設定EAP鏈結與TEAP
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本文檔介紹如何配置可擴展身份驗證協定(EAP)鏈的ISE和Windows請求方。
必要條件
需求
思科建議您瞭解以下主題:
-
ISE
-
Windows請求方配置
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- Cisco ISE版本3.0
- Windows 10建置2004
- 協定基於隧道的可擴展身份驗證協定(TEAP)的知識
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
背景資訊
TEAP是一種基於隧道的可擴展身份驗證協定方法,它建立安全隧道並在該安全隧道的保護下執行其他EAP方法。
TEAP驗證在初始EAP身份請求/響應交換後分兩個階段進行。 在第一階段,技經評估組使用TLS握手來提供經驗證的金鑰交換並建立受保護的隧道。隧道建立後,第二階段從對等體與伺服器進行進一步通話以建立所需的身份驗證和授權策略開始。
Cisco ISE 2.7及更高版本支援TEAP協定。 型別長度值(TLV)對象用於隧道內在EAP對等體和EAP伺服器之間傳輸身份驗證相關資料。
Microsoft在2020年5月發佈的Windows 10 2004版中引入了對TEAP的支援。
EAP鏈結允許使用者與機器在一個EAP/Radius作業階段內進行驗證,而不是在兩個不同的作業階段內進行驗證。 以前,要實現此功能,您需要使用Cisco AnyConnect NAM模組並在Windows請求方上使用EAP-FAST,因為本機Windows請求方不支援此功能。現在,您可以使用Windows本地請求方透過TEAP使用ISE 2.7執行EAP連結。
設定
Cisco ISE配置
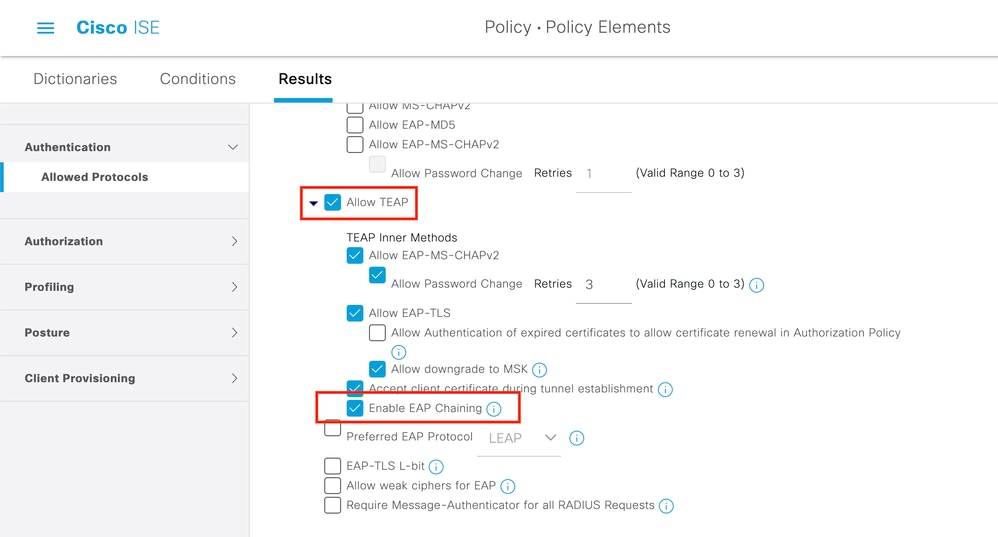
步驟 1.您需要編輯Allowed Protocols以啟用TEAP和EAP連結。
導航到ISE > Policy > Policy Elements > Results > Authentication > Allowed Protocols > Add New. 選中TEAP和EAP鏈覈取方塊。
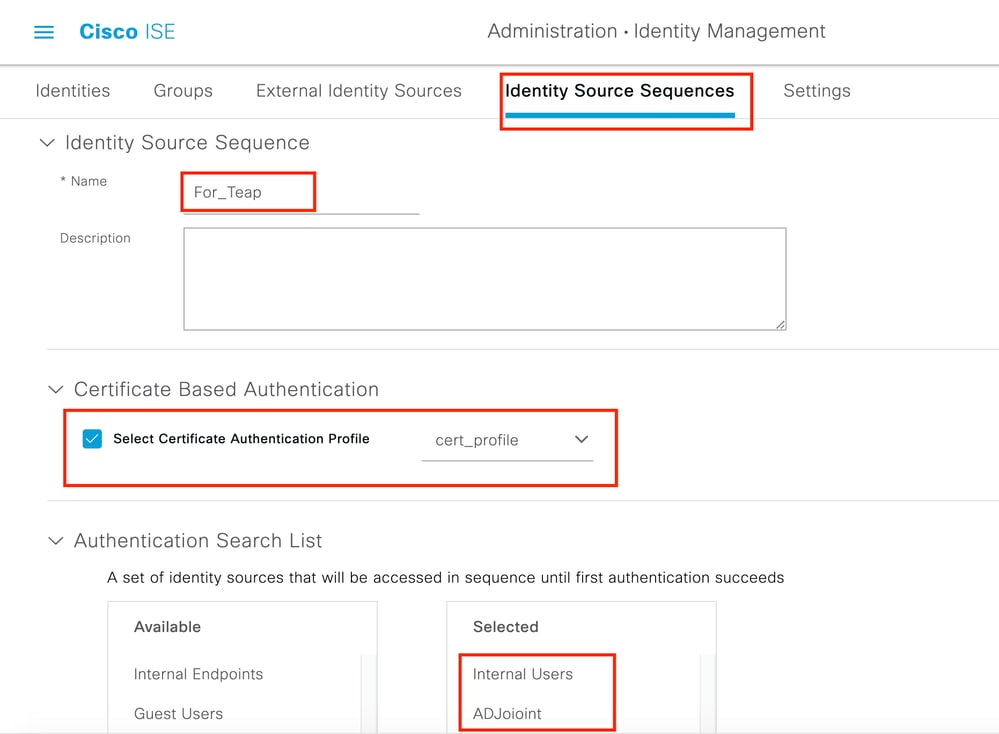
步驟 2.建立證書配置檔案並將其增加到身份源序列。
導航到ISE > Administration > Identities > identity Source Sequence,然後選擇「證書配置檔案」。
步驟 3.您需要在身份驗證策略中呼叫此序列。
導航到ISE > Policy > Policy Sets. Choose the Policy Set forDot1x > Authentication Policy 並選擇Step 2中建立的Identity源序列。

步驟 4.現在您需要修改Dot1x策略集下的授權策略。
導航到ISE > Policy > Policy Sets. Choose the Policy Set for Dot1x > Authentication Policy。
您需要建立兩個規則。第一條 規則檢查電腦是否已透過身份驗證,但使用者未通過身份驗證。第二規則驗證使用者和機器都經過驗證。

這將完成從ISE伺服器端的配置。
Windows原生Supplicant客戶端配置
Windows原生Supplicant客戶端配置配置本文檔中的有線身份驗證設定。
導航到Control Panel > Network and Sharing Center > Change Adapter Settings,然後按一下右鍵LAN Connection > Properties。按一下Authentication頁籤。
步驟 1.按一下Authentication下拉選單並選擇Microsoft EAP-TEAP。
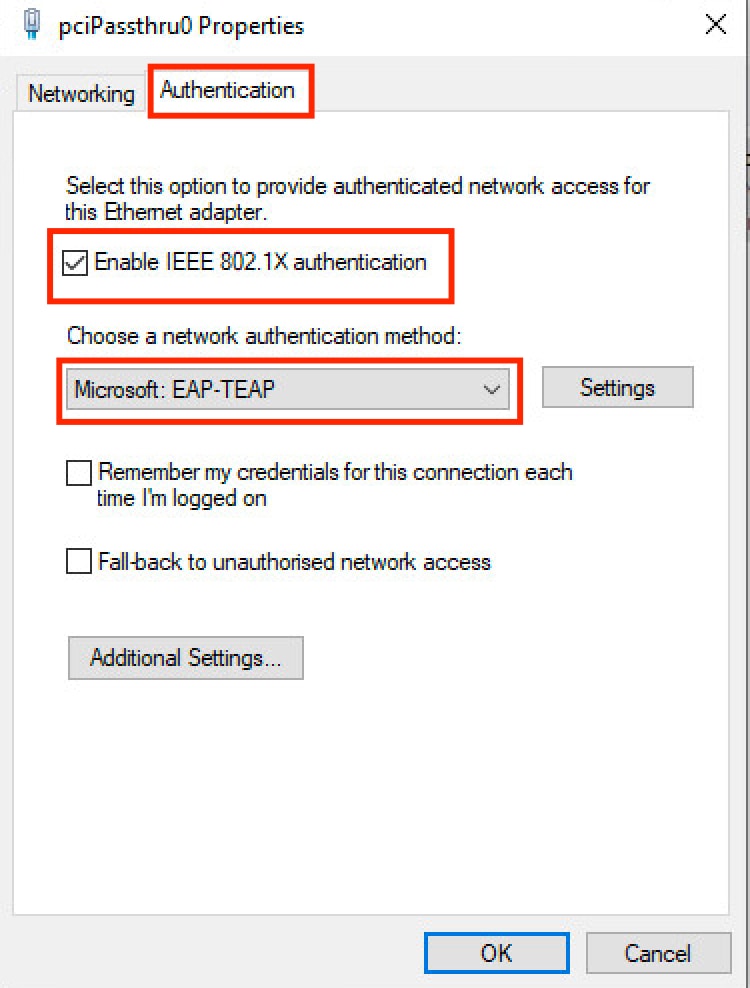
步驟 2. 點選TEAP旁邊的Settings按鈕。
- 使用
anonymous保持啟用Enable Identity Privacy。 - 在用於在ISE PSN上簽署EAP身份驗證證書的受信任根證書頒發機構下的根CA伺服器旁邊打勾。

步驟 3.在「Client Authentication」下,為Microsoft選擇EAP身份驗證方法:Smart Card of other certificate。
步驟 4.對於每個EAP方法下拉選單,按一下Configure按鈕,然後根據需要進行修改,然後按一下OK。
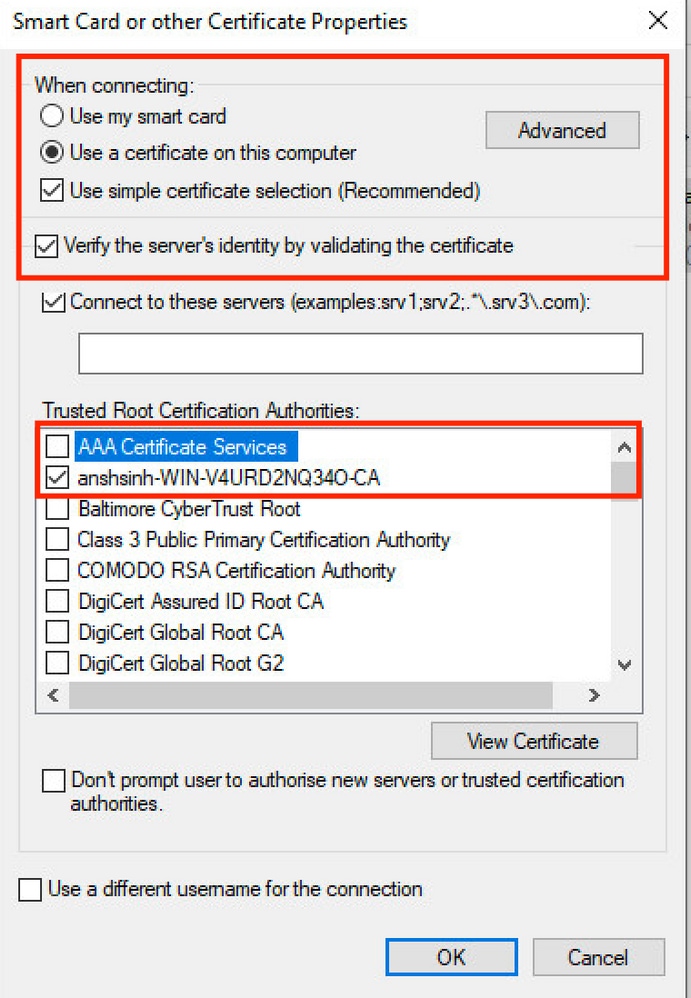
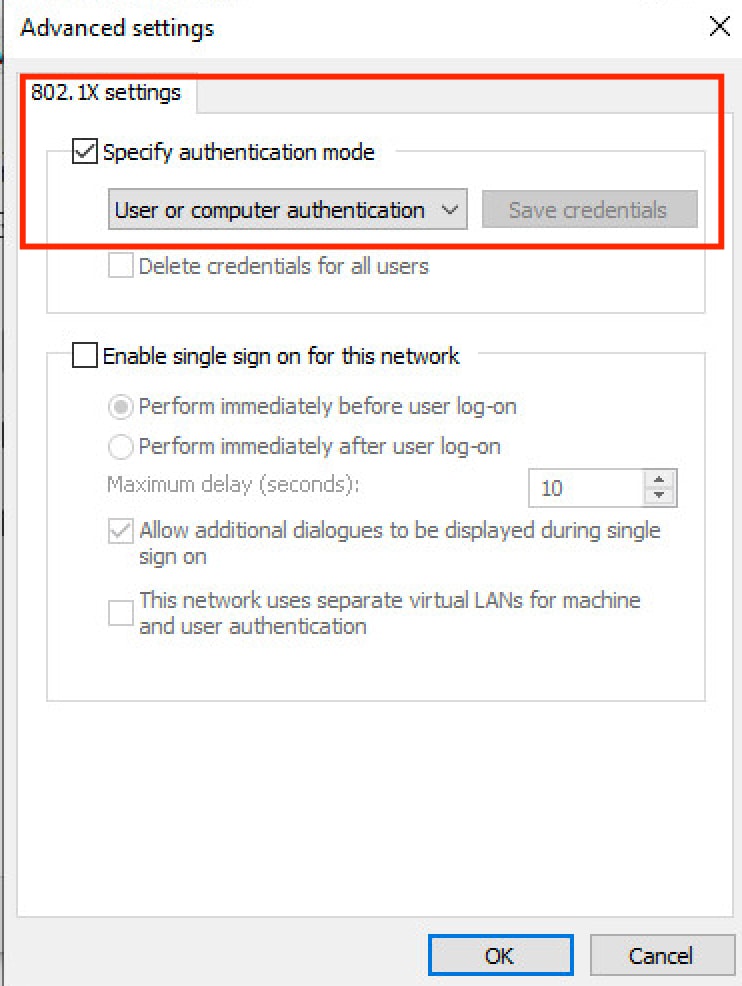
步驟 5.按一下底部的Additional Settings按鈕。
- 啟用指定驗證模式。
- 將下拉選單設定為相應的設定。
- 選擇
User or computer authentication以便驗證和按一下OK。
驗證
驗證您可以重新啟動Windows 10電腦,也可以註銷然後登入。每當windows登入螢幕顯示時,都會觸發電腦身份驗證。
在即時日誌中,您可以在身份欄位中看到匿名、主機/管理員(此處是電腦名稱)。您會看到匿名,因為您在上方配置了身份隱私請求方。
當您使用憑證登入PC時,可以在即時記錄中看到Administrator@example.local, host/Administrator。這是EAP鏈結,其中使用者與機器驗證皆在一個EAP作業階段中發生。

詳細的身份驗證報告
詳細的身份驗證報告 在Live Log Details中,電腦身份驗證只顯示一個NACRadiusUsername 條目,但連結使用者和電腦身份驗證顯示兩個條目(一個使用者條目,一個電腦條目)。此外,您將在Authentication Details 部分下看到,TEAP (EAP-TLS) 該命令用於Authentication Protocol。如果將MSCHAPv2用於電腦和使用者身份驗證,則身份驗證協定將顯示 TEAP (Microsoft: Secured password (EAP-MSCHAP v2))。
機器驗證
機器驗證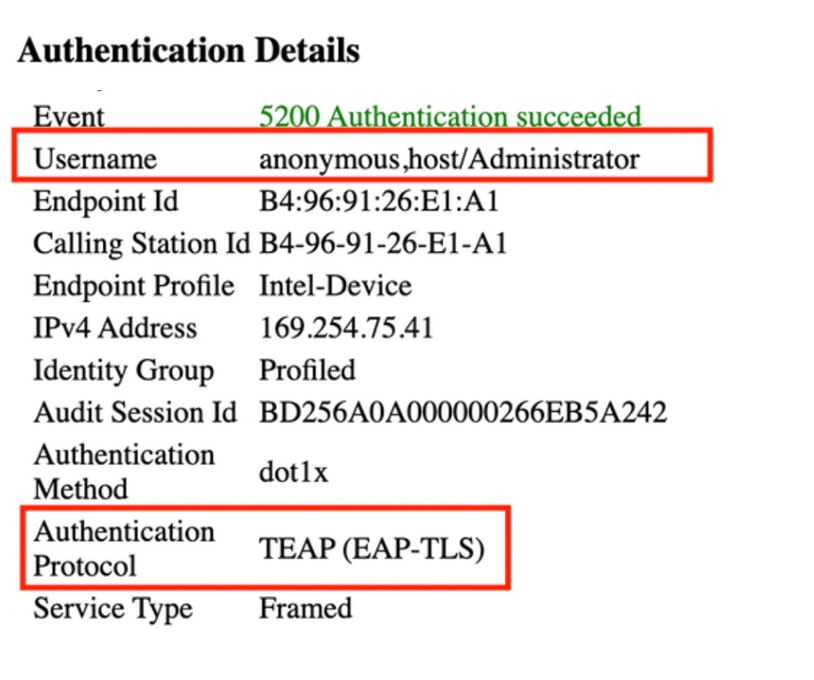

使用者和電腦身份驗證
使用者和電腦身份驗證

疑難排解
疑難排解您需要在ISE上啟用以下調試:
runtime-AAAnsfnsf-sessionActive Directory(用於排除ISE和AD之間的故障)
在Windows上,您可以檢查事件檢視器日誌。
即時日誌分析
即時日誌分析機器驗證
機器驗證
11001 Received RADIUS Access-Request 11017 RADIUS created a new session ... ... 11507 Extracted EAP-Response/Identity 12756 Prepared EAP-Request proposing TEAP with challenge ... ... 12758 Extracted EAP-Response containing TEAP challenge-response and accepting TEAP as negotiated 12800 Extracted first TLS record; TLS handshake started 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message ... ... 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded ... ... 11559 Client certificate was requested but not received inside the tunnel. Will continue with inner method. 11620 TEAP full handshake finished successfully ... ... 11627 Starting EAP chaining 11573 Selected identity type 'User' 11564 TEAP inner method started 11521 Prepared EAP-Request/Identity for inner EAP method ... ... 11567 Identity type provided by client is equal to requested 11522 Extracted EAP-Response/Identity for inner EAP method 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request ... ... 11515 Supplicant declined inner EAP method selected by Authentication Policy but did not proposed another one; inner EAP negotiation failed 11520 Prepared EAP-Failure for inner EAP method 11566 TEAP inner method finished with failure 22028 Authentication failed and the advanced options are ignored 33517 Sent TEAP Intermediate Result TLV indicating failure 11596 Prepared EAP-Request with another TEAP challenge ... ... 11574 Selected identity type 'Machine' 11564 TEAP inner method started 11521 Prepared EAP-Request/Identity for inner EAP method ... ... 11567 Identity type provided by client is equal to requested 11522 Extracted EAP-Response/Identity for inner EAP method 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 11596 Prepared EAP-Request with another TEAP challenge ... ... 12523 Extracted EAP-Response/NAK for inner method requesting to use EAP-TLS instead 12522 Prepared EAP-Request for inner method proposing EAP-TLS with challenge 12625 Valid EAP-Key-Name attribute received 11596 Prepared EAP-Request with another TEAP challenge ... ... 12524 Extracted EAP-Response containing EAP-TLS challenge-response for inner method and accepting EAP-TLS as negotiated 12800 Extracted first TLS record; TLS handshake started 12545 Client requested EAP-TLS session ticket 12546 The EAP-TLS session ticket received from supplicant. Inner EAP-TLS does not support stateless session resume. Performing full authentication 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge ... ... 12571 ISE will continue to CRL verification if it is configured for specific CA - certificate for Users 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded 12509 EAP-TLS full handshake finished successfully ... ... 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge 11596 Prepared EAP-Request with another TEAP challenge ... ... 61025 Open secure connection with TLS peer 15041 Evaluating Identity Policy 22072 Selected identity source sequence - forAD1 22070 Identity name is taken from certificate attribute 22037 Authentication Passed 12528 Inner EAP-TLS authentication succeeded 11519 Prepared EAP-Success for inner EAP method 11565 TEAP inner method finished successfully ... ... 33516 Sent TEAP Intermediate Result TLV indicating success 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 11595 Extracted EAP-Response containing TEAP challenge-response 11637 Inner method supports EMSK but the client provided only MSK. Allow downgrade as per configuration 11576 TEAP cryptobinding verification passed ... ... 15036 Evaluating Authorization Policy 24209 Looking up Endpoint in Internal Endpoints IDStore - anonymous,host/Administrator 24211 Found Endpoint in Internal Endpoints IDStore 11055 User name change detected for the session. Attributes for the session will be removed from the cache 15048 Queried PIP - Network Access.EapChainingResult 15016 Selected Authorization Profile - PermitAccess 33514 Sent TEAP Result TLV indicating success ... ... 11597 TEAP authentication phase finished successfully 11503 Prepared EAP-Success 11002 Returned RADIUS Access-Accept
使用者和電腦身份驗證
使用者和電腦身份驗證
11001 Received RADIUS Access-Request 11017 RADIUS created a new session ... ... 12756 Prepared EAP-Request proposing TEAP with challenge ... ... 12758 Extracted EAP-Response containing TEAP challenge-response and accepting TEAP as negotiated 12800 Extracted first TLS record; TLS handshake started 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message 11596 Prepared EAP-Request with another TEAP challenge ... ... 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded 11559 Client certificate was requested but not received inside the tunnel. Will continue with inner method. 11620 TEAP full handshake finished successfully 11596 Prepared EAP-Request with another TEAP challenge ... ... 11595 Extracted EAP-Response containing TEAP challenge-response 11627 Starting EAP chaining 11573 Selected identity type 'User' 11564 TEAP inner method started 11521 Prepared EAP-Request/Identity for inner EAP method 11596 Prepared EAP-Request with another TEAP challenge ... ... 11567 Identity type provided by client is equal to requested 11522 Extracted EAP-Response/Identity for inner EAP method 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 11596 Prepared EAP-Request with another TEAP challenge ... ... 12523 Extracted EAP-Response/NAK for inner method requesting to use EAP-TLS instead 12522 Prepared EAP-Request for inner method proposing EAP-TLS with challenge ... ... 11595 Extracted EAP-Response containing TEAP challenge-response 12524 Extracted EAP-Response containing EAP-TLS challenge-response for inner method and accepting EAP-TLS as negotiated 12800 Extracted first TLS record; TLS handshake started 12545 Client requested EAP-TLS session ticket 12546 The EAP-TLS session ticket received from supplicant. Inner EAP-TLS does not support stateless session resume. Performing full authentication 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge ... ... 12526 Extracted EAP-Response for inner method containing TLS challenge-response 12571 ISE will continue to CRL verification if it is configured for specific CA - certificate for Users 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded 12509 EAP-TLS full handshake finished successfully 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge ... ... 12526 Extracted EAP-Response for inner method containing TLS challenge-response 61025 Open secure connection with TLS peer 15041 Evaluating Identity Policy 22072 Selected identity source sequence - forAD1 22070 Identity name is taken from certificate attribute 22037 Authentication Passed 12528 Inner EAP-TLS authentication succeeded 11519 Prepared EAP-Success for inner EAP method 11565 TEAP inner method finished successfully 33516 Sent TEAP Intermediate Result TLV indicating success 11596 Prepared EAP-Request with another TEAP challenge ... ... 11595 Extracted EAP-Response containing TEAP challenge-response 11637 Inner method supports EMSK but the client provided only MSK. Allow downgrade as per configuration 11576 TEAP cryptobinding verification passed 11574 Selected identity type 'Machine' 11564 TEAP inner method started ... ... 11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge 11596 Prepared EAP-Request with another TEAP challenge ... ... 12523 Extracted EAP-Response/NAK for inner method requesting to use EAP-TLS instead 12522 Prepared EAP-Request for inner method proposing EAP-TLS with challenge ... ... 12524 Extracted EAP-Response containing EAP-TLS challenge-response for inner method and accepting EAP-TLS as negotiated 12800 Extracted first TLS record; TLS handshake started 12545 Client requested EAP-TLS session ticket 12546 The EAP-TLS session ticket received from supplicant. Inner EAP-TLS does not support stateless session resume. Performing full authentication 12805 Extracted TLS ClientHello message 12806 Prepared TLS ServerHello message 12807 Prepared TLS Certificate message 12808 Prepared TLS ServerKeyExchange message 12809 Prepared TLS CertificateRequest message 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge ... ... 12526 Extracted EAP-Response for inner method containing TLS challenge-response 12571 ISE will continue to CRL verification if it is configured for specific CA - certificate for Users 12811 Extracted TLS Certificate message containing client certificate 12812 Extracted TLS ClientKeyExchange message 12813 Extracted TLS CertificateVerify message 12804 Extracted TLS Finished message 12801 Prepared TLS ChangeCipherSpec message 12802 Prepared TLS Finished message 12816 TLS handshake succeeded 12509 EAP-TLS full handshake finished successfully 12527 Prepared EAP-Request for inner method with another EAP-TLS challenge 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 11595 Extracted EAP-Response containing TEAP challenge-response 12526 Extracted EAP-Response for inner method containing TLS challenge-response 61025 Open secure connection with TLS peer 15041 Evaluating Identity Policy 22072 Selected identity source sequence - forAD1 22070 Identity name is taken from certificate attribute 22037 Authentication Passed 12528 Inner EAP-TLS authentication succeeded 11519 Prepared EAP-Success for inner EAP method 11565 TEAP inner method finished successfully 33516 Sent TEAP Intermediate Result TLV indicating success 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 11595 Extracted EAP-Response containing TEAP challenge-response 11637 Inner method supports EMSK but the client provided only MSK. Allow downgrade as per configuration 11576 TEAP cryptobinding verification passed 15036 Evaluating Authorization Policy 24209 Looking up Endpoint in Internal Endpoints IDStore - Administrator@example.local,host/Administrator 24211 Found Endpoint in Internal Endpoints IDStore 11055 User name change detected for the session. Attributes for the session will be removed from the cache 15048 Queried PIP - Network Access.EapChainingResult 15016 Selected Authorization Profile - PermitAccess 33514 Sent TEAP Result TLV indicating success 11596 Prepared EAP-Request with another TEAP challenge 11006 Returned RADIUS Access-Challenge 11001 Received RADIUS Access-Request 11018 RADIUS is re-using an existing session 11595 Extracted EAP-Response containing TEAP challenge-response 11597 TEAP authentication phase finished successfully 11503 Prepared EAP-Success 11002 Returned RADIUS Access-Accept
相關資訊
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
3.0 |
18-Jun-2024 |
已更新標題、簡介、替代文字、機器翻譯及格式設定。 |
1.0 |
10-Dec-2020 |
初始版本 |
由思科工程師貢獻
- Anshu SinhaASIC Engineering Technical Leader
 意見
意見