使用Microsoft IAS為L2TP配置Cisco IOS和Windows 2000客戶端
目錄
簡介
本文提供如何使用Microsoft的Internet身份驗證伺服器(IAS)為第2層隧道協定(L2TP)配置Cisco IOS®軟體和Windows 2000客戶端的說明。
請參閱Windows 2000/XP PC和PIX/ASA 7.2之間的L2TP Over IPsec使用預共用金鑰配置示例,以瞭解有關如何使用預共用金鑰和Microsoft Windows 2003 IAS RADIUS伺服器進行使用者身份驗證來將遠端Microsoft Windows 2000/2003和XP客戶端的L2TP over IPsec配置到PIX安全裝置公司辦公室的更多資訊。
有關如何使用加密方法將L2TP over IPSec從遠端Microsoft Windows 2000和XP客戶端配置到公司站點的詳細資訊,請參閱使用預共用金鑰將L2TP over IPSec從Windows 2000或XP客戶端配置到Cisco VPN 3000系列集中器。
必要條件
需求
本文件沒有特定先決條件。
採用元件
本文中的資訊係根據以下軟體和硬體版本:
-
Microsoft IAS可選元件安裝在帶有Active Directory的Microsoft 2000高級伺服器上
-
Cisco 3600路由器
-
Cisco IOS軟體版本c3640-io3s56i-mz.121-5.T
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路正在作用,請確保您已瞭解任何指令可能造成的影響。
慣例
如需文件慣例的詳細資訊,請參閱思科技術提示慣例。
設定
本節提供用於設定本文件中所述功能的資訊。
註:使用Command Lookup Tool(僅限註冊客戶)查詢有關本文檔中使用的命令的更多資訊。
網路圖表
本檔案會使用以下網路設定:
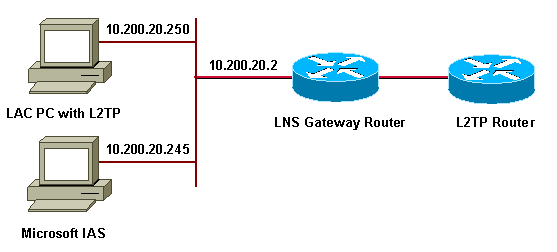
本檔案將以下IP池用於撥號使用者端:
-
網關路由器:192.168.1.2 ~ 192.168.1.254
-
LNS :172.16.10.1 ~ 172.16.10.1
為Microsoft IAS配置Windows 2000高級伺服器
確保已安裝Microsoft IAS。要安裝Microsoft IAS,請以管理員身份登入並完成以下步驟:
-
在Network Services下,驗證是否已清除所有覈取方塊。
-
選中Internet Authentication Server(IAS)覈取方塊,然後按一下OK。
-
在「Windows元件」嚮導中,按一下下一步。如果出現提示,請插入Windows 2000 CD。
-
複製所需檔案後,按一下完成,然後關閉所有視窗。您無需重新啟動。
設定RADIUS使用者端
請完成以下步驟:
-
在管理工具中,開啟Internet Authentication Server Console,然後按一下Clients。
-
在Friendly Name框中,輸入網路訪問伺服器(NAS)的IP地址。
-
按一下「Use This IP」。
-
在「Client-Vendor」下拉式清單中,確保選擇「RADIUS Standard」。
-
在Shared Secret和Confirm Shared Secret框中,輸入密碼,然後按一下Finish。
-
在控制檯樹中,按一下右鍵Internet Authentication Service,然後按一下Start。
-
關閉控制檯。
在IAS上配置使用者
與CiscoSecure不同,Windows 2000遠端身份驗證撥入使用者伺服器(RADIUS)使用者資料庫與Windows使用者資料庫緊密繫結。
-
如果在Windows 2000伺服器上安裝了Active Directory,請從Active Directory使用者和電腦建立新撥號使用者。
-
如果尚未安裝Active Directory,則可以使用管理工具中的本地使用者和組來建立新使用者。
在Active Directory中配置使用者
完成以下步驟,以便使用Active Directory配置使用者:
-
在「Active Directory Users and Computers」控制檯中,展開域。
-
按一下右鍵Users Scroll以選擇New User。
-
建立一個名為tac的新使用者。
-
在Password和Confirm Password對話方塊中輸入您的密碼。
-
清除User Must Change Password at Next Logon選項,然後按一下Next。
-
開啟使用者tac的屬性框。切換到Dial-in頁籤。
-
在Remote Access Permission(Dial-in or VPN)下,按一下Allow Access,然後按一下OK。
配置使用者(如果未安裝Active Directory)
完成以下步驟,在未安裝Active Directory的情況下配置使用者:
-
在Administrative Tools中,按一下Computer Management。
-
展開Computer Management控制檯,然後按一下Local Users and Groups。
-
按一下右鍵Users Scroll以選擇New User。
-
在密碼和確認密碼對話方塊中輸入密碼。
-
清除User Must Change Password at Next Logon選項,然後按一下Next。
-
開啟新使用者tac的屬性框。切換到Dial-in頁籤。
-
在Remote Access Permission(Dial-in or VPN)下,按一下Allow Access,然後按一下OK。
將遠端訪問策略應用於Windows使用者
完成以下步驟以應用遠端訪問策略:
-
在Administrative Tools中,開啟Internet Authentication Server控制檯,然後按一下Remote Access Policies。
-
按一下Specify the Conditions to Match上的Add按鈕並新增Service-type。選擇可用型別作為Framed。將其新增到所選型別,然後按確定。
-
按一下Specify the Conditions to Match上的Add按鈕並新增Framed Protocol。選擇可用型別為PPP。將其新增到所選型別,然後按確定。
-
按一下Specify the Conditions to Match上的Add按鈕並新增Windows-Groups,以新增使用者所屬的Windows組。選擇組並將其新增到所選型別。按OK。
-
在Allow Access if Dial-in Permission is Enabled Properties上,選擇Grant Remote Access Permission。
-
關閉控制檯。
為L2TP配置Windows 2000客戶端
完成以下步驟,以便為L2TP配置Windows 2000客戶端:
-
在Start Menu中選擇Settings,然後執行以下路徑之一:
-
控制面板>網路和撥號連線
或
-
網路和撥號連線> 新建連線
-
-
使用嚮導建立名為L2TP的連線。此連線通過Internet連線到專用網路。您還需要指定L2TP隧道網關的IP地址或名稱。
-
新連線出現在「Control Panel(控制面板)」下的「Network and Dial-up Connections(網路和撥號連線)」視窗中。在此處,按一下右鍵編輯屬性。
-
在Networking頁籤下,確保Type Of Server I Am Calling設定為L2TP。
-
如果計畫通過本地池或DHCP從網關為此客戶端分配動態內部地址,請選擇TCP/IP協定。確保將客戶端配置為自動獲取IP地址。您也可以自動發出DNS資訊。
-
Advanced按鈕允許您定義靜態WINS和DNS資訊。
-
Options頁籤允許您關閉IPSec,或為連線分配不同的策略。
-
在安全頁籤下,您可以定義使用者身份驗證引數,例如PAP、CHAP或MS-CHAP或Windows域登入。
-
-
配置連線後,您可以按兩下該連線以啟動登入螢幕,然後點選連線。
為Windows 2000客戶端禁用IPSec
-
編輯剛建立的撥號連線L2TP的屬性。按一下右鍵新連線L2TP以獲取L2TP Properties視窗。
-
在「Networking」頁籤下,按一下「Internet Protocol(TCP/IP)properties」。按兩下Advanced頁籤。轉到選項索引標籤,按一下IP安全性屬性,如果選擇Do not use IPSEC,請將其雙重檢查。
注意:Microsoft Windows 2000客戶端具有預設遠端訪問和策略代理服務,預設情況下會為L2TP流量建立策略。此預設策略不允許沒有IPSec和加密的L2TP流量。您可以通過編輯Microsoft客戶端登錄檔編輯器來禁用Microsoft預設行為。本節提供了編輯Windows登錄檔和為L2TP流量禁用IPSec預設策略的過程。有關編輯Windows登錄檔的資訊,請參閱Microsoft文檔。
使用登錄檔編輯器(Regedt32.exe)新增新的登錄檔項以禁用IPSec。有關詳細資訊,請參閱Microsoft的文檔或Regedt32.exe的Microsoft幫助主題。
您必須將ProhibitIpSec登錄檔值新增到L2TP或IPSec連線的每個基於Windows 2000的終端電腦,以防止建立L2TP和IPSec流量的自動過濾器。當ProhibitIpSec登錄檔值設定為1時,基於Windows 2000的電腦不會建立使用CA身份驗證的自動過濾器。而是檢查本地或Active Directory IPSec策略。若要將ProhibitIpSec登錄檔值新增到基於Windows 2000的電腦,請使用Regedt32.exe在登錄檔中查詢此項:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters
將此登錄檔值新增到此項:
Value Name: ProhibitIpSec Data Type: REG_DWORD Value: 1
注意:要使更改生效,必須重新啟動基於Windows 2000的電腦。有關詳細資訊,請參閱以下Microsoft文章:
-
Q258261 — 禁用用於L2TP的IPSEC策略
-
Q240262 — 如何使用預共用金鑰配置L2TP/IPSec連線
配置Cisco IOS for L2TP
這些配置概括了沒有IPSec的L2TP所需的命令。此基本配置工作正常後,您還可以配置IPSec。
| 安琪拉 |
|---|
Building configuration... Current configuration : 1595 bytes ! version 12.1 no service single-slot-reload-enable service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname angela ! logging rate-limit console 10 except errors !--- Enable AAA services here. aaa new-model aaa authentication login default group radius local aaa authentication login console none aaa authentication ppp default group radius local aaa authorization network default group radius local enable password ww ! memory-size iomem 30 ip subnet-zero ! ! no ip finger no ip domain-lookup ip host rund 172.17.247.195 ! ip audit notify log ip audit po max-events 100 ip address-pool local ! ! !--- Enable VPN/VPDN services and define groups and !--- specific variables required for the group. vpdn enable no vpdn logging ! vpdn-group L2TP_Windows 2000Client !--- Default L2TP VPDN group. !--- Allow the Router to accept incoming requests. accept-dialin protocol L2TP virtual-template 1 no L2TP tunnel authentication !--- Users are authenticated at the NAS or LNS !--- before the tunnel is established. This is not !--- required for client-initiated tunnels. ! ! call rsvp-sync ! ! ! ! ! ! ! controller E1 2/0 ! ! interface Loopback0 ip address 172.16.10.100 255.255.255.0 ! interface Ethernet0/0 ip address 10.200.20.2 255.255.255.0 half-duplex ! interface Virtual-Template1 ip unnumbered Loopback0 peer default ip address pool default ppp authentication ms-chap ! ip local pool default 172.16.10.1 172.16.10.10 ip classless ip route 0.0.0.0 0.0.0.0 10.200.20.1 ip route 192.168.1.0 255.255.255.0 10.200.20.250 no ip http server ! radius-server host 10.200.20.245 auth-port 1645 acct-port 1646 radius-server retransmit 3 radius-server key cisco ! dial-peer cor custom ! ! ! ! ! line con 0 exec-timeout 0 0 login authentication console transport input none line 33 50 modem InOut line aux 0 line vty 0 4 exec-timeout 0 0 password ww ! end angela# *Mar 12 23:10:54.176: L2TP: I SCCRQ from RSHANMUG-W2K1.cisco.com tnl 5 *Mar 12 23:10:54.176: Tnl 8663 L2TP: New tunnel created for remote RSHANMUG-W2K1.cisco.com, address 192.168.1.56 *Mar 12 23:10:54.176: Tnl 8663 L2TP: O SCCRP to RSHANMUG-W2K1.cisco.com tnlid 5 *Mar 12 23:10:54.180: Tnl 8663 L2TP: Tunnel state change from idle to wait-ctl-reply *Mar 12 23:10:54.352: Tnl 8663 L2TP: I SCCCN from RSHANMUG-W2K1.cisco.com tnl 5 *Mar 12 23:10:54.352: Tnl 8663 L2TP: Tunnel state change from wait-ctl-reply to established *Mar 12 23:10:54.352: Tnl 8663 L2TP: SM State established *Mar 12 23:10:54.356: Tnl 8663 L2TP: I ICRQ from RSHANMUG-W2K1.cisco.com tnl 5 *Mar 12 23:10:54.356: Tnl/Cl 8663/44 L2TP: Session FS enabled *Mar 12 23:10:54.356: Tnl/Cl 8663/44 L2TP: Session state change from idle to wait-connect *Mar 12 23:10:54.356: Tnl/Cl 8663/44 L2TP: New session created *Mar 12 23:10:54.356: Tnl/Cl 8663/44 L2TP: O ICRP to RSHANMUG-W2K1.cisco.com 5/1 *Mar 12 23:10:54.544: Tnl/Cl 8663/44 L2TP: I ICCN from RSHANMUG-W2K1.cisco.com tnl 5, cl 1 *Mar 12 23:10:54.544: Tnl/Cl 8663/44 L2TP: Session state change from wait-connect to established *Mar 12 23:10:54.544: Vi1 VPDN: Virtual interface created for *Mar 12 23:10:54.544: Vi1 PPP: Phase is DOWN, Setup [0 sess, 0 load] *Mar 12 23:10:54.544: Vi1 VPDN: Clone from Vtemplate 1 filterPPP=0 blocking *Mar 12 23:10:54.620: Tnl/Cl 8663/44 L2TP: Session with no hwidb *Mar 12 23:10:54.624: %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to up *Mar 12 23:10:54.624: Vi1 PPP: Using set call direction *Mar 12 23:10:54.624: Vi1 PPP: Treating connection as a callin *Mar 12 23:10:54.624: Vi1 PPP: Phase is ESTABLISHING, Passive Open [0 sess, 0 load] *Mar 12 23:10:54.624: Vi1 LCP: State is Listen *Mar 12 23:10:54.624: Vi1 VPDN: Bind interface direction=2 *Mar 12 23:10:56.556: Vi1 LCP: I CONFREQ [Listen] id 1 len 44 *Mar 12 23:10:56.556: Vi1 LCP: MagicNumber 0x595E7636 (0x0506595E7636) *Mar 12 23:10:56.556: Vi1 LCP: PFC (0x0702) *Mar 12 23:10:56.556: Vi1 LCP: ACFC (0x0802) *Mar 12 23:10:56.556: Vi1 LCP: Callback 6 (0x0D0306) *Mar 12 23:10:56.556: Vi1 LCP: MRRU 1614 (0x1104064E) *Mar 12 23:10:56.556: Vi1 LCP: EndpointDisc 1 Local *Mar 12 23:10:56.556: Vi1 LCP: (0x1317012E07E41982EB4EF790F1BF1862) *Mar 12 23:10:56.556: Vi1 LCP: (0x10D0AC00000002) *Mar 12 23:10:56.556: Vi1 AAA/AUTHOR/FSM: (0): LCP succeeds trivially *Mar 12 23:10:56.556: Vi1 LCP: O CONFREQ [Listen] id 1 len 15 *Mar 12 23:10:56.556: Vi1 LCP: AuthProto MS-CHAP (0x0305C22380) *Mar 12 23:10:56.556: Vi1 LCP: MagicNumber 0x4E1B09B8 (0x05064E1B09B8) *Mar 12 23:10:56.560: Vi1 LCP: O CONFREJ [Listen] id 1 len 34 *Mar 12 23:10:56.560: Vi1 LCP: Callback 6 (0x0D0306) *Mar 12 23:10:56.560: Vi1 LCP: MRRU 1614 (0x1104064E) *Mar 12 23:10:56.560: Vi1 LCP: EndpointDisc 1 Local *Mar 12 23:10:56.560: Vi1 LCP: (0x1317012E07E41982EB4EF790F1BF1862) *Mar 12 23:10:56.560: Vi1 LCP: (0x10D0AC00000002) *Mar 12 23:10:56.700: Vi1 LCP: I CONFACK [REQsent] id 1 len 15 *Mar 12 23:10:56.700: Vi1 LCP: AuthProto MS-CHAP (0x0305C22380) *Mar 12 23:10:56.704: Vi1 LCP: MagicNumber 0x4E1B09B8 (0x05064E1B09B8) *Mar 12 23:10:56.704: Vi1 LCP: I CONFREQ [ACKrcvd] id 2 len 14 *Mar 12 23:10:56.704: Vi1 LCP: MagicNumber 0x595E7636 (0x0506595E7636) *Mar 12 23:10:56.704: Vi1 LCP: PFC (0x0702) *Mar 12 23:10:56.704: Vi1 LCP: ACFC (0x0802) *Mar 12 23:10:56.704: Vi1 LCP: O CONFACK [ACKrcvd] id 2 len 14 *Mar 12 23:10:56.708: Vi1 LCP: MagicNumber 0x595E7636 (0x0506595E7636) *Mar 12 23:10:56.708: Vi1 LCP: PFC (0x0702) *Mar 12 23:10:56.708: Vi1 LCP: ACFC (0x0802) *Mar 12 23:10:56.708: Vi1 LCP: State is Open *Mar 12 23:10:56.708: Vi1 PPP: Phase is AUTHENTICATING, by this end [0 sess, 0 load] *Mar 12 23:10:56.708: Vi1 MS-CHAP: O CHALLENGE id 28 len 21 from angela *Mar 12 23:10:56.852: Vi1 LCP: I IDENTIFY [Open] id 3 len 18 magic 0x595E7636 MSRASV5.00 *Mar 12 23:10:56.872: Vi1 LCP: I IDENTIFY [Open] id 4 len 27 magic 0x595E7636 MSRAS-1- RSHANMUG-W2K1 *Mar 12 23:10:56.880: Vi1 MS-CHAP: I RESPONSE id 28 len 57 from tac *Mar 12 23:10:56.880: AAA: parse name=Virtual-Access1 idb type=21 tty=-1 *Mar 12 23:10:56.880: AAA: name=Virtual-Access1 flags=0x11 type=5 shelf=0 slot=0 adapter=0 port=1 channel=0 *Mar 12 23:10:56.884: AAA/MEMORY: create_user (0x6273D024) user='tac' ruser='' port='Virtual-Access1' rem_addr='' authen_type=MSCHAP service=PPP priv=1 *Mar 12 23:10:56.884: AAA/AUTHEN/START (3634835145): port='Virtual-Access1' list='' action=LOGIN service=PPP *Mar 12 23:10:56.884: AAA/AUTHEN/START (3634835145): using default list *Mar 12 23:10:56.884: AAA/AUTHEN/START (3634835145): Method=radius (radius) *Mar 12 23:10:56.884: RADIUS: ustruct sharecount=0 *Mar 12 23:10:56.884: RADIUS: Initial Transmit Virtual-Access1 id 173 10.200.20.245:1645, Access-Request, len 129 *Mar 12 23:10:56.884: Attribute 4 6 0AC81402 *Mar 12 23:10:56.884: Attribute 5 6 00000001 *Mar 12 23:10:56.884: Attribute 61 6 00000001 *Mar 12 23:10:56.884: Attribute 1 5 7461631A *Mar 12 23:10:56.884: Attribute 26 16 000001370B0A0053 *Mar 12 23:10:56.884: Attribute 26 58 0000013701341C01 *Mar 12 23:10:56.884: Attribute 6 6 00000002 *Mar 12 23:10:56.884: Attribute 7 6 00000001 *Mar 12 23:10:56.900: RADIUS: Received from id 173 10.200.20.245:1645, Access-Accept, len 116 *Mar 12 23:10:56.900: Attribute 7 6 00000001 *Mar 12 23:10:56.900: Attribute 6 6 00000002 *Mar 12 23:10:56.900: Attribute 25 32 502605A6 *Mar 12 23:10:56.900: Attribute 26 40 000001370C22F6D5 *Mar 12 23:10:56.900: Attribute 26 12 000001370A061C4E *Mar 12 23:10:56.900: AAA/AUTHEN (3634835145): status = PASS *Mar 12 23:10:56.900: Vi1 AAA/AUTHOR/LCP: Authorize LCP *Mar 12 23:10:56.900: Vi1 AAA/AUTHOR/LCP (1995716469): Port='Virtual-Access1' list='' service=NET *Mar 12 23:10:56.900: AAA/AUTHOR/LCP: Vi1 (1995716469) user='tac' *Mar 12 23:10:56.900: Vi1 AAA/AUTHOR/LCP (1995716469): send AV service=ppp *Mar 12 23:10:56.900: Vi1 AAA/AUTHOR/LCP (1995716469): send AV protocol=lcp *Mar 12 23:10:56.900: Vi1 AAA/AUTHOR/LCP (1995716469): found list default *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/LCP (1995716469): Method=radius (radius) *Mar 12 23:10:56.904: RADIUS: unrecognized Microsoft VSA type 10 *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR (1995716469): Post authorization status = PASS_REPL *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/LCP: Processing AV service=ppp *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/LCP: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:10:56.904: Vi1 MS-CHAP: O SUCCESS id 28 len 4 *Mar 12 23:10:56.904: Vi1 PPP: Phase is UP [0 sess, 0 load] *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/FSM: (0): Can we start IPCP? *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/FSM (2094713042): Port='Virtual-Access1' list='' service=NET *Mar 12 23:10:56.904: AAA/AUTHOR/FSM: Vi1 (2094713042) user='tac' *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/FSM (2094713042): send AV service=ppp *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/FSM (2094713042): send AV protocol=ip *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/FSM (2094713042): found list default *Mar 12 23:10:56.904: Vi1 AAA/AUTHOR/FSM (2094713042): Method=radius (radius) *Mar 12 23:10:56.908: RADIUS: unrecognized Microsoft VSA type 10 *Mar 12 23:10:56.908: Vi1 AAA/AUTHOR (2094713042): Post authorization status = PASS_REPL *Mar 12 23:10:56.908: Vi1 AAA/AUTHOR/FSM: We can start IPCP *Mar 12 23:10:56.908: Vi1 IPCP: O CONFREQ [Closed] id 1 len 10 *Mar 12 23:10:56.908: Vi1 IPCP: Address 172.16.10.100 (0x0306AC100A64) *Mar 12 23:10:57.040: Vi1 CCP: I CONFREQ [Not negotiated] id 5 len 10 *Mar 12 23:10:57.040: Vi1 CCP: MS-PPC supported bits 0x01000001 (0x120601000001) *Mar 12 23:10:57.040: Vi1 LCP: O PROTREJ [Open] id 2 len 16 protocol CCP (0x80FD0105000A120601000001) *Mar 12 23:10:57.052: Vi1 IPCP: I CONFREQ [REQsent] id 6 len 34 *Mar 12 23:10:57.052: Vi1 IPCP: Address 0.0.0.0 (0x030600000000) *Mar 12 23:10:57.052: Vi1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000) *Mar 12 23:10:57.052: Vi1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000) *Mar 12 23:10:57.052: Vi1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000) *Mar 12 23:10:57.052: Vi1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000) *Mar 12 23:10:57.052: Vi1 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 0.0.0.0 *Mar 12 23:10:57.056: Vi1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 12 23:10:57.056: Vi1 AAA/AUTHOR/IPCP: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:10:57.056: Vi1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 12 23:10:57.056: Vi1 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 0.0.0.0 *Mar 12 23:10:57.056: Vi1 IPCP: Pool returned 172.16.10.1 *Mar 12 23:10:57.056: Vi1 IPCP: O CONFREJ [REQsent] id 6 len 28 *Mar 12 23:10:57.056: Vi1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000) *Mar 12 23:10:57.056: Vi1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000) *Mar 12 23:10:57.056: Vi1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000) *Mar 12 23:10:57.056: Vi1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000) *Mar 12 23:10:57.060: Vi1 IPCP: I CONFACK [REQsent] id 1 len 10 *Mar 12 23:10:57.060: Vi1 IPCP: Address 172.16.10.100 (0x0306AC100A64) *Mar 12 23:10:57.192: Vi1 IPCP: I CONFREQ [ACKrcvd] id 7 len 10 *Mar 12 23:10:57.192: Vi1 IPCP: Address 0.0.0.0 (0x030600000000) *Mar 12 23:10:57.192: Vi1 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 172.16.10.1 *Mar 12 23:10:57.192: Vi1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 12 23:10:57.192: Vi1 AAA/AUTHOR/IPCP: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:10:57.192: Vi1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 12 23:10:57.192: Vi1 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 172.16.10.1 *Mar 12 23:10:57.192: Vi1 IPCP: O CONFNAK [ACKrcvd] id 7 len 10 *Mar 12 23:10:57.192: Vi1 IPCP: Address 172.16.10.1 (0x0306AC100A01) *Mar 12 23:10:57.324: Vi1 IPCP: I CONFREQ [ACKrcvd] id 8 len 10 *Mar 12 23:10:57.324: Vi1 IPCP: Address 172.16.10.1 (0x0306AC100A01) *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR/IPCP: Start. Her address 172.16.10.1, we want 172.16.10.1 *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR/IPCP (413757991): Port='Virtual-Access1' list='' service=NET *Mar 12 23:10:57.324: AAA/AUTHOR/IPCP: Vi1 (413757991) user='tac' *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR/IPCP (413757991): send AV service=ppp *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR/IPCP (413757991): send AV protocol=ip *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR/IPCP (413757991): send AV addr*172.16.10.1 *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR/IPCP (413757991): found list default *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR/IPCP (413757991): Method=radius (radius) *Mar 12 23:10:57.324: RADIUS: unrecognized Microsoft VSA type 10 *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR (413757991): Post authorization status = PASS_REPL *Mar 12 23:10:57.324: Vi1 AAA/AUTHOR/IPCP: Reject 172.16.10.1, using 172.16.10.1 *Mar 12 23:10:57.328: Vi1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 12 23:10:57.328: Vi1 AAA/AUTHOR/IPCP: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:10:57.328: Vi1 AAA/AUTHOR/IPCP: Processing AV addr*172.16.10.1 *Mar 12 23:10:57.328: Vi1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 12 23:10:57.328: Vi1 AAA/AUTHOR/IPCP: Done. Her address 172.16.10.1, we want 172.16.10.1 *Mar 12 23:10:57.328: Vi1 IPCP: O CONFACK [ACKrcvd] id 8 len 10 *Mar 12 23:10:57.328: Vi1 IPCP: Address 172.16.10.1 (0x0306AC100A01) *Mar 12 23:10:57.328: Vi1 IPCP: State is Open *Mar 12 23:10:57.332: Vi1 IPCP: Install route to 172.16.10.1 *Mar 12 23:10:57.904: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up *Mar 12 23:11:06.324: Vi1 LCP: I ECHOREP [Open] id 1 len 12 magic 0x595E7636 *Mar 12 23:11:06.324: Vi1 LCP: Received id 1, sent id 1, line up |
angela#show vpdn L2TP Tunnel and Session Information Total tunnels 1 sessions 1 LocID RemID Remote Name State Remote Address Port Sessions 8663 5 RSHANMUG-W2K1.c est 192.168.1.56 1701 1 LocID RemID TunID Intf Username State Last Chg Fastswitch 44 1 8663 Vi1 tac est 00:00:18 enabled %No active L2F tunnels %No active PPTP tunnels %No active PPPoE tunnels *Mar 12 23:11:16.332: Vi1 LCP: I ECHOREP [Open] id 2 len 12 magic 0x595E7636 *Mar 12 23:11:16.332: Vi1 LCP: Received id 2, sent id 2, line upsh caller ip Line User IP Address Local Number Remote Number <-> Vi1 tac 172.16.10.1 - - in angela#show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 10.200.20.1 to network 0.0.0.0 172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks C 172.16.10.0/24 is directly connected, Loopback0 C 172.16.10.1/32 is directly connected, Virtual-Access1 10.0.0.0/24 is subnetted, 1 subnets C 10.200.20.0 is directly connected, Ethernet0/0 S 192.168.1.0/24 [1/0] via 10.200.20.250 S* 0.0.0.0/0 [1/0] via 10.200.20.1 *Mar 12 23:11:26.328: Vi1 LCP: I ECHOREP [Open] id 3 len 12 magic 0x595E7636 *Mar 12 23:11:26.328: Vi1 LCP: Received id 3, sent id 3, line up172.16.10.1 angela#ping 172.16.10.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.10.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 156/160/168 ms
啟用加密
在interface virtual-template 1下新增ppp encrypt mppe 40命令。確保在Microsoft客戶端中也選擇了加密。
*Mar 12 23:27:36.608: L2TP: I SCCRQ from RSHANMUG-W2K1.cisco.com tnl 13 *Mar 12 23:27:36.608: Tnl 31311 L2TP: New tunnel created for remote RSHANMUG-W2K1.cisco.com, address 192.168.1.56 *Mar 12 23:27:36.608: Tnl 31311 L2TP: O SCCRP to RSHANMUG-W2K1.cisco.com tnlid 13 *Mar 12 23:27:36.612: Tnl 31311 L2TP: Tunnel state change from idle to wait-ctl-reply *Mar 12 23:27:36.772: Tnl 31311 L2TP: I SCCCN from RSHANMUG-W2K1.cisco.com tnl 13 *Mar 12 23:27:36.772: Tnl 31311 L2TP: Tunnel state change from wait-ctl-reply to established *Mar 12 23:27:36.776: Tnl 31311 L2TP: SM State established *Mar 12 23:27:36.780: Tnl 31311 L2TP: I ICRQ from RSHANMUG-W2K1.cisco.com tnl 13 *Mar 12 23:27:36.780: Tnl/Cl 31311/52 L2TP: Session FS enabled *Mar 12 23:27:36.780: Tnl/Cl 31311/52 L2TP: Session state change from idle to wait-connect *Mar 12 23:27:36.780: Tnl/Cl 31311/52 L2TP: New session created *Mar 12 23:27:36.780: Tnl/Cl 31311/52 L2TP: O ICRP to RSHANMUG-W2K1.cisco.com 13/1 *Mar 12 23:27:36.924: Tnl/Cl 31311/52 L2TP: I ICCN from RSHANMUG-W2K1.cisco.com tnl 13, cl 1 *Mar 12 23:27:36.928: Tnl/Cl 31311/52 L2TP: Session state change from wait-connect to established *Mar 12 23:27:36.928: Vi1 VPDN: Virtual interface created for *Mar 12 23:27:36.928: Vi1 PPP: Phase is DOWN, Setup [0 sess, 0 load] *Mar 12 23:27:36.928: Vi1 VPDN: Clone from Vtemplate 1 filterPPP=0 blocking *Mar 12 23:27:36.972: Tnl/Cl 31311/52 L2TP: Session with no hwidb *Mar 12 23:27:36.976: %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to up *Mar 12 23:27:36.976: Vi1 PPP: Using set call direction *Mar 12 23:27:36.976: Vi1 PPP: Treating connection as a callin *Mar 12 23:27:36.976: Vi1 PPP: Phase is ESTABLISHING, Passive Open [0 sess, 0 load] *Mar 12 23:27:36.976: Vi1 LCP: State is Listen *Mar 12 23:27:36.976: Vi1 VPDN: Bind interface direction=2 *Mar 12 23:27:38.976: Vi1 LCP: TIMEout: State Listen *Mar 12 23:27:38.976: Vi1 AAA/AUTHOR/FSM: (0): LCP succeeds trivially *Mar 12 23:27:38.976: Vi1 LCP: O CONFREQ [Listen] id 1 len 15 *Mar 12 23:27:38.976: Vi1 LCP: AuthProto MS-CHAP (0x0305C22380) *Mar 12 23:27:38.976: Vi1 LCP: MagicNumber 0x4E2A5593 (0x05064E2A5593) *Mar 12 23:27:38.984: Vi1 LCP: I CONFREQ [REQsent] id 1 len 44 *Mar 12 23:27:38.984: Vi1 LCP: MagicNumber 0x4B4817ED (0x05064B4817ED) *Mar 12 23:27:38.984: Vi1 LCP: PFC (0x0702) *Mar 12 23:27:38.984: Vi1 LCP: ACFC (0x0802) *Mar 12 23:27:38.984: Vi1 LCP: Callback 6 (0x0D0306) *Mar 12 23:27:38.984: Vi1 LCP: MRRU 1614 (0x1104064E) *Mar 12 23:27:38.984: Vi1 LCP: EndpointDisc 1 Local *Mar 12 23:27:38.984: Vi1 LCP: (0x1317012E07E41982EB4EF790F1BF1862) *Mar 12 23:27:38.984: Vi1 LCP: (0x10D0AC0000000A) *Mar 12 23:27:38.984: Vi1 LCP: O CONFREJ [REQsent] id 1 len 34 *Mar 12 23:27:38.984: Vi1 LCP: Callback 6 (0x0D0306) *Mar 12 23:27:38.984: Vi1 LCP: MRRU 1614 (0x1104064E) *Mar 12 23:27:38.984: Vi1 LCP: EndpointDisc 1 Local *Mar 12 23:27:38.988: Vi1 LCP: (0x1317012E07E41982EB4EF790F1BF1862) *Mar 12 23:27:38.988: Vi1 LCP: (0x10D0AC0000000A) *Mar 12 23:27:39.096: Vi1 LCP: I CONFACK [REQsent] id 1 len 15 *Mar 12 23:27:39.096: Vi1 LCP: AuthProto MS-CHAP (0x0305C22380) *Mar 12 23:27:39.096: Vi1 LCP: MagicNumber 0x4E2A5593 (0x05064E2A5593) *Mar 12 23:27:39.128: Vi1 LCP: I CONFREQ [ACKrcvd] id 2 len 14 *Mar 12 23:27:39.128: Vi1 LCP: MagicNumber 0x4B4817ED (0x05064B4817ED) *Mar 12 23:27:39.128: Vi1 LCP: PFC (0x0702) *Mar 12 23:27:39.128: Vi1 LCP: ACFC (0x0802) *Mar 12 23:27:39.128: Vi1 LCP: O CONFACK [ACKrcvd] id 2 len 14 *Mar 12 23:27:39.128: Vi1 LCP: MagicNumber 0x4B4817ED (0x05064B4817ED) *Mar 12 23:27:39.128: Vi1 LCP: PFC (0x0702) *Mar 12 23:27:39.128: Vi1 LCP: ACFC (0x0802) *Mar 12 23:27:39.128: Vi1 LCP: State is Open *Mar 12 23:27:39.128: Vi1 PPP: Phase is AUTHENTICATING, by this end [0 sess, 0 load] *Mar 12 23:27:39.128: Vi1 MS-CHAP: O CHALLENGE id 32 len 21 from angela *Mar 12 23:27:39.260: Vi1 LCP: I IDENTIFY [Open] id 3 len 18 magic 0x4B4817ED MSRASV5.00 *Mar 12 23:27:39.288: Vi1 LCP: I IDENTIFY [Open] id 4 len 27 magic 0x4B4817ED MSRAS-1- RSHANMUG-W2K1 *Mar 12 23:27:39.296: Vi1 MS-CHAP: I RESPONSE id 32 len 57 from tac *Mar 12 23:27:39.296: AAA: parse name=Virtual-Access1 idb type=21 tty=-1 *Mar 12 23:27:39.296: AAA: name=Virtual-Access1 flags=0x11 type=5 shelf=0 slot=0 adapter=0 port=1 channel=0 *Mar 12 23:27:39.296: AAA/MEMORY: create_user (0x6273D528) user='tac' ruser='' port='Virtual-Access1' rem_addr='' authen_type=MSCHAP service=PPP priv=1 *Mar 12 23:27:39.296: AAA/AUTHEN/START (2410248116): port='Virtual-Access1' list='' action=LOGIN service=PPP *Mar 12 23:27:39.296: AAA/AUTHEN/START (2410248116): using default list *Mar 12 23:27:39.296: AAA/AUTHEN/START (2410248116): Method=radius (radius) *Mar 12 23:27:39.296: RADIUS: ustruct sharecount=0 *Mar 12 23:27:39.300: RADIUS: Initial Transmit Virtual-Access1 id 181 10.200.20.245:1645, Access-Request, len 129 *Mar 12 23:27:39.300: Attribute 4 6 0AC81402 *Mar 12 23:27:39.300: Attribute 5 6 00000001 *Mar 12 23:27:39.300: Attribute 61 6 00000001 *Mar 12 23:27:39.300: Attribute 1 5 7461631A *Mar 12 23:27:39.300: Attribute 26 16 000001370B0AFC72 *Mar 12 23:27:39.300: Attribute 26 58 0000013701342001 *Mar 12 23:27:39.300: Attribute 6 6 00000002 *Mar 12 23:27:39.300: Attribute 7 6 00000001 *Mar 12 23:27:39.312: RADIUS: Received from id 181 10.200.20.245:1645, Access-Accept, len 116 *Mar 12 23:27:39.312: Attribute 7 6 00000001 *Mar 12 23:27:39.312: Attribute 6 6 00000002 *Mar 12 23:27:39.312: Attribute 25 32 502E05AE *Mar 12 23:27:39.312: Attribute 26 40 000001370C225042 *Mar 12 23:27:39.312: Attribute 26 12 000001370A06204E *Mar 12 23:27:39.312: AAA/AUTHEN (2410248116): status = PASS *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/LCP: Authorize LCP *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/LCP (2365724222): Port='Virtual-Access1' list='' service=NET *Mar 12 23:27:39.316: AAA/AUTHOR/LCP: Vi1 (2365724222) user='tac' *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/LCP (2365724222): send AV service=ppp *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/LCP (2365724222): send AV protocol=lcp *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/LCP (2365724222): found list default *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/LCP (2365724222): Method=radius (radius) *Mar 12 23:27:39.316: RADIUS: unrecognized Microsoft VSA type 10 *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR (2365724222): Post authorization status = PASS_REPL *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/LCP: Processing AV service=ppp *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/LCP: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:27:39.316: Vi1 MS-CHAP: O SUCCESS id 32 len 4 *Mar 12 23:27:39.316: Vi1 PPP: Phase is UP [0 sess, 0 load] *Mar 12 23:27:39.316: Vi1 AAA/AUTHOR/FSM: (0): Can we start IPCP? *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR/FSM (1499311111): Port='Virtual-Access1' list='' service=NET *Mar 12 23:27:39.320: AAA/AUTHOR/FSM: Vi1 (1499311111) user='tac' *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR/FSM (1499311111): send AV service=ppp *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR/FSM (1499311111): send AV protocol=ip *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR/FSM (1499311111): found list default *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR/FSM (1499311111): Method=radius (radius) *Mar 12 23:27:39.320: RADIUS: unrecognized Microsoft VSA type 10 *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR (1499311111): Post authorization status = PASS_REPL *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR/FSM: We can start IPCP *Mar 12 23:27:39.320: Vi1 IPCP: O CONFREQ [Closed] id 1 len 10 *Mar 12 23:27:39.320: Vi1 IPCP: Address 172.16.10.100 (0x0306AC100A64) *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR/FSM: (0): Can we start CCP? *Mar 12 23:27:39.320: Vi1 AAA/AUTHOR/FSM (327346364): Port='Virtual-Access1' list='' service=NET *Mar 12 23:27:39.324: AAA/AUTHOR/FSM: Vi1 (327346364) user='tac' *Mar 12 23:27:39.324: Vi1 AAA/AUTHOR/FSM (327346364): send AV service=ppp *Mar 12 23:27:39.324: Vi1 AAA/AUTHOR/FSM (327346364): send AV protocol=ccp *Mar 12 23:27:39.324: Vi1 AAA/AUTHOR/FSM (327346364): found list default *Mar 12 23:27:39.324: Vi1 AAA/AUTHOR/FSM (327346364): Method=radius (radius) *Mar 12 23:27:39.324: RADIUS: unrecognized Microsoft VSA type 10 *Mar 12 23:27:39.324: Vi1 AAA/AUTHOR (327346364): Post authorization status = PASS_REPL *Mar 12 23:27:39.324: Vi1 AAA/AUTHOR/FSM: We can start CCP *Mar 12 23:27:39.324: Vi1 CCP: O CONFREQ [Closed] id 1 len 10 *Mar 12 23:27:39.324: Vi1 CCP: MS-PPC supported bits 0x01000020 (0x120601000020) *Mar 12 23:27:39.460: Vi1 CCP: I CONFREQ [REQsent] id 5 len 10 *Mar 12 23:27:39.460: Vi1 CCP: MS-PPC supported bits 0x01000001 (0x120601000001) *Mar 12 23:27:39.460: Vi1 AAA/AUTHOR/FSM: Check for unauthorized mandatory AV's *Mar 12 23:27:39.460: Vi1 AAA/AUTHOR/FSM: Processing AV service=ppp *Mar 12 23:27:39.460: Vi1 AAA/AUTHOR/FSM: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:27:39.460: Vi1 AAA/AUTHOR/FSM: Succeeded *Mar 12 23:27:39.464: Vi1 CCP: O CONFNAK [REQsent] id 5 len 10 *Mar 12 23:27:39.464: Vi1 CCP: MS-PPC supported bits 0x01000020 (0x120601000020) *Mar 12 23:27:39.472: Vi1 IPCP: I CONFREQ [REQsent] id 6 len 34 *Mar 12 23:27:39.472: Vi1 IPCP: Address 0.0.0.0 (0x030600000000) *Mar 12 23:27:39.472: Vi1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000) *Mar 12 23:27:39.472: Vi1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000) *Mar 12 23:27:39.472: Vi1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000) *Mar 12 23:27:39.472: Vi1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000) *Mar 12 23:27:39.472: Vi1 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 0.0.0.0 *Mar 12 23:27:39.472: Vi1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 12 23:27:39.472: Vi1 AAA/AUTHOR/IPCP: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:27:39.472: Vi1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 12 23:27:39.472: Vi1 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 0.0.0.0 *Mar 12 23:27:39.472: Vi1 IPCP: Pool returned 172.16.10.1 *Mar 12 23:27:39.476: Vi1 IPCP: O CONFREJ [REQsent] id 6 len 28 *Mar 12 23:27:39.476: Vi1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000) *Mar 12 23:27:39.476: Vi1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000) *Mar 12 23:27:39.476: Vi1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000) *Mar 12 23:27:39.476: Vi1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000) *Mar 12 23:27:39.480: Vi1 IPCP: I CONFACK [REQsent] id 1 len 10 *Mar 12 23:27:39.484: Vi1 IPCP: Address 172.16.10.100 (0x0306AC100A64) *Mar 12 23:27:39.488: Vi1 CCP: I CONFACK [REQsent] id 1 len 10 *Mar 12 23:27:39.488: Vi1 CCP: MS-PPC supported bits 0x01000020 (0x120601000020) *Mar 12 23:27:39.596: Vi1 CCP: I CONFREQ [ACKrcvd] id 7 len 10 *Mar 12 23:27:39.596: Vi1 CCP: MS-PPC supported bits 0x01000020 (0x120601000020) *Mar 12 23:27:39.596: Vi1 AAA/AUTHOR/FSM: Check for unauthorized mandatory AV's *Mar 12 23:27:39.596: Vi1 AAA/AUTHOR/FSM: Processing AV service=ppp *Mar 12 23:27:39.596: Vi1 AAA/AUTHOR/FSM: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:27:39.596: Vi1 AAA/AUTHOR/FSM: Succeeded *Mar 12 23:27:39.596: Vi1 CCP: O CONFACK [ACKrcvd] id 7 len 10 *Mar 12 23:27:39.596: Vi1 CCP: MS-PPC supported bits 0x01000020 (0x120601000020) *Mar 12 23:27:39.596: Vi1 CCP: State is Open *Mar 12 23:27:39.600: Vi1 MPPE: Generate keys using RADIUS data *Mar 12 23:27:39.600: Vi1 MPPE: Initialize keys *Mar 12 23:27:39.600: Vi1 MPPE: [40 bit encryption] [stateless mode] *Mar 12 23:27:39.620: Vi1 IPCP: I CONFREQ [ACKrcvd] id 8 len 10 *Mar 12 23:27:39.620: Vi1 IPCP: Address 0.0.0.0 (0x030600000000) *Mar 12 23:27:39.620: Vi1 AAA/AUTHOR/IPCP: Start. Her address 0.0.0.0, we want 172.16.10.1 *Mar 12 23:27:39.620: Vi1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 12 23:27:39.620: Vi1 AAA/AUTHOR/IPCP: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:27:39.620: Vi1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 12 23:27:39.620: Vi1 AAA/AUTHOR/IPCP: Done. Her address 0.0.0.0, we want 172.16.10.1 *Mar 12 23:27:39.624: Vi1 IPCP: O CONFNAK [ACKrcvd] id 8 len 10 *Mar 12 23:27:39.624: Vi1 IPCP: Address 172.16.10.1 (0x0306AC100A01) *Mar 12 23:27:39.756: Vi1 IPCP: I CONFREQ [ACKrcvd] id 9 len 10 *Mar 12 23:27:39.756: Vi1 IPCP: Address 172.16.10.1 (0x0306AC100A01) *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR/IPCP: Start. Her address 172.16.10.1, we want 172.16.10.1 *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR/IPCP (2840659706): Port='Virtual-Access1' list='' service=NET *Mar 12 23:27:39.756: AAA/AUTHOR/IPCP: Vi1 (2840659706) user='tac' *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR/IPCP (2840659706): send AV service=ppp *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR/IPCP (2840659706): send AV protocol=ip *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR/IPCP (2840659706): send AV addr*172.16.10.1 *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR/IPCP (2840659706): found list default *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR/IPCP (2840659706): Method=radius (radius) *Mar 12 23:27:39.756: RADIUS: unrecognized Microsoft VSA type 10 *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR (2840659706): Post authorization status = PASS_REPL *Mar 12 23:27:39.756: Vi1 AAA/AUTHOR/IPCP: Reject 172.16.10.1, using 172.16.10.1 *Mar 12 23:27:39.760: Vi1 AAA/AUTHOR/IPCP: Processing AV service=ppp *Mar 12 23:27:39.760: Vi1 AAA/AUTHOR/IPCP: Processing AV mschap_mppe_keys*1p1T11=1v1O1~11a1W11151\1V1M1#11Z1`1k1}111 *Mar 12 23:27:39.760: Vi1 AAA/AUTHOR/IPCP: Processing AV addr*172.16.10.1 *Mar 12 23:27:39.760: Vi1 AAA/AUTHOR/IPCP: Authorization succeeded *Mar 12 23:27:39.760: Vi1 AAA/AUTHOR/IPCP: Done. Her address 172.16.10.1, we want 172.16.10.1 *Mar 12 23:27:39.760: Vi1 IPCP: O CONFACK [ACKrcvd] id 9 len 10 *Mar 12 23:27:39.760: Vi1 IPCP: Address 172.16.10.1 (0x0306AC100A01) *Mar 12 23:27:39.760: Vi1 IPCP: State is Open *Mar 12 23:27:39.764: Vi1 IPCP: Install route to 172.16.10.1 *Mar 12 23:27:40.316: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up *Mar 12 23:27:46.628: Vi1 LCP: I ECHOREP [Open] id 1 len 12 magic 0x4B4817ED *Mar 12 23:27:46.628: Vi1 LCP: Received id 1, sent id 1, line up *Mar 12 23:27:56.636: Vi1 LCP: I ECHOREP [Open] id 2 len 12 magic 0x4B4817ED *Mar 12 23:27:56.636: Vi1 LCP: Received id 2, sent id 2, line upcaller ip Line User IP Address Local Number Remote Number <-> Vi1 tac 172.16.10.1 - - in angela#show ppp mppe virtual-Access 1 Interface Virtual-Access1 (current connection) Software encryption, 40 bit encryption, Stateless mode packets encrypted = 0 packets decrypted = 16 sent CCP resets = 0 receive CCP resets = 0 next tx coherency = 0 next rx coherency = 16 tx key changes = 0 rx key changes = 16 rx pkt dropped = 0 rx out of order pkt= 0 rx missed packets = 0 *Mar 12 23:28:06.604: Vi1 LCP: I ECHOREP [Open] id 3 len 12 magic 0x4B4817ED *Mar 12 23:28:06.604: Vi1 LCP: Received id 3, sent id 3, line up angela#ping 172.16.10.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.10.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 188/196/204 ms angela#show ppp mppe virtual-Access 1 Interface Virtual-Access1 (current connection) Software encryption, 40 bit encryption, Stateless mode packets encrypted = 5 packets decrypted = 22 sent CCP resets = 0 receive CCP resets = 0 next tx coherency = 5 next rx coherency = 22 tx key changes = 5 rx key changes = 22 rx pkt dropped = 0 rx out of order pkt= 0 rx missed packets = 0 angela#ping 172.16.10.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.10.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 184/200/232 ms angela#ping 172.16.10.1sh ppp mppe virtual-Access 1 Interface Virtual-Access1 (current connection) Software encryption, 40 bit encryption, Stateless mode packets encrypted = 10 packets decrypted = 28 sent CCP resets = 0 receive CCP resets = 0 next tx coherency = 10 next rx coherency = 28 tx key changes = 10 rx key changes = 28 rx pkt dropped = 0 rx out of order pkt= 0 rx missed packets = 0 angela#
debug和show命令
使用 debug 指令之前,請先參閱有關 Debug 指令的重要資訊。
輸出直譯器工具(僅供已註冊客戶使用)(OIT)支援某些show命令。使用OIT檢視show命令輸出的分析。
如果操作失敗,則最小的debug命令包括:
-
debug aaa authentication — 顯示有關AAA/TACACS+身份驗證的資訊。
-
debug aaa authorization — 顯示有關AAA/TACACS+授權的資訊。
-
debug ppp negotiation — 顯示在PPP啟動期間傳輸的PPP資料包,其中協商了PPP選項。
-
debug ppp authentication — 顯示身份驗證協定消息,包括質詢身份驗證協定(CHAP)資料包交換和密碼身份驗證協定(PAP)交換。
-
debug radius — 顯示與RADIUS關聯的詳細調試資訊。
如果驗證有效,但Microsoft點對點加密(MPPE)加密出現問題,請使用以下命令之一:
-
debug ppp mppe packet — 顯示所有傳入傳出MPPE流量。
-
debug ppp mppe event — 顯示關鍵MPPE事件。
-
debug ppp mppe detailed — 顯示詳細的MPPE資訊。
-
debug vpdn l2x-packets — 顯示有關2級轉發(L2F)協定標頭和狀態的消息。
-
debug vpdn events — 顯示有關屬於正常隧道建立或關閉一部分的事件的消息。
-
debug vpdn errors — 顯示阻止隧道建立的錯誤或導致已建立的隧道關閉的錯誤。
-
debug vpdn packets — 顯示交換的每個協定資料包。此選項可能導致大量調試消息,通常只能在具有單個活動會話的調試機箱上使用。
-
show vpdn — 顯示有關虛擬專用撥接網路(VPDN)中作用中L2F通訊協定通道和訊息識別符號的資訊。
您還可以使用show vpdn ?命令檢視其他vpdn特定的show命令。
分割通道
假設網關路由器是Internet服務提供商(ISP)路由器。當PC上啟動點對點通道通訊協定(PPTP)通道時,PPTP路由所安裝的度量高於之前的預設值,因此會失去網際網路連線。為了解決此問題,請修改Microsoft路由以刪除預設路由並重新安裝預設路由(需要知道分配了PPTP客戶端的IP地址;目前的範例為172.16.10.1):
route delete 0.0.0.0 route add 0.0.0.0 mask 0.0.0.0 192.168.1.47 metric 1 route add 172.16.10.1 mask 255.255.255.0 192.168.1.47 metric 1
疑難排解
本節提供的資訊可用於對組態進行疑難排解。
問題1:未禁用IPSec
症狀
PC使用者看到以下消息:
Error connecting to L2TP: Error 781: The encryption attempt failed because no valid certificate was found.
解決方案
轉到Virtual Private Connection視窗的Properties部分,然後按一下Security頁籤。禁用Require Data Encryption選項。
問題2:錯誤789
症狀
L2TP連線嘗試失敗,因為安全層在與遠端電腦的初始協商期間遇到處理錯誤。
由於L2TP不提供加密,因此Microsoft遠端訪問和策略代理服務會建立用於L2TP流量的策略。這適用於Microsoft Windows 2000 Advanced Server、Microsoft Windows 2000 Server和Microsoft Windows 2000 Professional。
解決方案
使用登錄檔編輯器(Regedt32.exe)新增新的登錄檔項以禁用IPSec。有關Regedt32.exe,請參閱Microsoft文檔或Microsoft幫助主題。
您必須將ProhibitIpSec登錄檔值新增到L2TP或IPSec連線的每個基於Windows 2000的終端電腦,以防止建立L2TP和IPSec流量的自動過濾器。當ProhibitIpSec登錄檔值設定為1時,基於Windows 2000的電腦不會建立使用CA身份驗證的自動過濾器。而是檢查本地或Active Directory IPSec策略。若要將ProhibitIpSec登錄檔值新增到基於Windows 2000的電腦,請使用Regedt32.exe在登錄檔中查詢此項:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters
將此登錄檔值新增到此項:
Value Name: ProhibitIpSec Data Type: REG_DWORD Value: 1
注意:要使更改生效,必須重新啟動基於Windows 2000的電腦。
問題3:通道驗證問題
建立通道之前,使用者在NAS或LNS進行驗證。客戶端啟動的隧道(如來自Microsoft客戶端的L2TP)不需要此功能。
PC使用者看到以下消息:
Connecting to 10.200.20.2.. Error 651: The modem(or other connecting device) has reported an error. Router debugs: *Mar 12 23:03:47.124: L2TP: I SCCRQ from RSHANMUG-W2K1.cisco.com tnl 1 *Mar 12 23:03:47.124: Tnl 30107 L2TP: New tunnel created for remote RSHANMUG-W2K1.cisco.com, address 192.168.1.56 *Mar 12 23:03:47.124: Tnl 30107 L2TP: O SCCRP to RSHANMUG-W2K1.cisco.com tnlid 1 *Mar 12 23:03:47.124: Tnl 30107 L2TP: Tunnel state change from idle to wait-ctl-reply *Mar 12 23:03:47.308: Tnl 30107 L2TP: I SCCCN from RSHANMUG-W2K1.cisco.com tnl 1 *Mar 12 23:03:47.308: Tnl 30107 L2TP: Got a Challenge Response in SCCCN from RSHANMUG-W2K1.cisco.com *Mar 12 23:03:47.308: AAA: parse name= idb type=-1 tty=-1 *Mar 12 23:03:47.308: AAA/MEMORY: create_user (0x6273D528) user='angela' ruser='' port='' rem_addr='' authen_type=CHAP service=PPP priv=1 *Mar 12 23:03:47.308: AAA/AUTHEN/START (4077585132): port='' list='default' action=SENDAUTH service=PPP *Mar 12 23:03:47.308: AAA/AUTHEN/START (4077585132): found list default *Mar 12 23:03:47.308: AAA/AUTHEN/START (4077585132): Method=radius (radius) *Mar 12 23:03:47.308: AAA/AUTHEN/SENDAUTH (4077585132): no authenstruct hwidb *Mar 12 23:03:47.308: AAA/AUTHEN/SENDAUTH (4077585132): Failed sendauthen for angela *Mar 12 23:03:47.308: AAA/AUTHEN (4077585132): status = FAIL *Mar 12 23:03:47.308: AAA/AUTHEN/START (4077585132): Method=LOCAL *Mar 12 23:03:47.308: AAA/AUTHEN (4077585132): SENDAUTH no password for angela *Mar 12 23:03:47.308: AAA/AUTHEN (4077585132): status = ERROR *Mar 12 23:03:47.308: AAA/AUTHEN/START (4077585132): no methods left to try *Mar 12 23:03:47.308: AAA/AUTHEN (4077585132): status = ERROR *Mar 12 23:03:47.308: AAA/AUTHEN/START (4077585132): failed to authenticate *Mar 12 23:03:47.308: VPDN: authentication failed, couldn't find user information for angela *Mar 12 23:03:47.308: AAA/MEMORY: free_user (0x6273D528) user='angela' ruser='' port='' rem_addr='' authen_type=CHAP service=PPP priv=1 *Mar 12 23:03:47.312: Tnl 30107 L2TP: O StopCCN to RSHANMUG-W2K1.cisco.com tnlid 1 *Mar 12 23:03:47.312: Tnl 30107 L2TP: Tunnel state change from wait-ctl-reply to shutting-down *Mar 12 23:03:47.320: Tnl 30107 L2TP: Shutdown tunnel *Mar 12 23:03:47.320: Tnl 30107 L2TP: Tunnel state change from shutting-down to idle *Mar 12 23:03:47.324: L2TP: Could not find tunnel for tnl 30107, discarding ICRQ ns 3 nr 1 *Mar 12 23:03:47.448: L2TP: Could not find tunnel for tnl 30107, discarding ICRQ ns 3 nr 2
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
23-Oct-2009 |
初始版本 |
 意見
意見