簡介
本文檔介紹如何使用設定配置ASA,以從VPN連線中排除發往Microsoft Office 365(Microsoft Teams)和Cisco Webex的流量。
背景資訊
配置自適應安全裝置(ASA)還為支援自適應安全裝置的AnyConnect客戶端引入網路地址排除和基於動態完全限定域名(FQDN)的排除。
分割通道
需要將ASA配置為從隧道中排除指定的IPv4和IPv6目標清單。遺憾的是,地址清單是動態的,並且可能會更改。有關python指令碼和聯機python讀取/評估列印循環(REPL)的連結,請參閱「配置」一節,此循環可用來檢索清單和生成示例配置。
動態分割通道
除了分割排除網路地址清單之外,在Windows和Mac版AnyConnect 4.6中還新增了動態分割隧道。動態分割隧道使用FQDN來確定連線是否可以經過隧道。Python指令碼還確定要新增到自定義AnyConnect屬性的終結點的FQDN。
組態
在Python 3 REPL中運行此指令碼,或在公共REPL環境(如AnyConnectO365DynamicExclude)中運行此指令碼
import urllib.request
import uuid
import json
import re
def print_acl_lines(acl_name, ips, section_comment):
slash_to_mask = (
"0.0.0.0",
"192.0.2.1",
"192.0.2.1",
"10.224.0.0",
"10.240.0.0",
"10.248.0.0",
"10.252.0.0",
"10.254.0.0",
"10.255.0.0",
"10.255.128.0",
"10.255.192.0",
"10.255.224.0",
"10.255.240.0",
"10.255.248.0",
"10.255.252.0",
"10.255.254.0",
"10.255.255.0",
"10.255.255.128",
"10.255.255.192",
"10.255.255.224",
"10.255.255.240",
"10.255.255.248",
"10.255.255.252",
"10.255.255.254",
"10.255.255.255",
"10.255.255.255",
"10.255.255.255",
"10.255.255.255",
"10.255.255.240",
"10.255.255.248",
"10.255.255.252",
"10.255.255.254",
"10.255.255.255",
)
print(
"access-list {acl_name} remark {comment}".format(
acl_name=acl_name, comment=section_comment
)
)
for ip in sorted(ips):
if ":" in ip:
# IPv6 address
print(
"access-list {acl_name} extended permit ip {ip} any6".format(
acl_name=acl_name, ip=ip
)
)
else:
# IPv4 address. Convert to a mask
addr, slash = ip.split("/")
slash_mask = slash_to_mask[int(slash)]
print(
"access-list {acl_name} extended permit ip {addr} {mask} any4".format(
acl_name=acl_name, addr=addr, mask=slash_mask
)
)
# Fetch the current endpoints for O365
http_res = urllib.request.urlopen(
url="https://endpoints.office.com/endpoints/worldwide?clientrequestid={}".format(
uuid.uuid4()
)
)
res = json.loads(http_res.read())
o365_ips = set()
o365_fqdns = set()
for service in res:
if service["category"] == "Optimize":
for ip in service.get("ips", []):
o365_ips.add(ip)
for fqdn in service.get("urls", []):
o365_fqdns.add(fqdn)
# Generate an acl for split excluding For instance
print("##### Step 1: Create an access-list to include the split-exclude networks\n")
acl_name = "ExcludeSass"
# O365 networks
print_acl_lines(
acl_name=acl_name,
ips=o365_ips,
section_comment="v4 and v6 networks for Microsoft Office 365",
)
# Microsoft Teams
# https://docs.microsoft.com/en-us/office365/enterprise/office-365-vpn-implement-split-tunnel#configuring-and-securing-teams-media-traffic
print_acl_lines(
acl_name=acl_name,
ips=["10.107.60.1/32"],
section_comment="v4 address for Microsoft Teams"
)
# Cisco Webex - Per https://help.webex.com/en-us/WBX000028782/Network-Requirements-for-Webex-Teams-Services
webex_ips = [
"10.68.96.1/19",
"10.114.160.1/20",
"10.163.32.1/19",
"192.0.2.1/18",
"192.0.2.2/19",
"198.51.100.1/20",
"203.0.113.1/19",
"203.0.113.254/19",
"203.0.113.2/19",
"172.29.192.1/19",
"203.0.113.1/20",
"10.26.176.1/20",
"10.109.192.1/18",
"10.26.160.1/19",
]
print_acl_lines(
acl_name=acl_name,
ips=webex_ips,
section_comment="IPv4 and IPv6 destinations for Cisco Webex",
)
# Edited. April 1st 2020
# Per advice from Microsoft they do NOT advise using dynamic split tunneling for their properties related to Office 365
#
print(
"\n\n##### Step 2: Create an Anyconnect custom attribute for dynamic split excludes\n"
)
print("SKIP. Per Microsoft as of April 2020 they advise not to dynamically split fqdn related to Office365")
#print(
# """
#webvpn
# anyconnect-custom-attr dynamic-split-exclude-domains description dynamic-split-exclude-domains
#
#anyconnect-custom-data dynamic-split-exclude-domains saas {}
#""".format(
# ",".join([re.sub(r"^\*\.", "", f) for f in o365_fqdns])
# )
#)
#
print("\n##### Step 3: Configure the split exclude in the group-policy\n")
print(
"""
group-policy GP1 attributes
split-tunnel-policy excludespecified
ipv6-split-tunnel-policy excludespecified
split-tunnel-network-list value {acl_name}
""".format(
acl_name=acl_name
)
)
注意:Microsoft建議使用發佈的IPv4和IPv6地址範圍配置分割隧道,將發往關鍵Office 365服務的流量從VPN連線範圍中排除。為了獲得最佳效能並最有效地使用VPN容量,可以直接在VPN隧道之外路由與Office 365 Exchange Online、SharePoint Online和Microsoft Teams(在Microsoft文檔中稱為「最佳化」類別)關聯的這些專用IP地址範圍的流量。有關此建議的更多詳細資訊,請參閱使用VPN拆分隧道最佳化遠端使用者的Office 365連線。
註:截至2020年4月初,Microsoft Teams有一個依賴關係,即必須從隧道中排除IP範圍10.107.60.1/32。有關詳細資訊,請參閱配置和保護Teams媒體流量。
驗證
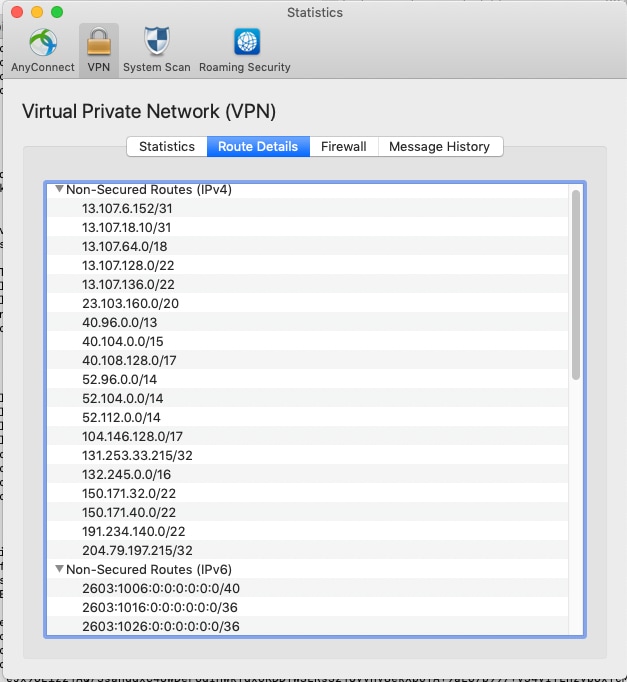
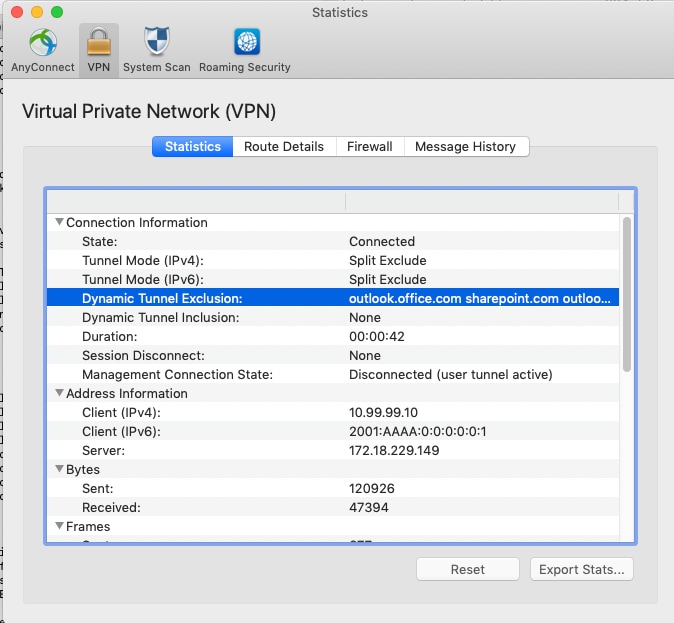
連線使用者後,您會看到用ACL中提供的地址填充的非安全路由以及動態隧道排除清單。


 意見
意見