了解安全Web设备中的数据包流
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
简介
本文档介绍代理配置网络中的网络流量,特别侧重于安全Web设备(SWA)。
先决条件
要求
Cisco 建议您了解以下主题:
- 基本TCP/IP概念。
- 代理设置的基本知识。
- 代理环境中使用的身份验证机制的基本知识。
本文使用的缩写为:
TCP:传输控制协议
UDP:用户数据报协议
IP:Internet协议
GRE:通用路由封装
HTTP:超文本传输协议。
HTTPS:安全超文本传输协议。
URL:统一资源定位符
TLS:传输层安全
使用的组件
本文档不限于特定的软件和硬件版本。
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
代理部署的不同类型
TLS握手
当客户端和服务器通过Internet通信时,HTTPS中的TLS握手可提供安全连接。该过程维护两个正在通信的应用程序之间的隐私性和数据完整性。它通过一系列步骤运行,其中客户端和服务器就所有后续传输的加密标准和代码达成一致。握手的目的是阻止第三方的任何未经授权的访问或操纵。它还对通信方的身份进行身份验证以消除模拟。此过程在HTTPS中至关重要,因为它可确保数据在传输过程中保持安全。
以下是TLS握手的步骤:
-
客户端Hello:客户端使用Hello消息启动握手过程。此消息包含客户端TLS版本、支持的密码套件和称为“client random”的随机字节字符串。
-
服务器Hello:服务器以Hello消息做出响应。此消息包括服务器选择的TLS版本、所选的密码套件、称为“服务器随机”的随机字节字符串以及服务器数字证书。如有必要,服务器还会请求客户端数字证书进行相互身份验证。
-
客户端验证服务器证书:客户端向颁发证书的证书颁发机构检查服务器数字证书。这可以确保客户端正在与合法服务器通信。
-
Pre-master Secret:客户端发送一个称为“pre-master secret”的随机字节字符串,该字符串有助于创建会话密钥。客户端使用服务器公钥对此预主密钥进行加密,因此只有服务器才能使用其私钥对其进行解密。
-
主密钥:客户端和服务器都使用预主密钥和来自问候消息的随机字节字符串来独立计算相同的“主密钥”。 此共享密钥是生成会话密钥的基础。
-
Client Finished:客户端发送一个“Finished”消息(使用会话密钥加密),以指示握手的客户端部分完成。
-
Server Finished:服务器发送“Finished”消息(也使用会话密钥加密),以发出握手的服务器部分完成的信号。
HTTP响应代码
1xx :信息
| 代码 | 详细信息 |
| 100继续 |
通常在ICAP协议中看到。这是信息性响应,告知客户端可以继续发送数据。对于ICAP服务(例如病毒扫描),服务器仅希望看到前x个字节。当扫描完第一组字节并且未检测到病毒时,它会发送100 Continue以告知客户端发送对象的其余部分。 |
2xx:成功
| 代码 | 详细信息 |
| 200正常 |
最常见的响应代码。这表示请求成功而没有任何问题。 |
3xx:重定向
| 代码 | 详细信息 |
| 301永久重定向 |
这是永久重定向,当您重定向到www子域时,可以看到此代码。 |
| 302临时重定向 |
这是临时重定向。指示客户端对Location:标头中指定的对象发出新请求。 |
| 304未修改 |
这是对GIMS (GET If-modified-since)的响应。这实际上是一个包含报头If-modified-since: <date>的标准HTTP GET。此标头告诉服务器客户端在本地缓存中有一个请求对象的副本,其中包括该对象的读取日期。如果自该日期以来对象已被修改,则服务器将以200 OK和对象的新副本做出响应。如果自获取日期以来对象未更改,服务器将发回304 Not Modified响应。 |
| 307身份验证重定向 |
这在透明代理部署中最为明显,当代理服务器配置为对请求进行身份验证并将请求重定向到另一个URL以对用户进行身份验证时, |
4xx代码:客户端错误
| 代码 | 详细信息 |
| 400错误请求 |
这表明HTTP请求存在问题,因为它不符合正确的语法。可能的原因可能包括同一行上的多个报头、报头中的空格或URI中缺少HTTP/1.1等等。有关正确的语法,请参阅RFC 2616。 |
| 401未授权 需要Web服务器身份验证 |
访问请求的对象需要身份验证。401代码用于与目标Web服务器进行身份验证。当SWA以透明模式运行并在代理上启用身份验证时,它会将一个401返回给客户端,因为设备将自己显示为OCS(源内容服务器)。 “www-authenticate:”HTTP响应报头中详细介绍了可以使用的身份验证方法。这会通知客户端服务器是否请求NTLM、基本或其他形式的身份验证。 |
| 403被拒绝 |
客户端无法访问请求的对象。导致服务器拒绝对象访问的原因有很多。服务器通常在HTTP数据或HTML响应中提供原因说明。 |
| 404未找到 |
服务器上不存在请求的对象。 |
| 407需要代理身份验证 |
这与401相同,不同之处在于它专门用于代理而不是OCS的身份验证。仅当请求已明确发送到代理时,才会发送此消息。 当SWA配置为透明代理时,无法将407发送到客户端,因为客户端不知道该代理存在。如果出现这种情况,客户端很可能FIN或RST为TCP套接字。 |
5xx:服务器错误
| 代码 | 详细信息 |
| 501内部服务器错误 |
一般Web服务器故障。 |
| 502错误的网关 |
当充当网关或代理的服务器从入站服务器收到无效响应时发生。它表示网关收到了来自上游或源服务器的不当响应。 |
| 503服务不可用 |
表示由于临时过载或计划的维护,服务器当前无法处理该请求。这意味着服务器暂时停止服务,但一段时间后可以再次使用。 |
| 504网关超时 |
表示客户端或代理未从它尝试访问的Web服务器收到及时响应,以加载网页或满足浏览器的另一个请求。这通常意味着上游服务器发生故障。 |
显式部署
此处....
无身份验证的显式部署中的HTTP流量
客户端和SWA
网络流量在客户端的IP地址和SWA代理接口的IP地址之间传输(通常是P1接口,但可能是P2或管理接口,具体取决于代理配置)。
来自客户端的流量指向TCP端口80或3128到SWA(默认SWA代理端口为TCP 80和3128,在本例中使用端口3128)
- TCP握手。
- 从客户端获取HTTP(目标IP = SWA IP ,目标端口= 3128)
- 来自代理的HTTP响应(源IP = SWA)
- 数据传输
- TCP连接终止(四次握手)
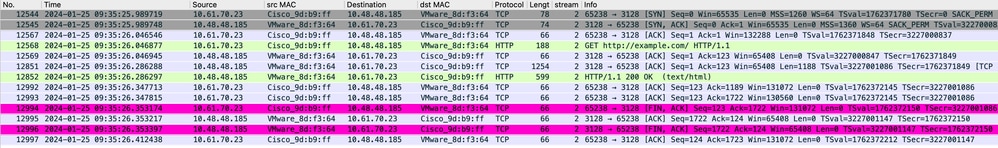 Image-Client to SWA, HTTP Explicit mode
Image-Client to SWA, HTTP Explicit mode
SWA和Web服务器
网络流量发生在代理的IP地址和Web服务器的IP地址之间。
来自SWA的流量发往TCP端口80,且来自随机端口(非代理端口)
- TCP握手。
- 从代理获取HTTP(目标IP = Web服务器,目标端口= 80)
- 来自Web服务器的HTTP响应(源IP =代理服务器)
- 数据传输
- TCP连接终止(四次握手)
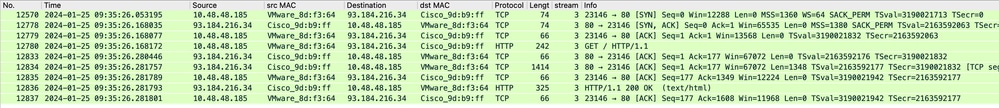 图像- HTTP-SWA到Web服务器-显式-无缓存
图像- HTTP-SWA到Web服务器-显式-无缓存
以下是来自客户端的HTTP Get示例
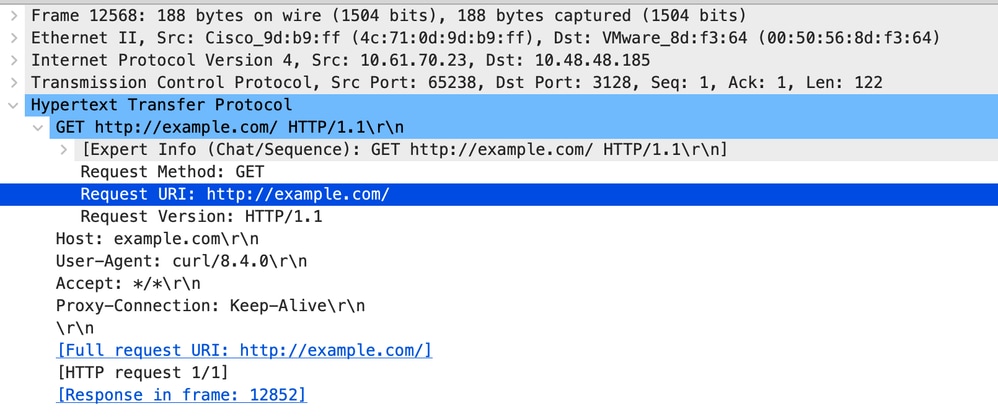 Image - Client to SWA HTTP GET- Explicit
Image - Client to SWA HTTP GET- Explicit
这表示从客户端到SWA,然后到Web服务器,最后返回客户端的整个流量流。
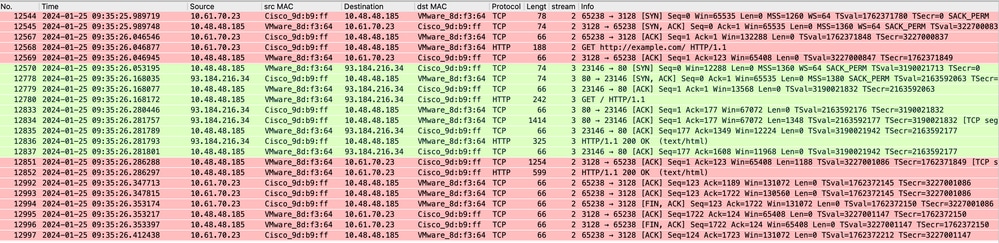 映像-所有流量HTTP显式-无缓存
映像-所有流量HTTP显式-无缓存

注意:每个数据流都有不同的颜色;从客户端到SWA的流为一种颜色,从SWA到Web服务器的流为另一种颜色。
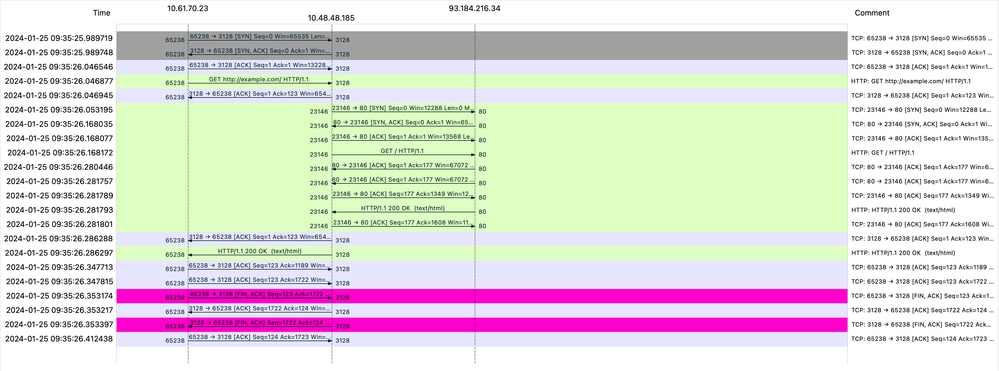 图像-流量HTTP显式-无缓存
图像-流量HTTP显式-无缓存
以下是访问日志的示例:
1706172876.686 224 10.61.70.23 TCP_MISS/200 1721 GET http://www.example.com/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,1,"-",0,0,0,1,"-",-,-,-,"-",1,-,"-","-",-,-,"IW_ref",-,"Unknown","Reference","-","Unknown","Unknown","-","-",61.46,0,-,"Unknown","-",1,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 10, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 108, Request Header = 0, Request to Server = 0, 1st byte to client = 3, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 106, Response header = 0, Server response = 1, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 2, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 1, AMP response = 0, AMP total = 0; Latency = 4; "25/Jan/2024:09:54:36 +0100" ][Client Port = 65238, Server IP = 10.184.216.34, Server Port = 80]包含缓存数据的流量
这表示当数据在SWA缓存中时,从客户端到SWA的整个流量。
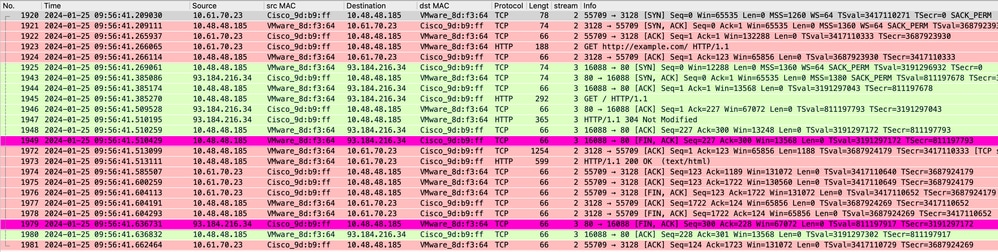 图像- HTTP显式缓存数据
图像- HTTP显式缓存数据

注意:正如您看到的,Web服务器返回HTTP响应304:缓存未修改。(在本示例中,数据包编号为1947)
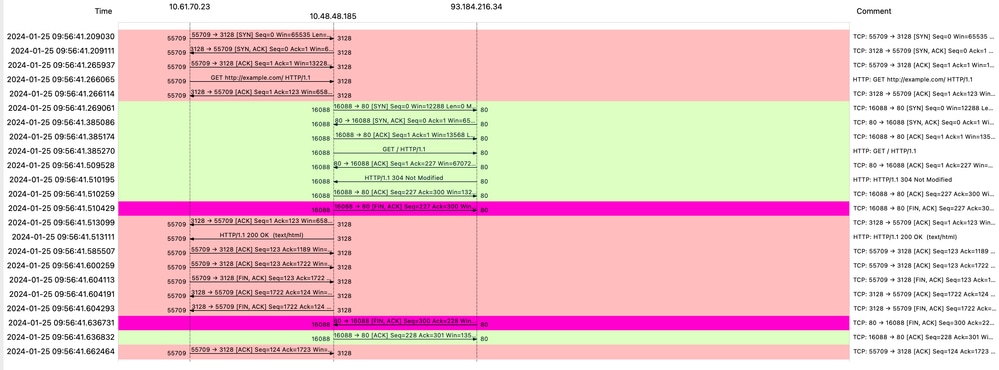 图像-带缓存的流HTTP显式
图像-带缓存的流HTTP显式
以下是HTTP响应304的示例
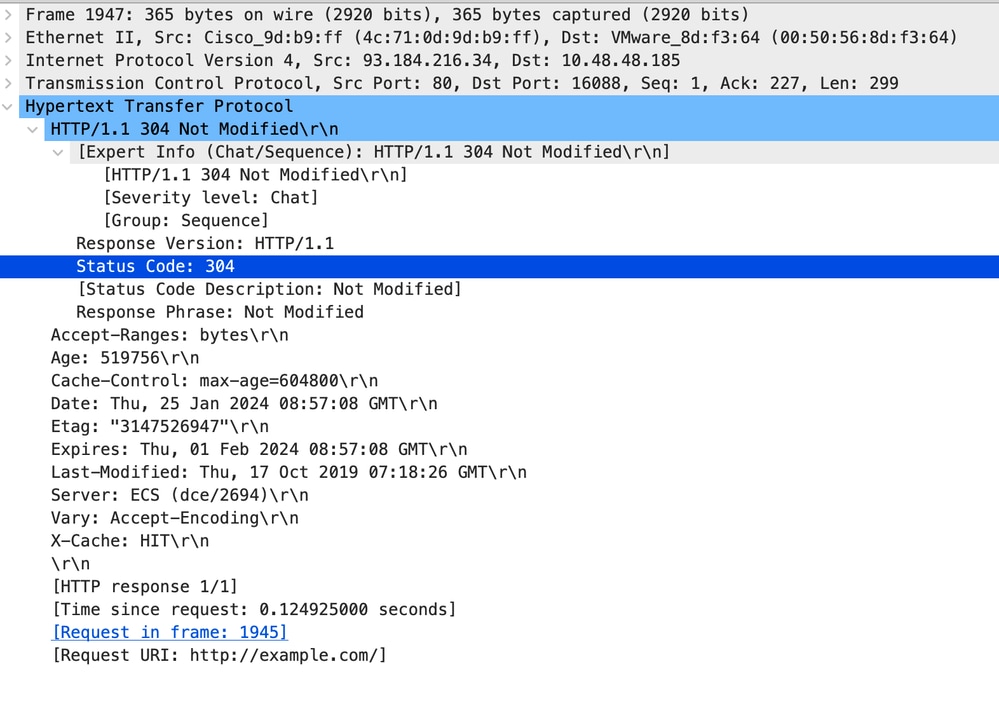 图像- HTTP显式304响应
图像- HTTP显式304响应
以下是访问日志的示例:
1706173001.489 235 10.61.70.23 TCP_REFRESH_HIT/200 1721 GET http://www.example.com/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,1,"-",0,0,0,1,"-",-,-,-,"-",1,-,"-","-",-,-,"IW_ref",-,"Unknown","Reference","-","Unknown","Unknown","-","-",58.59,0,-,"Unknown","-",1,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 150, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 110, Request Header = 0, Request to Server = 0, 1st byte to client = 2, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 119, Response header = 0, Server response = 0, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 1, AMP response = 0, AMP total = 0; Latency = 1; "25/Jan/2024:09:56:41 +0100" ][Client Port = 55709, Server IP = 10.184.216.34, Server Port = 80]无身份验证的显式部署中的HTTPs流量
客户端和SWA
网络流量在客户端的IP地址和SWA代理接口的IP地址之间传输(通常是P1接口,但可能是P2或管理接口,具体取决于代理配置)。
来自客户端的流量指向TCP端口80或3128到SWA(默认SWA代理端口为TCP 80和3128,在本例中使用端口3128)
- TCP握手。
- 来自客户端的HTTP CONNECT(目标IP = SWA,目标端口= 3128)
- 来自代理的HTTP响应(源IP = SWA)
- 使用URL的SNI的客户端Hello(源IP =客户端)
- Server Hello ( Source IP = SWA )
- 服务器密钥交换(源IP = SWA)
- 客户端密钥交换(源IP =客户端)
- 数据传输
- TCP连接终止(四次握手)
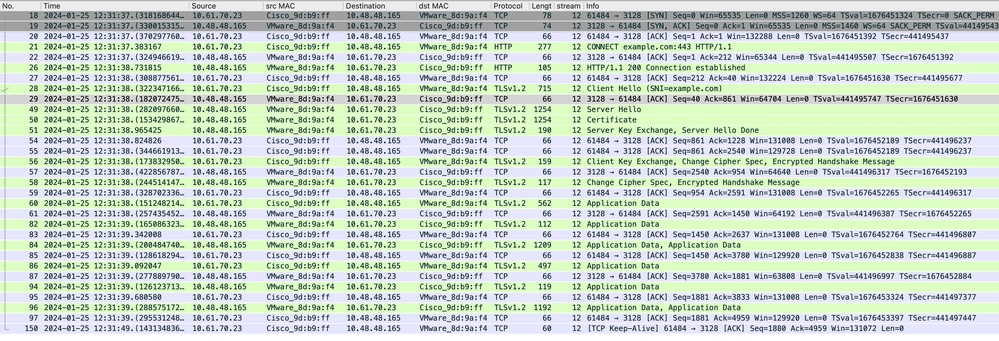 映像- HTTPS客户端到SWA显式-无缓存
映像- HTTPS客户端到SWA显式-无缓存
以下是客户端到SWA的客户端Hello的详细信息,如服务器名称指示(SNI)所示,Web服务器的URL在本示例中为www.example.com,并且客户端通告17个密码套件:
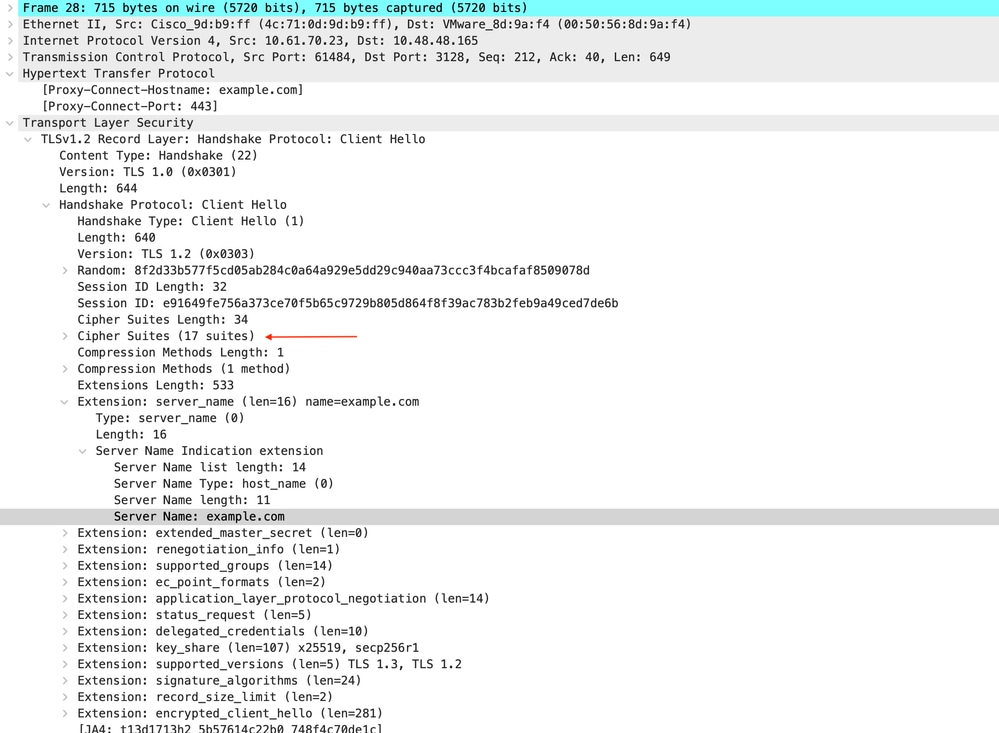 映像- HTTPS客户端hello -显式- SWA的客户端
映像- HTTPS客户端hello -显式- SWA的客户端

提示:您可以在Wireshark中使用此过滤器搜索URL/SNI: tls.handshake.extensions_server_name == "www.example.com"
以下是SWA发送到客户端的证书示例
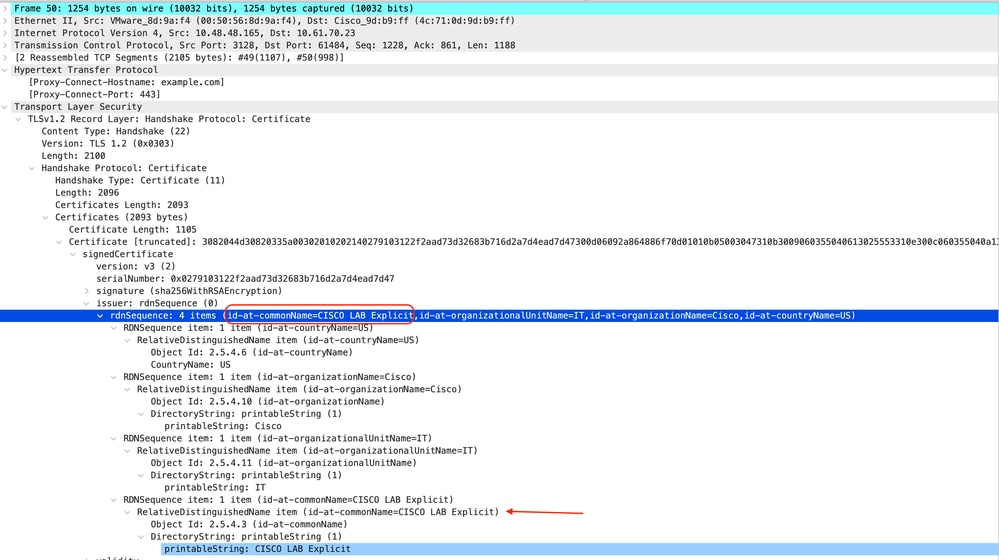 映像- HTTPS证书-显式- SWA到客户端
映像- HTTPS证书-显式- SWA到客户端
SWA和Web服务器
网络流量发生在代理的IP地址和Web服务器的IP地址之间。
来自SWA的流量指向TCP端口443(不是代理端口)
- TCP握手。
- 客户端Hello(目标IP = Web服务器,目标端口= 443)
- Server Hello ( Source IP = Web server )
- 数据传输
- TCP连接终止(四次握手)
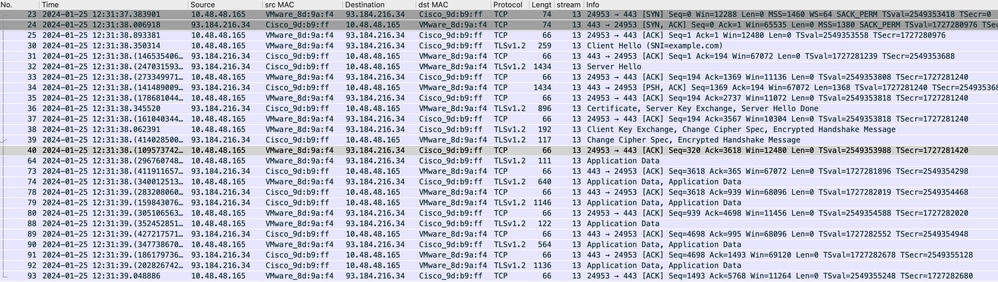 映像- HTTPS -显式- SWA到Web服务器
映像- HTTPS -显式- SWA到Web服务器
以下是从SWA到Web服务器的客户端Hello的详细信息,因为您可以看到SWA通告了12个密码套件:
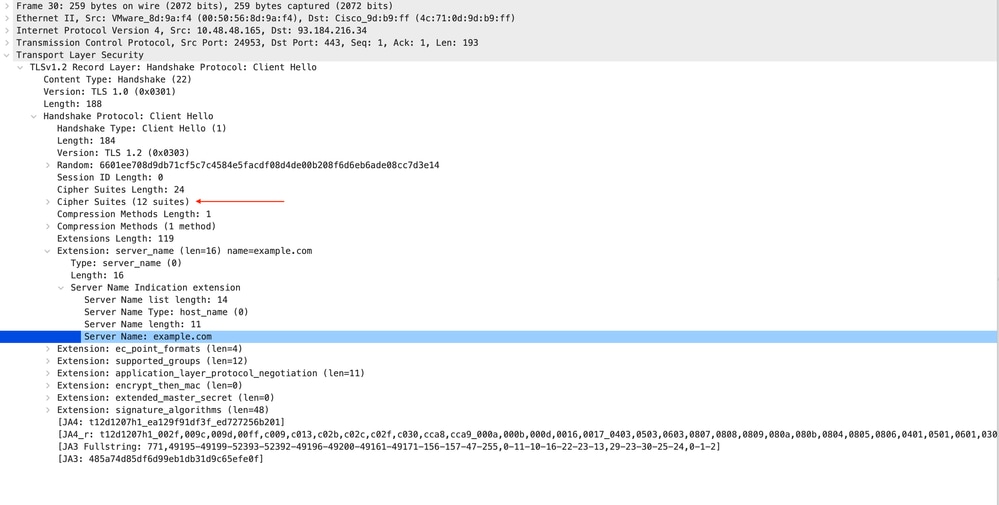 图像- HTTPS客户端Hello - SWA到Web服务器-无缓存
图像- HTTPS客户端Hello - SWA到Web服务器-无缓存

注意:此处观察的密码套件与从客户端到SWA的客户端Hello中的密码套件不同,因为配置为解密此流量的SWA使用其自己的密码。

提示:在从SWA到Web服务器的服务器密钥交换中,会显示Web服务器证书。但是,如果上游代理找到SWA的配置,则显示其证书而不是Web服务器证书。
以下是来自客户端的HTTP CONNECT示例
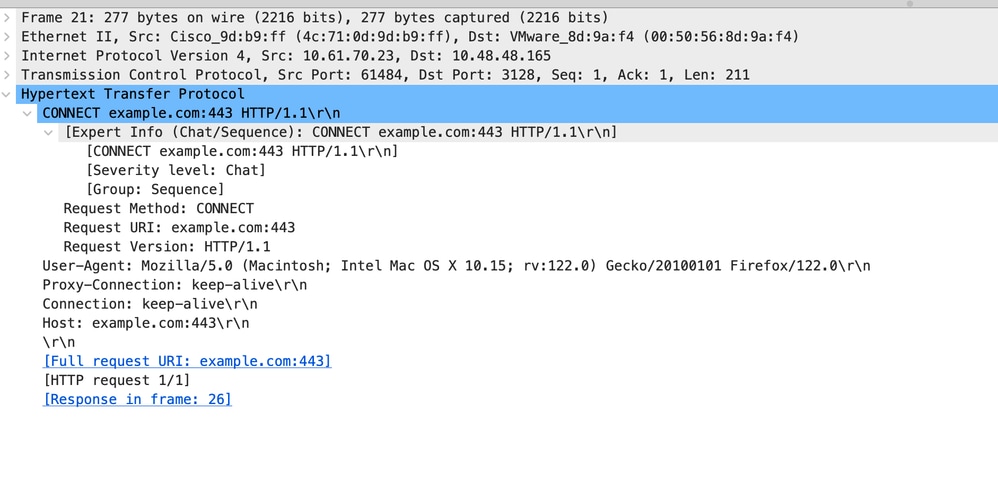 图像-客户端HTTP连接
图像-客户端HTTP连接
这表示从客户端到SWA,然后到Web服务器,最后返回客户端的整个流量流。
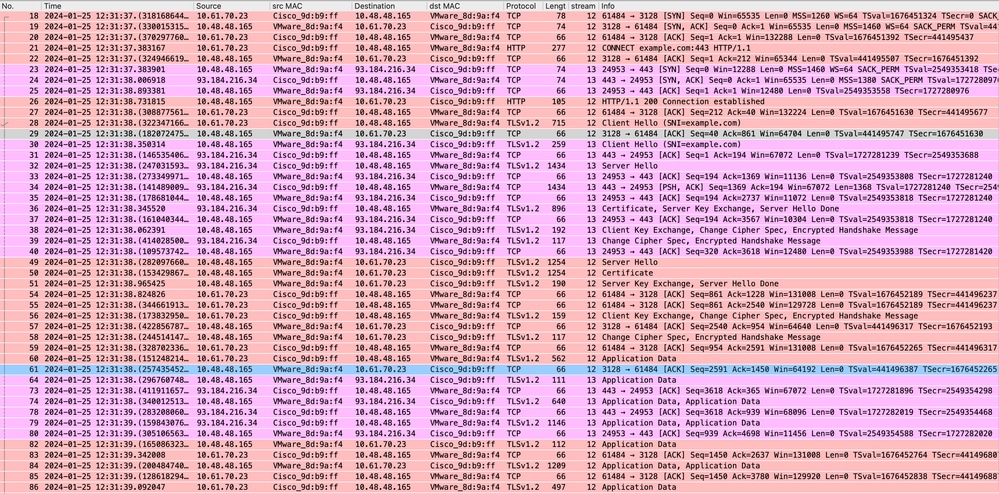 映像-完整HTTPS显式-无缓存
映像-完整HTTPS显式-无缓存

注意:每个数据流都有不同的颜色;从客户端到SWA的流为一种颜色,从SWA到Web服务器的流为另一种颜色。
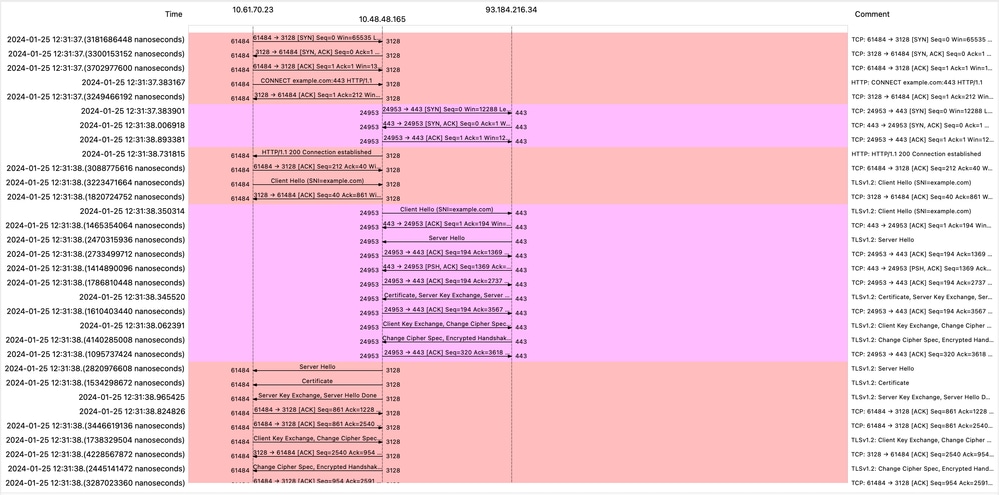 映像- HTTPS流-显式-无缓存
映像- HTTPS流-显式-无缓存
以下是访问日志的示例:
1706174571.215 582 10.61.70.23 TCP_MISS_SSL/200 39 CONNECT tunnel://www.example.com:443/ - DIRECT/www.example.com - DECRYPT_WEBCAT_7-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"IW_ref",-,"-","Reference","-","Unknown","Unknown","-","-",0.54,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 1600, User Agent = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 113, Request Header = 0, Request to Server = 0, 1st byte to client = 113, Response Header = 0, Client Body = 79 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 0, Response header = 0, Server response = 344, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 0, AMP total = 0; Latency = 0; "25/Jan/2024:10:22:51 +0100" ][Client Port = 24953, Server IP = 10.184.216.34, Server Port = 443]
1706174571.486 270 10.61.70.23 TCP_MISS_SSL/200 1106 GET https://www.example.com:443/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,1,"-",0,0,0,1,"-",-,-,-,"-",1,-,"-","-",-,-,"IW_ref",-,"Unknown","Reference","-","Unknown","Unknown","-","-",32.77,0,-,"Unknown","-",1,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 1630, User Agent = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 3, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 264, Response header = 0, Server response = 2, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 1, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 1, AMP response = 0, AMP total = 0; Latency = 2; "25/Jan/2024:10:22:51 +0100" ][Client Port = 24953, Server IP = 10.184.216.34, Server Port = 443]
注意:正如您在HTTPS流量的透明部署中看到的,Accesslogs中有2行,第一行是流量被加密的时间,您可以看到CONNECT,并且Web服务器的URL以tunnel://开头。如果在SWA中启用解密,则第二行包含GET,整个URL以HTTPS开头,这意味着流量已解密。
直通HTTPS流量
如果您将SWA配置为通过流量,则总流量如下:
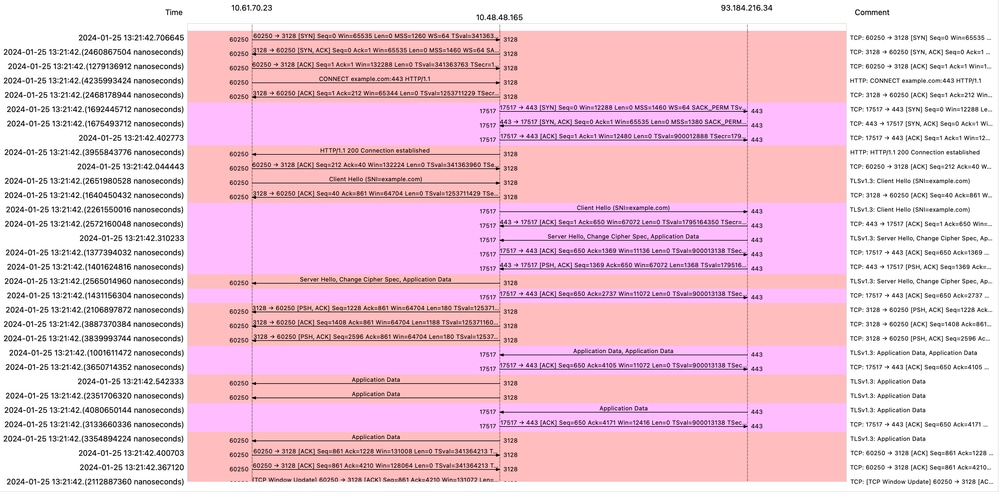 图像- HTTPS直通-显式-流
图像- HTTPS直通-显式-流
以下是从SWA到Web服务器的客户端Hello的示例:
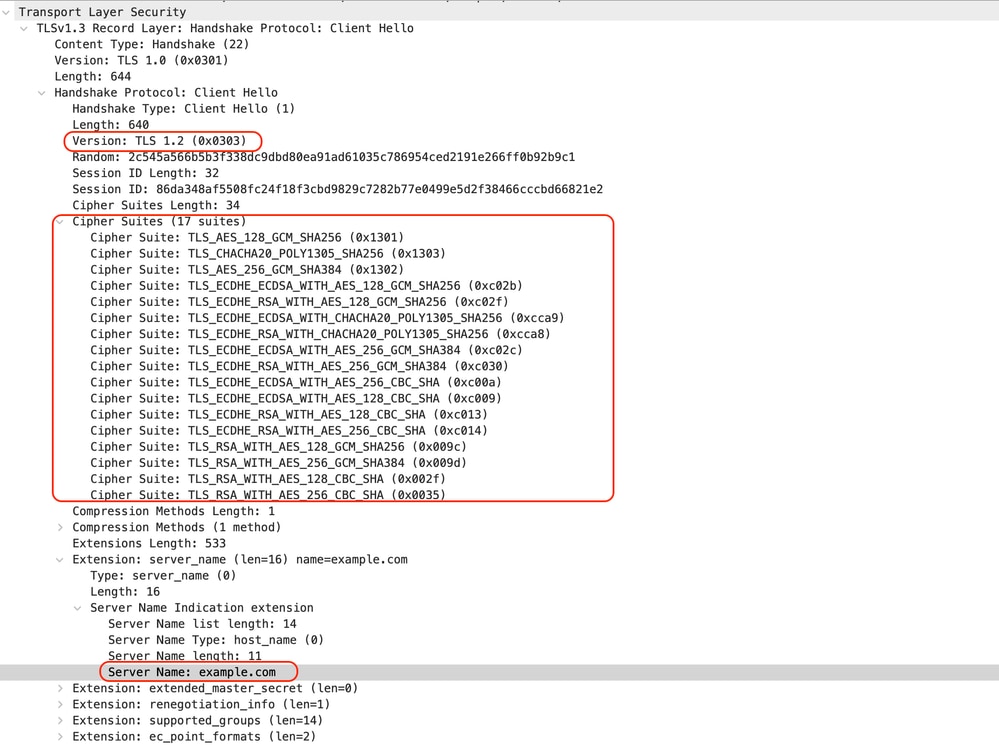 图像- HTTPS直通-显式- SWA到Web服务器-客户端hello
图像- HTTPS直通-显式- SWA到Web服务器-客户端hello
与从客户端到SWA的客户端Hello相同:
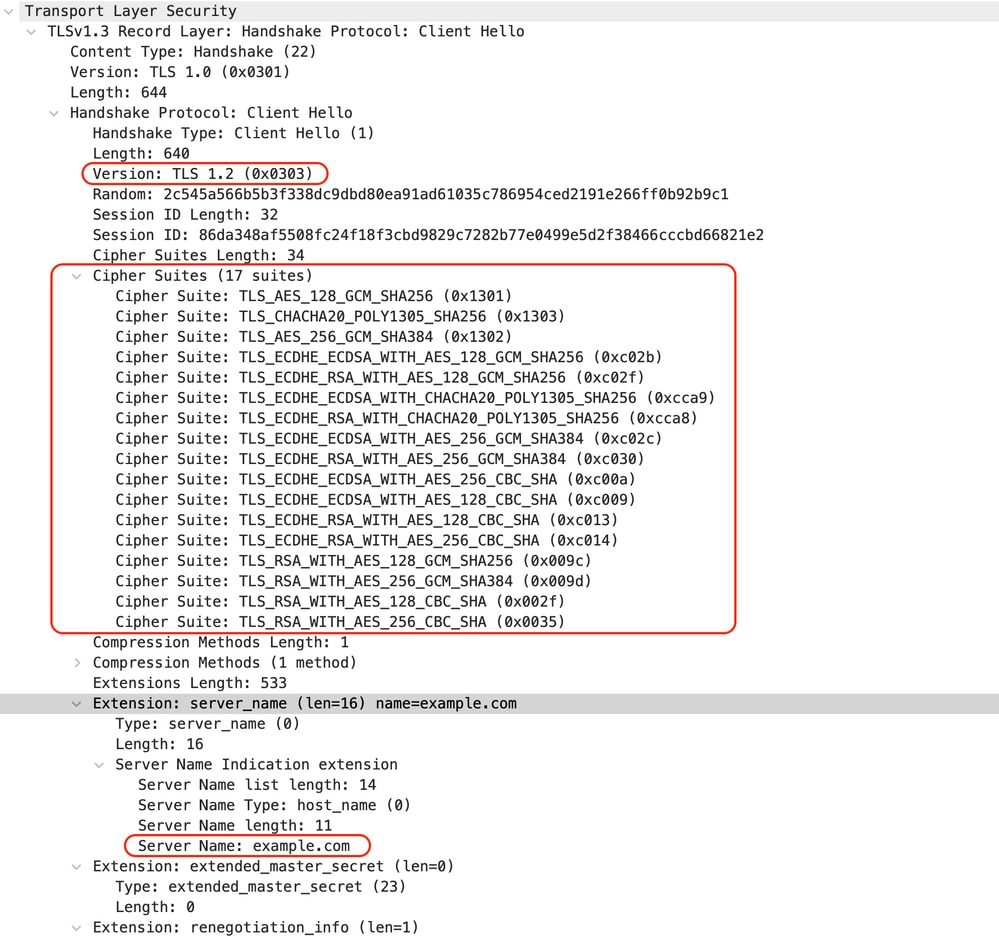 映像- HTTPS直通-显式-客户端到SWA -客户端呼叫
映像- HTTPS直通-显式-客户端到SWA -客户端呼叫
以下是访问日志示例:
1706185288.920 53395 10.61.70.23 TCP_MISS/200 6549 CONNECT tunnel://www.example.com:443/ - DIRECT/www.example.com - PASSTHRU_WEBCAT_7-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"IW_ref",3.7,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"IW_ref",-,"-","Reference","-","Unknown","Unknown","-","-",0.98,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 210, User Agent = "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 233, Request Header = 0, Request to Server = 0, 1st byte to client = 119, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 0, Client Body = 0, 1st response byte = 0, Response header = 0, Server response = 436, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 22, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 0, AMP total = 0; Latency = 22; "25/Jan/2024:13:21:28 +0100" ][Client Port = 59939, Server IP = 10.184.216.34, Server Port = 443]
注意:正如您看到的,它只是单行,操作为PASSTHRU。
透明部署
无身份验证的透明部署中的HTTP流量
客户端和SWA
网络流量在客户端的IP地址和Web服务器的IP地址之间传输。
来自客户端的流量发往TCP端口80(不是代理端口)
- TCP握手。
- 从客户端获取HTTP(目标IP = Web服务器,目标端口= 80)
- 来自代理的HTTP响应(源IP = Web服务器)
- 数据传输
- TCP连接终止(四次握手)
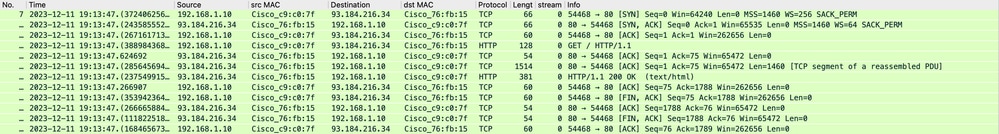 图像-客户端到代理- HTTP -透明-无身份验证
图像-客户端到代理- HTTP -透明-无身份验证
以下是来自客户端的HTTP Get示例
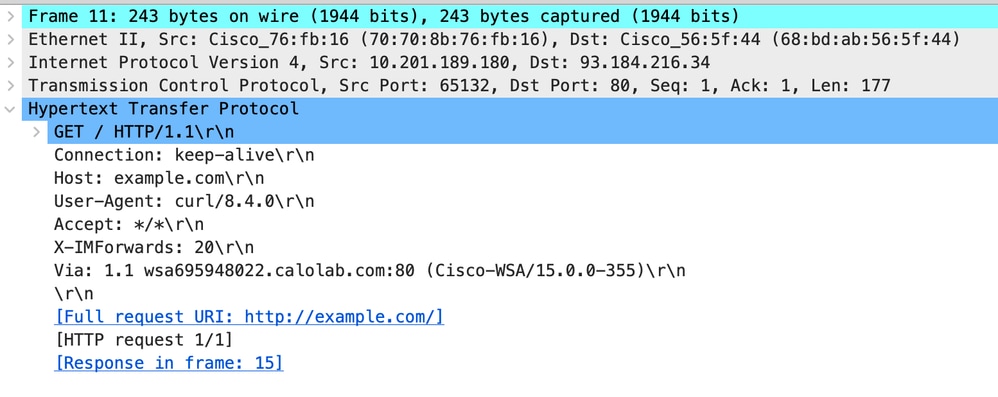 映像-客户端到代理- HTTP -透明-无身份验证-客户端HTTP Get
映像-客户端到代理- HTTP -透明-无身份验证-客户端HTTP Get
SWA和Web服务器
网络流量发生在代理的IP地址和Web服务器的IP地址之间。
来自SWA的流量发往TCP端口80(不是代理端口)
- TCP握手。
- 从代理获取HTTP(目标IP = Web服务器,目标端口= 80)
- 来自Web服务器的HTTP响应(源IP =代理服务器)
- 数据传输
- TCP连接终止(四次握手)
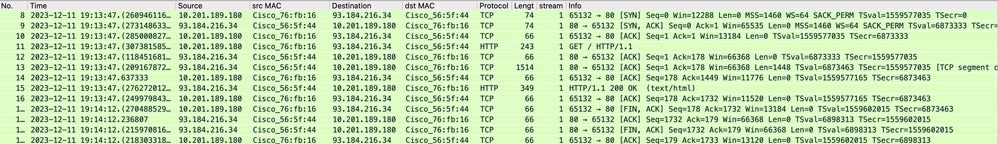 图像-代理和Web服务器- HTTP -透明-无身份验证
图像-代理和Web服务器- HTTP -透明-无身份验证
以下是来自代理的HTTP Get示例
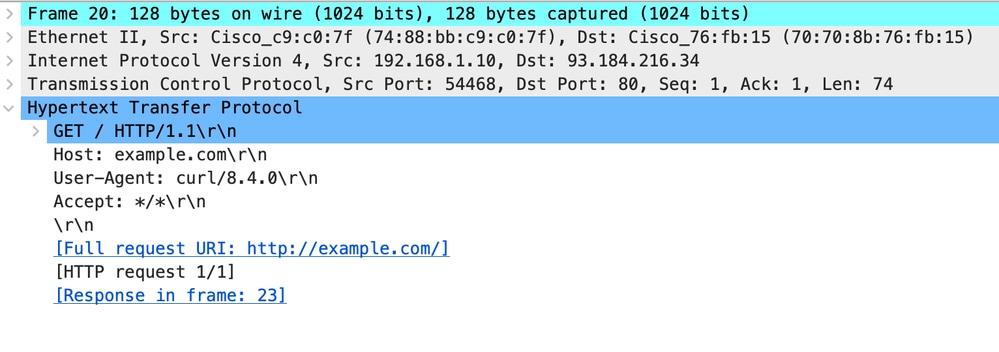 图像- Web服务器的代理- HTTP -透明-无身份验证-代理HTTP Get
图像- Web服务器的代理- HTTP -透明-无身份验证-代理HTTP Get
这表示从客户端到SWA,然后到Web服务器,最后返回客户端的整个流量流。
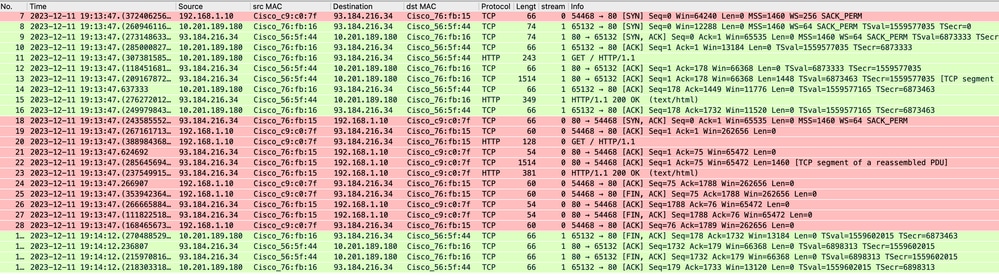 映像-总流量- HTTP -透明-无身份验证
映像-总流量- HTTP -透明-无身份验证

注意:每个数据流都有不同的颜色;从客户端到SWA的流为一种颜色,从SWA到Web服务器的流为另一种颜色。
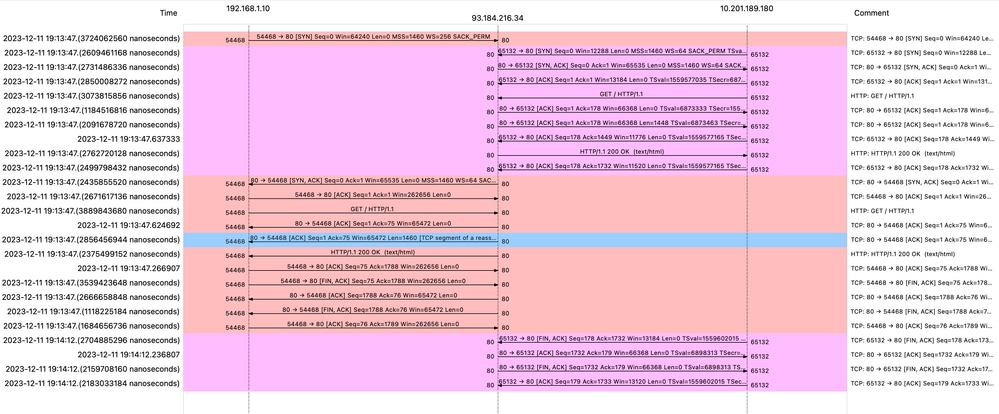 映像- WCCP HTTP流
映像- WCCP HTTP流
以下是访问日志的示例:
1702318427.181 124 192.168.1.10 TCP_MISS/200 1787 GET http://www.example.com/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"-",-,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"-",-,"-","-","-","-","-","-","-",115.29,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 50, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 0, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 1, Request Header = 0, Client Body = 0, 1st response byte = 124, Response header = 0, Server response = 0, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 124>, AMP total = 124<; Latency = 1; "11/Dec/2023:19:13:47 +0100" ][Client Port = 54468, Server IP = 10.184.216.34, Server Port = 80]包含缓存数据的流量
这表示当数据在SWA缓存中时,从客户端到SWA的整个流量。
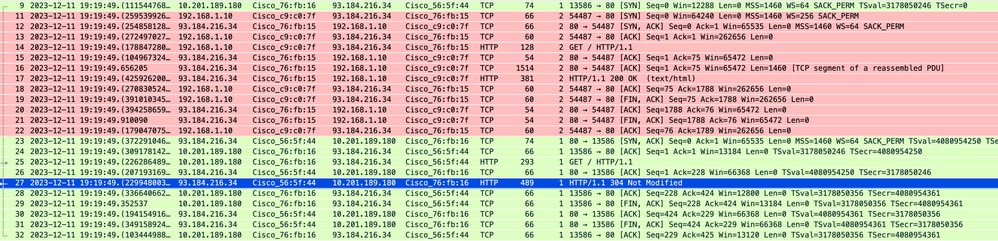 映像-缓存-总流量- HTTP -透明-无身份验证
映像-缓存-总流量- HTTP -透明-无身份验证

注意:正如您看到的,Web服务器返回HTTP响应304:缓存未修改。(在本示例中,数据包编号为27)
以下是HTTP响应304的示例
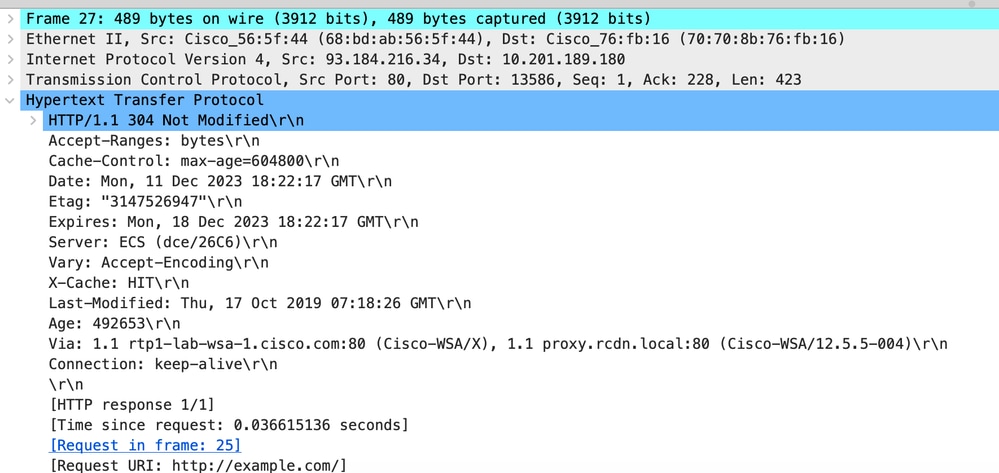 映像-缓存- HTTP响应304 - HTTP -透明-无身份验证
映像-缓存- HTTP响应304 - HTTP -透明-无身份验证
以下是访问日志的示例:
1702318789.560 105 192.168.1.10 TCP_REFRESH_HIT/200 1787 GET http://www.example.com/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"-",-,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"-",-,"-","-","-","-","-","-","-",136.15,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 360, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 0, Response Header = 0, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 2, Request Header = 0, Client Body = 0, 1st response byte = 104, Response header = 0, Server response = 0, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 105>, AMP total = 105<; Latency = 2; "11/Dec/2023:19:19:49 +0100" ][Client Port = 54487, Server IP = 10.184.216.34, Server Port = 80]无身份验证的透明部署中的HTTPs流量
客户端和SWA
网络流量在客户端的IP地址和Web服务器的IP地址之间传输。
来自客户端的流量发往TCP端口443(不是代理端口)
- TCP握手。
- TLS握手客户端呼叫-服务器呼叫-服务器密钥交换-客户端密钥交换
- 数据传输
- TCP连接终止(四次握手)
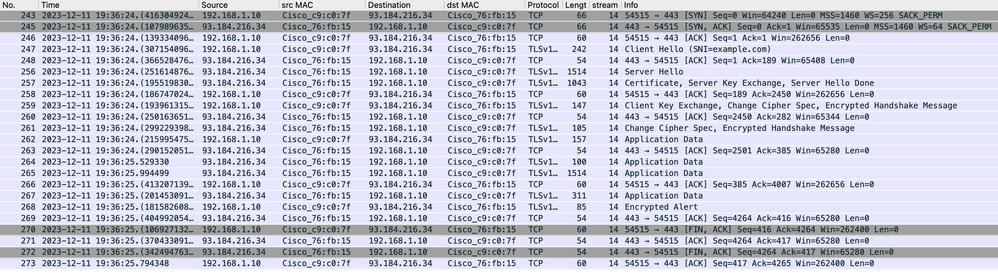 映像-客户端到代理- HTTP -透明-无身份验证
映像-客户端到代理- HTTP -透明-无身份验证
以下是客户端到SWA的客户端Hello的详细信息,如服务器名称指示(SNI)所示,在此示例中为www.example.com 的Web服务器的URL。
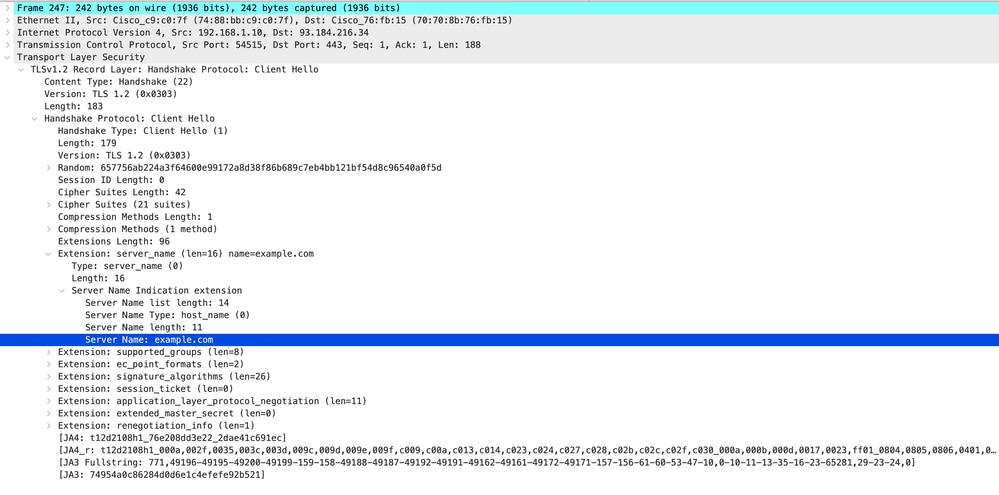 映像-客户端呼叫-客户端到代理-透明-无身份验证
映像-客户端呼叫-客户端到代理-透明-无身份验证

提示:您可以在Wireshark中使用此过滤器搜索URL/SNI:tls.handshake.extensions_server_name == "www.example.com"
下面是服务器密钥交换的示例
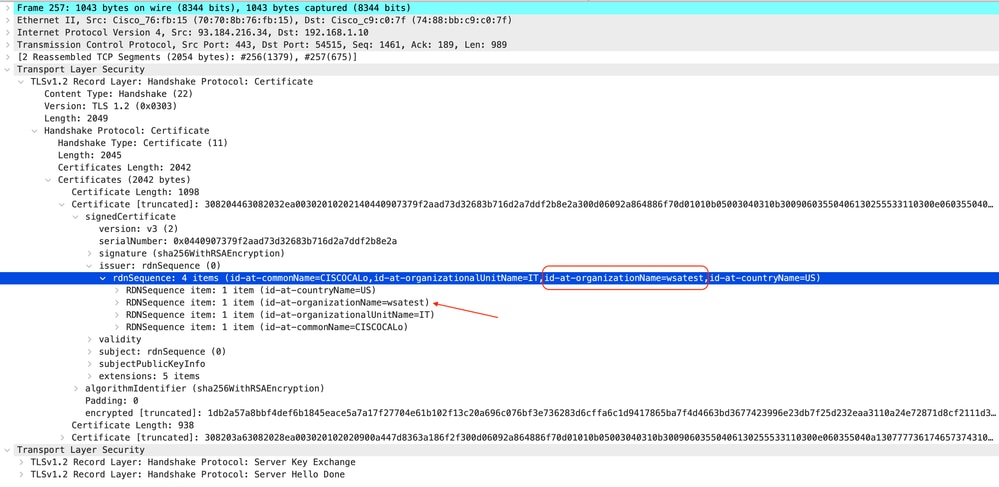 映像-服务器密钥交换-客户端到代理-透明-无身份验证
映像-服务器密钥交换-客户端到代理-透明-无身份验证

注意:正如您看到的,证书是在SWA中配置为解密证书的证书。
SWA和Web服务器
网络流量发生在代理的IP地址和Web服务器的IP地址之间。
来自SWA的流量指向TCP端口443(不是代理端口)
- TCP握手。
- TLS握手客户端呼叫-服务器呼叫-服务器密钥交换-客户端密钥交换
- 数据传输
- TCP连接终止(四次握手)
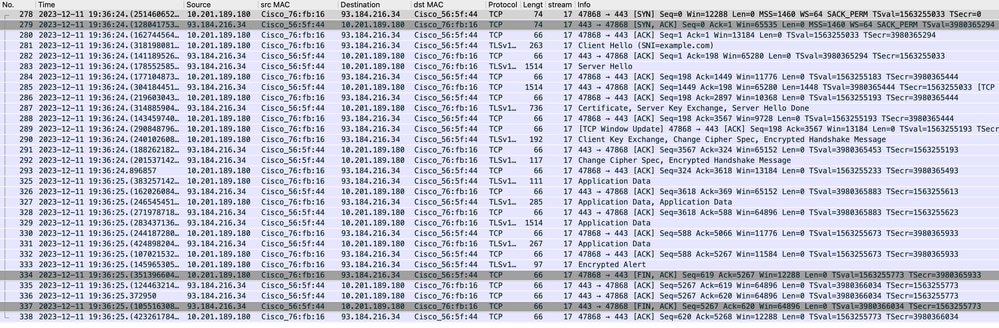 图像- Web服务器的代理- HTTP -透明-无身份验证
图像- Web服务器的代理- HTTP -透明-无身份验证
以下是从SWA到Web服务器的客户端Hello示例
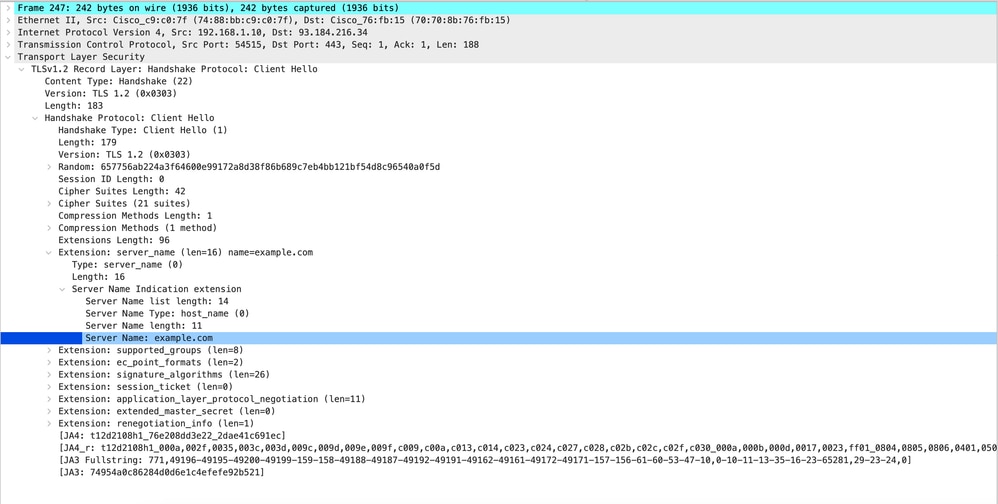 图像-客户端呼叫-代理到Web服务器-透明-无身份验证
图像-客户端呼叫-代理到Web服务器-透明-无身份验证

注意:此处观察的密码套件与从客户端到SWA的客户端Hello中的密码套件不同,因为配置为解密此流量的SWA使用其自己的密码。

提示:在从SWA到Web服务器的服务器密钥交换中,会显示Web服务器证书。但是,如果上游代理找到SWA的配置,则显示其证书而不是Web服务器证书。
以下是访问日志的示例:
1702319784.943 558 192.168.1.10 TCP_MISS_SSL/200 0 TCP_CONNECT 10.184.216.34:443 - DIRECT/www.example.com - DECRYPT_ADMIN_DEFAULT_ACTION_7-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"-",-,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"-",-,"-","-","-","-","-","-","-",0.00,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 940, User Agent = -, AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 0, Response Header = 0, Client Body = 50 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 45, Client Body = 0, 1st response byte = 0, Response header = 0, Server response = 249, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 5, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 558>, AMP total = 558<; Latency = 50; "11/Dec/2023:19:36:24 +0100" ][Client Port = 54515, Server IP = 10.184.216.34, Server Port = 443]
1702319785.190 247 192.168.1.10 TCP_MISS_SSL/200 1676 GET https://www.example.com:443/ - DIRECT/www.example.com text/html DEFAULT_CASE_12-DefaultGroup-DefaultGroup-NONE-NONE-NONE-DefaultGroup-NONE <"-",-,-,"-",-,-,-,-,"-",-,-,-,"-",-,-,"-","-",-,-,"-",-,"-","-","-","-","-","-","-",54.28,0,-,"-","-",-,"-",-,-,"-","-",-,-,"-",-,-> - - [ Request Details: ID = 960, User Agent = "curl/8.4.0", AD Group Memberships = ( NONE ) - ] [ Tx Wait Times (in ms): 1st byte to server = 0, Request Header = 0, Request to Server = 0, 1st byte to client = 50, Response Header = 50, Client Body = 0 ] [ Rx Wait Times (in ms): 1st request byte = 0, Request Header = 97, Client Body = 0, 1st response byte = 48, Response header = 0, Server response = 0, Disk Cache = 0; Auth response = 0, Auth total = 0; DNS response = 0, DNS total = 0, WBRS response = 0, WBRS total = 0, AVC response = 0, AVC total = 0, DCA response = 0, DCA total = 0, McAfee response = 0, McAfee total = 0, Sophos response = 0, Sophos total = 0, Webroot response = 0, Webroot total = 0, Anti-Spyware response = 0, Anti-Spyware total = 0, AMP response = 247>, AMP total = 247<; Latency = 97; "11/Dec/2023:19:36:25 +0100" ][Client Port = 54515, Server IP = 10.184.216.34, Server Port = 443]
注意:正如您在HTTPS流量的透明部署中所看到的,Accesslogs中有2行,第一行是流量被加密的时间,您可以看到TCP_CONNECT和Web服务器的IP地址。如果在SWA中启用解密,则第二行包含GET,整个URL以HTTPS开头,这意味着流量已解密,并且SWA知道该URL。
相关信息
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
13-May-2024 |
初始版本 |
 反馈
反馈