用於檢測和清除PfR轉發環路的EEM小程式
目錄
簡介
本檔案介紹內嵌事件管理員(EEM)小程式,用於效能路由(PfR)透過多個邊界中繼(BR)最佳化流量的網路。還觀察到一些轉發環路。這些applet用於在觀察到環路時收集資料並減輕轉發環路的影響。
必要條件
需求
本文件沒有特定需求。
採用元件
本檔案中的資訊是根據支援EEM 4.0版的Cisco IOS®軟體。
要檢查Cisco IOS版本支援的EEM版本,請使用以下命令:
Router#sh event manager version | i Embedded
Embedded Event Manager Version 4.00
Router#
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路正在作用,請確保您已瞭解任何指令可能造成的影響。
背景資訊
當PfR控制流量類(TC)時,它會在BR上建立動態路由對映/訪問控制清單(ACL)。具有選定出口的BR上的路由對映指向選定出口,而其他BR上的路由對映指向內部介面(下一跳=選定BR)。
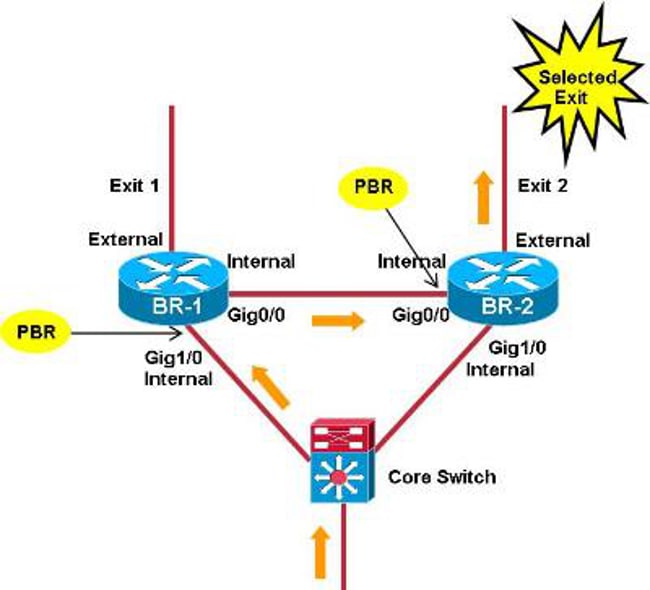
當動態ACL未在不同的BR之間正確同步時,會發生問題(例如由於錯誤所致)。
在本圖中,重點介紹使用DSCP EF匹配發往172.16.1.0/24的任何IP資料包的TC。在本場景中,相關ACL條目從所選BR (BR-2)中刪除,而不是從BR-1中刪除。該TC的資料包在BR-2上命中,字首條目匹配發往172.16.1.0/24的所有IP資料包。字首條目的所選出口是Exit-1,因此BR-2上的相關路由對映/ACL指向BR-1。
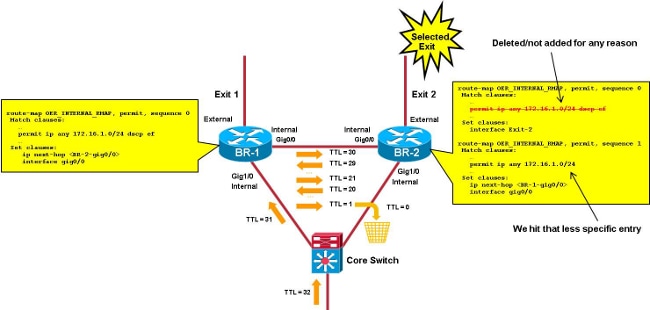
現在,該TC的資料包在BR之間循環,直到生存時間(TTL)達到0。
本檔案提供必要的EEM Applet,用於:
- 檢測BR之間的轉發環路
- 收集相關資訊並清除PfR
主控制器(MC)/BR組合式案例中使用的Applet要容易得多(當其中一個BR上執行MC時)。還介紹了具有專用MC的場景。
EEM Applet詳細資訊
本節說明用於此程式的存取清單,以及Applet日誌檔。
使用的訪問清單
為了檢測轉發環路,Applet依賴ACL來匹配具有低TTL的資料包。
建議在2x連續且相對較低的TTL值(20和21)上使用ACE匹配,以便在BR之間循環的每個資料包獲得一個(且僅一個)命中。所用的TTL值不應太低,以避免來自traceroute資料包的頻繁命中。
interface gig0/0 (internal interface)
ip access-group LOOP in
!
ip access-list extended LOOP
permit ip 10.116.48.0 0.0.31.255 any ttl range 20 21
permit ip any any
ACL應放置在show pfr master border topology命令輸出報告的內部介面上。
源IP範圍(此處10.116.48.0/20)應與內部網路(可透過內部介面訪問的字首)匹配。
為了確定哪個遠端站點/TC受到環路的影響,您可以在介面上增加第二個ACL,為每個遠端站點/TC增加更具體的ACE。
interface gig0/0 (internal interface)
ip access-group LOOP-DETAIL out
!
ip access-list extended LOOP-DETAIL
permit ip 10.116.48.0 0.0.31.255 10.116.132.0 0.0.0.255 ttl range 20 21
permit ip 10.116.48.0 0.0.31.255 10.116.128.0 0.0.0.255 ttl range 20 21
.... (add here one line per remote site)
permit ip any an
目的IP與不同遠端站點中的子網匹配:
10.116.132.0/24 -> site-1
10.116.128.0/24 -> site-2
如果需要確定受環路影響的確切的TC,還可以為每個遠端站點增加幾行。
Applet職責
Applet每30秒檢查一次ACL環路中TTL上匹配的ACE的命中數。根據這些檢查的結果,Applet可能會執行下列工作:
- 如果命中計數超過配置的閾值(THRESHOLD_1),Applet將清除ACL計數並在15秒內重新檢查命中計數。
- 在15秒之後,如果命中計數高於第二個閾值(閾值2),可能存在環路。您必須收集一組輸出並清除PfR才能解決環路問題。
- 第二個閾值定義為全局變數,因此無需重新啟動小程式即可輕鬆對其進行調整。
- 這些閾值的最佳值主要取決於每個TC的平均資料包速率。
Applet記錄檔
Applet會維護一個記錄檔,以追蹤中斷計數的數目(當計數大於0時),以及任何出現暫時回圈(當超過THRESHOLD_1但不超過THRESHOLD_2時)或實際回圈(當同時超過THRESHOLD_1和THRESHOLD_2時)的情況。
MC/BR組合和其他BR場景的Applet
這些是本文檔中描述的最簡單方案。環路檢測和PfR清除在同一台裝置上完成,因此無需進入裝置EEM小程式通訊。在MC/BR Combo和其他BR上運行單獨的小程式。
MC/BR Combo上的小程式
此輸出顯示MC/BR組合上使用的applet的重要資訊。以下是此特定輸出的一些重要說明:
- THRESHOLD_1顯示的值為1000,THRESHOLD_2顯示的值為500。這意味著,如果受環路影響的TC速率高於1000/30(33 pps),則會啟動該applet。
- DISK變數標識日誌檔案和輸出檔案的推送位置(顯示在bootflash上)。
- 日誌檔案條目從show clock命令輸出派生的時間戳。中間的字元(此處顯示為「est」)取決於時區,必須進行調整(請參閱操作240)。
- 在出現環路時必須收集的輸出會推送到bootflash中的script-output-xxxxxxx檔案中,其中「xxxxxx」是自1970年以來經過的秒數(用於使每次出現環路時獲得唯一的檔名)。
- 操作330、340、350和360中列出了所收集的命令。可以增加一些其他/不同的命令。
event manager environment THRESHOLD_1 1000
event manager environment THRESHOLD_2 500
event manager environment DISK bootflash
!
event manager applet LOOP-MON authorization bypass
event timer watchdog name LOOP time 30
action 100 cli command "enable"
action 110 cli command "show ip access-list LOOP"
action 120 set regexp_substr 0
action 130 regexp "range 20 21 \(([0-9]+) matches\)"
$_cli_result _regexp_result regexp_substr
action 140 cli command "clear ip access-list counters LOOP"
action 150 if $regexp_substr gt 0
action 200 set MATCHES $regexp_substr
action 210 file open LOGS $DISK:script-logs.txt a
action 220 cli command "enable"
action 230 cli command "show clock"
action 240 regexp "[0-9]+:[0-9]+:[0-9]+.[0-9]+ est [A-Za-z]+
[A-Za-z]+ [0-9]+ 201[0-9]" $_cli_result _regexp_result
action 250 set TIME $_regexp_result
action 260 if $MATCHES gt $THRESHOLD_1
action 270 wait 15
action 280 cli command "show ip access-list LOOP"
action 290 set regexp_substr 0
action 300 regexp "range 20 21 \(([0-9]+) matches\)"
$_cli_result _regexp_result regexp_substr
action 310 if $regexp_substr gt $THRESHOLD_2
action 320 cli command "enable"
action 330 cli command "show ip access-list LOOP-DETAIL
| tee /append $DISK:script-output-$_event_pub_sec.txt"
action 340 cli command "show pfr master traffic-class perf det
| tee /append $DISK:script-output-$_event_pub_sec.txt"
action 350 cli command "show route-map dynamic detail
| tee /append $DISK:script-output-$_event_pub_sec.txt"
action 360 cli command "show ip route
| tee /append $DISK:script-output-$_event_pub_sec.txt"
action 370 cli command "clear pfr master *"
action 380 cli command "clear ip access-list counters LOOP-DETAIL"
action 390 file puts LOGS "$TIME - LOOP DETECTED - PfR CLEARED -
matches $MATCHES > $THRESHOLD_1 and $regexp_substr
> $THRESHOLD_2 - see $DISK:script-output-$_event_pub_sec.txt"
action 400 syslog priority emergencies msg "LOOP DETECTED -
PfR CLEARED - see $DISK:script-output-$_event_pub_sec.txt !"
action 410 else
action 420 file puts LOGS "$TIME - TEMPORARY LOOP : matches
$MATCHES > $THRESHOLD_1 and $regexp_substr < or = $THRESHOLD_2"
action 430 cli command "clear ip access-list counters LOOP-DETAIL"
action 440 end
action 450 else
action 460 cli command "en"
action 470 cli command "clear ip access-list counters LOOP-DETAIL"
action 480 file puts LOGS "$TIME - number of matches =
$MATCHES < $THRESHOLD_1"
action 490 end
action 500 else
action 510 cli command "clear ip access-list counters LOOP-DETAIL"
action 520 end
適用於其他BR的Applet
本節介紹用於其他BR的applet。以下是此特定輸出的一些重要說明:
- Applet每20秒運行一次,而MC/BR Combo上的指令碼每30秒運行一次。這可以確保BR上的小程式在透過MC/BR上運行的小程式清除PfR之前啟動。
- 使用唯一的閾值,因此無需避免故障陽性。
- 為THRESHOLD顯示的值為700,應根據MC/BR Applet中的THRESHOLD_1值進行設定。
- applet日誌檔案被推送到flash0中的script-logs.txt檔案中。這可以在操作170和DISK變數中更改。
- 日誌檔案條目從show clock命令輸出派生的時間戳。中間的字元(此處顯示為「est」)取決於時區,必須進行調整(請參閱操作190)。
- script-output-xxxxxxx檔案中推送在出現環路時必須收集的輸出資訊,其中「xxxxxx」是自1970年以來經過的秒數(用於使每次出現環路時獲得唯一的檔名)。
- 所收集的命令列於操作230和操作240中。可以增加一些其他/不同的命令。
event manager environment THRESHOLD 700
event manager environment DISK flash 0
!
event manager applet LOOP-BR authorization bypass
event timer watchdog name LOOP time 20
action 100 cli command "enable"
action 110 cli command "show ip access-list LOOP"
action 120 set regexp_substr 0
action 130 regexp "range 20 21 \(([0-9]+) matches\)"
$_cli_result _regexp_result regexp_substr
action 140 cli command "clear ip access-list counters LOOP"
action 150 if $regexp_substr gt 0
action 160 set MATCHES $regexp_substr
action 170 file open LOGS $DISK:script-logs.txt a
action 180 cli command "show clock"
action 190 regexp "[0-9]+:[0-9]+:[0-9]+.[0-9]+
est [A-Za-z]+ [A-Za-z]+ [0-9]+ 201[0-9]" $_cli_result _regexp_result
action 200 set TIME $_regexp_result
action 210 if $MATCHES gt $THRESHOLD
action 220 cli command "enable"
action 230 cli command "show route-map dynamic detail | tee /append
$DISK:script-output-$_event_pub_sec.txt"
action 240 cli command "show ip route | tee /append
$DISK:script-output-$_event_pub_sec.txt"
action 250 file puts LOGS "$TIME : matches = $MATCHES >
$THRESHOLD - see $DISK:script-output-$_event_pub_sec.txt"
action 260 syslog priority emergencies msg "LOOP DETECTED -
Outputs captured - see $DISK:script-output-$_event_pub_sec.txt !"
action 270 else
action 280 file puts LOGS "$TIME : matches = $MATCHES < or = $THRESHOLD"
action 290 end
action 300 end
專用MC案例的Applet
環路檢測和PfR清除/統計資訊收集在必須具有裝置間EEM Applet通訊的不同裝置上完成。裝置之間的通訊以不同方式進行。本文檔介紹透過跟蹤對象進行的裝置通訊,以檢查IGP中通告的專用環回的可達性。偵測到事件時,會關閉回送,如此可讓遠端裝置上的applet在追蹤的物件離線時啟動。如果需要交換不同的資訊,可以使用不同的環回。
Applet通訊
使用這些Applet和通訊方法:
| Applet名稱 | 哪裡? | 什麼? | 扳機? | 通訊? |
| LOOP-BR | BR | 檢查ACL命中數以偵測回圈 |
定期 | 關閉回圈100 |
| LOOP-MC | MC | - 收集PfR資訊 - 清除PfR |
追蹤可達性回圈100 | 關閉回圈200 |
| COLLECT-BR | BR | 收集資訊 | 追蹤可達性回圈200 | none |
以下圖片說明了這一點:
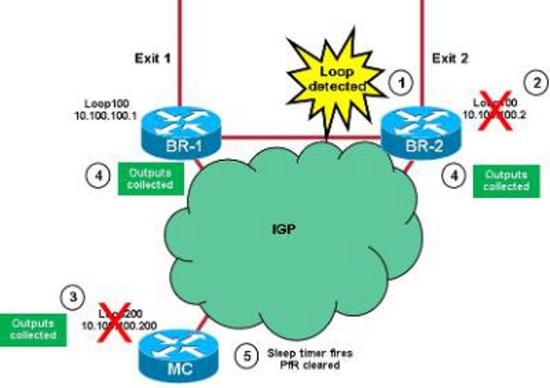
Applet使用的程式如下:
- BR上的LOOP-BR小程式檢測到環路。假定首先在BR-2上檢測到環路。
- applet關閉BR-2上的Loop100,並在內部網關協定(IGP)上通告資訊。
- BR-2的Loop100所跟蹤的對象在MC上離線,並且LOOP-MC applet將啟動。收集PfR主輸出,並關閉MC上的Loopback 200。該資訊在IGP上通告。十秒睡眠計時器開始。
- MC上Loop200的跟蹤對象會在兩個BR上離線。這將觸發收集BR特定資訊的COLLECT-BR Applet。
- 休眠計時器(步驟3)開始,MC清除PfR。
建立跟蹤對象和環回
本節介紹如何建立環回(確保IP在IGP上通告)和跟蹤對象。
追蹤物件
建立追蹤物件時,請謹記以下幾點重要事項:
- BR上需要單個跟蹤對象,該對象用於跟蹤MC上的loopback200(這將觸發資料收集)。
- MC需要數個追蹤物件:
- 軌道1和2用於分別跟蹤BR-1和BR-2上的loopback100。
- 軌道11和12用於分別跟蹤BR-1和BR-2之間的連通性(避免在BR之間出現連通性問題時進行PfR清除)。
- 路線20追蹤路線11與路線12之間的邏輯AND。用於驗證MC是否可到達所有BR。
- track timer ip route值設定為一秒,以加快可接通性問題檢測的速度(預設值為15秒)。
BR-1
interface Loopback100
ip address 10.100.100.1 255.255.255.255
!
track timer ip route 1
track 1 ip route 10.100.100.200 255.255.255.255 reachability
BR-2
interface Loopback100
ip address 10.100.100.2 255.255.255.255
!
track timer ip route 1
track 1 ip route 10.100.100.200 255.255.255.255 reachability
MC
interface Loopback200
ip address 10.100.100.200 255.255.255.255
!
track timer ip route 1
track 1 ip route 10.100.100.1 255.255.255.255 reachability
track 2 ip route 10.100.100.2 255.255.255.255 reachability
track 11 ip route 10.116.100.1 255.255.255.255 reachability
track 12 ip route 10.116.100.2 255.255.255.255 reachability
track 20 list boolean and
object 11
object 12
BR和MC環回
LOOP-BR
本節介紹如何在BR上建立環回。以下是需要牢記的一些重要注意事項:
- THRESHOLD_1值為1000,THRESHOLD_2值為500。這意味著,如果受環路影響的TC的速率高於1000/30 (33 p/s),則小程式將啟動。
- applet日誌檔案推送到bootflash中的script-detect-logs.txt檔案中。這在操作210中進行了更改,並使用DISK變數進行了更改。
- 日誌檔案中條目的時間戳從sh clock輸出派生。中間的字元(顯示為「est」)取決於時區並需要調整(操作240)。
- 關閉Loopback100以通知MC後,請等待五秒(以確保IGP有時間傳播資訊)並重新打開它(操作370)。
event manager environment THRESHOLD_1 100event manager environment
THRESHOLD_2 500event manager environment DISK bootflash
!event manager applet LOOP-BR authorization bypass
event timer watchdog name LOOP time 30 maxrun 27
action 100 cli command "enable"
action 110 cli command "show ip access-list LOOP"
action 120 set regexp_substr 0
action 130 regexp "range 20 21 \(([0-9]+) matches\)"
$_cli_result _regexp_result regexp_substr
action 140 cli command "clear ip access-list counters LOOP"
action 150 if $regexp_substr gt 0
action 200 set MATCHES $regexp_substr
action 210 file open LOGS $DISK:script-detect-logs.txt a
action 220 cli command "enable"
action 230 cli command "show clock"
action 240 regexp "[0-9]+:[0-9]+:[0-9]+.[0-9]+
est [A-Za-z]+ [A-Za-z]+ [0-9]+ 201[0-9]"
$_cli_result _regexp_result
action 250 set TIME $_regexp_result
action 260 if $MATCHES gt $THRESHOLD_1
action 270 wait 15
action 280 cli command "show ip access-list LOOP"
action 290 set regexp_substr 0
action 300 regexp "range 20 21 \(([0-9]+) matches\)"
$_cli_result _regexp_result regexp_substr
action 310 if $regexp_substr gt $THRESHOLD_2
action 320 cli command "enable"
action 330 cli command "conf t"
action 340 cli command "interface loop100"
action 350 cli command "shut"
action 360 file puts LOGS "$TIME - LOOP DETECTED - Message sent to MC -
matches $MATCHES > $THRESHOLD_1 and $regexp_substr > $THRESHOLD_2"
action 370 wait 5
action 375 cli command "enable"
action 380 cli command "conf t"
action 390 cli command "interface loop100"
action 400 cli command "no shut"
action 410 else
action 420 file puts LOGS "$TIME - TEMPORARY LOOP : matches $MATCHES >
$THRESHOLD_1 and $regexp_substr < or = $THRESHOLD_2"
action 430 cli command "clear ip access-list counters LOOP-DETAIL"
action 440 end
action 450 else
action 460 cli command "en"
action 470 cli command "clear ip access-list counters LOOP-DETAIL"
action 480 file puts LOGS "$TIME - number of matches =
$MATCHES < $THRESHOLD_1"
action 490 end
action 500 else
action 510 cli command "clear ip access-list counters LOOP-DETAIL"
action 520 end
LOOP-MC
本節介紹如何在MC上建立環回。以下是需要牢記的一些重要注意事項:
- 比率限制值取決於applet以60的比率限制值執行的頻率(程式檔每分鐘執行一次)。這是為了避免兩個BR檢測到相同的環路時PfR清除兩次。
- 在操作130中,等待兩秒鐘,然後再檢查到所有BR的可達性。這是為了避免由MC和BR之間的連線問題引起的誤報。
- 在操作240中,在關閉Loopback200後等待十秒,再清除PfR。這是為了確保BR有時間收集資料。
event manage environment DISK bootflash
event manager applet LOOP-MC authorization bypass
event syslog pattern "10.100.100.[0-9]/32 reachability Up->Dow" ratelimit 60
action 100 file open LOGS $DISK:script-logs.txt a
action 110 regexp "10.100.100.[0-9]" "$_syslog_msg" _regexp_result
action 120 set BR $_regexp_result
action 130 wait 2
action 140 track read 20
action 150 if $_track_state eq "up"
action 160 cli command "enable"
action 170 cli command "show clock"
action 180 regexp "[0-9]+:[0-9]+:[0-9]+.[0-9]+
est [A-Za-z]+ [A-Za-z]+ [0-9]+ 201[0-9]"
"$_cli_result" _regexp_result
action 190 set TIME "$_regexp_result"
action 200 cli command "show pfr master traffic-class perf det
| tee /append $DISK:script-output-$_event_pub_sec.txt"
action 210 cli command "conf t"
action 220 cli command "interface loop200"
action 230 cli command "shut"
action 240 wait 10
action 250 cli command "conf t"
action 260 cli command "interface loop200"
action 270 cli command "no shut"
action 280 cli command "end"
action 290 cli command "clear pfr master *"
action 300 file puts LOGS "$TIME - LOOP DETECTED by $BR -
PfR CLEARED - see $DISK:script-output-$_event_pub_sec.txt"
action 310 syslog priority emergencies msg "LOOP DETECTED by $BR -
PfR CLEARED - see $DISK:script-output-$_event_pub_sec.txt !"
action 320 else
action 330 file puts LOGS "$TIME - REACHABILITY LOST with
$BR - REACHABILITY TO ALL BRs NOT OK - NO ACTION"
action 340 end
COLLECT-BR
本節介紹如何收集BR。當BR失去對MC上Loopback200 (10.100.100.200)的可訪問性時,小程式將啟動。操作120、130和140中列出了用於收集的命令。
event manager environment DISK bootflash
event manager applet COLLECT-BR authorization bypass
event syslog pattern "10.100.100.200/32 reachability Up->Dow" ratelimit 45
action 100 file open LOGS $DISK:script-collect-logs.txt a
action 110 cli command "enable"
action 120 cli command "sh ip access-list LOOP-DETAIL |
tee /append $DISK:script-output-$_event_pub_sec.txt"
action 130 cli command "show route-map dynamic detail
| tee /append $DISK:script-output-$_event_pub_sec.txt"
action 140 cli command "show ip route | tee /append
$DISK:script-output-$_event_pub_sec.txt"
action 150 cli command "show clock"
action 160 regexp "[0-9]+:[0-9]+:[0-9]+.[0-9]+ CET [A-Za-z]+ [A-Za-z]+
[0-9]+ 201[0-9]" "$_cli_result" _regexp_result
action 170 set TIME "$_regexp_result"
action 180 file puts LOGS "$TIME - OUTPUTs COLLECTED -
see $DISK:script-output-$_event_pub_sec.txt"
SYSLOG-MC
以下是檢測到環路時MC上的系統日誌:
MC#
*Mar 8 08:52:12.529: %TRACKING-5-STATE: 1 ip route 10.100.100.1/32
reachability Up->Down
MC#
*Mar 8 08:52:16.683: %LINEPROTO-5-UPDOWN:
Line protocol on Interface Loopback200, changed state to down
*Mar 8 08:52:16.683: %LINK-5-CHANGED: Interface Loopback200,
changed state to administratively down
MC#
*Mar 8 08:52:19.531: %TRACKING-5-STATE: 1
ip route 10.100.100.1/32 reachability Down->Up
MC#
*Mar 8 08:52:24.727: %SYS-5-CONFIG_I: Configured from console by
on vty0 (EEM:LOOP-MC)
*Mar 8 08:52:24.744: %PFR_MC-1-ALERT: MC is inactive due to PfR
minimum requirements not met;
Less than two external interfaces are operational
MC#
*Mar 8 08:52:24.757: %HA_EM-0-LOG: LOOP-MC:
LOOP DETECTED by 10.100.100.1 - PfR CLEARED
- see unix:script-output-1362732732.txt !
MC#
*Mar 8 08:52:26.723: %LINEPROTO-5-UPDOWN:
Line protocol on Interface Loopback200, changed state to up
MC#
*Mar 8 08:52:26.723: %LINK-3-UPDOWN: Interface Loopback200,
changed state to up
MC#
*Mar 8 08:52:29.840: %PFR_MC-5-MC_STATUS_CHANGE: MC is UP
*Mar 8 08:52:30.549: %TRACKING-5-STATE: 2
ip route 10.100.100.2/32 reachability Up->Down
MC#
*Mar 8 08:52:37.549: %TRACKING-5-STATE: 2
ip route 10.100.100.2/32 reachability Down->Up
MC#
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
27-May-2013 |
初始版本 |
 意見
意見