在FMC管理的FTD上使用IP SLA配置ECMP
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
简介
本文档介绍如何在由FMC管理的FTD上配置ECMP和IP SLA。
先决条件
要求
Cisco 建议您了解以下主题:
- 思科安全防火墙威胁防御(FTD)上的ECMP配置
- 思科安全防火墙威胁防御(FTD)上的IP SLA配置
- 思科安全防火墙管理中心(FMC)
使用的组件
本文档中的信息基于以下软件和硬件版本:
-
思科FTD版本7.4.1
-
思科FMC版本7.4.1
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
背景信息
本文档介绍如何在由Cisco FMC管理的思科FTD上配置等价多路径(ECMP)以及互联网协议服务级别协议(IP SLA)。 ECMP允许您在FTD上将接口分组到一起,并在多个接口之间均衡流量负载。 IP SLA是一种通过交换常规数据包来监控端到端连接的机制。与ECMP一起,可以实施IP SLA以确保下一跳的可用性。 在本例中,ECMP用于在两个Internet服务提供商(ISP)电路上平均分配数据包。同时,IP SLA会跟踪连通性,确保在发生故障时无缝过渡至任何可用电路。
本文档的具体要求包括:
- 使用具有管理员权限的用户帐户访问设备
- 思科安全防火墙威胁防御7.1版或更高版本
- Cisco安全防火墙管理中心7.1版或更高版本
配置
网络图
在本例中,Cisco FTD有两个外部接口:outside1和outside2。每个都连接到ISP网关,outside1和outside2属于名为outside的同一个ECMP区域。
来自内部网络的流量通过FTD路由,并通过两个ISP实现到Internet的负载均衡。
同时,FTD使用IP SLA来监控与每个ISP网关的连接。如果任何ISP电路出现故障,FTD会故障切换到另一个ISP网关以保持业务连续性。
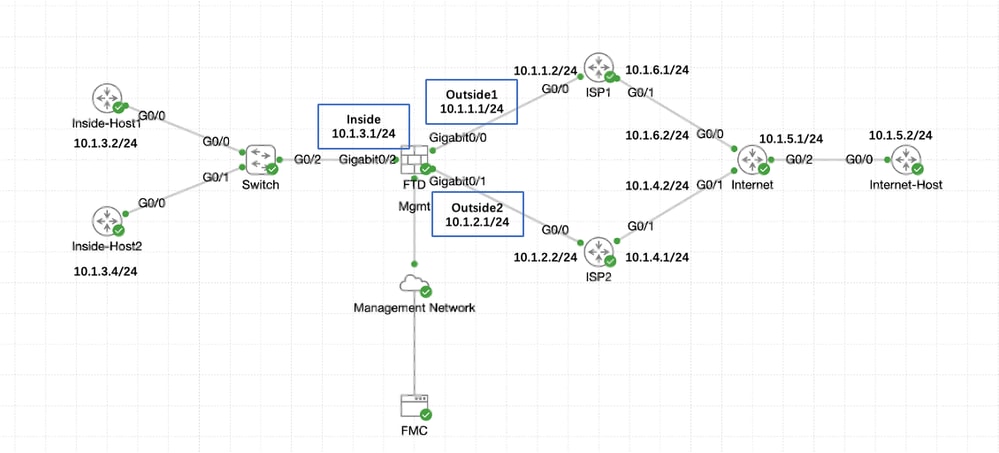 网络图
网络图
配置
步骤 0预配置接口/网络对象
登录FMC Web GUI,选择Devices > Device Management,然后针对威胁防御设备点击Edit按钮。默认情况下,Interfaces 页处于选中状态。针对要编辑的接口(在本示例中为GigabitEthernet0/0)单击Edit按钮。
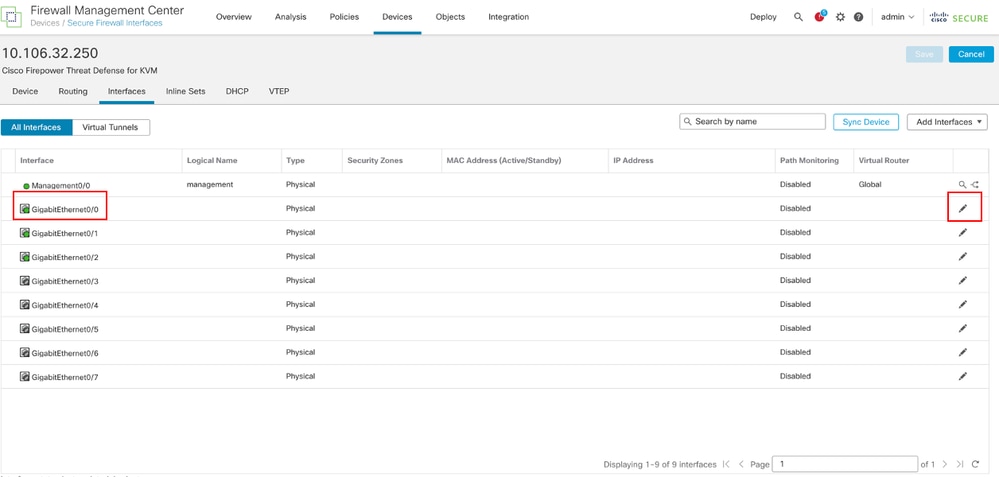 编辑接口Gi0/0
编辑接口Gi0/0
在Edit Physical Interface窗口的General选项卡下:
- 设置Name,在本例中为Outside1。
- 通过选中Enabled复选框启用接口。
- 在安全区域下拉列表中,选择现有的安全区域或创建一个新安全区域,本示例中为Outside1_Zone。
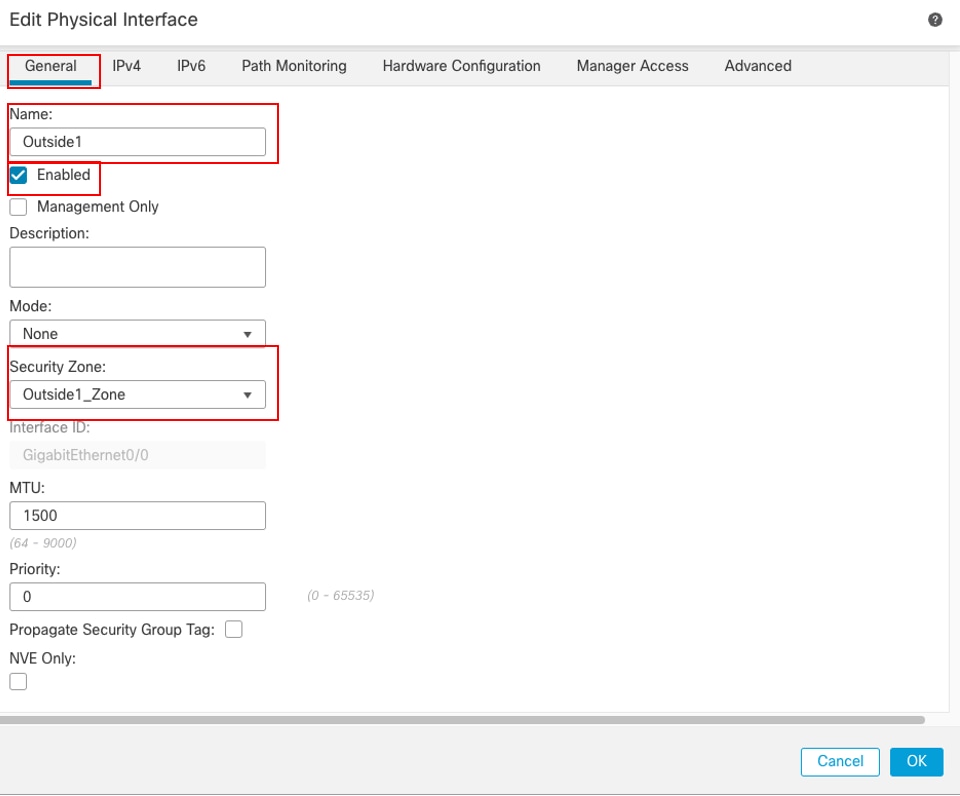 接口Gi0/0常规
接口Gi0/0常规
在IPv4选项卡下:
- 从IP Type下拉列表中选择其中一个选项,在本示例中为Use Static IP。
- 设置IP地址,在本示例中为10.1.1.1/24。
- Click OK.
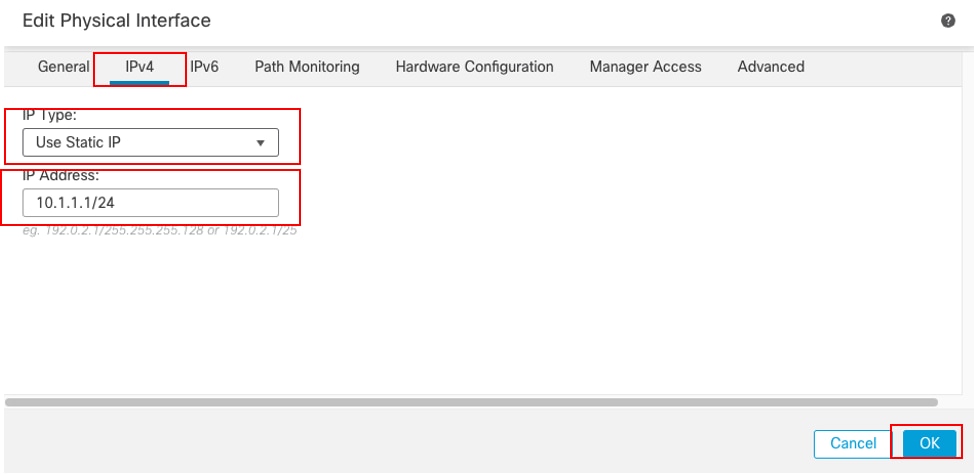 接口Gi0/0 IPv4
接口Gi0/0 IPv4
在Edit Physical Interface窗口的General选项卡下,重复类似步骤以配置接口GigabitEthernet0/1:
- 设置Name,在本例中为Outside2。
- 通过选中Enabled复选框启用接口。
- 在安全区域下拉列表中,选择现有的安全区域或创建一个新安全区域,本示例中为Outside2_Zone。
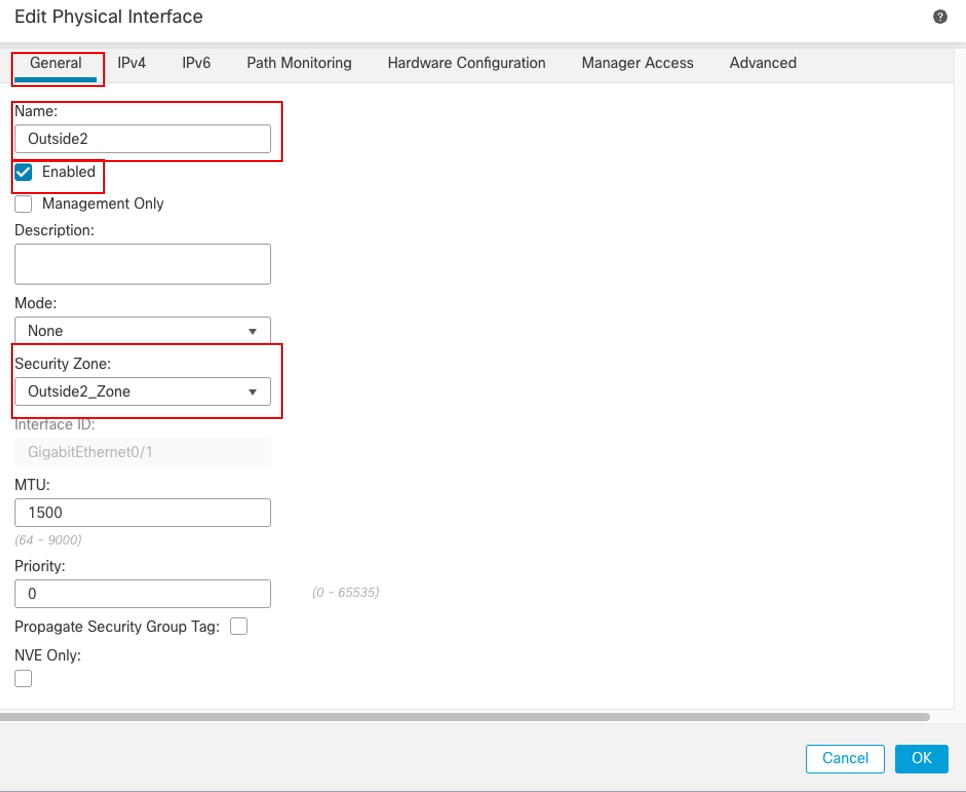 接口Gi0/1常规
接口Gi0/1常规
在IPv4选项卡下:
- 从IP Type下拉列表中选择其中一个选项,在本示例中为Use Static IP。
- 设置IP地址,在本示例中为10.1.2.1/24。
- Click OK.
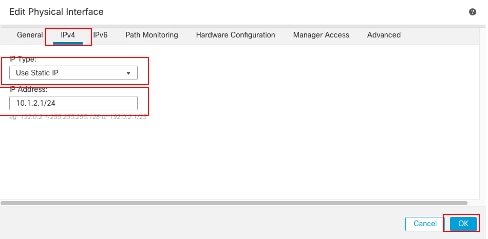 接口Gi0/1 IPv4
接口Gi0/1 IPv4
重复类似步骤,在Edit Physical Interface窗口的General选项卡下配置接口GigabitEthernet0/2:
- 设置Name,在本例中为Inside。
- 通过选中Enabled复选框启用接口。
- 在安全区域下拉列表中,选择现有的安全区域或创建一个新安全区域,本示例中为Inside_Zone。
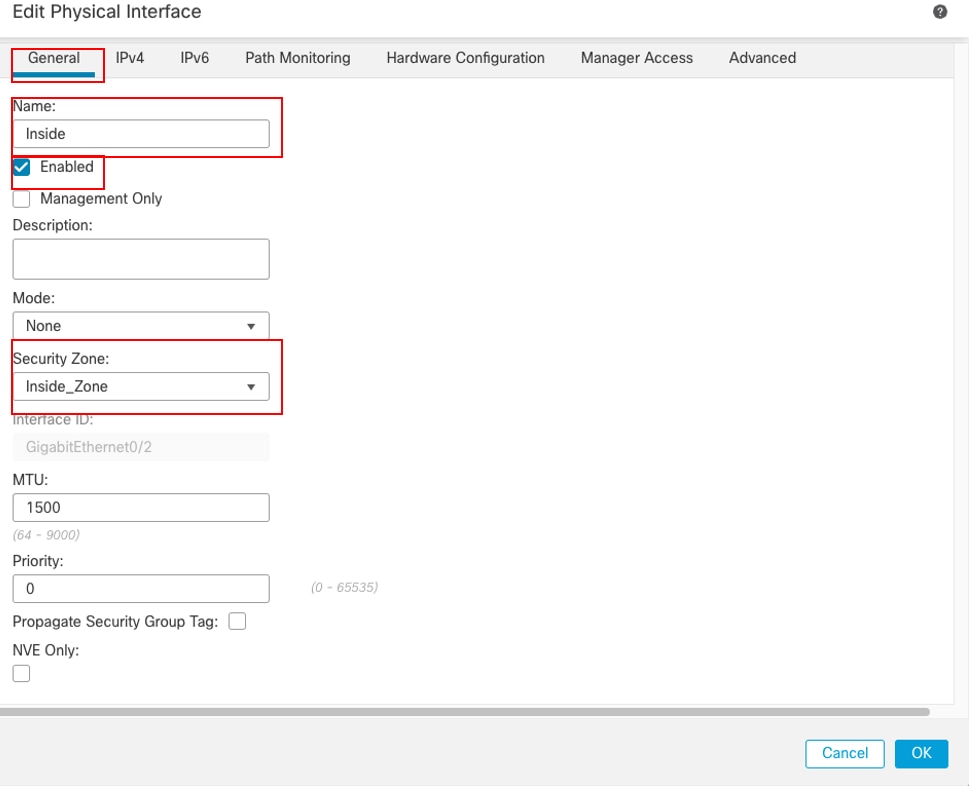 接口Gi0/2常规
接口Gi0/2常规
在IPv4选项卡下:
- 从IP Type下拉列表中选择其中一个选项,在本示例中为Use Static IP。
- 设置IP地址,在本示例中为10.1.3.1/24。
- Click OK.
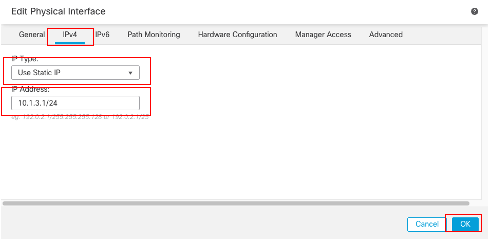 接口Gi0/2 IPv4
接口Gi0/2 IPv4
点击保存和部署配置。
导航到Objects > Object Management,从对象类型列表中选择Network,然后从Add Network下拉菜单中选择Add Object,以便为第一个ISP网关创建对象。
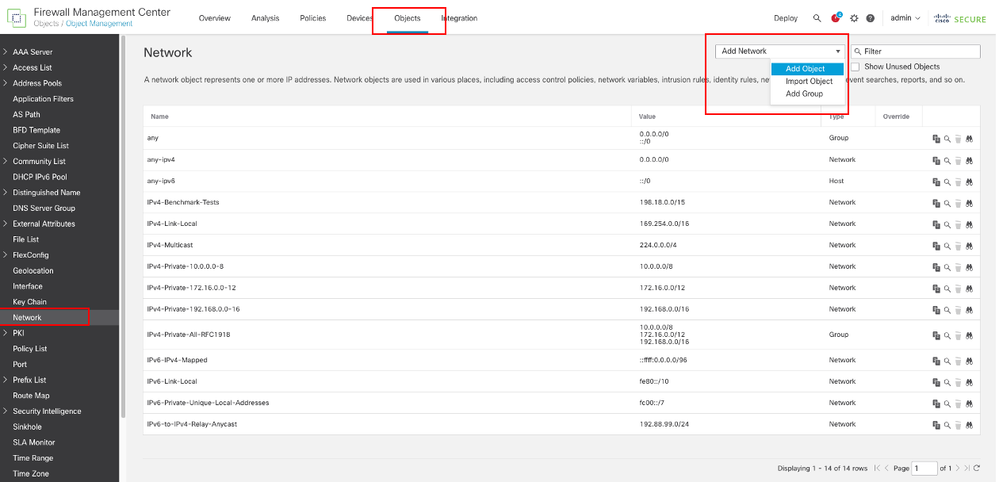 网络对象
网络对象
在New Network Object窗口中:
- 设置Name,在此示例中为gw-outside1。
- 在网络字段中,选择所需的选项并输入适当的值,如本示例中的主机和10.1.1.2。
- Click Save.
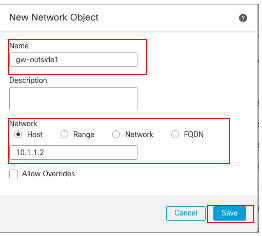 对象Gw-outside1
对象Gw-outside1
重复类似步骤,为第二个ISP网关创建另一个对象。在New Network Object窗口中:
- 设置Name,在本示例中为gw-outside2。
- 在网络字段中,选择所需的选项并输入适当的值,如本示例中的主机和10.1.2.2。
- Click Save.
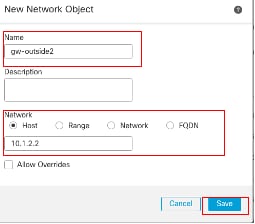 对象Gw-outside2
对象Gw-outside2
步骤1:配置ECMP区域
导航到设备 > 设备管理,编辑威胁防御设备,点击路由。从virtual router下拉列表中,选择要创建ECMP区域的虚拟路由器。您可以在全局虚拟路由器和用户定义的虚拟路由器中创建ECMP区域。本示例中选择Global。
单击ECMP,然后单击Add。
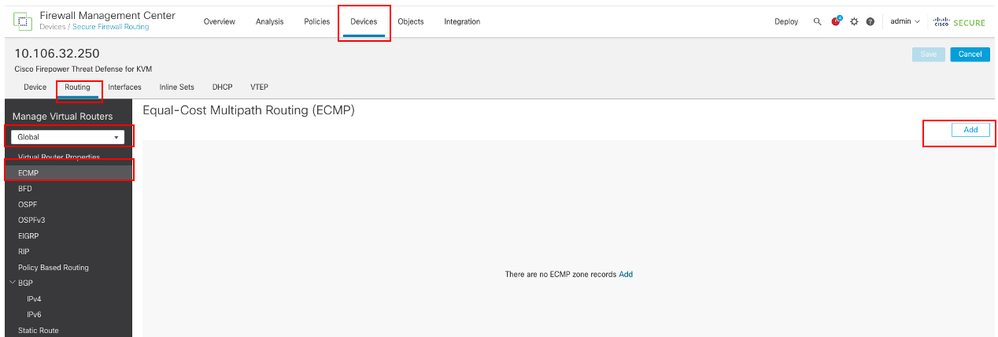 配置ECMP区域
配置ECMP区域
在Add ECMP窗口中:
- 设置ECMP区域的名称,在本示例中为Outside。
- 要关联接口,请选择Available Interfaces框下的接口,然后单击Add。在本示例中,Outside1和Outside2。
- Click OK.
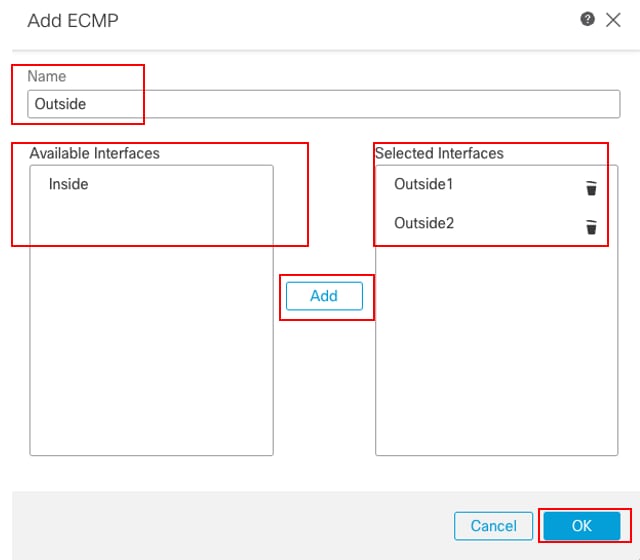 配置ECMP区域外部
配置ECMP区域外部
点击保存和部署配置。
第二步:配置IP SLA对象
导航到对象 > 对象管理,从对象类型列表中选择SLA监控器,点击添加SLA监控器,为第一个ISP网关添加新的SLA监控器。
 创建SLA监控器
创建SLA监控器
在New SLA Monitor Object窗口中:
- 为SLA监控器对象设置Name,在此例中为sla-outside1。
- 在SLA Monitor ID字段中输入SLA操作的ID编号。值范围为1到2147483647。您最多可以在设备上创建2000个SLA操作。每个ID号对于策略和设备配置必须是唯一的。在本示例1中。
- 在Monitored Address字段中输入由SLA操作监控的可用性的IP地址。在本示例中,10.1.1.2。
- Available Zones/Interfaces列表显示了区域和接口组。在Zones/Interfaces列表中,添加包含设备与管理站通信时所通过的接口的区域或接口组。要指定单个接口,需要为该接口创建区域或接口组。在本示例中,Outside1_Zone。
- Click Save.
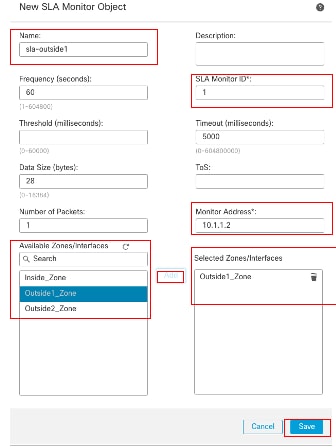 SLA对象Sla-outside1
SLA对象Sla-outside1
重复类似步骤,为第二个ISP网关创建另一个SLA监控器。
在New SLA Monitor Object窗口中:
- 为SLA监控器对象设置Name,在此例中为sla-outside2。
- 在SLA Monitor ID字段中输入SLA操作的ID编号。值范围为1到2147483647。您最多可以在设备上创建2000个SLA操作。每个ID号对于策略和设备配置必须是唯一的。在本示例2中。
- 在Monitored Address字段中输入由SLA操作监控的可用性的IP地址。在本示例中,10.1.2.2。
- Available Zones/Interfaces列表显示了区域和接口组。在Zones/Interfaces列表中,添加包含设备与管理站通信时所通过的接口的区域或接口组。要指定单个接口,需要为该接口创建区域或接口组。在本示例中,Outside2_Zone。
- Click Save.
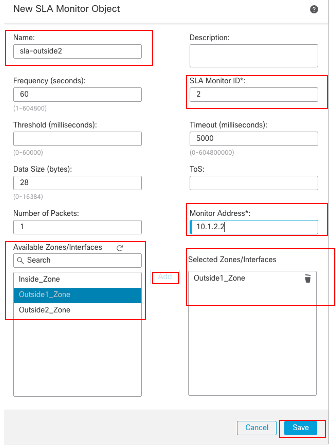 SLA对象Sla-outside2
SLA对象Sla-outside2
第三步:使用路由跟踪配置静态路由
导航到设备 > 设备管理,然后编辑威胁防御设备,点击路由,从虚拟路由器下拉列表中,选择您要配置静态路由的虚拟路由器。在本示例中为Global。
选择Static Route,单击Add Route将默认路由添加到第一个ISP网关。
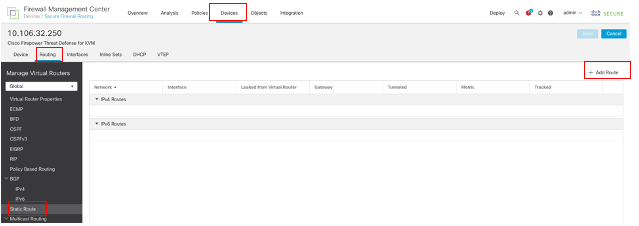 配置静态路由
配置静态路由
在Add Static Route Configuration窗口中:
- 根据您要添加的静态路由类型,单击IPv4或IPv6。在本示例中,IPv4。
- 选择此静态路由所应用的Interface。在本示例中,Outside1。
- 在Available Network列表中,选择目标网络。在本示例中,any-ipv4。
- 在Gateway或IPv6 Gateway字段中,输入或选择作为此路由的下一跳的网关路由器。可以提供IP地址或网络/主机对象。在本示例中,gw-outside1。
- 在Metric字段中,输入到达目标网络的跳数。有效值范围为1到255;默认值为1。在本示例1中。
- 要监控路由可用性,请在路由跟踪字段中输入或选择定义监控策略的SLA监控器对象的名称。在本示例中,sla-outside1。
- Click OK.
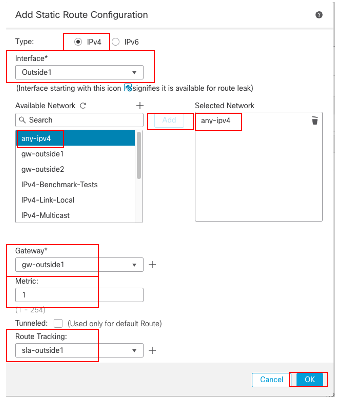 首先添加静态路由到ISP
首先添加静态路由到ISP
重复类似步骤,将默认路由添加到第二个ISP网关。在Add Static Route Configuration窗口中:
- 根据您要添加的静态路由类型,单击IPv4或IPv6。在本示例中,IPv4。
- 选择此静态路由所应用的Interface。在本例中为Outside2。
- 在Available Network列表中,选择目标网络。在本示例中,any-ipv4。
- 在Gateway或IPv6 Gateway字段中,输入或选择作为此路由的下一跳的网关路由器。可以提供IP地址或网络/主机对象。在本示例中,gw-outside2。
- 在Metric字段中,输入到达目标网络的跳数。有效值范围为1到255;默认值为1。确保指定与第一个路由相同的度量,在本示例中为1。
- 要监控路由可用性,请在路由跟踪字段中输入或选择定义监控策略的SLA监控器对象的名称。在本示例中,sla-outside2。
- Click OK.
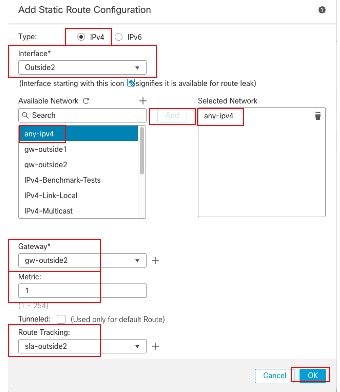 添加第二个ISP静态路由
添加第二个ISP静态路由
点击保存和部署配置。
验证
登录到FTD的CLI,运行命令 show zone 以检查有关ECMP流量区域的信息,包括属于每个区域的接口。
> show zone
Zone: Outside ecmp
Security-level: 0
Zone member(s): 2
Outside2 GigabitEthernet0/1
Outside1 GigabitEthernet0/0 运行show running-config route命令以检查运行配置,了解路由配置,在这种情况下,有两条具有路由跟踪的静态路由。
> show running-config route
route Outside1 0.0.0.0 0.0.0.0 10.1.1.2 1 track 1
route Outside2 0.0.0.0 0.0.0.0 10.1.2.2 1 track 2 运行show route命令以检查路由表,如果有两个默认路由是通过接口outside1和outside2且开销相等,流量可以在两个ISP电路之间分配。
> show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF, BI - BGP InterVRF
Gateway of last resort is 10.1.2.2 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 10.1.2.2, Outside2
[1/0] via 10.1.1.2, Outside1
C 10.1.1.0 255.255.255.0 is directly connected, Outside1
L 10.1.1.1 255.255.255.255 is directly connected, Outside1
C 10.1.2.0 255.255.255.0 is directly connected, Outside2
L 10.1.2.1 255.255.255.255 is directly connected, Outside2
C 10.1.3.0 255.255.255.0 is directly connected, Inside
L 10.1.3.1 255.255.255.255 is directly connected, Inside
运行命令 show sla monitor configuration 以检查SLA监控器的配置。
> show sla monitor configuration
SA Agent, Infrastructure Engine-II
Entry number: 1
Owner:
Tag:
Type of operation to perform: echo
Target address: 10.1.1.2
Interface: Outside1
Number of packets: 1
Request size (ARR data portion): 28
Operation timeout (milliseconds): 5000
Type Of Service parameters: 0x0
Verify data: No
Operation frequency (seconds): 60
Next Scheduled Start Time: Start Time already passed
Group Scheduled : FALSE
Life (seconds): Forever
Entry Ageout (seconds): never
Recurring (Starting Everyday): FALSE
Status of entry (SNMP RowStatus): Active
Enhanced History:
Entry number: 2
Owner:
Tag:
Type of operation to perform: echo
Target address: 10.1.2.2
Interface: Outside2
Number of packets: 1
Request size (ARR data portion): 28
Operation timeout (milliseconds): 5000
Type Of Service parameters: 0x0
Verify data: No
Operation frequency (seconds): 60
Next Scheduled Start Time: Start Time already passed
Group Scheduled : FALSE
Life (seconds): Forever
Entry Ageout (seconds): never
Recurring (Starting Everyday): FALSE
Status of entry (SNMP RowStatus): Active
Enhanced History:
运行命令show sla monitor operational-state以确认SLA监控器的状态。在这种情况下,您可在命令输出中找到“Timeout occurred: FALSE”,表明发送到网关的ICMP回应正在应答,因此通过目标接口的默认路由处于活动状态并已安装在路由表中。
> show sla monitor operational-state
Entry number: 1
Modification time: 09:31:28.785 UTC Thu Feb 15 2024
Number of Octets Used by this Entry: 2056
Number of operations attempted: 82
Number of operations skipped: 0
Current seconds left in Life: Forever
Operational state of entry: Active
Last time this entry was reset: Never
Connection loss occurred: FALSE
Timeout occurred: FALSE
Over thresholds occurred: FALSE
Latest RTT (milliseconds): 1
Latest operation start time: 10:52:28.785 UTC Thu Feb 15 2024
Latest operation return code: OK
RTT Values:
RTTAvg: 1 RTTMin: 1 RTTMax: 1
NumOfRTT: 1 RTTSum: 1 RTTSum2: 1
Entry number: 2
Modification time: 09:31:28.785 UTC Thu Feb 15 2024
Number of Octets Used by this Entry: 2056
Number of operations attempted: 82
Number of operations skipped: 0
Current seconds left in Life: Forever
Operational state of entry: Active
Last time this entry was reset: Never
Connection loss occurred: FALSE
Timeout occurred: FALSE
Over thresholds occurred: FALSE
Latest RTT (milliseconds): 1
Latest operation start time: 10:52:28.785 UTC Thu Feb 15 2024
Latest operation return code: OK
RTT Values:
RTTAvg: 1 RTTMin: 1 RTTMax: 1
NumOfRTT: 1 RTTSum: 1 RTTSum2: 1
负载平衡
通过FTD的初始流量,用于检验ECMP是否在ECMP区域中的网关之间对流量进行负载均衡。在这种情况下,启动从Inside-Host1 (10.1.3.2)和Inside-Host2 (10.1.3.4)到Internet-Host (10.1.5.2)的telnet连接,运行 show conn 命令以确认流量在两个ISP链路之间实现负载均衡,Inside-Host1 (10.1.3.2)通过interface outside1,Inside-Host2 (10.1.3.4)通过interface outside2。
> show conn
2 in use, 3 most used
Inspect Snort:
preserve-connection: 2 enabled, 0 in effect, 2 most enabled, 0 most in effect
TCP Inside 10.1.3.2:46069 Outside1 10.1.5.2:23, idle 0:00:24, bytes 1329, flags UIO N1
TCP Inside 10.1.3.4:61915 Outside2 10.1.5.2:23, idle 0:00:04, bytes 1329, flags UIO N1

注:根据散列源和目标IP地址、传入接口、协议、源和目标端口的算法,在指定网关之间对流量进行负载均衡。运行测试时,由于使用散列算法,可以模拟的流量路由到同一网关,这是预期的,更改6个元组(源IP、目标IP、传入接口、协议、源端口、目标端口)中的任何值,以更改散列结果。
丢失的路由
在这种情况下,如果通向第一个ISP网关的链路关闭,请关闭第一个网关路由器进行模拟。如果FTD在SLA监控器对象中指定的阈值计时器内没有收到来自第一个ISP网关的回应应答,则认为主机无法访问,并标记为关闭。通向第一个网关的跟踪路由也会从路由表中删除。
运行命令show sla monitor operational-state以确认SLA监控器的当前状态。在这种情况下,您可以在命令输出中找到“Timeout occurred: True”,这表示发往第一个ISP网关的ICMP回应没有响应。
> show sla monitor operational-state
Entry number: 1
Modification time: 09:31:28.783 UTC Thu Feb 15 2024
Number of Octets Used by this Entry: 2056
Number of operations attempted: 104
Number of operations skipped: 0
Current seconds left in Life: Forever
Operational state of entry: Active
Last time this entry was reset: Never
Connection loss occurred: FALSE
Timeout occurred: TRUE
Over thresholds occurred: FALSE
Latest RTT (milliseconds): NoConnection/Busy/Timeout
Latest operation start time: 11:14:28.813 UTC Thu Feb 15 2024
Latest operation return code: Timeout
RTT Values:
RTTAvg: 0 RTTMin: 0 RTTMax: 0
NumOfRTT: 0 RTTSum: 0 RTTSum2: 0
Entry number: 2
Modification time: 09:31:28.783 UTC Thu Feb 15 2024
Number of Octets Used by this Entry: 2056
Number of operations attempted: 104
Number of operations skipped: 0
Current seconds left in Life: Forever
Operational state of entry: Active
Last time this entry was reset: Never
Connection loss occurred: FALSE
Timeout occurred: FALSE
Over thresholds occurred: FALSE
Latest RTT (milliseconds): 1
Latest operation start time: 11:14:28.813 UTC Thu Feb 15 2024
Latest operation return code: OK
RTT Values:
RTTAvg: 1 RTTMin: 1 RTTMax: 1
NumOfRTT: 1 RTTSum: 1 RTTSum2: 1
运行 show route 命令以检查当前路由表,通过接口outside1到第一个ISP网关的路由被删除,通过接口outside2到第二个ISP网关只有一个活动默认路由。
> show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF, BI - BGP InterVRF
Gateway of last resort is 10.1.2.2 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 10.1.2.2, Outside2
C 10.1.1.0 255.255.255.0 is directly connected, Outside1
L 10.1.1.1 255.255.255.255 is directly connected, Outside1
C 10.1.2.0 255.255.255.0 is directly connected, Outside2
L 10.1.2.1 255.255.255.255 is directly connected, Outside2
C 10.1.3.0 255.255.255.0 is directly connected, Inside
L 10.1.3.1 255.255.255.255 is directly connected, Inside
运行show conn命令,您会发现两个连接仍然运行。Telnet会话在Inside-Host1 (10.1.3.2)和Inside-Host2 (10.1.3.4)上也处于活动状态,没有出现任何中断。
> show conn
2 in use, 3 most used
Inspect Snort:
preserve-connection: 2 enabled, 0 in effect, 2 most enabled, 0 most in effect
TCP Inside 10.1.3.2:46069 Outside1 10.1.5.2:23, idle 0:00:22, bytes 1329, flags UIO N1
TCP Inside 10.1.3.4:61915 Outside2 10.1.5.2:23, idle 0:00:02, bytes 1329, flags UIO N1

注意:在show conn的输出中,您会注意到,虽然通过接口outside1的默认路由已从路由表中删除,但来自Inside-Host1 (10.1.3.2)的telnet会话仍通过接口outside1。这是预期的,而且根据设计,实际流量流经接口outside2。如果从Inside-Host1 (10.1.3.2)发起到Internet-Host (10.1.5.2)的新连接,则可以发现所有流量都通过接口outside2。
故障排除
故障排除 要验证路由表更改,请运行命令debug ip routing。
在本例中,当通向第一个ISP网关的链路断开时,通过接口outside1的路由将从路由表中删除。
> debug ip routing
IP routing debugging is on
RT: ip_route_delete 0.0.0.0 0.0.0.0 via 10.1.1.2, Outside1
ha_cluster_synced 0 routetype 0
RT: del 0.0.0.0 via 10.1.1.2, static metric [1/0]NP-route: Delete-Output 0.0.0.0/0 hop_count:1 , via 0.0.0.0, Outside1
RT(mgmt-only): NP-route: Update-Output 0.0.0.0/0 hop_count:1 , via 10.1.2.2, Outside2
NP-route: Update-Input 0.0.0.0/0 hop_count:1 Distance:1 Flags:0X0 , via 10.1.2.2, Outside2
运行show route命令以确认当前路由表。
> show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF, BI - BGP InterVRF
Gateway of last resort is 10.1.2.2 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 10.1.2.2, Outside2
C 10.1.1.0 255.255.255.0 is directly connected, Outside1
L 10.1.1.1 255.255.255.255 is directly connected, Outside1
C 10.1.2.0 255.255.255.0 is directly connected, Outside2
L 10.1.2.1 255.255.255.255 is directly connected, Outside2
C 10.1.3.0 255.255.255.0 is directly connected, Inside
L 10.1.3.1 255.255.255.255 is directly connected, Inside
当通向第一个ISP网关的链路重新接通时,通过接口outside1的路由将添加回路由表。
> debug ip routing
IP routing debugging is on
NP-route: Update-Output 0.0.0.0/0 hop_count:1 , via 10.1.2.2, Outside2
NP-route: Update-Output 0.0.0.0/0 hop_count:1 , via 10.1.1.2, Outside2
NP-route: Update-Input 0.0.0.0/0 hop_count:2 Distance:1 Flags:0X0 , via 10.1.2.2, Outside2
via 10.1.1.2, Outside1
运行show route命令以确认当前路由表。
> show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF, BI - BGP InterVRF
Gateway of last resort is 10.1.2.2 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 10.1.2.2, Outside2
[1/0] via 10.1.1.2, Outside1
C 10.1.1.0 255.255.255.0 is directly connected, Outside1
L 10.1.1.1 255.255.255.255 is directly connected, Outside1
C 10.1.2.0 255.255.255.0 is directly connected, Outside2
L 10.1.2.1 255.255.255.255 is directly connected, Outside2
C 10.1.3.0 255.255.255.0 is directly connected, Inside
L 10.1.3.1 255.255.255.255 is directly connected, Inside
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
16-Feb-2024 |
初始版本 |
 反馈
反馈