在FTD和StrongSwan服务器之间配置站点到站点隧道
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
简介
本文档介绍如何使用认证身份验证在Cisco FTD和StrongSwan之间配置站点到站点IKEv2 VPN连接。
先决条件
要求
Cisco 建议您了解以下主题:
- 站点到站点 VPN
- 证书身份验证(IKEv2)
- 公用密钥基础结构 (PKI)
- StrongSwan基础知识
使用的组件
本文档中的信息基于以下软件和硬件版本:
- 运行版本7.2.0内部版本18的Cisco FTD
- 运行版本7.2.0内部版本18的Cisco FMC
- 运行版本20.04的Ubuntu服务器(Focal Fossa)
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
配置
场景
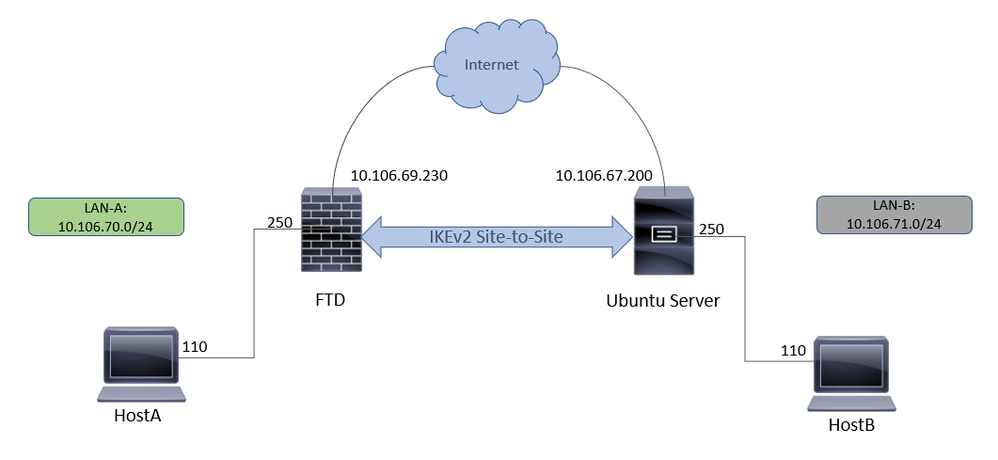
在此设置中,LAN-A中的HOST-A要与LAN-B中的HOST-B通信。此流量必须经过加密,并通过FTD与运行StrongSwan的Ubuntu服务器之间的IKEv2隧道发送。两个对等体使用Certificate Authentication相互进行身份验证。
网络图
FMC配置
获取FTD证书
1.从FMC导航至 Objects > Object Management > PKI > Cert Enrollment.
2.单击 Add Cert Enrollment.
3. “名称”部分是必填字段;请为信任点指定名称。
4.使用手动证书注册。在CA信息选项卡上,粘贴颁发者证书。

注意:如果您没有颁发者证书,则可以在没有证书的情况下继续生成CSR,并且在从CA签署CSR后,编辑第1步中提到的信任点。然后粘贴第4步中所述的CA信息。
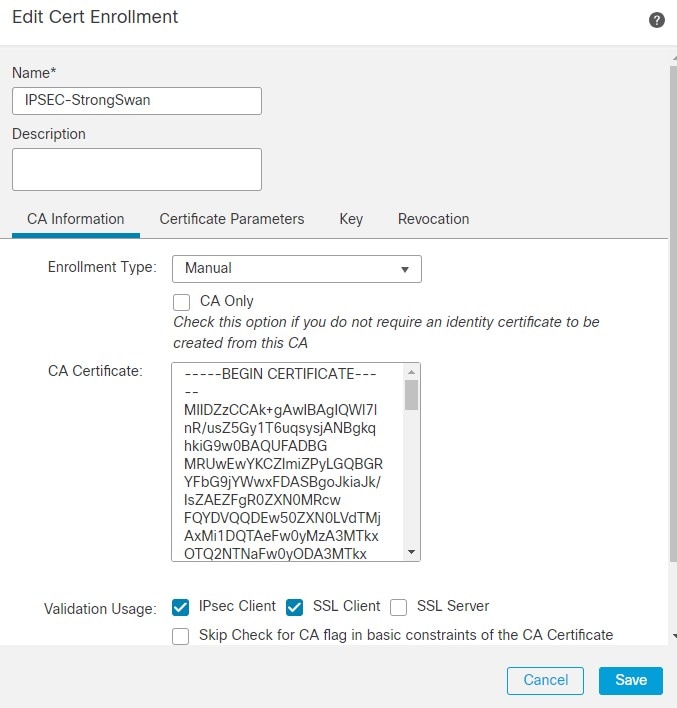
5.在“证书参数”字段中,根据需要输入参数。
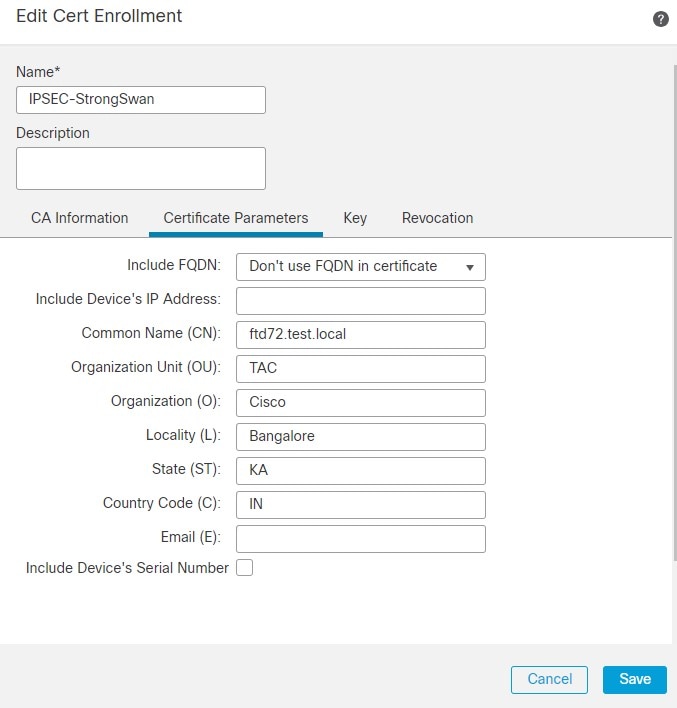
6.在“密钥”字段中,您可以使用默认的RSA密钥对,也可以通过编辑“密钥名称”字段来生成新的密钥。

注意:如果使用Windows证书颁发机构(CA),则默认应用策略扩展为IP安全IKE中间。如果使用此默认设置,则必须为所选对象在PKI证书注册(PKI Certificate Enrollment)对话框中“密钥”(Key)选项卡上的“高级设置”(Advanced Settings)部分中选择“忽略IPsec密钥使用”(Ignore IPsec Key Usage)选项。否则,终端无法完成站点到站点VPN连接。
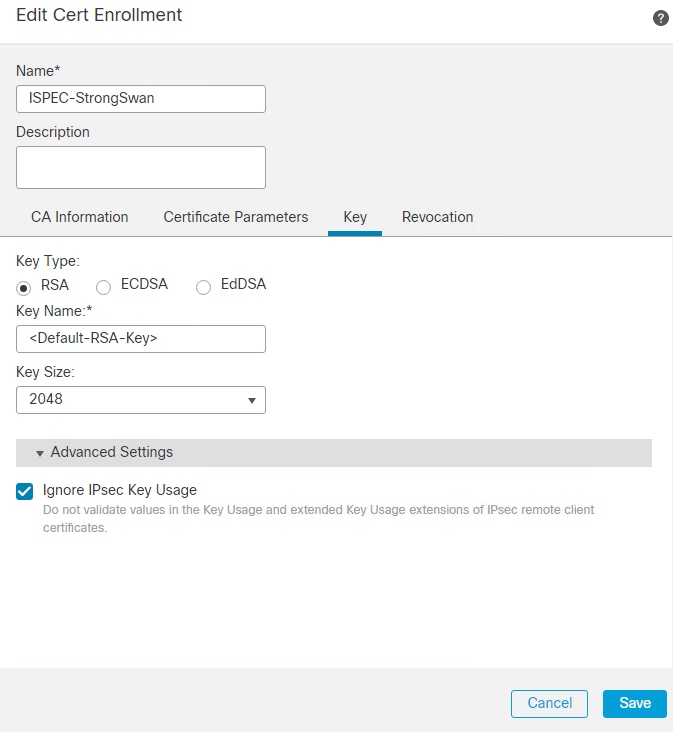
7.在“撤销”字段中,选中旁边的复选框 Consider the Certificate valid if revocation information can not be reached.未使用CRL或OCSP检查。 Click Save.

注:如果设备能够从FTD访问CRL或OCSP服务器,则可以启用广泛的撤销检查以获取证书状态。仅当在CRL服务器和FTD设备之间没有连接时,才会启用Consider the Certificate valid if revocation information cannot be reached复选框。默认情况下,在FMC上选中此项。
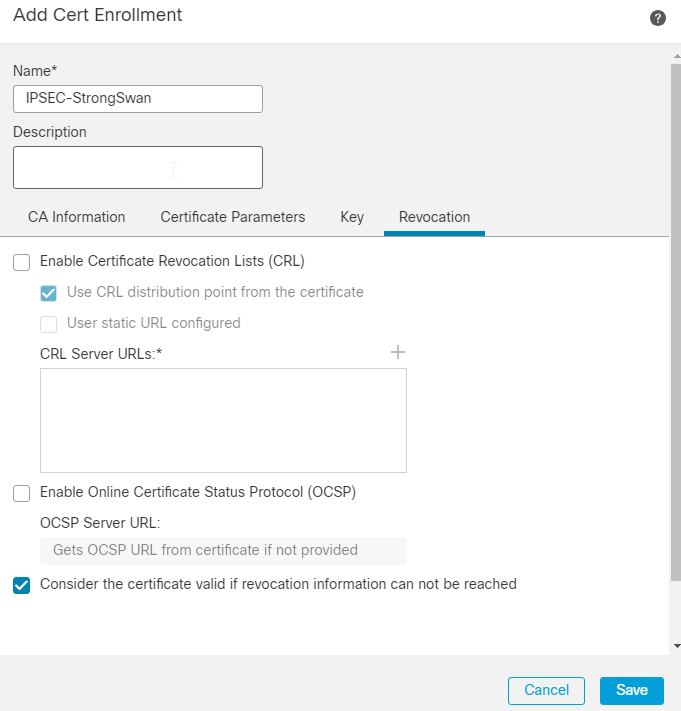
8.接下来,导航至 Devices > Certificates,单击 Add,并选择您创建的FTD设备和信任点。然后,单击 Add.
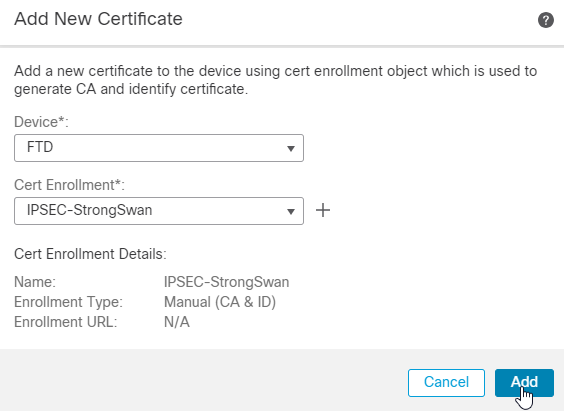
9.您可以通过单击标记为的放大镜图标来检查颁发者证书 CA.
10.您会得到类似的输出。
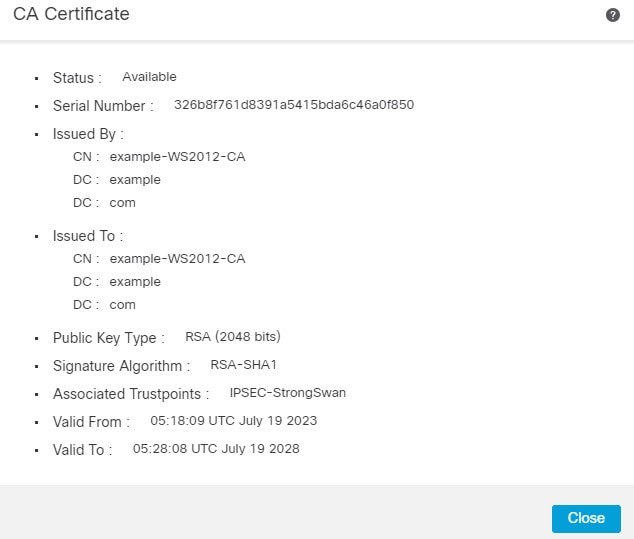
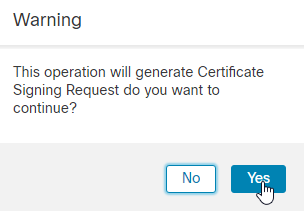
11.在下一步中,您必须单击 ID 字段中,您将看到一个弹出窗口,用于生成CSR。点击 Yes.
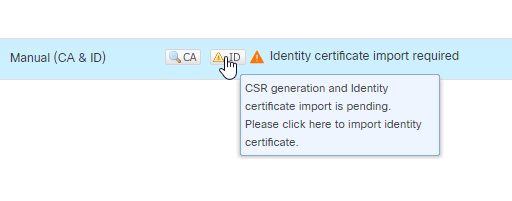
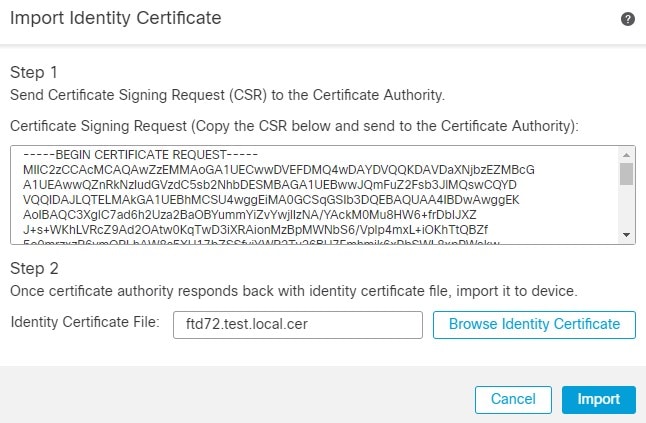
12.从CA获取身份证书文件后,您可以使用 Browse Identity Certificate 并点击 Import.

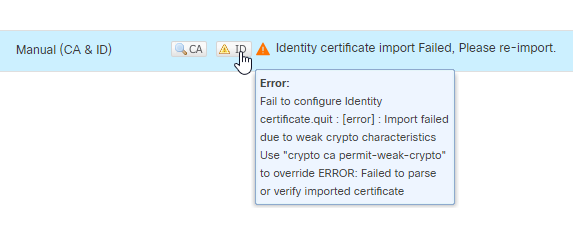
注:如果您收到有关以下内容的错误 Import failed due to weak crypto characteristics,请使用 Enable weak-crypto 选项,收到弹出窗口后,单击Yes继续。
13.重复上述步骤以生成CSR,并导入身份证书。
无需再次提交CSR,因为设备没有任何更改。您可以通过导航到CA直接导入颁发的证书。
14.现在,您可以通过点击标记为的放大镜图标来查看身份证书 ID.
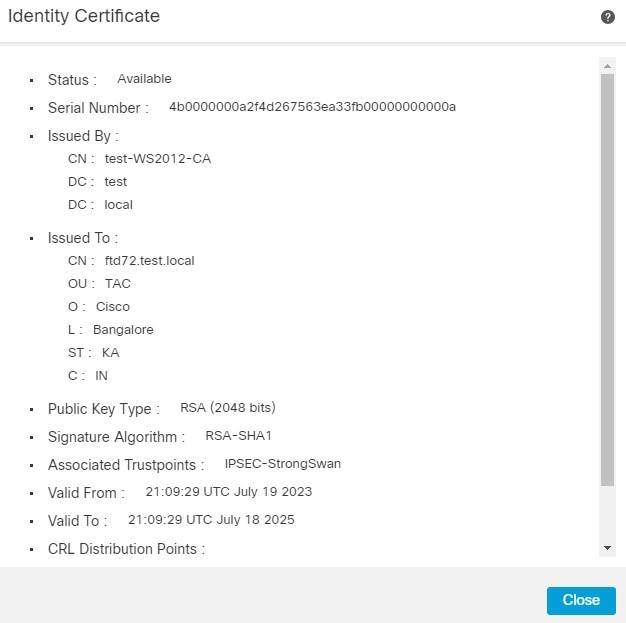
15.证书已成功添加。
VPN 配置
1.导航至 Devices > Site to Site VPN .
2.单击 Add > VPN Tunnel.
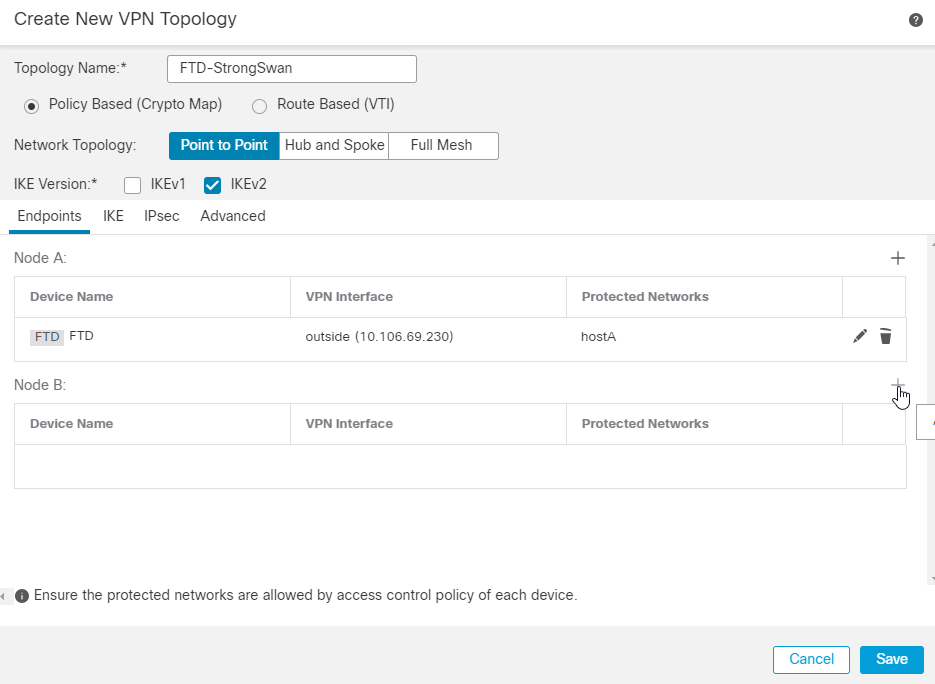
3.输入拓扑名称,该名称为必填字段。 Policy based (Crypto Map), Point-to-Point Topology,和 IKEv2 默认情况下已选择,您必须使用这些选项。
4.在“终端”部分,单击 + 图标。
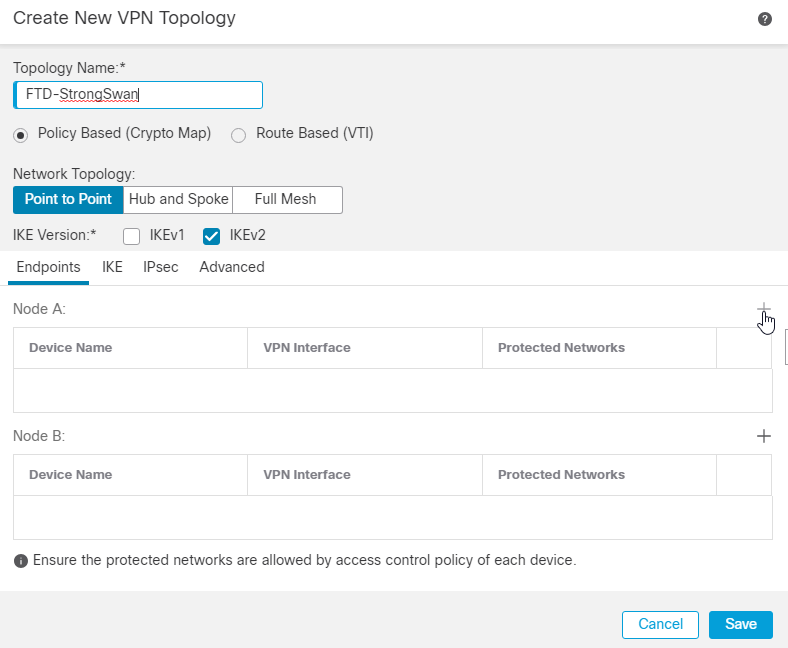
5.选择FTD设备作为节点A,VPN终端接口为外部接口。
6.在“受保护的网络”字段中,选择子网/IP地址(网络),然后单击 + 图标。
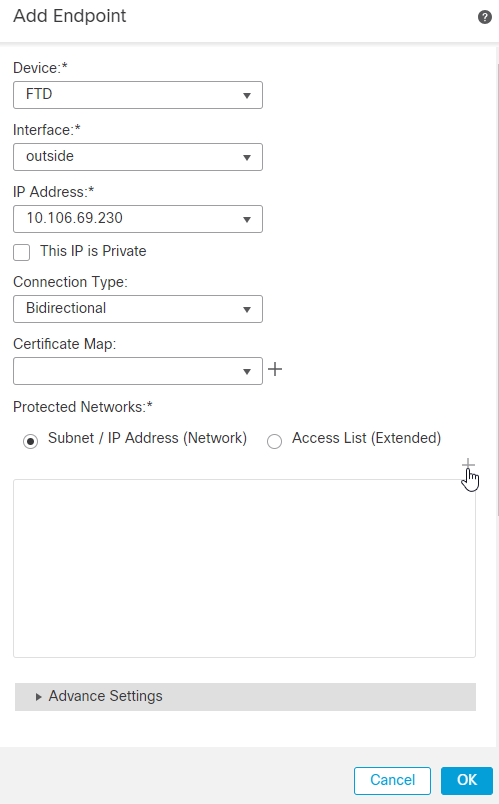
7.点击旁边的+图标 Available Networks.
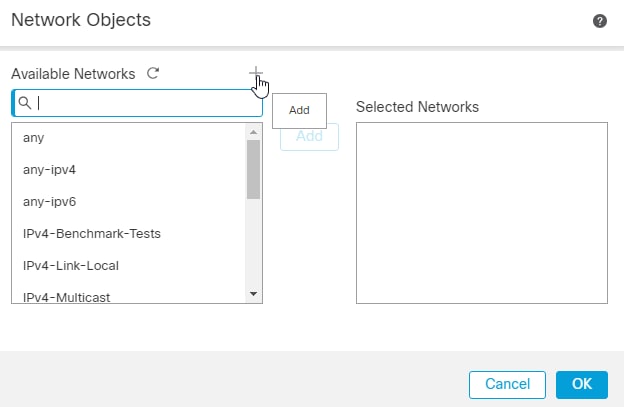
8.此处定义了必须受到保护的FTD后面的网络或主机或IP地址范围。在本例中,hostA的IP地址为10.106.70.110/32。点击 Save.
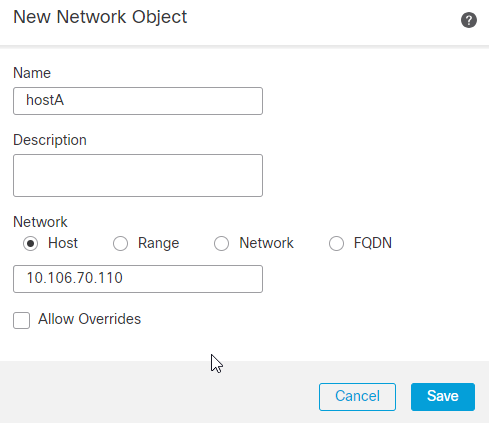
9.选择在前一步骤中为网络对象输入的名称并点击 Add.现在,您可以看到在选定网络中配置的网络对象名称。点击 OK.
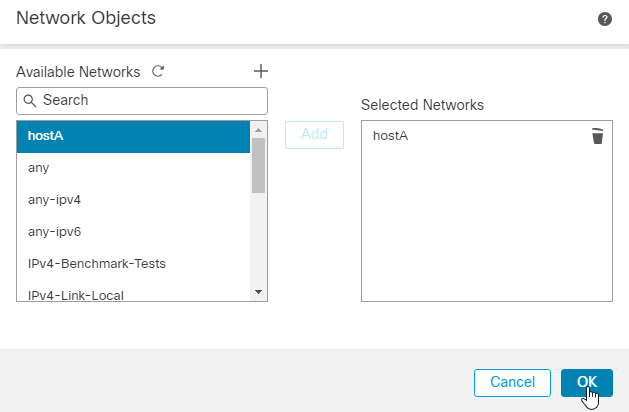
10.您现在可以在“受保护的网络”列表中看到我们的网络对象已配置。点击 OK.FTD端点现已配置,接下来是远程对等端配置。
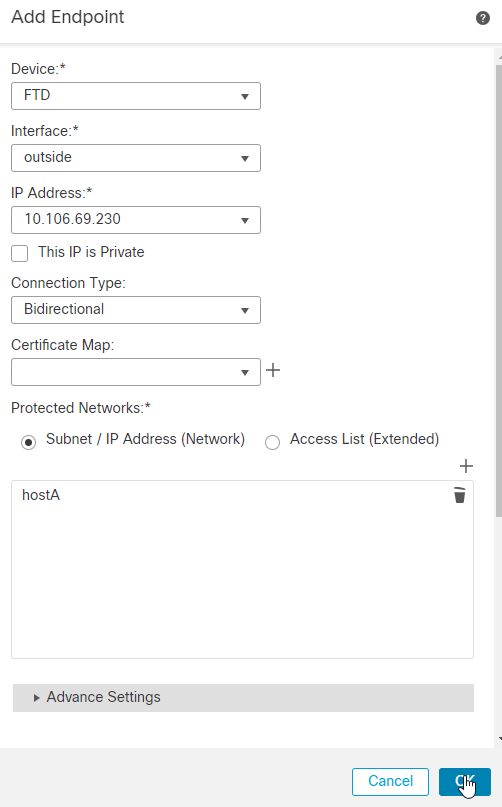
11.对节点B执行相同的流程。单击 + 图标。
12.如果远程对等设备是外部设备,则必须选择设备作为外联网。添加设备名称及其面向公众的IP地址作为对等体地址。
13.在“受保护的网络”字段中,选择子网/IP地址(网络),然后单击 +.
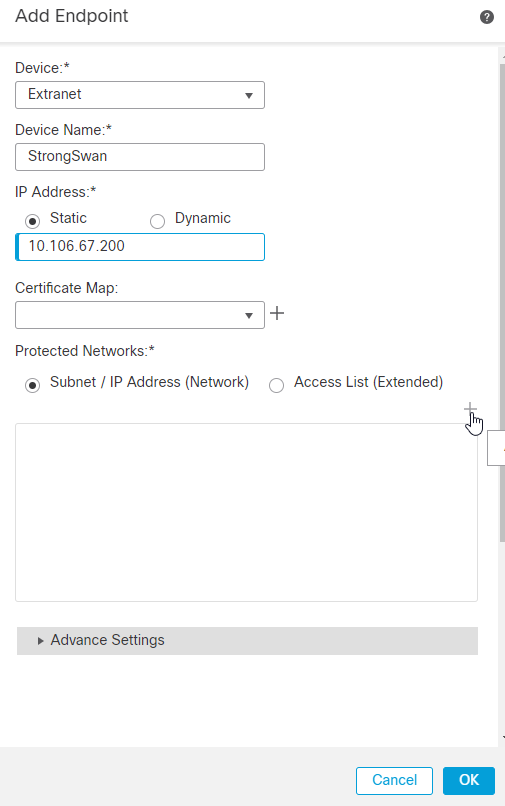
14.单击 + 图标。
15.输入要在Ubuntu服务器后面保护的主机或网络或范围IP地址。 在本例中,hostB的IP地址为10.106.71.110/32。Click Save.
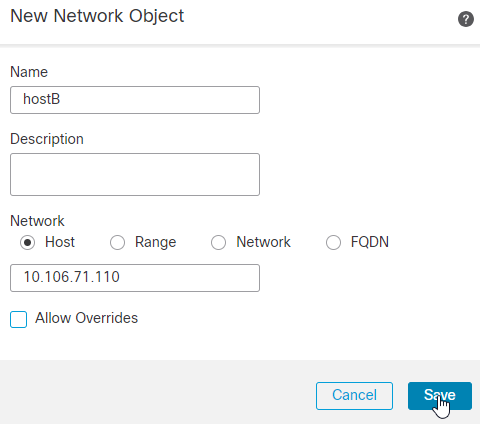
16.选择在前面步骤中为网络对象输入的名称并点击 Add现在,您可以看到在选定网络中配置的网络对象名称。点击 OK .
17.现在,您可以看到“受保护的网络”列表中配置的网络对象。Click OK.
18.现在配置必须保护的终端和网络。
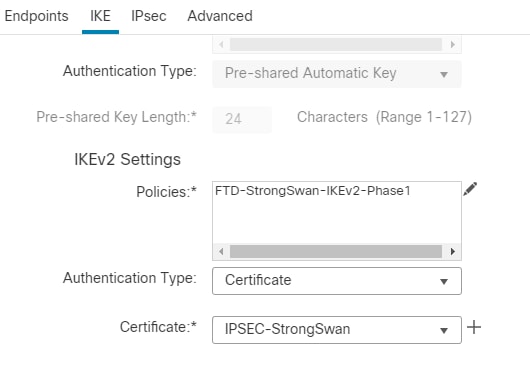
19.接下来,从“终端”部分转到IKE部分。通过点击IKEv2 Settings下的 Pencil 图标旁边的Policies。
20.在政策一节中, Encryption AES, Integrity SHA1, PRF SHA1, DH Group 14 (mod 2048),和 FTD-StrongSwan-IKEv2-Phase1 使用。
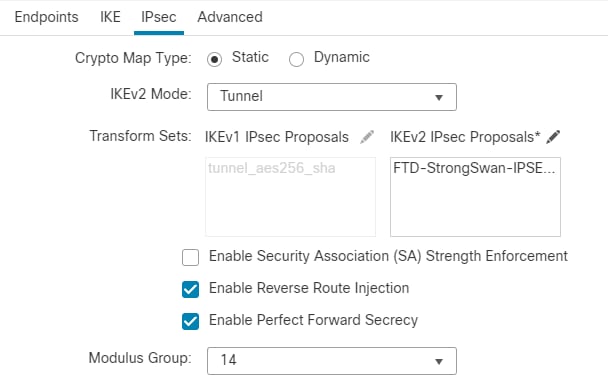
21.将默认加密映射保留为静态,将IKEv2模式保留为隧道。在转换集中,单击 Pencil 图标旁边的“建议”。在建议书中,选择 Encryption AES, Integrity sha-1,和 PFS DH group 14 (2048) 如FTD-StrongSwan-IPSec中的建议。
22.现在,从顶部的导航窗格导航至 Policies > Access Control.编辑您处理的FTD的ACP。
23.单击 Add Rule.
24.默认规则是阻止所有流量,以允许主机A和主机B之间的双向流量。如果已配置区域,请选择相关区域并将其添加到源和目标区域。??然后单击 Add .
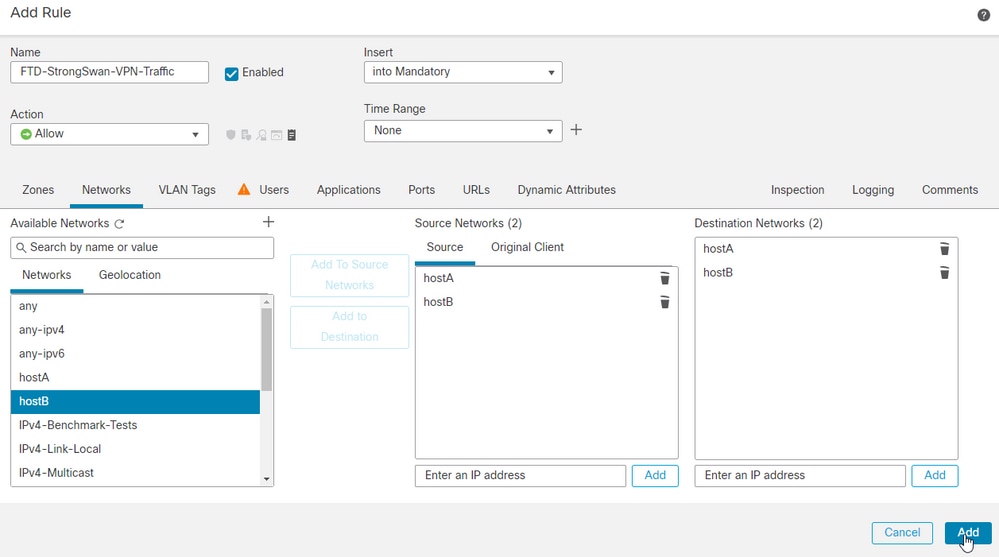
25.添加规则后,单击 Save .
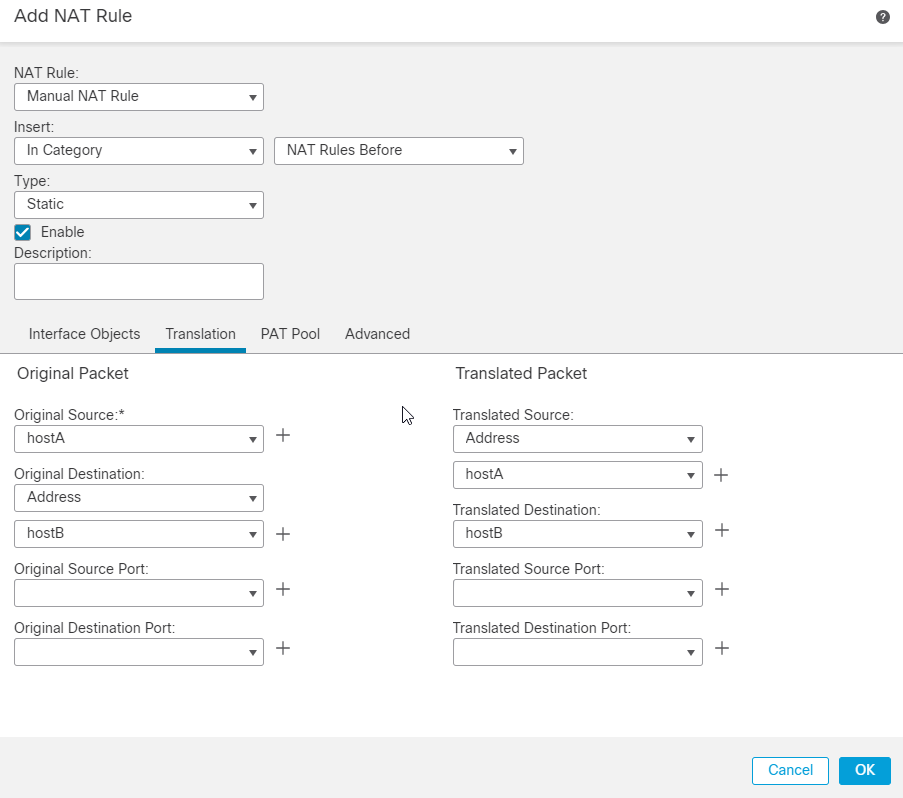
26.最后,您必须为要免除的VPN流量配置No NAT语句,以防FTD上存在任何NAT。导航至 Devices > NAT.点击 Add Rule.
27.添加相关的接口对象,并在translation部分下选择Original和Translated源作为FTD后面受VPN保护的网络,在本例中为hostA。同样,对于Original和Translated目标,选择远程终端后方受VPN保护的网络,在本例中为hostB。
28.在“高级”部分下,确保检查 Do not proxy ARP on Destination Interface 和 Perform Route Lookup for Destination Interface No NAT语句所需的复选框。
StrongSwan配置
获取证书
显示的所有命令都需要sudo权限。如果您没有sudo访问权限或安装软件的权限,请与您的系统管理员联系。此处可以找到官方StrongSwan配置示例。
1.首先更新系统包缓存。
apt update
2.安装StrongSwan及其依赖项。您可以在此处找到有关软件包的更多信息。
apt install strongswan strongswan-pki strongswan-swanctl libcharon-extra-plugins libcharon-extauth-plugins libstrongswan-extra-plugins
3.检查StrongSwan后台守护程序的状态。状态必须显示活动(正在运行)。
systemctl status strongswan-starter.service
4.如果由于某种原因未启用,请将其启用,然后使用此命令将其启动。
systemctl enable --now strongswan-starter.service
5.接下来,使用 strong-swan pki 命令行工具,用于生成私钥和CSR。要生成服务器的私钥,请执行此命令。
pki --gen > sswan.priv.key
6.为StrongSwan服务器生成CSR请求。您可以修改 --dn 根据您的要求选择参数。
pki --req --in sswan.priv.key --dn "CN=sswan.test.local, O=Cisco, OU=TAC, ST=KA, C=IN" --outform pem > sswan.test.local.pem
7.获得CA签名的CSR后,将颁发者证书、身份证书和私钥复制到相应的证书。 /etc/swanctl 目录。
cp $HOME/certs/root-ca.cer /etc/swanctl/x509ca/
cp $HOME/certs/sswan.test.local.cer /etc/swanctl/x509/
cp $HOME/certs/sswan.priv.key /etc/swanctl/private/
Swanctl配置文件
connections {
strongswan-ftd {
# Peer IP's
local_addrs = 10.106.67.200
remote_addrs = 10.106.69.230
local {
auth = pubkey
certs = sswan.test.local.cer
id = "sswan.test.local"
}
remote {
auth = pubkey
id = "C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local"
}
children {
hostB-hostA {
local_ts = 10.106.71.110/32
remote_ts = 10.106.70.110/32
rekey_time = 28800 # Phase-2 Lifetime
esp_proposals = aes-sha-modp2048 # Phase-2 Paramters
}
}
mobike = no
version = 2 # IKE version 2
reauth_time = 86400 # Phase-1 Lifetime
proposals = aes-sha-prfsha1-modp2048 # Phase-1 Paramters
}
}
验证
FTD
1.检查IKEv2第1阶段参数。
firepower# sh run crypto ikev2
crypto ikev2 policy 1
encryption aes
integrity sha
group 14
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
2.检查第2阶段的参数。
firepower# sh run crypto ipsec
crypto ipsec ikev2 ipsec-proposal CSM_IP_2
protocol esp encryption aes
protocol esp integrity sha-1
3.检查加密映射配置。

注:在FTD 7.2.0版本上,默认值为 PFS is DH Group 14 (MOD 2048).您可以通过以下方式验证相同内容: running sh run all crypto map.
firepower# sh run crypto map
crypto map CSM_outside_map 1 match address CSM_IPSEC_ACL_1
crypto map CSM_outside_map 1 set pfs
crypto map CSM_outside_map 1 set peer 10.106.67.200
crypto map CSM_outside_map 1 set ikev2 ipsec-proposal CSM_IP_2
crypto map CSM_outside_map 1 set trustpoint IPSEC-StrongSwan
crypto map CSM_outside_map 1 set reverse-route
crypto map CSM_outside_map interface outside
4.检查加密ACL。
firepower# sh access-list CSM_IPSEC_ACL_1
access-list CSM_IPSEC_ACL_1; 1 elements; name hash: 0x1fb1fb7
access-list CSM_IPSEC_ACL_1 line 1 extended permit ip host 10.106.70.110 host 10.106.71.110 (hitcnt=37) 0xc8d25938
5.检查隧道状态。
firepower# sh vpn-sessiondb det l2l
Session Type: LAN-to-LAN Detailed
Connection : 10.106.67.200
Index : 61 IP Addr : 10.106.67.200
Protocol : IKEv2 IPsec
Encryption : IKEv2: (1)AES128 IPsec: (1)AES128
Hashing : IKEv2: (1)SHA1 IPsec: (1)SHA1
Bytes Tx : 0
Bytes Rx : 0
Login Time : 12:16:25 UTC Mon Jul 17 2023
Duration : 0h:11m:30s
Tunnel Zone : 0
IKEv2 Tunnels: 1
IPsec Tunnels: 1
IKEv2:
Tunnel ID : 61.1
UDP Src Port : 500 UDP Dst Port : 500
Rem Auth Mode: rsaCertificate
Loc Auth Mode: rsaCertificate
Encryption : AES128 Hashing : SHA1
Rekey Int (T): 86400 Seconds Rekey Left(T): 85710 Seconds
PRF : SHA1 D/H Group : 14
Filter Name :
IPsec:
Tunnel ID : 61.2
Local Addr : 10.106.70.110/255.255.255.255/0/0
Remote Addr : 10.106.71.110/255.255.255.255/0/0
Encryption : AES128 Hashing : SHA1
Encapsulation: Tunnel PFS Group : 14
Rekey Int (T): 28800 Seconds Rekey Left(T): 28110 Seconds
Rekey Int (D): 4608000 K-Bytes Rekey Left(D): 4608000 K-Bytes
Idle Time Out: 30 Minutes Idle TO Left : 29 Minutes
Conn Time Out: 1032728 Minutes Conn TO Left : 1032714 Minutes
Bytes Tx : 600 Bytes Rx : 880
Pkts Tx : 10 Pkts Rx : 10
6.检查IPSEC SA计数器。
firepower# sh cry ipsec sa
interface: outside
Crypto map tag: CSM_outside_map, seq num: 1, local addr: 10.106.69.230
access-list CSM_IPSEC_ACL_1 extended permit ip host 10.106.70.110 host 10.106.71.110
Protected vrf:
local ident (addr/mask/prot/port): (10.106.70.110/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (10.106.71.110/255.255.255.255/0/0)
current_peer: 10.106.67.200
#pkts encaps: 10, #pkts encrypt: 10, #pkts digest: 10
#pkts decaps: 10, #pkts decrypt: 10, #pkts verify: 10
StrongSwan
1.检查加载的连接。如果未看到任何连接,请运行 swanctl --load-all.
root@strongswan:~# swanctl --list-conn
strongswan-ftd: IKEv2, reauthentication every 86400s, no rekeying
local: 10.106.67.200
remote: 10.106.69.230
local public key authentication:
id: sswan.test.local
certs: C=IN, ST=KA, O=Cisco, OU=TAC, CN=sswan.test.local
remote public key authentication:
id: C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local
hostB-hostA: TUNNEL, rekeying every 28800s
local: 10.106.71.110/32
remote: 10.106.70.110/32
2.检查子级的SA状态。
root@strongswan:~# swanctl --list-sas
strongswan-ftd: #11, ESTABLISHED, IKEv2, 791c5a5633f9ea83_i a4e0487769c49dad_r*
local 'sswan.test.local' @ 10.106.67.200[500]
remote 'C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local' @ 10.106.69.230[500]
AES_CBC-128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
established 279s ago, reauth in 83226s
hostB-hostA: #8, reqid 6, INSTALLED, TUNNEL, ESP:AES_CBC-128/HMAC_SHA1_96
installed 279s ago, rekeying in 25753s, expires in 31401s
in cc01a2a7, 600 bytes, 10 packets, 10s ago
out 3594c049, 600 bytes, 10 packets, 10s ago
local 10.106.71.110/32
remote 10.106.70.110/32
故障排除
FTD
debug crypto condition peer 10.106.67.200
debug crypto ikev2 platfform 127
debug crypto ikev2 protocol 127
debug crypto ipsec 127
对等体ID验证已打开。
==== OUTPUT OMITTED ====
IKEv2-PLAT-4: (203): Peer ID check started, received ID type: IPv4 address
IKEv2-PLAT-4: (203): Peer ID check: failed to retreive IP from SAN
IKEv2-PLAT-4: (203): Peer ID check: failed to retreive DNS name from SAN
IKEv2-PLAT-4: (203): Peer ID check: failed to retreive RFC822 name from SAN
IKEv2-PLAT-4: (203): retrieving SAN for peer ID check
IKEv2-PLAT-2: (203): Peer ID check failed
IKEv2-PROTO-2: (203): Failed to locate an item in the database
IKEv2-PROTO-7: (203): SM Trace-> SA: I_SPI=40DC7DC3A0BDF20D R_SPI=E02399BAC06E0944 (I) MsgID = 00000001 CurState: I_PROC_AUTH Event: EV_AUTH_FAIL
IKEv2-PROTO-4: (203): Verification of peer's authentication data FAILED
IKEv2-PROTO-7: (203): SM Trace-> SA: I_SPI=40DC7DC3A0BDF20D R_SPI=E02399BAC06E0944 (I) MsgID = 00000001 CurState: AUTH_DONE Event: EV_FAIL
IKEv2-PROTO-4: (203): Auth exchange failed
IKEv2-PROTO-2: (203): Auth exchange failed
IKEv2-PROTO-2: (203): Auth exchange failed
IKEv2-PROTO-7: (203): SM Trace-> SA: I_SPI=40DC7DC3A0BDF20D R_SPI=E02399BAC06E0944 (I) MsgID = 00000001 CurState: EXIT Event: EV_ABORT
IKEv2-PROTO-7: (203): SM Trace-> SA: I_SPI=40DC7DC3A0BDF20D R_SPI=E02399BAC06E0944 (I) MsgID = 00000001 CurState: EXIT Event: EV_CHK_PENDING_ABORT
IKEv2-PLAT-7: Negotiating SA request deleted
IKEv2-PLAT-7: Decrement count for outgoing negotiating
IKEv2-PROTO-7: (203): SM Trace-> SA: I_SPI=40DC7DC3A0BDF20D R_SPI=E02399BAC06E0944 (I) MsgID = 00000001 CurState: EXIT Event: EV_UPDATE_CAC_STATS
IKEv2-PROTO-4: (203): Abort exchange
IKEv2-PROTO-4: (203): Deleting SA
==== OUTPUT OMITTED ====
StrongSwan
root@strongswan:~# swanctl --log
01[NET] received packet: from 10.106.69.230[500] to 10.106.67.200[500] (574 bytes)
01[ENC] parsed IKE_SA_INIT request 0 [ SA KE No V V N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) V ]
01[IKE] received Cisco Delete Reason vendor ID
01[IKE] received Cisco Copyright (c) 2009 vendor ID
01[IKE] received FRAGMENTATION vendor ID
01[IKE] 10.106.69.230 is initiating an IKE_SA
01[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
01[IKE] sending cert request for "DC=local, DC=test, CN=test-WS2012-CA"
01[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(CHDLESS_SUP) N(MULT_AUTH) ]
01[NET] sending packet: from 10.106.67.200[500] to 10.106.69.230[500] (481 bytes)
06[NET] received packet: from 10.106.69.230[500] to 10.106.67.200[500] (528 bytes)
06[ENC] parsed IKE_AUTH request 1 [ EF(1/5) ]
06[ENC] received fragment #1 of 5, waiting for complete IKE message
07[NET] received packet: from 10.106.69.230[500] to 10.106.67.200[500] (528 bytes)
07[ENC] parsed IKE_AUTH request 1 [ EF(2/5) ]
07[ENC] received fragment #2 of 5, waiting for complete IKE message
12[NET] received packet: from 10.106.69.230[500] to 10.106.67.200[500] (528 bytes)
12[ENC] parsed IKE_AUTH request 1 [ EF(3/5) ]
12[ENC] received fragment #3 of 5, waiting for complete IKE message
11[NET] received packet: from 10.106.69.230[500] to 10.106.67.200[500] (528 bytes)
11[ENC] parsed IKE_AUTH request 1 [ EF(4/5) ]
11[ENC] received fragment #4 of 5, waiting for complete IKE message
09[NET] received packet: from 10.106.69.230[500] to 10.106.67.200[500] (208 bytes)
09[ENC] parsed IKE_AUTH request 1 [ EF(5/5) ]
09[ENC] received fragment #5 of 5, reassembled fragmented IKE message (2012 bytes)
09[ENC] parsed IKE_AUTH request 1 [ V IDi CERT CERTREQ AUTH SA TSi TSr N(INIT_CONTACT) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
09[IKE] received cert request for "DC=local, DC=test, CN=test-WS2012-CA"
09[IKE] received end entity cert "C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local"
09[CFG] looking for peer configs matching 10.106.67.200[%any]...10.106.69.230[C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local]
09[CFG] selected peer config 'strongswan-ftd'
09[CFG] using certificate "C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local"
09[CFG] using trusted ca certificate "DC=local, DC=test, CN=test-WS2012-CA"
09[CFG] reached self-signed root ca with a path length of 0
09[CFG] checking certificate status of "C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local"
09[CFG] fetching crl from 'ldap:///CN=test-WS2012-CA,CN=ws2012,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=test,DC=local?certificateRevocationList?base?objectClass=cRLDistributionPoint' ...
09[LIB] LDAP bind to 'ldap:///CN=test-WS2012-CA,CN=ws2012,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=test,DC=local?certificateRevocationList?base?objectClass=cRLDistributionPoint' failed: Can't contact LDAP server
09[CFG] crl fetching failed
09[CFG] certificate status is not available
09[IKE] authentication of 'C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local' with RSA signature successful
09[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
09[IKE] authentication of 'sswan.test.local' (myself) with RSA signature successful
09[IKE] IKE_SA strongswan-ftd[11] established between 10.106.67.200[sswan.test.local]...10.106.69.230[C=IN, ST=KA, L=Bangalore, O=Cisco, OU=TAC, CN=ftd72.test.local]
09[IKE] scheduling reauthentication in 83505s
09[IKE] maximum IKE_SA lifetime 92145s
09[IKE] sending end entity cert "C=IN, ST=KA, O=Cisco, OU=TAC, CN=sswan.test.local"
09[CFG] selected proposal: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ
09[IKE] CHILD_SA hostB-hostA{8} established with SPIs cc01a2a7_i 3594c049_o and TS 10.106.71.110/32 === 10.106.70.110/32
09[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH SA TSi TSr N(AUTH_LFT) ]
09[ENC] splitting IKE message (1852 bytes) into 2 fragments
09[ENC] generating IKE_AUTH response 1 [ EF(1/2) ]
09[ENC] generating IKE_AUTH response 1 [ EF(2/2) ]
09[NET] sending packet: from 10.106.67.200[500] to 10.106.69.230[500] (1248 bytes)
09[NET] sending packet: from 10.106.67.200[500] to 10.106.69.230[500] (672 bytes)
12[NET] received packet: from 10.106.69.230[500] to 10.106.67.200[500] (76 bytes)
12[ENC] parsed INFORMATIONAL request 2 [ ]
12[ENC] generating INFORMATIONAL response 2 [ ]
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
28-Jul-2023 |
初始版本 |
由思科工程师提供
- 《山什里马》思科TAC工程师
- 帕万·贡杜思科TAC工程师
- 斯里尼瓦苏鲁波达思科TAC工程师
 反馈
反馈