採用Windows 7或Android VPN客戶端和證書身份驗證配置的ASA IKEv2 RA VPN
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
目錄
簡介
本文檔介紹如何配置Cisco Adaptive Security Appliance(ASA)9.7.1版及更高版本,以便允許Windows 7和Android本地(虛擬專用網路)VPN客戶端使用網際網路金鑰交換協定(IKEv2)和證書作為身份驗證方法建立(遠端訪問)RA VPN連線。
作者:David Rivera和Cesar Lopez Zamarripa,思科TAC工程師。
必要條件
需求
思科建議您瞭解以下主題:
- 證書頒發機構(CA)
- 公開金鑰基礎架構 (PKI)
- ASA上帶IKEv2的RA VPN
- Windows 7內建VPN客戶端
- Android原生VPN客戶端
採用元件
本檔案中的資訊是根據以下軟體版本:
- CISCO1921/K9 - 15.5(3)M4a(作為IOS CA伺服器)
- ASA5506X - 9.7(1)作為VPN頭端
- Windows 7作為客戶端電腦
- Galaxy J5 - Android 6.0.1作為移動客戶端
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
設定
概觀
以下是配置Windows 7和Android本地VPN客戶端以連線到ASA頭端的步驟:
配置證書頒發機構
CA允許將所需的擴充金鑰使用(EKU)嵌入憑證中。對於ASA頭端,需要證書伺服器身份驗證EKU,而客戶端證書需要客戶端身份驗證EKU。
可以使用各種CA伺服器,例如:
- Cisco IOS CA伺服器
- OpenSSL CA伺服器
- Microsoft CA伺服器
- 3rd 參與方CA
此配置示例使用IOS CA伺服器。
本節概述使版本15.5(3)M4a的CISCO1921/K9作為CA伺服器工作的基本配置。
步驟1.確保裝置和版本支援eku命令。
IOS-CA# show run | section crypto pki crypto pki server <CA_Server> issuer-name <cn=calo_root,ou=TAC,o=cisco> grant auto eku server-auth client-auth
步驟2.在路由器上啟用HTTP伺服器。
IOS-CA(config)#ip http server
步驟3.生成可匯出的RSA金鑰對。
IOS-CA(config)# crypto key generate rsa modulus 2048 label <HeadEnd> exportable The name for the keys will be: HeadEnd % The key modulus size is 2048 bits % Generating 2048 bit RSA keys, keys will be exportable... [OK] (elapsed time was 5 seconds)
步驟4.配置信任點。
IOS-CA(config)# crypto pki trustpoint <HeadEnd> IOS-CA(ca-trustpoint)#enrollment url http://10.201.180.230:80 IOS-CA(ca-trustpoint)#subject-name <cn=HeadEnd.david.com> IOS-CA(ca-trustpoint)#revocation-check none IOS-CA(ca-trustpoint)#rsakeypair <HeadEnd>
附註:enrollment命令的IP地址是路由器為可達介面配置的IP地址之一。
步驟5.驗證信任點(取得CA憑證)。
IOS-CA(config)#crypto pki authenticate <HeadEnd>
Certificate has the following attributes:
Fingerprint MD5: DA4502F4 CEFB4F08 AAA3179B 70019185
Fingerprint SHA1: A887F6DB 0656C7E2 857749F3 EA3D7176 8920F52F
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
步驟6.註冊信任點(獲取身份證書)。
IOS-CA(config)#crypto pki enroll <HeadEnd> % % Start certificate enrollment .. % Create a challenge password. You will need to verbally provide this password to the CA Administrator in order to revoke your certificate. For security reasons your password will not be saved in the configuration. Please make a note of it. Password: cisco123 Re-enter password: cisco123 % The subject name in the certificate will include: cn=HeadEnd.david.com % The subject name in the certificate will include: Connected_2_INET-B % Include the router serial number in the subject name? [yes/no]: no % Include an IP address in the subject name? [no]: no Request certificate from CA? [yes/no]: yes % Certificate request sent to Certificate Authority % The 'show crypto pki certificate verbose HeadEnd' command will show the fingerprint. *Jul 17 15:21:11.343: CRYPTO_PKI: Certificate Request Fingerprint MD5: 0017C310 9F6084E8 63053228 B449794F *Jul 17 15:21:11.343: CRYPTO_PKI: Certificate Request Fingerprint SHA1: CFE22C7A B2855C4D B4B2412B 57FC7106 1C5E7791 *Jul 17 15:21:15.675: %PKI-6-CERTRET: Certificate received from Certificate Authority
步驟7.驗證憑證。
IOS-CA#show crypto pki certificates verbose <HeadEnd>
Certificate
Status: Available
Version: 3
Certificate Serial Number (hex): 05
Certificate Usage: General Purpose
Issuer:
cn=calo_root
Subject:
Name: Connected_2_INET-B
hostname=Connected_2_INET-B
cn=HeadEnd.david.com
Validity Date:
start date: 16:56:14 UTC Jul 16 2017
end date: 16:56:14 UTC Jul 16 2018
Subject Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Signature Algorithm: SHA1 with RSA Encryption
Fingerprint MD5: 0017C310 9F6084E8 63053228 B449794F
Fingerprint SHA1: CFE22C7A B2855C4D B4B2412B 57FC7106 1C5E7791
X509v3 extensions:
X509v3 Key Usage: A0000000
Digital Signature
Key Encipherment
X509v3 Subject Key ID: E9B3A080 779A76E7 8BE44F38 C3E4DEDF 18E75009
X509v3 Authority Key ID: B5EEEEB9 31B9A06C CBD9893C 0E318810 5CA657E6
Authority Info Access:
Extended Key Usage:
Client Auth
Server Auth
Associated Trustpoints: HeadEnd
Key Label: HeadEnd
CA Certificate
Status: Available
Version: 3
Certificate Serial Number (hex): 01
Certificate Usage: Signature
Issuer:
cn=calo_root
Subject:
cn=calo_root
Validity Date:
start date: 13:24:35 UTC Jul 13 2017
end date: 13:24:35 UTC Jul 12 2020
Subject Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Signature Algorithm: MD5 with RSA Encryption
Fingerprint MD5: DA4502F4 CEFB4F08 AAA3179B 70019185
Fingerprint SHA1: A887F6DB 0656C7E2 857749F3 EA3D7176 8920F52F
X509v3 extensions:
X509v3 Key Usage: 86000000
Digital Signature
Key Cert Sign
CRL Signature
X509v3 Subject Key ID: B5EEEEB9 31B9A06C CBD9893C 0E318810 5CA657E6
X509v3 Basic Constraints:
CA: TRUE
X509v3 Authority Key ID: B5EEEEB9 31B9A06C CBD9893C 0E318810 5CA657E6
Authority Info Access:
Associated Trustpoints: test HeadEnd CA_Server
步驟8.將HeadEnd信任點匯出到PKCS12格式的終端以獲取身份證書。CA證書和私鑰新增到一個檔案中。
IOS-CA(config)#crypto pki export
pkcs12 terminal password
<cisco123>
Exported pkcs12 follows:
MIIL3wIBAzCCC5kGCSqGSIb3DQEHAaCCC4oEgguGMIILgjCCC34GCSqGSIb3DQEH
BqCCC28wggtrAgEAMIILZAYJKoZIhvcNAQcBMBsGCiqGSIb3DQEMAQMwDQQIocGz
Fa6tZyACAQGAggs4qNTJi7l/f0IvQr8n1c/SCeaSYRLBvcY9yPgJ2K2/Nmu9+KNB
3dAoYkCrGwDdfpobJE0XqBpIE1uBOtAeF7zdFJt/Pgpie4fcqpCVIbDXG8Ansmhj
v0j6W9Z/IJHe7JrENatbi4nhTnCDP79Z65QSkzrb9DenkCGjoQsWP9zLHTiCDNzV
ajMlWFuCFb0wSW/6L73BLTjS7rwtE74gYMU5NJwtOVsJM2LdwuQ+iOnpsnp6q9fu
niUFEutPe8imOCRApe0tpPqhDp74hKziKT8JEsQ8HMO/lX1y/LIXdLISnz1nkoN3
vxD4AMGRFYACPH8PiGcVSx+vD+wmNaHp1vAOrq4pS7ZQ37ko4mFudnftdOUzaPIz
EzTrOwlRE6il/gF8vb14EfeR09vumJBsajF12hrFGugIJTZnElp5go+oHEEAo4Y+
Yhoj/MIOyhZzo3/ujhjKqtsAJXybYF9YqVkTee9u4Xjkcsg5AmbaqeUUfd7Q8CC2
bi39S1maoWbTYiNcHFs/bWKWJsgZwPzfWtmPch/8MNvXn46AJAwIwRQjHruuFE9F
bhv7SRhYSRQZPf7j1PTmJuMkKA3AzjdbmmJuLidbX3yKbTt4PxPMusbv+ojc6Nam
RCsRf7+gnNZLWs3eU1n84rryZg5Pjw3MRTu2yXDvr799gvx7NIZH5yUZyVl1T70b
eC4KbflcmpM6mJ2UVnaoP2N5u892m41BWuk9rt5isl2f/Z/ZuSbkFaxzU0456zSg
VbYsR+51XfQEH5xu88E5EUPWZ86YdUSlbD8ky6WOn0M1O4K6rNDLkgwXcxw3CaZ8
zhao+dE3qoEYWaKPgCQzPqW0BW3y7WSIELug2uSEsXQjIQcF+42CX6RA3yCmy2T8
C+osKlSSao0nzjrlpTWnPiFss9KRFgJDZhV2ItisiALNw9PqruddcmYtw44LXvdc
+OfnyRvuLS6LE/AMmGk0GaVetAXPezD+5pVZW13UMT/ZdzUjLiXjV9GzF6V8i8qN
Ua0MbDEa8T5Le4dCigaA+t1QxQOPGb+w0ZAQzWN4gZpSEk3ejRixOt14SU5ivj/O
lGXNn8Fvebk42CHohjXG9fq/IfbsVWSkxn2OZ/fhXkZztv4ic1VgprgJURjCtcBw
9Qp/ONda+9aDHiSBrKeHC/urgX6rgWXv9+hpRKIRfj3b8WE+N1sivuQEjlWxbD7h
9fpwxXb+/i7HisjzSkOWUNw4lyulfYSiOv86FPWK0H9Vjbg0G0di1rvGZ8uJHQCC
77RLFXp4jrvCgeo4oWKQbphgPAng7rT794vMwq0rYOb4D3HlHCUvU3JJmScDJQy2
zQxbG2q8Htm44COOuJEUBzx1ImayH2XvDck6VmLTGn8XH5Vq7LOlCeUcVDM8aQfy
HJSPk/VmfQ0lXwPIaxxYlr+jOpcorFkH+OH04hz07grAsGyLRoFICTEvHAzVnF0X
2A1j/z/BFAPG86ssAtInRZVeYUS72NwPEtpKmlHZnl+2iWno5iwTZgtjv7oREZKE
RE6m7O8RiPSD2RjjamCmmmnH5dK5wxF7YlIeK/+ZVrfwLecEPRl+eVw0isM/JN/a
WmkZkCcVMx/ec1P8jp8LzCx17HgVNYbg9lsiffD4xo0G/k0QLUlpliAt7LA2BeGs
yl55wtYUcOBH0/Es39yWnm2Ea//IK6BLw98PvU90vkXWwiD3ajFmcHmssDeU/tZR
4KKNuNor7Le9ycXZFM9ofKZ6AIJ9A1AYvOyhGO88voq8MMGXEe/q+DIjaVE1htYu
k0ELmYAD/XOkEvp3SqOkLQZiCzZ20iMWUTWXlXfgrfLEH0utwHTyr3J2vQk5CD37
ZAfsF6zxEvtU2t41J0e9OjWJw9WtWnnS0gzLeXWtW3H0YAIw3QodKNzbaY4eLP4y
BEdsLmWbM4eza0m9BoZOmMUSkhvFrEz5Q5X5r9vCuAi1rYDqyIjhgdme56tVV0Vg
ZauhbNX59PQQzwOdIZJVVL5tgjf0h7XCm9OBsqd12lHurCCmHy7kM5pqf0MMlhH7
oM/DhXdTU+1sEabt/9c2qs1ihJLS1Zaw2q1AaS5h00+xL8Lxwh2/1/R7Q8FferhR
QZDpix+CmtakRu7uPOMa0zsyOko3P9mf74AWDrThAwMA6G238TC6XI1vrXhvEX1l
BVplQq0Wh/p7ZorSjD5l+z7TkXmJNp7iIxAqp0yobC6vOBwQP7/QAs88q9JNSAte
ErdCXoizvs8YmZMoEap948oplYFaIP+xCnCr8l3v7znwfZwTMQPoPvqEFqUmWYgt
xkJ0qaE645ihTnLgk4eglsBLslwPR1RJU+t6kGGAUmxqhPFxb3/1xNRPVzOGn12w
S9yw+XLC6kS4PmKoxkxax4nnCx7s3e7B5e0qmYtgRTJ0GuW7Uf+T3royTOuYm0d+
ik6bmxcnO0qdcHtt2HTbI+kYpken3YrFOh9Jnm9ZKT63gQSqQWL800ZVd4dAZceg
FciNKs9r26fyy+L3rGCh+U9TLf6mNuWu8RstjjIGPHEPKZ9gnMgMJmikP2ghgOAd
XVhs6ashXx33bZ9dIuhRx6uTNMrppsXyg6SxUyeGDYhpxsPt7uRwBswOpi6iDMZn
ISSzQjrkxoNwwOfn87O5fTCLhHlTZa8HS5HMK3KE7LiZv9pa1z6KTo4z+LCQSLDy
FoRJhSaEsCYJsLDS5nYBoR8hE/eMvQDX1f+RZBrJDcftxx7FQ+8RtvHSJRcJK9N/
Ph/pL62NBlSbvCfn1AbisKrbbgCVLOSj/doufPvpMT2UDL0TY8UnQiyWMH1MF3tZ
jJy6Si2glLwA9hu/c1NsREbA0gxMTjAREb5BjAUmlc3fuv2DWpwnkwyZNyHdm9B9
TPRoByGPvSZXa8MwY/8DUEwUQEsfDJi5jlAD4I6VFFUB72ZS7wn/mVR02fPkfOMp
3yhnGgX29OaDDiDlKw1Xwj1NybOhpZ6unDo5J3stMxlbv5TYL2Tl6egZS0SjsLmn
cj5zkyUU22/93E5vfKD1CMiXx9/e4j2rRh3QCIXqaCjC9acTJ8a/k9/bp8Nz5Cir
pnaCbuQsvna92nxVUqcmLlSbVIvGqlH9qm4DurhcLh59j20tX6K8AMJ90+azaYbX
AJV/MCElhJg6wcN8QnCHMhiuK9+zpsUK2FQgfbcgaaNe3xGaXuoOIGQmlbAGtEkp
kuauRzQ8/pwszaZuPh/5rE77z8zMut3+OE5CslB9npzNi0b0itaaRl13bBBml1xn
r6SBUw7AWapZwRx6pihvptLJaqU1IzaV5SWk0zTABR7BmR84L0+/8v/bedcPSioG
ecside21F6CcWO5ywABBxDYQXM1P9qkC/2bkPkEJ0jBI5P5L1+Yqb8hTlone/InR
B8ktEd8+QW8o60h0seONXumTqBfAuNBkprOA3ssXLeEGB0IpeC5oGW+VSziyS9id
zYq8WaehpAIf3pqwn8gsi0B/wd57T0KK91+v0Ei4z+yIdu8Kh9GTiqGvgNAeakgr
ECDiXoKAwltYAn7cLKNpZaojSs2Jt+60oBA5crT04Mtgpjb9Pd/DLqWQDJTyoRVv
cJRb68aOyZvVBU0yoLbox84QKLHIsA92pplS7VFrAWP65wrhs4XOf4YSFlM89Sn4
GD/yEsGVJzwGrxgCNnOZkLIKsFbIOjp2lMps5jVKoFfpPJCie3F2FB3ecS+xRpHo
5u2KOTmH0rFQ6Vu+JYCo/qWh0ERtL/8gczP7C9ehiaZfemw2bq9xrUo+6y3H9Q+Z
LADwMlAkI+kzbng3R+fj4AYBvf8GTJdpBs8s/t7mZXHiXCtH6qxTMRWJx5Xuxs9F
I8Ii8TA9MCEwCQYFKw4DAhoFAAQUjO/On/REYODupznP9SwYnFX92BYEFESx1MSa
ho3Cv1cZYM0TzZEzlsKdAgIEAA==
---End - This line not part of the pkcs12---
CRYPTO_PKI: Exported PKCS12 file successfully.
*Jul 17 15:46:49.706: %PKI-6-PKCS12EXPORT_SUCCESS: PKCS #12 Successfully Exported.
步驟9.在ASA上建立空信任點。
ASA(config)# crypto ca trustpoint <HeadEnd> DRIVERAP(config-ca-trustpoint)# exit
步驟10 。匯入PKCS12檔案。
ASA(config)#crypto ca import <HeadEnd> pkcs12 <cisco123> Enter the base 64 encoded pkcs12. End with the word "quit" on a line by itself: MIIL3wIBAzCCC5kGCSqGSIb3DQEHAaCCC4oEgguGMIILgjCCC34GCSqGSIb3DQEH BqCCC28wggtrAgEAMIILZAYJKoZIhvcNAQcBMBsGCiqGSIb3DQEMAQMwDQQIocGz Fa6tZyACAQGAggs4qNTJi7l/f0IvQr8n1c/SCeaSYRLBvcY9yPgJ2K2/Nmu9+KNB 3dAoYkCrGwDdfpobJE0XqBpIE1uBOtAeF7zdFJt/Pgpie4fcqpCVIbDXG8Ansmhj v0j6W9Z/IJHe7JrENatbi4nhTnCDP79Z65QSkzrb9DenkCGjoQsWP9zLHTiCDNzV ajMlWFuCFb0wSW/6L73BLTjS7rwtE74gYMU5NJwtOVsJM2LdwuQ+iOnpsnp6q9fu niUFEutPe8imOCRApe0tpPqhDp74hKziKT8JEsQ8HMO/lX1y/LIXdLISnz1nkoN3 vxD4AMGRFYACPH8PiGcVSx+vD+wmNaHp1vAOrq4pS7ZQ37ko4mFudnftdOUzaPIz EzTrOwlRE6il/gF8vb14EfeR09vumJBsajF12hrFGugIJTZnElp5go+oHEEAo4Y+ Yhoj/MIOyhZzo3/ujhjKqtsAJXybYF9YqVkTee9u4Xjkcsg5AmbaqeUUfd7Q8CC2 bi39S1maoWbTYiNcHFs/bWKWJsgZwPzfWtmPch/8MNvXn46AJAwIwRQjHruuFE9F bhv7SRhYSRQZPf7j1PTmJuMkKA3AzjdbmmJuLidbX3yKbTt4PxPMusbv+ojc6Nam RCsRf7+gnNZLWs3eU1n84rryZg5Pjw3MRTu2yXDvr799gvx7NIZH5yUZyVl1T70b eC4KbflcmpM6mJ2UVnaoP2N5u892m41BWuk9rt5isl2f/Z/ZuSbkFaxzU0456zSg VbYsR+51XfQEH5xu88E5EUPWZ86YdUSlbD8ky6WOn0M1O4K6rNDLkgwXcxw3CaZ8 zhao+dE3qoEYWaKPgCQzPqW0BW3y7WSIELug2uSEsXQjIQcF+42CX6RA3yCmy2T8 C+osKlSSao0nzjrlpTWnPiFss9KRFgJDZhV2ItisiALNw9PqruddcmYtw44LXvdc +OfnyRvuLS6LE/AMmGk0GaVetAXPezD+5pVZW13UMT/ZdzUjLiXjV9GzF6V8i8qN Ua0MbDEa8T5Le4dCigaA+t1QxQOPGb+w0ZAQzWN4gZpSEk3ejRixOt14SU5ivj/O lGXNn8Fvebk42CHohjXG9fq/IfbsVWSkxn2OZ/fhXkZztv4ic1VgprgJURjCtcBw 9Qp/ONda+9aDHiSBrKeHC/urgX6rgWXv9+hpRKIRfj3b8WE+N1sivuQEjlWxbD7h 9fpwxXb+/i7HisjzSkOWUNw4lyulfYSiOv86FPWK0H9Vjbg0G0di1rvGZ8uJHQCC 77RLFXp4jrvCgeo4oWKQbphgPAng7rT794vMwq0rYOb4D3HlHCUvU3JJmScDJQy2 zQxbG2q8Htm44COOuJEUBzx1ImayH2XvDck6VmLTGn8XH5Vq7LOlCeUcVDM8aQfy HJSPk/VmfQ0lXwPIaxxYlr+jOpcorFkH+OH04hz07grAsGyLRoFICTEvHAzVnF0X 2A1j/z/BFAPG86ssAtInRZVeYUS72NwPEtpKmlHZnl+2iWno5iwTZgtjv7oREZKE RE6m7O8RiPSD2RjjamCmmmnH5dK5wxF7YlIeK/+ZVrfwLecEPRl+eVw0isM/JN/a WmkZkCcVMx/ec1P8jp8LzCx17HgVNYbg9lsiffD4xo0G/k0QLUlpliAt7LA2BeGs yl55wtYUcOBH0/Es39yWnm2Ea//IK6BLw98PvU90vkXWwiD3ajFmcHmssDeU/tZR 4KKNuNor7Le9ycXZFM9ofKZ6AIJ9A1AYvOyhGO88voq8MMGXEe/q+DIjaVE1htYu k0ELmYAD/XOkEvp3SqOkLQZiCzZ20iMWUTWXlXfgrfLEH0utwHTyr3J2vQk5CD37 ZAfsF6zxEvtU2t41J0e9OjWJw9WtWnnS0gzLeXWtW3H0YAIw3QodKNzbaY4eLP4y BEdsLmWbM4eza0m9BoZOmMUSkhvFrEz5Q5X5r9vCuAi1rYDqyIjhgdme56tVV0Vg ZauhbNX59PQQzwOdIZJVVL5tgjf0h7XCm9OBsqd12lHurCCmHy7kM5pqf0MMlhH7 oM/DhXdTU+1sEabt/9c2qs1ihJLS1Zaw2q1AaS5h00+xL8Lxwh2/1/R7Q8FferhR QZDpix+CmtakRu7uPOMa0zsyOko3P9mf74AWDrThAwMA6G238TC6XI1vrXhvEX1l BVplQq0Wh/p7ZorSjD5l+z7TkXmJNp7iIxAqp0yobC6vOBwQP7/QAs88q9JNSAte ErdCXoizvs8YmZMoEap948oplYFaIP+xCnCr8l3v7znwfZwTMQPoPvqEFqUmWYgt xkJ0qaE645ihTnLgk4eglsBLslwPR1RJU+t6kGGAUmxqhPFxb3/1xNRPVzOGn12w S9yw+XLC6kS4PmKoxkxax4nnCx7s3e7B5e0qmYtgRTJ0GuW7Uf+T3royTOuYm0d+ ik6bmxcnO0qdcHtt2HTbI+kYpken3YrFOh9Jnm9ZKT63gQSqQWL800ZVd4dAZceg FciNKs9r26fyy+L3rGCh+U9TLf6mNuWu8RstjjIGPHEPKZ9gnMgMJmikP2ghgOAd XVhs6ashXx33bZ9dIuhRx6uTNMrppsXyg6SxUyeGDYhpxsPt7uRwBswOpi6iDMZn ISSzQjrkxoNwwOfn87O5fTCLhHlTZa8HS5HMK3KE7LiZv9pa1z6KTo4z+LCQSLDy FoRJhSaEsCYJsLDS5nYBoR8hE/eMvQDX1f+RZBrJDcftxx7FQ+8RtvHSJRcJK9N/ Ph/pL62NBlSbvCfn1AbisKrbbgCVLOSj/doufPvpMT2UDL0TY8UnQiyWMH1MF3tZ jJy6Si2glLwA9hu/c1NsREbA0gxMTjAREb5BjAUmlc3fuv2DWpwnkwyZNyHdm9B9 TPRoByGPvSZXa8MwY/8DUEwUQEsfDJi5jlAD4I6VFFUB72ZS7wn/mVR02fPkfOMp 3yhnGgX29OaDDiDlKw1Xwj1NybOhpZ6unDo5J3stMxlbv5TYL2Tl6egZS0SjsLmn cj5zkyUU22/93E5vfKD1CMiXx9/e4j2rRh3QCIXqaCjC9acTJ8a/k9/bp8Nz5Cir pnaCbuQsvna92nxVUqcmLlSbVIvGqlH9qm4DurhcLh59j20tX6K8AMJ90+azaYbX AJV/MCElhJg6wcN8QnCHMhiuK9+zpsUK2FQgfbcgaaNe3xGaXuoOIGQmlbAGtEkp kuauRzQ8/pwszaZuPh/5rE77z8zMut3+OE5CslB9npzNi0b0itaaRl13bBBml1xn r6SBUw7AWapZwRx6pihvptLJaqU1IzaV5SWk0zTABR7BmR84L0+/8v/bedcPSioG ecside21F6CcWO5ywABBxDYQXM1P9qkC/2bkPkEJ0jBI5P5L1+Yqb8hTlone/InR B8ktEd8+QW8o60h0seONXumTqBfAuNBkprOA3ssXLeEGB0IpeC5oGW+VSziyS9id zYq8WaehpAIf3pqwn8gsi0B/wd57T0KK91+v0Ei4z+yIdu8Kh9GTiqGvgNAeakgr ECDiXoKAwltYAn7cLKNpZaojSs2Jt+60oBA5crT04Mtgpjb9Pd/DLqWQDJTyoRVv cJRb68aOyZvVBU0yoLbox84QKLHIsA92pplS7VFrAWP65wrhs4XOf4YSFlM89Sn4 GD/yEsGVJzwGrxgCNnOZkLIKsFbIOjp2lMps5jVKoFfpPJCie3F2FB3ecS+xRpHo 5u2KOTmH0rFQ6Vu+JYCo/qWh0ERtL/8gczP7C9ehiaZfemw2bq9xrUo+6y3H9Q+Z LADwMlAkI+kzbng3R+fj4AYBvf8GTJdpBs8s/t7mZXHiXCtH6qxTMRWJx5Xuxs9F I8Ii8TA9MCEwCQYFKw4DAhoFAAQUjO/On/REYODupznP9SwYnFX92BYEFESx1MSa ho3Cv1cZYM0TzZEzlsKdAgIEAA== quit INFO: Import PKCS12 operation completed successfully
步驟11.驗證憑證資訊。
ASA(config)#show crypto ca certificates <HeadEnd>
CA Certificate
Status: Available
Certificate Serial Number: 01
Certificate Usage: Signature
Public Key Type: RSA (1024 bits)
Signature Algorithm: MD5 with RSA Encryption
Issuer Name:
cn=calo_root
Subject Name:
cn=calo_root
Validity Date:
start date: 13:24:35 UTC Jul 13 2017
end date: 13:24:35 UTC Jul 12 2020
Storage: config
Associated Trustpoints: test HeadEnd
Certificate
Status: Available
Certificate Serial Number: 05
Certificate Usage: General Purpose
Public Key Type: RSA (2048 bits)
Signature Algorithm: SHA1 with RSA Encryption
Issuer Name:
cn=calo_root
Subject Name:
hostname=Connected_2_INET-B
cn=HeadEnd.david.com
Validity Date:
start date: 16:56:14 UTC Jul 16 2017
end date: 16:56:14 UTC Jul 16 2018
Storage: config
Associated Trustpoints: HeadEnd
生成客戶端證書
步驟1.生成可匯出的RSA金鑰對。
IOS-CA(config)# crypto key generate rsa modulus 2048 label <Win7_PC> exportable The name for the keys will be: Win7_PC % The key modulus size is 2048 bits % Generating 2048 bit RSA keys, keys will be exportable... [OK] (elapsed time was 5 seconds
步驟2.配置信任點。
IOS-CA(config)# crypto pki trustpoint <Win7_PC> IOS-CA(ca-trustpoint)#enrollment url http://10.201.180.230:80 IOS-CA(ca-trustpoint)#subject-name <cn=Win7_PC.david.com> IOS-CA(ca-trustpoint)#revocation-check none IOS-CA(ca-trustpoint)#rsakeypair <Win7_PC>
步驟3.對配置的信任點進行身份驗證(獲取CA證書)。
IOS-CA(config)#crypto pki authenticate <Win7_PC>
Certificate has the following attributes:
Fingerprint MD5: DA4502F4 CEFB4F08 AAA3179B 70019185
Fingerprint SHA1: A887F6DB 0656C7E2 857749F3 EA3D7176 8920F52F
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
步驟4.註冊經過身份驗證的信任點(獲取身份證書)。
IOS-CA(config)#crypto pki enroll <Win7_PC> % % Start certificate enrollment .. % Create a challenge password. You will need to verbally provide this password to the CA Administrator in order to revoke your certificate. For security reasons your password will not be saved in the configuration. Please make a note of it. Password: cisco123 Re-enter password: cisco123 % The subject name in the certificate will include: cn=Win7_PC.david.com % The subject name in the certificate will include: Connected_2_INET-B % Include the router serial number in the subject name? [yes/no]: no % Include an IP address in the subject name? [no]: no Request certificate from CA? [yes/no]: yes % Certificate request sent to Certificate Authority % The 'show crypto pki certificate verbose Win7_PC' command will show the fingerprint. *Jul 17 15:21:11.343: CRYPTO_PKI: Certificate Request Fingerprint MD5: 9153E537 11C16FAE B03F7A38 775DBB92 *Jul 17 15:21:11.343: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 3BC4AC98 91067707 BB6BBBFB ABD97796 F7FB3DD1 *Jul 17 15:21:15.675: %PKI-6-CERTRET: Certificate received from Certificate Authority
步驟5.驗證憑證資訊。
IOS-CA#show crypto pki certificates verbose <Win7_PC>
Certificate
Status: Available
Version: 3
Certificate Serial Number (hex): 03
Certificate Usage: General Purpose
Issuer:
cn=calo_root
Subject:
Name: Connected_2_INET-B
hostname=Connected_2_INET-B
cn=Win7_PC.david.com
Validity Date:
start date: 13:29:51 UTC Jul 13 2017
end date: 13:29:51 UTC Jul 13 2018
Subject Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Signature Algorithm: SHA1 with RSA Encryption
Fingerprint MD5: 9153E537 11C16FAE B03F7A38 775DBB92
Fingerprint SHA1: 3BC4AC98 91067707 BB6BBBFB ABD97796 F7FB3DD1
X509v3 extensions:
X509v3 Key Usage: A0000000
Digital Signature
Key Encipherment
X509v3 Subject Key ID: F37266AE 61F64BD9 3E9FA80C 77455F21 5BEB870D
X509v3 Authority Key ID: B5EEEEB9 31B9A06C CBD9893C 0E318810 5CA657E6
Authority Info Access:
Extended Key Usage:
Client Auth
Server Auth
Associated Trustpoints: Win7_PC
Key Label: Win7_PC
CA Certificate
Status: Available
Version: 3
Certificate Serial Number (hex): 01
Certificate Usage: Signature
Issuer:
cn=calo_root
Subject:
cn=calo_root
Validity Date:
start date: 13:24:35 UTC Jul 13 2017
end date: 13:24:35 UTC Jul 12 2020
Subject Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Signature Algorithm: MD5 with RSA Encryption
Fingerprint MD5: DA4502F4 CEFB4F08 AAA3179B 70019185
Fingerprint SHA1: A887F6DB 0656C7E2 857749F3 EA3D7176 8920F52F
X509v3 extensions:
X509v3 Key Usage: 86000000
Digital Signature
Key Cert Sign
CRL Signature
X509v3 Subject Key ID: B5EEEEB9 31B9A06C CBD9893C 0E318810 5CA657E6
X509v3 Basic Constraints:
CA: TRUE
X509v3 Authority Key ID: B5EEEEB9 31B9A06C CBD9893C 0E318810 5CA657E6
Authority Info Access:
Associated Trustpoints: test HeadEnd Win7_PC CA_Server
在Windows 7客戶端電腦上安裝身份證書
步驟1.以PKCS12格式(.p12)將命名的Win7_PC信任點匯出到FTP/TFTP伺服器(安裝在Windows 7電腦上),以在單個檔案中獲取身份證書、CA證書和私鑰。
IOS-CA(config)#crypto pki export <Win7_PC> pkcs12 <tftp://10.152.206.175/ Win7_PC.p12> password <cisco123> Address or name of remote host [10.152.206.175]? Destination filename [Win7_PC.p12]? !Writing pkcs12 file to tftp://10.152.206.175/Win7_PC.p12 ! CRYPTO_PKI: Exported PKCS12 file successfully. *Jul 17 16:29:20.310: %PKI-6-PKCS12EXPORT_SUCCESS: PKCS #12 Successfully Exported.
這是匯出檔案在客戶端電腦上的外觀。
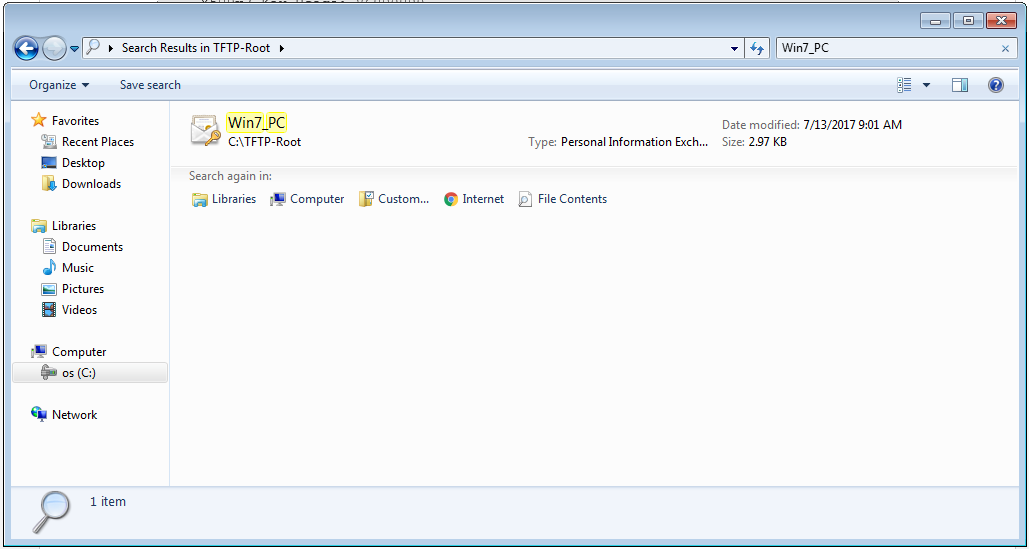
步驟2.按Ctrl + R並鍵入mmc以開啟Microsoft管理控制檯(MMC)。

步驟3.選擇OK。
步驟4.導航到檔案>新增/刪除管理單元。

步驟5.選擇Certificates > Add > Computer Account。
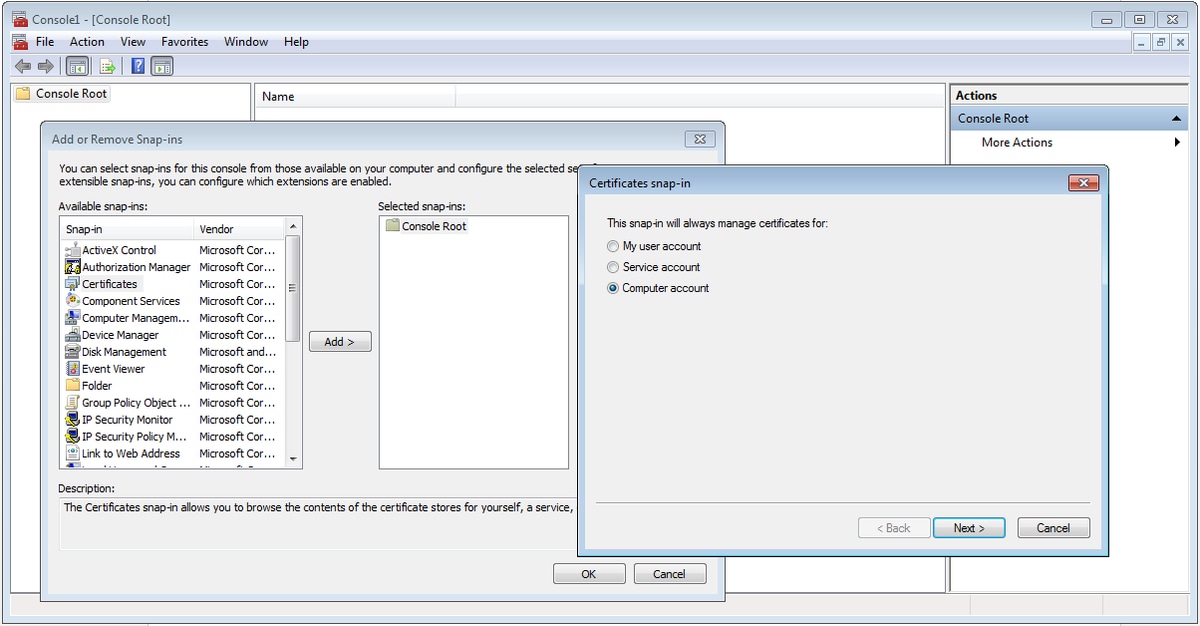
步驟6.選擇下一步,

步驟7.完成。
步驟8.選擇OK。
步驟9.轉到Certificates(Local Computer)>Personal>Certificates,按一下右鍵資料夾並導航到All Tasks>Import:
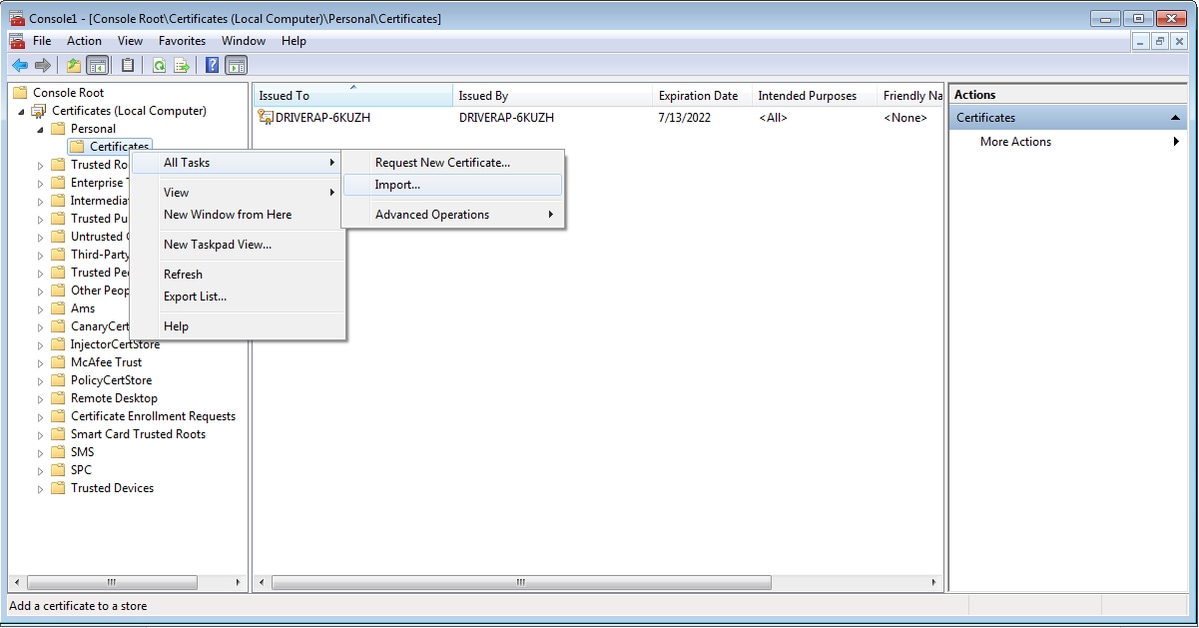

步驟10.按一下「Next」。指示儲存PKCS12檔案的路徑。

步驟11.再次選擇下一步,並鍵入在crypto pki export <Win7_PC> pkcs12 <tftp://10.152.206.175/ Win7_PC.p12> password <cisco123>命令中輸入的密碼
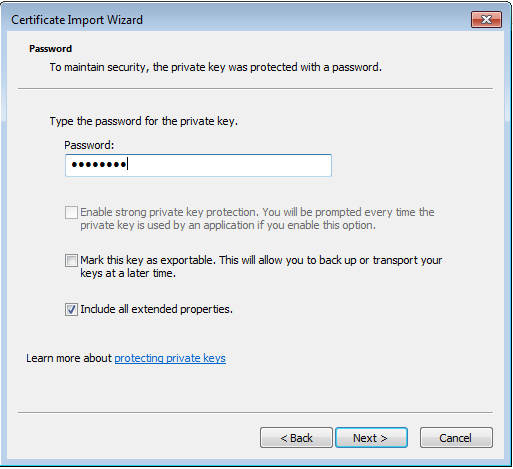
步驟12.選擇下一步。

步驟13.再次選擇Next。
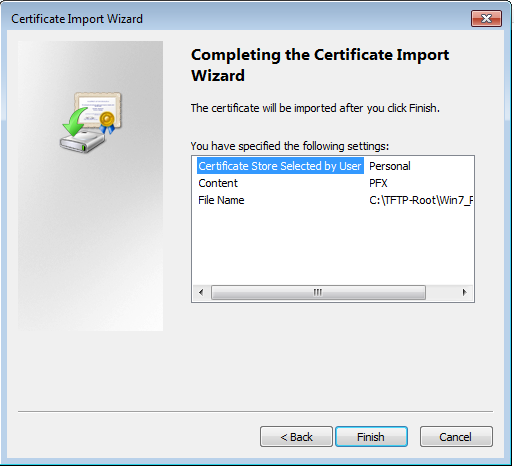
步驟14.選擇完成。
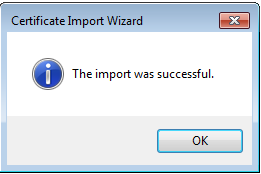
步驟15.選擇OK。現在您將看到已安裝的證書(CA證書和身份證書)。
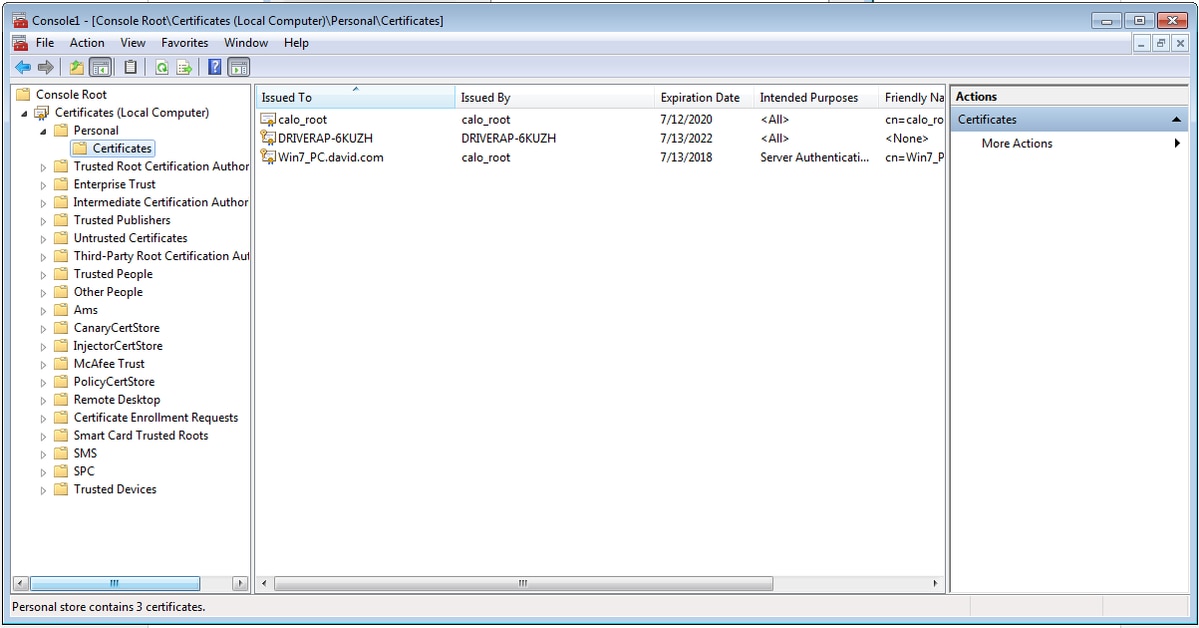
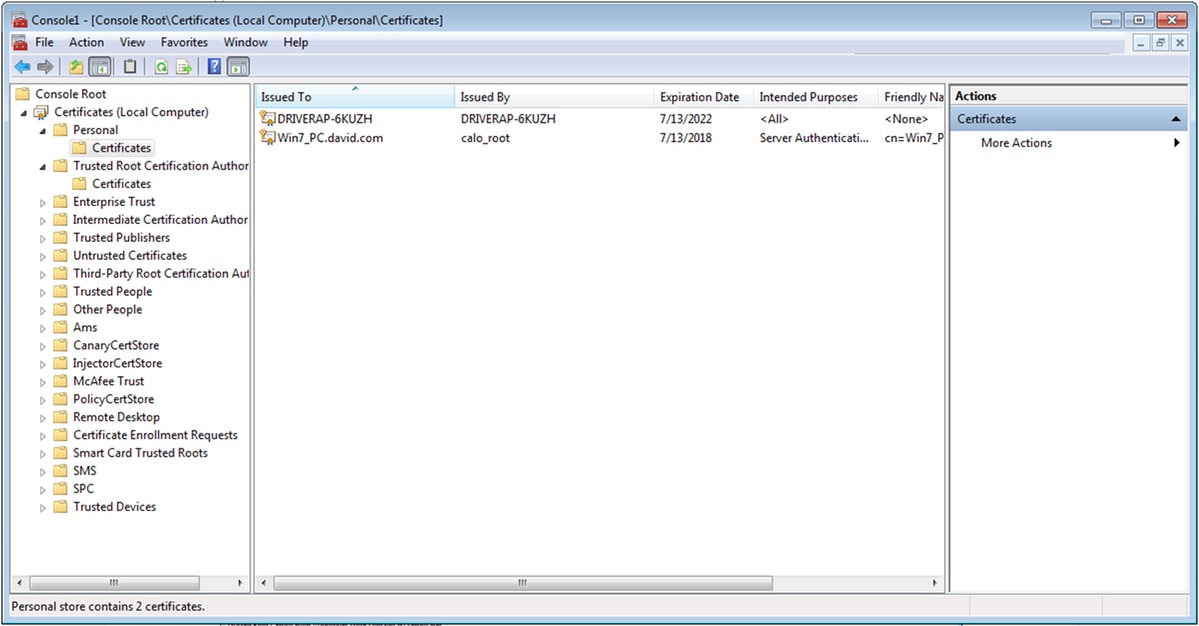
步驟16.將CA證書從證書(本地電腦)>個人>證書拖放到證書(本地電腦)>受信任的根證書頒發機構>證書。

如何在Android流動裝置上安裝身份證書
附註:Android支援副檔名為.pfx或.p12的PKCS#12金鑰儲存檔案。
附註:Android僅支援DER編碼的X.509 SSL證書。
步驟1。從PKCS12(.p12)格式的IOS CA伺服器匯出使用者端憑證後,透過電子郵件將檔案傳送到Android裝置。安裝完畢後,請點選檔案的名稱以啟動自動安裝。(不下載檔案)
步驟2.輸入用於匯出證書的密碼,在本例中,密碼為cisco123。

步驟3.選擇OK並輸入Certificate name。它可以是任何單詞,在本示例中,名稱為Android ID Cert。

步驟4.選擇「OK」,系統將顯示消息「Android ID Cert installed」。
步驟5。若要安裝CA憑證,請以base64格式從IOS CA伺服器擷取該憑證,並以.crt擴充檔儲存該憑證。通過電子郵件將檔案傳送到Android裝置。這一次,您需要透過貼上檔案名稱旁邊的箭頭來下載檔案。
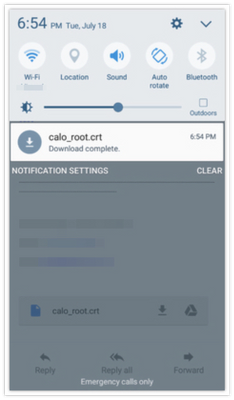
步驟6.導覽至Settings和Lock screen and security。
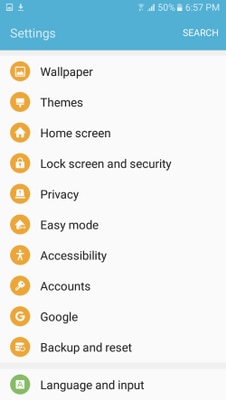
步驟7.選擇Other security settings。

步驟8.導航至從裝置儲存安裝。

步驟9.選擇.crt檔案並點選完成。

步驟10.輸入憑證名稱。它可以是任何單詞,在本例中,名稱為calo_root-1。

步驟10.選擇OK,您將看到消息「calo_root-1 installed」。

步驟11.若要驗證是否已安裝身份證書,請導航到Settings/Lock Screen and Security/Other > Security Settings/User Certificates/System頁籤。
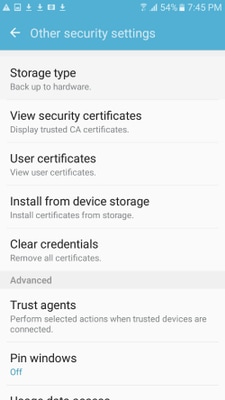
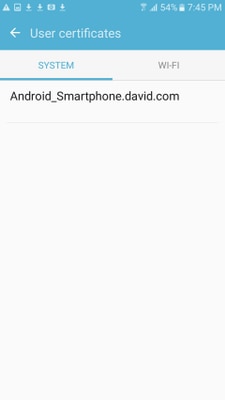
步驟12.要驗證CA證書是否已安裝,請導航到Settings/Lock螢幕和security/Other security settings/View security certificates/User頁籤。


為使用IKEv2的RA VPN配置ASA頭端
步驟1。在ASDM上,導航到Configuration>Remote Access VPN > Network(client)Access> Anyconnect Connection Profiles。在面向VPN客戶端的介面上選中IPSec(IKEv2)access, Allow Access框(Enable Client Services選項不是必需的)。
步驟2.選擇Device Certificate,然後從Use same device certificate for SSL and IPSec IKEv2中刪除檢查標籤。
步驟3.為IPSec連線選擇頭端證書,為SSL連線選擇 — 無。
此選項將實施加密ikev2、加密ipsec、加密動態對映和加密對映配置。
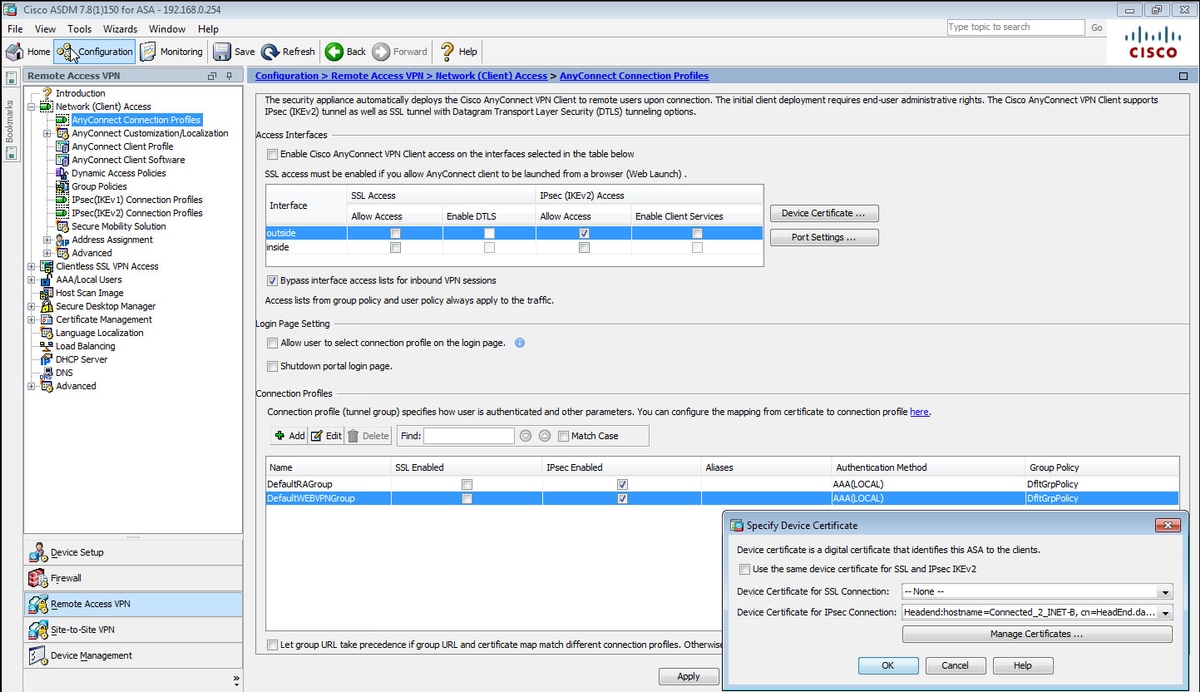
這是組態在指令行介面(CLI)上的樣子。
crypto ikev2 policy 1 encryption aes-256 integrity sha group 5 prf sha lifetime seconds 86400 crypto ikev2 enable outside crypto ikev2 remote-access trustpoint HeadEnd crypto ipsec ikev2 ipsec-proposal AES256 protocol esp encryption aes-256 protocol esp integrity sha-1 md5 crypto dynamic-map Anyconnect 65535 set ikev2 ipsec-proposal AES256 crypto map outside_map 65535 ipsec-isakmp dynamic Anyconnect crypto map outside_map interface outside
步驟4.導航到Configuration > Remote Access VPN > Network(Client)Access > Group Policies以建立組策略
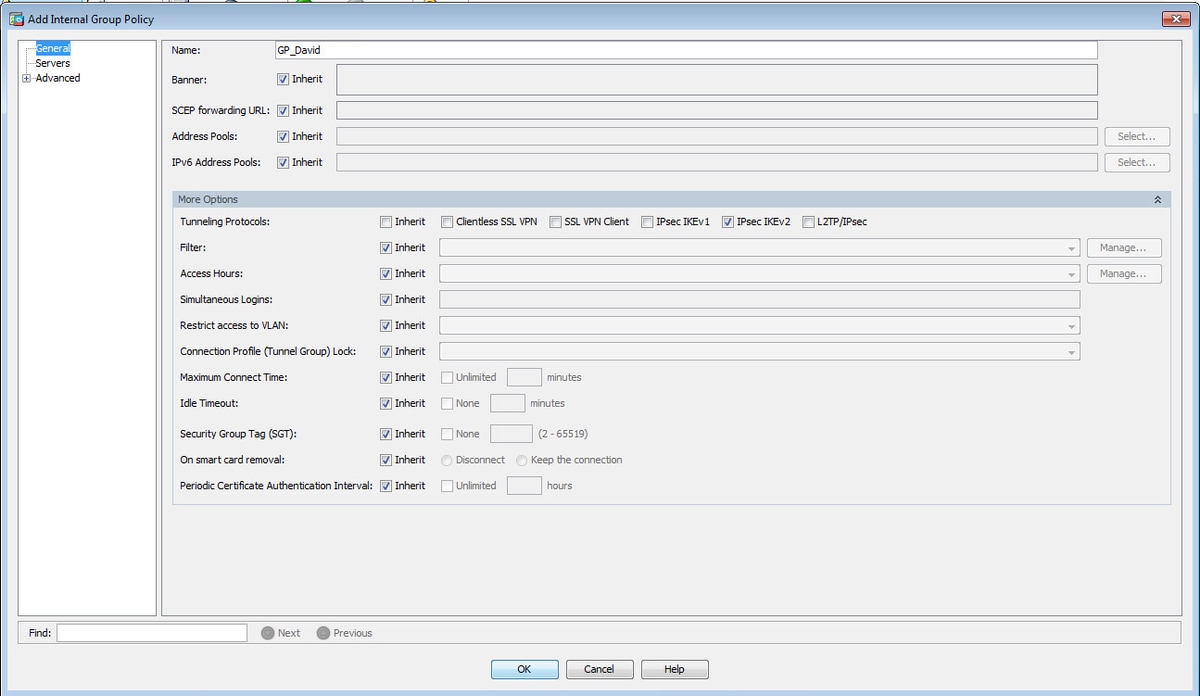
在CLI上。
group-policy GP_David internal group-policy GP_David attributes vpn-tunnel-protocol ikev2
步驟5.導航到Configuration > Remote Access VPN > Network(Client)Access > Address Pools,然後選擇Add以建立IPv4池。
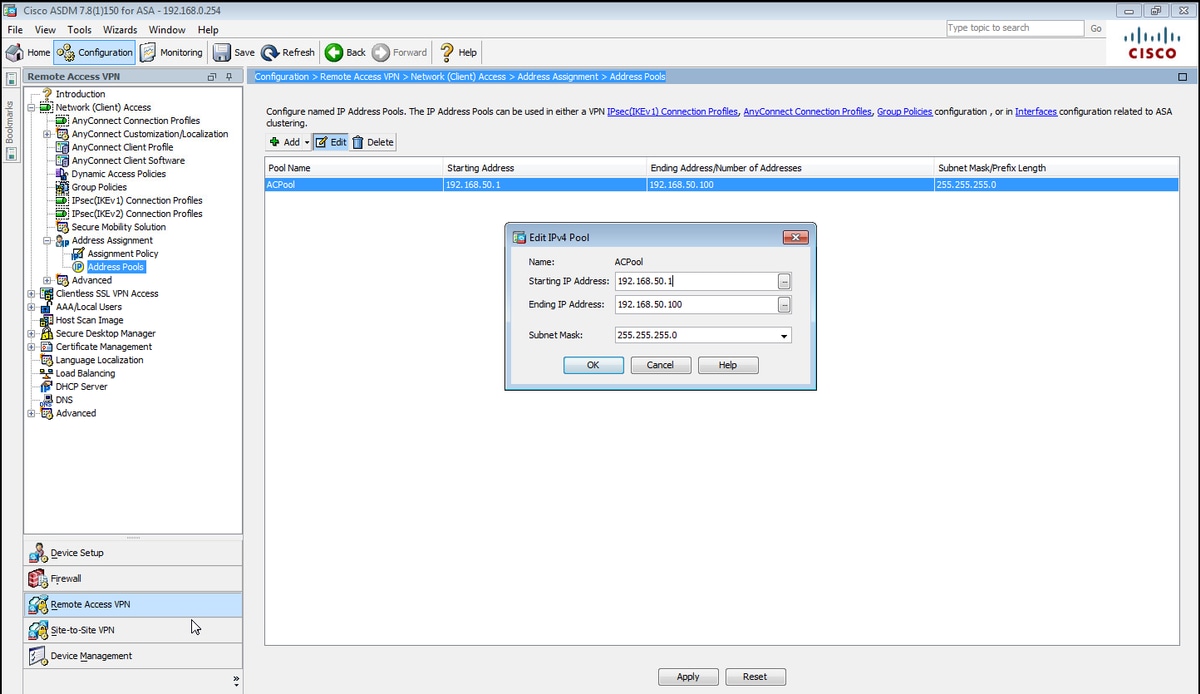
在CLI上。
ip local pool ACPool 192.168.50.1-192.168.50.100 mask 255.255.255.0
步驟6.導航到Configuration > Remote Access VPN > Network(Client)Access > IPSec(IKEv2)Connection Profiles,然後選擇Add以建立新的隧道組。

在CLI上。
tunnel-group David type remote-access tunnel-group David general-attributes address-pool ACPool default-group-policy GP_David authentication-server-group LOCAL tunnel-group David webvpn-attributes authentication certificate tunnel-group David ipsec-attributes ikev2 remote-authentication certificate ikev2 local-authentication certificate HeadEnd
步驟7.導航到Configuration > Remote Access VPN > Network(Client)Access > Advanced > IPsec > Certificate to Connection Profile maps > Policy,然後選中Used the configured rules to math a certificate to a Connection Profile框。

在CLI上。
tunnel-group-map enable rules
步驟8.導航到Configuration > Remote Access VPN > Network(Client)Access > Advanced > IPsec > Certificate to Connection Profile maps > Rules,然後建立新的證書對映。選擇Add並將其關聯到隧道組。在本示例中,隧道組名為David。
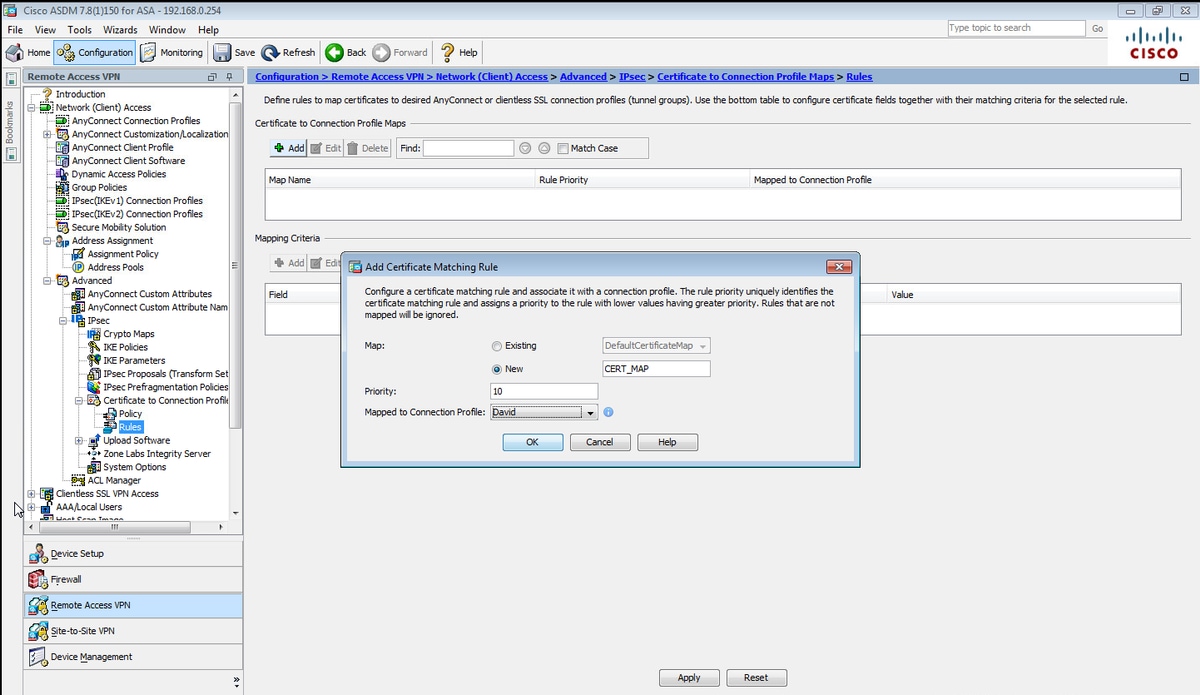
在CLI上。
tunnel-group-map CERT_MAP 10 David
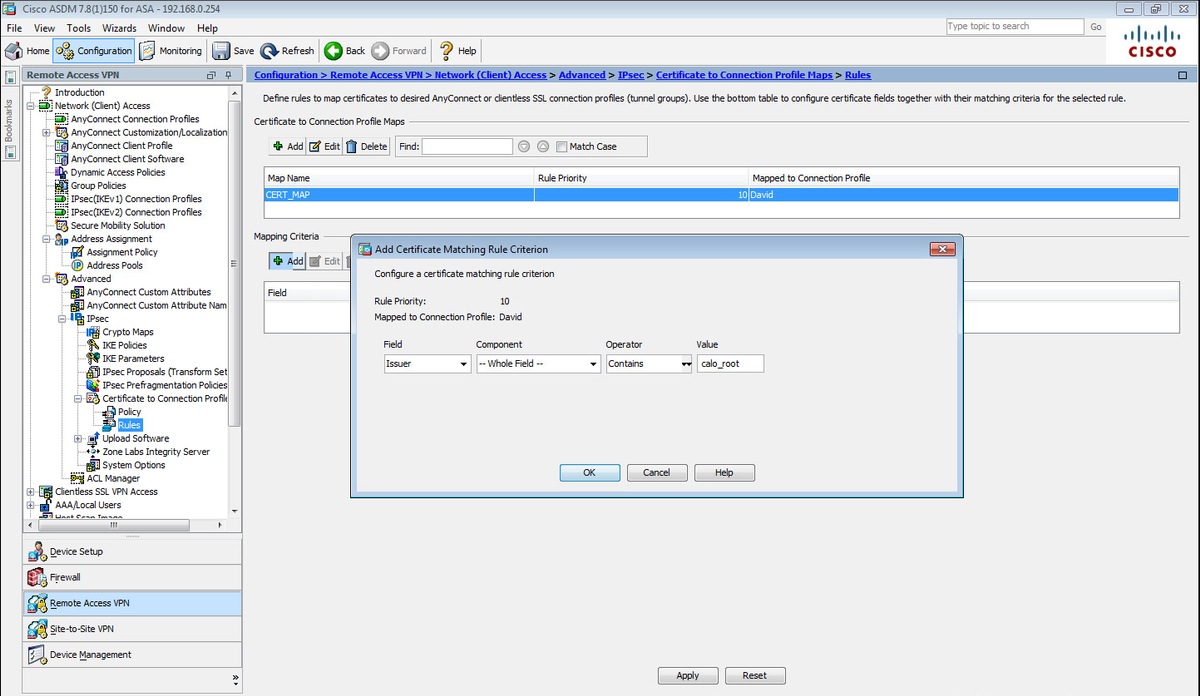
步驟9.在對映條件部分選擇Add,然後輸入這些值。
欄位:發行商
操作員:包含
值:calo_root
在CLI上。
crypto ca certificate map CERT_MAP 10 issuer-name co calo_root
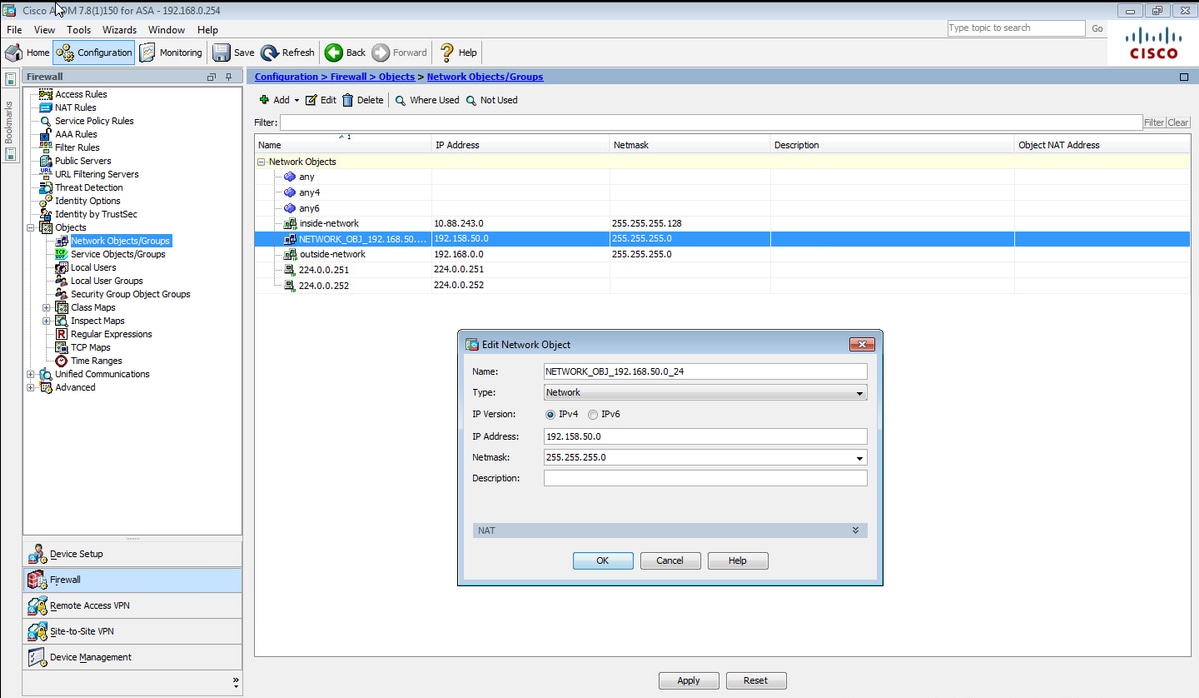
步驟10.使用要使用的IP池網路建立對象,以便在Configuration > Firewall > Objects > Network Objects/Groups> Add處新增(網路地址轉換)NAT免除規則。
在CLI上。
object network NETWORK_OBJ_192.168.50.0_24 subnet 192.168.50.0 255.255.255.0
步驟11.導航到Configuration > Firewall > NAT Rules,然後選擇Add為RA VPN流量建立NAT免除規則。

在CLI上。
nat (inside,outside) source static any any destination static NETWORK_OBJ_192.168.50.0_24 NETWORK_OBJ_192.168.50.0_24 no-proxy-arp route-lookup
這是用於此示例的完整ASA配置。
interface GigabitEthernet1/1 nameif outside security-level 0 ip address 10.88.243.108 255.255.255.128 object network NETWORK_OBJ_192.168.50.0_24 subnet 192.168.50.0 255.255.255.0 nat (inside,outside) source static any any destination static NETWORK_OBJ_192.168.50.0_24 NETWORK_OBJ_192.168.50.0_24 ip local pool ACPool 192.168.50.1-192.168.50.100 mask 255.255.255.0 crypto ikev2 policy 1 encryption aes-256 integrity sha group 5 prf sha lifetime seconds 86400 crypto ikev2 enable outside crypto ikev2 remote-access trustpoint HeadEnd group-policy GP_David internal group-policy GP_David attributes vpn-tunnel-protocol ikev2 tunnel-group David type remote-access tunnel-group David general-attributes address-pool ACPool default-group-policy GP_David authentication-server-group LOCAL tunnel-group David webvpn-attributes authentication certificate tunnel-group David ipsec-attributes ikev2 remote-authentication certificate ikev2 local-authentication certificate HeadEnd tunnel-group-map enable rules crypto ca certificate map CERT_MAP 10 issuer-name co calo_root tunnel-group-map CERT_MAP 10 David crypto ipsec ikev2 ipsec-proposal AES256 protocol esp encryption aes-256 protocol esp integrity sha-1 md5 crypto dynamic-map Anyconnect 65535 set ikev2 ipsec-proposal AES256 crypto map outside_map 65535 ipsec-isakmp dynamic Anyconnect crypto map outside_map interface outside
配置Windows 7內建客戶端
步驟1.導覽至控制面板>網路和Internet >網路和共用中心。
步驟2.選擇設定新的連線或網路。

步驟3.選擇連線到工作區和下一步。
步驟4.選擇否,建立新連線和下一步。
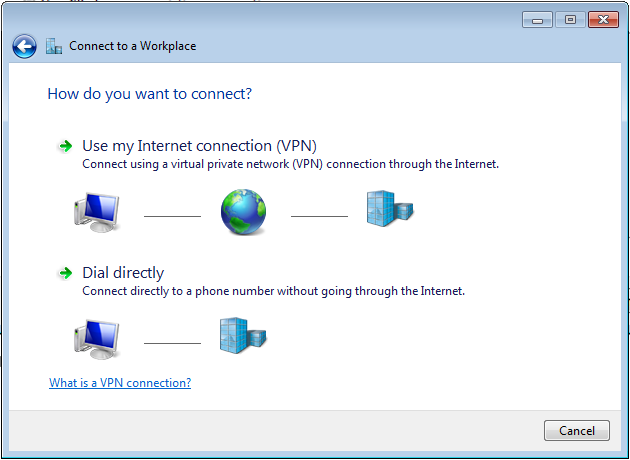
步驟5.選擇Use my Internet connection(VPN),然後在Internet address欄位上新增HeadEnd certificate Common Name(CN)字元串。在Destination Name欄位中,鍵入連線的名稱。它可以是任何字串。請確保選中Don't connect now;只需設定它,我可以在以後連線機箱。

步驟6.選擇下一步。

步驟7.選擇Create。
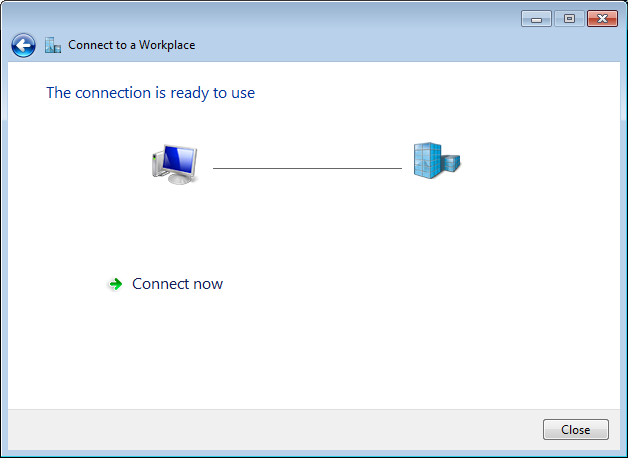
步驟8.選擇關閉並導航到控制面板>網路和Internet >網路連線。選擇已建立的網路連線並按一下右鍵它。選擇屬性。
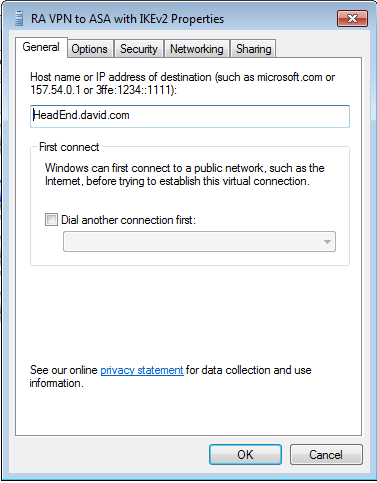
步驟9.在General索引標籤中,您可以驗證頭端的適當主機名是否正確。您的電腦會將此名稱解析為用於連線RA VPN使用者的ASA IP地址。
步驟10.導航到Security頁籤,然後選擇IKEv2作為VPN的型別。在Authentication部分中選擇Use machine certificates。
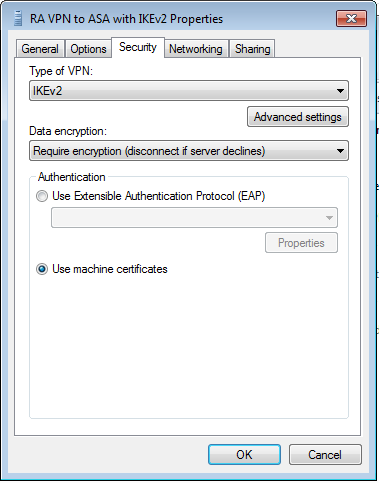
步驟11.選擇OK並導航到C:\Windows\System32\drivers\etc。使用文本編輯器開啟hosts檔案。配置條目以將網路連線中配置的(完全限定域名)FQDN解析為ASA頭端(在本例中為外部介面)的IP地址。
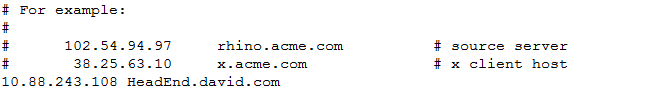
步驟12.返回控制面板>網路和Internet >網路連線。選擇您建立的網路連線。按一下右鍵該連結,然後選擇「連線」。
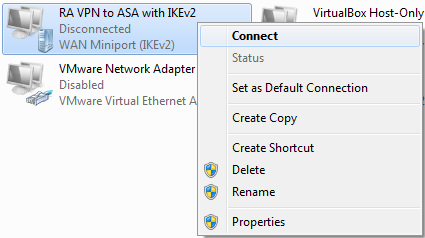
步驟13.網路連線狀態從「已斷開連線」轉變為「已連線」,然後轉變為「已連線」。最後,顯示您為網路連線指定的名稱。
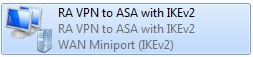
此時電腦已連線到VPN頭端。
配置Android本地VPN客戶端
步驟1.導覽至Settings>More connection Settings
步驟2.選擇VPN
步驟3.選擇Add VPN。如果連線已建立如本例所示,請輕觸引擎圖示以對其進行編輯。在「類型」字段中指定IPSec IKEv2 RSA。Server address是啟用IKEv2的ASA介面IP地址。對於IPSec使用者證書和IPSec CA證書,請點選下拉選單選擇安裝的證書。使用預設選項「從伺服器接收」保留IPSec伺服器證書。


步驟4.選擇Save,然後點選新VPN連線的名稱。

步驟5.選擇連線。

步驟6.再次鍵入VPN連線以驗證狀態。現在顯示為Connected。

驗證
ASA頭端上的驗證命令:
ASA#show vpn-sessiondb detail ra-ikev2-ipsec
Session Type: Generic Remote-Access IKEv2 IPsec Detailed
Username : Win7_PC.david.com Index : 24
Assigned IP : 192.168.50.1 Public IP : 10.152.206.175
Protocol : IKEv2 IPsec
License : AnyConnect Premium
Encryption : IKEv2: (1)AES256 IPsec: (1)AES256
Hashing : IKEv2: (1)SHA1 IPsec: (1)SHA1
Bytes Tx : 0 Bytes Rx : 16770
Pkts Tx : 0 Pkts Rx : 241
Pkts Tx Drop : 0 Pkts Rx Drop : 0
Group Policy : GP_David Tunnel Group : David
Login Time : 08:00:01 UTC Tue Jul 18 2017
Duration : 0h:00m:21s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 0a0a0a0100018000596dc001
Security Grp : none
IKEv2 Tunnels: 1
IPsec Tunnels: 1
IKEv2:
Tunnel ID : 24.1
UDP Src Port : 4500 UDP Dst Port : 4500
Rem Auth Mode: rsaCertificate
Loc Auth Mode: rsaCertificate
Encryption : AES256 Hashing : SHA1
Rekey Int (T): 86400 Seconds Rekey Left(T): 86379 Seconds
PRF : SHA1 D/H Group : 2
Filter Name :
IPsec:
Tunnel ID : 24.2
Local Addr : 0.0.0.0/0.0.0.0/0/0
Remote Addr : 192.168.50.1/255.255.255.255/0/0
Encryption : AES256 Hashing : SHA1
Encapsulation: Tunnel
Rekey Int (T): 28800 Seconds Rekey Left(T): 28778 Seconds
Idle Time Out: 30 Minutes Idle TO Left : 30 Minutes
Conn Time Out: 518729 Minutes Conn TO Left : 518728 Minutes
Bytes Tx : 0 Bytes Rx : 16947
Pkts Tx : 0 Pkts Rx : 244
ASA# show crypto ikev2 sa
IKEv2 SAs:
Session-id:24, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
2119549341 10.88.243.108/4500 10.152.206.175/4500 READY RESPONDER Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:2, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/28 sec
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 192.168.50.1/0 - 192.168.50.1/65535
ESP spi in/out: 0xbfff64d7/0x76131476
ASA# show crypto ipsec sa
interface: outside
Crypto map tag: Anyconnect, seq num: 65535, local addr: 10.88.243.108
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (192.168.50.1/255.255.255.255/0/0)
current_peer: 10.152.206.175, username: Win7_PC.david.com
dynamic allocated peer ip: 192.168.50.1
dynamic allocated peer ip(ipv6): 0.0.0.0
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 339, #pkts decrypt: 339, #pkts verify: 339
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.88.243.108/4500, remote crypto endpt.: 10.152.206.175/4500
path mtu 1496, ipsec overhead 58(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 76131476
current inbound spi : BFFF64D7
inbound esp sas:
spi: 0xBFFF64D7 (3221185751)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={RA, Tunnel, IKEv2, }
slot: 0, conn_id: 98304, crypto-map: Anyconnect
sa timing: remaining key lifetime (sec): 28767
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x76131476 (1980961910)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={RA, Tunnel, IKEv2, }
slot: 0, conn_id: 98304, crypto-map: Anyconnect
sa timing: remaining key lifetime (sec): 28767
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
ASA#show vpn-sessiondb license-summary
---------------------------------------------------------------------------
VPN Licenses and Configured Limits Summary
---------------------------------------------------------------------------
Status : Capacity : Installed : Limit
-----------------------------------------
AnyConnect Premium : ENABLED : 50 : 50 : NONE
AnyConnect Essentials : DISABLED : 50 : 0 : NONE
Other VPN (Available by Default) : ENABLED : 10 : 10 : NONE
Shared License Server : DISABLED
Shared License Participant : DISABLED
AnyConnect for Mobile : ENABLED(Requires Premium or Essentials)
Advanced Endpoint Assessment : ENABLED(Requires Premium)
AnyConnect for Cisco VPN Phone : ENABLED
VPN-3DES-AES : ENABLED
VPN-DES : ENABLED
---------------------------------------------------------------------------
---------------------------------------------------------------------------
VPN Licenses Usage Summary
---------------------------------------------------------------------------
Local : Shared : All : Peak : Eff. :
In Use : In Use : In Use : In Use : Limit : Usage
----------------------------------------------------
AnyConnect Premium : 1 : 0 : 1 : 1 : 50 : 2%
AnyConnect Client : : 0 : 1 : 0%
AnyConnect Mobile : : 0 : 0 : 0%
Clientless VPN : : 0 : 0 : 0%
Generic IKEv2 Client : : 1 : 1 : 2%
Other VPN : : 0 : 0 : 10 : 0%
Cisco VPN Client : : 0 : 0 : 0%
L2TP Clients
Site-to-Site VPN : : 0 : 0 : 0%
---------------------------------------------------------------------------
ASA# show vpn-sessiondb
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
AnyConnect Client : 0 : 11 : 1 : 0
SSL/TLS/DTLS : 0 : 1 : 1 : 0
IKEv2 IPsec : 0 : 10 : 1 : 0
Generic IKEv2 Remote Access : 1 : 14 : 1
---------------------------------------------------------------------------
Total Active and Inactive : 1 Total Cumulative : 25
Device Total VPN Capacity : 50
Device Load : 2%
---------------------------------------------------------------------------
---------------------------------------------------------------------------
Tunnels Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concurrent
----------------------------------------------
IKEv2 : 1 : 25 : 1
IPsec : 1 : 14 : 1
IPsecOverNatT : 0 : 11 : 1
AnyConnect-Parent : 0 : 11 : 1
SSL-Tunnel : 0 : 1 : 1
DTLS-Tunnel : 0 : 1 : 1
---------------------------------------------------------------------------
Totals : 2 : 63
疑難排解
本節提供的資訊可用於對組態進行疑難排解。
附註:使用debug指令之前,請先參閱有關Debug指令的重要資訊。
注意:在ASA上,您可以設定各種調試級別;預設情況下,使用級別1。如果更改調試級別,調試的詳細程度會增加。請謹慎執行此操作,尤其是在生產環境中。
- Debug crypto ikev2 protocol 15
- Debug crypto ikev2 platform 15
- Debug crypto ca 255
由思科工程師貢獻
- David RiveraCisco TAC工程師
- Cesar Lopez ZamarripaCisco TAC工程師
 意見
意見