Catalyst 9000系列交換器上的SISF疑難排解
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本檔案介紹Catalyst 9000系列交換器中使用的交換器整合式安全功能(SISF)。 它還解釋了如何使用SISF以及如何與其他功能互動。
必要條件
需求
本文件沒有特定需求。
採用元件
本檔案中的資訊是根據執行Cisco IOS® XE 17.3.x的Cisco Catalyst 9300-48P
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
附註:請參閱適當的組態設定指南來瞭解使用的命令,以便在其他思科平台上啟用這些功能。
相關產品
本文件也適用於以下硬體和軟體版本:
- Catalyst 9200
- Catalyst 9300
- Catalyst 9400
- Catalyst 9500
- Catalyst 9600
使用17.3.4及更高版本的Cisco IOS XE軟體

附註:本檔案也適用於大多數使用SISF與裝置追蹤的Cisco IOS XE版本。
背景資訊
概觀
SISF提供了一個主機繫結表,並且有一些功能客戶端使用該表中的資訊。通過收集資料包(如DHCP、ARP、ND和RA)來將條目填充到表中,這些資料包跟蹤主機活動並幫助動態填充該表。如果L2域中有靜默主機,則可使用靜態條目向SISF表中新增條目。
SISF使用策略模型來配置交換機上的裝置角色和其他設定。可以在介面或VLAN級別上應用單個策略。如果在VLAN上應用了策略,而在介面上應用了不同的策略,則優先使用介面策略。
SISF還可用於限製表中主機的數量,但IPv4和IPv6行為之間有所不同。如果設定了SISF限制並達到該限制:
- IPv4主機繼續運行,但不會向SISF表中新增超出限制的條目
- 未進入SISF表的IPv6主機不允許進入網路,並且不會向SISF表新增任何新條目。
從16.9.x和更新版本引入了SISF客戶端功能優先順序。它將新增選項來控制到SISF中的更新,如果兩個或更多客戶端正在使用繫結表,則應用來自更高優先順序的更新。此處的例外是「每個mac的IPv4/IPv6的限制地址計數」設定,具有最低優先順序的策略的設定是有效的。
需要啟用裝置跟蹤的一些示例功能包括:
- LISP/EVPN
- Dot1x
- Web驗證
- CTS
- DHCP窺探
附註:優先順序用於選擇策略設定。
從CLI建立的策略具有最高的優先順序(128),因此允許使用者應用不同於程式設計策略中的策略設定。可以手動更改自定義策略下的所有可配置設定。
下一張影象是SISF策略及其讀取方式的示例:
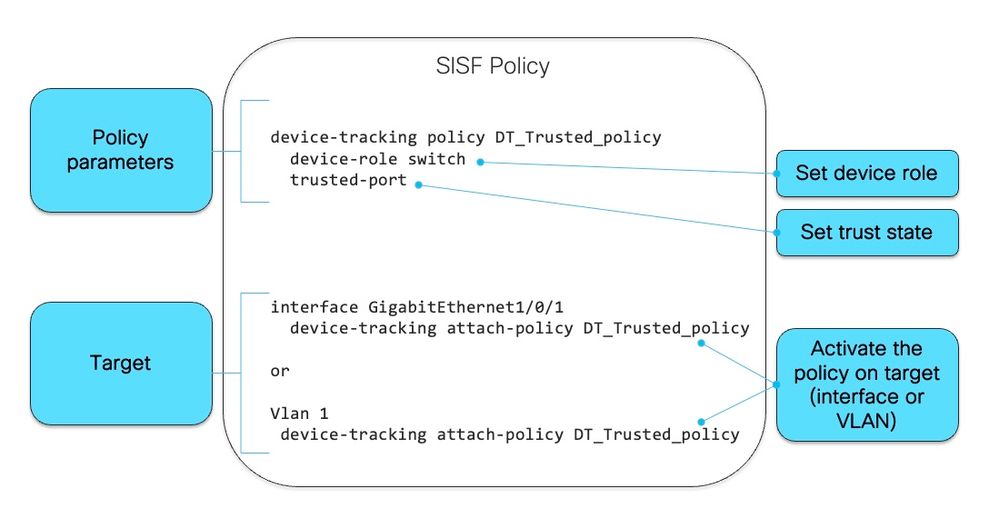
在策略內部,在protocol關鍵字下,您可以選擇檢視用於填充SISF資料庫的資料包型別:
switch(config-device-tracking)#?
device-tracking policy configuration mode:
data-glean binding recovery by data traffic source address
gleaning
default Set a command to its defaults
destination-glean binding recovery by data traffic destination address
gleaning
device-role Sets the role of the device attached to the port
distribution-switch Distribution switch to sync with
exit Exit from device-tracking policy configuration mode
limit Specifies a limit
medium-type-wireless Force medium type to wireless
no Negate a command or set its defaults
prefix-glean Glean prefixes in RA and DHCP-PD traffic
protocol Sets the protocol to glean (default all) <--
security-level setup security level
tracking Override default tracking behavior
trusted-port setup trusted port
vpc setup vpc port
switch(config-device-tracking)#protocol ?
arp Glean addresses in ARP packets
dhcp4 Glean addresses in DHCPv4 packets
dhcp6 Glean addresses in DHCPv6 packets
ndp Glean addresses in NDP packets
udp Gleaning from UDP packets
SISF程式設計和客戶端功能
下表中的功能在啟用SISF時以程式設計方式啟用,或作為SISF的客戶端:
| SISF程式設計功能 |
SISF客戶端功能 |
| VLAN上的LISP |
Dot1x |
| VLAN上的EVPN |
Web驗證 |
| DHCP窺探 |
CTS |
如果在未配置啟用SISF功能的裝置上啟用了SISF客戶端功能,則必須在連線到主機的介面上配置自定義策略。
使用SISF資訊的IPv4功能
- CTS
- IEEE 802.1x
- LISP
- EVPN
- DHCP窺探(僅啟用SISF但不使用)
- IP來源防護
使用SISF資訊的IPv6功能
- IPv6路由器通告(RA)防護
- IPv6 DHCP防護,第2層DHCP中繼
- IPv6重複位址偵測(DAD)代理
- 泛洪抑制
- IPv6來源防護
- IPv6目的地防護
- RA節流器
- IPv6首碼防護
裝置追蹤
裝置跟蹤的主要作用是跟蹤網路中終端節點的存在、位置和移動。SISF會監聽交換機接收的流量,提取裝置標識(MAC和IP地址),並將它們儲存在繫結表中。 許多功能(如IEEE 802.1X、Web驗證、Cisco TrustSec和LISP等)都依賴於此資訊的準確性才能正常運行。 基於SISF的裝置跟蹤支援IPv4和IPv6。 客戶端可以通過五種受支援的方法學習IP:
- DHCPv4
- DHCPv6
- ARP
- NDP
- 資料收集
埠通道上的SISF
支援埠通道(或ether-channel)上的裝置跟蹤。但是配置必須應用於通道組,而不是單個埠通道成員。從繫結角度顯示(且已知)的唯一介面是port-channel。
探測和資料庫調整
探測:
- 在IPDT中,有一個命令通過將初始探測延遲10秒來幫助解決重複地址問題:鏈路接通時「ip device tracking probe delay」。
- 在SISF中,已經有一個內建的等待計時器,該計時器在傳送第一個探測器之前等待。它不可配置,並且解決了相同的問題。由於這是SISF代碼,因此不再需要此命令
資料庫:
在SISF中,可以配置幾個選項來控制條目在資料庫中保留的時間:
tracking enable reachable-lifetime <second|infinite> <-- how long an entry is kept reachable (or keep permanently reachable)
tracking disable stale-lifetime <seconds|infinite> <-- how long and entry is kept inactive before deletion (or keep permanently inactive)
IP裝置追蹤
輪詢主機的條目的生命週期:
- SISF維護每個MAC的IPv4/IPv6繫結,一旦IP學習成功,將繫結轉換到REACHABLE 狀態
- SISF通過監控控制包跟蹤活動客戶端
- 如果客戶端在5分鐘內沒有發出控制資料包,則繫結將轉換到VERIFY狀態並傳送 探測到客戶端
- 如果客戶端不響應探測,則繫結轉換到STALE狀態或REACHABLE狀態
- STALE條目的預設超時為24小時並可配置
- 過時的條目將在24小時後刪除(或配置的超時值)
盜竊檢測
節點盜竊型別:
- IP盜竊(相同IP、不同MAC、不同/相同埠)
- MAC THEFT(相同的MAC、不同的IP、不同的埠)
- MAC IP THEFT(相同mac、相同ip、不同埠)
IP安全性功能
以下是SISF相關的一些功能:
- NDP檢查:檢查IPv6 NDP消息
- NDP地址收集:用通過監聽NDP流量收集的資訊填充繫結表
- 裝置跟蹤:監控終端裝置活動,包括通過某種活動機制
- 監聽:收集NDP、ARP和DHCP消息中的地址。阻止未經授權的郵件
- DHCPv4中繼:將DHCP廣播資料包中繼到已配置的幫助地址。
- NDP和ARP組播抑制:通過轉換為單播或代表目標響應來抑制組播NDP消息。
- DAD代理:重復地址檢測和代表目標客戶端傳送NA
- DHCPv4要求:它強制客戶端通過DHCP
SISF警告
觀察到的一些與SISF相關的最常見行為包括:
- 可通過啟用其他功能(例如dhcp監聽)來啟用SISF
- SISF的預設探測行為可能影響客戶端IP地址分配。
- 啟用SISF後,上行鏈路埠上也會啟用它,這可能會對網路造成影響。
疑難排解
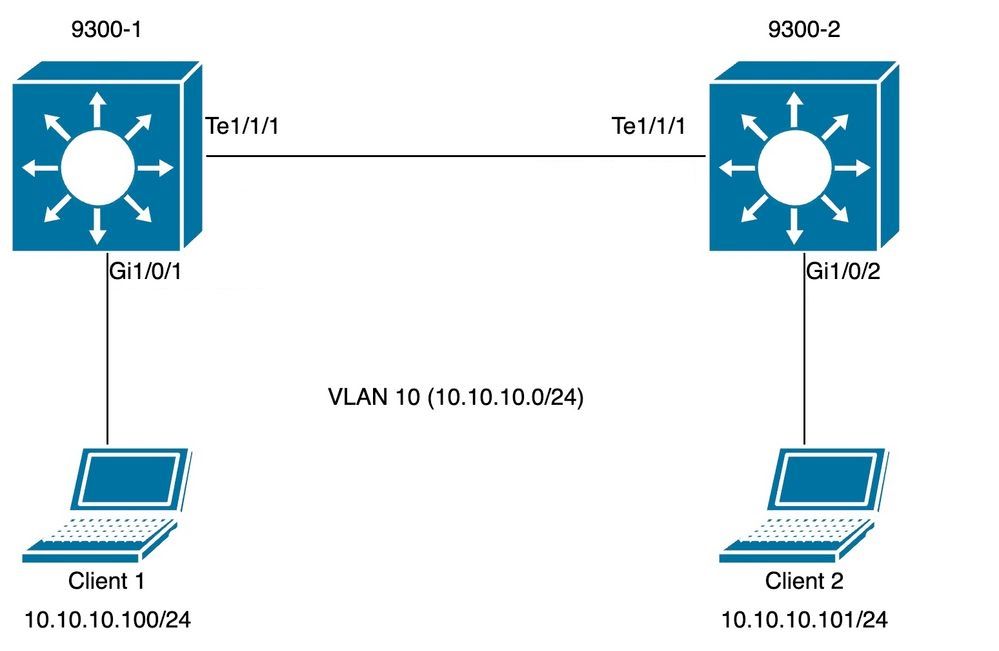
拓撲
拓撲圖用於下一個SISF場景。9300交換機僅屬於第2層,未在客戶端Vlan 10中配置SVI。
注意:本實驗手動啟用了SISF。
組態
在面向接入埠的兩台9300交換機上設定預設SISF配置,而在中繼埠上應用自定義策略來說明預期的SISF輸出。
交換機9300-1:
9300-1#show running-config interface GigabitEthernet 1/0/1 Building configuration... Current configuration : 111 bytes ! interface GigabitEthernet1/0/1 switchport access vlan 10 switchport mode access device-tracking <-- enable default SISF policy end
9300-1#
9300-1#show running-config | section trunk-policy
device-tracking policy trunk-policy <-- custom policy
trusted-port <-- custom policy parameters
device-role switch <-- custom policy parameters
no protocol udp
9300-1# 9300-1#show running-config interface tenGigabitEthernet 1/1/1 Building configuration... Current configuration : 109 bytes ! interface TenGigabitEthernet1/1/1 switchport mode trunk device-tracking attach-policy trunk-policy <-- enable custom SISF policy
end
交換機9300-2:
9300-2#show running-config interface GigabitEthernet 1/0/2 Building configuration... Current configuration : 105 bytes ! interface GigabitEthernet1/0/2 switchport access vlan 10 switchport mode access device-tracking <-- enable default SISF policy end
9300-2#show running-config | section trunk-policy
device-tracking policy trunk-policy <-- custom policy
trusted-port <-- custom policy parameters
device-role switch <-- custom policy parameters
no protocol udp
9300-2#show running-config interface tenGigabitEthernet 1/1/1 Building configuration... Current configuration : 109 bytes ! interface TenGigabitEthernet1/1/1 switchport mode trunk device-tracking attach-policy trunk-policy <-- custom policy applied to interface
end
驗證
可以使用以下命令驗證應用的策略:
show device-tracking policy <policy name>
show device-tracking policies
show device-tracking database
交換機9300-1:
9300-1#show device-tracking policy default Device-tracking policy default configuration: security-level guard device-role node <-- gleaning from Neighbor Discovery gleaning from DHCP gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn Policy default is applied on the following targets: Target Type Policy Feature Target range Gi1/0/1 PORT default Device-tracking vlan all
9300-1#show device-tracking policy trunk-policy Device-tracking policy trunk-policy configuration: trusted-port <-- security-level guard device-role switch <-- gleaning from Neighbor Discovery gleaning from DHCP gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn Policy trunk-policy is applied on the following targets: Target Type Policy Feature Target range Te1/1/1 PORT trunk-policy Device-tracking vlan all 9300-1#
9300-1#show device-tracking policies Target Type Policy Feature Target range Te1/1/1 PORT trunk-policy Device-tracking vlan all Gi1/0/1 PORT default Device-tracking vlan all
9300-1#show device-tracking database Binding Table has 1 entries, 1 dynamic (limit 200000) Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created Preflevel flags (prlvl): 0001:MAC and LLA match 0002:Orig trunk 0004:Orig access 0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned 0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned Network Layer Address Link Layer Address Interface vlan prlvl age state Time left ARP 10.10.10.100 98a2.c07e.7902 Gi1/0/1 10 0005 8s REACHABLE 306 s 9300-1#
交換機9300-2:
9300-2#show device-tracking policy default Device-tracking policy default configuration: security-level guard device-role node <-- gleaning from Neighbor Discovery gleaning from DHCP gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn Policy default is applied on the following targets: Target Type Policy Feature Target range Gi1/0/2 PORT default Device-tracking vlan all
9300-2#show device-tracking policy trunk-policy Device-tracking policy trunk-policy configuration: trusted-port <-- security-level guard device-role switch <-- gleaning from Neighbor Discovery gleaning from DHCP gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn Policy trunk-policy is applied on the following targets: Target Type Policy Feature Target range Te1/1/1 PORT trunk-policy Device-tracking vlan all 9300-2#
9300-2#show device-tracking policies Target Type Policy Feature Target range Te1/1/1 PORT trunk-policy Device-tracking vlan all Gi1/0/2 PORT default Device-tracking vlan all
9300-2#show device-tracking database Binding Table has 1 entries, 1 dynamic (limit 200000) Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created Preflevel flags (prlvl): 0001:MAC and LLA match 0002:Orig trunk 0004:Orig access 0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned 0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned Network Layer Address Link Layer Address Interface vlan prlvl age state Time left ARP 10.10.10.101 98a2.c07e.9902 Gi1/0/2 10 0005 41s REACHABLE 273 s 9300-2#
常見方案
主機裝置上的重複IPv4地址錯誤
問題
交換機傳送的「keepalive」探測器是L2檢查。因此,從交換機的角度來看,在ARP中用作源的IP地址並不重要:此功能可以在未配置IP地址的裝置上使用,因此0.0.0.0的IP源不相關。 當主機收到此消息時,它會回覆並填寫目標IP欄位,其中包含所接收資料包中唯一可用的IP地址,即其自己的IP地址。這可能會導致錯誤重複的IP地址警報,因為作出回覆的主機將自己的IP地址同時視為資料包的源和目標。
建議將SISF策略配置為對其keepalive探測使用自動源。
附註:有關詳細資訊,請參閱有關重複地址問題的文章
預設探測
在沒有本地SVI和預設探測設定時,這是探測資料包:
Ethernet II, Src: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02), Dst: Cisco_76:63:c6 (00:41:d2:76:63:c6) <-- Probe source MAC is the BIA of physical interface connected to client
Destination: Cisco_76:63:c6 (00:41:d2:76:63:c6)
Address: Cisco_76:63:c6 (00:41:d2:76:63:c6)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
Address: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: ARP (0x0806)
Padding: 000000000000000000000000000000000000
Address Resolution Protocol (request)
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
Sender IP address: 0.0.0.0 <-- Sender IP is 0.0.0.0 (default)
Target MAC address: Cisco_76:63:c6 (00:41:d2:76:63:c6)
Target IP address: 10.10.10.101 <-- Target IP is client IP
解決方案
將探測配置為使用主機PC以外的其它地址進行探測。這可以通過以下方法實現
「Keep-Alive」探測的自動來源
為「keep-alive」探測配置自動源,以減少將0.0.0.0用作源IP的使用:
device-tracking tracking auto-source fallback <IP> <MASK> [override]
應用auto-source命令時的邏輯工作如下:
device-tracking tracking auto-source fallback 0.0.0.253 255.255.255.0 [override] <-- Optional parameter
- 將源設定為VLAN SVI(如果存在)。
- 在同一個子網的IP主機表中搜尋源/MAC對。探測源自交換機物理介面MAC +資料庫中現有子網中某個其他主機的IP。
- 使用提供的主機位和遮罩從目的地IP計算來源IP。探測功能是通過偵聽客戶端IP並在配置最後位的情況下在子網中建立探測功能生成的。
附註:如果命令與<override>一起應用,我們總是跳到步驟3。
已修改的探測器
將自動源回退配置設定為使用子網中的IP將修改探測。由於子網中沒有SVI和其它客戶端,因此我們返回到配置中配置的IP/掩碼。
switch(config)#device-tracking tracking auto-source fallback 0.0.0.253 255.255.255.0 <-- it uses .253 for all subnets where there is no existing client and no SVI
以下是已修改的探測封包:
Ethernet II, Src: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02), Dst: Cisco_76:63:c6 (00:41:d2:76:63:c6) <-- Probe source MAC is the BIA of physical interface connected to client
Destination: Cisco_76:63:c6 (00:41:d2:76:63:c6)
Address: Cisco_76:63:c6 (00:41:d2:76:63:c6)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
Address: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: ARP (0x0806)
Padding: 000000000000000000000000000000000000
Address Resolution Protocol (request)
Hardware type: Ethernet (1)
Protocol type: IPv4 (0x0800)
Hardware size: 6
Protocol size: 4
Opcode: request (1)
Sender MAC address: c0:64:e4:cc:66:02 (c0:64:e4:cc:66:02)
Sender IP address: 10.10.10.253 <-- Note the new sender IP is now using the fallback IP configured.
Target MAC address: Cisco_76:63:c6 (00:41:d2:76:63:c6)
Target IP address: 10.10.10.101
有關探測器行為的更多詳細資訊
| 指令 |
動作 (為了選擇裝置跟蹤ARP探測的源IP和MAC地址) |
備註 |
| 裝置跟蹤跟蹤自動源 |
|
我們建議禁用所有中繼埠上的裝置跟蹤以避免MAC抖動。 |
| 裝置跟蹤跟蹤跟蹤自動源覆蓋 |
|
如果沒有SVI,則不建議使用。 |
| 裝置跟蹤跟蹤跟蹤自動源回退<IP> <MASK> |
|
我們建議禁用所有中繼埠上的裝置跟蹤以避免MAC抖動。 計算得出的IPv4地址不能分配給任何客戶端或網路裝置。 |
| 裝置跟蹤跟蹤跟蹤自動源回退<IP> <MASK>覆蓋 |
|
計算得出的IPv4地址不能分配給任何客戶端或網路裝置。 |
device-tracking tracking auto-source fallback <IP> <MASK> [override]命令說明:
根據主機IP,需要保留IPv4地址。
<reserved IPv4 address> = (<host-ip> & <MASK> ) | <IP>
附註:這是一個布林公式
範例.
如果我們使用命令:
device-tracking tracking auto-source fallback 0.0.0.1 255.255.255.0 override
主機IP = 10.152.140.25
IP = 0.0.0.1
掩碼= 24
讓我們將布林公式分成兩部分。
1. 10.152.140.25和255.255.255.0操作:
10.152.140.25 = 00001010.10011000.10001100.00011001
AND
255.255.255.0 = 11111111.11111111.11111111.00000000
RESULT
10.152.140.0 = 00001010.10011000.10001100.00000000
2. 10.152.140.0或0.0.0.1操作:
10.152.140.0 = 00001010.10011000.10001100.00000000
OR
0.0.0.1 = 00000000.00000000.00000000.00000001
RESULT
10.152.140.1 = 00001010.10011000.10001100.00000001
保留的IP = 10.152.140.1
保留的IP =(10.152.140.25和255.255.255.0) |(0.0.0.1)= 10.152.140.1
註:用作子網的DHCP繫結中必須包含用作IP源的地址。
重複IPv6地址錯誤
問題
在網路中啟用IPv6並在VLAN上配置交換虛擬介面(SVI)時,出現重複IPv6地址錯誤。
在普通IPv6 DAD資料包中,IPv6報頭中的Source Address欄位設定為未指定的地址(0:0:0:0:0:0:0:0:0)。 類似於IPv4案例。
在SISF探測中選擇源地址的順序為:
- SVI的本地鏈路地址(如果已配置)
- 使用0:0:0:0:0:0:0
解決方案
我們建議您向SVI配置新增以下命令。這使SVI能夠自動獲取本地鏈路地址;此地址用作SISF探測的源IP地址,從而防止了重複的IP地址問題。
interface vlan <vlan> ipv6 enable
記憶體和CPU利用率提高
問題
當以程式設計方式啟用時,交換器傳送的「keepalive」探測功能會從所有連線埠中廣播。 同一L2域中的連線交換機將這些廣播傳送到其主機,導致源交換機將遠端主機新增到其裝置跟蹤資料庫。 附加主機條目增加了裝置上的記憶體使用率,新增遠端主機的過程增加了裝置的CPU使用率。
建議通過在連線到交換機的上行鏈路上配置策略來限定程式設計策略的範圍,將埠定義為受信任並連線到交換機。
注意:請注意,SISF相關功能(如DHCP監聽)使SISF能夠正常工作,從而可能觸發此問題。
解決方案
在上行鏈路(中繼)上配置策略以停止探測和學習位於其他交換機上的遠端主機(僅需要使用SISF來維護本地主機表)
device-tracking policy DT_trunk_policy trusted-port device-role switch interface <interface> device-tracking policy DT_trunk_policy
裝置跟蹤可達時間太短
問題
由於從IPDT遷移到基於SISF的裝置跟蹤的問題,從較舊版本遷移到16.x和更新版本時,有時會引入非預設可到達時間。
解決方案
建議配置以下內容,恢復到預設的可到達時間:
no device-tracking binding reachable-time
已註冊到Meraki工具的交換機(CPU增加和埠刷新)
問題
當交換機登入Meraki雲監控工具時,此類工具會推出自定義裝置跟蹤策略。
device-tracking policy MERAKI_POLICY security-level glean no protocol udp tracking enable
此策略應用於所有介面而不存在任何區別,也就是說,它不會區分面向其他網路裝置(例如交換機、防火牆路由器等)的邊緣埠和中繼埠。 交換機可以在配置了MERAKI_POLICY的中繼埠上建立多個SISF條目,因此會導致這些埠上的刷新以及CPU使用率增加。
switch#show interfaces port-channel 5
Port-channel5 is up, line protocol is up (connected)
<omitted output> Input queue: 0/2000/0/112327 (size/max/drops/flushes); Total output drops: 0 <-- we have many flushes <omitted output>
switch#show process cpu sorted CPU utilization for five seconds: 26%/2%; one minute: 22%; five minutes: 22% PID Runtime(ms) Invoked uSecs 5Sec 1Min 5Min TTY Process 572 1508564 424873 3550 11.35% 8.73% 8.95% 0 SISF Main Thread 105 348502 284345 1225 2.39% 2.03% 2.09% 0 Crimson flush tr
解決方案
在所有非邊緣介面上設定下一個策略:
configure terminal device-tracking policy NOTRACK no protocol ndp no protocol dhcp6 no protocol arp no protocol dhcp4 no protocol udp exit
interface <interface> device-tracking policy NOTRACK end
具有相同MAC的IP地址不在SISF表中
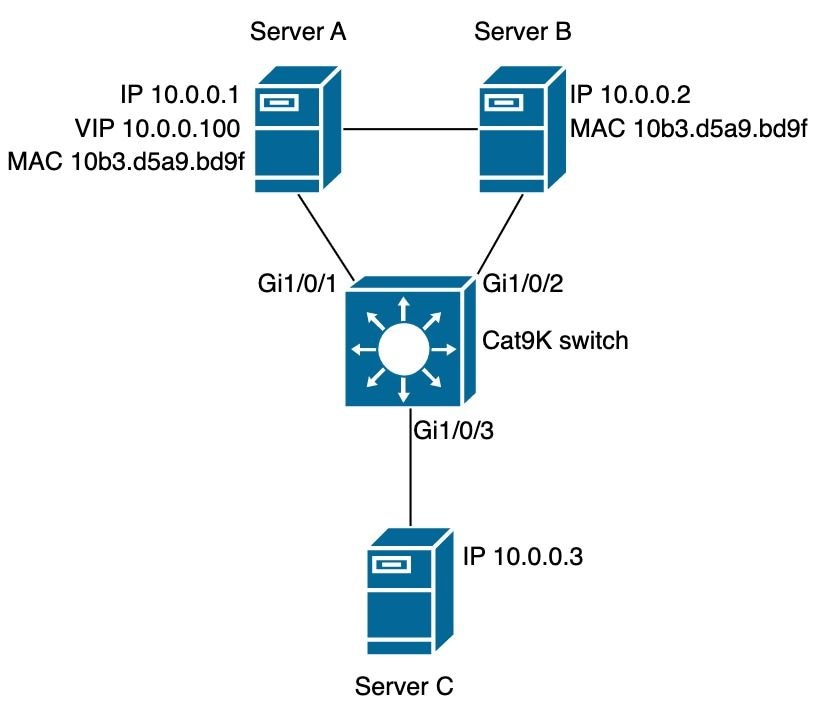
問題
此情況常見於HA(高可用性)模式中具有不同IP地址但共用相同MAC地址的裝置。在共用相同條件(兩個或多個IP地址使用單個MAC地址)的VM環境中也可觀察到。 當處於保護模式的自定義SISF策略處於適當位置時,此條件會阻止連線到所有在SISF表中沒有條目的IP。根據SISF功能,每個MAC地址只獲知一個IP。
附註:17.7.1及後續版本中存在此問題
範例:
- MAC地址為10b3.d5a9.bd9f的IP 10.0.0.1在SISF表上學習,並允許與網路裝置10.0.0.3通訊。
- 但是,共用MAC地址10b3.d659.7858的第二個IP 10.0.0.2和虛擬IP 10.0.0.100未在SISF表中程式設計,並且不允許與網路通訊。
SISF策略
switch#show run | sec IPDT_POLICY device-tracking policy IPDT_POLICY no protocol udp tracking enable
switch#show device-tracking policy IPDT_POLICY Device-tracking policy IPDT_POLICY configuration: security-level guard <-- default mode device-role node gleaning from Neighbor Discovery gleaning from DHCP6 gleaning from ARP gleaning from DHCP4 NOT gleaning from protocol unkn tracking enable Policy IPDT_POLICY is applied on the following targets: Target Type Policy Feature Target range Gi1/0/1 PORT IPDT_POLICY Device-tracking vlan all Gi1/0/2 PORT IPDT_POLICY Device-tracking vlan all
SISF資料庫
switch#show device-tracking database
Binding Table has 2 entries, 2 dynamic (limit 200000)
Codes: L - Local, S - Static, ND - Neighbor Discovery, ARP - Address Resolution Protocol, DH4 - IPv4 DHCP, DH6 - IPv6 DHCP, PKT - Other Packet, API - API created
Preflevel flags (prlvl):
0001:MAC and LLA match 0002:Orig trunk 0004:Orig access
0008:Orig trusted trunk 0010:Orig trusted access 0020:DHCP assigned
0040:Cga authenticated 0080:Cert authenticated 0100:Statically assigned
Network Layer Address Link Layer Address Interface vlan prlvl age state Time left
ARP 10.0.0.3 10b3.d659.7858 Gi1/0/3 10 0005 90s REACHABLE 222 s try 0
ARP 10.0.0.1 10b3.d5a9.bd9f Gi1/0/1 10 0005 84s REACHABLE 220 s try 0
可達性測試伺服器A
ServerA#ping 10.0.0.3 source 10.0.0.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
ServerA#ping 10.0.0.3 source 10.0.0.100 <-- entry for 10.0.0.100 is not on SISF table
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
Packet sent with a source address of 10.0.0.100
.....
可達性測試伺服器B.
ServerB#ping 10.0.0.3 <-- entry for 10.0.0.2 is not on SISF table
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
正在驗證交換機上的丟包。
switch(config)#device-tracking logging
記錄檔
switch#show logging
<omitted output>
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.100 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/1 P=ARP Reason=Packet accepted but not forwarded
<omitted output>
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
%SISF-4-PAK_DROP: Message dropped IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f I/F=Gi1/0/2 P=ARP Reason=Packet accepted but not forwarded
%SISF-4-MAC_THEFT: MAC Theft IP=10.0.0.2 VLAN=10 MAC=10b3.d5a9.bd9f IF=Gi1/0/1 New I/F=Gi1/0/2
解決方案
選項 1:從埠刪除IPDT策略允許ARP資料包和受影響的裝置可訪問
switch(config)#interface gigabitEthernet 1/0/1
switch(config-if)#no device-tracking attach-policy IPDT_POLICY
switch(config-if)#interface gigabitEthernet 1/0/2
switch(config-if)#no device-tracking attach-policy IPDT_POLICY
選項 2:從裝置跟蹤策略中刪除協定arp收集。
switch(config)#device-tracking policy IPDT_POLICY
switch(config-device-tracking)#no protocol arp
選項 3:將IPDT_POLICY的安全級別更改為收集。
switch(config)#device-tracking policy IPDT_POLICY
switch(config-device-tracking)#security-level glean
相關資訊
- 安全配置指南,Cisco IOS XE Bengaluru 17.6.x(Catalyst 9300交換機):配置交換機整合安全功能
- 安全配置指南,Cisco IOS XE Cupertino 17.9.x(Catalyst 9300交換機):配置交換機整合安全功能
- Cisco Catalyst 9000系列交換機整合安全功能(SISF)白皮書
- 思科錯誤ID CSCvx75602 - AR中繼和ND抑制中的SISF記憶體洩漏
- 思科錯誤ID CSCwf33293 - [EVPN SISF]使用EVPN + DHCP修改IPv4/V6的限制地址值所需的自定義方法
- 思科錯誤ID CSCvq22011 - IOS-XE在IPDT從ARP閃爍時丟棄ARP應答
- 思科錯誤ID CSCwc20488 - 每vlan/evi的255偽埠限制
- 思科錯誤ID CSCwh52315 - 9300交換器在連線埠中具有IPDT原則時捨棄ARP回覆
- 思科錯誤ID CSCvd51480 - 解除繫結ip dhcp窺探和裝置跟蹤
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
17-Jan-2024 |
初始版本 |
由思科工程師貢獻
- Luis Escalante Azcona
- Clark Dyson
- Ambrose Taylor
 意見
意見