透過OSPF、NAT和Cisco IOS防火牆配置使用GRE Over IPsec的動態多點VPN
簡介
本文提供使用通用路由封裝(GRE) over IPsec搭配開放最短路徑優先(OSPF)、網路位址翻譯(NAT)和Cisco IOS®防火牆的動態多點VPN (DMVPN)組態範例。
必要條件
需求
在建立多點GRE (mGRE)和IPSec隧道之前,必須先使用crypto isakmp policy命令定義Internet金鑰交換(IKE)策略。
注意:使用命令查詢工具(僅限註冊客戶)可獲取有關此部分使用的命令的更多資訊。
採用元件
本文中的資訊係根據以下軟體和硬體版本:
-
中心路由器上的Cisco IOS®軟體版本12.2(15)T1和分支路由器上的Cisco IOS軟體版本12.3(1.6)
-
Cisco 3620作為中心路由器、兩台Cisco 1720路由器和一台Cisco 3620路由器作為分支路由器
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路正在作用,請確保您已瞭解任何指令可能造成的影響。
慣例
設定
本節提供用於設定本文件中所述功能的資訊。
注意:使用命令查詢工具(僅限註冊客戶)可獲取有關此部分使用的命令的更多資訊。
網路圖表
本檔案會使用此網路設定。
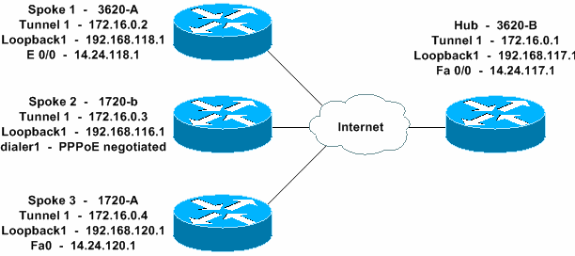
組態
本檔案會使用這些組態。
| 集線器- 3620-B |
|---|
W2N-6.16-3620-B#write terminal Building configuration... Current configuration : 2613 bytes ! version 12.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname W2N-6.16-3620-B ! logging queue-limit 100 ! memory-size iomem 10 ip subnet-zero ! ! ip cef no ip domain lookup ! !--- This is the Cisco IOS Firewall configuration and what to inspect. !--- This is applied outbound on the external interface. ip inspect name in2out rcmd ip inspect name in2out ftp ip inspect name in2out tftp ip inspect name in2out tcp timeout 43200 ip inspect name in2out http ip inspect name in2out udp ip audit po max-events 100 ! ! ! !--- Create an Internet Security Association and Key Management !--- Protocol (ISAKMP) policy for Phase 1 negotiations. crypto isakmp policy 5 authentication pre-share group 2 !--- Add dynamic pre-shared key. crypto isakmp key dmvpnkey address 0.0.0.0 0.0.0.0 crypto isakmp nat keepalive 20 ! ! !--- Create the Phase 2 policy for actual data encryption. crypto ipsec transform-set dmvpnset esp-3des esp-sha-hmac ! !--- Create an IPsec profile to be applied dynamically !--- to the GRE over IPsec tunnels. crypto ipsec profile dmvpnprof set transform-set dmvpnset ! ! ! ! ! ! ! ! ! ! ! no voice hpi capture buffer no voice hpi capture destination ! ! mta receive maximum-recipients 0 ! ! ! !--- This is the inbound interface. interface Loopback1 ip address 192.168.117.1 255.255.255.0 ip nat inside ! !--- Create a GRE tunnel template to be applied !--- to all the dynamically created GRE tunnels. interface Tunnel1 description MULTI-POINT GRE TUNNEL for BRANCHES bandwidth 1000 ip address 172.16.0.1 255.255.255.0 no ip redirects ip mtu 1416 ip nhrp authentication dmvpn ip nhrp map multicast dynamic ip nhrp network-id 99 ip nhrp holdtime 300 no ip route-cache ip ospf network broadcast no ip mroute-cache delay 1000 tunnel source FastEthernet0/0 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile dmvpnprof ! !--- This is the outbound interface. interface FastEthernet0/0 ip address 14.24.117.1 255.255.0.0 ip nat outside ip access-group 100 in ip inspect in2out out no ip mroute-cache duplex auto speed auto ! interface Serial0/0 no ip address shutdown clockrate 2000000 no fair-queue ! interface FastEthernet0/1 no ip address no ip mroute-cache duplex auto speed auto ! !--- Enable a routing protocol to send/receive dynamic !--- updates about the private networks. router ospf 1 log-adjacency-changes network 172.16.0.0 0.0.0.255 area 0 network 192.168.117.0 0.0.0.255 area 0 ! !--- Except the private network traffic from the NAT process. ip nat inside source route-map nonat interface FastEthernet0/0 overload ip http server no ip http secure-server ip classless ip route 0.0.0.0 0.0.0.0 14.24.1.1 ip route 2.0.0.0 255.0.0.0 14.24.121.1 ! ! ! !--- Allow ISAKMP, ESP, and GRE traffic inbound. !--- Cisco IOS Firewall opens other inbound access as needed. access-list 100 permit udp any host 14.24.117.1 eq 500 access-list 100 premit esp any host 14.24.117.1 access-list 100 permit gre any host 14.24.117.1 access-list 100 deny ip any any !--- Except the private network traffic from the NAT process. access-list 110 deny ip 192.168.117.0 0.0.0.255 192.168.118.0 0.0.0.255 access-list 110 deny ip 192.168.117.0 0.0.0.255 192.168.116.0 0.0.0.255 access-list 110 deny ip 192.168.117.0 0.0.0.255 192.168.120.0 0.0.0.255 access-list 110 permit ip 192.168.117.0 0.0.0.255 any ! !--- Except the private network traffic from the NAT process. route-map nonat permit 10 match ip address 110 ! call rsvp-sync ! ! mgcp profile default ! dial-peer cor custom ! ! ! ! ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 login ! ! end W2N-6.16-3620-B# |
| 分支1 ― 3620-A |
|---|
W2N-6.16-3620-A#write terminal Building configuration... Current configuration : 2678 bytes ! version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname W2N-6.16-3620-A ! boot system flash slot0:c3620-ik9o3s7-mz.122-15.T1.bin logging queue-limit 100 ! memory-size iomem 15 ip subnet-zero ! ! ip cef no ip domain lookup ! !--- This is the Cisco IOS Firewall configuration and what to inspect. !--- This is applied outbound on the external interface. ip inspect name in2out rcmd ip inspect name in2out tftp ip inspect name in2out udp ip inspect name in2out tcp timeout 43200 ip inspect name in2out realaudio ip inspect name in2out vdolive ip inspect name in2out netshow ip audit po max-events 100 ! ! ! !--- Create an ISAKMP policy for !--- Phase 1 negotiations. crypto isakmp policy 5 authentication pre-share group 2 !--- Add dynamic pre-shared key. crypto isakmp key dmvpnkey address 0.0.0.0 0.0.0.0 ! ! !--- Create the Phase 2 policy for actual data encryption. crypto ipsec transform-set dmvpnset esp-3des esp-sha-hmac ! !--- Create an IPsec profile to be applied dynamically !--- to the GRE over IPsec tunnels. crypto ipsec profile dmvpnprof set transform-set dmvpnset ! ! ! ! ! ! ! ! ! ! ! no voice hpi capture buffer no voice hpi capture destination ! ! mta receive maximum-recipients 0 ! ! ! !--- This is the inbound interface. interface Loopback1 ip address 192.168.118.1 255.255.255.0 ip nat inside ! !--- Create a GRE tunnel template to be applied to !--- all the dynamically created GRE tunnels. interface Tunnel1 description HOST DYNAMIC TUNNEL bandwidth 1000 ip address 172.16.0.2 255.255.255.0 no ip redirects ip mtu 1416 ip nhrp authentication dmvpn ip nhrp map multicast dynamic ip nhrp map 172.16.0.1 14.24.117.1 ip nhrp map multicast 14.24.117.1 ip nhrp network-id 99 ip nhrp holdtime 300 ip nhrp nhs 172.16.0.1 no ip route-cache ip ospf network broadcast no ip mroute-cache delay 1000 tunnel source Ethernet0/0 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile dmvpnprof ! !--- This is the outbound interface. interface Ethernet0/0 ip address 14.24.118.1 255.255.0.0 ip nat outside ip access-group 100 in ip inspect in2out out no ip mroute-cache half-duplex ! interface Ethernet0/1 no ip address half-duplex ! interface Ethernet0/2 no ip address shutdown half-duplex ! interface Ethernet0/3 no ip address shutdown half-duplex ! !--- Enable a routing protocol to send/receive dynamic !--- updates about the private networks. router ospf 1 log-adjacency-changes redistribute connected network 172.16.0.0 0.0.0.255 area 0 network 192.168.118.0 0.0.0.255 area 0 ! !--- Except the private network traffic from the NAT process. ip nat inside source route-map nonat interface Ethernet0/0 overload ip http server no ip http secure-server ip classless ip route 0.0.0.0 0.0.0.0 14.24.1.1 ip route 2.0.0.0 255.0.0.0 14.24.121.1 ! ! ! !--- Allow ISAKMP, ESP, and GRE traffic inbound. !--- Cisco IOS Firewall opens inbound access as needed. access-list 100 permit udp any host 14.24.118.1 eq 500 access-list 100 premit esp any host 14.24.118.1 access-list 100 permit gre any host 14.24.118.1 access-list 100 deny ip any any !--- Except the private network traffic from the NAT process. access-list 110 deny ip 192.168.118.0 0.0.0.255 192.168.117.0 0.0.0.255 access-list 110 deny ip 192.168.118.0 0.0.0.255 192.168.116.0 0.0.0.255 access-list 110 deny ip 192.168.118.0 0.0.0.255 192.168.120.0 0.0.0.255 access-list 110 permit ip 192.168.118.0 0.0.0.255 any ! !--- Except the private network traffic from the NAT process. route-map nonat permit 10 match ip address 110 ! call rsvp-sync ! ! mgcp profile default ! dial-peer cor custom ! ! ! ! ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 login ! ! end W2N-6.16-3620-A# |
| 分支2 ― 1720-b |
|---|
1720-b#write terminal Building configuration... Current configuration : 2623 bytes ! version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname 1720-b ! logging queue-limit 100 enable password cisco ! username 7206-B password 0 cisco ip subnet-zero ! ! no ip domain lookup ! ip cef !--- This is the Cisco IOS Firewall configuration and what to inspect. !--- This is applied outbound on the external interface. ip inspect name in2out rcmd ip inspect name in2out tftp ip inspect name in2out udp ip inspect name in2out tcp timeout 43200 ip inspect name in2out realaudio ip inspect name in2out vdolive ip inspect name in2out netshow ip audit po max-events 100 vpdn-group 1 request-dialin protocol pppoe ! ! ! ! ! !--- Create an ISAKMP policy for !--- Phase 1 negotiations. crypto isakmp policy 5 authentication pre-share group 2 !--- Add dynamic pre-shared key. crypto isakmp key dmvpnkey address 0.0.0.0 0.0.0.0 ! ! !--- Create the Phase 2 policy for actual data encryption. crypto ipsec transform-set dmvpnset esp-3des esp-sha-hmac ! !--- Create an IPsec profile to be applied dynamically !--- to the GRE over IPsec tunnels. crypto ipsec profile dmvpnprof set transform-set dmvpnset ! ! ! ! ! !--- This is the inbound interface. interface Loopback1 ip address 192.168.116.1 255.255.255.0 ip nat inside ! !--- Create a GRE tunnel template to be applied to !--- all the dynamically created GRE tunnels. interface Tunnel1 description HOST DYNAMIC TUNNEL bandwidth 1000 ip address 172.16.0.3 255.255.255.0 no ip redirects ip mtu 1416 ip nhrp authentication dmvpn ip nhrp map multicast dynamic ip nhrp map 172.16.0.1 14.24.117.1 ip nhrp map multicast 14.24.117.1 ip nhrp network-id 99 ip nhrp holdtime 300 ip nhrp nhs 172.16.0.1 no ip route-cache ip ospf network broadcast no ip mroute-cache delay 1000 tunnel source Dialer1 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile dmvpnprof ! interface Ethernet0 no ip address half-duplex ! interface FastEthernet0 no ip address no ip mroute-cache speed auto pppoe enable pppoe-client dial-pool-number 1 ! !--- This is the outbound interface. interface Dialer1 ip address 2.2.2.10 255.255.255.0 ip inspect in2out out ip access-group 100 in encapsulation ppp dialer pool 1 dialer-group 1 ppp authentication pap chap callin ! !--- Enable a routing protocol to send/receive dynamic !--- updates about the private networks. router ospf 1 log-adjacency-changes redistribute connected network 172.16.0.0 0.0.0.255 area 0 network 192.168.116.0 0.0.0.255 area 0 ! !--- Except the private network traffic from the NAT process. ip nat inside source route-map nonat interface Dialer1 overload ip classless ip route 0.0.0.0 0.0.0.0 14.24.1.1 ip route 0.0.0.0 0.0.0.0 Dialer1 no ip http server no ip http secure-server ! ! ! !--- Allow ISAKMP, ESP, and GRE traffic inbound. !--- Cisco IOS Firewall opens inbound access as needed. access-list 100 permit udp any host 14.24.116.1 eq 500 access-list 100 premit esp any host 14.24.116.1 access-list 100 permit gre any host 14.24.116.1 access-list 100 deny ip any any !--- Except the private network traffic from the NAT process. access-list 110 deny ip 192.168.116.0 0.0.0.255 192.168.117.0 0.0.0.255 access-list 110 deny ip 192.168.116.0 0.0.0.255 192.168.118.0 0.0.0.255 access-list 110 deny ip 192.168.116.0 0.0.0.255 192.168.120.0 0.0.0.255 access-list 110 permit ip 192.168.116.0 0.0.0.255 any dialer-list 1 protocol ip permit ! !--- Except the private network traffic from the NAT process. route-map nonat permit 10 match ip address 110 ! ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 login ! no scheduler allocate end 1720-b# |
| 分支3 ― 1720-A |
|---|
W2N-6.16-1720-A#write terminal Building configuration... Current configuration : 2303 bytes ! version 12.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname W2N-6.16-1720-A ! logging queue-limit 100 ! memory-size iomem 25 ip subnet-zero ! ! no ip domain lookup ! ip cef !--- This is the Cisco IOS Firewall configuration and what to inspect. !--- This is applied outbound on the external interface. ip inspect name in2out rcmd ip inspect name in2out tftp ip inspect name in2out udp ip inspect name in2out tcp timeout 43200 ip inspect name in2out realaudio ip inspect name in2out vdolive ip inspect name in2out netshow ip audit notify log ip audit po max-events 100 ! ! ! ! !--- Create an ISAKMP policy for !--- Phase 1 negotiations. crypto isakmp policy 5 authentication pre-share group 2 !--- Add dynamic pre-shared key. crypto isakmp key dmvpnkey address 0.0.0.0 0.0.0.0 ! ! !--- Create the Phase 2 policy for actual data encryption. crypto ipsec transform-set dmvpnset esp-3des esp-sha-hmac ! !--- Create an IPsec profile to be applied dynamically !--- to the GRE over IPsec tunnels. crypto ipsec profile dmvpnprof set transform-set dmvpnset ! ! ! ! ! !--- This is the inbound interface. interface Loopback1 ip address 192.168.120.1 255.255.255.0 ip nat inside ! !--- Create a GRE tunnel template to be applied to !--- all the dynamically created GRE tunnels. interface Tunnel1 description HOST DYNAMIC TUNNEL bandwidth 1000 ip address 172.16.0.4 255.255.255.0 no ip redirects ip mtu 1416 ip nhrp authentication dmvpn ip nhrp map multicast dynamic ip nhrp map 172.16.0.1 14.24.117.1 ip nhrp map multicast 14.24.117.1 ip nhrp network-id 99 ip nhrp holdtime 300 ip nhrp nhs 172.16.0.1 ip ospf network broadcast no ip mroute-cache delay 1000 tunnel source FastEthernet0 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile dmvpnprof ! interface Ethernet0 no ip address no ip mroute-cache half-duplex ! !--- This is the outbound interface. interface FastEthernet0 ip address 14.24.120.1 255.255.0.0 ip nat outside ip inspect in2out out ip access-group 100 in no ip mroute-cache speed auto ! !--- Enable a routing protocol to send/receive dynamic !--- updates about the private networks. router ospf 1 log-adjacency-changes redistribute connected network 172.16.0.0 0.0.0.255 area 0 network 192.168.120.0 0.0.0.255 area 0 ! !--- Except the private network traffic from the NAT process. ip nat inside source route-map nonat interface FastEthernet0 overload ip classless ip route 0.0.0.0 0.0.0.0 14.24.1.1 ip route 2.0.0.0 255.0.0.0 14.24.121.1 no ip http server no ip http secure-server ! ! ! !--- Allow ISAKMP, ESP, and GRE traffic inbound. !--- Cisco IOS Firewall opens inbound access as needed. access-list 100 permit udp any host 14.24.116.1 eq 500 access-list 100 premit esp any host 14.24.116.1 access-list 100 permit gre any host 14.24.116.1 access-list 100 deny ip any any access-list 110 permit ip 192.168.120.0 0.0.0.255 any !--- Except the private network traffic from the NAT process. access-list 110 deny ip 192.168.120.0 0.0.0.255 192.168.116.0 0.0.0.255 access-list 110 deny ip 192.168.120.0 0.0.0.255 192.168.117.0 0.0.0.255 access-list 110 deny ip 192.168.120.0 0.0.0.255 192.168.118.0 0.0.0.255 access-list 110 permit ip 192.168.120.0 0.0.0.255 any ! !--- Except the private network traffic from the NAT process. route-map nonat permit 10 match ip address 110 ! ! line con 0 exec-timeout 0 0 line aux 0 line vty 0 4 login ! end W2N-6.16-1720-A# |
驗證
使用本節內容,確認您的組態是否正常運作。
輸出直譯器工具(僅供註冊客戶使用) (OIT)支援某些show指令。使用OIT檢視對show命令輸出的分析。
-
show crypto isakmp sa -顯示ISAKMP安全關聯(SA)的狀態。
-
show crypto engine connections active -按SA顯示總加密/解密。
-
show crypto ipsec sa -顯示有關活動隧道的統計資料。
-
show ip route -顯示路由表。
-
show ip ospf neighbor -按介面顯示OSPF鄰居資訊。
-
show ip nhrp -顯示IP下一跳解析協定(NHRP)快取,可選擇限制為特定介面的動態或靜態快取條目。
疑難排解
本節提供的資訊可用於對組態進行疑難排解。
疑難排解指令
注意:發出debug命令之前,請參閱有關Debug命令的重要資訊。
-
debug crypto ipsec -顯示IPSec事件。
-
debug crypto isakmp -顯示有關IKE事件的消息。
-
debug crypto engine -顯示來自加密引擎的資訊。
有關IPsec故障排除的其他資訊,請參閱IP安全故障排除-瞭解和使用debug命令。
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
28-May-2003 |
初始版本 |
 意見
意見