簡介
本文檔介紹如何針對裝置模式下的安全防火牆1000、2100和安全防火牆3100/4200的故障轉移部署升級ASA。
必要條件
需求
思科建議您瞭解以下主題:
- 思科安全防火牆威脅防禦。
- 思科自適應安全裝置(ASA)配置。
採用元件
本檔案中的資訊是根據軟體版本:
- 思科調適型安全裝置軟體版本9.14(4)
- 思科調適型安全裝置軟體版本9.16(4)
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
設定
驗證必要條件
步驟1. 運行命令show fxos mode 以驗證裝置是否處於裝置模式

附註:對於9.13及更低版本中的Secure Firewall 21XX,僅支援平台模式。在9.14及更高版本中,裝置模式是預設模式。
ciscoasa# show fxos mode
Mode is currently set to appliance
步驟2.驗證相容性。
請參閱Cisco安全防火牆ASA相容性文檔,驗證FTD硬體平台和安全防火牆ASA軟體之間的相容性。請參閱
Cisco安全防火牆ASA相容性
步驟3.從思科軟體中心下載升級套件。

附註:對於安全防火牆1000/2100和安全防火牆3100/4200,不能單獨安裝ASA或FXOS;兩個映像都是套件組合的一部分。
請參閱連結的標題,瞭解捆綁包中的ASA和FXOS版本。請參閱安全防火牆1000/2100和3100/4200 ASA和FXOS捆綁版本。
使用CLI升級
步驟1. 重置ASDM映像。
在全域性配置模式下連線到主裝置並運行以下命令:
ciscoasa(config)# asdm image disk0:/asdm.bin
ciscoasa(config)# exit
ciscoasa# copy running-config startup-config
Source filename [running-config]?
Cryptochecksum: 6beb01d1 b7a3c30f 5e8eb557 a8ebb8ca
12067 bytes copied in 3.780 secs (4022 bytes/sec)
步驟2. 將軟體映像上傳到主裝置。

附註:在本檔案中,您使用的是FTP伺服器,但可以使用TFTP、HTTP或其他伺服器型別。
ciscoasa# copy ftp://calo:calo@10.88.7.12/cisco-asa-fp2k.9.16.4.SPA disk0:/cisco-asa-fp2k.9.16.4.SPA
Address or name of remote host [10.88.7.12]?
Source username [calo]?
Source password []? ****
Source filename [cisco-asa-fp2k.9.16.4.SPA]?
Destination filename [cisco-asa-fp2k.9.16.4.SPA]?
Accessing ftp:/calo:
@10.88.7.12/cisco-asa-fp2k.9.16.4.SPA...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Verifying file disk0:/cisco-asa-fp2k.9.16.4.SPA... Writing file disk0:/cisco-asa-fp2k.9.16.4.SPA... 474475840 bytes copied in 843.230 secs (562842 bytes/sec)
步驟3. 將軟體映像上傳到輔助裝置。
在主裝置上運行命令。
ciscoasa# failover exec mate copy /noconfirm ftp://calo:calo@10.88.7.12/cisco-asa-fp2k.9.16.4.SPA disk0:/cisco-asa-fp2k.9.16.4.SPA
Accessing ftp://calo :
@10.88.7.12/cisco-asa-fp2k.9.16.4.SPA...!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Verifying file disk0:/cisco-asa-fp2k.9.16.4.SPA... Writing file disk0:/cisco-asa-fp2k.9.16.4.SPA... 474475840 bytes copied in 843.230 secs (562842 bytes/sec)
步驟4.檢查您是否有使用命令設定的目前開機show running-config boot system映像。
ciscoasa(config)# show running-config boot system
boot system disk0:/cisco-asa-fp2k.9.14.4.SPA
步驟5(可選)。如果已設定開機映像,則必須將其移除。
no boot system diskn:/asa_image_name
範例:
ciscoasa(config)# no boot system disk0:/cisco-asa-fp2k.9.14.4.SPA
步驟6. 選擇要啟動的映像。
ciscoasa(config)# boot system disk0:/cisco-asa-fp2k.9.16.4.SPA
The system is currently installed with security software package 9.14.4, which has:
- The platform version: 2.8.1.172
- The CSP (asa) version: 9.14.4
Preparing new image for install...
!!!!!!!!!!!!
Image download complete (Successful unpack the image).
Installation of version 9.16.4 will do the following:
- upgrade to the new platform version 2.10.1.217
- upgrade to the CSP ASA version 9.16.4
After installation is complete, ensure to do write memory and reload to save this config and apply the new image.
Finalizing image install process...
Install_status: ready............................
Install_status: validating-images....
Install_status: upgrading-npu
Install_status: upgrading-system.
Install_status: update-software-pack-completed
步驟7.使用copy running-config startup-config 指令儲存組態。
步驟8.重新載入輔助裝置以安裝新版本。
ciscoasa(config)# failover reload-standby
等待輔助裝置載入。
步驟9.備用單元重新載入後,將主單元從活動狀態更改為備用狀態。
ciscoasa# no failover active
步驟10.重新載入新的備用裝置以安裝新版本。您必須連線到新的主用裝置。
ciscoasa(config)# failover reload-standby
載入新的備用裝置後,升級完成。
使用ASDM升級
步驟1.使用ASDM連線到輔助裝置。
步驟2. 前往 > 。
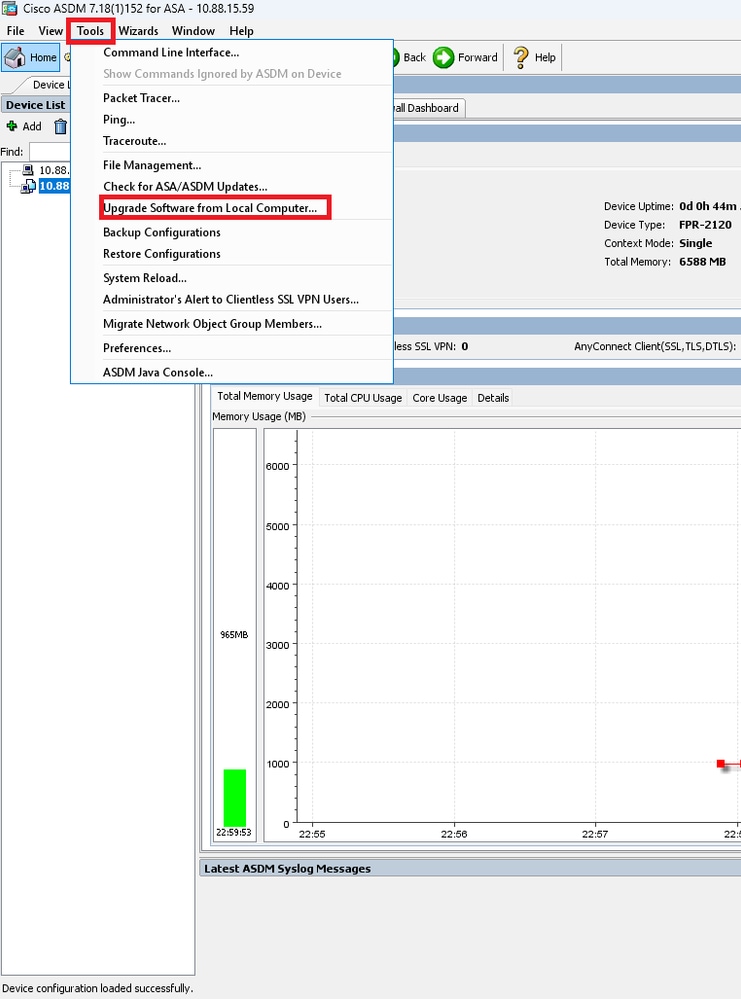
步驟3.從下拉選單中選擇ASA。

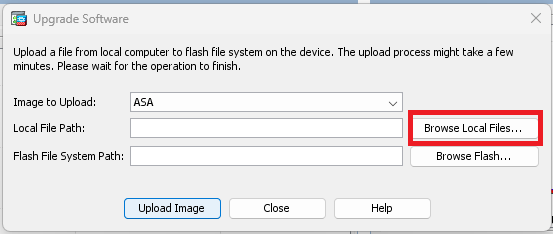
步驟4. 在Upgrade Software視窗中,按一下Browse Local Files ,將軟體映像上傳到輔助裝置。

附註:預設情況下,Flash File System Path為disk0;要更改它,請按一下Browse Flash,然後選擇新路徑。
按一下「Upload Image」。
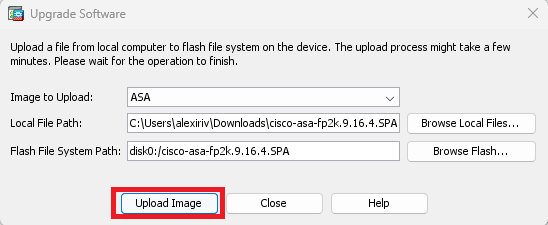
映像上傳完成後,按一下No。

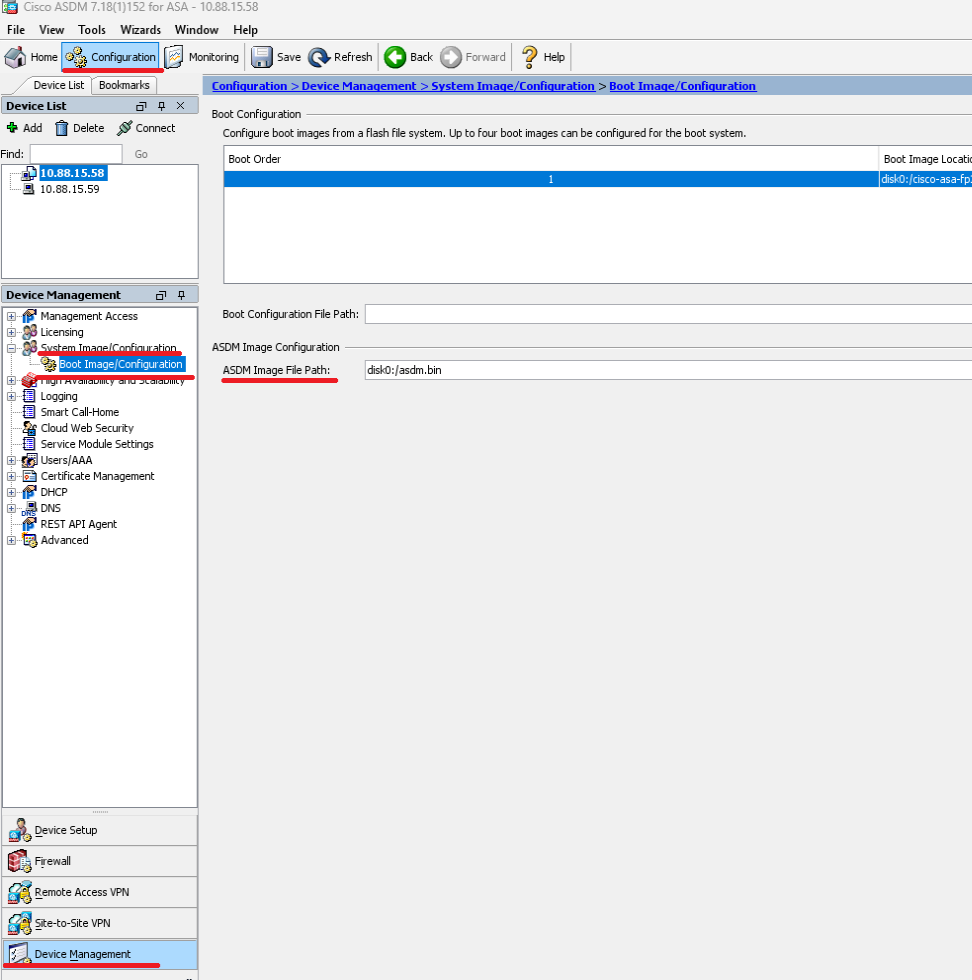
步驟5.重置ASDM映像。
使用ASDM連線到主裝置,然後轉到 > > > 。
在ASDM映像檔案路徑中,輸入disk0:/asdm.bin 和Apply值。
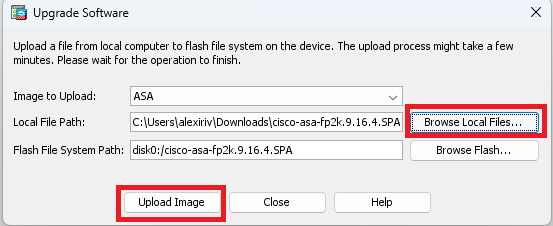
步驟6. 將軟體映像上傳到主裝置。
按一下Browse Local Files,然後選擇裝置上的升級包。
按一下「Upload Image」。
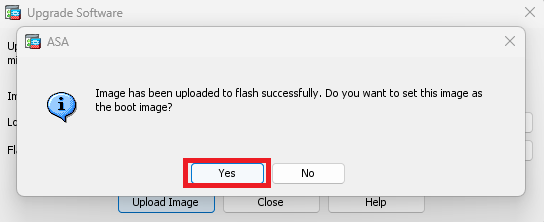
映像上傳完成後,按一下Yes。
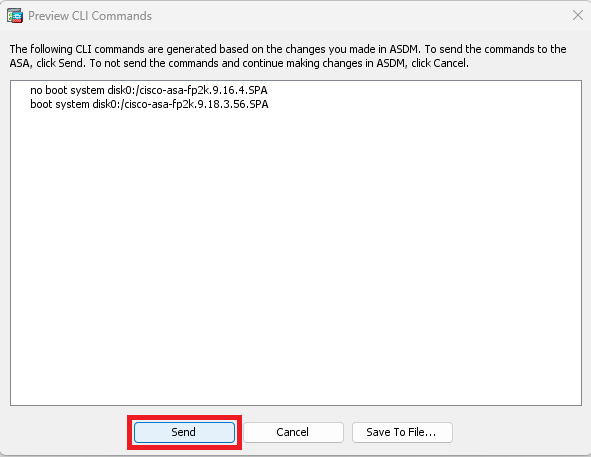
在預覽視窗中,按一下Send按鈕儲存配置。
步驟7.按一下Save以儲存組態。
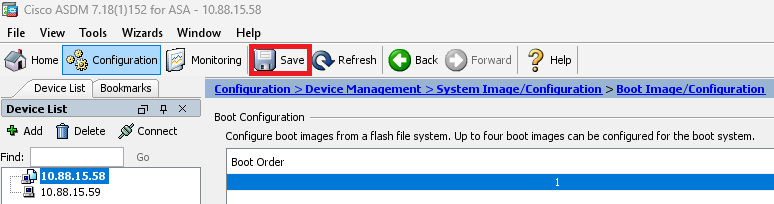
步驟8.重新載入輔助裝置以安裝新版本。
轉至Monitoring > > Status ,然後按一下。
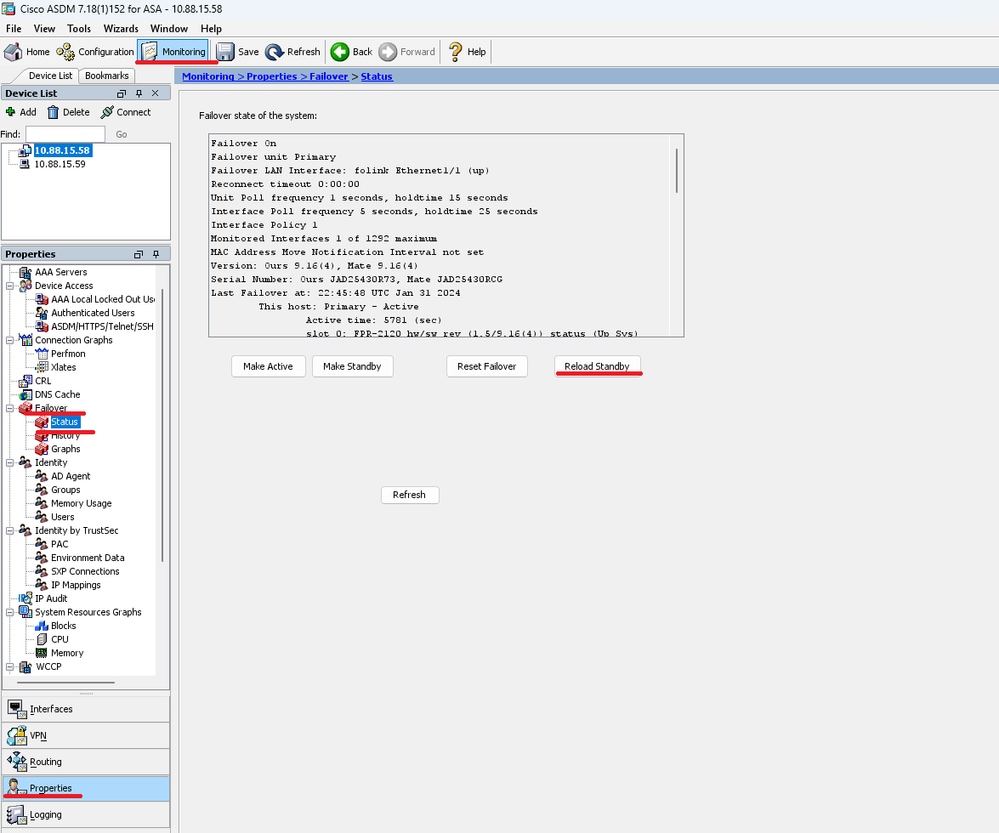
等待備用裝置載入。
步驟9.在重新載入備用單元後,將主單元從活動狀態更改為備用狀態。
轉至Monitoring > > Status ,然後按一下。
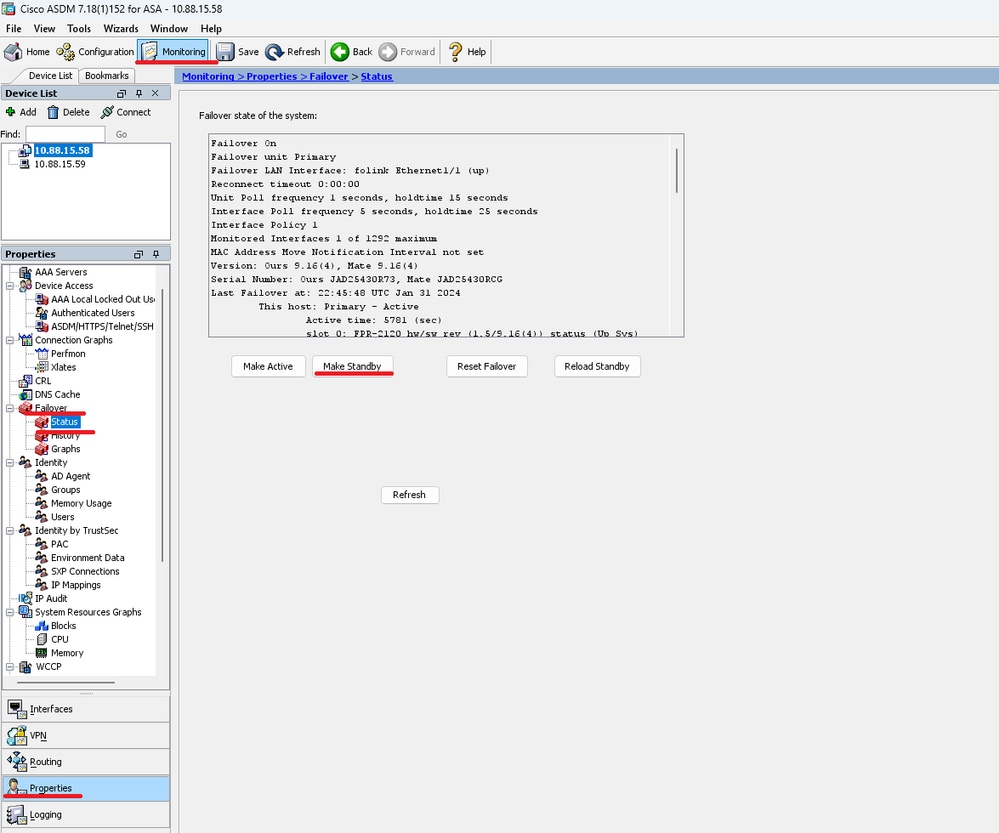
步驟10.重新載入新的備用裝置以安裝新版本。
轉至Monitoring > > Status ,然後按一下。
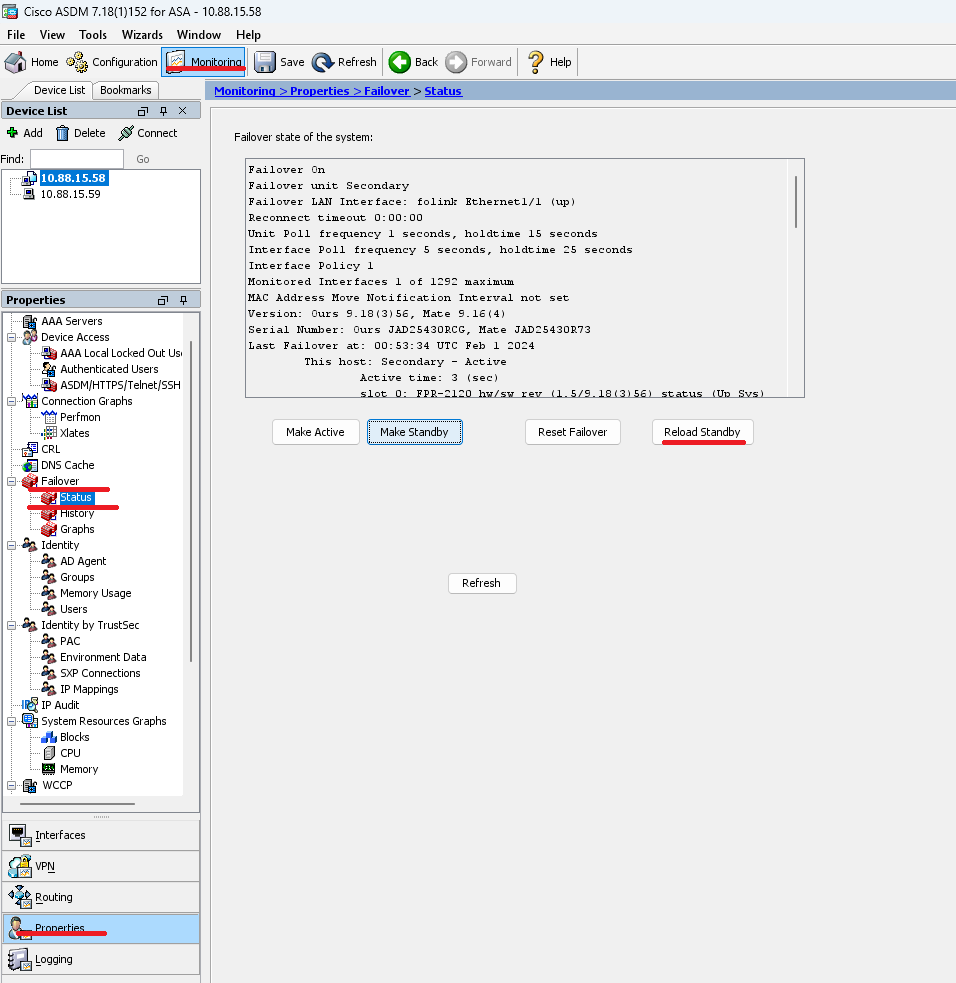
載入新的備用裝置後,升級完成。
驗證
要驗證兩台裝置是否已完成升級,請通過CLI和ASDM檢查升級。
通過CLI
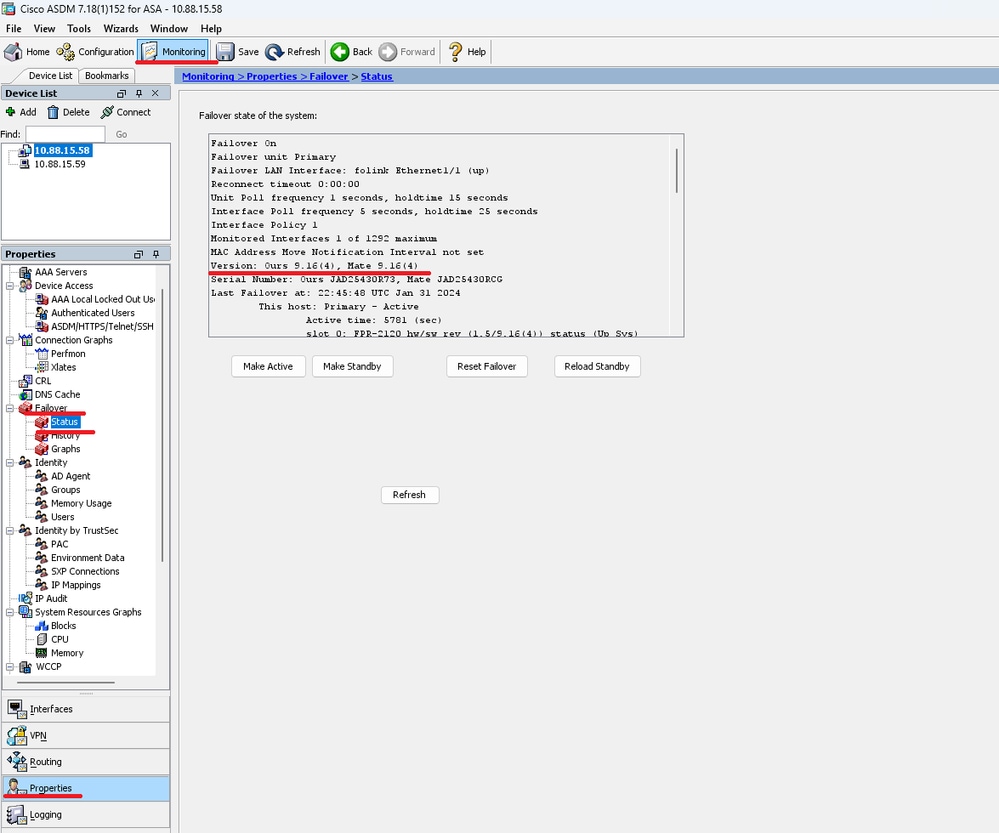
ciscoasa# show failover
Failover On
Failover unit Primary
Failover LAN Interface: folink Ethernet1/1 (up)
Reconnect timeout 0:00:00
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 1 of 1292 maximum
MAC Address Move Notification Interval not set
Version: Ours 9.16(4), Mate 9.16(4)
Serial Number: Ours JAD25430R73, Mate JAD25430RCG
Last Failover at: 22:45:48 UTC Jan 31 2024
This host: Primary - Active
Active time: 45 (sec)
slot 0: FPR-2120 hw/sw rev (1.5/9.16(4)) status (Up Sys)
Interface management (10.88.15.58): Normal (Monitored)
Other host: Secondary - Standby Ready
Active time: 909 (sec)
slot 0: FPR-2120 hw/sw rev (1.5/9.16(4)) status (Up Sys)
Interface management (10.88.15.59): Normal (Monitored)
Stateful Failover Logical Update Statistics
Link : folink Ethernet1/1 (up)
Stateful Obj xmit xerr rcv rerr
General 27 0 29 0
sys cmd 27 0 27 0
up time 0 0 0 0
RPC services 0 0 0 0
TCP conn 0 0 0 0
UDP conn 0 0 0 0
ARP tbl 0 0 1 0
Xlate_Timeout 0 0 0 0
IPv6 ND tbl 0 0 0 0
VPN IKEv1 SA 0 0 0 0
VPN IKEv1 P2 0 0 0 0
VPN IKEv2 SA 0 0 0 0
VPN IKEv2 P2 0 0 0 0
VPN CTCP upd 0 0 0 0
VPN SDI upd 0 0 0 0
VPN DHCP upd 0 0 0 0
SIP Session 0 0 0 0
SIP Tx 0 0 0 0
SIP Pinhole 0 0 0 0
Route Session 0 0 0 0
Router ID 0 0 0 0
User-Identity 0 0 1 0
CTS SGTNAME 0 0 0 0
CTS PAC 0 0 0 0
TrustSec-SXP 0 0 0 0
IPv6 Route 0 0 0 0
STS Table 0 0 0 0
Umbrella Device-ID 0 0 0 0
Logical Update Queue Information
Cur Max Total
Recv Q: 0 10 160
Xmit Q: 0 1 53
通過ASDM
轉至 > > > ,您可以看到兩台裝置的ASA版本。
相關資訊