Catalyst 9000系列交换机上的SISF故障排除
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
简介
本文档介绍Catalyst 9000系列交换机中使用的交换机集成安全功能(SISF)。 它还解释了如何使用SISF以及如何与其他功能交互。
先决条件
要求
本文档没有任何特定的要求。
使用的组件
本文档中的信息基于运行Cisco IOS® XE 17.3.x的Cisco Catalyst 9300-48P
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
注意:有关在其他思科平台上启用这些功能所使用的命令,请参阅相应的配置指南。
相关产品
本文档还可与以下硬件和软件版本一起使用:
- Catalyst 9200
- Catalyst 9300
- Catalyst 9400
- Catalyst 9500
- Catalyst 9600
使用17.3.4及更高版本的Cisco IOS XE软件

注意:本文档也适用于大多数使用SISF与设备跟踪的Cisco IOS XE版本。
背景信息
概述
SISF提供了一个主机绑定表,并且有一些功能客户端使用该表中的信息。条目通过收集数据包(如DHCP、ARP、ND、RA)填充到表中,这些数据包跟踪主机活动并帮助动态填充表。如果L2域中有静默主机,则可以使用静态条目向SISF表中添加条目。
SISF使用策略模型配置交换机上的设备角色和其他设置。单个策略可以应用于接口或VLAN级别。如果在VLAN上应用了策略,而在接口上应用了不同的策略,则优先使用接口策略。
SISF也可用于限制表中的主机数量,但IPv4和IPv6行为之间有所不同。如果设置了SISF限制且达到该限制:
- IPv4主机继续运行,但不会向SISF表中添加超出限制的条目
- 未将其加入到SISF表中的IPv6主机不允许进入网络,并且不会向SISF表添加新条目。
从16.9.x及更高版本中引入了SISF客户端功能优先级。它添加选项以控制更新到SISF,如果两个或更多客户端使用绑定表,则应用较高优先级功能的更新。此处的例外是“每个mac的IPv4/IPv6的限制地址计数”设置,具有最低优先级的策略的设置是有效的。
需要启用设备跟踪的一些示例功能包括:
- LISP/EVPN
- Dot1x
- Web身份验证
- CTS
- DHCP 监听
注意:优先级用于选择策略设置。
从CLI创建的策略具有最高优先级(128),因此允许用户应用不同于编程策略中的策略设置。可以手动更改自定义策略下的所有可配置设置。
下一张图片是SISF策略及其读取方式的示例:
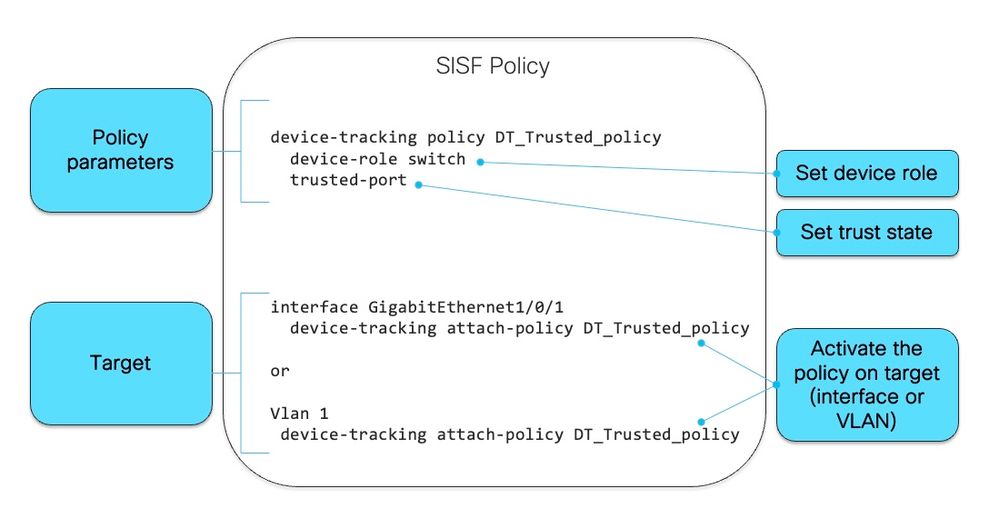
在策略内部,在protocol关键字下,您可以选择使用哪种类型的数据包来填充SISF数据库:
switch(config-device-tracking)#?
device-tracking policy configuration mode:
data-glean binding recovery by data traffic source address
gleaning
default Set a command to its defaults
destination-glean binding recovery by data traffic destination address
gleaning
device-role Sets the role of the device attached to the port
distribution-switch Distribution switch to sync with
exit Exit from device-tracking policy configuration mode
limit Specifies a limit
medium-type-wireless Force medium type to wireless
no Negate a command or set its defaults
prefix-glean Glean prefixes in RA and DHCP-PD traffic
protocol Sets the protocol to glean (default all) <--
security-level setup security level
tracking Override default tracking behavior
trusted-port setup trusted port
vpc setup vpc port
switch(config-device-tracking)#protocol ?
arp Glean addresses in ARP packets
dhcp4 Glean addresses in DHCPv4 packets
dhcp6 Glean addresses in DHCPv6 packets
ndp Glean addresses in NDP packets
udp Gleaning from UDP packets
SISF编程和客户端功能
下表中的功能可在启用SISF时以编程方式启用,或作为SISF的客户端:
| SISF编程功能 |
SISF客户端功能 |
| VLAN上的LISP |
Dot1x |
| VLAN上的EVPN |
Web身份验证 |
| DHCP 监听 |
CTS |
如果在没有启用SISF功能的配置设备上启用了SISF客户端功能,则必须在连接到主机的接口上配置自定义策略。
使用SISF信息的IPv4功能
- CTS
- IEEE 802.1x
- LISP
- EVPN
- DHCP监听(仅激活SISF,但不使用)
- IP 源防护
使用SISF信息的IPv6功能
- IPv6路由器通告(RA)防护
- IPv6 DHCP保护,第2层DHCP中继
- IPv6重复地址检测(DAD)代理
- 泛洪抑制
- IPv6源保护
- IPv6目标防护
- RA节流器
- IPv6前缀防护
设备跟踪
设备跟踪的主要作用是跟踪网络中终端节点的存在、位置和移动。SISF监听交换机接收的流量,提取设备身份(MAC和IP地址),并将它们存储在绑定表中。 许多功能(如IEEE 802.1X、Web身份验证、Cisco TrustSec和LISP等)都取决于此信息的准确性才能正常运行。 基于SISF的设备跟踪支持IPv4和IPv6。 客户端可以通过五种受支持的方法学习IP:
- DHCPv4
- DHCPv6
- ARP
- NDP
- 数据收集
端口通道上的SISF
支持端口通道(或以太网通道)上的设备跟踪。但配置必须应用于信道组,而不是单个端口信道成员。从绑定角度来看,唯一显示(且已知)的接口是port-channel。
探测和数据库调整
探测:
- 在IPDT中,有一个命令通过延迟链路接通时的“ip device tracking probe delay”将初始探测延迟10秒来帮助解决重复地址问题。
- 在SISF中,已经内置了等待计时器,该计时器在发送第一个探测之前会等待。它不可配置,并且解决了相同的问题。由于这是SISF代码,因此不再需要此命令
数据库:
在SISF中,您可以配置几个选项来控制条目在数据库中保留的时间:
tracking enable reachable-lifetime <second|infinite> <-- how long an entry is kept reachable (or keep permanently reachable)
tracking disable stale-lifetime <seconds|infinite> <-- how long and entry is kept inactive before deletion (or keep permanently inactive)
IP设备跟踪
轮询主机的条目的生命周期:
- SISF维护每个MAC的IPv4/IPv6绑定,一旦IP学习成功,绑定将转换为REACHABLE 状态
- SISF通过监控控制数据包跟踪活动客户端
- 如果5分钟内没有来自客户端的控制数据包,绑定将转换到VERIFY状态并发送 探测到客户端
- 如果客户端不响应探测,则绑定将转换到陈旧状态,否则为REACHABLE状态
- STALE条目的默认超时为24小时,并且可配置
- 过时的条目将在24小时后(或配置的超时值)删除
盗窃检测
节点盗窃类型:
- IP盗窃(相同IP、不同MAC、不同/相同端口)
- MAC盗窃(相同的MAC、不同的IP、不同的端口)
- MAC IP THEFT(相同mac、相同ip、不同端口)
IP安全功能
以下是SISF相关的一些功能:
- NDP检查:检查IPv6 NDP消息
- NDP地址收集:使用通过监听NDP流量收集的信息填充绑定表
- 设备跟踪:监控终端设备活动,包括通过某种活动机制
- 监听:收集NDP、ARP和DHCP消息中的地址。阻止未经授权的邮件
- DHCPv4中继:将DHCP广播的数据包中继到已配置的帮助地址。
- NDP和ARP组播抑制:通过转换为单播或代表目标响应来抑制组播NDP消息。
- DAD代理:重复地址检测和代表目标客户端发送NA
- DHCPv4要求:它强制客户端仅通过DHCP获取IP
SISF警告
观察到的一些与SISF相关的最常见行为包括:
- 通过启用其他功能(例如dhcp监听)可以启用SISF
- SISF的默认探测行为可能影响客户端IP地址分配。
- 启用SISF后,上行链路端口也会启用它,这会对网络造成影响。
故障排除
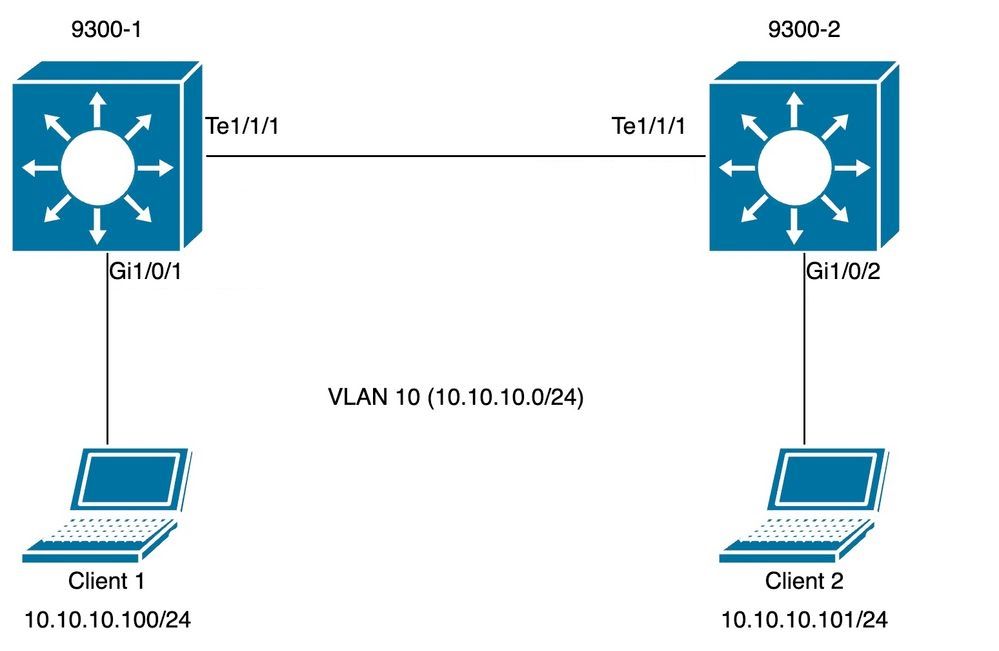
拓扑
拓扑图用于下一个SISF场景。9300交换机仅属于第2层,未在客户端Vlan 10中配置SVI。
注:在本实验中手动启用SISF。
配置
面向接入端口的两台9300交换机都设置了默认SISF配置,而针对中继端口应用了自定义策略来说明预期的SISF输出。
交换机9300-1:
9300-1#show running-config interface GigabitEthernet 1/0/1 Building configuration... Current configuration : 111 bytes ! interface GigabitEthernet1/0/1 switchport access vlan 10 switchport mode access device-tracking <-- enable default SISF policy end
9300-1#
9300-1#show running-config | section trunk-policy
device-tracking policy trunk-policy <-- custom policy
trusted-port <-- custom policy parameters
device-role switch <-- custom policy parameters
no protocol udp
9300-1# 9300-1#show running-config interface tenGigabitEthernet 1/1/1 Building configuration... Current configuration : 109 bytes ! interface TenGigabitEthernet1/1/1 switchport mode trunk device-tracking attach-policy trunk-policy <-- enable custom SISF policy
end
交换机9300-2:
9300-2#show running-config interface GigabitEthernet 1/0/2 Building configuration... Current configuration : 105 bytes ! interface GigabitEthernet1/0/2 switchport access vlan 10 switchport mode access device-tracking <-- enable default SISF policy end
9300-2#show running-config | section trunk-policy
device-tracking policy trunk-policy <-- custom policy
trusted-port <-- custom policy parameters
device-role switch <-- custom policy parameters
no protocol udp
9300-2#show running-config interface tenGigabitEthernet 1/1/1 Building configuration... Current configuration : 109 bytes ! interface TenGigabitEthernet1/1/1 switchport mode trunk device-tracking attach-policy trunk-policy <-- custom policy applied to interface
end
确认
您可以使用以下命令验证应用的策略:
show device-tracking policy <policy name>
show device-tracking policies
show device-tracking database
交换机9300-1:
9300-1#show device-tracking policy default Device-tracking policy default configuration: security-level guard device-role node <-- gleaning from Neighbor Discovery gleaning from DHCP gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn Policy default is applied on the following targets: Target Type Policy Feature Target range Gi1/0/1 PORT default Device-tracking vlan all
9300-1#show device-tracking policy trunk-policy Device-tracking policy trunk-policy configuration: trusted-port <-- security-level guard device-role switch <-- gleaning from Neighbor Discovery gleaning from DHCP gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn Policy trunk-policy is applied on the following targets: Target Type Policy Feature Target range Te1/1/1 PORT trunk-policy Device-tracking vlan all 9300-1#
9300-1#show device-tracking policies Target Type Policy Feature Target range Te1/1/1 PORT trunk-policy Device-tracking vlan all Gi1/0/1 PORT default Device-tracking vlan all
9300-1#show device-tracking database Binding Table has 1 entries, 1 dynamic (limit 200000) Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created Preflevel flags (prlvl): 0001:MAC and LLA match 0002:Orig trunk 0004:Orig access 0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned 0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned Network Layer Address Link Layer Address Interface vlan prlvl age state Time left ARP 10.10.10.100 98a2.c07e.7902 Gi1/0/1 10 0005 8s REACHABLE 306 s 9300-1#
交换机9300-2:
9300-2#show device-tracking policy default Device-tracking policy default configuration: security-level guard device-role node <-- gleaning from Neighbor Discovery gleaning from DHCP gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn Policy default is applied on the following targets: Target Type Policy Feature Target range Gi1/0/2 PORT default Device-tracking vlan all
9300-2#show device-tracking policy trunk-policy Device-tracking policy trunk-policy configuration: trusted-port <-- security-level guard device-role switch <-- gleaning from Neighbor Discovery gleaning from DHCP gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn Policy trunk-policy is applied on the following targets: Target Type Policy Feature Target range Te1/1/1 PORT trunk-policy Device-tracking vlan all 9300-2#
9300-2#show device-tracking policies Target Type Policy Feature Target range Te1/1/1 PORT trunk-policy Device-tracking vlan all Gi1/0/2 PORT default Device-tracking vlan all
9300-2#show device-tracking database Binding Table has 1 entries, 1 dynamic (limit 200000) Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created Preflevel flags (prlvl): 0001:MAC and LLA match 0002:Orig trunk 0004:Orig access 0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned 0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned Network Layer Address Link Layer Address Interface vlan prlvl age state Time left ARP 10.10.10.101 98a2.c07e.9902 Gi1/0/2 10 0005 41s REACHABLE 273 s 9300-2#
常见情况
主机设备上的IPv4地址重复错误
问题
交换机发送的“keepalive”探针是L2检查。因此,从交换机的角度来看,ARP中用作源的IP地址并不重要:此功能可用于根本没有配置IP地址的设备,因此IP源0.0.0.0不相关。 当主机收到此消息时,它会回复并填写目标IP字段,该字段将使用收到的数据包中唯一可用的IP地址,即主机自己的IP地址。这会导致错误重复的IP地址警报,因为作出回复的主机将自己的IP地址同时视为数据包的源和目标。
建议将SISF策略配置为对其keepalive探测使用自动源。
注意:有关详细信息,请参阅有关重复地址问题的文章
默认探测
当不存在本地SVI和默认探测设置时,这是探测数据包:
Ethernet II, Src: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02), Dst: Cisco_76:63:c6 (00:41:d2:76:63:c6) <-- Probe source MAC is the BIA of physical interface connected to client
Destination: Cisco_76:63:c6 (00:41:d2:76:63:c6)
Address: Cisco_76:63:c6 (00:41:d2:76:63:c6)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
Address: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: ARP (0x0806)
Padding: 000000000000000000000000000000000000
Address Resolution Protocol (request)
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
Sender IP address: 0.0.0.0 <-- Sender IP is 0.0.0.0 (default)
Target MAC address: Cisco_76:63:c6 (00:41:d2:76:63:c6)
Target IP address: 10.10.10.101 <-- Target IP is client IP
解决方案
将探测配置为使用除主机PC以外的地址进行探测。这可以通过以下方法实现
“保持连接”探测功能的自动源
为“keep-alive”探测功能配置一个自动源,以减少将0.0.0.0用作源IP的用量:
device-tracking tracking auto-source fallback <IP> <MASK> [override]
如果应用auto-source命令,逻辑工作如下:
device-tracking tracking auto-source fallback 0.0.0.253 255.255.255.0 [override] <-- Optional parameter
- 将源设置为VLAN SVI(如果有)。
- 在IP主机表中搜索同一子网的源/MAC对。探测源自交换机物理接口MAC +数据库中已有的其他子网主机的IP。
- 根据提供的主机位和掩码,从目标IP计算源IP。探测功能是通过侦听客户端IP并在配置了最后位数的子网中创建探测功能生成的。
注意:如果命令与<override>一起应用,我们总是跳到步骤3。
修改后的探测器
将auto-source fallback config设置为使用子网中的IP会修改探测。由于子网中没有SVI和其它客户端,因此我们返回到配置中配置的IP/掩码。
switch(config)#device-tracking tracking auto-source fallback 0.0.0.253 255.255.255.0 <-- it uses .253 for all subnets where there is no existing client and no SVI
这是修改的探测数据包:
Ethernet II, Src: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02), Dst: Cisco_76:63:c6 (00:41:d2:76:63:c6) <-- Probe source MAC is the BIA of physical interface connected to client
Destination: Cisco_76:63:c6 (00:41:d2:76:63:c6)
Address: Cisco_76:63:c6 (00:41:d2:76:63:c6)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
Address: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: ARP (0x0806)
Padding: 000000000000000000000000000000000000
Address Resolution Protocol (request)
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
Sender IP address: 10.10.10.253 <-- Note the new sender IP is now using the fallback IP configured.
Target MAC address: Cisco_76:63:c6 (00:41:d2:76:63:c6)
Target IP address: 10.10.10.101
有关探测行为的更多详细信息
| 命令 |
操作 (为了选择设备跟踪ARP探测的源IP和MAC地址) |
备注 |
| 设备跟踪跟踪自动源 |
|
我们建议禁用所有中继端口上的设备跟踪以避免MAC抖动。 |
| 设备跟踪跟踪自动源覆盖 |
|
不建议没有SVI时使用。 |
| 设备跟踪跟踪自动源回退<IP> <MASK> |
|
我们建议禁用所有中继端口上的设备跟踪以避免MAC抖动。 计算的IPv4地址不能分配给任何客户端或网络设备。 |
| 设备跟踪跟踪自动源回退<IP> <MASK>覆盖 |
|
计算的IPv4地址不能分配给任何客户端或网络设备。 |
device-tracking tracking auto-source fallback <IP> <MASK> [override]命令说明:
根据主机ip,需要保留IPv4地址。
<reserved IPv4 address> = (<host-ip> & <MASK> ) | <IP>
注意:这是一个布尔公式
示例。
如果我们使用命令:
device-tracking tracking auto-source fallback 0.0.0.1 255.255.255.0 override
主机IP = 10.152.140.25
IP = 0.0.0.1
掩码= 24
让我们将布尔公式分成两部分。
1. 10.152.140.25和255.255.255.0操作:
10.152.140.25 = 00001010.10011000.10001100.00011001
AND
255.255.255.0 = 11111111.11111111.11111111.00000000
RESULT
10.152.140.0 = 00001010.10011000.10001100.00000000
2. 10.152.140.0或0.0.0.1操作:
10.152.140.0 = 00001010.10011000.10001100.00000000
OR
0.0.0.1 = 00000000.00000000.00000000.00000001
RESULT
10.152.140.1 = 00001010.10011000.10001100.00000001
保留的IP = 10.152.140.1
保留的IP =(10.152.140.25和255.255.255.0) |(0.0.0.1)= 10.152.140.1
注:用作子网的DHCP绑定中必须包含用作IP源的地址。
重复IPv6地址错误
问题
在网络中启用IPv6并在VLAN上配置交换虚拟接口(SVI)时,出现重复IPv6地址错误。
在普通IPv6 DAD数据包中,IPv6报头中的Source Address字段设置为未指定的地址(0:0:0:0:0:0:0:0)。 类似于IPv4情况。
在SISF探测中选择源地址的顺序为:
- SVI的本地链路地址(如果已配置)
- 使用0:0:0:0:0:0:0:0
解决方案
我们建议您向SVI配置添加以下命令。这使SVI能够自动获取本地链路地址;此地址用作SISF探测的源IP地址,从而防止了重复的IP地址问题。
interface vlan <vlan> ipv6 enable
内存和CPU使用率提高
问题
当以编程方式启用时,交换机发送的“keepalive”探测功能会从所有端口广播。 同一L2域中的连接交换机将这些广播发送到其主机,导致源交换机将远程主机添加到其设备跟踪数据库中。 增加的主机条目会增加设备上的内存使用率,而添加远程主机的过程会增加设备的CPU利用率。
建议通过在连接到交换机的上行链路上配置策略来限定编程策略的范围,以便将端口定义为受信任并连接到交换机。
注意:请注意,SISF相关功能(如DHCP监听)使SISF能够正常工作,从而可能触发此问题。
解决方案
在上行链路(中继)上配置策略,以停止探测和学习位于其他交换机上的远程主机(仅需要使用SISF来维护本地主机表)
device-tracking policy DT_trunk_policy trusted-port device-role switch interface <interface> device-tracking policy DT_trunk_policy
设备跟踪可达时间太短
问题
由于从IPDT到基于SISF的设备跟踪的迁移问题,从较旧版本迁移到16.x及更高版本时,有时会引入非默认的可达时间。
解决方案
建议通过配置以下各项恢复到默认的可到达时间:
no device-tracking binding reachable-time
交换机已注册到Meraki工具(CPU增加和端口刷新)
问题
当交换机连接到Meraki云监控工具时,此类工具会推送自定义设备跟踪策略。
device-tracking policy MERAKI_POLICY security-level glean no protocol udp tracking enable
此策略应用于所有接口而不存在任何区别,也就是说,它不会区分面向其他网络设备(例如交换机、防火墙路由器等)的边缘端口和中继端口。 交换机可以在配置了MERAKI_POLICY的中继端口上创建多个SISF条目,因此会导致这些端口上的刷新以及CPU使用率增加。
switch#show interfaces port-channel 5
Port-channel5 is up, line protocol is up (connected)
<omitted output> Input queue: 0/2000/0/112327 (size/max/drops/flushes); Total output drops: 0 <-- we have many flushes <omitted output>
switch#show process cpu sorted CPU utilization for five seconds: 26%/2%; one minute: 22%; five minutes: 22% PID Runtime(ms) Invoked uSecs 5Sec 1Min 5Min TTY Process 572 1508564 424873 3550 11.35% 8.73% 8.95% 0 SISF Main Thread 105 348502 284345 1225 2.39% 2.03% 2.09% 0 Crimson flush tr
解决方案
在所有非边缘接口上设置下一个策略:
configure terminal device-tracking policy NOTRACK no protocol ndp no protocol dhcp6 no protocol arp no protocol dhcp4 no protocol udp exit
interface <interface> device-tracking policy NOTRACK end
具有相同MAC的IP地址不在SISF表中
问题
此场景常见于HA(高可用性)模式中具有不同IP地址但共享同一MAC地址的设备。在共享相同条件(两个或多个IP地址使用单个MAC地址)的VM环境中也可观察到。 当处于保护模式的自定义SISF策略已到位时,此条件会阻止连接到所有在SISF表中没有条目的IP。根据SISF功能,每个MAC地址只获知一个IP。
注意:17.7.1及后续版本中存在此问题
示例:
- IP 10.0.0.1的MAC地址为10b3.d5a9.bd9f在SISF表上学习并允许与网络设备10.0.0.3通信。
- 但是,共享MAC地址10b3.d659.7858的第二个IP 10.0.0.2和虚拟IP 10.0.0.100未在SISF表中编程,并且不允许与网络通信。
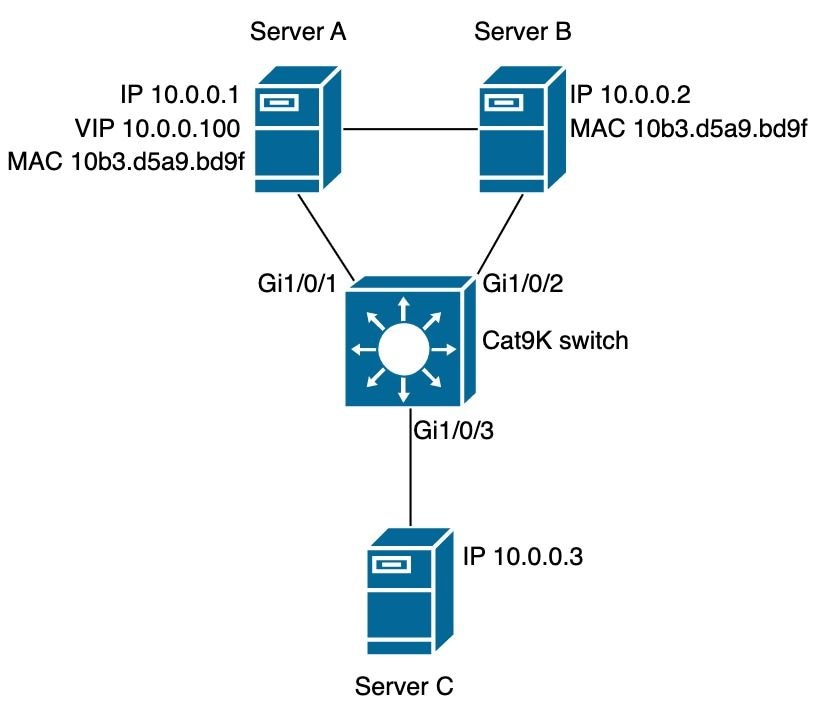
SISF策略
switch#show run | sec IPDT_POLICY device-tracking policy IPDT_POLICY no protocol udp tracking enable
switch#show device-tracking policy IPDT_POLICY Device-tracking policy IPDT_POLICY configuration: security-level guard <-- default mode device-role node gleaning from Neighbor Discovery gleaning from DHCP6 gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn tracking enable Policy IPDT_POLICY is applied on the following targets: Target Type Policy Feature Target range Gi1/0/1 PORT IPDT_POLICY Device-tracking vlan all Gi1/0/2 PORT IPDT_POLICY Device-tracking vlan all
SISF数据库
switch#show device-tracking database
Binding Table has 2 entries, 2 dynamic (limit 200000)
Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created
Preflevel flags (prlvl):
0001:MAC and LLA match 0002:Orig trunk 0004:Orig access
0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned
0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
ARP 10.0.0.3 10b3.d659.7858 Gi1/0/3 10 0005 90s REACHABLE 222 s try 0
ARP 10.0.0.1 10b3.d5a9.bd9f Gi1/0/1 10 0005 84s REACHABLE 220 s try 0
可达性测试服务器A
ServerA#ping 10.0.0.3 source 10.0.0.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
ServerA#ping 10.0.0.3 source 10.0.0.100 <-- entry for 10.0.0.100 is not on SISF table
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.100
.....
可达性测试服务器B。
ServerB#ping 10.0.0.3 <-- entry for 10.0.0.2 is not on SISF table
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
正在验证交换机上的丢包。
switch(config)#device-tracking logging
日志
switch#show logging
<omitted output>
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
<omitted output>
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
解决方案
选项 1:从端口删除IPDT策略可允许ARP数据包和受影响的设备到达
switch(config)#interface gigabitEthernet 1/0/1
switch(config-if)#no device-tracking attach-policy IPDT_POLICY
switch(config-if)#interface gigabitEthernet 1/0/2
switch(config-if)#no device-tracking attach-policy IPDT_POLICY
选项 2:从设备跟踪策略中删除协议arp收集。
switch(config)#device-tracking policy IPDT_POLICY
switch(config-device-tracking)#no protocol arp
选项 3:将IPDT_POLICY的安全级别更改为收集。
switch(config)#device-tracking policy IPDT_POLICY
switch(config-device-tracking)#security-level glean
相关信息
- 安全配置指南,Cisco IOS XE Bengaluru 17.6.x(Catalyst 9300交换机):配置交换机集成安全功能
- 安全配置指南,Cisco IOS XE Cupertino 17.9.x(Catalyst 9300交换机):配置交换机集成安全功能
- Cisco Catalyst 9000系列交换机集成安全功能(SISF)白皮书
- Cisco Bug ID CSCvx75602 - AR中继和ND抑制中的SISF内存泄漏
- Cisco bug ID CSCwf33293 - [EVPN SISF]使用EVPN + DHCP修改IPv4/V6的限制地址值所需的自定义方法
- Cisco Bug ID CSCvq22011 - IOS-XE在IPDT从ARP发出闪烁时丢弃ARP应答
- Cisco Bug ID CSCwc20488 - 255 pseudo-ports limit per vlan/evi
- 当端口中具有IPDT策略时,Cisco Bug ID CSCwh52315 - 9300交换机丢弃ARP应答
- Cisco Bug ID CSCvd51480 — 解除绑定ip dhcp监听和设备跟踪
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
17-Jan-2024 |
初始版本 |
由思科工程师提供
- 路易斯·阿斯科纳
- 克拉克·戴森
- 安布罗斯·泰勒
 反馈
反馈