| 功能 |
預設設定 |
|---|---|
| 交換機802.1x啟用狀態 |
停用。 |
| 每埠802.1x啟用狀態 |
停用(強制授權)。 連線埠會傳送和接收一般流量,而不需對使用者端進行基於802.1x的驗證。 |
| AAA |
停用。 |
| RADIUS伺服器
|
|
| 主機模式 |
單主機模式。 |
| 控制方向 |
雙向控制。 |
| 定期重新驗證 |
停用。 |
| 重新驗證嘗試之間的秒數 |
3600秒。 |
| 重新驗證號碼 |
2次(在埠變為未授權狀態之前,交換機重新啟動身份驗證過程的次數)。 |
| 靜默期 |
60秒(在與客戶端進行身份驗證交換失敗後,交換機保持靜默狀態的秒數)。 |
| 重新傳輸時間 |
30秒(交換機在重新傳送請求之前等待來自客戶端的EAP請求/身份幀響應的秒數)。 |
| 最大重新傳輸次數 |
2次(交換機在重新啟動身份驗證過程之前傳送EAP請求/身份幀的次數)。 |
| 使用者端逾時期間 |
30秒(當從身份驗證伺服器向客戶端中繼請求時,交換機在重新向客戶端傳送請求之前等待響應的時間。) |
| 驗證伺服器逾時期間 |
30秒(當從客戶端向身份驗證伺服器中繼響應時,交換機在重新向伺服器傳送響應之前等待應答的時間。) 您可以使用dot1x timeout server-timeout介面配置命令更改此超時時段。 |
| 非活動超時 |
停用。 |
| 訪客VLAN |
未指定。 |
| 無法存取的驗證略過 |
停用。 |
| 受限制的VLAN |
未指定。 |
| 身份驗證器(交換機)模式 |
未指定。 |
| MAC身份驗證繞行 |
停用。 |
| 語音感知安全 |
停用。 |
Catalyst 9000系列交換機上的Dot1x故障排除
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本檔案介紹如何在Catalyst 9000系列交換器上設定、驗證和疑難排解802.1x網路存取控制(NAC)。
必要條件
需求
思科建議您瞭解以下主題。
- Catalyst 9000 系列交換器
- 身分識別服務引擎 (ISE)
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- Catalyst 9300
- Catalyst 9400
- Catalyst 9500
- Catalyst 9600
- Cisco IOS® XE 17.6.x及更高版本
- ISE-VM-K9版本3.0.0.458
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
注意:請參閱相應的配置指南,瞭解在其他思科平台上啟用這些功能所使用的命令。
背景資訊
802.1x標準定義了基於客戶端伺服器的訪問控制和身份驗證協定,可防止未經授權的客戶端透過可公開訪問的埠連線到LAN,除非它們經過正確的身份驗證。驗證伺服器會在提供交換器或LAN提供的任何服務之前,驗證連線到交換器連線埠的每個使用者端。
802.1x驗證包含3個不同的元件:
Supplicant客戶端-提交憑據以進行身份驗證的客戶端
身份驗證程式 -提供客戶端與網路之間的網路連線並可能允許或阻止網路流量的網路裝置。
認證伺服器 -可接收和響應網路訪問請求的伺服器,告訴認證者是否允許連線以及要應用於認證會話的各種其他設定。
本文檔的目標讀者是工程師和支援人員,他們不一定注重安全性。有關基於802.1x埠的身份驗證和元件(例如ISE)的詳細資訊,請參閱相應的配置指南。
注意:請參閱適用於您特定平台和程式碼版本的適當組態指南,以取得最準確的預設802.1x驗證組態。
基本配置
本節介紹實作802.1x連線埠型驗證所需的基本組態。其他功能說明可於本檔案的「附錄」標籤中找到。不同版本之間的配置標準略有不同。根據您當前的版本配置指南驗證您的配置。
在配置基於802.1x的後續身份驗證之前,必須啟用身份驗證、授權和帳戶(AAA),並且必須建立方法清單。
- 方法清單描述了要查詢以驗證使用者的順序和驗證方法。
- 也必須全域啟用802.1x。
C9300> enable
C9300# configure terminal
C9300(config)# aaa new-model
C9300(config)# aaa authentication dot1x default group radius
C9300(config)# dot1x system-auth-control
定義交換器上的RADIUS伺服器
C9300(config)# radius server RADIUS_SERVER_NAME
C9300(config-radius-server)# address ipv4 10.0.1.12
C9300(config-radius-server)# key rad123
C9300(config-radius-server)# exit
在客戶端介面上啟用802.1x。
C9300(config)# interface TenGigabitEthernet 1/0/4
C9300(config-if)# switchport mode access
C9300(config-if)# authentication port-control auto
C9300(config-if)# dot1x pae authenticator
C9300(config-if)# end
驗證配置和操作
本節提供801.1x的背景資訊,以及如何驗證組態和作業。
802.1x簡介
802.1x涉及兩種不同型別的流量-基於EAPoL(區域網上的可擴展身份驗證協定)的客戶端到身份驗證器(點對點)流量和透過RADIUS封裝的身份驗證器到身份驗證伺服器流量。
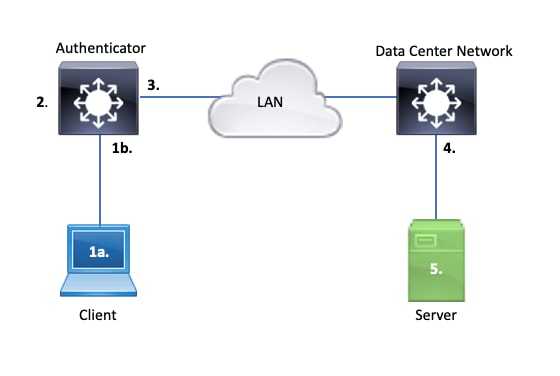
此圖表顯示簡單的dot1x交易的資料流
驗證器(交換器)和驗證伺服器(例如ISE)通常由第3層分隔。RADIUS流量在驗證器和伺服器之間透過網路路由。EAPoL流量透過請求方(客戶端)和身份驗證器之間的直接鏈路進行交換。
請注意,MAC學習發生在身份驗證和授權之後。
在處理涉及802.1x的問題時,請記住以下幾個問題:
- 是否配置正確?
- 身份驗證伺服器是否可以訪問?
- Authentication Manager的狀態是什麼?
- 客戶端和身份驗證器之間或身份驗證器與身份驗證伺服器之間的資料包傳輸是否存在任何問題?
組態
某些組態會在主要版本之間稍有不同。請參閱相關配置指南,瞭解平台/代碼特定指南。
AAA必須配置為使用基於802.1x埠的身份驗證。
- 必須為「dot1x」建立驗證方法清單。這表示啟用802.1X的常見AAA配置。
C9300#show running-config | section aaa aaa new-model <-- This enables AAA. aaa group server radius ISEGROUP <-- This block establishes a RADIUS server group named "ISEGROUP". server name DOT1x ip radius source-interface Vlan1 aaa authentication dot1x default group ISEGROUP <-- This line establishes the method list for 802.1X authentication. Group ISEGROUP is be used. aaa authorization network default group ISEGROUP aaa accounting update newinfo periodic 2880 aaa accounting dot1x default start-stop group ISEGROUP
C9300#show running-config | section radius aaa group server radius ISEGROUP server name DOT1x ip radius source-interface Vlan1 <-- Notice 'ip radius source-interface' configuration exists in both global configuration and the aaa server group block. These need to agree if configured in both places. ip radius source-interface Vlan1 radius server DOT1x address ipv4 10.122.141.228 auth-port 1812 acct-port 1813 <-- 1812 and 1813 are default auth-port and acct-port, respectively. key secretKey
以下是啟用802.1x的範例介面組態。MAB(MAC身份驗證繞行)是一種常用備份方法,用於對不支援dot1x請求方的客戶端進行身份驗證。
C9300#show running-config interface te1/0/4 Building configuration... Current configuration : 148 bytes ! interface TenGigabitEthernet1/0/4 switchport access vlan 50 switchport mode access
authentication order dot1x mab <-- Specifies authentication order, dot1x and then mab
authentication priority dot1x mab <-- Specifies authentication priority, dot1x and then mab authentication port-control auto <-- Enables 802.1x dynamic authentication on the port
mab <-- Enables MAB dot1x pae authenticator <-- Puts interface into "authenticator" mode. end
使用「show mac address-table interface <interface>」確定介面上是否獲知了MAC地址。成功透過身份驗證後,介面只會獲取MAC地址。
C9300#show mac address-table interface te1/0/4
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
50 0800.2766.efc7 STATIC Te1/0/4 <-- The "type" is STATIC and the MAC persists until the authentication session is cleared.
Total Mac Addresses for this criterion: 1
驗證工作階段
Show命令可用於802.1x身份驗證的驗證。
使用show authentication sessions或show authentication sessions <interface>顯示有關當前身份驗證會話的資訊。在本例中,只有Te1/0/4已建立主動身份驗證會話。
C9300#show authentication sessions interface te1/0/4
Interface MAC Address Method Domain Status Fg Session ID
--------------------------------------------------------------------------------------------
Te1/0/4 0800.2766.efc7 dot1x DATA Auth 13A37A0A0000011DC85C34C5 <-- "Method" and "Domain" in this example are dot1x and DATA, respectively. Multi-domain authentication is supported.
Key to Session Events Blocked Status Flags:
A - Applying Policy (multi-line status for details)
D - Awaiting Deletion
F - Final Removal in progress
I - Awaiting IIF ID allocation
P - Pushed Session
R - Removing User Profile (multi-line status for details)
U - Applying User Profile (multi-line status for details)
X - Unknown Blocker
Runnable methods list:
Handle Priority Name
13 5 dot1xSup
1 5 dot1x
2 10 webauth
14 15 mab
Show authentication sessions interface <interface> details提供有關特定介面身份驗證會話的其他詳細資訊。
C9300#show authentication session interface te1/0/4 details
Interface: TenGigabitEthernet1/0/4
IIF-ID: 0x14D66776
MAC Address: 0800.2766.efc7
IPv6 Address: Unknown
IPv4 Address: Unknown
User-Name: alice
Status: Authorized
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Session timeout: N/A
Acct update timeout: 172800s (local), Remaining: 152363s
Common Session ID: 13A37A0A0000011DC85C34C5
Acct Session ID: 0x00000002
Handle: 0xe8000015
Current Policy: POLICY_Te1/0/4 <-- If a post-authentication ACL is applied, it is listed here.
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Server Policies:
Method status list:
Method State
dot1x Authc Success <-- This example shows a successful 801.1x authentication session.
如果在介面上啟用了身份驗證,但是沒有活動會話,則會顯示可運行的方法清單。「No sessions match provided criteria」也會顯示。
C9300#show authentication sessions interface te1/0/5
No sessions match supplied criteria.
Runnable methods list:
Handle Priority Name
13 5 dot1xSup
1 5 dot1x
2 10 webauth
14 15 mab
如果在介面上未啟用身份驗證,則不會在介面上檢測到身份驗證管理器存在。「No sessions match provided criteria」也會顯示。
C9300#show authentication sessions interface te1/0/6
No sessions match supplied criteria.
No Auth Manager presence on this interface
可連線至驗證伺服器
能否連線至驗證伺服器是802.1x驗證成功的前提條件。
使用「ping <server_ip>」,快速測試可接通性。請確認您的ping來源是RADIUS來源介面。
C9300#ping 10.122.141.228 source vlan 1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.122.141.228, timeout is 2 seconds: Packet sent with a source address of 10.122.163.19 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
命令「show aaa servers」標識伺服器狀態,並提供所有已配置AAA伺服器的事務的統計資訊。
C9300#show aaa servers
RADIUS: id 3, priority 1, host 10.122.141.228, auth-port 1812, acct-port 1813, hostname DOT1x <-- Specific server
State: current UP, duration 84329s, previous duration 0s <-- Current State
Dead: total time 0s, count 1
Platform State from SMD: current UP, duration 24024s, previous duration 0s
SMD Platform Dead: total time 0s, count 45
Platform State from WNCD (1) : current UP
Platform State from WNCD (2) : current UP
Platform State from WNCD (3) : current UP
Platform State from WNCD (4) : current UP
Platform State from WNCD (5) : current UP
Platform State from WNCD (6) : current UP
Platform State from WNCD (7) : current UP
Platform State from WNCD (8) : current UP, duration 0s, previous duration 0s
Platform Dead: total time 0s, count 0UP
Quarantined: No
Authen: request 510, timeouts 468, failover 0, retransmission 351 <-- Authentication Statistics
Response: accept 2, reject 2, challenge 38
Response: unexpected 0, server error 0, incorrect 12, time 21ms
Transaction: success 42, failure 117
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Dot1x transactions:
Response: total responses: 42, avg response time: 21ms
Transaction: timeouts 114, failover 0
Transaction: total 118, success 2, failure 116
MAC auth transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
Author: request 0, timeouts 0, failover 0, retransmission 0
Response: accept 0, reject 0, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
MAC author transactions:
Response: total responses: 0, avg response time: 0ms
Transaction: timeouts 0, failover 0
Transaction: total 0, success 0, failure 0
Account: request 3, timeouts 0, failover 0, retransmission 0
Request: start 2, interim 0, stop 1
Response: start 2, interim 0, stop 1
Response: unexpected 0, server error 0, incorrect 0, time 11ms
Transaction: success 3, failure 0
Throttled: transaction 0, timeout 0, failure 0
Malformed responses: 0
Bad authenticators: 0
Elapsed time since counters last cleared: 1d3h4m
Estimated Outstanding Access Transactions: 0
Estimated Outstanding Accounting Transactions: 0
Estimated Throttled Access Transactions: 0
Estimated Throttled Accounting Transactions: 0
Maximum Throttled Transactions: access 0, accounting 0
Consecutive Response Failures: total 115
SMD Platform : max 113, current 0 total 113
WNCD Platform: max 0, current 0 total 0
IOSD Platform : max 2, current 2 total 2
Consecutive Timeouts: total 466
SMD Platform : max 455, current 0 total 455
WNCD Platform: max 0, current 0 total 0
IOSD Platform : max 11, current 11 total 11
Requests per minute past 24 hours:
high - 23 hours, 25 minutes ago: 4
low - 3 hours, 4 minutes ago: 0
average: 0
使用「test aaa」實用程式可確認交換機與身份驗證伺服器之間的可接通性。請注意,此公用程式已停用,無法無限期使用。
C9300#debug radius <-- Classic Cisco IOS debugs are only useful in certain scenarios. See "Cisco IOS XE Debugs" for details.
C9300#test aaa group ISE username password new-code <-- This sends a RADIUS test probe to the identified server. The username and password is meant to elicit a rejection from RADIUS.
User rejected <-- This means that the RADIUS server received our test probe, but rejected our user. We can conclude the server is reachable and listening on the configured auth-port.
*Jul 16 21:05:57.632: %PARSER-5-HIDDEN: Warning!!! ' test platform-aaa group server-group ISE user-name username password new-code blocked count delay level profile rate users ' is a hidden command. Use of this command is not recommended/supported and will be removed in future.
*Jul 16 21:05:57.644: RADIUS/ENCODE(00000000):Orig. component type = Invalid
*Jul 16 21:05:57.644: RADIUS/ENCODE(00000000): dropping service type, "radius-server attribute 6 on-for-login-auth" is off
*Jul 16 21:05:57.644: RADIUS(00000000): Config NAS IP: 10.122.161.63
*Jul 16 21:05:57.644: vrfid: [65535] ipv6 tableid : [0]
*Jul 16 21:05:57.644: idb is NULL
*Jul 16 21:05:57.644: RADIUS(00000000): Config NAS IPv6: ::
*Jul 16 21:05:57.644: RADIUS(00000000): sending
*Jul 16 21:05:57.644: RADIUS/DECODE(00000000): There is no General DB. Want server details may not be specified
*Jul 16 21:05:57.644: RADIUS(00000000): Send Access-Request to 10.122.141.199:1812 id 1645/8, len 50 <-- Sending Access-Request to RADIUS server
RADIUS: authenticator 3B 65 96 37 63 E3 32 41 - 3A 93 63 B6 6B 6A 5C 68
*Jul 16 21:05:57.644: RADIUS: User-Password [2] 18 *
*Jul 16 21:05:57.644: RADIUS: User-Name [1] 6 "username"
*Jul 16 21:05:57.644: RADIUS: NAS-IP-Address [4] 6 10.122.161.63
*Jul 16 21:05:57.644: RADIUS(00000000): Sending a IPv4 Radius Packet
*Jul 16 21:05:57.644: RADIUS(00000000): Started 5 sec timeout
*Jul 16 21:05:57.669: RADIUS: Received from id 1645/8 10.122.141.199:1812, Access-Reject, len 20 <-- Receiving the Access-Reject from RADIUS server
RADIUS: authenticator 1A 11 32 19 12 F9 C3 CC - 6A 83 54 DF 0F DB 00 B8
*Jul 16 21:05:57.670: RADIUS/DECODE(00000000): There is no General DB. Reply server details may not be recorded
*Jul 16 21:05:57.670: RADIUS(00000000): Received from id 1645/8
疑難排解
本節提供如何對Catalyst交換機上的大多數802.1x問題進行故障排除的指南。
方法
系統地解決涉及802.1x和身份驗證的問題,以獲得最佳效果。一些好的問題需要回答:
- 此問題是否與單個交換機無關?單一連線埠?單一使用者端型別?
- 是否已驗證配置?身份驗證伺服器是否可以訪問?
- 問題是每次都出現,還是間歇性的?它是否僅在重新身份驗證或授權更改時發生?
如果排除明顯故障後問題仍然存在,請端到端檢查單個失敗的交易。用於調查從客戶端到伺服器的802.1x事務的最好、最完整的資料集包括:
1a。 客戶端和/或上的捕獲
1b.在客戶端連線的接入介面上
此參考點對於深入瞭解在啟用dot1x的接入埠與客戶端之間交換的EAPoL資料包至關重要。SPAN是檢視使用者端和驗證者之間流量的最可靠工具。
2. 身份驗證器上的調試
調試允許我們透過身份驗證器跟蹤事務。
- 驗證者必須傳送收到的EAPoL封包,並產生目的地為驗證伺服器的單點傳播RADIUS封裝流量。
- 確保設定適當的調試級別以最大程度地提高效率。
3. 捕獲身份驗證器旁的流量
透過此捕獲,我們可以檢視身份驗證器和身份驗證伺服器之間的通話。
- 此捕獲從身份驗證器的角度準確顯示整個會話。
- 當與點4中的捕獲配對時,您可以確定身份驗證伺服器和身份驗證器之間是否存在丟失情況。
4. 與驗證伺服器相鄰的擷取
此擷取是第3點擷取的輔助專案。
- 此捕獲從身份驗證伺服器的角度提供了整個會話。
- 當與點3中的捕獲配對時,您可以確定身份驗證器和身份驗證伺服器之間是否存在丟失情況。
5. 擷取、偵錯、登入驗證伺服器
最後一個謎題,伺服器偵錯會告訴我們伺服器對交易的瞭解。
- 藉助這一組端到端資料,網路工程師可以確定事務中斷的位置並排除不導致問題的元件。
示例症狀
此部分提供常見症狀和問題方案的清單。
- 使用者端沒有回應
如果交換機生成的EAPoL流量未引發響應,則會看到以下系統日誌:
Aug 23 11:23:46.387 EST: %DOT1X-5-FAIL: Switch 1 R0/0: sessmgrd: Authentication failed for client (aaaa.bbbb.cccc) with reason (No Response from Client) on Interface Gi6/0/32 AuditSessionID CBFF000A000001056EFE9E73
原因代碼「No Response from Client」表示交換機已啟動dot1x進程,但在超時時間內未從客戶端收到任何響應。
這表示使用者端沒有收到或瞭解交換器連線埠傳送的驗證流量,或未在交換器連線埠上收到來自使用者端的回應。
- 客戶端放棄會話
如果身份驗證會話已啟動但未完成,則身份驗證伺服器(例如ISE)報告客戶端已啟動會話,但在完成之前已放棄該會話。
通常,這意味著身份驗證過程只能部分完成。
確保端到端傳送身份驗證器交換機和身份驗證伺服器之間的整個事務,並確保身份驗證伺服器正確解釋這些事務。
如果RADIUS流量在網路上丟失,或以無法正確組合的方式傳輸,則事務不完整,客戶端將重試身份驗證。伺服器接著會報告使用者端已放棄其作業階段。
- MAB客戶端無法通過DHCP/回退到APIPA
MAC驗證略過(MAB)允許根據MAC位址進行驗證。通常不支援請求方軟體的客戶端透過MAB進行身份驗證。
如果MAB用作身份驗證的後退方法,而dot1x是在交換機埠上運行的首選初始方法,則可能導致客戶端無法完成DHCP的情況。
問題歸結為操作的順序。當dot1x執行時,交換器連線埠會使用EAPoL以外的封包,直到驗證完成或dot1x逾時為止。但是,客戶端會立即嘗試獲取IP地址並廣播其DHCP發現消息。這些發現消息由交換機埠使用,直到dot1x超出其配置的超時值並且MAB能夠運行。如果客戶端DHCP超時時間小於dot1x超時時間,則DHCP會失敗,並且客戶端會回退到APIPA或其回退策略規定的任何值。
此問題可透過多種方式避免。在透過MAB身份驗證的客戶端連線的介面上優先使用MAB。如果dot1x必須首先運行,請注意客戶端DHCP行為,並相應地調整超時值。
使用dot1x和MAB時,請注意考量使用者端行為。如上所述,有效的配置可能導致技術問題。
平台特定的多功能
本節概述了Catalyst 9000系列交換機上提供的許多平台特定的實用程式,這些實用程式可用於對dot1x問題進行故障排除。
- 交換器連線埠分析器(SPAN)
SPAN允許使用者將來自一個或多個埠的流量映象到目標埠以進行捕獲和分析。本地SPAN是最「可信」的捕獲實用程式。
有關配置和實施的詳細資訊,請參閱本配置指南:
配置SPAN和RSPAN,Cisco IOS XE班加羅爾17.6.x(Catalyst 9300)
- 內嵌式封包擷取(EPC)
EPC利用CPU和記憶體資源提供板載本地資料包捕獲功能。
EPC存在一些限制,這些限制影響其調查某些問題的效率。EPC的速率限制為每秒1000個資料包。EPC也無法可靠地捕獲物理介面出口的CPU注入的資料包。當重點是身份驗證器交換機和身份驗證伺服器之間的RADIUS事務時,這一點很重要。通常,面向伺服器的介面上的流量速率會大大超過每秒1000個資料包。此外,面向伺服器的介面出口上的EPC無法捕獲身份驗證器交換機生成的流量。
使用雙向訪問清單過濾EPC,以避免受到每秒1000資料包限制的影響。如果對身份驗證器和伺服器之間的RADIUS流量感興趣,請關注身份驗證器RADIUS源介面地址與伺服器地址之間的流量。
如果通向認證伺服器的下一個上游裝置是Catalyst交換機,請在通向認證器交換機的下行鏈路上使用經過過濾的EPC,以獲得最佳結果。
有關配置和實施的詳細資訊,請參閱本配置指南:
配置資料包捕獲,Cisco IOS Bengaluru 17.6.x (Catalyst 9300)
- Cisco IOS XE調試
從Cisco IOS XE 16.3.2版開始的軟體架構更改將AAA元件移動到單獨的Linux守護程式。熟悉的調試不再啟用日誌記錄緩衝區中的可檢視調試。相反,

提示:傳統IOS AAA調試不再在系統日誌中為系統日誌內的前面板埠身份驗證提供輸出
以下用於dot1x和RADIUS的傳統Cisco IOS調試不再啟用交換機日誌記錄緩衝區中的可檢視調試:
debug radius
debug access-session all
debug dot1x all
AAA元件調試現在可透過SMD(會話管理器守護程式)下的系統跟蹤進行訪問。
- 與傳統系統日誌一樣,Catalyst系統跟蹤報告在預設級別,必須指示其收集更多深入日誌。
- 使用set platform software trace smd switch active r0 <component> debug命令更改所需子元件的常式跟蹤級別。
Switch#set platform software trace smd switch active R0 auth-mgr debug <<<--- This sets the "auth-mgr" subcomponent to "debug" log level.
此表將傳統IOS調試對映到其等效跟蹤。
| 舊樣式指令 | 新樣式指令 |
| #debug半徑 | #set platform software trace smd switch active R0 radius debug |
| #debug dot1x all | #set platform software trace smd switch active R0 dot1x-all debug |
| #debug access-session all | #set platform software trace smd switch active R0 auth-mgr-all debug |
| #debug epm all | #set platform software trace smd switch active R0 epm-all debug |
傳統調試支援所有指向「調試」級別的相關元件跟蹤。平台命令還用於根據需要啟用特定跟蹤。
使用show platform software trace level smd switch active R0命令顯示SMD子元件的當前跟蹤級別。
Switch#show platform software trace level smd switch active R0
Module Name Trace Level
-----------------------------------------------
aaa Notice <--- Default level is "Notice"
aaa-acct Notice
aaa-admin Notice
aaa-api Notice
aaa-api-attr Notice
<snip>
auth-mgr Debug <--- Subcomponent "auth-mgr" traces at "debug" level
auth-mgr-all Notice
<snip>
子元件跟蹤級別可透過兩種方式恢復為預設值。
- 使用「undebug all」或「set platform software trace smd switch active R0 <sub-component> notice」進行恢復。
- 如果裝置重新載入,追蹤層級也會還原為預設值。
Switch#undebug all
All possible debugging has been turned off
or
Switch#set platform software trace smd switch active R0 auth-mgr notice <--- Sets sub-component "auth-mgr" to trace level "Notice", the system default.
可在控制檯上檢視元件跟蹤日誌,也可以將其寫入存檔並離線檢視。 跟蹤儲存在需要解碼的壓縮二進位制存檔中。在處理存檔跟蹤時,請聯絡TAC以獲得調試幫助。此工作流程說明如何在CLI中檢視跟蹤。
使用「show platform software trace message smd switch active R0」命令檢視儲存在SMD元件記憶體中的跟蹤日誌。
Switch#show platform software trace message smd switch active R0
2016/11/26 03:32:24.790 [auth-mgr]: [1422]: UUID: 0, ra: 0 (info): [0000.0000.0000:unknown] Auth-mgr aaa_acct_reply
2016/11/26 03:32:29.678 [btrace]: [1422]: UUID: 0, ra: 0 (note): Single message size is greater than 1024
2016/11/26 03:32:24.790 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Delay-Time [41] 6 0 RADIUS: authenticator 55 de 16 e1 82 2a d8 3f - a3 9d db 63 5d 61 a5 f0
2016/11/26 03:32:24.790 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Received from id 1646/52 10.48.26.135:0, Accounting-response, len 20
2016/11/26 03:32:24.758 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Started 5 sec timeout
2016/11/26 03:32:24.758 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Sending a IPv4 Radius Packet
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Output-Packets [48] 6 0
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Input-Packets [47] 6 8
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Output-Octets [43] 6 0
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Input-Octets [42] 6 658
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Session-Time [46] 6 125
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Event-Timestamp [55] 6 1480131144
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Status-Type [40] 6 Stop [2]
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: 36 36 33 36 36 39 30 30 2f 33 39 39 38 [ 66366900/3998]
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: 68 72 65 6e 65 6b 2d 69 73 65 32 31 2d 31 2f 32 [hrenek-ise21-1/2]
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: 30 30 30 32 41 39 45 41 45 46 44 39 33 3a 76 63 [0002A9EAEFD93:vc]
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Class [25] 63
RADIUS: 43 41 43 53 3a 30 41 30 30 30 41 46 45 30 30 30 [CACS:0A000AFE000]
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Terminate-Cause[49] 6 admin-reset [6]
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Authentic [45] 6 Remote [3]
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Acct-Session-Id [44] 10 "00000014"
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port [5] 6 50108
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port-Id [87] 22 "GigabitEthernet1/0/8"
2016/11/26 03:32:24.757 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Nas-Identifier [32] 17 "C3850-3-BUSHIDO"
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: NAS-IP-Address [4] 6 10.48.44.182
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Calling-Station-Id [31] 19 "00-50-56-99-01-6B"
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Called-Station-Id [30] 19 "00-CA-E5-52-46-08"
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 12 "method=mab"
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 18
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 43 "audit-session-id=0A000AFE0000002A9EAEFD93"
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 49
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: User-Name [1] 19 "00-50-56-99-01-6B"
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Framed-IP-Address [8] 6 10.0.10.4
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 205 "cts-pac-opaque= "
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 211
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS: authenticator 95 52 40 05 8f f7 41 7d - fe cf 7e 1f e7 b6 4a f9
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Send Accounting-Request to 10.48.26.135:1646 id 1813/52, len 551
2016/11/26 03:32:24.756 [radius]: [1422]: UUID: 0, ra: 0 (debug): abcdefghijklmno:NO EAP-MESSAGE
2016/11/26 03:32:24.755 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS(00000000): sending
2016/11/26 03:32:24.755 [radius]: [1422]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Config NAS IP: 10.48.44.182
2016/11/26 03:32:24.755 [radius]: [1422]: UUID: 0, ra: 0 (debug): Config for source interface found in VRF DB for tableid:3, IDB: 73
<snip>
輸出是詳細的,因此將輸出重定向到檔案非常有用。
- 使用「更多」實用程式可透過CLI讀取檔案,或將其離線以便在文本編輯器中檢視。
Switch#show platform software trace message smd switch active R0 | redirect flash:SMD_debugs.txt
Switch#more flash:SMD_debugs.txt
This command is being deprecated. Please use 'show logging process' command.
executing cmd on chassis 1 ...
2022/12/02 15:04:47.434368 {smd_R0-0}{2}: [auth-mgr] [16908]: (debug): [0800.27dd.3016:Gi2/0/11] Started Accounting (0) timer (300 secs) for client 0800.27dd.3016
2022/12/02 15:04:47.434271 {smd_R0-0}{2}: [auth-mgr] [16908]: (info): [0800.27dd.3016:Gi2/0/11] Accounting timer (0) expired for client 0800.27dd.3016
2022/12/02 15:04:43.366688 {smd_R0-0}{2}: [auth-mgr] [16908]: (debug): [5057.a8e1.6f49:Gi2/0/11] Started Accounting (0) timer (300 secs) for client 5057.a8e1.6f49
2022/12/02 15:04:43.366558 {smd_R0-0}{2}: [auth-mgr] [16908]: (info): [5057.a8e1.6f49:Gi2/0/11] Accounting timer (0) expired for client 5057.a8e1.6f49
2022/12/02 15:01:03.629116 {smd_R0-0}{2}: [smd] [16908]: (warn): Setting trace for 52:7
2022/12/02 15:00:19.350560 {smd_R0-0}{2}: [smd] [16908]: (warn): Setting trace for 52:7
2022/12/02 01:28:39.841376 {smd_R0-0}{2}: [auth-mgr] [16908]: (ERR): [0000.0000.0000:unknown] sm ctx unlock: Invalid auth mgr handle
<snip>
Show logging process是Cisco IOS XE 17.9.x版及後續版本中跟蹤和標準的更新實用程式。
C9300#show logging process smd ?
<0-25> instance number
end specify log filtering end location
extract-pcap Extract pcap data to a file
filter specify filter for logs
fru FRU specific commands
internal select all logs. (Without the internal keyword only
customer curated logs are displayed)
level select logs above specific level
metadata CLI to display metadata for every log message
module select logs for specific modules
reverse show logs in reverse chronological order
start specify log filtering start location
switch specify switch number
to-file decode files stored in disk and write output to file
trace-on-failure show the trace on failure summary
| Output modifiers
Show logging process」提供了與「show platform software trace」相同的功能,而且格式更加優雅和易於訪問。
C9300#clear auth sessions
C9300#show logging process smd reverse
Logging display requested on 2023/05/02 16:44:04 (UTC) for Hostname: [C9300], Model: [C9300X-24HX], Version: [17.09.01], SN: [FOC263569FP], MD_SN: [FOC2641Y2MK]
Displaying logs from the last 0 days, 0 hours, 10 minutes, 0 seconds
executing cmd on chassis 1 ...
===========================================================
UTM [LUID NOT FOUND] .............. 0
UTM [PCAP] ........................ 0
UTM [MARKER] ...................... 0
UTM [APP CONTEXT] ................. 0
UTM [TDL TAN] ..................... 5
UTM [MODULE ID] ................... 0
UTM [DYN LIB] ..................... 0
UTM [PLAIN TEXT] .................. 6
UTM [ENCODED] ..................... 85839
UTM [Skipped / Rendered / Total] .. 85128 / 722 / 85850
Last UTM TimeStamp ................ 2023/05/02 16:44:03.775663010
First UTM TimeStamp ............... 2023/05/02 15:52:18.763729918
===========================================================
----------------- Decoder Output Information --------------
===========================================================
MRST Filter Rules ...... 1
UTM Process Filter ..... smd
Total UTM To Process ... 85850
Total UTF To Process ... 1
Num of Unique Streams .. 1
===========================================================
----------------- Decoder Input Information ---------------
===========================================================
======= Unified Trace Decoder Information/Statistics ======
===========================================================
2023/05/02 16:44:03.625123675 {smd_R0-0}{1}: [radius] [22624]: (ERR): Failed to mark Identifier for reuse
2023/05/02 16:44:03.625123382 {smd_R0-0}{1}: [radius] [22624]: (ERR): RSPE- Set Identifier Free for Reuse : Input Validation Failed Level-2
2023/05/02 16:44:03.625116747 {smd_R0-0}{1}: [radius] [22624]: (info): Valid Response Packet, Free the identifier
2023/05/02 16:44:03.625091040 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: authenticator 2b f4 ea 87 d9 db 75 3a - 2c 8a c4 36 56 46 b5 57
2023/05/02 16:44:03.625068520 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Received from id 1813/9 10.122.141.228:0, Accounting-response, len 20
2023/05/02 16:44:03.610151863 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Started 5 sec timeout
2023/05/02 16:44:03.610097362 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Acct-Delay-Time [41] 6 0
2023/05/02 16:44:03.610090044 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Event-Timestamp [55] 6 1683045843
2023/05/02 16:44:03.610085857 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Acct-Status-Type [40] 6 Start [1]
2023/05/02 16:44:03.610040912 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Class [25] 63 ...
2023/05/02 16:44:03.610037444 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Acct-Authentic [45] 6 Remote [3]
2023/05/02 16:44:03.610032802 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Acct-Session-Id [44] 10 "00000004"
2023/05/02 16:44:03.610028677 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Called-Station-Id [30] 19 "00-01-02-02-AA-BF"
2023/05/02 16:44:03.610024641 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Nas-Identifier [32] 7 "C9300"
2023/05/02 16:44:03.610020641 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Calling-Station-Id [31] 19 "08-00-27-66-EF-C7"
2023/05/02 16:44:03.610016809 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: NAS-Port [5] 6 50104
2023/05/02 16:44:03.610012487 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
2023/05/02 16:44:03.610007504 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: NAS-Port-Id [87] 25 "TenGigabitEthernet1/0/4"
2023/05/02 16:44:03.610003581 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: NAS-IP-Address [4] 6 10.122.163.19
2023/05/02 16:44:03.609998136 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Calling-Station-Id [31] 19 "08-00-27-66-EF-C7"
2023/05/02 16:44:03.609994109 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Called-Station-Id [30] 19 "00-01-02-02-AA-BF"
2023/05/02 16:44:03.609989329 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Cisco AVpair [1] 14 "method=dot1x"
2023/05/02 16:44:03.609985171 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Vendor, Cisco [26] 20
2023/05/02 16:44:03.609981606 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Cisco AVpair [1] 43 "audit-session-id=13A37A0A0000011FDD598189"
2023/05/02 16:44:03.609976961 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Vendor, Cisco [26] 49
2023/05/02 16:44:03.609969166 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: User-Name [1] 7 "alice"
2023/05/02 16:44:03.609963241 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: authenticator 0b 99 e3 50 d8 d3 8c 26 - e8 41 c3 f6 11 b9 ab 2f
2023/05/02 16:44:03.609953614 {smd_R0-0}{1}: [radius] [22624]: (info): RADIUS: Send Accounting-Request to 10.122.141.228:1813 id 1813/9, len 319
2023/05/02 16:44:03.609863172 {smd_R0-0}{1}: [auth-mgr] [22624]: (info): [0800.2766.efc7:Te1/0/4] Handling external PRE event AuthZ Success
2023/05/02 16:44:03.609695649 {smd_R0-0}{1}: [dot1x] [22624]: (info): [0800.2766.efc7:Te1/0/4] EAPOL packet sent to client
2023/05/02 16:44:03.609689224 {smd_R0-0}{1}: [dot1x] [22624]: (info): [0000.0000.0000:unknown] Pkt body: 03 68 00 04
2023/05/02 16:44:03.609686794 {smd_R0-0}{1}: [dot1x] [22624]: (info): [0800.2766.efc7:Te1/0/4] EAP Packet - SUCCESS, ID : 0x68
2023/05/02 16:44:03.609683919 {smd_R0-0}{1}: [dot1x] [22624]: (info): [0800.2766.efc7:Te1/0/4] Sent EAPOL packet - Version : 3,EAPOL Type : EAP, Payload Length : 4, EAP-Type = 0
2023/05/02 16:44:03.609334292 {smd_R0-0}{1}: [dot1x] [22624]: (info): [0000.0000.0000:Te1/0/4] Sending out EAPOL packet
2023/05/02 16:44:03.609332867 {smd_R0-0}{1}: [dot1x] [22624]: (info): [0000.0000.0000:Te1/0/4] Setting EAPOL eth-type to 0x888e, destination mac to 0800.2766.efc7
2023/05/02 16:44:03.609310820 {smd_R0-0}{1}: [dot1x] [22624]: (info): [0800.2766.efc7:Te1/0/4] Posting AUTHZ_SUCCESS on Client
2023/05/02 16:44:03.609284841 {smd_R0-0}{1}: [auth-mgr] [22624]: (info): [0800.2766.efc7:Te1/0/4] Raising ext evt AuthZ Success (21) on this session, client (unknown) (0)
追蹤範例
此段落包含完整、失敗交易(伺服器拒絕使用者端身份證明)之dot1x和radius元件的階段作業管理員追蹤。其目的是為導航與前面板身份驗證相關的系統蹤跡提供基本指南。
- 測試客戶端嘗試連線到GigabitEthernet1/0/2,被拒絕。
在本示例中,SMD元件跟蹤設定為「debug」。
C9300#set platform software trace smd sw active r0 dot1x-all
C9300#set platform software trace smd sw active r0 radius debug
EAPoL:開始
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0000.0000.0000:unknown] Received EAPOL pkt (size=92) on l2 socket
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] queuing an EAPOL pkt on Auth Q
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Dequeued pkt: CODE= 0,TYPE= 0,LEN= 0
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Received pkt saddr = 0040.E93E.0000 , daddr = 0180.C200.0003, pae-ether-type = 0x888E
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Couldn't find the supplicant in the list
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] New client detected, sending session start event for 0040.E93E.0000
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: initialising
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: disconnected
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: entering restart
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Sending create new context event to EAP for 0x0A00000E (0040.E93E.0000)
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: entering init state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering idle state
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Created a client entry (0x0A00000E)
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Dot1x authentication started for 0x0A00000E (0040.E93E.0000)
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting !EAP_RESTART on Client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:enter connecting state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: restart connecting
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting RX_REQ on Client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: authenticating state entered
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:connecting authenticating action
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting AUTH_START for 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering request state
EAPoL:EAP請求身份
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Sending EAPOL packet
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Sending out EAPOL packet
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] EAPOL packet sent to client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:idle request action
EAPoL:EAP回應
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0000.0000.0000:unknown] Received EAPOL pkt (size=92) on l2 socket
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Queuing an EAPOL pkt on Authenticator Q
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Dequeued pkt: CODE= 2,TYPE= 1,LEN= 14
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Received pkt saddr = 0040.E93E.0000 , daddr = 0180.C200.0003, pae-ether-type = 0x888E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting EAPOL_EAP for 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering response state
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Response sent to the server from 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:request response action
[aaa-authen]: [16498]: UUID: 0, ra: 0 (debug): AAA/AUTHEN/8021X (00000000): Pick method list 'default'
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS/ENCODE: Best Local IP-Address 172.28.99.147 for Radius-Server 172.28.99.252
[radius-failover]: [16498]: UUID: 0, ra: 0 (debug): RADIUS/ENCODE: Nas-Identifier "C9300"
[aaa-author]: [16498]: UUID: 0, ra: 0 (debug): VALID SG handle
RADIUS: ACCESS-REQUEST
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Send Access-Request to 172.28.99.252:1645 id 1812/82, len 242
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: authenticator 59 c9 e0 be 4d b5 1c 11 - 02 cb 5b eb 78 d0 4b ad
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: User-Name [1] 11 "ixia_data"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Service-Type [6] 6 Framed [2]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 27
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 21 "service-type=Framed"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Framed-MTU [12] 6 1500
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Calling-Station-Id [31] 19 "00-40-E9-3E-00-00"
0e 01 69 78 69 61 5f 64 61 74 61 [ ixia_data]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Message [79] 16
69 87 3c 61 80 3a 31 a8 73 2b 55 76 f4 [ Ei<a:1s+Uv]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Message-Authenticator[80] 18
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Key-Name [102] 2 *
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 49
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 43 "audit-session-id=AC1C639300000017E53C6E8E"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 20
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 14 "method=dot1x"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-IP-Address [4] 6 172.28.99.147
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Nas-Identifier [32] 8 "C9300"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port-Id [87] 22 "GigabitEthernet1/0/2"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Sending a IPv4 Radius Packet
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Started 5 sec timeout
RADIUS:訪問質詢
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Received from id 1645/82 172.28.99.252:0, Access-Challenge, len 127
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port [5] 6 50014 RADIUS: authenticator 82 71 61 a5 30 bc 98 78 - fa f1 48 ec 05 fb ca 3a
RADIUS: 33 37 43 50 4d 53 65 73 73 69 6f 6e 49 44 3d 41 [37CPMSessionID=A]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: State [24] 81
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 43 31 43 36 33 39 33 30 30 30 30 30 30 31 37 45 [C1C639300000017E]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 35 33 43 36 45 38 45 3b 33 36 53 65 73 73 69 6f [53C6E8E;36Sessio]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 6e 49 44 3d 69 73 65 2d 70 6f 6c 2d 65 73 63 2f [nID=ise-pol-esc/]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 32 34 30 31 39 38 34 32 39 2f 38 39 32 34 3b [ 240198429/8924;]
RADIUS: 01 f9 00 06 0d 20 [ ]
02/15 14:01:28.986 [radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Message [79] 8
RADIUS: 78 66 ec be 2c a4 af 79 5e ec c6 47 8b da 6a c2 [ xf,y^Gj]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Message-Authenticator[80] 18
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS:rad_code 11, suppress reject flag 0
[radius-authen]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Received from id 1645/82
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting EAP_REQ for 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:exiting response state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering request state########## EAPoL: EAP-REQUEST ##########
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Sending EAPOL packet
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Sending out EAPOL packet
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] EAPOL packet sent to client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:response request action
EAPoL:EAP回應
02/15 14:01:28.988 [dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0000.0000.0000:unknown] Received EAPOL pkt (size=92) on l2 socket
02/15 14:01:28.989 [dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Queuing an EAPOL pkt on Authenticator Q
02/15 14:01:28.989 [dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Dequeued pkt: CODE= 2,TYPE= 3,LEN= 6
02/15 14:01:28.989 [dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Received pkt saddr = 0040.E93E.0000 , daddr = 0180.C200.0003, pae-ether-type = 0x888E
02/15 14:01:28.989 [dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting EAPOL_EAP for 0x0A00000E
02/15 14:01:28.989 [dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering response state
02/15 14:01:28.989 [dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Response sent to the server from 0x0A00000E
02/15 14:01:28.989 [dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:request response action
02/15 14:01:28.989 [aaa-authen]: [16498]: UUID: 0, ra: 0 (debug): AAA/AUTHEN/8021X (00000000): Pick method list 'default'
02/15 14:01:28.990 [radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS/ENCODE: Best Local IP-Address 172.28.99.147 for Radius-Server 172.28.99.252
02/15 14:01:28.990 [radius-failover]: [16498]: UUID: 0, ra: 0 (debug): RADIUS/ENCODE: Nas-Identifier "C9300"
02/15 14:01:28.990 [aaa-author]: [16498]: UUID: 0, ra: 0 (debug): VALID SG handle
RADIUS: ACCESS-REQUEST
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Send Access-Request to 172.28.99.252:1645 id 1812/83, len 315
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: authenticator 3d 31 3f ee 14 b8 9d 63 - 7a 8b 52 90 5f 77 6d b8
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: User-Name [1] 11 "ixia_data"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Service-Type [6] 6 Framed [2]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 27
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 21 "service-type=Framed"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Framed-MTU [12] 6 1500
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Calling-Station-Id [31] 19 "00-40-E9-3E-00-00"
RADIUS: 02 f9 00 06 03 04
02/15 14:01:28.991 [radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Message [79] 8
RADIUS: 8b 2a 2e 75 90 a2 e1 c9 06 84 c9 fe f5 d0 98 39 [ *.u9]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Message-Authenticator[80] 18
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Key-Name [102] 2 *
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 49
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 43 "audit-session-id=AC1C639300000017E53C6E8E"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 20
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 14 "method=dot1x"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-IP-Address [4] 6 172.28.99.147
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Nas-Identifier [32] 8 "C9300"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port-Id [87] 22 "GigabitEthernet1/0/2"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port [5] 6 50014
RADIUS: 33 37 43 50 4d 53 65 73 73 69 6f 6e 49 44 3d 41 [37CPMSessionID=A]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: State [24] 81
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 43 31 43 36 33 39 33 30 30 30 30 30 30 31 37 45 [C1C639300000017E]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 35 33 43 36 45 38 45 3b 33 36 53 65 73 73 69 6f [53C6E8E;36Sessio]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 6e 49 44 3d 69 73 65 2d 70 6f 6c 2d 65 73 63 2f [nID=ise-pol-esc/]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 32 34 30 31 39 38 34 32 39 2f 38 39 32 34 3b [ 240198429/8924;]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Sending a IPv4 Radius Packet
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Started 5 sec timeout
RADIUS:訪問質詢
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Received from id 1645/83 172.28.99.252:0, Access-Challenge, len 154
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: authenticator 0c 8d 49 80 0f 51 89 fa - ba 22 2f 96 41 99 c2 4e
RADIUS: 33 37 43 50 4d 53 65 73 73 69 6f 6e 49 44 3d 41 [37CPMSessionID=A]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: State [24] 81
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 43 31 43 36 33 39 33 30 30 30 30 30 30 31 37 45 [C1C639300000017E]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 35 33 43 36 45 38 45 3b 33 36 53 65 73 73 69 6f [53C6E8E;36Sessio]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 6e 49 44 3d 69 73 65 2d 70 6f 6c 2d 65 73 63 2f [nID=ise-pol-esc/]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 32 34 30 31 39 38 34 32 39 2f 38 39 32 34 3b [ 240198429/8924;]
RADIUS: 01 fa 00 21 04 10 5b d0 b6 4e 68 37 6b ca 5e 6f 5a 65 78 04 77 bf 69 73 65 2d [![Nh7k^oZexwise-]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Message [79] 35
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 70 6f 6c 2d 65 73 63 [ pol-esc]
RADIUS: a3 0d b0 02 c8 32 85 2c 94 bd 03 b3 22 e6 71 1e [ 2,"q]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Message-Authenticator[80] 18
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS:rad_code 11, suppress reject flag 0
[radius-authen]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Received from id 1645/83
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting EAP_REQ for 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:exiting response state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering request state
EAPoL:EAP請求
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Sending EAPOL packet
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Sending out EAPOL packet
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] EAPOL packet sent to client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:response request action
EAPoL:EAP回應
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0000.0000.0000:unknown] Received EAPOL pkt (size=92) on l2 socket
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Queuing an EAPOL pkt on Authenticator Q
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Dequeued pkt: CODE= 2,TYPE= 4,LEN= 31
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Received pkt saddr = 0040.E93E.0000 , daddr = 0180.C200.0003, pae-ether-type = 0x888E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting EAPOL_EAP for 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering response state
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Response sent to the server from 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:request response action
[aaa-authen]: [16498]: UUID: 0, ra: 0 (debug): AAA/AUTHEN/8021X (00000000): Pick method list 'default'
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS/ENCODE: Best Local IP-Address 172.28.99.147 for Radius-Server 172.28.99.252
[radius-failover]: [16498]: UUID: 0, ra: 0 (debug): RADIUS/ENCODE: Nas-Identifier "C9300"
[aaa-author]: [16498]: UUID: 0, ra: 0 (debug): VALID SG handle
RADIUS: ACCESS-REQUEST
radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Send Access-Request to 172.28.99.252:1645 id 1812/84, len 340
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: authenticator 41 4d 76 8e 03 93 9f 05 - 5e fa f1 d6 ca 3c 84 08
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: User-Name [1] 11 "ixia_data"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Service-Type [6] 6 Framed [2]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 27
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 21 "service-type=Framed"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Framed-MTU [12] 6 1500
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Calling-Station-Id [31] 19 "00-40-E9-3E-00-00"
RADIUS: 02 fa 00 1f 04 10 02 b6 bc aa f4 91 2b d6 cf 9e 3b d5 44 96 78 d5 69 78 69 61 5f 64 61 74 61 [ +;Dxixia_data]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Message [79] 33
RADIUS: 3b 70 b1 dd 97 ac 47 ae 81 ca f8 78 5b a3 7b fe [ ;pGx[{]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Message-Authenticator[80] 18
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Key-Name [102] 2 *
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 49
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 43 "audit-session-id=AC1C639300000017E53C6E8E"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Vendor, Cisco [26] 20
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Cisco AVpair [1] 14 "method=dot1x"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-IP-Address [4] 6 172.28.99.147
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Nas-Identifier [32] 8 "C9300"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port-Id [87] 22 "GigabitEthernet1/0/2"
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: NAS-Port [5] 6 50014
RADIUS: 33 37 43 50 4d 53 65 73 73 69 6f 6e 49 44 3d 41 [37CPMSessionID=A]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: State [24] 81
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 43 31 43 36 33 39 33 30 30 30 30 30 30 31 37 45 [C1C639300000017E]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 35 33 43 36 45 38 45 3b 33 36 53 65 73 73 69 6f [53C6E8E;36Sessio]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 6e 49 44 3d 69 73 65 2d 70 6f 6c 2d 65 73 63 2f [nID=ise-pol-esc/]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: 32 34 30 31 39 38 34 32 39 2f 38 39 32 34 3b [ 240198429/8924;]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Sending a IPv4 Radius Packet
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Started 5 sec timeout
RADIUS:訪問拒絕
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Received from id 1645/84 172.28.99.252:0, Access-Reject, len 44---------->User not authenticaded
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: authenticator d1 a3 eb 43 11 45 6b 8f - 07 a7 34 dd 3a 49 67 c6
RADIUS: 04 fa 00 04
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: EAP-Message [79] 6
RADIUS: 80 77 07 f7 4d f8 a5 60 a6 b0 30 e4 67 85 ae ba [ wM`0g]
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS: Message-Authenticator[80] 18
[radius]: [16498]: UUID: 0, ra: 0 (debug): RADIUS:rad_code 3, suppress reject flag 0
[radius-authen]: [16498]: UUID: 0, ra: 0 (debug): RADIUS(00000000): Received from id 1645/84
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Received an EAP Fail
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting EAP_FAIL for 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:exiting response state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering fail state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:response fail action
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering idle state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting AUTH_FAIL on Client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:exiting authenticating state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering authc result state
[errmsg]: [16498]: UUID: 0, ra: 0 (note): %DOT1X-5-FAIL: Authentication failed for client (0040.E93E.0000) on Interface Gi1/0/2 AuditSessionID AC1C639300000017E53C6E8E
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Added username in dot1x
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Dot1x did not receive any key data
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Received Authz fail (result: 2) for the client 0x0A00000E (0040.E93E.0000)
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting_AUTHZ_FAIL on Client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: held
EAPoL:EAP拒絕
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Sending EAPOL packet
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0000.0000.0000:Gi1/0/2] Sending out EAPOL packet
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] EAPOL packet sent to client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting FAILOVER_RETRY on Client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: exiting held state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: entering restart
[dot1x]: [16498]: UUID: 0, ra: 0 (info): [0040.E93E.0000:Gi1/0/2] Sending create new context event to EAP for 0x0A00000E (0040.E93E.0000)
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:restart action called
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting RESTART on Client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting !EAP_RESTART on Client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:enter connecting state
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: restart connecting
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting RX_REQ on Client 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E: authenticating state entered
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:connecting authenticating action
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] Posting AUTH_START for 0x0A00000E
[dot1x]: [16498]: UUID: 0, ra: 0 (debug): [0040.E93E.0000:Gi1/0/2] 0x0A00000E:entering request state
其他資訊
預設設定
可選設定
定期重新驗證
您可以啟用定期的802.1x客戶端重新身份驗證並指定其發生頻率:
- authentication periodic -啟用客戶端的定期重新身份驗證
-
inactivity -以秒為單位的間隔,如果在此間隔後客戶端未進行任何活動,則表示未授權
-
reauthenticate -啟動自動重新身份驗證嘗試之前經過的時間(以秒為單位)
-
restartvalue -嘗試驗證未授權埠之前的時間間隔(以秒為單位)
-
unauthorizedvalue -刪除未授權會話的間隔秒數
authentication periodic
authentication timer {{[inactivity | reauthenticate | restart | unauthorized]} {value}}
違規模式
您可以配置802.1x埠,使其關閉、生成系統日誌錯誤,或者當裝置連線到已啟用802.1x的埠時,丟棄來自新裝置的資料包,或者在該埠上驗證有關裝置的允許最大數量。
-
shutdown -因錯誤而停用埠。
-
restrict- 生成系統日誌錯誤。
-
protect -丟棄來自將流量傳送到埠的任何新裝置的資料包。
-
replace -刪除當前會話並使用新主機進行身份驗證。
authentication violation {shutdown | restrict | protect | replace}
更改靜默期
authentication timer restart介面配置命令控制空閒期,它規定了在交換機無法對客戶端進行身份驗證之後交換機保持空閒的設定時間段。值的範圍是1到65535秒。
authentication timer restart {seconds}
更改交換機到客戶端的重傳時間
客戶端使用EAP-response/identity幀響應來自交換機的EAP請求/身份幀。如果交換機未收到此響應,它將等待一段設定的時間(稱為重新傳輸時間),然後重新傳送幀。
authentication timer reauthenticate {seconds}
設定交換機到客戶端的幀重新傳輸編號
您可以更改交換機在重新啟動身份驗證過程之前向客戶端傳送EAP請求/身份幀(假設沒有收到響應)的次數。 範圍介於 1 至 10。
dot1x max-reauth-req {count}
配置主機模式
您可以在802.1x授權連線埠上允許多個主機(使用者端)。
-
multi-auth -在語音VLAN和資料VLAN上允許多個透過身份驗證的客戶端。
-
多主機- 在單個主機透過身份驗證後,允許802.1x授權埠上有多個主機。
- 多域- 允許在經過IEEE 802.1x授權的埠上驗證主機和語音裝置,例如IP電話(思科或非Cisco)。
authentication host-mode [multi-auth | multi-domain | multi-host | single-host]
啟用MAC Move
MAC移動允許經過身份驗證的主機從裝置的一個埠移動到另一個埠。
authentication mac-move permit
啟用MAC取代
MAC replace允許主機替換埠上經過身份驗證的主機。
-
protect - 埠在不生成系統消息的情況下丟棄具有意外MAC地址的資料包。
-
restrict - CPU丟棄衝突資料包,並生成系統消息。
-
shutdown - 埠在收到意外的MAC地址時因錯誤而被停用。
authentication violation {protect | replace | restrict | shutdown}
設定重新驗證號碼
您還可以更改裝置在埠變為未授權狀態之前重新啟動身份驗證過程的次數。 範圍為0至10
dot1x max-req {count}
配置訪客VLAN
配置訪客VLAN時,如果伺服器未收到對其EAP請求/身份幀的響應,則不支援802.1x的客戶端將被放入訪客VLAN中。
authentication event no-response action authorize vlan {vlan-id}
配置受限制的VLAN
在裝置上配置受限制的VLAN時,如果身份驗證伺服器未收到有效的使用者名稱和密碼,則符合IEEE 802.1x標準的客戶端將被移動到受限制的VLAN中。
authentication event fail action authorize vlan {vlan-id}
在受限制的VLAN上配置身份驗證嘗試次數
您可使用authentication event fail retryretry countinterface configuration命令配置將使用者分配到受限制VLAN之前允許的最大身份驗證嘗試次數。允許的身份驗證嘗試範圍為1至3。
authentication event fail retry {retry count}
使用重要語音VLAN配置802.1x不可訪問的身份驗證旁路
您可以在埠上配置一個關鍵的語音VLAN並啟用不可訪問的身份驗證旁路功能。
- authorize - 將嘗試進行身份驗證的所有新主機移動到使用者指定的關鍵VLAN
- reinitialize - 將埠上的所有授權主機移動到使用者指定的關鍵VLAN
authentication event server dead action {authorize | reinitialize} vlanvlan-id] authentication event server dead action authorize voice
使用WoL配置802.1x身份驗證
您可以啟用具有Wake on LAN (WoL)的802.1x驗證
authentication control-direction both
配置MAC身份驗證旁路
mab
配置靈活的身份驗證排序
authentication order [ dot1x | mab ] | {webauth}
authentication priority [ dot1x | mab ] | {webauth}
配置語音感知802.1x安全
您可以在裝置上使用語音感知802.1x安全功能僅停用發生安全違規的VLAN,無論是資料還是語音VLAN。 在資料VLAN上發現的安全違規僅導致資料VLAN關閉。這是全域組態。
errdisable detect cause security-violation shutdown vlan errdisable recovery cause security-violation
流程圖
身份驗證流程圖
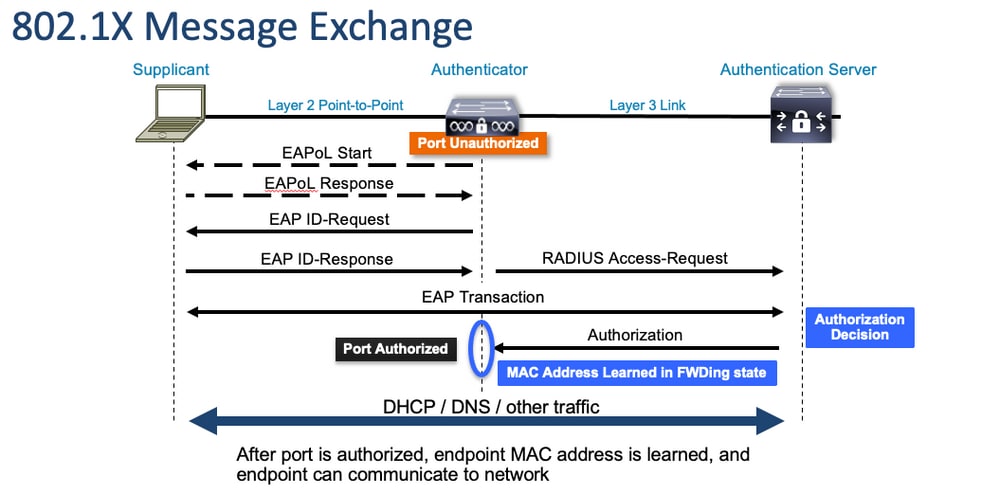
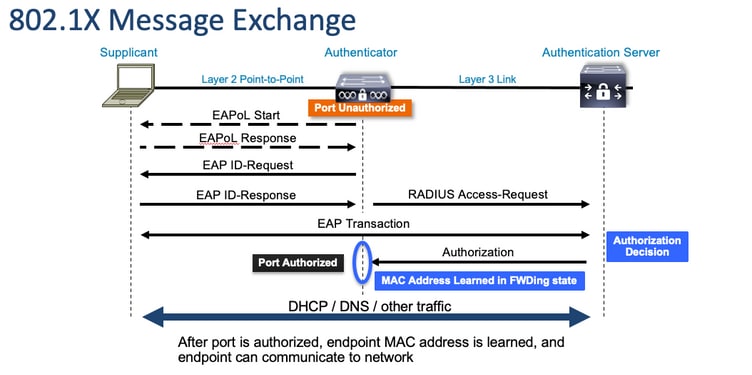
連線埠型驗證初始和訊息交換
此圖顯示客戶端向RADIUS伺服器發起消息交換。
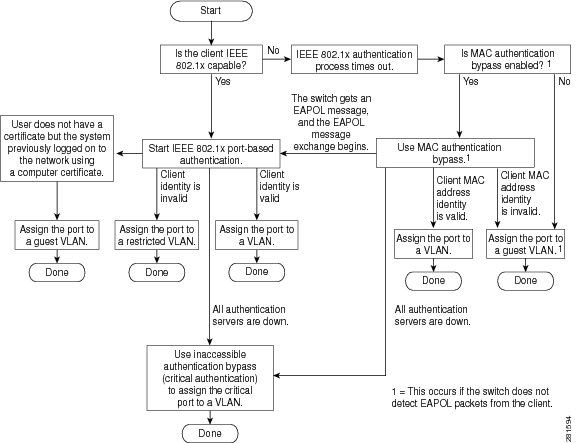
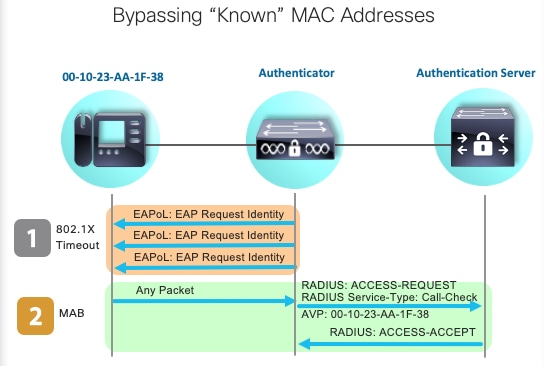
MAB身份驗證啟動和消息交換
此圖顯示MAC驗證略過(MAB)期間的訊息交換
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
21-Sep-2023 |
初始版本 |
由思科工程師貢獻
- Jason BabbCisco TAC Engineer
- Gerardo Trejo OrtegaCisco TAC Engineer
 意見
意見