簡介
本檔案介紹IKEv2加密對映備份對等體在思科安全防火牆裝置上的鏈路故障轉移期間的功能。
必要條件
·自適應安全裝置版本9.14(1)或更高版本
·防火牆威脅防禦6.6版或更高版本
·防火牆管理中心版本6.6或更高版本
·防火牆裝置管理器版本6.6 - 7.0(通過API)或通過GUI的7.1+
需求
思科建議您瞭解以下主題:
·對IKEv2站點到站點加密對映的基本瞭解
· VPN端點之間的基本底層連線
·對IP服務級別協定功能有基礎認識
採用元件
本檔案中的資訊是根據以下軟體版本和硬體版本:
·兩個Cisco ASAv裝置版本9.16(2)
·三台Cisco IOS®路由器15.9(3)M4版
·兩個Ubuntu主機版本20.04
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
理論
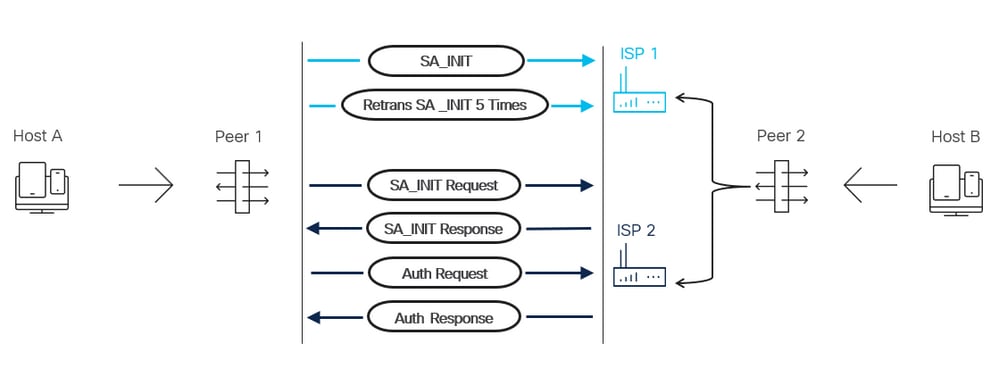
IKEv2多對等體拓撲的響應方端不支援IKEv2對等體遍歷。例如,拓撲中有兩個VPN端點稱為對等點1和對等點2。對等2有兩個ISP介面,對等1有1個ISP介面。發生ISP故障切換時,如果配置到位,則對等體2在輔助ISP介面上啟動IKE以監控路徑。對等體1不會自動遍歷IP地址以使用為加密對映列出的備份對等體來容納對等體2的ISP故障切換。連線失敗,直到流量從對等體1發起。一旦對等體1根據加密ACL發起流量,它就會嘗試通過主ISP路徑進行通訊,直到路徑被重新傳輸宣告為失效為止。此過程大約需要2分鐘。一旦主對等體被宣告為非活動狀態,對等體1啟動與列出的備份對等體的連線,然後建立連線。一旦主ISP路徑再次可用,且對等2交換至其主ISP介面,對等1需要生成相關流量。此過程允許對等體1啟動與加密對映中列出的主對等體的連線,並正常建立IKE連線。
操作順序
1. VPN對等體2 SLA檢測到路徑故障。
2. VPN對等點2具有路由表更新,以更改用於到達VPN對等點1的路徑,該路徑會更改其IKE標識。
3.主機A不斷發起目的地為主機B的流量。
4. VPN對等點1嘗試與VPN對等點2的主要ISP介面形成IKE連線,直到發生5次重新傳輸。
5.然後,VPN對等體1宣告該對等體失效,並移動到加密對映中的輔助對等體,該加密對映是VPN對等體2的輔助ISP介面。此連線已成功建立。
網路圖表
組態範例
VPN對等點2
Interfaces:
interface GigabitEthernet0/0
nameif PRIMARY-ISP
security-level 0
ip address 203.0.113.1 255.255.255.0
interface GigabitEthernet0/1
nameif BACKUP-ISP
security-level 0
ip address 198.51.100.1 255.255.255.0
interface GigabitEthernet0/2
nameif inside
security-level 100
ip address 192.168.10.2 255.255.255.00
SLA和路由:
sla monitor 500
type echo protocol ipIcmpEcho 209.165.200.226 interface PRIMARY-ISP
num-packets 3
frequency 5
sla monitor schedule 500 life forever start-time now
track 1 rtr 500 reachability
route PRIMARY-ISP 0.0.0.0 0.0.0.0 203.0.113.2 1 track 1
route BACKUP-ISP 0.0.0.0 0.0.0.0 198.51.100.2 254
加密:
crypto ikev2 policy 1
encryption aes-256
integrity sha256
group 21
prf sha256
lifetime seconds 86400
crypto ikev2 enable PRIMARY-ISP
crypto ikev2 enable BACKUP-ISP
crypto ipsec ikev2 ipsec-proposal PROPOSAL
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto map MAP 1 match address CRYPTO
crypto map MAP 1 set peer 192.0.2.1
crypto map MAP 1 set ikev2 ipsec-proposal PROPOSAL
crypto map MAP interface PRIMARY-ISP
crypto map MAP interface BACKUP-ISP
Tunnel-group:
tunnel-group 192.0.2.1 type ipsec-l2l
tunnel-group 192.0.2.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
Access-list:
access-list CRYPTO line 1 extended permit ip 192.168.10.0 255.255.255.0 10.10.10.0 255.255.255.0
VPN對等點1
Interfaces:
interface GigabitEthernet0/0
nameif OUTSIDE
security-level 0
ip address 192.0.2.1 255.255.255.0
interface GigabitEthernet0/1
nameif INSIDE
security-level 100
ip address 10.10.10.2 255.255.255.0
路由:
route OUTSIDE 0.0.0.0 0.0.0.0 192.0.2.2
加密:
crypto ikev2 policy 1
encryption aes-256
integrity sha256
group 21
prf sha256
lifetime seconds 86400
crypto ikev2 enable OUTSIDE
crypto ipsec ikev2 ipsec-proposal PROPOSAL
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto map MAP-2 1 match address CRYPTO-2
crypto map MAP-2 1 set peer 203.0.113.1 198.51.100.1
crypto map MAP-2 1 set ikev2 ipsec-proposal PROPOSAL
crypto map MAP-2 interface OUTSIDE
Tunnel-group:
tunnel-group 203.0.113.1 type ipsec-l2l
tunnel-group 203.0.113.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
tunnel-group 198.51.100.1 type ipsec-l2l
tunnel-group 198.51.100.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
Access-List:
access-list CRYPTO-2 line 1 extended permit ip 10.10.10.0 255.255.255.0 192.168.10.0 255.255.255.0
主ISP
介面:
GigabitEthernet0/0 203.0.113.2 255.255.255.0
GigabitEthernet0/1 209.165.200.225 255.255.255.224
備用ISP
介面:
GigabitEthernet0/0 198.51.100.2 255.255.255.0
GigabitEthernet0/1 209.165.202.130 255.255.255.224
ISP
介面:
GigabitEthernet0/0 209.165.202.129 255.255.255.224
GigabitEthernet0/1 209.165.200.226 255.255.255.224
主機
主機2:
192.168.10.1 255.255.255.0 dev ens2
主機1:
10.10.10.1 255.255.255.0 dev ens2
配置目標
在本實驗中,VPN對等體2查詢主ISP的G0/1介面的可達性。此查詢通過SLA監控使用ICMP完成。SLA配置繫結到路徑,然後該路徑又繫結到主ISP路由。如果此路由由於SLA可達性故障而不可用,則備份ISP路由將自動變為活動狀態。這表示現在從IP地址為198.51.100.1的BACKUP-ISP介面發起來自VPN對等體2的IKE協商。在VPN對等點1端上,198.51.100.1地址在加密對映中列為次要對等點。VPN對等體1需要啟動到加密對映中主對等體的加密ACL流量。然後,在使用加密對映中的輔助對等體之前,通過重新傳輸宣告對等體處於非活動狀態。
驗證
使用本節內容,確認設定功能符合預期
在SLA檢測到故障之前:
VPN-PEER-2# show track
Track 1
Response Time Reporter 500 reachability
Reachability is Up
12 changes, last change 05:51:34
Latest operation return code: OK
Latest RTT (millisecs) 7
Tracked by:
STATIC-IP-ROUTING 0
VPN-PEER-2# show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF
Gateway of last resort is 203.0.113.2 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 203.0.113.2, PRIMARY-ISP
C 192.168.10.0 255.255.255.0 is directly connected, inside
L 192.168.10.2 255.255.255.255 is directly connected, inside
C 198.51.100.0 255.255.255.0 is directly connected, BACKUP-ISP
L 198.51.100.1 255.255.255.255 is directly connected, BACKUP-ISP
C 203.0.113.0 255.255.255.0 is directly connected, PRIMARY-ISP
L 203.0.113.1 255.255.255.255 is directly connected, PRIMARY-ISP
VPN-PEER-2# show crypto ikev2 sa
IKEv2 SAs:
Session-id:75, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
160993547 203.0.113.1/500 192.0.2.1/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/21202 sec
Child sa: local selector 192.168.10.0/0 - 192.168.10.255/65535
remote selector 10.10.10.0/0 - 10.10.10.255/65535
ESP spi in/out: 0x30138366/0x7405d4a0
VPN-PEER-1# show crypto ikev2 sa
IKEv2 SAs:
Session-id:75, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
168559091 192.0.2.1/500 203.0.113.1/500 READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/21386 sec
Child sa: local selector 10.10.10.0/0 - 10.10.10.255/65535
remote selector 192.168.10.0/0 - 192.168.10.255/65535
ESP spi in/out: 0x7405d4a0/0x30138366
SLA檢測到故障後:
VPN-PEER-2# show track 1
Track 1
Response Time Reporter 500 reachability
Reachability is Down
13 changes, last change 00:05:23
Latest operation return code: Timeout
Tracked by:
STATIC-IP-ROUTING 0
VPN-PEER-2# show route
S* 0.0.0.0 0.0.0.0 [254/0] via 198.51.100.2, BACKUP-ISP
VPN-PEER-2# show crypto ikev2 sa
There are no IKEv2 SAs

注意:在主機A啟動要用於主機B的流量之前,IKE保持關閉。然後,VPN對等體1宣佈加密對映中的主對等體失效,並移動到備份對等體IP地址。
VPN-PEER-1# show crypto ikev2 sa
IKEv2 SAs:
Session-id:79, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
178593183 192.0.2.1/500 198.51.100.1/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/232 sec
Child sa: local selector 10.10.10.0/0 - 10.10.10.255/65535
remote selector 192.168.10.0/0 - 192.168.10.255/65535
ESP spi in/out: 0x695d6bf0/0xbefc13c

注意:VPN對等體1宣告加密對映中的主對等體失效,並啟動與備份對等體IP地址的連線。
疑難排解
Debug crypto ikev2 platform 255
Debug crypto ikev2 protocol 255
Debug crypto ispec 255
Debug sla monitor error #
Debug sla monitor trace



 意見
意見