:62:b1:63:7e:92:34:92:b3:cf:54:86:f9:8e:2a:4c:fd priv aes 128 ca:1b:18:f3:62:b1:63:7e:92:34:92:b3:cf:54:86:f9
snmp-server listen-port 161
snmp-server host inside 192.168.203.61 version 3 snmpUser udp-port 162
snmp-server location null
snmp-server contact null
snmp-server community *****
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
no snmp-server enable traps syslog
no snmp-server enable traps ipsec start stop
no snmp-server enable traps entity config-change fru-insert fru-remove fan-failure power-supply power-supply-presence cpu-temperature chassis-temperature power-supply-temperature chassis-fan-failure accelerator-temperature l1-bypass-status
no snmp-server enable traps memory-threshold
no snmp-server enable traps interface-threshold
no snmp-server enable traps remote-access session-threshold-exceeded
no snmp-server enable traps connection-limit-reached
no snmp-server enable traps cpu threshold rising
no snmp-server enable traps ikev2 start stop
no snmp-server enable traps nat packet-discard
no snmp-server enable traps config
no snmp-server enable traps failover-state
no snmp-server enable traps cluster-state
snmp-server enable oid mempool
snmp-server enable
snmpwalk test
root@kali2:~# snmpwalk -v3 -l authPriv -u snmpUser -a SHA -A cisco123 -x AES -X cisco123 192.168.203.71
iso.3.6.1.2.1.1.1.0 = STRING: "Cisco Firepower Threat Defense, Version 6.7.0 (Build 65), ASA Version 9.15(1)"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.9.1.2663
iso.3.6.1.2.1.1.3.0 = Timeticks: (1616700) 4:29:27.00
iso.3.6.1.2.1.1.4.0 = STRING: "null"
iso.3.6.1.2.1.1.5.0 = STRING: "FP1120-1"
iso.3.6.1.2.1.1.6.0 = STRING: "null"
iso.3.6.1.2.1.1.7.0 = INTEGER: 4
...
SNMP v2c验证
FP1120-1# show run snmp-server
snmp-server host inside 192.168.203.61 community ***** version 2c
snmp-server location null
snmp-server contact null
snmp-server community *****
v2c的snmpwalk:
root@kali2:~# snmpwalk -v2c -c cisco123 -OS 192.168.203.71
iso.3.6.1.2.1.1.1.0 = STRING: "Cisco Firepower Threat Defense, Version 6.7.0 (Build 65), ASA Version 9.15(1)"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.9.1.2663
iso.3.6.1.2.1.1.3.0 = Timeticks: (10482200) 1 day, 5:07:02.00
iso.3.6.1.2.1.1.4.0 = STRING: "null"
iso.3.6.1.2.1.1.5.0 = STRING: "FP1120-1"
iso.3.6.1.2.1.1.6.0 = STRING: "null"
iso.3.6.1.2.1.1.7.0 = INTEGER: 4
故障排除
在防火墙上启用带跟踪的捕获:
FP1120-1# capture CAPI trace interface inside match udp any any eq snmp
使用snmpwalk工具并验证是否可以看到数据包:
FP1120-1# show capture
capture CAPI type raw-data trace interface inside [Capturing - 3137 bytes]
match udp any any eq snmp
捕获内容:
FP1120-1# show capture CAPI
154 packets captured
1: 17:04:16.720131 192.168.203.61.51308 > 192.168.203.71.161: udp 39
2: 17:04:16.722252 192.168.203.71.161 > 192.168.203.61.51308: udp 119
3: 17:04:16.722679 192.168.203.61.51308 > 192.168.203.71.161: udp 42
4: 17:04:16.756400 192.168.203.71.161 > 192.168.203.61.51308: udp 51
5: 17:04:16.756918 192.168.203.61.51308 > 192.168.203.71.161: udp 42
验证SNMP服务器统计信息计数器是否显示SNMP Get或Get-next请求和响应:
FP1120-1# show snmp-server statistics
62 SNMP packets input
0 Bad SNMP version errors
0 Unknown community name
0 Illegal operation for community name supplied
0 Encoding errors
58 Number of requested variables
0 Number of altered variables
0 Get-request PDUs
58 Get-next PDUs
0 Get-bulk PDUs
0 Set-request PDUs (Not supported)
58 SNMP packets output
0 Too big errors (Maximum packet size 1500)
0 No such name errors
0 Bad values errors
0 General errors
58 Response PDUs
0 Trap PDUs
跟踪入口数据包。数据包对内部NLP接口执行UN-NAT:
FP1120-1# show capture CAPI packet-number 1 trace
30 packets captured
1: 17:04:16.720131 192.168.203.61.51308 > 192.168.203.71.161: udp 39
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
Additional Information:
NAT divert to egress interface nlp_int_tap(vrfid:0)
Untranslate 192.168.203.71/161 to 169.254.1.3/4161
Phase: 4
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 1078, packet dispatched to next module
Phase: 10
Type: INPUT-ROUTE-LOOKUP-FROM-OUTPUT-ROUTE-LOOKUP
Subtype: Resolve Preferred Egress interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 169.254.1.3 using egress ifc nlp_int_tap(vrfid:0)
Phase: 11
Type: ADJACENCY-LOOKUP
Subtype: Resolve Nexthop IP address to MAC
Result: ALLOW
Config:
Additional Information:
Found adjacency entry for Next-hop 169.254.1.3 on interface nlp_int_tap
Adjacency :Active
MAC address 3208.e2f2.b5f9 hits 0 reference 1
Result:
input-interface: inside(vrfid:0)
input-status: up
input-line-status: up
output-interface: nlp_int_tap(vrfid:0)
output-status: up
output-line-status: up
Action: allow
NAT规则作为SNMP配置的一部分自动部署:
FP1120-1# show nat
Manual NAT Policies (Section 1)
1 (nlp_int_tap) to (inside) source dynamic nlp_client_0_192.168.203.61_intf4 interface destination static nlp_client_0_ipv4_40 nlp_client_0_ipv4_40 service nlp_client_0_17svc162_39 nlp_client_0_17svc162_39
translate_hits = 0, untranslate_hits = 0
Auto NAT Policies (Section 2)
…
2 (nlp_int_tap) to (inside) source static nlp_server_0_snmp_intf4 interface service udp 4161 snmp
translate_hits = 0, untranslate_hits = 2
在后端端口中,UDP 4161侦听SNMP流量:
> expert
admin@FP1120-1:~$ sudo netstat -an | grep 4161
Password:
udp 0 0 169.254.1.3:4161 0.0.0.0:*
udp6 0 0 fd00:0:0:1::3:4161 :::*
在配置不正确/不完整的情况下,由于没有UN-NAT阶段,入口SNMP数据包将被丢弃:
FP1120-1# show cap CAPI packet-number 1 trace
6 packets captured
1: 18:36:35.868485 192.168.203.61.50105 > 192.168.203.71.161: udp 42
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: ROUTE-LOOKUP
Subtype: No ECMP load balancing
Result: ALLOW
Config:
Additional Information:
Destination is locally connected. No ECMP load balancing.
Found next-hop 192.168.203.71 using egress ifc identity(vrfid:0)
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: inside(vrfid:0)
input-status: up
input-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x0000557415b6347d flow (NA)/NA
FTD LINA系统日志显示入口数据包被丢弃:
FP1120-1# show log | include 161
Dec 30 2020 18:36:38: %FTD-7-710005: UDP request discarded from 192.168.203.61/50105 to inside:192.168.203.71/161
Dec 30 2020 18:36:39: %FTD-7-710005: UDP request discarded from 192.168.203.61/50105 to inside:192.168.203.71/161
问题解答
问:是否可以使用FTD管理接口发送SNMP消息?
否,当前不支持此功能。
相关增强缺陷:6.7 SNMP Rest API支持ngfw-mgmt接口
相关信息





















 反馈
反馈