在具有VPN服務模組的Catalyst 6500和PIX防火牆之間的IPSec LAN到LAN隧道配置示例
簡介
本文描述如何在具有IPSec VPN服務模組(W)的Cisco Catalyst 6500系列交換機和Cisco PIX防火牆之間建立IPSec LAN到LAN隧道。
必要條件
需求
本文件沒有特定需求。
採用元件
本文中的資訊係根據以下軟體和硬體版本:
-
適用於Catalyst 6000系列Supervisor Engine的Cisco IOS®軟體版本12.2(14)SY2,含IPSec VPN服務模組
-
Cisco PIX防火牆軟體版本6.3(3)
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路正在作用,請確保您已瞭解任何指令可能造成的影響。
慣例
如需文件慣例的詳細資訊,請參閱思科技術提示慣例。
背景資訊
Catalyst 6500 VPN服務模組具有兩個千兆乙太網(GE)埠,沒有外部可見聯結器。這些埠可定址僅用於配置。連線埠1一律是內部連線埠。此埠處理來自和流向內部網路的所有流量。第二個埠(埠2)處理來自WAN或外部網路的所有流量。這兩個埠始終在802.1Q中繼模式下配置。VPN服務模組使用一種稱為線路中凸點(BITW)的技術來傳輸封包。
資料包由一對VLAN處理,一個VLAN內部的第3層和一個外部VLAN的第2層。封包從內部到外部,透過稱為編碼位址識別邏輯(EARL)的方法路由到內部VLAN。在對資料包進行加密後,VPN服務模組將使用相應的外部VLAN。在解密過程中,使用外部VLAN將來自外部的封包橋接到VPN服務模組。VPN服務模組解密封包並將該VLAN對應到內部VLAN後,EARL會將封包路由到適當的LAN連線埠。第3層內部VLAN和第2層外部VLAN通過crypto connect vlan命令連線在一起。Catalyst 6500系列交換器中有三種型別的連線埠:
-
路由埠 — 預設情況下,所有乙太網埠都是Cisco IOS中的路由埠。這些連線埠具有與其相關聯的隱藏VLAN。
-
存取連接埠 — 這些連線埠具有與其相關的外部或VLAN中繼線通訊協定(VTP)VLAN。您可以將多個埠與定義的VLAN關聯。
-
中繼埠 — 這些埠承載許多外部或VTP VLAN,所有資料包都以802.1Q報頭封裝在這些埠上。
設定
本節提供用於設定本文件中所述功能的資訊。
註:使用Command Lookup Tool(僅限註冊客戶)查詢有關本文檔中使用的命令的更多資訊。
網路圖表
本檔案會使用以下網路設定:
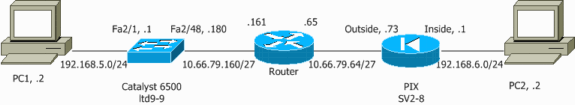
使用第2層接入或中繼埠配置IPSec
執行以下步驟,藉助外部物理介面的第2層接入或中繼埠配置IPSec。
-
將內部VLAN新增到VPN服務模組的內部埠。
假設VPN服務模組位於插槽4中。使用VLAN 100作為內部VLAN,使用VLAN 209作為外部VLAN。按如下方式配置VPN服務模組GE埠:
interface GigabitEthernet4/1 no ip address flowcontrol receive on flowcontrol send off switchport switchport trunk encapsulation dot1q switchport trunk allowed vlan 1,100,1002-1005 switchport mode trunk cdp enable interface GigabitEthernet4/2 no ip address flowcontrol receive on flowcontrol send off switchport switchport trunk encapsulation dot1q switchport trunk allowed vlan 1,209,1002-1005 switchport mode trunk cdp enable spanning-tree portfast trunk
-
新增VLAN 100介面和隧道終止的介面(在本例中為介面Vlan 209,如下所示)。
interface Vlan100 ip address 10.66.79.180 255.255.255.224 interface Vlan209 no ip address crypto connect vlan 100
-
將外部物理埠配置為接入或中繼埠(在本例中為FastEthernet 2/48,如下所示)。
!--- This is the configuration that uses an access port. interface FastEthernet2/48 no ip address switchport switchport access vlan 209 switchport mode access !--- This is the configuration that uses a trunk port. interface FastEthernet2/48 no ip address switchport switchport trunk encapsulation dot1q switchport mode trunk
-
建立旁路NAT。將這些條目新增到no nat語句中,以免除在這些網路之間的命名:
access-list inside_nat0_outbound permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255 global (outside) 1 interface nat (inside) 0 access-list inside_nat0_outbound nat (inside) 1 192.168.5.0 255.255.255.0
-
建立密碼編譯組態以及定義要加密的流量的存取控制清單(ACL)。
-
建立加密ACL(在本案例中為ACL 100 — 相關流量),定義從內部網路192.168.5.0/24到遠端網路192.168.6.0/24的流量,如下所示:
access-list 100 permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255
-
定義您的Internet安全關聯和金鑰管理協定(ISAKMP)策略提案,如下所示:
crypto isakmp policy 1 hash md5 authentication pre-share group 2
-
發出以下命令(在本例中)以使用和定義預共用金鑰:
crypto isakmp key cisco address 10.66.79.73
-
定義您的IPSec建議,如下所示:
crypto ipsec transform-set cisco esp-des esp-md5-hmac
-
建立加密對映語句,如下所示:
crypto map cisco 10 ipsec-isakmp set peer 10.66.79.73 set transform-set cisco match address 100
-
-
將密碼編譯對應套用到VLAN 100介面,如下所示:
interface vlan100 crypto map cisco
使用以下配置:
| Catalyst 6500 |
|---|
!--- Define the Phase 1 policy. crypto isakmp policy 1 hash md5 authentication pre-share group 2 crypto isakmp key cisco address 10.66.79.73 ! ! !--- Define the encryption policy for this setup. crypto ipsec transform-set cisco esp-des esp-md5-hmac ! !--- Define a static crypto map entry for the peer !--- with mode ipsec-isakmp. !--- This indicates that Internet Key Exchange (IKE) !--- is used to establish the IPSec !--- security associations (SAs) to protect the traffic !--- specified by this crypto map entry. crypto map cisco 10 ipsec-isakmp set peer 10.66.79.73 set transform-set cisco match address 100 ! ! no spanning-tree vlan 100 ! ! ! interface FastEthernet2/1 ip address 192.168.5.1 255.255.255.0 ! !--- This is the outside Layer 2 port that allows !--- VLAN 209 traffic to enter. interface FastEthernet2/48 no ip address switchport switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet4/1 no ip address flowcontrol receive on flowcontrol send off switchport switchport trunk encapsulation dot1q !--- VLAN 100 is defined as the Interface VLAN (IVLAN). switchport trunk allowed vlan 1,100,1002-1005 switchport mode trunk cdp enable ! interface GigabitEthernet4/2 no ip address flowcontrol receive on flowcontrol send off switchport switchport trunk encapsulation dot1q !--- The Port VLAN (PVLAN) configuration is handled transparently by !--- the VPN service module without user configuration !--- or involvement. It also is not shown in the configuration. !--- Note: For every IVLAN, a corresponding PVLAN exists. switchport trunk allowed vlan 1,209,1002-1005 switchport mode trunk cdp enable spanning-tree portfast trunk ! interface Vlan1 no ip address shutdown ! !--- This is the IVLAN that is configured to intercept the traffic !--- destined to the secure port on which the inside port !--- of the VPN service module is the only port present. interface Vlan100 ip address 10.66.79.180 255.255.255.224 crypto map cisco !--- This is the secure port that is a virtual Layer 3 interface. !--- This interface purposely does not have a Layer 3 IP address !--- configured. This is normal for the BITW process. !--- The IP address is moved from this interface to the VLAN 100 to !--- accomplish BITW. This brings the VPN service module into !--- the packet path. interface Vlan209 no ip address crypto connect vlan 100 ! ip classless global (outside) 1 interface !--- NAT 0 prevents NAT for networks specified in the ACL inside_nat0_outbound. nat (inside) 0 access-list inside_nat0_outbound nat (inside) 1 192.168.5.0 255.255.255.0 !--- Configure the routing so that the device !--- is directed to reach its destination network. ip route 0.0.0.0 0.0.0.0 10.66.79.161 !--- This access list (inside_nat0_outbound) is used with the nat zero command. !--- This prevents traffic which matches the access list from undergoing !--- network address translation (NAT). The traffic specified by this ACL is !--- traffic that is to be encrypted and !--- sent across the VPN tunnel. This ACL is intentionally !--- the same as (100). !--- Two separate access lists should always be used in this configuration. access-list inside_nat0_outbound permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255 !--- This is the crypto ACL. access-list 100 permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255 |
| PIX防火牆 |
|---|
SV2-8(config)# show run : Saved : PIX Version 6.3(3) interface ethernet0 auto interface ethernet1 auto interface ethernet2 auto shutdown interface ethernet3 auto shutdown interface ethernet4 auto shutdown interface ethernet5 auto shutdown interface ethernet6 auto shutdown nameif ethernet0 outside security0 nameif ethernet1 inside security100 nameif ethernet2 intf2 security10 nameif ethernet3 intf3 security15 nameif ethernet4 intf4 security20 nameif ethernet5 intf5 security25 nameif ethernet6 intf6 security30 enable password 8Ry2YjIyt7RRXU24 encrypted passwd 2KFQnbNIdI.2KYOU encrypted hostname SV2-8 domain-name cisco.com fixup protocol dns maximum-length 512 fixup protocol ftp 21 fixup protocol h323 h225 1720 fixup protocol h323 ras 1718-1719 fixup protocol http 80 fixup protocol ils 389 fixup protocol rsh 514 fixup protocol rtsp 554 fixup protocol sip 5060 fixup protocol sip udp 5060 fixup protocol skinny 2000 fixup protocol smtp 25 fixup protocol sqlnet 1521 fixup protocol tftp 69 names !--- This is the traffic to the router. access-list 100 permit ip 192.168.6.0 255.255.255.0 192.168.5.0 255.255.255.0 access-list nonat permit ip 192.168.6.0 255.255.255.0 192.168.5.0 255.255.255.0 pager lines 24 mtu outside 1500 mtu inside 1500 mtu intf2 1500 mtu intf3 1500 mtu intf4 1500 mtu intf5 1500 mtu intf6 1500 ip address outside 10.66.79.73 255.255.255.224 ip address inside 192.168.6.1 255.255.255.0 ip address intf2 127.0.0.1 255.255.255.255 no ip address intf3 no ip address intf4 no ip address intf5 no ip address intf6 ip audit info action alarm ip audit attack action alarm no failover failover timeout 0:00:00 failover poll 15 no failover ip address outside no failover ip address inside no failover ip address intf2 no failover ip address intf3 no failover ip address intf4 no failover ip address intf5 no failover ip address intf6 pdm history enable arp timeout 14400 global (outside) 1 interface nat (inside) 0 access-list nonat nat (inside) 1 192.168.6.0 255.255.255.0 0 0 route outside 0.0.0.0 0.0.0.0 10.66.79.65 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h225 1:00:00 timeout h323 0:05:00 mgcp 0:05:00 sip 0:30:00 sip_media 0:02:00 timeout uauth 0:05:00 absolute aaa-server TACACS+ protocol tacacs+ aaa-server RADIUS protocol radius aaa-server LOCAL protocol local no snmp-server location no snmp-server contact snmp-server community public no snmp-server enable traps floodguard enable !--- These are IPSec policies. sysopt connection permit-ipsec crypto ipsec transform-set cisco esp-des esp-md5-hmac crypto map cisco 10 ipsec-isakmp crypto map cisco 10 match address 100 crypto map cisco 10 set peer 10.66.79.180 crypto map cisco 10 set transform-set cisco crypto map cisco interface outside !--- These are IKE policies. isakmp enable outside isakmp key ******** address 10.66.79.180 netmask 255.255.255.255 isakmp policy 1 authentication pre-share isakmp policy 1 encryption des isakmp policy 1 hash md5 isakmp policy 1 group 2 isakmp policy 1 lifetime 86400 telnet timeout 5 ssh timeout 5 console timeout 0 terminal width 80 Cryptochecksum:244c86c9beab00bda8f790502ca74db9 : end |
使用路由埠配置IPSec
執行以下步驟,藉助外部物理介面的第3層路由埠配置IPSec。
-
將內部VLAN新增到VPN服務模組的內部埠。
假設VPN服務模組位於插槽4中。使用VLAN 100作為內部VLAN,使用VLAN 209作為外部VLAN。按如下方式配置VPN服務模組GE埠:
interface GigabitEthernet4/1 no ip address flowcontrol receive on flowcontrol send off switchport switchport trunk encapsulation dot1q switchport trunk allowed vlan 1,100,1002-1005 switchport mode trunk cdp enable interface GigabitEthernet4/2 no ip address flowcontrol receive on flowcontrol send off switchport switchport trunk encapsulation dot1q switchport trunk allowed vlan 1,209,1002-1005 switchport mode trunk cdp enable spanning-tree portfast trunk
-
新增VLAN 100介面和隧道終止的介面(在本例中為FastEthernet2/48,如下所示)。
interface Vlan100 ip address 10.66.79.180 255.255.255.224 interface FastEthernet2/48 no ip address crypto connect vlan 100
-
建立旁路NAT。將這些條目新增到no nat語句中,以免除在這些網路之間的命名:
access-list inside_nat0_outbound permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255 global (outside) 1 interface nat (inside) 0 access-list inside_nat0_outbound nat (inside) 1 192.168.5.0 255.255.255.0
-
建立密碼編譯組態和定義要加密的流量的ACL。
-
建立一個ACL(在本例中為ACL 100),定義從內部網路192.168.5.0/24到遠端網路192.168.6.0/24的流量,如下所示:
access-list 100 permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255
-
定義您的ISAKMP策略建議,如下所示:
crypto isakmp policy 1 hash md5 authentication pre-share group 2
-
發出以下命令(在本例中)以使用和定義預共用金鑰:
crypto isakmp key cisco address 10.66.79.73
-
定義您的IPSec建議,如下所示:
crypto ipsec transform-set cisco esp-des esp-md5-hmac
-
建立加密對映語句,如下所示:
crypto map cisco 10 ipsec-isakmp set peer 10.66.79.73 set transform-set cisco match address 100
-
-
將密碼編譯對應套用到VLAN 100介面,如下所示:
interface vlan100 crypto map cisco
使用以下配置:
| Catalyst 6500 |
|---|
!--- Define the Phase 1 policy. crypto isakmp policy 1 hash md5 authentication pre-share group 2 crypto isakmp key cisco address 10.66.79.73 ! ! !--- Define the encryption policy for this setup. crypto ipsec transform-set cisco esp-des esp-md5-hmac ! !--- Define a static crypto map entry for the peer !--- with mode ipsec-isakmp. !--- This indicates that IKE is used to establish the !--- IPSec SAs to protect the traffic !--- specified by this crypto map entry. crypto map cisco 10 ipsec-isakmp set peer 10.66.79.73 set transform-set cisco match address 100 ! ! no spanning-tree vlan 100 ! ! ! interface FastEthernet2/1 ip address 192.168.5.1 255.255.255.0 ! !--- This is the secure port that is configured in routed port mode. !--- This routed port mode does not have a Layer 3 IP address !--- configured. This is normal for the BITW process. !--- The IP address is moved from this interface to the VLAN 100 to !--- accomplish BITW. This brings the VPN service module into !--- the packet path. This is the Layer 2 port VLAN on which the !--- outside port of the VPN service module also belongs. ! interface FastEthernet2/48 no ip address crypto connect vlan 100 ! interface GigabitEthernet4/1 no ip address flowcontrol receive on flowcontrol send off switchport switchport trunk encapsulation dot1q !--- VLAN 100 is defined as the IVLAN. switchport trunk allowed vlan 1,100,1002-1005 switchport mode trunk cdp enable ! interface GigabitEthernet4/2 no ip address flowcontrol receive on flowcontrol send off switchport switchport trunk encapsulation dot1q !--- The PVLAN configuration is handled transparently by the !--- VPN service module without user configuration !--- or involvement. It also is not shown in the configuration. !--- Note: For every IVLAN, a corresponding PVLAN exists. switchport trunk allowed vlan 1,209,1002-1005 switchport mode trunk cdp enable spanning-tree portfast trunk ! interface Vlan1 no ip address shutdown ! !--- This is the IVLAN that is configured to intercept the traffic !--- destined to the secure port on which the inside port of the !--- VPN service module is the only port present. interface Vlan100 ip address 10.66.79.180 255.255.255.224 crypto map cisco !--- This is the secure port that is a virtual Layer 3 interface. !--- This interface purposely does not have a Layer 3 IP address !--- configured. This is normal for the BITW process. !--- The IP address is moved from this interface to the VLAN 100 to !--- accomplish BITW. This brings the VPN service module into !--- the packet path. ! ip classless global (outside) 1 interface !--- NAT 0 prevents NAT for networks specified in the ACL inside_nat0_outbound. nat (inside) 0 access-list inside_nat0_outbound nat (inside) 1 192.168.6.0 255.255.255.0 !--- Configure the routing so that the device !--- is directed to reach its destination network. ip route 0.0.0.0 0.0.0.0 10.66.79.161 ! !--- This access list (inside_nat0_outbound) is used with the nat zero command. !--- This prevents traffic which matches the access list from undergoing !--- network address translation (NAT). The traffic specified by this ACL is !--- traffic that is to be encrypted and !--- sent across the VPN tunnel. This ACL is intentionally !--- the same as (100). !--- Two separate access lists should always be used in this configuration. access-list inside_nat0_outbound permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255 !--- This is the crypto ACL. access-list 100 permit ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255 |
| PIX防火牆 |
|---|
SV2-8(config)# show run : Saved : PIX Version 6.3(3) interface ethernet0 auto interface ethernet1 auto interface ethernet2 auto shutdown interface ethernet3 auto shutdown interface ethernet4 auto shutdown interface ethernet5 auto shutdown interface ethernet6 auto shutdown nameif ethernet0 outside security0 nameif ethernet1 inside security100 nameif ethernet2 intf2 security10 nameif ethernet3 intf3 security15 nameif ethernet4 intf4 security20 nameif ethernet5 intf5 security25 nameif ethernet6 intf6 security30 enable password 8Ry2YjIyt7RRXU24 encrypted passwd 2KFQnbNIdI.2KYOU encrypted hostname SV2-8 domain-name cisco.com fixup protocol dns maximum-length 512 fixup protocol ftp 21 fixup protocol h323 h225 1720 fixup protocol h323 ras 1718-1719 fixup protocol http 80 fixup protocol ils 389 fixup protocol rsh 514 fixup protocol rtsp 554 fixup protocol sip 5060 fixup protocol sip udp 5060 fixup protocol skinny 2000 fixup protocol smtp 25 fixup protocol sqlnet 1521 fixup protocol tftp 69 names !--- This is the traffic to the router. access-list 100 permit ip 192.168.6.0 255.255.255.0 192.168.5.0 255.255.255.0 access-list nonat permit ip 192.168.6.0 255.255.255.0 192.168.5.0 255.255.255.0 pager lines 24 mtu outside 1500 mtu inside 1500 mtu intf2 1500 mtu intf3 1500 mtu intf4 1500 mtu intf5 1500 mtu intf6 1500 ip address outside 10.66.79.73 255.255.255.224 ip address inside 192.168.6.1 255.255.255.0 ip address intf2 127.0.0.1 255.255.255.255 no ip address intf3 no ip address intf4 no ip address intf5 no ip address intf6 ip audit info action alarm ip audit attack action alarm no failover failover timeout 0:00:00 failover poll 15 no failover ip address outside no failover ip address inside no failover ip address intf2 no failover ip address intf3 no failover ip address intf4 no failover ip address intf5 no failover ip address intf6 pdm history enable arp timeout 14400 global (outside) 1 interface nat (inside) 0 access-list nonat nat (inside) 1 192.168.6.0 255.255.255.0 0 0 route outside 0.0.0.0 0.0.0.0 10.66.79.65 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h225 1:00:00 timeout h323 0:05:00 mgcp 0:05:00 sip 0:30:00 sip_media 0:02:00 timeout uauth 0:05:00 absolute aaa-server TACACS+ protocol tacacs+ aaa-server RADIUS protocol radius aaa-server LOCAL protocol local no snmp-server location no snmp-server contact snmp-server community public no snmp-server enable traps floodguard enable !--- These are IPSec policies. sysopt connection permit-ipsec crypto ipsec transform-set cisco esp-des esp-md5-hmac crypto map cisco 10 ipsec-isakmp crypto map cisco 10 match address 100 crypto map cisco 10 set peer 10.66.79.180 crypto map cisco 10 set transform-set cisco crypto map cisco interface outside !--- These are IKE policies. isakmp enable outside isakmp key ******** address 10.66.79.180 netmask 255.255.255.255 isakmp policy 1 authentication pre-share isakmp policy 1 encryption des isakmp policy 1 hash md5 isakmp policy 1 group 2 isakmp policy 1 lifetime 86400 telnet timeout 5 ssh timeout 5 console timeout 0 terminal width 80 Cryptochecksum:244c86c9beab00bda8f790502ca74db9 : end |
驗證
本節提供的資訊用於確認您的組態是否正常運作。
輸出直譯器工具(僅供已註冊客戶使用)(OIT)支援某些show命令。使用OIT檢視show命令輸出的分析。
-
show crypto ipsec sa — 顯示當前IPSec SA使用的設定。
-
show crypto isakmp sa — 顯示對等體上的所有當前IKE SA。
-
show crypto vlan — 顯示與加密配置關聯的VLAN。
-
show crypto eli — 顯示VPN服務模組統計資訊。
有關驗證和排除IPSec故障的其他資訊,請參閱IP安全故障排除 — 瞭解和使用debug命令。
疑難排解
本節提供的資訊用於對組態進行疑難排解。
指令疑難排解
注意:發出debug指令之前,請參閱有關Debug指令的重要資訊。
-
debug crypto ipsec — 顯示第2階段的IPSec協商。
-
debug crypto isakmp — 顯示第1階段的ISAKMP協商。
-
debug crypto engine — 顯示加密的流量。
-
clear crypto isakmp — 清除與第1階段相關的SA。
-
clear crypto sa — 清除與第2階段相關的SA。
有關驗證和排除IPSec故障的其他資訊,請參閱IP安全故障排除 — 瞭解和使用debug命令。
 意見
意見