在Catalyst 9000系列交換器上實作BGP EVPN受保護重疊分段
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
目錄
簡介
本檔案介紹如何在Catalyst 9000系列交換器上實作BGP EVPN VXLAN受保護重疊分段。
必要條件
需求
思科建議您瞭解以下主題:
- BGP EVPN VxLAN概念
- BGP EVPN單點傳播疑難排解
- BGP EVPN VxLAN路由策略
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- Catalyst 9300
- Catalyst 9400
- Catalyst 9500
- Catalyst 9600
- Cisco IOS® XE 17.12.1及更高版本
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
背景資訊
高級功能說明
受保護網段功能是一種安全措施,可防止連線埠將流量轉送到對方,即使這些連線埠位於同一個VLAN和同一交換器上
- 此功能與「switchport protected」或專用VLAN類似,但適用於EVPN交換矩陣。
- 此設計會強制所有流量傳送到CGW,然後由防火牆對其進行檢查,再將其傳送到最終目的地。
- 使用集中式安全裝置可以控制、確定且易於檢查流量。
檔案詳細資訊
本檔案是第2部分或第3部分相關檔案:
- 檔案1:在Catalyst 9000系列交換器上實作BGP EVPN路由原則涵蓋如何在重疊中控制BGP BUM流量,必須首先設定
- 檔案2:本檔案。基於文檔1的Overlay設計和策略,本文檔描述了「protected」關鍵字的實現
- 文檔3:在Catalyst 9000系列交換器上實作BGP EVPN DHCP第2層中繼介紹DHCP中繼在僅第2層VTEP上的運作方式

注意:在實施受保護分段配置之前,必須實施文檔1中的配置。
受保護段型別
完全隔離
- 僅允許從北向南通訊,
- 網關通過「default-gateway advertise」 CLI通告到交換矩陣中
大部分孤立
- 允許從北向南通訊(在此使用案例中,根據防火牆流量策略允許東/西流量流)
- 允許從東向西通訊(基於防火牆流量策略)
- 網關位於交換矩陣外部,不會使用「default-gateway advertise」 CLI通告SVI
交換機行為
- 即使主機連線到同一交換機,它們也無法直接相互通訊(當主機位於同一個VRF/Vlan/Segment中時,ARP請求不會傳送到同一交換機上的其他埠)。
- 第2層VTEP之間沒有BUM流量(使用路由策略配置過濾的IMET字首)
- 來自主機的所有資料包都會中繼到邊界枝葉以轉發。(這表示主機1要與同一枝葉上的主機2通訊,流量固定到CGW)
路由型別2處理
- 訪問枝葉使用E-Tree Extended Community和Leaf標誌集通告本地RT2。
- 訪問枝葉不會安裝資料平面中設定了E-Tree Extended Community和Leaf標誌的任何遠端RT2。
- 訪問枝葉不會相互將RT2安裝在資料平面中。
- Access Leafs和Border Leaf(CGW)將RT2彼此安裝在資料平面中。
- 無需在接入枝葉或邊界枝葉上進行配置更改。
設計摘要
- 對於廣播(BUM),RT3拓撲是中心輻射型,以便強制廣播流量(例如ARP)達到GCW。
- 為了考慮主機移動性,RT2在BGP控制平面處全網狀(當主機從一個VTEP移動到另一個VTEP時,RT2中的序列號遞增)
- 資料平面有選擇地安裝MAC地址。
- 枝葉僅安裝包含DEF GW屬性的本地MAC和RT2
- CGW沒有受保護的KW,並將所有本地MAC和遠端RT2安裝在其資料平面中。
技術
| VRF |
虛擬路由轉送 |
定義與其他VRF和全域性IPv4/IPv6路由域分離的第3層路由域 |
| AF |
地址系列 |
定義BGP處理的型別字首和路由資訊 |
| AS |
自治系統 |
一組網際網路可路由IP字首,它們屬於一個網路或一組網路,都由單個實體或組織管理、控制和監督 |
| EVPN |
乙太網路虛擬私人網路 |
允許BGP傳輸第2層MAC和第3層IP資訊的擴展是EVPN和 使用多協定邊界網關協定(MP-BGP)作為協定,以分發與VXLAN重疊網路相關的可達性資訊。 |
| VXLAN |
虛擬可擴充LAN(區域網路) |
VXLAN的用途是克服VLAN和STP的固有限制。建議採用的IETF標準[RFC 7348]提供與VLAN相同的乙太網第2層網路服務,但具有更高的靈活性。功能上,它是UDP內MAC封裝協定,在第3層底層網路上作為虛擬重疊運行。 |
| CGW |
集中式網關 |
以及網關SVI不在每個枝葉上的EVPN的實現。相反,所有路由都是由使用非對稱IRB(整合路由和橋接)的特定枝葉完成的 |
| DEF網關 |
預設閘道 |
在「l2vpn evpn」配置部分下通過命令「default-gateway advertise enable」新增到MAC/IP字首的BGP擴展社群屬性。 |
| IMET(RT3) |
包含型組播乙太網標籤(路由) |
也稱為BGP type-3路由。此路由型別在EVPN中用於在VTEP之間傳送BUM(廣播/未知單點傳播/多點傳送)流量。 |
| RT2 |
路由型別2 |
代表主機MAC或網關MAC-IP的BGP MAC或MAC/IP字首 |
| EVPN管理器 |
EVPN管理員 |
中央管理元件,用於各種其他元件(例如:從SISF和訊號到L2RIB) |
| SISF |
交換器整合式安全功能 |
EVPN使用的不可知主機跟蹤表,用於瞭解枝葉上存在哪些本地主機 |
| L2RIB |
第2層路由資訊庫 |
在用於管理BGP、EVPN管理器、L2FIB之間互動的中間元件中 |
| FED |
轉發引擎驅動程式 |
對ASIC(硬體)層程式設計 |
| MATLAB |
Mac位址表管理員 |
IOS矩陣:僅安裝本地地址的軟體表 聯邦儲備基金:硬體表,用於安裝從控制平面獲取的本地和遠端地址,並且是硬體轉發平面的一部分。(對於受保護網段,FED MATM僅安裝本地MAC和遠端MAC,其中BGP RT2包含DEF GW擴展社群標誌)。 |
流程圖
路由型別2(RT2)圖
此圖顯示第2類MAC/MAC-IP主機字首的全網狀設計。

附註:支援移動性和漫遊需要全網狀

路由型別3(RT3)圖
此圖顯示廣播IMET(RT3)隧道的集中星型設計

附註:中心輻射型廣播是必需的,這樣可以防止具有同一網段的枝葉直接互相傳送廣播。

位址解析(ARP)圖表
此圖顯示,ARP不允許到達同一EPVN網段中的任何主機。當另一台主機的主機ARP時,只有CGW獲取此ARP並回覆


附註:此ARP行為更改通過使用「protected」關鍵字進行例項化。
範例:成員evpn例項202 vni 20201 protected
配置(完全隔離)
網路圖表
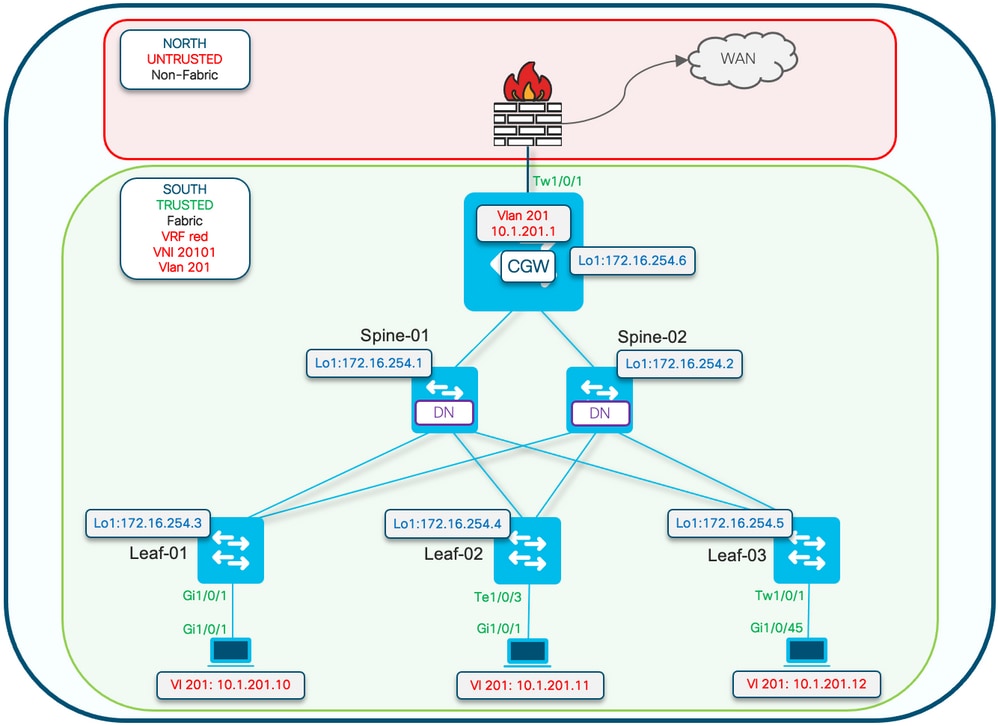
受保護配置關鍵字應用於枝葉交換機。CGW是一個混雜裝置,會安裝所有mac地址。

附註:在Catalyst 9000系列交換器上實作BGP EVPN路由原則中顯示了控制匯入/匯出IMET首碼的路由原則社群清單和路由對映組態。本檔案只顯示受保護區段的差異。
Leaf-01(基本EVPN配置)
Leaf-01#show run | sec l2vpn
l2vpn evpn
replication-type static
flooding-suppression address-resolution disable <-- Disables ARP caching so ARP is always sent up to the CGW
router-id Loopback1
l2vpn evpn instance 201 vlan-based encapsulation vxlan replication-type ingress <-- Sets segment to use Unicast replication of BUM traffic via RT3 type BGP routes multicast advertise enable
Leaf01#show run | sec vlan config vlan configuration 201 member evpn-instance 201 vni 20101 protected <-- protected keyword added
CGW(基本配置)
CGW#show running-config | beg l2vpn evpn instance 201 l2vpn evpn instance 201 vlan-based encapsulation vxlan replication-type ingress default-gateway advertise enable <-- adds the BGP attribute EVPN DEF GW:0:0 to the MAC/IP prefix multicast advertise enable
CGW#show running-config | sec vlan config vlan configuration 201
member evpn-instance 201 vni 20101
CGW#show run int nve 1 Building configuration... Current configuration : 313 bytes ! interface nve1 no ip address source-interface Loopback1 host-reachability protocol bgp
member vni 20101 ingress-replication local-routing <-- 'ingress-replication' (Unicast all BUM traffic) / 'local-routing' (Enables vxlan centralized gateway forwarding)
CGW#show run interface vlan 201 Building configuration... Current configuration : 231 bytes ! interface Vlan201 mac-address 0000.beef.cafe <-- MAC is static in this example for viewing simplicity. This is not required vrf forwarding red <-- SVI is in VRF red ip address 10.1.201.1 255.255.255.0 no ip redirects ip local-proxy-arp <-- Sets CGW to Proxy reply even for local subnet ARP requests ip pim sparse-mode ip route-cache same-interface <-- This is auto added when local-proxy-arp is configured. However, this is a legacy 'fast switching' command that is not used by CEF & is not required for forwarding ip igmp version 3 no autostate

附註:在CGW沒有應用BGP策略。允許CGW接收和傳送所有字首型別(RT2、RT5 / RT3)。
驗證(完全隔離)
EVI詳細資訊
Leaf01#sh l2vpn evpn evi 201 detail
EVPN instance: 201 (VLAN Based)
RD: 172.16.254.3:201 (auto)
Import-RTs: 65001:201
Export-RTs: 65001:201
Per-EVI Label: none
State: Established
Replication Type: Ingress
Encapsulation: vxlan
IP Local Learn: Enabled (global)
Adv. Def. Gateway: Disabled (global)
Re-originate RT5: Disabled
Adv. Multicast: Enabled
AR Flood Suppress: Disabled (global)
Vlan: 201
Protected: True (local access p2p blocked) <-- Vlan 201 is in protected mode
<...snip...>
本地RT2生成(本地主機到RT2)
驗證從本地主機學習到RT2生成的元件依賴鏈:
- SISF(雖然枝葉沒有SVI,但SISF仍通過主機的ARP幀來收集主機資訊)
- EVPN管理器
- L2RIB
- BGP

提示:如果前一元件未正確程式設計,則整個從屬鏈會斷開(例如:SISF沒有en條目,則BGP無法建立RT2)。
SISF
驗證SISF是否已在資料庫中獲取主機(從DHCP或ARP獲取主機資訊)
- SISF從IOS-MATM learning獲取MAC條目,然後傳送到EVPN管理器(必須使用策略「evpn-sisf-policy」實現MAC可訪問)。
- SISF在本地VTEP上收集IP/MAC繫結,並使用EVPN管理器將資訊程式設計為通過BGP到其他枝葉的/32路由。

附註:在此案例中,主機具有靜態IP,因此SISF使用ARP來收集主機詳細資訊。在「Most Isolated(大部分隔離)」部分中顯示DHCP和DHCP監聽。
Leaf01#show device-tracking database vlanid 201
vlanDB has 1 entries for vlan 201, 1 dynamic
Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created
Preflevel flags (prlvl):
0001:MAC and LLA match 0002:Orig trunk 0004:Orig access
0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned
0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
ARP 10.1.201.10 0006.f601.cd43 Gi1/0/1 201 0005 3mn REACHABLE 86 s <-- Gleaned from local host ARP Request
EVPN管理員
EVPN 經理 學習本地MAC並安裝到L2RIB中。EVPN 經理 也從L2RIB學習遠端MAC,但條目僅用於處理MAC移動性
確認已使用SISF條目更新EVPN管理器
Leaf01#show l2vpn evpn mac evi 201 MAC Address EVI VLAN ESI Ether Tag Next Hop(s) -------------- ----- ----- ------------------------ ---------- --------------- 0006.f601.cd43 201 201 0000.0000.0000.0000.0000 0 Gi1/0/1:201 <-- MAC in VLan 201 local interface Gi1/0/1:service instance 201 <...snip...>
L2RIB
- L2RIB從EVPN管理器獲取本地MAC並傳送到BGP和L2FIB。
- L2RIB還負責從BGP學習遠端MAC以更新EVPN管理器和L2FIB。
- L2RIB需要「本地」和「遠端」兩者才能正確更新其他組件。
- L2RIB元件位於本地和遠端MAC學習之間,具體取決於需要更新的方向/元件
驗證是否從EVPN管理器使用本地MAC更新了L2RIB
Leaf01#show l2route evpn mac topology 201 <-- View the overall topology for this segment EVI ETag Prod Mac Address Next Hop(s) Seq Number ----- ---------- ----- -------------- ---------------------------------------------------- ---------- 201 0 BGP 0000.beef.cafe V:20101 172.16.254.6 0 <-- produced by BGP who updated L2RIB (remote learn) 201 0 L2VPN 0006.f601.cd43 Gi1/0/1:201 0 <-- produced by EVPN Mgr who updated L2RIB (local learn) Leaf01#show l2route evpn mac mac-address 0006.f601.cd43 detail EVPN Instance: 201 Ethernet Tag: 0 Producer Name: L2VPN <-- Produced by local MAC Address: 0006.f601.cd43 <-- Host MAC Address Num of MAC IP Route(s): 1 Sequence Number: 0 ESI: 0000.0000.0000.0000.0000 Flags: B() Next Hop(s): Gi1/0/1:201 (E-LEAF) <-- Port:Instance and info about the Role (Leaf)
BGP
驗證BGP是否由L2RIB更新
Leaf01#show bgp l2vpn evpn route-type 2 0 0006.f601.cd43 *
BGP routing table entry for [2][172.16.254.3:201][0][48][0006F601CD43][0][*]/20, version 268232
Paths: (1 available, best #1, table evi_201) <-- In the totally isolated evi context
Advertised to update-groups:
2
Refresh Epoch 1
Local
0.0.0.0 (via default) from 0.0.0.0 (172.16.255.3) <-- from 0.0.0.0 indicates local
Origin incomplete, localpref 100, weight 32768, valid, sourced, local, best <-- also indicates local
EVPN ESI: 00000000000000000000, Label1 20101
Extended Community: RT:65001:201 ENCAP:8 EVPN E-Tree:flag:1,label:0 <-- EVPN e-Tree attribute with Leaf flag = 1 (added to indicate this is a host address)
Local irb vxlan vtep:
vrf:not found, l3-vni:0
local router mac:0000.0000.0000
core-irb interface:(not found)
vtep-ip:172.16.254.3 <-- Local VTEP Loopback
rx pathid: 0, tx pathid: 0x0
Updated on Sep 14 2023 20:16:17 UTC
遠端RT2學習(預設網關RT2)
BGP
驗證BGP是否已得知CGW RT2字首
Leaf01#show bgp l2vpn evpn route-type 2 0 0000.beef.cafe 10.1.201.1
BGP routing table entry for [2][172.16.254.3:201][0][48][0000BEEFCAFE][32][10.1.201.1]/24, version 114114
Paths: (1 available, best #1, table evi_201) <-- EVI context is 201
Flag: 0x100
Not advertised to any peer
Refresh Epoch 2
Local, imported path from [2][172.16.254.6:201][0][48][0000BEEFCAFE][32][10.1.201.1]/24 (global)
172.16.254.6 (metric 3) (via default) from 172.16.255.1 (172.16.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 20101 <-- Correct segment identifier
Extended Community: RT:65001:201 ENCAP:8 EVPN DEF GW:0:0 <-- Default gateway attribute is added via the 'default gateway advertise CLI'
Originator: 172.16.255.6, Cluster list: 172.16.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Sep 1 2023 15:27:45 UTC
L2RIB
驗證BGP已更新L2RIB
- L2RIB從EVPN管理器獲取本地MAC並傳送到BGP和L2FIB。L2RIB還負責從BGP學習遠端MAC以更新EVPN管理器和L2FIB。
- L2RIB需要「本地」和「遠端」兩者才能正確更新其他組件。
- L2RIB元件位於本地和遠端MAC學習之間,具體取決於需要更新的方向和元件。
Leaf01#show l2route evpn default-gateway host-ip 10.1.201.1 EVI ETag Prod Mac Address Host IP Next Hop(s) ----- ---------- ----- -------------- --------------------------------------- -------------------------------------------------- 201 0 BGP 0000.beef.cafe 10.1.201.1 V:20101 172.16.254.6 <-- L2RIB has the MAC-IP of the Gateway programmed
L2FIB
在L2FIB中驗證
- 負責使用MAC更新FED以在硬體中程式設計的元件。
- 由L2FIB安裝到FED-MATM的遠端MAC條目不會推入IOS-MATM。(IOS-MATM僅顯示本地MAC,而FED-MATM同時顯示本地和遠端MAC)
- L2FIB輸出僅顯示遠端MAC(它不負責對本地MAC進行程式設計)。
Leaf01#show l2fib bridge-domain 201 address unicast 0000.beef.cafe MAC Address : 0000.beef.cafe <-- CGW MAC Reference Count : 1 Epoch : 0 Producer : BGP <-- Learned from BGP Flags : Static Adjacency : VXLAN_UC PL:2973(1) T:VXLAN_UC [MAC]20101:172.16.254.6 <-- CGW Loopback IP PD Adjacency : VXLAN_UC PL:2973(1) T:VXLAN_UC [MAC]20101:172.16.254.6 Packets : 6979 Bytes : 0
FED
在FED MATM驗證
- 在配置了「protected keyword」的枝葉的硬體級別,您應該只看到CGW預設網關MAC和本地主機MAC。
- 交換機檢視DEF GW屬性的RT2字首,以確定哪些遠端MAC適合安裝。
Leaf01#show platform software fed switch active matm macTable vlan 201
VLAN MAC Type Seq# EC_Bi Flags machandle siHandle riHandle diHandle *a_time *e_time ports Con ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ 201 0000.beef.cafe 0x5000001 0 0 64 0x7a199d182498 0x7a199d183578 0x71e059173e08 0x0 0 82 VTEP 172.16.254.6 adj_id 9 No
<-- Only remote MAC installed in Fed is the Default Gateway (0x5000001 type) Conn = No (meaning not directly connected) 201 0006.f601.cd01 0x1 2458 0 0 0x7a199d1a2248 0x7a199d19eef8 0x0 0x7a199c6f7cd8 300 2 GigabitEthernet1/0/1 Yes 201 0006.f601.cd43 0x1 8131 0 0 0x7a199d195a98 0x7a199d19eef8 0x0 0x7a199c6f7cd8 300 84 GigabitEthernet1/0/1
<-- Two local MAC addresses (0x1 type) Conn = Yes (directly connected)
Total Mac number of addresses:: 5 Summary: Total number of secure addresses:: 0 Total number of drop addresses:: 0 Total number of lisp local addresses:: 0 Total number of lisp remote addresses:: 3 *a_time=aging_time(secs) *e_time=total_elapsed_time(secs) Type: MAT_DYNAMIC_ADDR 0x1 MAT_STATIC_ADDR 0x2 MAT_CPU_ADDR 0x4 MAT_DISCARD_ADDR 0x8 MAT_ALL_VLANS 0x10 MAT_NO_FORWARD 0x20 MAT_IPMULT_ADDR 0x40 MAT_RESYNC 0x80 MAT_DO_NOT_AGE 0x100 MAT_SECURE_ADDR 0x200 MAT_NO_PORT 0x400 MAT_DROP_ADDR 0x800 MAT_DUP_ADDR 0x1000 MAT_NULL_DESTINATION 0x2000 MAT_DOT1X_ADDR 0x4000 MAT_ROUTER_ADDR 0x8000 MAT_WIRELESS_ADDR 0x10000 MAT_SECURE_CFG_ADDR 0x20000 MAT_OPQ_DATA_PRESENT 0x40000 MAT_WIRED_TUNNEL_ADDR 0x80000 MAT_DLR_ADDR 0x100000 MAT_MRP_ADDR 0x200000 MAT_MSRP_ADDR 0x400000 MAT_LISP_LOCAL_ADDR 0x800000 MAT_LISP_REMOTE_ADDR 0x1000000 MAT_VPLS_ADDR 0x2000000 MAT_LISP_GW_ADDR 0x4000000
<-- the addition of these values = 0x5000001
MAT_LISP_REMOTE_ADDR 0x1000000
MAT_LISP_GW_ADDR 0x4000000
MAT_DYNAMIC_ADDR 0x1
資料平面鄰接
確認FED專案後的最後一個步驟是您可以解析重寫索引(RI)
Leaf01#sh platform hardware fed switch active fwd-asic abstraction print-resource-handle 0x71e059173e08 0
<-- 0x71e059173e08 is taken from previous FED command riHandle for the CGW MAC Handle:0x71e059173e08 Res-Type:ASIC_RSC_RI Res-Switch-Num:255 Asic-Num:255 Feature-ID:AL_FID_L2_WIRELESS Lkp-ftr-id:LKP_FEAT_INVALID ref_count:1 priv_ri/priv_si Handle: 0x71e05917b8d8Hardware Indices/Handles: index0:0x38 mtu_index/l3u_ri_index0:0x0 index1:0x38 mtu_index/l3u_ri_index1:0x0 Features sharing this resource:58 (1)] Brief Resource Information (ASIC_INSTANCE# 0) ---------------------------------------- ASIC#:0 RI:56 Rewrite_type:AL_RRM_REWRITE_LVX_IPV4_L2_PAYLOAD_ENCAP_EPG(116) Mapped_rii:LVX_L3_ENCAP_L2_PAYLOAD_EPG(137) Src IP: 172.16.254.3 <-- source tunnel IP Dst IP: 172.16.254.6 <-- dest tunnel IP iVxlan dstMac: 0x9db:0x00:0x00 iVxlan srcMac: 0x00:0x00:0x00 IPv4 TTL: 0 iid present: 0 lisp iid: 20101 <-- Segment 20101 lisp flags: 0 dst Port: 4789 <-- VxLAN update only l3if: 0 is Sgt: 0 is TTL Prop: 0 L3if LE: 53 (0) Port LE: 281 (0) Vlan LE: 8 (0)

附註:您也可以使用「show platform software fed switch active matm macTable vlan 201 detail」,該命令與FED命令一起連結為一個結果
配置(部分隔離)
網路圖表
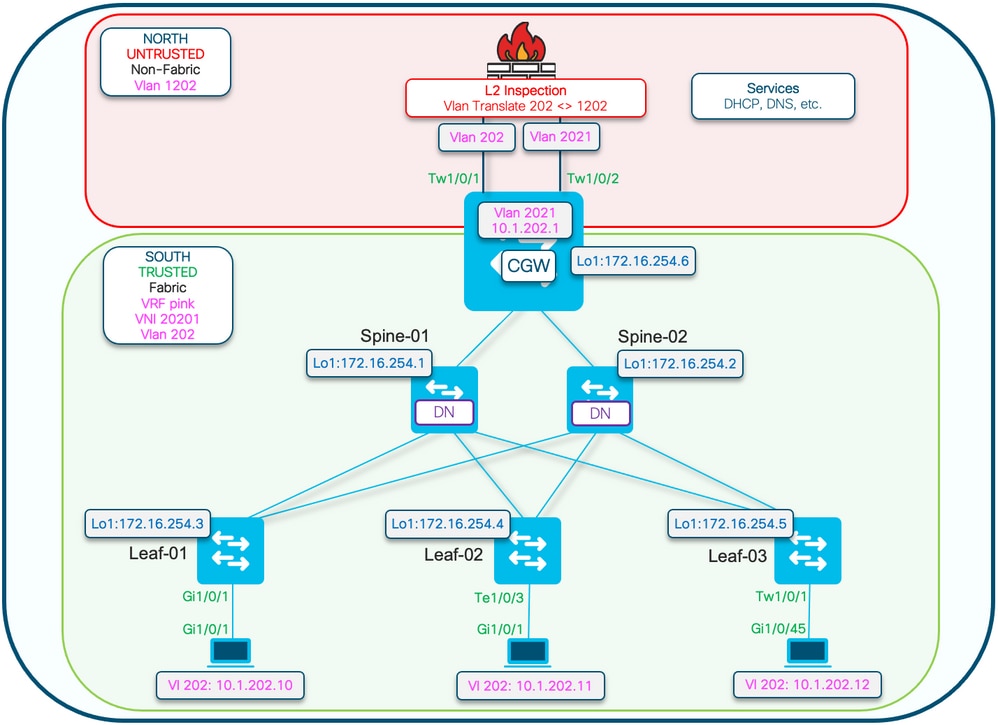


附註:本節僅介紹與完全隔離網段的區別。
- 使用DEF GW屬性標籤GCW網關MAC IP的路由策略
- 需要自定義裝置跟蹤策略來防止MAC擺動
- GW MAC IP的靜態裝置跟蹤繫結
Leaf-01(基本EVPN配置)
Leaf-01#show run | sec l2vpn
l2vpn evpn
replication-type static
flooding-suppression address-resolution disable <-- Disables ARP caching so ARP is always sent up to the CGW
router-id Loopback1 l2vpn evpn instance 202 vlan-based encapsulation vxlan replication-type ingress multicast advertise enable
Leaf01#show run | sec vlan config vlan configuration 202 member evpn-instance 202 vni 20201 protected <-- protected keyword added
CGW(基本配置)
在nve下設定複製模式
CGW#show run int nve 1 Building configuration... Current configuration : 313 bytes ! interface nve1 no ip address source-interface Loopback1 host-reachability protocol bgp member vni 20201 ingress-replication local-routing <-- 'ingress-replication' (Unicast all BUM traffic) / 'local-routing' (Enables vxlan centralized gateway forwarding) end
配置外部網關SVI
CGW#show run interface vlan 2021 Building configuration... Current configuration : 231 bytes ! interface Vlan2021 mac-address 0000.beef.cafe <-- MAC is static in this example for viewing simplicity. This is not required vrf forwarding pink <-- SVI is in VRF pink ip address 10.1.202.1 255.255.255.0 no ip redirects ip local-proxy-arp <-- Sets CGW to Proxy reply even for local subnet ARP requests ip pim sparse-mode ip route-cache same-interface <-- This is auto added when local-proxy-arp is configured. However, this is a legacy 'fast switching' command that is not used by CEF & is not required for forwarding ip igmp version 3 no autostate end
建立禁用蒐集功能的策略
device-tracking policy dt-no-glean <-- Configure device tracking policy to prevent MAC-IP flapping security-level glean no protocol ndp no protocol dhcp6 no protocol arp no protocol dhcp4
連線到externalgatewayevi/vlan
CGW#show running-config | sec vlan config vlan configuration 202 member evpn-instance 202 vni 20201
device-tracking attach-policy dt-no-glean <-- apply the new device tracking policy to the vlan configuration
將靜態條目新增到外部網關mac-ip的裝置跟蹤表
device-tracking binding vlan 202 10.1.202.1 interface TwentyFiveGigE1/0/1 0000.beef.cafe
<-- All static entries in device tracking table should be for external gateway mac-ip’s.
If there is any other static entry in device tracking table, match ip/ipv6 configurations in route map with prefix lists (permit/deny) are required to attach default gateway extended community to external gateway mac-ip routes only.
建立BGP路由對映以匹配RT2 MAC-IP字首並設定預設網關擴展社群
route-map CGW_DEF_GW permit 10
match evpn route-type 2-mac-ip <-- match RT2 type MAC-IP
set extcommunity default-gw <-- Set Default-gateway (DEF GW 0:0) extended community
route-map CGW_DEF_GW permit 20
將route-map應用於BGP路由反射器鄰居
CGW#sh run | s r bgp
address-family l2vpn evpn
neighbor 172.16.255.1 activate
neighbor 172.16.255.1 send-community both
neighbor 172.16.255.1 route-map CGW_DEF_GW out <-- Sets the DEF GW Community when it advertises MAC-IP type RT2 to the RR
neighbor 172.16.255.2 activate
neighbor 172.16.255.2 send-community both
neighbor 172.16.255.2 route-map CGW_DEF_GW out <-- Sets the DEF GW Community when it advertises MAC-IP type RT2 to the RR
驗證(部分隔離)
EVI詳細資訊
Leaf01#show l2vpn evpn evi 202 detail
EVPN instance: 202 (VLAN Based)
RD: 172.16.254.3:202 (auto)
Import-RTs: 65001:202
Export-RTs: 65001:202
Per-EVI Label: none
State: Established
Replication Type: Ingress
Encapsulation: vxlan
IP Local Learn: Enabled (global)
Adv. Def. Gateway: Enabled (global)
Re-originate RT5: Disabled
Adv. Multicast: Enabled
Vlan: 202
Protected: True (local access p2p blocked) <-- Vlan 202 is in protected mode
<...snip...>
本地RT2生成(本地主機到RT2)
在上一完全隔離的示例中介紹
遠端RT2學習(預設網關RT2)
覆蓋與完全隔離的區別
CGW預設網關字首(枝葉)
檢查字首是否具有適當的屬性,以便有資格安裝到硬體中

附註:這對於DHCP L2中繼正常運行至關重要
Leaf01#show bgp l2vpn evpn route-type 2 0 0000.beef.cafe 10.1.202.1
BGP routing table entry for [2][172.16.254.3:202][0][48][0000BEEFCAFE][32][10.1.202.1]/24, version 184602
Paths: (1 available, best #1, table evi_202) <-- the EVI context of 202 which matches the Vlan/EVI we are concerned about
Not advertised to any peer
Refresh Epoch 2
Local, imported path from [2][172.16.254.6:202][0][48][0000BEEFCAFE][32][10.1.202.1]/24 (global)
172.16.254.6 (metric 3) (via default) from 172.16.255.1 (172.16.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 20201 <-- Correct Segment ID
Extended Community: RT:65001:202 ENCAP:8 EVPN DEF GW:0:0 <-- prefix has the Default GW attribute added
Originator: 172.16.255.6, Cluster list: 172.16.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Sep 7 2023 19:56:43 UTC
FED MATM(分葉)
F241.03.23-9300-Leaf01#show platform software fed active matm macTable vlan 202 mac 0000.beef.cafe VLAN MAC Type Seq# EC_Bi Flags machandle siHandle riHandle diHandle *a_time *e_time ports Con ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ 202 0000.beef.cafe 0x5000001 0 0 64 0x71e058da7858 0x71e05916c0d8 0x71e059171678 0x0 0 5 VTEP 172.16.254.6 adj_id 651 No
<-- MAC of Default GW is installed in FED
SISF(CGW)
CGW#sh device-tracking database vlanid 202
vlanDB has 1 entries for vlan 202, 0 dynamic
Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created
Preflevel flags (prlvl):
0001:MAC and LLA match 0002:Orig trunk 0004:Orig access
0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned
0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
S 10.1.202.1 0000.beef.cafe Twe1/0/1 202 0100 13006mn STALE N/A
IOS模組(CGW)
CGW#show mac address-table address 0000.beef.cafe
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
201 0000.beef.cafe STATIC Vl201
2021 0000.beef.cafe STATIC Vl2021 <-- The Vlan 2021 SVI MAC advertised out Tw1/0/1
202 0000.beef.cafe DYNAMIC Twe1/0/1 <-- The Vlan 2021 SVI MAC learned dynamically after passing through the Firewall and the Dot1q tag swapped to fabric Vlan 202
疑難排解
位址解析(ARP)
隔離ARP問題的常規步驟
- 確認IMET隧道已準備就緒
- 在CGW上行鏈路上進行捕獲,以驗證從枝葉封裝的ARP已接收
- 如果沒有ARP出現在上行鏈路上,
- 驗證枝葉和CGW上的IMET隧道是否已就緒。
- 在枝葉上行鏈路上進行捕獲,以確認ARP已封裝並傳送。
- 排除中間路徑故障。
- 如果ARP到達邊界IMET隧道捕獲,但未在VRF ARP表中程式設計。
- 排除CPU/CoPP突發路徑故障,確認向CPU傳送的ARP。
- 確認IP地址/客戶端資訊是否正確。
- 在VRF中調試ARP以檢視可能影響ARP進程的內容
- 驗證主機上作為下一跳/目標mac安裝的CGW MAC
- 確認CGW具有包含實際主機MAC的兩個ARP條目
- 驗證防火牆策略是否允許此類流量

注意:啟用debug時要小心!
確保您已禁用泛洪抑制
Leaf-01#show run | sec l2vpn
l2vpn evpn
replication-type static
flooding-suppression address-resolution disable <-- This CLI prevents a VTEP from trying to unicast other VTEPs based on its EVPN table
當Leaf-02的主機為Leaf-01的主機解析ARP時,ARP請求不會直接廣播到Leaf-01
- 相反,ARP會向上傳遞在Leaf-02上程式設計的唯一通向CGW的BUM隧道
- CGW不會將此資訊轉發到Leaf-01,而是使用自己的MAC進行回覆
- 這會導致所有通訊都向上傳遞到CGW,然後路由到主機之間
- CGW會路由資料包,即使它們位於同一個本地子網上
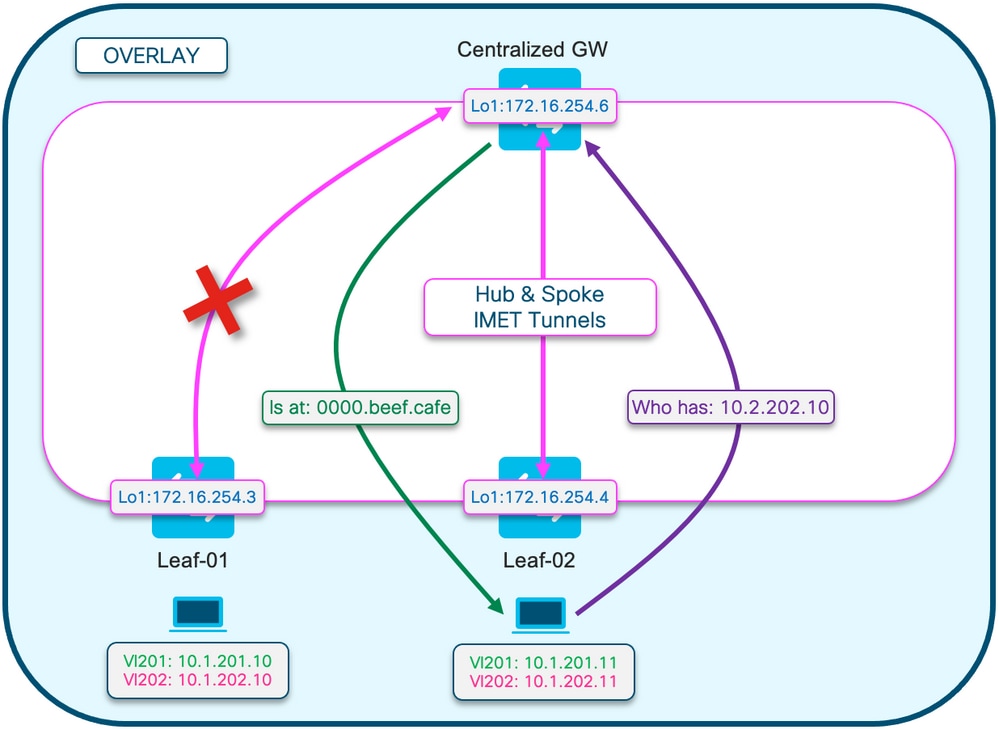
此圖有助於直觀顯示本節所述的ARP解析過程。
ARP請求顯示為紫色
- 此ARP請求用於解析主機10.1.202.10 Leaf-01的MAC地址
- 請注意,紫色線在CGW終止,並且未到達枝葉01
ARP應答顯示為綠色
- 回覆包含用於Vlan 202的CGW SVI的MAC
- 請注意,綠線來自CGW,而不是來自實際主機

附註:紅色X表示此通訊不涉及向枝葉01傳送流量。
觀察每台相應主機上的ARP條目
Leaf02-HOST#sh ip arp 10.1.202.10 Protocol Address Age (min) Hardware Addr Type Interface Internet 10.1.202.10 1 0000.beef.cafe ARPA Vlan202 <-- MAC address for Leaf01 host is CGW MAC Leaf01-HOST#sh ip arp 10.1.202.11 Protocol Address Age (min) Hardware Addr Type Interface Internet 10.1.202.11 7 0000.beef.cafe ARPA Vlan202 <-- MAC address for Leaf02 host is CGW MAC
觀察在CGW上學習了RT2字首。CGW路由資料包時需要此步驟
CGW#sh bgp l2vpn evpn route-type 2 0 0006.f617.eec4 * <-- Leaf02 actual MAC
BGP routing table entry for [2][172.16.254.6:202][0][48][0006F617EEC4][0][*]/20, version 235458
Paths: (1 available, best #1, table evi_202)
Not advertised to any peer
Refresh Epoch 2
Local, imported path from [2][172.16.254.4:202][0][48][0006F617EEC4][0][*]/20 (global)
172.16.254.4 (metric 3) (via default) from 172.16.255.1 (172.16.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 20201 <-- correct segment identifier
Extended Community: RT:65001:202 ENCAP:8 EVPN E-Tree:flag:1,label:0 <-- prefix contains the Leaf flag indicating this is a normal host
Originator: 172.16.255.4, Cluster list: 172.16.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Apr 9 2025 17:11:22 UTC
CGW#sh bgp l2vpn evpn route-type 2 0 0006.f601.cd44 * <-- Leaf01 actual MAC
BGP routing table entry for [2][172.16.254.6:202][0][48][0006F601CD44][0][*]/20, version 235521
Paths: (1 available, best #1, table evi_202)
Not advertised to any peer
Refresh Epoch 2
Local, imported path from [2][172.16.254.3:202][0][48][0006F601CD44][0][*]/20 (global)
172.16.254.3 (metric 3) (via default) from 172.16.255.1 (172.16.255.1)
Origin incomplete, metric 0, localpref 100, valid, internal, best
EVPN ESI: 00000000000000000000, Label1 20201 <-- correct segment identifier
Extended Community: RT:65001:202 ENCAP:8 EVPN E-Tree:flag:1,label:0 <-- prefix contains the Leaf flag indicating this is a normal host
Originator: 172.16.255.3, Cluster list: 172.16.255.1
rx pathid: 0, tx pathid: 0x0
Updated on Apr 9 2025 17:17:06 UTC
捕獲上行鏈路上的ARP交換以確認雙向通訊
- 您可以在交換矩陣上行鏈路上使用嵌入式資料包捕獲(EPC)
- 此方案顯示Leaf01上行鏈路上的EPC。如有必要,在CGW上重複此相同過程
配置EPC
Leaf01#monitor capture 1 interface range te 1/1/2 , te 1/1/4 both match any buffer size 100 <-- both Uplinks toward fabric included
啟動捕獲
Leaf01#monitor capture 1 start
啟動ping以觸發ARP請求(在這種情況下,ping是從Leaf01主機10.1.201.10到Leaf02主機10.1.201.11)
Leaf01-HOST#ping vrf red 10.1.201.11
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.201.11, timeout is 2 seconds:
...!!
Success rate is 40 percent (2/5), round-trip min/avg/max = 1/1/1 ms
停止ARP幀的捕獲和檢查
Leaf01#mon cap 1 stop
F241.03.23-9300-Leaf01#show mon cap 1 buff br | i ARP
11 8.153510 00:06:f6:01:cd:42 -> ff:ff:ff:ff:ff:ff ARP 110 Who has 10.1.201.11? Tell 10.1.201.10 <-- .10 requests .11 MAC (this is Frame 11)
12 8.154030 00:00:be:ef:ca:fe -> 00:06:f6:01:cd:42 ARP 110 10.1.201.11 is at 00:00:be:ef:ca:fe <-- CGW replies with its MAC
詳細檢視捕獲資料包。如果您想檢視有關資料包的更多資訊,請使用EPC的detail選項
- 請注意,為了簡潔,此輸出被剪裁到不同位置
Leaf01#show mon cap 1 buffer detailed | beg Frame 11 <-- begin detail result from Frame 11 (ARP Request)
Frame 11: 110 bytes on wire (880 bits), 110 bytes captured (880 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0
Ethernet II, Src: 00:00:00:00:00:00 (00:00:00:00:00:00), Dst: 00:00:00:00:00:00 (00:00:00:00:00:00) <-- Expected to see all zeros for outbound VxLAN encapped packet
Destination: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 00:00:00:00:00:00 (00:00:00:00:00:00)
Address: 00:00:00:00:00:00 (00:00:00:00:00:00)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 172.16.254.3, Dst: 172.16.254.6 <--- Outer tunnel IP header
Source: 172.16.254.3
Destination: 172.16.254.6
User Datagram Protocol, Src Port: 65483, Dst Port: 4789 <-- VXLAN Dest port
Virtual eXtensible Local Area Network
VXLAN Network Identifier (VNI): 20101 <-- Verify the VNI for the segment you are investigating
Reserved: 0
Ethernet II, Src: 00:06:f6:01:cd:42 (00:06:f6:01:cd:42), Dst: ff:ff:ff:ff:ff:ff (ff:ff:ff:ff:ff:ff) <-- Start of inner payload info
Type: ARP (0x0806)
Trailer: 000000000000000000000000000000000000
Address Resolution Protocol (request) <-- is an ARP request
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: 00:06:f6:01:cd:42 (00:06:f6:01:cd:42) <-- Sending host
Sender IP address: 10.1.201.10
Target MAC address: 00:00:00:00:00:00 (00:00:00:00:00:00) <-- Trying to resolve MAC for host
Target IP address: 10.1.201.11
Frame 12: 110 bytes on wire (880 bits), 110 bytes captured (880 bits) on interface /tmp/epc_ws/wif_to_ts_pipe, id 0 <-- ARP reply
Ethernet II, Src: dc:77:4c:8a:6d:7f (dc:77:4c:8a:6d:7f), Dst: 68:2c:7b:f8:87:48 (68:2c:7b:f8:87:48) <-- Underlay MACs
Internet Protocol Version 4, Src: 172.16.254.6, Dst: 172.16.254.3 <-- From CGW loopback to Leaf01 loopback
User Datagram Protocol, Src Port: 65410, Dst Port: 4789
Virtual eXtensible Local Area Network
VXLAN Network Identifier (VNI): 20101
Reserved: 0
Ethernet II, Src: 00:00:be:ef:ca:fe (00:00:be:ef:ca:fe), Dst: 00:06:f6:01:cd:42 (00:06:f6:01:cd:42) <-- Start of payload
Type: ARP (0x0806)
Trailer: 000000000000000000000000000000000000
Address Resolution Protocol (reply) <-- is an ARP reply
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: reply (2)
Sender MAC address: 00:00:be:ef:ca:fe (00:00:be:ef:ca:fe) <-- Reply is that of the CGW MAC due to local proxy on SVI
Sender IP address: 10.1.201.11
Target MAC address: 00:06:f6:01:cd:42 (00:06:f6:01:cd:42)
Target IP address: 10.1.201.10
CGW RT2網關字首
缺少網關字首
如上一節關於部分隔離網段中所述,需要在交換矩陣VLAN中學習MAC
- 如果沒有超過MAC老化計時器的流量流向網關,則可能會出現此問題。
- 如果缺少CGW網關字首,則需要確認存在MAC
CGW#show bgp l2vpn evpn route-type 2 0 0000.beef.cafe 10.1.202.1
% Network not in table <-- RT2 not generated on CGW
CGW#show mac address-table address 0000.beef.cafe
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
201 0000.beef.cafe STATIC Vl201
2021 0000.beef.cafe STATIC Vl2021
<-- MAC is not learned in Fabric Vlan 202
Total Mac Addresses for this criterion: 2
網關字首缺失補救
在大多數生產網路中,可能始終存在一些流量。但是,如果您遇到此問題,可以使用以下選項之一來修正問題:
- 添加靜態MAC條目,例如「mac address-table static 0000.beef.cafe vlan 202 interface TwentyFiveGigE1/0/1」
- 使用「mac address-table aging-time <seconds>」增加MAC老化計時器。(請記住,這會增加所有MAC地址的老化時間,因此首選靜態MAC選項)
缺少DEF網關屬性
對於部分隔離網段,有許多附加配置可新增此屬性。
缺少DEF GW屬性補救
確認以下詳細資訊:
- 您運行的是17.12.1或更高版本
- 配置中存在SISF(裝置跟蹤)CLI
- 配置route-map match & set命令並將路由對映應用於BGP鄰居
- 您已刷新BGP通告(您必須清除BGP以使用新屬性重新通告字首
無線漫遊
頻繁漫遊可能導致BGP更新過於頻繁,在交換機宣告它擁有MAC並傳送RT2更新之前,應增加每個時間間隔的漫遊
- 當主機在不同交換機上的兩個AP之間移動時,會發生這種情況。
- 漫遊的預設限制是每180秒5次
Leaf01#sh run | sec l2vpn
l2vpn evpn
replication-type static
flooding-suppression address-resolution disable
ip duplication limit 10 time 180 <--- You can adjust this default in the global l2vpn section
mac duplication limit 10 time 180
Leaf01#sh l2vpn evpn summary
L2VPN EVPN
EVPN Instances (excluding point-to-point): 4
VLAN Based: 4
Vlans: 4
BGP: ASN 65001, address-family l2vpn evpn configured
Router ID: 172.16.254.3
Global Replication Type: Static
ARP/ND Flooding Suppression: Disabled
Connectivity to Core: UP
MAC Duplication: seconds 180 limit 10
MAC Addresses: 13
Local: 6
Remote: 7
Duplicate: 0
IP Duplication: seconds 180 limit 10
IP Addresses: 7
Local: 4
Remote: 3
Duplicate: 0
<...snip...>
為TAC收集的命令
如果此指南未解決您的問題,請收集顯示的命令清單,並將它們附加到TAC服務請求。
要收集的最低資訊
(在重新載入/恢復操作之前收集資料的時間有限)
- 顯示技術事件
- 顯示技術
- 顯示技術資訊集
要收集的詳細資訊
(如果有時間收集更完整的資料,則最好這樣做)
-
show tech
-
show tech evpn
-
show tech platform evpn_vxlan switch <number>
-
show tech platform
-
顯示技術資源
-
show tech sisf
-
show tech isis
-
show tech bgp
-
show monitor event-trace evpn event all
-
show monitor event-trace evpn error all
-
request platform software trace archive
相關資訊
- 在Catalyst 9000系列交換器上實作BGP EVPN路由原則
- DHCP第2層中繼(即將推出)
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
3.0 |
22-Nov-2024 |
術語表中有關聯儲物料清單的更新詳情 |
2.0 |
15-May-2024 |
在Catalyst 9000系列交換器上實作BGP EVPN DHCP第2層中繼檔案中新增的連結 |
1.0 |
20-Sep-2023 |
初始版本 |
由思科工程師貢獻
- Ambrose Taylor
 意見
意見