使用OSPF配置通過IPsec的GRE隧道
簡介
一般IP安全(IPsec)配置無法傳輸路由協定(如增強型內部網關路由協定(EIGRP)和開放最短路徑優先(OSPF))或非IP流量(如網際網路資料包交換(IPX)和AppleTalk)。本文檔說明了如何通過IPsec在使用路由協定的不同網路與非IP流量之間進行路由。此範例使用通用路由封裝(GRE)來完成不同網路之間的路由。
請參閱PIX/ASA 7.x及更高版本:帶OSPF的VPN/IPsec配置示例,瞭解有關如何在Cisco PIX安全裝置軟體版本7.x或Cisco Adaptive Security Appliance(ASA)上為沒有GRE隧道的VPN/IPsec配置開放最短路徑優先(OSPF)的詳細資訊。
有關如何配置三台路由器之間的中心輻射型IPsec設計的資訊,請參閱配置IPsec路由器到路由器的中心輻射型IPsec和輻射型IPsec之間的通訊。
有關如何使用網路位址轉譯(NAT)在GRE通道上設定基本Cisco IOS®防火牆組態的資訊,請參閱使用IOS防火牆和NAT在GRE通道上設定路由器到路由器IPSec(預共用金鑰)。
必要條件
需求
嘗試此組態之前,請確保符合以下要求:
-
應用密碼編譯對應之前,請確保通道正常運作。
-
請參閱在Windows和Sun系統上調整IP MTU、TCP MSS和PMTUD,瞭解可能的最大傳輸單元(MTU)問題的資訊。
採用元件
本文中的資訊係根據以下軟體和硬體版本:
-
執行Cisco IOS軟體版本12.4(8)的Cisco 3600
-
執行Cisco IOS軟體版本12.4(8)的Cisco 2600
-
PIX防火牆(Lion)軟體版本6.3(5)
-
PIX防火牆(Tiger)軟體版本6.3(5)
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路正在作用,請確保您已瞭解任何指令可能造成的影響。
慣例
如需文件慣例的詳細資訊,請參閱思科技術提示慣例。
設定
本節提供用於設定本檔案中所述功能的資訊。
註:使用Command Lookup Tool(僅限註冊客戶)查詢有關本文檔中使用的命令的更多資訊。
網路圖表
本檔案會使用以下網路設定:
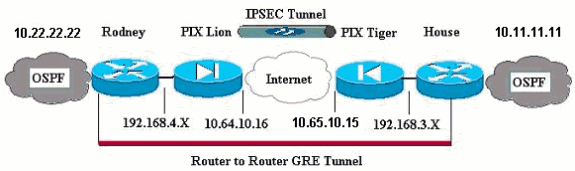
注意:此配置中使用的IP編址方案在Internet上不能合法路由。以下是RFC 1918 ![]() 位址,已在實驗室環境中使用。
位址,已在實驗室環境中使用。
註:加密不支援Cisco 7600系列路由器。您可能必須安裝VPN模組才能使此操作生效。
組態
本檔案會使用以下設定:
| PIX Lion |
|---|
PIX Version 6.3(5) interface ethernet0 auto interface ethernet1 auto interface ethernet2 auto shutdown interface ethernet3 auto shutdown interface ethernet4 auto shutdown interface ethernet5 auto shutdown nameif ethernet0 outside security0 nameif ethernet1 inside security100 nameif ethernet2 intf2 security4 nameif ethernet3 intf3 security6 nameif ethernet4 intf4 security8 nameif ethernet5 intf5 security10 enable password 8Ry2YjIyt7RRXU24 encrypted passwd 2KFQnbNIdI.2KYOU encrypted hostname Lion fixup protocol dns maximum-length 512 fixup protocol ftp 21 fixup protocol h323 h225 1720 fixup protocol h323 ras 1718-1719 fixup protocol http 80 fixup protocol rsh 514 fixup protocol rtsp 554 fixup protocol sip 5060 fixup protocol sip udp 5060 fixup protocol skinny 2000 fixup protocol smtp 25 fixup protocol sqlnet 1521 fixup protocol tftp 69 names !--- Defines interesting traffic that is protected by the IPsec tunnel. access-list 101 permit gre 192.168.4.0 255.255.255.0 192.168.3.0 255.255.255.0 !--- Do not perform NAT for traffic to other PIX Firewall. access-list nonat permit ip 192.168.4.0 255.255.255.0 192.168.3.0 255.255.255.0 pager lines 24 mtu outside 1500 mtu inside 1500 mtu intf2 1500 mtu intf3 1500 mtu intf4 1500 mtu intf5 1500 ip address outside 10.64.10.16 255.255.255.224 ip address inside 192.168.4.1 255.255.255.0 !--- Output suppressed. global (outside) 1 interface !--- Do not Network Address Translate (NAT) traffic. nat (inside) 0 access-list nonat nat (inside) 1 0.0.0.0 0.0.0.0 0 0 route outside 0.0.0.0 0.0.0.0 10.64.10.1 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h323 0:05:00 s0 timeout h323 0:05:00 mgcp 0:05:00 sip 0:30:00 sip_media 0:02:00 timeout sip-disconnect 0:02:00 sip-invite 0:03:00 timeout uauth 0:05:00 absolute aaa-server TACACS+ protocol tacacs+ aaa-server TACACS+ max-failed-attempts 3 aaa-server TACACS+ deadtime 10 aaa-server RADIUS protocol radius aaa-server RADIUS max-failed-attempts 3 aaa-server RADIUS deadtime 10 aaa-server LOCAL protocol local no snmp-server location no snmp-server contact snmp-server community public no snmp-server enable traps floodguard enable !--- Trust IPSec traffic and avoid going through !--- access control lists (ACLs)/NAT. sysopt connection permit-ipsec !--- IPsec configuration. crypto ipsec transform-set pixset esp-des esp-md5-hmac crypto map pixmap 20 ipsec-isakmp crypto map pixmap 20 match address 101 crypto map pixmap 20 set peer 10.65.10.15 crypto map pixmap 20 set transform-set pixset crypto map pixmap interface outside isakmp enable outside !--- IKE parameters. isakmp key ******** address 10.65.10.15 netmask 255.255.255.255 isakmp identity address isakmp policy 20 authentication pre-share isakmp policy 20 encryption des isakmp policy 20 hash md5 isakmp policy 20 group 1 isakmp policy 20 lifetime 3600 telnet timeout 5 ssh 10.104.205.124 255.255.255.255 outside ssh timeout 5 terminal width 80 Cryptochecksum:d39b3d449563c7cd434b43f82f0f0a21 : end |
| PIX老虎 |
|---|
PIX Version 6.3(5) interface ethernet0 auto interface ethernet1 auto interface ethernet2 auto shutdown interface ethernet3 auto shutdown interface ethernet4 auto shutdown interface ethernet5 auto shutdown nameif ethernet0 outside security0 nameif ethernet1 inside security100 nameif ethernet2 intf2 security4 nameif ethernet3 intf3 security6 nameif ethernet4 intf4 security8 nameif ethernet5 intf5 security10 enable password 8Ry2YjIyt7RRXU24 encrypted passwd 2KFQnbNIdI.2KYOU encrypted hostname Tiger fixup protocol dns maximum-length 512 fixup protocol ftp 21 fixup protocol h323 h225 1720 fixup protocol h323 ras 1718-1719 fixup protocol http 80 fixup protocol rsh 514 fixup protocol rtsp 554 fixup protocol sip 5060 fixup protocol sip udp 5060 fixup protocol skinny 2000 fixup protocol smtp 25 fixup protocol sqlnet 1521 fixup protocol tftp 69 names access-list 101 permit gre 192.168.3.0 255.255.255.0 192.168.4.0 255.255.255.0 access-list nonat permit ip 192.168.3.0 255.255.255.0 192.168.4.0 255.255.255.0 mtu outside 1500 mtu inside 1500 mtu intf2 1500 mtu intf3 1500 mtu intf4 1500 mtu intf5 1500 ip address outside 10.65.10.15 255.255.255.224 ip address inside 192.168.3.1 255.255.255.0 !--- Output suppressed. global (outside) 1 interface !--- Do not NAT traffic. nat (inside) 0 access-list nonat nat (inside) 1 0.0.0.0 0.0.0.0 0 0 route outside 0.0.0.0 0.0.0.0 10.64.10.1 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h323 0:05:00 s0 timeout h323 0:05:00 mgcp 0:05:00 sip 0:30:00 sip_media 0:02:00 timeout sip-disconnect 0:02:00 sip-invite 0:03:00 timeout uauth 0:05:00 absolute aaa-server TACACS+ protocol tacacs+ aaa-server TACACS+ max-failed-attempts 3 aaa-server TACACS+ deadtime 10 aaa-server RADIUS protocol radius aaa-server RADIUS max-failed-attempts 3 aaa-server RADIUS deadtime 10 aaa-server LOCAL protocol local no snmp-server location no snmp-server contact snmp-server community public no snmp-server enable traps floodguard enable sysopt connection permit-ipsec !--- IPsec parameters. crypto ipsec transform-set pixset esp-des esp-md5-hmac crypto map pixmap 20 ipsec-isakmp crypto map pixmap 20 match address 101 crypto map pixmap 20 set peer 10.64.10.16 crypto map pixmap 20 set transform-set pixset crypto map pixmap interface outside !--- IKE parameters. isakmp enable outside isakmp key ******** address 10.64.10.16 netmask 255.255.255.255 isakmp identity address isakmp policy 20 authentication pre-share isakmp policy 20 encryption des isakmp policy 20 hash md5 isakmp policy 20 group 1 isakmp policy 20 lifetime 3600 telnet timeout 5 ssh timeout 5 terminal width 80 Cryptochecksum:a0a7ac847b05d9d080d1c442ef053a0b : end |
| 羅德尼 |
|---|
version 12.4 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname rodney ! memory-size iomem 15 ip subnet-zero ! ip audit notify log ip audit po max-events 100 ! ! interface Loopback1 ip address 10.22.22.22 255.255.255.0 ! interface Tunnel0 ip address 10.1.1.2 255.255.255.0 !--- Tunnel source. tunnel source Ethernet0/1 !--- Tunnel destination. tunnel destination 192.168.3.2 ! interface Ethernet0/0 no ip address ! interface Serial0/0 no ip address shutdown ! interface Ethernet0/1 ip address 192.168.4.2 255.255.255.0 ! interface Serial0/1 no ip address shutdown ! router ospf 22 log-adjacency-changes network 10.1.1.0 0.0.0.255 area 0 network 10.22.22.0 0.0.0.255 area 0 ! ip classless ip route 0.0.0.0 0.0.0.0 192.168.4.1 !--- The 10.11.11.0 traffic is passed through !--- the GRE tunnel. ip route 10.11.11.0 255.255.255.0 Tunnel0 no ip http server ! line con 0 line aux 0 line vty 0 4 login ! end! End |
| 路由器外殼 |
|---|
version 12.4 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname house ! ip subnet-zero no ip domain-lookup ! ! interface Loopback1 ip address 10.11.11.11 255.255.255.0 ! interface Tunnel0 ip address 10.1.1.1 255.255.255.0 !--- Tunnel source. tunnel source FastEthernet0/1 !--- Tunnel destination. tunnel destination 192.168.4.2 ! interface FastEthernet0/0 no ip address shutdown duplex auto speed auto ! interface FastEthernet0/1 ip address 192.168.3.2 255.255.255.0 duplex auto speed auto ! interface FastEthernet4/0 no ip address shutdown duplex auto speed auto ! router ospf 11 log-adjacency-changes network 10.1.1.0 0.0.0.255 area 0 network 10.11.11.0 0.0.0.255 area 0 ! ip classless ip route 0.0.0.0 0.0.0.0 192.168.3.1 !--- The 10.22.22.0 traffic is passed through !--- the GRE tunnel. ip route 10.22.22.0 255.255.255.0 Tunnel0 ip http server ! line con 0 line aux 0 line vty 0 4 |
驗證
目前沒有適用於此組態的驗證程序。
疑難排解
本節提供的資訊可用於對組態進行疑難排解。
請參閱排除PIX故障以在已建立的IPSec隧道上傳遞資料流量,以瞭解有關排除PIX和IPsec隧道故障的其他資訊。
疑難排解指令
輸出直譯器工具(僅供已註冊客戶使用)(OIT)支援某些show命令。使用OIT檢視show命令輸出的分析。
附註:使用 debug 指令之前,請先參閱有關 Debug 指令的重要資訊。
PIX IPsec正常調試
-
show crypto isakmp sa — 顯示對等體之間構建的網際網路安全關聯管理協定(ISAKMP)安全關聯(SA)。
Lion#show crypto isakmp sa Total : 1 Embryonic : 0 dst src state pending created 10.65.10.15 10.64.10.16 QM_IDLE 0 1 Tiger#show crypto isakmp sa Total SAs : 1 Embryonic : 0 dst src state pending created 10.65.10.15 10.64.10.16 QM_IDLE 0 1
-
show crypto engine connection active — 顯示已建立的每個第2階段SA和已傳送的流量數量。
Lion#show crypto engine connection active Crypto Engine Connection Map: size = 8, free = 6, used = 2, active = 2 Tiger#show crypto engine connection active Crypto Engine Connection Map: size = 8, free = 6, used = 2, active = 2
-
show debug — 顯示調試輸出。
Lion#show debug debug crypto ipsec debug crypto isakmp debug crypto engine crypto_isakmp_process_block: src 10.65.10.15, dest 10.64.10.16 OAK_MM exchange ISAKMP (0): processing SA payload. message ID = 0 ISAKMP (0): Checking ISAKMP transform 1 against priority 20 policy ISAKMP: encryption DES-CBC ISAKMP: hash MD5 ISAKMP: default group 1 ISAKMP: auth pre-share ISAKMP: life type in seconds ISAKMP: life duration (basic) of 3600 ISAKMP (0): atts are acceptable. Next payload is 0 ISAKMP (0): SA is doing pre-shared key authentication using id type ID_IPV4_ADDR return status is IKMP_NO_ERROR# crypto_isakmp_process_block: src 10.65.10.15, dest 10.64.10.16 OAK_MM exchange ISAKMP (0): processing KE payload. message ID = 0 ISAKMP (0): processing NONCE payload. message ID = 0 ISAKMP (0): processing vendor id payload ISAKMP (0): speaking to another IOS box! ISAKMP (0): ID payload next-payload : 8 type : 1 protocol : 17 port : 500 length : 8 ISAKMP (0): Total payload length: 12 return status is IKMP_NO_ERROR crypto_isakmp_process_block: src 10.65.10.15, dest 10.64.10.16 OAK_MM exchange ISAKMP (0): processing ID payload. message ID = 0 ISAKMP (0): processing HASH payload. message ID = 0 ISAKMP (0): SA has been authenticated ISAKMP (0): beginning Quick Mode exchange, M-ID of 1220019031:48b80357IPSEC(key. IPSEC(spi_response): getting spi 0xa67177c5(2792454085) for SA from 10.65.10.15 to 10.64.10.16 for prot 3 return status is IKMP_NO_ERROR crypto_isakmp_process_block: src 10.65.10.15, dest 10.64.10.16 OAK_QM exchange oakley_process_quick_mode: OAK_QM_IDLE ISAKMP (0): processing SA payload. message ID = 1220019031 ISAKMP : Checking IPSec proposal 1 ISAKMP: transform 1, ESP_DES ISAKMP: attributes in transform: ISAKMP: encaps is 1 ISAKMP: SA life type in seconds ISAKMP: SA life duration (basic) of 28800 ISAKMP: SA life type in kilobytes ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0 ISAKMP: authenticator is HMAC-MD5 ISAKMP (0): atts are acceptable.IPSEC(validate_proposal_request): proposal part, (key eng. msg.) dest= 10.65.10.15, src= 10.64.10.16, dest_proxy= 192.168.3.0/255.255.255.0/0/0 (type=4), src_proxy= 192.168.4.0/255.255.255.0/0/0 (type=4), protocol= ESP, transform= esp-des esp-md5-hmac , lifedur= 0s and 0kb, spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x4 ISAKMP (0): processing NONCE payload. message ID = 1220019031 ISAKMP (0): processing ID payload. message ID = 1220019031 ISAKMP (0): processing ID payload. message ID = 1220019031map_alloc_entry: allo2 map_alloc_entry: allocating entry 1 ISAKMP (0): Creating IPSec SAs inbound SA from 10.65.10.15 to 10.64.10.16 (proxy 192.168.3) has spi 2792454085 and conn_id 2 and flags 4 lifetime of 28800 seconds lifetime of 4608000 kilobytes outbound SA from 10.64.10.16 to 10.65.10.15 (proxy 192.168.) has spi 285493108 and conn_id 1 and flags 4 lifetime of 28800 seconds lifetime of 4608000 kilobytesIPSEC(key_engine): got a queue event... IPSEC(initialize_sas): , (key eng. msg.) dest= 10.64.10.16, src= 10.65.10.15, dest_proxy= 192.168.4.0/255.255.255.0/0/0 (type=4), src_proxy= 192.168.3.0/255.255.255.0/0/0 (type=4), protocol= ESP, transform= esp-des esp-md5-hmac , lifedur= 28800s and 4608000kb, spi= 0xa67177c5(2792454085), conn_id= 2, keysize= 0, flags= 0x4 IPSEC(initialize_sas): , (key eng. msg.) src= 10.64.10.16, dest= 10.65.10.15, src_proxy= 192.168.4.0/255.255.255.0/0/0 (type=4), dest_proxy= 192.168.3.0/255.255.255.0/0/0 (type=4), protocol= ESP, transform= esp-des esp-md5-hmac , lifedur= 28800s and 4608000kb, spi= 0x11044774(285493108), conn_id= 1, keysize= 0, flags= 0x4 return status is IKMP_NO_ERROR
路由器GRE通過路由和Ping
-
show ip route — 顯示IP路由表條目。
rodney#show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 192.168.4.1 to network 0.0.0.0 10.0.0.0/24 is subnetted, 1 subnets C 10.1.1.0 is directly connected, Tunnel0 10.0.0.0/24 is subnetted, 1 subnets C 10.20.20.0 is directly connected, Loopback0 10.0.0.0/24 is subnetted, 1 subnets C 10.22.22.0 is directly connected, Loopback1 C 192.168.4.0/24 is directly connected, Ethernet0/1 10.0.0.0/24 is subnetted, 1 subnets S 10.10.10.0 is directly connected, Tunnel0 10.0.0.0/32 is subnetted, 1 subnets O 10.11.11.11 [110/11112] via 10.1.1.1, 03:34:01, Tunnel0 S* 0.0.0.0/0 [1/0] via 192.168.4.1 rodney# rodney#ping 10.11.11.11 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.11.11.11, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms house#show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is 192.168.3.1 to network 0.0.0.0 10.0.0.0/24 is subnetted, 1 subnets C 1.1.1.0 is directly connected, Tunnel0 10.0.0.0/24 is subnetted, 1 subnets S 10.20.20.0 is directly connected, Tunnel0 10.0.0.0/32 is subnetted, 1 subnets O 10.22.22.22 [110/11112] via 10.1.1.2, 03:33:39, Tunnel0 10.0.0.0/24 is subnetted, 1 subnets C 10.10.10.0 is directly connected, Loopback0 10.0.0.0/24 is subnetted, 1 subnets C 10.11.11.0 is directly connected, Loopback1 C 192.168.3.0/24 is directly connected, FastEthernet0/1 S* 0.0.0.0/0 [1/0] via 192.168.3.1 house#ping 10.22.22.22 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.22.22.22, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/4 ms
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
26-Sep-2008 |
初始版本 |
 意見
意見